IEEE Account
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Corpus ID: 212469884
4G Wireless Technology: A Brief Review
- Ashish Kumar , Ankit Aswal , L. Singh
- Published 2013
- Engineering, Computer Science
Figures and Tables from this paper

7 Citations
Study on call admission control schemes in 3gpp lte network, deep learning autoencoder based anomaly detection model on 4g network performance data, ehealth: a survey of architectures, developments in mhealth, security concerns and solutions, effect of internet use on medical students before and after 4g internet service in india: a comparative study., ubiquitous flipped classroom instructional model with learning process of scientific to enhance problem-solving skills for higher education (ufc-ps model), advances in fronthauling of communication technologies: a review, monografía internet de las cosas: modelos de comunicación, desafíos y aplicaciones., 14 references, 4g wireless technology: when will it happen what does it offer, beyond 3g: 4g mobile communication, 4g wireless networks: benefits and challenges.
- Highly Influential
- 10 Excerpts
The software radio concept
3gpp long term evolution: a technical overview, lte for umts - ofdma and sc-fdma based radio access, fundamentals of wimax: understanding broadband wireless networking, 3gpp long term evolution, trends in broadband wireless networks technologies, overview of handoff schemes in cellular mobile networks and their comparative performance evaluation, related papers.
Showing 1 through 3 of 0 Related Papers
Evolution of Wireless Communications with 3G, 4G, 5G, and Next Generation Technologies in India
- Conference paper
- First Online: 29 January 2021
- Cite this conference paper

- Pranay Yadav 38 ,
- Alok Upadhyay 39 ,
- V. B. Surya Prasath 40 ,
- Zakir Ali 41 &
- Bharat Bhooshan Khare 42
Part of the book series: Lecture Notes in Electrical Engineering ((LNEE,volume 709))
Included in the following conference series:
- International Conference on Emerging Trends and Advances in Electrical Engineering and Renewable Energy
905 Accesses
17 Citations
In the era of wireless communication, internet devices such as smart phones, hotspots, and Wi-Fi zone are important player of rapid growth of data usage. Internet connection devices are building new challenges for internet service providers such as higher bandwidth and indomitable increasing users day to day. This article gives an overview of existing different technologies of wireless communication as well as future enhancement of wireless services is explained. Different techniques during last decade are introduced for handling next generation techniques for ISPs. We provided a comparative analysis of different generations such as 3G, 4G, and 5G, and we focus on the next generation communication technologies 6G and 7G. Current research works are focused on 5G and next era generation of communication technologies. The development of internet infrastructure is essential for better mobile broadband experiences. In this work, we compared all the available generation communication systems, either wireless or wired, that are being deployed as well as future directions.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
- Durable hardcover edition
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Similar content being viewed by others

Evolution of Next-Generation Communication Technology

A Review on Progress and Future Trends for Wireless Network for Communication System

Comparative Study of Different Generations of Mobile Network
Lin, Y.-B., Lin, P.-J., Sung, Y. C., Chen, Y.-K., & Chen, W.-E. (2013). Performance measurements of TD-LTE, WiMAX and 3G systems. In IEEE Wireless Communications , June 2013.
Google Scholar
Pareit, D., et al. (2010). A throughput analysis at the MAC layer of mobile WiMAX. In Wireless Commun. and Net. Conf. (WCNC) , Apr. 2010.
Westall, J. M., & Martin, J. J. (2011). Performance characteristics of an oprational WiMAX network. IEEE Transactions Mobile Computing, 10 (7), 941–953.
Article Google Scholar
Sarma, A., Chakraborty, S., & Nandi, S. (2016). Deciding handover points based on context-aware load balancing in a WiFi-WiMAX heterogeneous network environment. IEEE Transactions on Vehicular Technology, 65 (1), January 2016.
Sapakal, R. S., & Kadam, S. S. (2013). 5G mobile technology. International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), 2 ,(2), February 2013.
Sharma, P., Verma, M., Sundriyal, N., & Chauhan, J. (2014). 5G mobile wireless technology. International Journal of Research (IJR), 1 (9), October 2014, ISSN 2348-6848.
Gupta, & Jha, R. K. (2015). A survey of 5G network: Architecture and emerging technologies. IEEE Access, 3 , 28.
Singh, A. P., Nigam, S., Gupta, N. K. (2016). A study of next generation wireless network 6G. International Journal of Innovative Research in Computer and Communication Engineering, 4 (1), January 2016.
Lin, Y.-B., & Alrajeh, N. (2012). Mobile telecommunications and applications to healthcare network . Kingdom of Saudi Arabia: Speech at King Abdulaziz City for Science and Technology.
Niyato, D., & Hossain, E. (2007). Wireless broadband access: WiMAX and beyond-integration of WiMAX and WiFi: Optimal pricing for bandwidth sharing. IEEE Communications Magazine, 45 (5), 140–146.
Wang, W., Liu, X., Vicente, J., & Mohapatra, P. (2011). Integration gain of heterogeneous WiFi/WiMAX networks. IEEE Transactions Mobile Comput, 10 (8), 1131–1143.
Meier, R. C., Dettloff, K., & Waclawsky, J. G. (2013). System and method for integrated WiFi/WiMAX neighbor AP discovery and AP advertisement . U.S. Patent 20 130 070 641, Mar. 21, 2013.
