- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences

You’re Not Powerless in the Face of Online Harassment
- Viktorya Vilk

Eight steps to take.
If you or someone you know is experiencing online harassment, remember that you are not powerless. There are concrete steps you can take to defend yourself and others. First, understand what’s happening to you. If you’re being critiqued or insulted, you can choose to refute it or let it go. But if you’re being abused, naming what you’re experiencing not only signals that it’s a tangible problem, but can also help you communicate with allies, employers, and law enforcement. Next, be sure to document. If you report online abuse and succeed in getting it taken down, you could lose valuable evidence. Save emails, voicemails, and texts. Take screenshots on social media and copy direct links whenever possible. Finally, assess your safety. If you’re being made to feel physically unsafe in any way — trust your instincts. While police may not always be able to stop the abuse (and not all authorities are equally well-trained in dealing with it), at the very least you are creating a record that could be useful later.
Online abuse — from impersonation accounts to hateful slurs and death threats — began with the advent of the internet itself, but the problem is pervasive and growing. A 2017 study from the Pew Research Center found that more than 40% of Americans have experienced online abuse, and more than 60% have witnessed it. People of color and LGBTQ+ people are disproportionately targeted, and women are twice as likely as men to experience sexual harassment online.
- VV Viktorya Vilk is Program Director for Digital Safety and Free Expression at PEN America, where she develops resources, including the Online Harassment Field Manual , and conducts trainings on online abuse, self-defense, and best practices for offering support.
Partner Center

- High contrast
- Press Centre
Search UNICEF
Cyberbullying: what is it and how to stop it, what teens want to know about cyberbullying..

- Available in:
We brought together UNICEF specialists, international cyberbullying and child protection experts, and teamed up with Facebook, Instagram, Snapchat, TikTok and X to answer some of the most common questions about online bullying and give advice on ways to deal with it.
What is cyberbullying?
Cyberbullying is bullying with the use of digital technologies. It can take place on social media, messaging platforms, gaming platforms and mobile phones. It is repeated behaviour, aimed at scaring, angering or shaming those who are targeted. Examples include:
- spreading lies about or posting embarrassing photos or videos of someone on social media
- sending hurtful, abusive or threatening messages, images or videos via messaging platforms
- impersonating someone and sending mean messages to others on their behalf or through fake accounts.
Face-to-face bullying and cyberbullying can often happen alongside each other. But cyberbullying leaves a digital footprint – a record that can prove useful and provide evidence to help stop the abuse.
If you are worried about your safety or something that has happened to you online, you can seek help by calling your national helpline . If your country does not have a helpline, please urgently speak to an adult you trust or seek professional support from trained and experienced carers.
The top questions on cyberbullying
- Am I being bullied online? How do you tell the difference between a joke and bullying?
- What are the effects of cyberbullying?
- How can cyberbullying affect my mental health?
- Who should I talk to if someone is bullying me online? Why is reporting important?
- I’m experiencing cyberbullying, but I’m afraid to talk to my parents about it. How can I approach them?
- How can I help my friends report a case of cyberbullying especially if they don’t want to do it?
- How do we stop cyberbullying without giving up access to the internet?
- How do I prevent my personal information from being used to manipulate or humiliate me on social media?
- Is there a punishment for cyberbullying?
- Technology companies don’t seem to care about online bullying and harassment. Are they being held responsible?
- Are there any online anti-bullying tools for children or young people?

1. Am I being bullied online? How do you tell the difference between a joke and bullying?
Unicef: .
All friends joke around with each other, but sometimes it’s hard to tell if someone is just having fun or trying to hurt you, especially online. Sometimes they’ll laugh it off with a “just kidding,” or “don’t take it so seriously.”
But if you feel hurt or think others are laughing at you instead of with you, then the joke has gone too far. If it continues even after you’ve asked the person to stop and you are still feeling upset about it, then this could be bullying.
And when the bullying takes place online, it can result in unwanted attention from a wide range of people including strangers. Wherever it may happen, if you are not happy about it, you should not have to stand for it.
Call it what you will – if you feel bad and it doesn’t stop, then it’s worth getting help. Stopping cyberbullying is not just about calling out bullies, it’s also about recognizing that everyone deserves respect – online and in real life.
> Back to top

2. What are the effects of cyberbullying?
When bullying happens online it can feel as if you’re being attacked everywhere, even inside your own home. It can seem like there’s no escape. The effects can last a long time and affect a person in many ways:
- Mentally – feeling upset, embarrassed, stupid, even afraid or angry
- Emotionally – feeling ashamed or losing interest in the things you love
- Physically – tired (loss of sleep), or experiencing symptoms like stomach aches and headaches
The feeling of being laughed at or harassed by others, can prevent people from speaking up or trying to deal with the problem. In extreme cases, cyberbullying can even lead to people taking their own lives.
Cyberbullying can affect us in many ways. But these can be overcome and people can regain their confidence and health.

3. How can cyberbullying affect my mental health?
When you experience cyberbullying you might start to feel ashamed, nervous, anxious and insecure about what people say or think about you. This can lead to withdrawing from friends and family, negative thoughts and self-talk, feeling guilty about things you did or did not do, or feeling that you are being judged negatively. Feeling lonely, overwhelmed, frequent headaches, nausea or stomachaches are also common.
You can lose your motivation to do the things that you usually enjoy doing and feel isolated from the people you love and trust. This can perpetuate negative feelings and thoughts which can adversely affect your mental health and well-being.
Skipping school is another common effect of cyberbullying and can affect the mental health of young people who turn to substances like alcohol and drugs or violent behaviour to deal with their psychological and physical pain. Talking to a friend, family member or school counsellor you trust can be a first step to getting help.
The effects of cyberbullying on mental health can vary depending on the medium through which it happens. For example, bullying via text messaging or through pictures or videos on social media platforms has proven to be very harmful for adolescents.
Cyberbullying opens the door to 24-hour harassment and can be very damaging. That’s why we offer in-app mental health and well-being support through our feature “ Here For You .” This Snapchat portal provides resources on mental health, grief, bullying, harassment, anxiety, eating disorders, depression, stress, and suicidal thoughts. It was developed in partnership with leading international advocacy and mental health organizations to help Snapchatters contend with some very real issues. Still, our foundational piece of guidance for any well-being issue is to talk to someone: a friend, parent, caregiver, trusted adult – anyone whom you trust to listen.
At Snap, nothing is more important than the safety and well-being of our community. Reach out and tell us how we might be able to help.
Cyberbullying has the potential of having a negative impact on people's mental health. It's why it's so important that you reach out to someone you trust – whether it's a parent, teacher, friend or caregiver – and let them know what you're going through so that they can help you.
The well-being of our community matters hugely to us, and we recognise that cyberbullying can have an adverse impact on people's mental health. As well as taking strong action against content or behaviour that seeks to shame, bully or harass members of our community, we have partnered with experts to develop our well-being guide to help people learn more about improving their well-being, and keep TikTok a safe and inclusive home for our community.

4. Who should I talk to if someone is bullying me online? Why is reporting important?
If you think you’re being bullied, the first step is to seek help from someone you trust such as your parents, a close family member or another trusted adult.
In your school you can reach out to a counsellor, the sports coach or your favourite teacher – either online or in person.
And if you are not comfortable talking to someone you know, search for a helpline in your country to talk to a professional counsellor.
If the bullying is happening on a social platform, consider blocking the bully and formally reporting their behaviour on the platform itself. Social media companies are obligated to keep their users safe.
For bullying to stop, it needs to be identified and reporting it is key.
It can be helpful to collect evidence – text messages and screen shots of social media posts – to show what’s been going on.
For bullying to stop, it needs to be identified and reporting it is key. It can also help to show the bully that their behaviour is unacceptable.
If you are in immediate danger, then you should contact the police or emergency services in your country.
Facebook/Instagram
At Meta, we take bullying and harassment situations seriously. Bullying and harassment is a unique challenge and one of the most complex issues to address because context is critical. We work hard to enforce against this content while also equipping our community with tools to protect themselves in ways that work best for them.
If you're experiencing bullying online, we encourage you to talk to a parent, teacher or someone else you can trust – you have a right to be safe and supported.
We also make it easy to report bullying directly within Facebook or Instagram. You can send our team a report from a post, comment, story or direct message (DM). Your report is anonymous; the account you reported won’t see who reported them. We have a team who reviews these reports 24/7 around the world in 70+ languages and we will remove anything that violates our policies.
Meta’s Family Center offers resources, insights and expert guidance to help parents, guardians and trusted adults support their teen’s online experiences across our technologies. Additionally, the Meta Safety Center provides bullying prevention resources that can help teens seeking support for issues related to bullying like what to do if you or a friend is being bullied or if you've been called a bully. For educators , we have expert-backed tips on how to proactively handle and work to implement bullying prevention strategies
Bullying is something no one should have to experience, either in person or online.
Snapchat’s Community Guidelines clearly and explicitly prohibit bullying, intimidation, and harassment of any kind. We don’t want it on the platform; it’s not in keeping with why Snapchat was created and designed. Learn more here .
Letting us know when you experience or witness someone breaking our rules allows us to take action, which helps to protect you and other members of our community. In addition to reporting violating content or behaviour to Snapchat, speak with a friend, parent, caregiver, or other trusted adult. Our goal is for everyone to stay safe and have fun!
Everyone has the right to feel safe and to be treated with respect and dignity. Bullying and harassment are incompatible with the inclusive environment we aim to foster on TikTok.
If you ever feel someone is bullying you or otherwise being inappropriate, reach out to someone you trust - for example, a parent, a teacher or a caregiver – who can provide support.
We deploy both technology and thousands of safety professionals to help keep bullying off TikTok. We also encourage our community members to make use of the easy in-app reporting tools to alert us if they or someone they know has experienced bullying. You can report videos, comments, accounts and direct messages so that we can take appropriate action and help keep you safe. Reports are always confidential.
You can find out more in our Bullying Prevention guide for teens, caregivers, and educators on how to identify and prevent bullying, and provide support.
Being the target of bullying online is not easy to deal with. If you are being cyberbullied, the most important thing to do is to ensure you are safe. It’s essential to have someone to talk to about what you are going through. This may be a teacher, another trusted adult, or a parent. Talk to your parents and friends about what to do if you or a friend are being cyberbullied.
We encourage people to report accounts to us that may break our rules . You can do this on our Help Center or through the in-post reporting mechanism by clicking on the “Report a post” option.
Last updated: January 2022.

5. I’m experiencing cyberbullying, but I’m afraid to talk to my parents about it. How can I approach them?
If you are experiencing cyberbullying, speaking to a trusted adult – someone you feel safe talking to – is one of the most important first steps you can take.
Talking to parents isn’t easy for everyone. But there are things you can do to help the conversation. Choose a time to talk when you know you have their full attention. Explain how serious the problem is for you. Remember, they might not be as familiar with technology as you are, so you might need to help them to understand what’s happening.
They might not have instant answers for you, but they are likely to want to help and together you can find a solution. Two heads are always better than one! If you are still unsure about what to do, consider reaching out to other trusted people . There are often more people who care about you and are willing to help than you might think!

6. How can I help my friends report a case of cyberbullying especially if they don’t want to do it?
Anyone can become a victim of cyberbullying. If you see this happening to someone you know, try to offer support.
It is important to listen to your friend. Why don’t they want to report being cyberbullied? How are they feeling? Let them know that they don’t have to formally report anything, but it’s crucial to talk to someone who might be able to help.
Anyone can become a victim of cyberbullying.
Remember, your friend may be feeling fragile. Be kind to them. Help them think through what they might say and to whom. Offer to go with them if they decide to report. Most importantly, remind them that you’re there for them and you want to help.
If your friend still does not want to report the incident, then support them in finding a trusted adult who can help them deal with the situation. Remember that in certain situations the consequences of cyberbullying can be life threatening.
Doing nothing can leave the person feeling that everyone is against them or that nobody cares. Your words can make a difference.
We know that it can be hard to report bullying, but everyone deserves to feel safe online. If your friend is experiencing cyberbullying, encourage them to talk to a parent, a teacher or an adult they trust.
Reporting content or accounts to Facebook or Instagram is anonymous and can help us better keep our platforms safe. Bullying and harassment are highly personal by nature, so in many instances, we need a person to report this behaviour to us before we can identify or remove it. You can report something you experience yourself, but it’s also just as easy to submit a report for one of your friends. You can find more information on how to report something on our How to Report Bullying section at the Meta Safety Center.
You and your friends may be reluctant to report to a technology platform for any number of reasons, but it’s important to know that reporting on Snapchat is confidential and easy. And remember: You can report Snaps (photos and videos), Chats (messages) and accounts – about your own experiences or on behalf of someone else.
In the more public places of Snapchat, like Stories and Spotlight, simply press and hold on the piece of content and a card with “Report Tile” (as one option) will appear in red. Click that link and our reporting menu will appear. Bullying and harassment are among the first categories in the reporting list. Just follow the prompts and provide as much information as you can about the incident. We appreciate you doing your part to help us protect the Snapchat community!
If you believe another member of the TikTok community is being bullied or harassed, there are ways you can provide support. For example, you can make a confidential report on TikTok so that we take appropriate action and help keep your friend safe.
If you know the person, consider checking in with them and encourage them to read our Bullying Prevention guide so they can find out more information about how to identify bullying behaviour and take action.
If your friends are experiencing cyberbullying, encourage them to talk to a parent, a teacher or an adult they trust.
If a friend of yours does not want to report their experience, you can submit a bystander report on their behalf. This can include reports of private information , non -consensual nudity or impersonation.