Lim, W.-S., Kim, D.-W., Suh, Y.-J., & Won, J.-J. (2009). Implementation and performance study of IEEE 802.21 in integrated IEEE 802.11/802.16e networks. Computer Communications, 32 (1), 134–143.
Kiran Gowda, H. N., Kusuma, M., & Udaya Kumar, C. (2013). A comprehensive study on 4G broadband networks: WiMAX and LTE. International Journal of Advanced Research in Computer and Communication Engineering, 2 (9), September 2013.
Abbas Ali, M., & Barakabitze, A. A. (2015). Evolution of LTE and related technologies towards IMT-advanced. International Journal of Advanced Research in Computer Science and Software Engineering, 5 (1), January 2015.
Yadav, P., Sharma, S., Tiwar, P., Prasad, M., Mohanty, S. P., & Puthal, D. (2018). A modified link consistency based routing protocol to prevent wormhole attacks in IoT. In IEEE, Consumer Electronics .
Yaday, P., Sharma, S., Tiwari, P., Prasad, M., & Mohanty, S. P. A system design for IoT based smart sensing and auto controlling for smart residence. IEEE Access (Under Review).
Yadav, P., Sharma, S., Tiwari, P., Dey, N., Ashour, A. S., & Nguyen, G. N. A Modified Hybrid Structure for Next Generation Super High Speed Communication Using TDLTE and Wi-Max . Accepted for publication in Studies in Big Data, Springer Book Chapter (Web of Science) 2017.
Download references
Author information
Authors and affiliations.
R&D, Ultra-Light Technology, Bhopal, India
Pranay Yadav
Quality Officer Vodaphone Idea Limited, Indore, MP, India
Alok Upadhyay
Division of Biomedical Informatics, Cincinnati Children’s Hospital Medical Center, Cincinnati, USA
V. B. Surya Prasath
Department of Electronics & Communication Engineering, IET, Bundelkhand University, Jhansi, India
Department of Electrical Engineering, UIT, Bhopal, MP, India
Bharat Bhooshan Khare
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Pranay Yadav .
Editor information
Editors and affiliations.
School of Computer Engineering, Kalinga Institute of Industrial Technology (KIIT Deemed to be University), Bhubaneswar, Odisha, India
Pradeep Kumar Mallick
Department Electrical and Electronics Engineering, Sikkim Manipal Institute of Technology, Rangpo, Sikkim, India
Akash Kumar Bhoi
Division of Information and Communication, Baekseok University, Cheonan, Ch’ungch’ong-namdo, Korea (Republic of)
Gyoo-Soo Chae
Vel Tech Rangarajan Dr. Sagunthala R&D Institute of Science and Technology, Chennai, Tamil Nadu, India
Kanak Kalita
Rights and permissions
Reprints and permissions
Copyright information
© 2021 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper.
Yadav, P., Upadhyay, A., Prasath, V.B.S., Ali, Z., Khare, B.B. (2021). Evolution of Wireless Communications with 3G, 4G, 5G, and Next Generation Technologies in India. In: Mallick, P.K., Bhoi, A.K., Chae, GS., Kalita, K. (eds) Advances in Electronics, Communication and Computing. ETAEERE 2020. Lecture Notes in Electrical Engineering, vol 709. Springer, Singapore. https://doi.org/10.1007/978-981-15-8752-8_35
Download citation
DOI : https://doi.org/10.1007/978-981-15-8752-8_35
Published : 29 January 2021
Publisher Name : Springer, Singapore
Print ISBN : 978-981-15-8751-1
Online ISBN : 978-981-15-8752-8
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

2G-4G Networks: Evolution of Technologies, Standards, and Deployment

2010, Encyclopedia of Multimedia Technology and …
Related Papers
Wasim Sulehria
International Journal IJRITCC
Cellular technology is the foundation of mobile wireless communications and supports users in locations that are not easily served by wired networks. Cellular technology is the underlying technology for mobile telephones, personal communications systems, wireless Internet and wireless Web applications, and much more. This article looks at how cellular technology has evolved through four generations and is poised for a fifth generation.
Xahara Eliya
Dragan Manevski
Garlapati Raviteja
srishti pathak
Shubham Dethe
Karamdeep Singh , Shivinder Devra
The need and demand of mobile and internet is increasing every day. Creation of technology and evolution of mobile industry has been initiated by mobile industry since early 1970s. First generation only provided voice communication facility, whereas second generation provided voice as well as data services. Further with more advancements in mobile wireless technology 3G provided us with video conferencing and etc. With increasing demand 4G came into existence and provided us with ultra-broadband internet access. 5G will be able to provide us facilities that one has never experienced till date. Our diversity of culture also plays a crucial role for this tremendous growth of mobile technology as they adopted this technology in friendly manner.
Ahmedul Haque
1. 5G technologies will change the way most high-bandwidth users access their phones. With 5G pushed over a VOIP-enabled device, people will experience a level of call volume and data transmission never experienced before.5G technology is offering the services in Product Engineering, Documentation, supporting electronic transactions (e-Payments, e-transactions) etc. As the customer becomes more and more aware of the mobile phone technology, he or she will look for a decent package all together, including all the advanced features a cellular phone can have. Hence the search for new technology is always the main motive of the leading cell phone giants to out innovate their competitors. Recently apple has produced shivers all around the electronic world by launching its new handset, the I-phone. Features that are getting embedded in such a small piece of electronics are huge.
American journal of Engineering Research (AJER)
This paper is focused on the specification of future generations of wireless mobile communication networks. The paper throws light on the evolution and development of various generations of mobile wireless technology along with their significance and advantages of one over the other. 5G technologies will change the way most high-bandwidth users access their phones. With 5G people will experience a level of call volume and data transmission never experienced before. 5G technology is offering the services in different fields like Documentation, supporting electronic transactions (e-Payments, e-transactions) etc. As the customer becomes more and more aware of the mobile phone technology, he or she will look for a decent package all together, including all the advanced features a cellular phone can have. The 5G design is based on user-centric mobile environment with many wireless and mobile technologies on the ground. WWWW that is World Wide Wireless Web allows complete wireless communication with almost no limitation, Multi-Media Newspapers, watch TV programs with the clarity as to that of an HD TV.
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Rahul Anand
Dan-jumbo Idaerefagha
Maheshkumar Sahu
Mian Ahmad Jan Palosa Campus AWKUM
IOSR Journals
Anish Mathews
IJRCAR JOURNAL
Independent IJCEROnline
Franklin Aditama Katoende
Iwan Krisnadi , Hartana Hartana
BIPUL KUMAR GUPTA
DIMAS HENDRATNO
ashwani kumar
virendra singh
Qammar Zaman
Abdulmajeed Ali Al Jabri
OBAIDALLAH ELSHAFIEY
Ilmah Rafia
Thayalan Ramasamy
Ahmed suliman
Carlos Negronomicón
IJCSMC Journal
Surbhi Mainde
Krishna Prasad K (Self Published)
Krishna Prasad
Ijariit Journal
Animesh Sonwane
The Ijes The Ijes
Samuel Ajayi
Innovative Research Publications
IJSTE - International Journal of Science Technology and Engineering
Darshan Lal
Shaik Mahaboob Subani
Bechtel Telecommunications Technical Journal
Tanu Jindal
MOHAMMAD ARIFIN RAHMAN KHAN
Agomuo Uchechukwu
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Sensors (Basel)

Study and Investigation on 5G Technology: A Systematic Review
Ramraj dangi.
1 School of Computing Science and Engineering, VIT University Bhopal, Bhopal 466114, India; [email protected] (R.D.); [email protected] (P.L.)
Praveen Lalwani
Gaurav choudhary.
2 Department of Applied Mathematics and Computer Science, Technical University of Denmark, 2800 Lyngby, Denmark; moc.liamg@7777yrahduohcvaruag
3 Department of Information Security Engineering, Soonchunhyang University, Asan-si 31538, Korea
Giovanni Pau
4 Faculty of Engineering and Architecture, Kore University of Enna, 94100 Enna, Italy; [email protected]
Associated Data
Not applicable.
In wireless communication, Fifth Generation (5G) Technology is a recent generation of mobile networks. In this paper, evaluations in the field of mobile communication technology are presented. In each evolution, multiple challenges were faced that were captured with the help of next-generation mobile networks. Among all the previously existing mobile networks, 5G provides a high-speed internet facility, anytime, anywhere, for everyone. 5G is slightly different due to its novel features such as interconnecting people, controlling devices, objects, and machines. 5G mobile system will bring diverse levels of performance and capability, which will serve as new user experiences and connect new enterprises. Therefore, it is essential to know where the enterprise can utilize the benefits of 5G. In this research article, it was observed that extensive research and analysis unfolds different aspects, namely, millimeter wave (mmWave), massive multiple-input and multiple-output (Massive-MIMO), small cell, mobile edge computing (MEC), beamforming, different antenna technology, etc. This article’s main aim is to highlight some of the most recent enhancements made towards the 5G mobile system and discuss its future research objectives.
1. Introduction
Most recently, in three decades, rapid growth was marked in the field of wireless communication concerning the transition of 1G to 4G [ 1 , 2 ]. The main motto behind this research was the requirements of high bandwidth and very low latency. 5G provides a high data rate, improved quality of service (QoS), low-latency, high coverage, high reliability, and economically affordable services. 5G delivers services categorized into three categories: (1) Extreme mobile broadband (eMBB). It is a nonstandalone architecture that offers high-speed internet connectivity, greater bandwidth, moderate latency, UltraHD streaming videos, virtual reality and augmented reality (AR/VR) media, and many more. (2) Massive machine type communication (eMTC), 3GPP releases it in its 13th specification. It provides long-range and broadband machine-type communication at a very cost-effective price with less power consumption. eMTC brings a high data rate service, low power, extended coverage via less device complexity through mobile carriers for IoT applications. (3) ultra-reliable low latency communication (URLLC) offers low-latency and ultra-high reliability, rich quality of service (QoS), which is not possible with traditional mobile network architecture. URLLC is designed for on-demand real-time interaction such as remote surgery, vehicle to vehicle (V2V) communication, industry 4.0, smart grids, intelligent transport system, etc. [ 3 ].
1.1. Evolution from 1G to 5G
First generation (1G): 1G cell phone was launched between the 1970s and 80s, based on analog technology, which works just like a landline phone. It suffers in various ways, such as poor battery life, voice quality, and dropped calls. In 1G, the maximum achievable speed was 2.4 Kbps.