7. How do we stop cyberbullying without giving up access to the Internet?
Being online has so many benefits. However, like many things in life, it comes with risks that you need to protect against.
If you experience cyberbullying, you may want to delete certain apps or stay offline for a while to give yourself time to recover. But getting off the Internet is not a long-term solution. You did nothing wrong, so why should you be disadvantaged? It may even send the bullies the wrong signal — encouraging their unacceptable behaviour.
We need to be thoughtful about what we share or say that may hurt others.
We all want cyberbullying to stop, which is one of the reasons reporting cyberbullying is so important. But creating the Internet we want goes beyond calling out bullying. We need to be thoughtful about what we share or say that may hurt others. We need to be kind to one another online and in real life. It's up to all of us!
We’re continuously developing new technologies to encourage positive interactions and take action on harmful content, and launching new tools to help people have more control over their experience. Here are some tools you can use:
- Comment warnings: When someone writes a caption or a comment that our AI detects as potentially offensive or intended to harass, we will show them an alert that asks them to pause and reflect on whether they would like to edit their language before it’s posted.
- Comment and message controls: Comments with common offensive words, phrases or emojis, and abusive messages or messages from strangers can be automatically hidden or filtered out with the ‘ Hidden words ’ setting, which is defaulted on for all people. If you want an even more personalized experience, you can create a custom list of emojis, words or phrases you don’t want to see, and comments containing these terms won’t appear under your posts and messages will be sent to a filtered inbox. All Instagram accounts have the option to switch off DMs from people they don’t follow. Messenger also gives you the option to ignore a conversation and automatically move it out of your inbox, without having to block the sender.
- Block and Mute: You can always block or mute an account that is bullying you, and that account will not be notified. When you block someone on Instagram, you’ll also have the option to block other accounts they may have or create, making it more difficult for them to interact with you.
- Restrict: With ‘Restrict,’ you can protect your account from unwanted interactions in a quieter, or more subtle way. Once Restrict is enabled, comments on your posts from a person you have restricted will only be visible to that person. You can choose to view the comment by tapping “See Comment”; approve the comment so everyone can see it; delete it; or ignore it. You won’t receive any notifications for comments from a restricted account.
- Limits: You can automatically hide comments and DM requests from people who don’t follow you, or who only recently followed you. If you’re going through an influx of unwanted comments or messages — or think you may be about to — you can turn on Limits and avoid it.
Our priority is to foster a welcoming and safe environment where people feel free to express themselves authentically. Our Community Guidelines make clear that we do not tolerate members of our community being shamed, bullied or harassed.
We use a combination of technology and moderation teams to help us identify and remove abusive content or behaviour from our platform.
We also provide our community with an extensive range of tools to help them better control their experience – whether it's control over exactly who can view and interact with your content or filtering tools to help you stay in control of comments. You can find out about them on our Safety Centre .
Since hundreds of millions of people share ideas on X every day, it’s no surprise that we don’t all agree with each other all the time. That’s one of the benefits of a public conversation in that we can all learn from respectful disagreements and discussions.
But sometimes, after you’ve listened to someone for a while, you may not want to hear them anymore. Their right to express themselves doesn’t mean you’re required to listen. If you see or receive a reply you don’t like, unfollow and end any communication with that account. If the behaviour continues, it is recommended that you block the account . If you continue receiving unwanted, targeted and continuous replies on X, consider reporting the behaviour to X here .
We are also working proactively to protect people using our service through a combination of human review and technology. Learn more about how to feel safer on X here .

8. How do I prevent my personal information from being used to manipulate or humiliate me on social media?
Think twice before posting or sharing anything on digital platforms – it may be online forever and could be used to harm you later. Don’t give out personal details such as your address, telephone number or the name of your school.
Learn about the privacy settings of your favourite social media apps. Here are some actions you can take on many of them:
- You can decide who can see your profile, send you direct messages or comment on your posts by adjusting your account privacy settings.
- You can report hurtful comments, messages, photos and videos and request they be removed.
- Besides ‘unfriending’, you can completely block people to stop them from seeing your profile or contacting you.
- You can also choose to have comments by certain people to appear only to them without completely blocking them.
- You can delete posts on your profile or hide them from specific people.
On most of your favourite social media, people aren't notified when you block, restrict or report them.

9. Is there a punishment for cyberbullying?
Most schools take bullying seriously and will take action against it. If you are being cyberbullied by other students, report it to your school.
People who are victims of any form of violence, including bullying and cyberbullying, have a right to justice and to have the offender held accountable.
Laws against bullying, particularly on cyberbullying, are relatively new and still do not exist everywhere. This is why many countries rely on other relevant laws, such as ones against harassment, to punish cyberbullies.
In countries that have specific laws on cyberbullying, online behaviour that deliberately causes serious emotional distress is seen as criminal activity. In some of these countries, victims of cyberbullying can seek protection, prohibit communication from a specified person and restrict the use of electronic devices used by that person for cyberbullying, temporarily or permanently.
However, it is important to remember that punishment is not always the most effective way to change the behaviour of bullies. Sometimes, focusing on repairing the harm and mending the relationship can be better.
On Facebook, we have a set of Community Standards , and on Instagram, we have Community Guidelines . We take action when we are aware of content that violates these policies, like in the case of bullying or harassment, and we are constantly improving our detection tools so we can find this content faster.
Bullying and harassment can happen in many places and come in many different forms from making threats and releasing personally identifiable information to sending threatening messages and making unwanted malicious contact. We do not tolerate this kind of behavior because it prevents people from feeling safe and respected on our apps.
Making sure people don’t see hateful or harassing content in direct messages can be challenging, given they’re private conversations, but we are taking steps to take tougher action when we become aware of people breaking our rules. If someone continues to send violating messages, we will disable their account. We’ll also disable new accounts created to get around our messaging restrictions and will continue to disable accounts we find that are created purely to send harmful messages.
On Snapchat, reports of cyberbullying are reviewed by Snap’s dedicated Trust & Safety teams, which operate around the clock and around the globe. Individuals found to be involved in cyberbullying may be given a warning, their accounts might be suspended or their accounts could be shut down completely.
We recommend leaving any group chat where bullying or any unwelcome behaviour is taking place and please report the behaviour and/or the account to us.
Our Community Guidelines define a set of norms and common code of conduct for TikTok and they provide guidance on what is and is not allowed to make a welcoming space for everyone. We make it clear that we do not tolerate members of our community being shamed, bullied or harassed. We take action against any such content and accounts, including removal.
We strongly enforce our rules to ensure all people can participate in the public conversation freely and safely. These rules specifically cover a number of areas including topics such as:
- Child sexual exploitation
- Abuse/harassment
- Hateful conduct
- Suicide or self-harm
- Sharing of sensitive media, including graphic violence and adult content
As part of these rules, we take a number of different enforcement actions when content is in violation. When we take enforcement actions, we may do so either on a specific piece of content (e.g., an individual post or Direct Message) or on an account.
You can find more on our enforcement actions here .

10. Technology companies don’t seem to care about online bullying and harassment. Are they being held responsible?
Technology companies are increasingly paying attention to the issue of online bullying.
Many of them are introducing ways to address it and better protect their users with new tools, guidance and ways to report online abuse.
But it is true that more is needed. Many young people experience cyberbullying every day. Some face extreme forms of online abuse. Some have taken their own lives as a result.
Technology companies have a responsibility to protect their users especially children and young people.
It is up to all of us to hold them accountable when they’re not living up to these responsibilities.

11. Are there any online anti-bullying tools for children or young people?
Each social platform offers different tools (see available ones below) that allow you to restrict who can comment on or view your posts or who can connect automatically as a friend, and to report cases of bullying. Many of them involve simple steps to block, mute or report cyberbullying. We encourage you to explore them.
Social media companies also provide educational tools and guidance for children, parents and teachers to learn about risks and ways to stay safe online.
Also, the first line of defense against cyberbullying could be you. Think about where cyberbullying happens in your community and ways you can help – by raising your voice, calling out bullies, reaching out to trusted adults or by creating awareness of the issue. Even a simple act of kindness can go a long way.
The first line of defense against cyberbullying could be you.
If you are worried about your safety or something that has happened to you online, urgently speak to an adult you trust. Many countries have a special helpline you can call for free and talk to someone anonymously. Visit United for Global Mental Health to find help in your country.
We have a number of anti-bullying tools across Facebook and Instagram:
- You can block people, including any existing and new accounts they might create.
- You can mute an account and that account will not be notified.
- You can limit unwanted interactions for a period of time by automatically hiding comments and message requests from people who don’t follow you, or who only recently followed you.
- You can use ‘ Restrict ’ to discreetly protect your account without that person being notified.
- You can moderate comments on your own posts.
- You can modify your settings so that only people you follow can send you a direct message.
- We will notify someone when they’re about to post something that might cross the line, encouraging them to reconsider.
- We automatically filter out comments and message requests that don’t go against our Community Guidelines but may be considered inappropriate or offensive. You can also create your own custom list of emojis, words or phrases that you don’t want to see.
For more tips and ideas, visit Instagram’s Safety page and Facebook’s Bullying Prevention Hub . We also offer resources, insights and expert guidance for parents and guardians on our Family Center .
We want teens and young adults to be aware of the blocking and removal functions on Snapchat. Clicking on the person’s avatar will bring up a three-dot menu in the upper right-hand corner. Opening that menu offers the option of “Manage Friendship,” which, in turn, offers the ability to Report, Block or Remove the person as a friend. Know that if you block someone, they will be told that their Snaps and Chats to you will be delivered once the relationship is restored.
It’s also a good idea to check privacy settings to ensure they continue to be set to the default setting of “Friends Only.” This way, only people you’ve added as Friends can send you Snaps and Chats.
We also recommend reviewing your Friends’ list from time to time to ensure it includes those people you still want to be friends with on Snapchat.
Alongside the work that our safety teams do to help keep bullying and harassment off our platform, we provide an extensive range of tools to help you control your TikTok experience. You can find these in full on our Safety Centre . Here are a few highlights:
- You can restrict who comments on your videos to no one, just friends or everyone (for those aged under 16, the everyone setting is not available)
- You can filter all comments or those with specific keywords that you choose. By default, spam and offensive comments are hidden from users when we detect them.
- You can delete or report multiple comments at once, and you can block accounts that post bullying or other negative comments in bulk too, up to 100 at a time.
- A comment prompt asks people to reconsider posting a comment that may be inappropriate or unkind, reminding them of our Community Guidelines and allowing them to edit their comments before sharing.
We want everybody to be safe on X. We continue to launch and improve tools for people to feel safer, be in control and manage their digital footprint. Here are some safety tools anyone on X can use:
- Select who can reply to your posts – either everyone, only people you follow or only people you mention
- Mute – removing an account's posts from your timeline without unfollowing or blocking that account
- Block – restricting specific accounts from contacting you, seeing your posts, and following you
- Report – filing a report about abusive behaviour
- Safety mode – a feature that temporarily blocks accounts for using potentially harmful language or sending repetitive and uninvited replies or mentions.
With special thanks to: Meta, Snap, TikTok and X (formerly known as Twitter). Last updated: February 2024.
To anyone who has ever been bullied online: You are not alone
TikTok stars Charli and Dixie D'Amelio open up about their personal experience of being bullied and share tips on how to make the internet a better place.
Reporting abuse and safety resources
Facebook instagram kik snapchat, tiktok tumblr wechat whatsapp youtube x, take action to stop cyberbullying.
The consequences of cyberbullying can be devastating. Youth can take action to stop it
5 ways to support your mental health online
Tips on how to look after yourself and others
Contribute to Kindly - help stop cyberbullying
Kindly - A UNICEF initiative to end cyberbullying — one message at a time
Mental health and well-being
Tips and resources to help you support your child and yourself
Resources for Prevention and Response to Online Harassment
What is online harassment.
Online harassment is a form of stalking, bullying, or harassment using the Internet or other electronic means. This harassment comes in a variety of forms including: sending threatening emails or direct messages/instant messages, filing false claims or police reports (swatting), or posting personal information online (doxxing). Cyberstalking is a type of online harassment to stalk or harass a victim. We've compiled the below resources to help prevent and respond to online harassment.
Berkeley Resources:
- For urgent 24/7 free and confidential support , call the Care Line at (510) 643-2005.
- For non-urgent support and questions, call the PATH to Care Center’s Main Line at (510) 642-1988.
- Email [email protected] or call (510) 643-7985.
- Visit the CAPS website or call (510) 642-9494 or, after-hours, (855) 817-5667.
Additional Resources:
Consumer Reports Security Planner : CR Security Planner is a free, easy-to-use guide to staying safer online. It provides personalized recommendations and expert advice on topics including: keeping social media accounts from being hacked, locking down devices, and reducing intrusive tracking by websites.
Heartmob Online Harassment Resources : HeartMob is a community dedicated to helping those experiencing online harassment.
Heartmob Technical Safety Guide : This guide will walk you through the immediate steps to take to feel safe and give you information to make informed decisions.
Heartmob Social Media Safety Guides : Social Media Safety Guides for Facebook, Twitter, Reddit, Tumblr, and Youtube - every guide gives user-friendly information on how to use each platforms' reporting and privacy tools.
OnlineSOS Action Center : OnlineSOS empowers people facing online harassment. The Action Center provides simple, actionable information, so you can choose what to do next.
UC Berkeley Privacy Office Advisory on How to Protect Yourself from Doxxing : Provides tips for preventing the unwanted exposure of private information online (doxxing) and for reporting incidents of doxxing to Campus officials.
Internet Matters.Org: Resources to help combat Cyberbullying. Internet Matters is a non-profit organization with the goal of keeping kids safe online. However, these tips can be used to also help adults protect themselves against cyberbullying.
EndTechAbuse. Org CyberAbuse Project Toolkit : EndTechAbuse.Org is a non-profit organization aimed at preventing cyber abuse, including cyber bullying, doxxing and the unwanted sharing of intimate images.
GoodTherapy.org : Article detailing how to mitigate online harassment and trolling.