Second Generation (2G): In 2G, the first digital system was offered in 1991, providing improved mobile voice communication over 1G. In addition, Code-Division Multiple Access (CDMA) and Global System for Mobile (GSM) concepts were also discussed. In 2G, the maximum achievable speed was 1 Mpbs.
Third Generation (3G): When technology ventured from 2G GSM frameworks into 3G universal mobile telecommunication system (UMTS) framework, users encountered higher system speed and quicker download speed making constant video calls. 3G was the first mobile broadband system that was formed to provide the voice with some multimedia. The technology behind 3G was high-speed packet access (HSPA/HSPA+). 3G used MIMO for multiplying the power of the wireless network, and it also used packet switching for fast data transmission.
Fourth Generation (4G): It is purely mobile broadband standard. In digital mobile communication, it was observed information rate that upgraded from 20 to 60 Mbps in 4G [ 4 ]. It works on LTE and WiMAX technologies, as well as provides wider bandwidth up to 100 Mhz. It was launched in 2010.
Fourth Generation LTE-A (4.5G): It is an advanced version of standard 4G LTE. LTE-A uses MIMO technology to combine multiple antennas for both transmitters as well as a receiver. Using MIMO, multiple signals and multiple antennas can work simultaneously, making LTE-A three times faster than standard 4G. LTE-A offered an improved system limit, decreased deferral in the application server, access triple traffic (Data, Voice, and Video) wirelessly at any time anywhere in the world.LTE-A delivers speeds of over 42 Mbps and up to 90 Mbps.
Fifth Generation (5G): 5G is a pillar of digital transformation; it is a real improvement on all the previous mobile generation networks. 5G brings three different services for end user like Extreme mobile broadband (eMBB). It offers high-speed internet connectivity, greater bandwidth, moderate latency, UltraHD streaming videos, virtual reality and augmented reality (AR/VR) media, and many more. Massive machine type communication (eMTC), it provides long-range and broadband machine-type communication at a very cost-effective price with less power consumption. eMTC brings a high data rate service, low power, extended coverage via less device complexity through mobile carriers for IoT applications. Ultra-reliable low latency communication (URLLC) offers low-latency and ultra-high reliability, rich quality of service (QoS), which is not possible with traditional mobile network architecture. URLLC is designed for on-demand real-time interaction such as remote surgery, vehicle to vehicle (V2V) communication, industry 4.0, smart grids, intelligent transport system, etc. 5G faster than 4G and offers remote-controlled operation over a reliable network with zero delays. It provides down-link maximum throughput of up to 20 Gbps. In addition, 5G also supports 4G WWWW (4th Generation World Wide Wireless Web) [ 5 ] and is based on Internet protocol version 6 (IPv6) protocol. 5G provides unlimited internet connection at your convenience, anytime, anywhere with extremely high speed, high throughput, low-latency, higher reliability and scalability, and energy-efficient mobile communication technology [ 6 ]. 5G mainly divided in two parts 6 GHz 5G and Millimeter wave(mmWave) 5G.
6 GHz is a mid frequency band which works as a mid point between capacity and coverage to offer perfect environment for 5G connectivity. 6 GHz spectrum will provide high bandwidth with improved network performance. It offers continuous channels that will reduce the need for network densification when mid-band spectrum is not available and it makes 5G connectivity affordable at anytime, anywhere for everyone.
mmWave is an essential technology of 5G network which build high performance network. 5G mmWave offer diverse services that is why all network providers should add on this technology in their 5G deployment planning. There are lots of service providers who deployed 5G mmWave, and their simulation result shows that 5G mmwave is a far less used spectrum. It provides very high speed wireless communication and it also offers ultra-wide bandwidth for next generation mobile network.
The evolution of wireless mobile technologies are presented in Table 1 . The abbreviations used in this paper are mentioned in Table 2 .
Summary of Mobile Technology.
| Generations | Access Techniques | Transmission Techniques | Error Correction Mechanism | Data Rate | Frequency Band | Bandwidth | Application | Description |
|---|---|---|---|---|---|---|---|---|
| 1G | FDMA, AMPS | Circuit Switching | NA | 2.4 kbps | 800 MHz | Analog | Voice | Let us talk to each other |
| 2G | GSM, TDMA, CDMA | Circuit Switching | NA | 10 kbps | 800 MHz, 900 MHz, 1800 MHz, 1900 MHz | 25 MHz | Voice and Data | Let us send messages and travel with improved data services |
| 3G | WCDMA, UMTS, CDMA 2000, HSUPA/HSDPA | Circuit and Packet Switching | Turbo Codes | 384 kbps to 5 Mbps | 800 MHz, 850 MHz, 900 MHz, 1800 MHz, 1900 MHz, 2100 MHz | 25 MHz | Voice, Data, and Video Calling | Let us experience surfing internet and unleashing mobile applications |
| 4G | LTEA, OFDMA, SCFDMA, WIMAX | Packet switching | Turbo Codes | 100 Mbps to 200 Mbps | 2.3 GHz, 2.5 GHz and 3.5 GHz initially | 100 MHz | Voice, Data, Video Calling, HD Television, and Online Gaming. | Let’s share voice and data over fast broadband internet based on unified networks architectures and IP protocols |
| 5G | BDMA, NOMA, FBMC | Packet Switching | LDPC | 10 Gbps to 50 Gbps | 1.8 GHz, 2.6 GHz and 30–300 GHz | 30–300 GHz | Voice, Data, Video Calling, Ultra HD video, Virtual Reality applications | Expanded the broadband wireless services beyond mobile internet with IOT and V2X. |
Table of Notations and Abbreviations.