Cyber-Bullying and Online Harassment: Awareness and Best Practices for Prevention
Oct 09, 2014
210 likes | 358 Views
Cyber-Bullying and Online Harassment: Awareness and Best Practices for Prevention. By Edward J. Lazaros, Ph.D. Department of Technology Ball State University Muncie, IN 47306 Phone: 765-285-5647 Fax: 765-285-2162 E-mail: [email protected]. Awareness.
Share Presentation
- online harassment
- cell phones
- des moines school
- rights 1 st amendment

Presentation Transcript
Cyber-Bullying and Online Harassment: Awareness and Best Practices for Prevention By Edward J. Lazaros, Ph.D. Department of Technology Ball State University Muncie, IN 47306 Phone: 765-285-5647 Fax: 765-285-2162 E-mail: [email protected]
Awareness • School bullying has typically occurred when one individual is in a position of power over another because of a difference in physical strength or stature. • Unlike face-to-face bullying, cyber-bullying can be perpetrated by anyone. bp3.blogger.com
Awareness • As Beckerman & Nocero (2003) report “anonymity is a factor in why this form of harassment is growing. Sitting behind a computer working the keyboard gives students a sense of power and control they do not have in a face-to-face situation” (p. 39). blogs.edweek.org
Awareness • Cyber-bullying and online harassment are often confused. Smith, Mahdavi, Carvalho, Fisher, Russell, and Tippett (2008) define cyber-bullying as “an aggressive, intentional act carried out by a group or individual, using electronic forms of contract, repeatedly and over time against a victim who cannot easily defend him or herself” (p. 376). • According to Wolak, Mitchell, and Finkelhor (2007), “we do not recommend using the term “bullying” to describe all online interpersonal offenses, because they vary so widely in their characteristics. We suggest using “online harassment,” with disclaimers that it does not constitute bullying unless it is part of or related to offline bullying” (p. 57).
Complexity of the Problem • Because students are using technology, it is often difficult to monitor and prevent these incidents. Often, it is difficult to investigate these incidents. • Authorities often have difficulty identifying who is causing the bullying or harassment. www.piquaoh.org
Complexity of the Problem • In 2006, Megan Meier started talking to a boy named Josh Evans on MySpace. He claimed to be a 16-year-old boy who lived nearby and was home schooled. • "Megan gets an e-mail, or a message from Josh on her MySpace on Oct. 15, 2006, saying, 'I don't know if I want to be friends with you any longer because I hear you're not nice to your friends,'“ He also posted lies about her online. • Josh never existed. It was 49 year old Lori Drew who was the mother of one of Megan’s former friends.
Complexity of the Problem • Keith and Martin (2004) describe why technology purchased to keep children safe may become cyber-bullying or harassment instruments: In the past several years, parents have provided cell phones for their children in order to keep track of them and to keep them safe. The same cell phones that make parents feel more connected to their children have become tools of harassment. And the newest forms of cell phones include the ability to send text messages, pictures, and even live video. In the hands of bored teenagers, these additions can become weapons for bullies to spread rumors as well as pictures of unsuspecting kids in locker rooms (p. 225).
Complexity of the Problem • It is often not easy for a school administrator to determine the perpetrator. As Beckerman & Nocero (2003) report, “it changes with each transfer, much like the elementary school game of “telephone” – the end message never matches the original. And, because the original was generated to create anger and frustration, the problem is magnified” (p. 39). • As Beckerman & Nocero report “just when you think you have located the culprit, you find out that the screen name and password have been shared with others or the original screen name has been subtly modified to create confusion. For example, John234 becomes J0hn234” (p. 39).
First Amendment Protection • Prior to school administrators intervening and using non-legal solutions or the resorting to the law to deal with cyber-bullying or online harassment, consideration must first be given to the First Amendment rights of the student perpetrator. • The U.S. Constitution Bill of Rights 1st Amendment does offer protection. According to Madison (1791), “Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the Government for a redress of grievances” (p. 1).
First Amendment Protection • A landmark First Amendment case pertaining to free speech in school was Tinker v. Des Moines. • In Tinker v. Des Moines (1969), John Tinker and his siblings wore black armbands to their Des Moines school to protest the Vietnam War. • The principals of the school suspended the children because they felt the armbands would provoke disturbances. • This case was brought before the United States Supreme Court voted seven to two in favor of Tinker, based on the First Amendment to the United States Constitution dealing with free speech, press, and assembly. • The principals did not provide evidence to show that wearing the armbands would substantially interfere with appropriate school discipline.
First Amendment Protection • School officials should try to apply the Tinker principle in every situation. They should try to determine if the situation substantially interferes with appropriate school discipline. Failing to do so could be costly for the school.
First Amendment Protection • In Dwyer v. Oceanport School District (2005), The United States District Court of New Jersey found that the Oceanport School District in New Jersey had to pay an 8th grade student Ryan Dwyer a $117,500 settlement in 2005 because they violated the First Amendment rights when he was suspended from school in 2003 for a website that he created. www.oceanport.k12.nj.us
First Amendment Protection • The website criticized the Maple Place school in Oceanport, New Jersey. The website criticized individual teachers and the school principal as well as a derogatory picture of the school principal. Interestingly, the website made various references to First Amendment rights, including: “This page protected by the U.S. Constitution”, and “Don’t even try to make me take my website down because it is illegal to do so”. He created the website at his house and outside of school hours. The court found that Ryan did not publish any material which could reasonably be expected to cause a material and substantial disruption to the operation of the school. Because of this, he could not be disciplined without violating his First Amendment rights to free speech.
First Amendment Protection • Threats of violence are not protected by the First Amendment, so school administrators should also determine if there is violence associated with the cyber-bullying situation. • In Watts v. United States (1969), the Supreme Court said that threats of violence are not protected by the First Amendment. • When a student is involved with a cyber-bullying or online harassment incident that substantially interferes with appropriate school discipline and violence is prevalent, the school will most likely be able to punish the student for his/her actions.
First Amendment Protection • In J.S. ex rel H.S. v. Bethlehem Area School District (2002), a student created a web site which had an image of a teacher’s face that changed to resemble Adolf Hitler. The same teacher was depicted with a decapitated head with dripping blood. • The web site requested donations of $20.00 so that a hit man could be hired to kill the teacher. • The Supreme Court in Pennsylvania decided that although the web site was not created at school, the site was aimed at a specific school and it’s personnel and did cause a material disruption when using the Tinker (1969) standard so the student could be punished for the web site. www.wallpaperez.info
Best Practices for Cyber Bullying • Hummell (2007) recommends schools develop acceptable use policies (AUPs). • McKinney (n.d.) also emphasizes the importance of an acceptable use policy, “an acceptable use policy will assist staff, students and their parents know and comply with appropriate boundaries” (p. 90). • According to McKinney (n.d.), “disciplinary measures for violating the acceptable use policy or otherwise misusing or abusing the Internet should be listed in the policy and the student handbook” (p. 91).
Best Practices for Cyber Bullying • Keith and Martin (2004, p.227) recommend the following Tips for children: • Never share or give out personal information, PIN numbers, phone numbers, etc. • Tell a trusted adult. • Do not read messages by cyber bullies. • Do not delete messages; they can be used to take action. • Bullying through instant messaging and chat rooms can often be blocked. • Do not open a message from someone you don’t know. • Do not reply to the person bullying or harassing you.
Best Practices for Cyber Bullying • Keith and Martin (2004, p.227) recommend the following Tips for parents: • Pay attention! Know how and when your children are using the Internet. • Become more tech savvy. • Install blocking or filtering software. • Encourage your child to talk to you if they are being bullied. • Limit your child’s time using the Internet. • Develop a family online agreement
Best Practices for Cyber Bullying • Keith and Martin (2004, p.227) recommend the following Tips for schools: • Develop school policies for acceptable Internet and cell phone use. Enforce them. • Zero tolerance for bullying in any form. • Ensure that children and young people are aware that all bullying concerns will be dealt with sensitively and effectively. • Ensure that parents / guardians expressing bullying concerns have them taken seriously.
Closing Recommendation! • Do what you do best as technology teachers! Educate students about cyber-bullying and online harassment. This is one way to make positive inroads to curb these problems in the educational setting.
Works Cited • Beckerman, L., & Nocero, J. (2003). High-tech student hate mail.Education Digest, 68(6), 37-40. • Dwyer v. Oceanport School District No. 03-6005 (2005). • Hummel, L. (2007). Cyber-bullying: what is it and how to prevent it.Delta Kappa Gamma Bulletin, 73(3), 26-27. • In J.S. ex rel H.S. v. Bethlehem Area School District., 569 A.2d 639 (2002). • Keith, S. & Martin, M. (2004). Cyber-bullyng: Creating a culture of respect in a cyber world. Reclaiming Children & Youth, 13(4), 224-228. • Madison, J. (1791). United States bill of rights. Philadelphia. • McKinney, J. (n.d.). The legal handbook for Indiana school administrators: Educators.cc. • Smith, P., Mahdavi, J., Carvalho, D., Fisher, S., Russell, S., &Tippett, N. (2008). Cyberbullying: its nature and impact in secondary school pupils. Journal of Child Psychology and Psychiatry, 49(4), 376-385. • Tinker v. DesMoines School Dist., 393 U.S. 503 (1969). • Watts v. United States, 394 U.S. 705 (1969). • Wolak, J., Mitchell, K., & Finkelhor, D. (2007). Does online harassment constitute bullying? An exploration of online harassment by known peers and online-only contacts. Journal of Adolescent Health, 46(6), 51-58.
- More by User

PREVENTION OF SEXUAL HARASSMENT
PREVENTION OF SEXUAL HARASSMENT Agenda Definition Types Forms of Sexual Harassment Resolution Techniques Complaint procedures Military Whistleblowers Protection Act Army’s Equal Opportunity Policy Equal treatment for soldiers, family members, and DoD civilian employees
1.17k views • 22 slides
![online harassment presentation Cyber Security Awareness [Everything You Were Afraid to Know About Computer Security, But Always Wanted to Ask]](https://cdn0.slideserve.com/59767/slide1-dt.jpg)
Cyber Security Awareness [Everything You Were Afraid to Know About Computer Security, But Always Wanted to Ask]
Cyber Security Awareness [Everything You Were Afraid to Know About Computer Security, But Always Wanted to Ask]. Commonwealth of Mass. Information Technology Division November, 2008. Objectives for Today. Understand network security threats Learn simple defensive measures
1.03k views • 33 slides

Cyber Security & Infrastructure Protection
Cyber Security & Infrastructure Protection. FBI Philadelphia Division Special Agent John B. Chesson. Cyber Terrorism. Potential Cyber Attacks. Unauthorized Intrusions Website Defacements Domain Name Server Attacks Distributed Denial of Service (DDoS) Attacks Computer Worms
1.11k views • 56 slides

DETECTION AND PROTECTION OF CYBER CRIME
DETECTION AND PROTECTION OF CYBER CRIME. By Dr. Narendra K. Amin, Assistant commissioner of Police, Crime branch, Ahmedabad city. Outline. This presentation highlights Introduction of cyber crime techniques and tools for the two realms of cyber crime: Detection Prevention. HISTORY.
1.92k views • 79 slides
To join the online webinar, go to: safetyleaders Online Access Password: Webinar1 (case-sensitive)
Welcome to the NQF Safe Practices for Better Healthcare Webinar: Updated 2010 CLABSI and SSI Practices: A New Standard of Care (Safe Practices 21-22) Hosted by NQF and TMIT. To join the online webinar, go to: www.safetyleaders.org Online Access Password: Webinar1 (case-sensitive).
1.05k views • 60 slides

Discrimination and Harassment Free Workplace
Discrimination and Harassment Free Workplace. Iowa Civil Rights Commission. Discrimination and Harassment Free Workplace. The State of Iowa is committed to a discrimination and harassment free work environment.
1.25k views • 35 slides

Cyber Crimes
Cyber Crimes. Chunlian QU. What’s Cyber Crimes?. Cyber crime, also called computer crime, is any illegal behavior directed by means of electronic operations that targets the security of computer systems and the data processed . Types of Attacks. Military and Intelligence Attacks
1.29k views • 16 slides

CYBER SKIRMISHES
CYBER SKIRMISHES. By Zubair Khan. Introducing Cyber Warfare. ". . . attaining one hundred victories in one hundred battles is not the pinnacle of excellence. Subjugating the enemy's army without fighting is the true pinnacle of excellence.". Is Cyber Warfare Best Strategy?.
953 views • 70 slides

Rob Fowler, Detective Ada County Sheriff’s Office School Resource Officer Eagle High School. Bullying. Course Objectives. Gain better understanding of what bullying is and what drives it. Learn to identify & address bullying Identify common traits of bullies
1.91k views • 174 slides

Anti Sexual Harassment Law
Anti Sexual Harassment Law. Report by: Chicky S. Recheta. Learning Objectives. Define the Anti-Sexual Harassment Law Identify the most common misconceptions about sexual harassment Know the proposed amendments to the Anti-Sexual Harassment Law. Anti Sexual Harassment Law.
2.13k views • 0 slides

Being Good Digital Citizens with Today’s Technologies
Being Good Digital Citizens with Today’s Technologies. Today’s Presentation:. Utah Statistics Benefits & Dangers Profile of a Teenager Potential Risks Cell Phones & Photos Posting a Picture. Cyber-bullying Personal Information Online Friends Talking to an Adult you Trust
1.01k views • 90 slides

Bullying & Harassment:
Bullying & Harassment:. Its not just the Students. By: Nicole M. Proesch AEA 267 Summit April 2, 2014. Bullying & Harassment in the Workplace. Bullying & Harassment in the Workplace. Harassment – Iowa Code § 708.7
1.06k views • 43 slides

Injury Awareness And Prevention For Dancers
Injury Awareness And Prevention For Dancers. Mariners Physical Therapy Mark Kirsch MPT Genevieve Sepulveda. Injury Statistics With Dancers. Professional dancers lifetime prevalence of injury: 80% Ankle, 57% Knee, 51% Foot Preprofessional dancers lifetime prevalence of injury:
1.18k views • 73 slides

CYBER STALKING
CYBER STALKING. PREPARED BY : SITI NUR ASHIKIN BINTI ABU BAKAR. WHAT IS CYBER STALKING ?. Cyber stalking is a crime in which the attacker harasses a victim using electronic communication, such as e-mail or instant messaging (IM), or messages posted to a Web site or a discussion group.
8.02k views • 19 slides

Bullying Prevention
Bullying Prevention. Meeting the Requirements of the Dignity Act SAANYS Saratoga Springs, NY Presented by: Dr. Susan Lipkins Dr. Karen Siris April 2, 2012 [email protected]. DEAR COLLEAGUE LETTER….
1.05k views • 94 slides

Bullying and the Student with Special Needs
Bullying and the Student with Special Needs. September 27, 2012. Susan Traynor Chastain Karen Glasser Sharp. Bullying - Statutory Requirements.
1.06k views • 90 slides

Cyber Warfare : The World War III
Cyber Warfare : The World War III. By: Hemal Patel MD & CEO, Elitecore Technologies Ltd. Presentation Sketch . What is Cyber crime / Cyber warfare? Cyber Warfare - Weapons Why Cyber Attacks Succeed Is India ready? Fighting Cyber Warfare. What is Cyber Crime / Warfare?. Cyber crime
1.24k views • 29 slides

AN ECOLOGICAL PERSPECTIVE ON HARASSMENT, INTIMIDATION, AND BULLYING
AN ECOLOGICAL PERSPECTIVE ON HARASSMENT, INTIMIDATION, AND BULLYING. Christopher Willis Ph.D. Newport County, Rhode Island John Lestino MS, LPC Edgewater Park, New Jersey NASP Convention – Atlanta Mini Skills Workshop March 31, 2005. THE ECOLOGICAL PERSPECTIVE.
1.09k views • 82 slides

Sexual Harassment Training
Sexual Harassment Training. Understanding and Preventing Sexual Harassment Created by: Mr. David McConnell Morale, Welfare and Recreation Kings Bay Georgia Updated: 2/4/00. Objectives. Understanding without a doubt what is and what is not sexual harassment.
907 views • 49 slides

Workplace Harassment
Workplace Harassment. What Supervisors Need to Know. Session Objectives. You will be able to: Understand the requirements of the law and company policy Identify incidents of workplace harassment Handle complaints and participate in investigations effectively
3.34k views • 30 slides

Sexual Harassment: Awareness and Prevention
Sexual Harassment: Awareness and Prevention. prepared and presented by: Office of General Counsel & OA, Bureau of Equal Employment Opportunity. Agenda. Introduction and Objectives Survey Definition of Sexual Harassment Video Vignettes Commonwealth Policy Reporting Procedure Summary.
1.18k views • 96 slides
Search form
Cyber-harassment: self-protection tips.

Being online gives you access to lots of information, but it also means you are exposed to online abuse. If not responsibly handled, the use of messaging apps, social media and other means of e-communication can be a source of harm: cyber-stalking, cyberbullying, violation of privacy, improper information and image sharing may damage survivors’ sense of safety, self-image and self-esteem. Da’esh has used this kind of tactic against persons who have spoken publicly against them or their ideology. There are a variety of ways to address this type of unwanted communication and protect yourself from its impacts.
What is cyber harassment?
Cyber harassment is a threat via the use of digital technologies. It can take place on social media, messaging platforms and cell phones. It is a repeated behavior, aimed at threatening, scaring, shaming, and silencing those who are targeted.
Type of cyber harassment
Cyber-intimidation and harassment fall into one or more of the following categories:
- Harassment and stalking: repeatedly sending threats or hurtful messages via messaging platforms or phone calls.
- Outing and trickery : engaging someone in instant messaging, tricking him or her into revealing personal and sensitive information. In the specific context of communities victimized by Da’esh this may involve “impersonation”, a trick to test allegiance of “returnees from captivity” and to ascertain whether they are still indoctrinated.
- Denigration : sending or posting gossip or rumors about a person to damage his or her reputation, friendships or to disadvantage his or her social inclusion.
What can you do to protect yourself?
Experiencing harassing calls and messages can be very difficult emotionally. It is important for you to know that you can protect yourself against such threats. Do not let the bullies silence you! If you think that you are being cyber threatened, the most important thing is to ensure you are safe. Speaking to a trusted person – someone you feel safe talking to – is one of the most important first steps you can take. Then take the following measures to protect yourself:
Information gathering
Try to document the cyber-harassment as much as possible, no matter how insignificant you may think it is. Such information gathering may include saving messages and threatening material, making screenshots, recording calls, tracking times, places and persons involved in the act.
Stop interaction
- If it is a phone call, calmly tell the threatening person to stop the harassing behavior then hang up and stop all kinds of interaction with the harasser.
- If it is a post or a text message, do not answer.
- Identify and record the number(s) used by the harasser to contact you.
Then ignore or block the communications:
One of the strategies can be to block the abusive person from contacting you. Blocking works differently depending on the technology platform or smartphone device. It may be useful to test the blocking feature with someone you trust to see how it works.
Set up privacy settings
- In addition to blocking the contact, on WhatsApp as well as other social networks you can: turn off “last seen” and restrict unknown people from adding you to groups.
- Hide your profile photo. This will limit your visibility of your activity on the different social networks.
Report the incident
It is critical to report incidents to fight against impunity and to stop victimization.
- Report the threat in detail to the local security officers, namely the National Security Service and the Community Police
- Report the threat in detail to your UNITAD focal point
General tips for cyber-security
- Think twice before posting or sharing anything online – it may stay online forever and could be used to harm you later.
- Limit information you post on your account, especially personal details such as your address, telephone number, the name of your IDP camp/city/location, names of your relatives.
- Make your phone number private. Consider making your phone number, “secret” so the receiver will see “private number” or “caller ID not available” on their phone when you ring. It can help to limit personal data dissemination.
- Consider opening an account on Signal instead of WhatsApp. Signal guarantees better privacy.
- Only accept on personal social networks people you know. Do not accept friend requests from strangers.
- Warn your friends and acquaintances, not to post personal information about you.
- Don’t post photographs of your home that might indicate its location.
- Learn about the privacy settings of your social media apps, including who can see your info and blocking/hiding contents options.
- Deactivate geo-location on all your accounts.
- Systematically check the background of your videos/Photos before publishing them.
- Report suspicious or threatening accounts.
- Keep private and business accounts strictly separate.
Remember, if you are a victim of harassment, you are not responsible for the behavior of the harasser; you should not be blamed in any way.
For more detailed information on cyber-security, please see the following (Cyber’-protection tips for survivors)

How To Stop Online Harassment: Laws, Reporting, & What You Can Do
Home » Resource Articles » How To Stop Online Harassment: Laws, Reporting, & What You Can Do
- Investigations
If you are experiencing cyber harassment, stalking, or bullying, it can be difficult to know where to turn. You may be thinking: Am I actually experiencing online harassment? How do I report it? Can I sue someone or involve the police? Let’s go over what constitutes online harassment, and what to do if someone targets you on the web.
Harassment is generally defined as a repeated pattern of behavior intended to scare, harm, anger, or shame a targeted individual. Online harassment means these actions occur using digital technologies such as social media platforms, email or messaging services, gaming platforms, or cell phone communication. Examples of such behavior include:
- Posting defamatory remarks intended to harm a person’s reputation
- Publishing private, explicit, or manipulated photos
- Sending threatening messages
- Posting false information or impersonating someone online
Types and Examples of Cyber Harassment
Online harassment, or cyber harassment , includes various forms of online abuse such as cyberbullying, cyberstalking, online impersonation, doxxing (also spelled “doxing”), swatting, revenge porn, sextortion, and more. Many of these acts are considered crimes punishable under federal and state laws, depending on the specific behavior and the harm caused to the victim.
Examples of cyber harassment often take one of the following forms:
- Hate speech is a common form of cyber harassment that involves offensive and discriminatory language or actions motivated by animosity toward aspects of identity such as race, religion, gender identity, etc. While there is no legal definition of hate speech , it’s characterized by the use of slurs, name-calling, and other forms of verbal abuse and can also be conveyed through images and memes on social media.
- Cyberbullying is the intentional, repeated harm inflicted on a person or group through digital means, most commonly through social media platforms. Each state has its own laws regarding cyberbullying, including criminal and school sanctions.
- Cyberstalking is another common example of cyber-harassment that involves targeted and repeated intimidation, threats, and harassment directed toward one person. It can include false accusations, defamation, and digital vandalism. In many cases, it is a crime that’s punishable under federal and state laws.
- Online impersonation occurs when someone uses the identity of a person, organization, or brand without their consent and with the intention of damaging, intimidating, or defrauding others. Impersonation is very common in phishing schemes using fake social media accounts and can cause costly damage to a business.
- Doxxing (or Doxing) is the act of revealing someone’s personal information online with the intention of harassing them. It is most common in the gaming and hacker communities but also affects celebrities, politicians, and journalists. Doxxing can range from a misdemeanor to a felony offense depending on the malicious intent and harm caused to the victim.
- Swatting is an extension of doxxing where a bad actor fabricates a dangerous story to law enforcement about the victim (i.e. “This person is holding someone hostage at their house). Law enforcement, in turn, shows up in force at the victim’s residence. It is a crime that can result in severe legal consequences for the perpetrator.
- Revenge Porn is the non-consensual sharing of sexually explicit images or videos of someone, usually by a former partner or spouse. It is a crime that is punishable under state laws and can lead to severe legal consequences for the perpetrator.
- Sextortion is when an individual uses sexually explicit images or videos to extort or blackmail a victim. It often includes threats to share and distribute the content to the victim’s friends, family, or employer if they don’t comply with the perpetrator’s demands. It is a serious cybercrime that is punishable under federal and state laws.
We recommend exploring this resource from the Online Harassment Field Manual for an in-depth look into the different terms and crimes associated with cyber harassment.
Cyber harassment cases unfortunately often involve specific groups of people over others, namely women and people of color. In one study from the Pew Research Center , 50% of American women polled reported experiencing online harassment, compared to 30% of men. Additionally, 54% of all those who reported experiencing cyber harassment identified as Black, despite the fact that the Black community constitutes only 13.4% of the total American population . Hispanic persons have also indicated higher levels of harassment as compared to white persons.
What Can I Do If I Am Being Harassed Online?
Identify, document, and report incidents of harassment. First things first: what specific actions are you considering to be harassment? Is it repeated and severe? This step is important when it comes to reporting online harassment; companies or courts will need to know exactly what behavior has occurred and its effect on you. Next, start keeping track of every instance of abuse.