| Abbreviation | Full Form | Abbreviation | Full Form |
|---|---|---|---|
| AMF | Access and Mobility Management Function | M2M | Machine-to-Machine |
| AT&T | American Telephone and Telegraph | mmWave | millimeter wave |
| BS | Base Station | NGMN | Next Generation Mobile Networks |
| CDMA | Code-Division Multiple Access | NOMA | Non-Orthogonal Multiple Access |
| CSI | Channel State Information | NFV | Network Functions Virtualization |
| D2D | Device to Device | OFDM | Orthogonal Frequency Division Multiplexing |
| EE | Energy Efficiency | OMA | Orthogonal Multiple Access |
| EMBB | Enhanced mobile broadband: | QoS | Quality of Service |
| ETSI | European Telecommunications Standards Institute | RNN | Recurrent Neural Network |
| eMTC | Massive Machine Type Communication | SDN | Software-Defined Networking |
| FDMA | Frequency Division Multiple Access | SC | Superposition Coding |
| FDD | Frequency Division Duplex | SIC | Successive Interference Cancellation |
| GSM | Global System for Mobile | TDMA | Time Division Multiple Access |
| HSPA | High Speed Packet Access | TDD | Time Division Duplex |
| IoT | Internet of Things | UE | User Equipment |
| IETF | Internet Engineering Task Force | URLLC | Ultra Reliable Low Latency Communication |
| LTE | Long-Term Evolution | UMTC | Universal Mobile Telecommunications System |
| ML | Machine Learning | V2V | Vehicle to Vehicle |
| MIMO | Multiple Input Multiple Output | V2X | Vehicle to Everything |
1.2. Key Contributions
The objective of this survey is to provide a detailed guide of 5G key technologies, methods to researchers, and to help with understanding how the recent works addressed 5G problems and developed solutions to tackle the 5G challenges; i.e., what are new methods that must be applied and how can they solve problems? Highlights of the research article are as follows.
- This survey focused on the recent trends and development in the era of 5G and novel contributions by the researcher community and discussed technical details on essential aspects of the 5G advancement.
- In this paper, the evolution of the mobile network from 1G to 5G is presented. In addition, the growth of mobile communication under different attributes is also discussed.
- This paper covers the emerging applications and research groups working on 5G & different research areas in 5G wireless communication network with a descriptive taxonomy.
- This survey discusses the current vision of the 5G networks, advantages, applications, key technologies, and key features. Furthermore, machine learning prospects are also explored with the emerging requirements in the 5G era. The article also focused on technical aspects of 5G IoT Based approaches and optimization techniques for 5G.
- we provide an extensive overview and recent advancement of emerging technologies of 5G mobile network, namely, MIMO, Non-Orthogonal Multiple Access (NOMA), mmWave, Internet of Things (IoT), Machine Learning (ML), and optimization. Also, a technical summary is discussed by highlighting the context of current approaches and corresponding challenges.
- Security challenges and considerations while developing 5G technology are discussed.
- Finally, the paper concludes with the future directives.
The existing survey focused on architecture, key concepts, and implementation challenges and issues. In contrast, this survey covers the state-of-the-art techniques as well as corresponding recent novel developments by researchers. Various recent significant papers are discussed with the key technologies accelerating the development and production of 5G products.
2. Existing Surveys and Their Applicability
In this paper, a detailed survey on various technologies of 5G networks is presented. Various researchers have worked on different technologies of 5G networks. In this section, Table 3 gives a tabular representation of existing surveys of 5G networks. Massive MIMO, NOMA, small cell, mmWave, beamforming, and MEC are the six main pillars that helped to implement 5G networks in real life.
A comparative overview of existing surveys on different technologies of 5G networks.