Document Everything
Luckily, digital media often leaves an overt trail of evidence. Posts are public, messages can be saved, and anything can be screenshotted. While your instinct emotionally could be to delete and ignore offending content, keeping records of the abuse will be key when attempting to get content taken down by social platform companies or if you choose to go to court.
Use screenshots to record incidents of harassment and keep them organized in preparation for taking action against the perpetrator(s). Additionally, make sure to also capture the URL of the account sending the offending messages. Justice will more easily be served if you can also report how the harassment is affecting your physical, emotional, and financial well-being. Keeping a visual record of harmful images, comments, or messages can also help you show evidence of harm without having to relive traumatic events verbally.
What many people don’t realize is that there are specific guidelines and requirements for submitting digital evidence in court. You need to be able to provide details such as metadata, hash values, times & dates, and other “behind the scenes” social media data. So do your best to document everything yourself, and consider hiring an investigative service that specializes in social media court case preparation to assist you.
Keep Yourself Safe
If you are being threatened online, you should stay vigilant in protecting your physical safety as well. Ask yourself: are you acquainted with the perpetrator of your online abuse, or is their identity unknown? If their identity is unknown, you can take steps to unmask them , but you should be aware that this process is often costly and time-consuming. If you know the person harassing you, consider the following red-flag questions:
- Do they know personal details about you, such as where you live?
- Have they made threatening comments? Are their threats specific? A specific threat may mention a time, date, or place where violence will occur.
- Are their claims irrational or erratic? Do they have a history of violent behavior?
If any of the above statements are true, you may need to seek immediate help to maintain your safety. Find a place to stay where you feel protected, and enlist the help of friends or family who can support you as you navigate this situation. If the harassment is work-related, you may need to notify your employer of what’s going on. At this point, some victims may consider involving law enforcement or an attorney. The reality is, different law enforcement agencies and legal offices have varying levels of understanding of cybercrimes. We’ll discuss the legal and criminal consequences of online harassment later on in this article.
Increase Your Personal Cybersecurity
There’s a lot you can do to increase your personal cybersecurity and prevent online harassment from occurring. Generally, the more active you are online or the more you broadcast yourself on social media platforms, the more vulnerable you’ll be to abusers. Here are a few ways you can better prevent cyber harassment.
- Check Your Privacy Settings – To discourage unsolicited comments and various forms of cyber harassment, make sure your social media accounts have privacy settings in place that limit your content to only permitted users.
- Block and Un-Friend – When unwarranted comments do occur, be relentless in blocking or “unfriending” any individuals or accounts responsible for the harassment. This also includes harassing email addresses and phone numbers. But keep in mind you may want to collect evidence for legal matters before blocking.
- Keep Personal Information Personal – Do not share personal information and details about yourself online, such as your address, phone number, place of work or school, credit card number, etc. This also includes sharing photos and videos that may be sensitive or revealing.
- Bolster Your Passwords – Ensure your passwords are as secure as possible and avoid using the same password across multiple websites and platforms. We recommend using password managers to make this as easy as possible. Additionally, enable two-factor authentication when appropriate and keep personal and professional online accounts separate.
- Utilize a Virtual Private Network – A virtual private network (VPN) is an Internet security service that uses encryption to create a secure connection, protecting users’ anonymity. While common in business settings, anyone can use a VPN to ensure details are protected, such as your IP address which reveals a lot about you.
The best measure against cyber harassment is to limit the information you make accessible online. You should avoid sharing any personal details and stay vigilant about revealing real-time data, like where you are and whom you’re with. Also, Google your name and assess what information shows up. You may be surprised at what data is publically available.
What if My Child is Being Harassed?
If your child is the victim of any targeted attacks as described above, start a conversation about how it’s not okay and that there are ways you can help. As kids and teens spend increasing hours online every day, cyberbullying is a constant threat. In fact, nearly half of all tweens and teens report experiencing bullying online. Your child may not even recognize their experience as harassment or may be reluctant to share what’s going on with an adult.
Explore this resource from UNICEF on how to address cyberbullying with your child, and start taking steps to protect them from further abuse.
How Can You Stop Someone From Harassing You?
Every social media and online messaging platform has avenues for reporting and removing offensive content, and it is possible to take legal action against perpetrators of online harassment as well.
Block, Mute, Report
Working within the platform where the harassment took place is the first option available to respond to online abuse.
Block : You can silence perpetrators on most social media sites by blocking their account(s), which will prevent them from viewing your profile or communicating with you in any way. This can stop harassment on one site, but pervasive attackers may seek out other platforms or use fake accounts to continue targeting you. Keep in mind, if you are gathering information to take to law enforcement or a lawyer, blocking will prevent you from recording new harassment.
Mute : On some social media platforms, you can “mute” certain information or accounts, meaning it will no longer show up in your feed, search, or inbox. This differs from blocking in one important way: you are only preventing yourself from seeing content, and others on the site may still view defamatory or threatening posts. This does not affect the perpetrator’s ability to continue to harass you or others.
Report : You may report an account as violating a social media platform’s community guidelines in an attempt to get their posting privileges revoked, or at least have offending posts removed. Section 230 of the Communications Decency Act prevents social media companies from being held liable for any comments or images posted using their service, so your best hope is to appeal to their internal policies for what may appear on their site. In the end, it’s up to their team to decide whether to respond. Each site has its own reporting process, and you can click these links to get started on Facebook , Instagram , Google , or Twitter . Unfortunately, many times they are slow to respond.
Helplines : If you are concerned for your mental health or need advice on what to do next, reach out to one of these helplines that provide free assistance for victims of cyber harassment.
What Will the Police Do About Online Harassment?
In general, the police will be most able to assist you if:
- The perpetrator has published sexual images of you without your consent.
- You have received true threats or specific threats of violence that name a time, day, or location.
- The perpetrator has violated state or federal stalking laws.
Choosing to go to the police can be a difficult or intimidating decision for many people. Not everyone will feel comfortable involving law enforcement, and not all police precincts will have experience investigating and prosecuting cybercrimes. Ultimately, it is your decision whether or not you feel safe filing a report with the police. If you do choose to report online harassment as a crime, be prepared to be asked to provide evidence and describe your experience to officers or detectives.
Unfortunately, our experience across the United States has shown that it is rare for law enforcement to get involved or provide meaningful help when online harassment occurs.
What If the Police Can’t Help?
Another avenue to justice is enlisting the help of a legal team like Bosco Legal Services , who can help you seek justice and possible compensation for harm caused by an online harasser. Bosco is not a law firm, but rather an investigation agency specializing in tracking down the true identities of online bad actors. Bosco works in tandem with law firms across the United States who specialize in helping victims of cyber harassment receive justice.
Can You Sue Someone for Harassing You Online?
Yes, you may sue someone for civil wrongs (or torts) such as defamation, harassment, and public disclosure of private facts that have occurred online. The object of such cases is to compensate the victim for any “injury” resulting from the civil wrong and impose liability on perpetrators of harmful acts. Additionally, in certain circumstances, filing a lawsuit is a necessary step in unmasking fake accounts .
Cyber Harassment Laws
18 U.S. Code Section 2261A prohibits the federal crime of stalking and has been amended to include online actions to harass, injure, harm, or intimidate a person. State laws differ on what constitutes criminal harassment vs. civil harassment, and if you’re considering legal action you should explore your state’s legislation surrounding harassment and cyberstalking. This index of social media court cases provides an idea of the process and outcomes associated with torts and crimes committed online.
Before you agree to pay any fees to a lawyer, investigate whether you have grounds in your state to sue based on online behavior and what distinctions exist between criminal and civil cases. The Cyber Civil Rights Initiative offers pro bono legal services to victims of cyber harassment and can provide guidance on your rights within your specific state.
What Do You Need To Go To Court?
In addition to keeping detailed records and screenshots of the harassment, you’ll likely need to work with a team that understands the regulations and laws requiring submitting content from social media as evidence in court as established by FRE 902(14) . Suppose your abuser’s true identity is still unknown. In that case, you will need to determine exactly who it is you are suing using a service designed to uncover the people behind social media accounts . At Bosco, our cyber investigators use advanced search tools and analysis to locate the critical metadata, times & dates, and other data that the court requires to pursue a lawsuit. Learn more about social media investigations here.
What Is the Cost of Suing Someone For Online Harassment?
There are financial, emotional, and possible social costs for any case involving interpersonal harassment and abuse. If you’re considering taking legal action, prepare to be questioned about your experience and for details surrounding the harassment to be made public in court. Initial court fees for filing a civil suit can be anywhere from $400-$1,000, and fees to investigative teams and attorneys can often start between $5,000-$10,000 in online harassment cases. Victims of harassment should also be aware that proving cyber crimes in court using evidence from social media can be a tricky business, and not all cases will be successful.
Additional Online Harassment Resources
We have published additional online harassment resources that you can explore below:
- Tracking Down Fake Social Media Accounts
- Automated Social Media Tools vs. Social Media Investigators: A Thorough Comparison
- False Customer Complaints: Taking Legal Action Against Fake Reviews
- Court Cases Relevant to Using Social Media Evidence
- Social Media Investigation Services
At Bosco Legal Services , we offer comprehensive social media investigation services that give you the highest chance of success when pursuing a cyber harassment case in court. Explore our court resources for more information, or contact us to learn more about stopping online harassment.


The Women’s Media Center’s research and reports shed a light on the underrepresentation and misrepresentation of women in the media.
More »

- Arts and culture
- Status of Women in the U.S. Media
- Reports and Research
- Infographics
WMC News & Features offer original reporting and commentary on headline stories and underreported topics.
- International
WMC Women Under Siege investigates how sexualized violence is used as a weapon in conflict and beyond.

- Violence against women
WMC Fbomb is an intersectional teen feminist media platform created by and for socially conscious youth.

WMC Climate positions the people climate change affects the most – women and people of color – front and center.

- Environment
- Race/Ethnicity
- Climate Map
WMC Speech Project is dedicated to raising public and media awareness about online harassment.

- Online harassment
Online Abuse 101
WMC IDAR/E spotlights the voices of diverse Latinas on a range of current and emerging issues.

WMC Live with Robin Morgan is a weekly radio show and podcast in 110 countries around the globe.

- Robin Morgan
- WMC Live on iTunes
WMC SheSource is an online database of media-experienced women experts who we connect to journalists, bookers and producers.

Areas of Expertise
- Business and the Economy
- Media and Entertainment
- Social justice
- Find an Expert
- Apply to WMC SheSource
- Journalist Sign Up
- Privacy Policy
- Apply for WMC SheSource
- Pitch our editor
- Experts for Media
- Gloria Steinem
- Journalist Sign up
- Name it Change it
- Press releases
- Press contact
- Privacy policy
- Progressive Women's Voices
- Publications
- Sign up for journalist newsletter
- Sources for journalists
- Status of women in media reports
- WMC SheSource Journalist email
- Unspinning the Spin
- Women's Media Awards
- Write for us
- WMC LOREEN ARBUS JOURNALISM PROGRAM
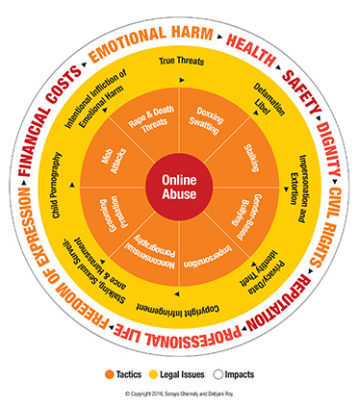
First, what exactly is online abuse?
Online abuse includes a diversity of tactics and malicious behaviors ranging from sharing embarrassing or cruel content about a person to impersonation, doxing, stalking and electronic surveillance to the nonconsensual use of photography and violent threats. The online harassment of women, sometimes called Cybersexism or cybermisogyny, is specifically gendered abuse targeted at women and girls online. It incorporates sexism, racism, religious prejudice, homophobia and transphobia.
The purpose of harassment differs with every incidence, but usually includes wanting to embarrass, humiliate, scare, threaten, silence, extort or, in some instances, encourages mob attacks or malevolent engagements.
Tactics are wide ranging. They are sometimes legal, but harmful and consequential. They may legal, but violate a particular platform’s guidelines and terms of service. Some, but not all, are illegal, including, but not limited to Child Pornography, Copyright Infringements, Data Theft, Defamation, Extortion, Intentional Infliction of Emotional Harm, Libel, Privacy Infringements, Sexual Harassment, Sexual Surveillance, Stalking and True Threats.
- Cross platform harassment
- Cyber-exploitation, Nonconsensual Photography or “Revenge Porn”
- Electronically enabled financial abuse
- False accusations of blasphemy
- Gender-based Slurs and Harassment
- Google Bombing
- Grooming and Predation
- Hate Speech
- Identity Theft and Online Impersonation
- IRL Attacks
- Mob Attacks/CyberMobs
- Rape Videos
- Retaliation Against Supporters of Victims
- Sexual Objectification
- Shock and Grief Trolling
- Spying and Sexual Surveillance
- Stalking and Stalking by Proxy
- Sexting/Abusive Sexting
- Slut-Shaming
- Trafficking
- Unsolicited Pornography
- Isn’t this “just bullying”?
- Why focus on women, if everyone is harassed and whose experiences can be radically different?
- Aren’t anonymity and stranger danger the problem? And, if we get rid of it, won’t harassment go away?
- Harassment isn’t “really violent,” right? Not compared to offline violence?
- But, aren’t men harassed, too?
- Don’t Women Harass Online As Well?
- Aren’t only women celebrities and writers being harassed? Aren’t they public figures and harassment goes with the territory?
- What are the costs?
An act of bullying is defined by the Berkman Center for Internet and Society as hostile acts or behaviors that share three characteristics: a) they are intentional; b) they involves a power imbalance between an aggressor (individual or group) and a victim; c) they are repetitive in nature and sustained. [i] While this definition provides an excellent framework, definitions can and do differ greatly and don’t necessarily align with academic and research definitions. Legal definitions of bullying and harassment vary by jurisdiction and the term bullying most frequently involves the targeting of children and teens. For example, only 16 US states define bullying as encompassing only behaviors that are intentional; seven states define it to include only behaviors that a ‘reasonable person’ thinks would harm another person.” Only four states take into account power imbalances.
Because abuse targeted at women is qualitatively and quantitatively different, and intersectionality matters when determining how and what to do about it. Gender based harassment is marked by the intent of the harasser to denigrate the target on the basis of sex. It is characterized by sexist vitriol and, frequently, the expression of violence.
When men face online harassment and abuse, it is first and foremost designed to embarrass or shame them. When women are targeted, the abuse is more likely to be gendered, sustained, sexualized and linked to off-line violence.
Women, the majority of the targets of some of the most severe forms of online assault – rape videos, extortion, doxing with the intent to harm – experience abuse in multi-dimensional ways and to greater effect. They are the vast majority of the victims of nonconsensual pornography, stalking, electronic abuse and other forms of electronically-enhanced violence.
In addition, women report higher rates of finding online harassment stressful. This is not because they “can’t stand the heat,” as is frequently suggested, but because the abuse online exists simultaneously with three facts:
- Women have to be hyper-vigilant in daily life. A double digit safety gap offline has an online corollary. Women are more likely to experience more gendered and consequential abuse. They are more frequently harassed, online and off, for sustained periods of times, in sexual ways and in ways that incorporate stalking and manipulation. They are more likely to be pornographically objectified and subjected to reputation damaging public shaming. Sexual slurs toward women evoke the threat of real-life sexual violence; they are also perceived as intended to “put a woman in her place” and tell her that her opinion is worthless because she is a woman.
- The abuse women experience online is intersectional. Women all over the world are experiencing misogyny online, but rarely is it experienced along only one dimension. Women who are targeted because of their race, ethnicity, sexuality or disability face abuse on multiple fronts and report higher rates of emotional and psychological harm. Sometimes, sexism is married to race, others to caste, others to sexuality – the overlap has a compounding effect. A lesbian woman experiences homophobia and sexism. A black woman, racism and sexism. A Moslem or Jewish woman, religious hatred and sexism.
- Globally, women still face sexist, patriarchal (power-over domination of all kinds) constraints that compound the negative effects of online harassment . There are preexisting, offline limitations on our ability to work, go to school, earn money, be politically active and shape culture. Limitations that, for the most part, men do not face. When girls and women are harassed online, that harassment taps into these restrictions and the potential damage is amplified. Girls and women are more likely to face bullying, harassment, censorship and abuse that reflect preexisting, and still enforced, sexist double standards and the disproportionate effect of honor culture norms. Many of the most commonly employed tactics rely on preexisting double standards regarding sexual behavior. Harassers, for example, count on women being judged for their sexual behavior and shamed and penalized because of it.
- The harassment men experience also lacks broader, resonant symbolism. Women are more frequently targeted with gendered slurs and pornographic photo manipulation because the objectification and dehumanization of women is central to normalizing violence against us. Philosophers Martha Nussbaum and Ray Langdon describe in detail how this works: women are thought of and portrayed as things for the use of others. Interchangeable; violable; silent and lacking in agency. Much of the harassment that women are subjected to online reflects these uses of objectification.
Anonymity is a serious problem, however, anonymity doesn’t mean that the abuse comes from strangers. Most women are harassed online by people they know: school peers, acquaintances, intimate partners, former intimate partners, employers and, in some countries, religious and political authorities. Many of these people do use anonymity to perpetrate abuse, but anonymity itself isn’t the problem.
Anonymity is often a lifeline for people online, an essential dimension of privacy and freedom from violence. There are many movements, globally, such as the #Nameless Coalition, encouraging platforms to create more nuanced and flexible approaches to the problems presented by anti-anonymity policies.
Online harassment exists on a continuum with offline violence. Harassment online is a very strong thread in an already densely woven fabric of socially acceptable and institutionalized resistance to women’s full participation in the world. A teenage girl in Pakistan might not only be harassed online, but might find that her life is at risk if her family finds out about her online life or because a conservative member of her community non-consensually shared a photograph of her on Facebook. A woman in Texas whose ex-husband nonconsensually shares naked pictures of her, might legally be fired by her conservative employer. A girl in Canada might kill herself after a video of her rape is shared electronically, and her classmates slut-shame her, literally to death. A writer might have to cancel speaking opportunities because of threats made on an open-carry campus. A trafficked 10-year old in a country where child marriage is acceptable might be terrorized when her trafficker tweets a picture of himself drowning her best friend in a toilet, just to prove he can. A woman’s small business might collapse after an online mob actively decides to flood Yelp reviews with defamatory comments. And, for those tempted to think, “women over there have real problems compared to those of you complaining about online trolls,” it pays to remember that the nonconsensual distribution of sexualized images is not illegal in the vast majority of US states.
Men are harassed and abused online. Studies show that they experience many of the same forms of abuse that women do. The argument that men are harassed equally or even more camouflages qualitative and quantitative differences. Men are more likely to be called names and are harassed in one-off incidents, whereas the scope of what women are experiencing is broader and more violent. Additionally, the harassment of many people, including men, is focused on their defying rigid gender and sexuality roles. Transgressions of conservative gender roles mean heightened risk for users who don’t conform. LGBTQUIA youth experience online bullying at three times the rate of their straight peers. When men are harassed, it is often by people using homophobic and feminizing slurs. Additionally, there are some notable aspects of perpetration. While women can and do engage in harassment of both men and women, most perpetrators of online assault, like offline crimes, are men.
Yes. Women also perpetrate online abuse and express hateful sentiments. However, particularly in cases of abuse that are sustained and include off-line dimensions, male-perpetration is more prevalent. For example, the overwhelming targets of abusive sharing of non-consensual pornography are women whose photos are shared by men. Similarly, stalking, in which men tend to be the majority of perpetrators, disproportionately affects women.
Women in the public eye, journalists and celebrities, are the most frequent targets of stranger abuse, primarily involving slurs and threats. However, that type of abuse frequently affects women who are not professionally in the public eye or involved in gaming or tech. They are not public figures or writers, and they don’t have huge social platforms. They are going about their lives biologists , teachers , debaters , business consultants , mothers , technologists , activists , students , violinists and they are being harassed while they do it. All over the world women are dealing with socially, and often legally, allowable, electronically enabled abuse every day. Frequently, organizations that advocate against cyber-hate on behalf of particular groups will overlook intersectionality, and therefore the specific harms and risks that women face. Part of our work is prioritizing the intersectionality of women’s online experiences of abuse so that better solutions can be developed.
Online abuse exacts many costs that are routinely minimized. Online harassment can be a steep tax on women’s freedom of speech, civic life, and democracy. It can and does inhibit their economic and educational opportunities. For women, harassment frequently perpetuates harmful stereotypes, is sexually objectifying and relies on the threat of violence to be effective. Among the most commonly reported by targets of online harassment are:
- Emotional and psychological distress and health problems related to anxiety, depression, anger, post-traumatic stress and hypervigilance
- Concerns about physical safety
- Concerns about the safety of immediate family
- Concerns about employers and family members finding out or being affected by harassment
- Incurring financial costs of trying to avoid or offset harassment and abuse
- Physical assault
- Privacy violations
The seamlessness of online and offline violence means that real world safety gaps are made even more pronounced. Perpetrators of intimate partner violence, stalkers and anonymous harassers all rely on pre-existing violence, and societal tolerance of that violence, to leverage new technologies. According to research conducted by the National Network to End Domestic Violence (NNEDV), 89 % of domestic violence programs report that victims experience intimidation and threats by abusers via technology, including through cell phones, texts, and email.” Intimate partners create impersonator content online, sometimes with brutal results . While media narratives often focus on stranger abuse and harassment, the fact is that the most sustained and destructive examples of abuse online, like offline, are most likely to be perpetrated by people known to victims. While this is true worldwide, there are also unique physical risks in countries where free speech norms and gender imbalances differ from those in the US. For example, in countries with highly punitive laws against blasphemy and/or where women are discouraged from engaging in public expression and political life, online abuse is enabled.
Professional
Harassment frequently involves harm to professional life and impairs people’s ability to pursue economic opportunities. Targets of harassment frequently worry about damage to their reputations and professional lives, their ability to find work and loss of employment. Women who are targeted, for example, might be bombarded with bad reviews for their place of business or their work products. Search engines might be maliciously optimized to highlight unflattering, inaccurate information.
Harassment makes women’s participation in male dominated fields or quickly evolving new markets difficult. Hostility towards girls and women in new and expanding markets is often particularly pronounced. Misogyny and sexism expressed profusely, for example, in gaming or sports, inhibit women’s ability to fully participate and be taken seriously when they do. Harassment reduces opportunities to engage as equals, be seen as authoritative or compete with for employment and education opportunities.
Civil and Human Rights
Danielle Citron and Mary Anne Franks argue that online abuse is, first and foremost, a civil rights issue, not only for women but for other historically discriminated against and marginalized groups. “Civil rights laws,” writes Citron in her book, Hate Crimes in Cyber Space , should “redress and punish harms that traditional remedies do not: the denial of one’s equal right to pursue life’s important opportunities due to membership in a historically subordinated group.”
According to global studies conducted by Take Back the Tech one in five women report that “the internet is inappropriate” for them. Fear of online violence, shaming, spying and tracking are significant impediments to women’s adoption and use of internet and mobile technologies. As a result, they are effectively, systemically restrained from participating as equals in civic and economic growth opportunities.
Harassment substantively constrains free speech. Many free speech absolutists think of safety and free speech as being in opposition to one another, as in, if we make changes to ensure people’s safety online we will necessarily squelch free speech. This equation fails to consider that for marginalized and non-dominant groups safety and free speech go hand-in-hand, and that the steps necessary to ensure the safety of people online rarely require new ways of censoring speech, but rely on the proper and fair execution of existing laws and policies.
Journalists and Media Marginalization
Hostility to women’s public engagement is hardly a new phenomenon and the experiences of women journalists and writers attests to its persistence today. An analysis of online harassment in Twitter conducted in 2014, for example, revealed that women journalists and writers are among the most targeted for online abuse. Research shows that women silence themselves, opt out of doing certain work, avoid certain topics, are fearful and restrict their level of public engagement.
Article.DirectLink