| Authors& References | MIMO | NOMA | MmWave | 5G IOT | 5G ML | Small Cell | Beamforming | MEC | 5G Optimization |
|---|---|---|---|---|---|---|---|---|---|
| Chataut and Akl [ ] | Yes | - | Yes | - | - | - | Yes | - | - |
| Prasad et al. [ ] | Yes | - | Yes | - | - | - | - | - | - |
| Kiani and Nsari [ ] | - | Yes | - | - | - | - | - | Yes | - |
| Timotheou and Krikidis [ ] | - | Yes | - | - | - | - | - | - | Yes |
| Yong Niu et al. [ ] | - | - | Yes | - | - | Yes | - | - | - |
| Qiao et al. [ ] | - | - | Yes | - | - | - | - | - | Yes |
| Ramesh et al. [ ] | Yes | - | Yes | - | - | - | - | - | - |
| Khurpade et al. [ ] | Yes | Yes | - | Yes | - | - | - | - | - |
| Bega et al. [ ] | - | - | - | - | Yes | - | - | - | Yes |
| Abrol and jha [ ] | - | - | - | - | - | Yes | - | - | Yes |
| Wei et al. [ ] | - | Yes | - | - | - | - | - | - | |
| Jakob Hoydis et al. [ ] | - | - | - | - | - | Yes | - | - | - |
| Papadopoulos et al. [ ] | Yes | - | - | - | - | - | Yes | - | - |
| Shweta Rajoria et al. [ ] | Yes | - | Yes | - | - | Yes | Yes | - | - |
| Demosthenes Vouyioukas [ ] | Yes | - | - | - | - | - | Yes | - | - |
| Al-Imari et al. [ ] | - | Yes | Yes | - | - | - | - | - | - |
| Michael Till Beck et al. [ ] | - | - | - | - | - | - | Yes | - | |
| Shuo Wang et al. [ ] | - | - | - | - | - | - | Yes | - | |
| Gupta and Jha [ ] | Yes | - | - | - | - | Yes | - | Yes | - |
| Our Survey | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
2.1. Limitations of Existing Surveys
The existing survey focused on architecture, key concepts, and implementation challenges and issues. The numerous current surveys focused on various 5G technologies with different parameters, and the authors did not cover all the technologies of the 5G network in detail with challenges and recent advancements. Few authors worked on MIMO (Non-Orthogonal Multiple Access) NOMA, MEC, small cell technologies. In contrast, some others worked on beamforming, Millimeter-wave (mmWave). But the existing survey did not cover all the technologies of the 5G network from a research and advancement perspective. No detailed survey is available in the market covering all the 5G network technologies and currently published research trade-offs. So, our main aim is to give a detailed study of all the technologies working on the 5G network. In contrast, this survey covers the state-of-the-art techniques as well as corresponding recent novel developments by researchers. Various recent significant papers are discussed with the key technologies accelerating the development and production of 5G products. This survey article collected key information about 5G technology and recent advancements, and it can be a kind of a guide for the reader. This survey provides an umbrella approach to bring multiple solutions and recent improvements in a single place to accelerate the 5G research with the latest key enabling solutions and reviews. A systematic layout representation of the survey in Figure 1 . We provide a state-of-the-art comparative overview of the existing surveys on different technologies of 5G networks in Table 3 .

Systematic layout representation of survey.
2.2. Article Organization
This article is organized under the following sections. Section 2 presents existing surveys and their applicability. In Section 3 , the preliminaries of 5G technology are presented. In Section 4 , recent advances of 5G technology based on Massive MIMO, NOMA, Millimeter Wave, 5G with IoT, machine learning for 5G, and Optimization in 5G are provided. In Section 5 , a description of novel 5G features over 4G is provided. Section 6 covered all the security concerns of the 5G network. Section 7 , 5G technology based on above-stated challenges summarize in tabular form. Finally, Section 8 and Section 9 conclude the study, which paves the path for future research.
3. Preliminary Section
3.1. emerging 5g paradigms and its features.
5G provides very high speed, low latency, and highly salable connectivity between multiple devices and IoT worldwide. 5G will provide a very flexible model to develop a modern generation of applications and industry goals [ 26 , 27 ]. There are many services offered by 5G network architecture are stated below:
Massive machine to machine communications: 5G offers novel, massive machine-to-machine communications [ 28 ], also known as the IoT [ 29 ], that provide connectivity between lots of machines without any involvement of humans. This service enhances the applications of 5G and provides connectivity between agriculture, construction, and industries [ 30 ].
Ultra-reliable low latency communications (URLLC): This service offers real-time management of machines, high-speed vehicle-to-vehicle connectivity, industrial connectivity and security principles, and highly secure transport system, and multiple autonomous actions. Low latency communications also clear up a different area where remote medical care, procedures, and operation are all achievable [ 31 ].
Enhanced mobile broadband: Enhance mobile broadband is an important use case of 5G system, which uses massive MIMO antenna, mmWave, beamforming techniques to offer very high-speed connectivity across a wide range of areas [ 32 ].
For communities: 5G provides a very flexible internet connection between lots of machines to make smart homes, smart schools, smart laboratories, safer and smart automobiles, and good health care centers [ 33 ].
For businesses and industry: As 5G works on higher spectrum ranges from 24 to 100 GHz. This higher frequency range provides secure low latency communication and high-speed wireless connectivity between IoT devices and industry 4.0, which opens a market for end-users to enhance their business models [ 34 ].
New and Emerging technologies: As 5G came up with many new technologies like beamforming, massive MIMO, mmWave, small cell, NOMA, MEC, and network slicing, it introduced many new features to the market. Like virtual reality (VR), users can experience the physical presence of people who are millions of kilometers away from them. Many new technologies like smart homes, smart workplaces, smart schools, smart sports academy also came into the market with this 5G Mobile network model [ 35 ].
3.2. Commercial Service Providers of 5G
5G provides high-speed internet browsing, streaming, and downloading with very high reliability and low latency. 5G network will change your working style, and it will increase new business opportunities and provide innovations that we cannot imagine. This section covers top service providers of 5G network [ 36 , 37 ].
Ericsson: Ericsson is a Swedish multinational networking and telecommunications company, investing around 25.62 billion USD in 5G network, which makes it the biggest telecommunication company. It claims that it is the only company working on all the continents to make the 5G network a global standard for the next generation wireless communication. Ericsson developed the first 5G radio prototype that enables the operators to set up the live field trials in their network, which helps operators understand how 5G reacts. It plays a vital role in the development of 5G hardware. It currently provides 5G services in over 27 countries with content providers like China Mobile, GCI, LGU+, AT&T, Rogers, and many more. It has 100 commercial agreements with different operators as of 2020.
Verizon: It is American multinational telecommunication which was founded in 1983. Verizon started offering 5G services in April 2020, and by December 2020, it has actively provided 5G services in 30 cities of the USA. They planned that by the end of 2021, they would deploy 5G in 30 more new cities. Verizon deployed a 5G network on mmWave, a very high band spectrum between 30 to 300 GHz. As it is a significantly less used spectrum, it provides very high-speed wireless communication. MmWave offers ultra-wide bandwidth for next-generation mobile networks. MmWave is a faster and high-band spectrum that has a limited range. Verizon planned to increase its number of 5G cells by 500% by 2020. Verizon also has an ultra wide-band flagship 5G service which is the best 5G service that increases the market price of Verizon.
Nokia: Nokia is a Finnish multinational telecommunications company which was founded in 1865. Nokia is one of the companies which adopted 5G technology very early. It is developing, researching, and building partnerships with various 5G renders to offer 5G communication as soon as possible. Nokia collaborated with Deutsche Telekom and Hamburg Port Authority and provided them 8000-hectare site for their 5G MoNArch project. Nokia is the only company that supplies 5G technology to all the operators of different countries like AT&T, Sprint, T-Mobile US and Verizon in the USA, Korea Telecom, LG U+ and SK Telecom in South Korea and NTT DOCOMO, KDDI, and SoftBank in Japan. Presently, Nokia has around 150+ agreements and 29 live networks all over the world. Nokia is continuously working hard on 5G technology to expand 5G networks all over the globe.
AT&T: AT&T is an American multinational company that was the first to deploy a 5G network in reality in 2018. They built a gigabit 5G network connection in Waco, TX, Kalamazoo, MI, and South Bend to achieve this. It is the first company that archives 1–2 gigabit per second speed in 2019. AT&T claims that it provides a 5G network connection among 225 million people worldwide by using a 6 GHz spectrum band.
T-Mobile: T-Mobile US (TMUS) is an American wireless network operator which was the first service provider that offers a real 5G nationwide network. The company knew that high-band 5G was not feasible nationwide, so they used a 600 MHz spectrum to build a significant portion of its 5G network. TMUS is planning that by 2024 they will double the total capacity and triple the full 5G capacity of T-Mobile and Sprint combined. The sprint buyout is helping T-Mobile move forward the company’s current market price to 129.98 USD.
Samsung: Samsung started their research in 5G technology in 2011. In 2013, Samsung successfully developed the world’s first adaptive array transceiver technology operating in the millimeter-wave Ka bands for cellular communications. Samsung provides several hundred times faster data transmission than standard 4G for core 5G mobile communication systems. The company achieved a lot of success in the next generation of technology, and it is considered one of the leading companies in the 5G domain.
Qualcomm: Qualcomm is an American multinational corporation in San Diego, California. It is also one of the leading company which is working on 5G chip. Qualcomm’s first 5G modem chip was announced in October 2016, and a prototype was demonstrated in October 2017. Qualcomm mainly focuses on building products while other companies talk about 5G; Qualcomm is building the technologies. According to one magazine, Qualcomm was working on three main areas of 5G networks. Firstly, radios that would use bandwidth from any network it has access to; secondly, creating more extensive ranges of spectrum by combining smaller pieces; and thirdly, a set of services for internet applications.
ZTE Corporation: ZTE Corporation was founded in 1985. It is a partially Chinese state-owned technology company that works in telecommunication. It was a leading company that worked on 4G LTE, and it is still maintaining its value and doing research and tests on 5G. It is the first company that proposed Pre5G technology with some series of solutions.
NEC Corporation: NEC Corporation is a Japanese multinational information technology and electronics corporation headquartered in Minato, Tokyo. ZTE also started their research on 5G, and they introduced a new business concept. NEC’s main aim is to develop 5G NR for the global mobile system and create secure and intelligent technologies to realize 5G services.
Cisco: Cisco is a USA networking hardware company that also sleeves up for 5G network. Cisco’s primary focus is to support 5G in three ways: Service—enable 5G services faster so all service providers can increase their business. Infrastructure—build 5G-oriented infrastructure to implement 5G more quickly. Automation—make a more scalable, flexible, and reliable 5G network. The companies know the importance of 5G, and they want to connect more than 30 billion devices in the next couple of years. Cisco intends to work on network hardening as it is a vital part of 5G network. Cisco used AI with deep learning to develop a 5G Security Architecture, enabling Secure Network Transformation.
3.3. 5G Research Groups
Many research groups from all over the world are working on a 5G wireless mobile network [ 38 ]. These groups are continuously working on various aspects of 5G. The list of those research groups are presented as follows: 5GNOW (5th Generation Non-Orthogonal Waveform for Asynchronous Signaling), NEWCOM (Network of Excellence in Wireless Communication), 5GIC (5G Innovation Center), NYU (New York University) Wireless, 5GPPP (5G Infrastructure Public-Private Partnership), EMPHATIC (Enhanced Multi-carrier Technology for Professional Adhoc and Cell-Based Communication), ETRI(Electronics and Telecommunication Research Institute), METIS (Mobile and wireless communication Enablers for the Twenty-twenty Information Society) [ 39 ]. The various research groups along with the research area are presented in Table 4 .