Learn more about topics like these by signing up for Women’s Media Center’s newsletter .
- • powered by feminism

- Cyberbullying
- Popular Categories
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories
Powerpoint Templates and Google slides for Cyberbullying
Save your time and attract your audience with our fully editable ppt templates and slides..
Presenting our Cyberbullying Online Harassment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cyberbullying Online Harassment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
Presenting Cyberbullying Social Media Ppt Powerpoint Presentation Show Display Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyberbullying Social Media. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
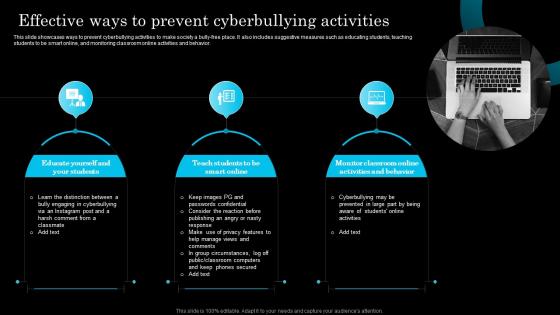
This slide showcases ways to prevent cyberbullying activities to make society a bully free place. It also includes suggestive measures such as educating students, teaching students to be smart online, and monitoring classroom online activities and behavior. Presenting our set of slides with Effective Ways To Prevent Cyberbullying Activities. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Educate, Students, Classroom.
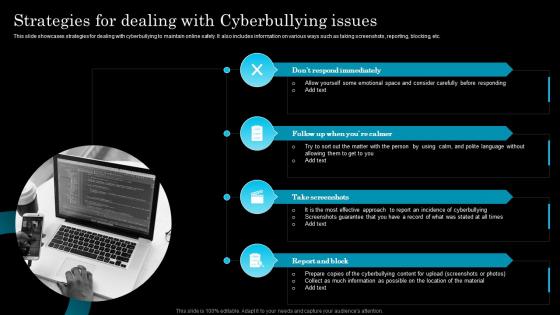
This slide showcases strategies for dealing with cyberbullying to maintain online safety. It also includes information on various ways such as taking screenshots, reporting, blocking, etc. Presenting our set of slides with Strategies For Dealing With Cyberbullying Issues. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Immediately, Follow, Screenshots.
Presenting Cyberbullying Articles Graph Ppt Powerpoint Presentation Show Cpb. slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like cyberbullying articles graph. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting our Cyberbullying Examples Ppt Powerpoint Presentation Pictures Templates Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Cyberbullying Examples. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.

Workplace Harassment Training
Explore anti-harassment training for a safe and inclusive workplace
REAL PEOPLE, REAL IMPACT
Workplace harassment can happen to any employee at any organization. But, every employee has the right to work in a safe environment free from harassment. And every employer has the responsibility to help make this a reality – with workplace harassment training as a valuable tool.
Creating a respectful and inclusive environment starts with anti-harassment training that educates employees on their pivotal role in eradicating harassment from the workplace.
WHAT SETS SKILLSOFT’S WORKPLACE HARASSMENT TRAINING APART?
Anti-harassment training must be designed and delivered to affect change..
With a full suite of anti-harassment training courses and the tools to easily design, deploy, and support ongoing harassment training for employees, Skillsoft Compliance Solutions help organizations educate their employees to understand, prevent, and respond to various forms of harassment.
CUSTOMIZE WORKPLACE HARASSMENT TRAINING
True compliance means the ability to be flexible. So, we’ve made it easy for you to adapt our anti-harassment training for specific audiences within your organization.
Comprehensive library to support other mission-critical compliance initiatives like anti-corruption, cybersecurity, privacy, and more.
GLOBAL COVERAGE & DEDICATED SUPPORT
Globalized content available in Australia, Canada, India, and New Zealand. Dedicated account support team, including Compliance Covers sexual harassment training mandates federally, as well as in California, Connecticut, Delaware, Illinois, Maine, and New York. Customer Success Managers and 24×7 technical support.
WHAT ARE THE WORKPLACE HARASSMENT REQUIREMENTS IN YOUR STATE?
Only one in five U.S. workers lives in a state where sexual harassment training courses are mandatory. Discover your state’s anti-harassment training requirements.
MAKING THE CASE FOR TRAINING
(Stats from: International Labour Organization, 2022)
22.8% of people experience at least one form of violence or harassment at work.
More than three in five victims of violence and harassment at work said it has happened to them multiple times.
Only slightly more than half (54.4%) of victims have shared their experience with someone.
WORKPLACE HARASSMENT HAS A REAL IMPACT ON REAL PEOPLE — EMPLOYERS JUST NEED TO OPEN THEIR EYES TO IT.
Create a safe workplace through skillsoft’s anti-harassment training, preventing sexual harassment: modern approaches to building a safe and inclusive workspace, bullying prevention, harassment and retaliation for managers, skillsoft content collections, leadership & business.
Core professional and leadership development training
Leadership Development Program from MIT Sloan Management Review
Courses available in multiple languages
Includes interactive learning resources
Easy data visualizations to measure progress
5,000+ on-demand tech courses, 700+ interactive and 500+ labs
Features emerging tech like GenAI, Security, Cloud
Offers both technical and non-technical learning
690 skill benchmarks to identify skill gaps
Subscription includes leadership and business training
Compliance & Ethics
500+ legal and safety topics in over 30 languages
Content developed with subject matter experts
Actively update for risk, legal, and regulatory changes
Access any time across devices
Customizable to meet your training goals
Top 10 Workplace Harassment courses
Harassment prevention for us employees – office 2, compliance short: preventing harassment and promoting respect, global workplace harassment prevention for employees, compliance short: promoting the reporting of misconduct, harassment prevention for us managers – office 2, harassment prevention for us employees – workplace, harassment prevention for california employees – office 2, compliance short: promoting diversity and avoiding discrimination, global diversity, compliance brief: race and color discrimination in the workplace, try our training, workplace harassment training faqs.
Mobile Menu Overlay
The White House 1600 Pennsylvania Ave NW Washington, DC 20500
Memorandum on the Establishment of the White House Task Force to Address Online Harassment and Abuse
MEMORANDUM FOR THE HEADS OF EXECUTIVE DEPARTMENTS AND AGENCIES
SUBJECT: Establishment of the White House Task Force to Address Online Harassment and Abuse
By the authority vested in me as President by the Constitution and the laws of the United States of America, and in order to improve efforts to prevent and address online harassment and abuse, it is hereby ordered as follows:
Section 1. Policy. Technology platforms and social media can be vital tools for expression, civic participation, and building a sense of community. But the scale, reach, and amplification effects of technology platforms have also exacerbated gender-based violence, particularly through online harassment and abuse. Online harassment and abuse include a broad array of harmful and sometimes illegal behaviors that are perpetrated through the use of technology. Women, adolescent girls, and LGBTQI+ individuals, who may be additionally targeted because of their race, ethnicity, religion, and other factors, can experience more severe harms from online harassment and abuse. Online harassment and abuse take many forms, including the non-consensual distribution of intimate digital images; cyberstalking; sextortion; doxing; malicious deep fakes; gendered disinformation; rape and death threats; the online recruitment and exploitation of victims of sex trafficking; and various forms of technology-facilitated intimate partner abuse. In the United States, 1 in 3 women under the age of 35 reports having been sexually harassed online, and over half of LGBTQI+ individuals report having been the target of severe online abuse, including sustained harassment, physical threats, and stalking in addition to sexual harassment. Globally, half of girls report that they are more likely to be harassed through social media than on the street.
In the United States and around the world, women and LGBTQI+ political leaders, public figures, activists, and journalists are especially targeted by sexualized forms of online harassment and abuse, undermining their ability to exercise their human rights and participate in democracy, governance, and civic life. Online abuse and harassment, which aim to preclude women from political decision-making about their own lives and communities, undermine the functioning of democracy. Growing evidence also demonstrates that online radicalization can be linked to gender-based violence, which, along with other forms of abuse and harassment, spans the digital and physical realms. Online harassment and abuse can result in a range of dire consequences for victims, from psychological distress and self-censorship to economic losses, disruptions to education, increased self-harm, suicide, homicide, and other forms of physical and sexual violence. Further, digital technologies are often used in concert with other forms of abuse and harassment, underscoring the urgency of addressing the interplay of in-person and online harms. More research is needed to fully understand the nature, magnitude, and costs of these harms and ways to address them in the United States and globally.
Therefore, I am directing the Director of the White House Gender Policy Council and the Assistant to the President for National Security Affairs to lead an interagency effort to address online harassment and abuse, specifically focused on technology-facilitated gender-based violence, and to develop concrete recommendations to improve prevention, response, and protection efforts through programs and policies in the United States and globally.
Sec. 2. Establishment. There is established within the Executive Office of the President the White House Task Force to Address Online Harassment and Abuse (Task Force).
Sec. 3. Membership. (a) The Director of the White House Gender Policy Council and the Assistant to the President for National Security Affairs, or their designees, shall serve as Co-Chairs of the Task Force.
(b) In addition to the Co-Chairs, the Task Force shall consist of the following members:
(i) the Secretary of State;
(ii) the Secretary of Defense;
(iii) the Attorney General;
(iv) the Secretary of Commerce;
(v) the Secretary of Health and Human Services;
(vi) the Secretary of Education;
(vii) the Secretary of Veterans Affairs;
(viii) the Secretary of Homeland Security;
(ix) the Director of the Office of Science and Technology Policy;
(x) the Assistant to the President and Director of the Domestic Policy Council;
(xi) the Assistant to the President for Economic Policy and Director of the National Economic Council;
(xii) the Administrator of the United States Agency for International Development;
(xiii) the Counsel to the President;
(xiv) the Counsel to the Vice President; and
(xv) the heads of such other executive departments, agencies, and offices as the Co-Chairs may, from time to time, designate.
(c) A member of the Task Force may designate, to perform the Task Force functions of the member, senior officials within the member’s executive department, agency, or office who are full-time officers or employees of the Federal Government.
Sec. 4. Mission and Function. (a) The Task Force shall work across executive departments, agencies, and offices to assess and address online harassment and abuse that constitute technology-facilitated gender-based violence, including by:
(i) improving coordination among executive departments, agencies, and offices to maximize the Federal Government’s effectiveness in preventing and addressing technology-facilitated gender-based violence in the United States and globally, including by developing policy solutions to enhance accountability for those who perpetrate online harms;
(ii) enhancing and expanding data collection and research across the Federal Government to measure the costs, prevalence, exposure to, and impact of technology-facilitated gender-based violence, including by studying the mental health effects of abuse on social media, particularly affecting adolescents;
(iii) increasing access to survivor-centered services, information, and support for victims, and increasing training and technical assistance for Federal, State, local, Tribal, and territorial governments as well as for global organizations and entities in the fields of criminal justice, health and mental health services, education, and victim services;
(iv) developing programs and policies to address online harassment, abuse, and disinformation campaigns targeting women and LGBTQI+ individuals who are public and political figures, government and civic leaders, activists, and journalists in the United States and globally;
(v) examining existing Federal laws, regulations, and policies to evaluate the adequacy of the current legal framework to address technology-facilitated gender-based violence; and
(vi) identifying additional opportunities to improve efforts to prevent and address technology-facilitated gender-based violence in United States foreign policy and foreign assistance, including through the Global Partnership for Action on Gender-Based Online Harassment and Abuse.
(b) Consistent with the objectives of this memorandum and applicable law, the Task Force may consult with and gather relevant information from external stakeholders, including Federal, State, local, Tribal, and territorial government officials, as well as victim advocates, survivors, law enforcement personnel, researchers and academics, civil and human rights groups, philanthropic leaders, technology experts, legal and international policy experts, industry stakeholders, and other entities and persons the Task Force identifies that will assist the Task Force in accomplishing the objectives of this memorandum.
Sec. 5. Reporting on the Work and Recommendations of the Task Force. (a) Within 180 days of the date of this memorandum, the Co-Chairs of the Task Force shall submit to the President a blueprint (Initial Blueprint) outlining a whole-of-government approach to preventing and addressing technology-facilitated gender-based violence, including concrete actions that executive departments, agencies, and offices have committed to take to implement the Task Force’s recommendations. The Initial Blueprint shall include a synopsis of key lessons from stakeholder consultations and preliminary recommendations for advancing strategies to improve efforts to prevent and address technology-facilitated gender-based violence. Following submission of the Initial Blueprint to the President, the Co-Chairs of the Task Force shall make an executive summary of the Initial Blueprint publicly available.
(b) Within 1 year of the date that the Initial Blueprint is submitted to the President, the Co-Chairs of the Task Force shall submit to the President and make publicly available an update and report (1-Year Report) with additional recommendations and actions that executive departments, agencies, and offices can take to advance how Federal, State, local, Tribal, and territorial governments; service providers; international organizations; technology platforms; schools; and other public and private entities can improve efforts to prevent and address technology-facilitated gender-based violence.
(c) Prior to issuing its Initial Blueprint and 1-Year Report, the Co-Chairs of the Task Force shall consolidate any input received and submit periodic recommendations to the President on policies, regulatory actions, and legislation on technology sector accountability to address systemic harms to people affected by online harassment and abuse.
(d) Following the submission of the 1-Year Report to the President, the Co-Chairs of the Task Force shall, on an annual basis, submit a follow-up report to the President on implementation of this memorandum.
Sec. 6. Definition. For the purposes of this memorandum, the term “technology-facilitated gender-based violence” shall refer to any form of gender-based violence, including harassment and abuse, which takes place through, or is aided by, the use of digital technologies and devices.
Sec. 7. General Provisions. (a) Nothing in this memorandum shall be construed to impair or otherwise affect:
(i) the authority granted by law to an executive department or agency, or the head thereof; or
(ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This memorandum shall not apply to independent regulatory agencies as described in section 3502(5) of title 44, United States Code. Independent regulatory agencies are nevertheless strongly encouraged to participate in the work of the Task Force.
(c) This memorandum shall be implemented consistent with applicable law and subject to the availability of appropriations.
(d) This memorandum is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
(e) The Attorney General is authorized and directed to publish this memorandum in the Federal Register .
JOSEPH R. BIDEN JR.
Stay Connected
We'll be in touch with the latest information on how President Biden and his administration are working for the American people, as well as ways you can get involved and help our country build back better.
Opt in to send and receive text messages from President Biden.
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
Internet & Technology
6 facts about americans and tiktok.
62% of U.S. adults under 30 say they use TikTok, compared with 39% of those ages 30 to 49, 24% of those 50 to 64, and 10% of those 65 and older.
Many Americans think generative AI programs should credit the sources they rely on
Americans’ use of chatgpt is ticking up, but few trust its election information, whatsapp and facebook dominate the social media landscape in middle-income nations, sign up for our internet, science, and tech newsletter.
New findings, delivered monthly
Electric Vehicle Charging Infrastructure in the U.S.
64% of Americans live within 2 miles of a public electric vehicle charging station, and those who live closest to chargers view EVs more positively.
When Online Content Disappears
A quarter of all webpages that existed at one point between 2013 and 2023 are no longer accessible.
A quarter of U.S. teachers say AI tools do more harm than good in K-12 education
High school teachers are more likely than elementary and middle school teachers to hold negative views about AI tools in education.
Teens and Video Games Today
85% of U.S. teens say they play video games. They see both positive and negative sides, from making friends to harassment and sleep loss.
Americans’ Views of Technology Companies
Most Americans are wary of social media’s role in politics and its overall impact on the country, and these concerns are ticking up among Democrats. Still, Republicans stand out on several measures, with a majority believing major technology companies are biased toward liberals.
22% of Americans say they interact with artificial intelligence almost constantly or several times a day. 27% say they do this about once a day or several times a week.
About one-in-five U.S. adults have used ChatGPT to learn something new (17%) or for entertainment (17%).
Across eight countries surveyed in Latin America, Africa and South Asia, a median of 73% of adults say they use WhatsApp and 62% say they use Facebook.
5 facts about Americans and sports
About half of Americans (48%) say they took part in organized, competitive sports in high school or college.
REFINE YOUR SELECTION
Research teams, signature reports.
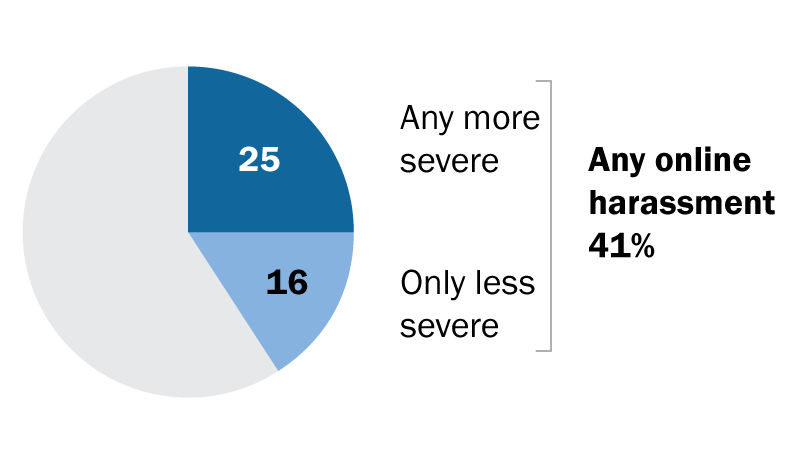
The State of Online Harassment
Roughly four-in-ten Americans have experienced online harassment, with half of this group citing politics as the reason they think they were targeted. Growing shares face more severe online abuse such as sexual harassment or stalking
Parenting Children in the Age of Screens
Two-thirds of parents in the U.S. say parenting is harder today than it was 20 years ago, with many citing technologies – like social media or smartphones – as a reason.
Dating and Relationships in the Digital Age
From distractions to jealousy, how Americans navigate cellphones and social media in their romantic relationships.
Americans and Privacy: Concerned, Confused and Feeling Lack of Control Over Their Personal Information
Majorities of U.S. adults believe their personal data is less secure now, that data collection poses more risks than benefits, and that it is not possible to go through daily life without being tracked.
Americans and ‘Cancel Culture’: Where Some See Calls for Accountability, Others See Censorship, Punishment
Social media fact sheet, digital knowledge quiz, video: how do americans define online harassment.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
© 2024 Pew Research Center
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

26 templates
49 templates

11 templates

71 templates

15 templates
first day of school
68 templates
Workplace Harassment Meeting
It seems that you like this template, workplace harassment meeting presentation, free google slides theme, powerpoint template, and canva presentation template.
Labor harassment is a reality. When this type of situation occurs, the most important thing is to make the problem visible, so that solutions can be applied. However, solving an event does not prevent it from happening again, so what is the best way to proceed? As this is such a serious issue, we do not have the exact right answer, but we think that raising awareness about workplace bullying can make people think and change their mentality. This professional template can help you by being the visual medium of a meeting. With a modern style, images and resources such as graphs or tables, you will be able to make a presentation of the information you consider relevant.
Features of this template
- 100% editable and easy to modify
- 20 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides, Canva, and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the resources used
How can I use the template?
Am I free to use the templates?
How to attribute?
Attribution required If you are a free user, you must attribute Slidesgo by keeping the slide where the credits appear. How to attribute?
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access


COMMENTS
Summary. If you or someone you know is experiencing online harassment, remember that you are not powerless. There are concrete steps you can take to defend yourself and others. First, understand ...
Women, on the other hand, are more likely than men to report having been sexually harassed online (16% vs. 5%) or stalked (13% vs. 9%). Young women are particularly likely to have experienced sexual harassment online. Fully 33% of women under 35 say they have been sexually harassed online, while 11% of men under 35 say the same.
Cyberbullying opens the door to 24-hour harassment and can be very damaging. That's why we offer in-app mental health and well-being support through our feature "Here For You." This Snapchat portal provides resources on mental health, grief, bullying, harassment, anxiety, eating disorders, depression, stress, and suicidal thoughts.
2. Whether on email, social media, or chat programs, the first thing you should do when experiencing bullying is block the person doing it. While they can still create a new account and reach you, this at least cuts them off from you temporarily and allows for time to figure out next steps. 3.
Online Harassment 2017. Lee Rainie, director of internet and technology research at Pew Research Center, discussed recent findings about the prevalence and impact of online harassment at the Cyber Health and Safety Virtual Summit: 41% of American adults have been harassed online and 66% have witnessed harassment.
Berkeley Resources: collaborates with the campus community to make social change with the goals of preventing, intervening in, and responding to harassment and violence, eliminating oppression, and creating the culture and environment we all aspire to and deserve. , call the Care Line at (510) 643-2005. For non-urgent support and questions ...
Cyber-Bullying and Online Harassment: Awareness and Best Practices for Prevention By Edward J. Lazaros, Ph.D. Department of Technology Ball State University Muncie, IN 47306 Phone: 765-285-5647 Fax: 765-285-2162 E-mail: [email protected]. Awareness • School bullying has typically occurred when one individual is in a position of power over another because of a difference in physical strength ...
Cyberbullying powerpoint. Sep 12, 2012 • Download as PPTX, PDF •. 46 likes • 111,877 views. AI-enhanced description. J. josiebrookeday. Cyberbullying involves using technology like phones or the internet to harass or threaten someone. Common tactics include gossip, impersonation, harassment, and cyberstalking. Victims can experience ...
Cyber Harassment. The document discusses cyber harassment, including common forms of harassment like abusive emails and posts, computer attacks, and identity theft. It provides statistics on victims, perpetrators, and duration of harassment, and examines federal and state laws related to cyberstalking, cyberbullying, and other online crimes.
Cyber harassment is a threat via the use of digital technologies. It can take place on social media, messaging platforms and cell phones. It is a repeated behavior, aimed at threatening, scaring, shaming, and silencing those who are targeted. Type of cyber harassment. Cyber-intimidation and harassment fall into one or more of the following ...
The State of Online Harassment. Roughly four-in-ten Americans have experienced online harassment, with half of this group citing politics as the reason they think they were targeted. Growing shares face more severe online abuse such as sexual harassment or stalking. short readsApr 9, 2020.
PowerPoint presentation slides. Presenting our Cyberbullying Online Harassment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cyberbullying Online Harassment This PPT slide can be easily accessed in standard screen and widescreen aspect ...
Online harassment refers to a wide range of harmful behaviors, including hate speech, insults, doxxing, and non-consensual image sharing. Social media platforms have developed complex processes to try to detect and manage content that may violate community guidelines; however, less work has examined the types of harms associated with online harassment or preferred remedies to that harassment.
Block, Mute, Report. Working within the platform where the harassment took place is the first option available to respond to online abuse. Block: You can silence perpetrators on most social media sites by blocking their account (s), which will prevent them from viewing your profile or communicating with you in any way.
The online harassment of women, sometimes called Cybersexism or cybermisogyny, is specifically gendered abuse targeted at women and girls online. It incorporates sexism, racism, religious prejudice, homophobia and transphobia. The purpose of harassment differs with every incidence, but usually includes wanting to embarrass, humiliate, scare ...
Online harassment and abuse is increasingly widespread in today's digitally connected world. This can include online threats and intimidation as well as various forms of technology-facilitated ...
Presenting our Cyberbullying Online Harassment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cyberbullying Online Harassment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios.
They outlined key actions the Administration is already taking to address online harassment and abuse, and explained that the Task Force will provide a blueprint for action within 180 days with ...
Workplace harassment training is important because it prevents incidents of harassment, bullying, and retaliation that may impact your organization's culture and expose your workplace to damaging consequences - personal and financial. Workplace harassment - in all of its forms - is highly disruptive and can lead to loss of productivity ...
Online harassment and abuse can result in a range of dire consequences for victims, from psychological distress and self-censorship to economic losses, disruptions to education, increased self ...
Presentation (250+) Feature (21) Video (10) Fact Sheet (8) Data Essay (4) Quiz (3) Database (1) Transcript (1) Regions & Countries. United States (250+) International (58) ... The State of Online Harassment. Roughly four-in-ten Americans have experienced online harassment, with half of this group citing politics as the reason they think they ...
30. Created By: Pennsylvania L&I. Download Atlantic Training's collection of safety training PowerPoints from around the web to train your team on important EHS Safety topics today. Harassment in the workplace creates a hostile work environment that no one would be comfortable working in. On top of it creating a work atmosphere detrimental to ...
Free Google Slides theme, PowerPoint template, and Canva presentation template. Labor harassment is a reality. When this type of situation occurs, the most important thing is to make the problem visible, so that solutions can be applied. However, solving an event does not prevent it from happening again, so what is the best way to proceed?
It is not just about sexual harassment; it encompasses any kind of harassment in the workplace. US law imposes mandatory sexual harassment training requirements to be fulfilled. As per EEOC charge data, the receipts of sexual harassment charges have fallen by 34.6% in 2021 compared to 2019 (7,514 charges in 2019; 5,581 charges in 2021).