Research groups working on 5G mobile networks.
| Research Groups | Research Area | Description |
|---|---|---|
| METIS (Mobile and wireless communications Enablers for Twenty-twenty (2020) Information Society) | Working 5G Framework | METIS focused on RAN architecture and designed an air interface which evaluates data rates on peak hours, traffic load per region, traffic volume per user and actual client data rates. They have generate METIS published an article on February, 2015 in which they developed RAN architecture with simulation results. They design an air interface which evaluates data rates on peak hours, traffic load per region, traffic volume per user and actual client data rates.They have generate very less RAN latency under 1ms. They also introduced diverse RAN model and traffic flow in different situation like malls, offices, colleges and stadiums. |
| 5G PPP (5G Infrastructure Public Private Partnership) | Next generation mobile network communication, high speed Connectivity. | Fifth generation infrastructure public partnership project is a joint startup by two groups (European Commission and European ICT industry). 5G-PPP will provide various standards architectures, solutions and technologies for next generation mobile network in coming decade. The main motto behind 5G-PPP is that, through this project, European Commission wants to give their contribution in smart cities, e-health, intelligent transport, education, entertainment, and media. |
| 5GNOW (5th Generation Non-Orthogonal Waveforms for asynchronous signaling) | Non-orthogonal Multiple Access | 5GNOW’s is working on modulation and multiplexing techniques for next generation network. 5GNOW’s offers ultra-high reliability and ultra-low latency communication with visible waveform for 5G. 5GNOW’s also worked on acquiring time and frequency plane information of a signal using short term Fourier transform (STFT) |
| EMPhAtiC (Enhanced Multicarrier Technology for Professional Ad-Hoc and Cell-Based Communications) | MIMO Transmission | EMPhAtiC is working on MIMO transmission to develop a secure communication techniques with asynchronicity based on flexible filter bank and multihop. Recently they also launched MIMO based trans-receiver technique under frequency selective channels for Filter Bank Multi-Carrier (FBMC) |
| NEWCOM (Network of Excellence in Wireless Communications) | Advanced aspects of wireless communications | NEWCOM is working on energy efficiency, channel efficiency, multihop communication in wireless communication. Recently, they are working on cloud RAN, mobile broadband, local and distributed antenna techniques and multi-hop communication for 5G network. Finally, in their final research they give on result that QAM modulation schema, system bandwidth and resource block is used to process the base band. |
| NYU New York University Wireless | Millimeter Wave | NYU Wireless is research center working on wireless communication, sensors, networking and devices. In their recent research, NYU focuses on developing smaller and lighter antennas with directional beamforming to provide reliable wireless communication. |
| 5GIC 5G Innovation Centre | Decreasing network costs, Preallocation of resources according to user’s need, point-to-point communication, Highspeed connectivity. | 5GIC, is a UK’s research group, which is working on high-speed wireless communication. In their recent research they got 1Tbps speed in point-to-point wireless communication. Their main focus is on developing ultra-low latency app services. |
| ETRI (Electronics and Telecommunication Research Institute) | Device-to-device communication, MHN protocol stack | ETRI (Electronics and Telecommunication Research Institute), is a research group of Korea, which is focusing on improving the reliability of 5G network, device-to-device communication and MHN protocol stack. |
3.4. 5G Applications
5G is faster than 4G and offers remote-controlled operation over a reliable network with zero delays. It provides down-link maximum throughput of up to 20 Gbps. In addition, 5G also supports 4G WWWW (4th Generation World Wide Wireless Web) [ 5 ] and is based on Internet protocol version 6 (IPv6) protocol. 5G provides unlimited internet connection at your convenience, anytime, anywhere with extremely high speed, high throughput, low-latency, higher reliability, greater scalablility, and energy-efficient mobile communication technology [ 6 ].
There are lots of applications of 5G mobile network are as follows:
- High-speed mobile network: 5G is an advancement on all the previous mobile network technologies, which offers very high speed downloading speeds 0 of up to 10 to 20 Gbps. The 5G wireless network works as a fiber optic internet connection. 5G is different from all the conventional mobile transmission technologies, and it offers both voice and high-speed data connectivity efficiently. 5G offers very low latency communication of less than a millisecond, useful for autonomous driving and mission-critical applications. 5G will use millimeter waves for data transmission, providing higher bandwidth and a massive data rate than lower LTE bands. As 5 Gis a fast mobile network technology, it will enable virtual access to high processing power and secure and safe access to cloud services and enterprise applications. Small cell is one of the best features of 5G, which brings lots of advantages like high coverage, high-speed data transfer, power saving, easy and fast cloud access, etc. [ 40 ].
- Entertainment and multimedia: In one analysis in 2015, it was found that more than 50 percent of mobile internet traffic was used for video downloading. This trend will surely increase in the future, which will make video streaming more common. 5G will offer High-speed streaming of 4K videos with crystal clear audio, and it will make a high definition virtual world on your mobile. 5G will benefit the entertainment industry as it offers 120 frames per second with high resolution and higher dynamic range video streaming, and HD TV channels can also be accessed on mobile devices without any interruptions. 5G provides low latency high definition communication so augmented reality (AR), and virtual reality (VR) will be very easily implemented in the future. Virtual reality games are trendy these days, and many companies are investing in HD virtual reality games. The 5G network will offer high-speed internet connectivity with a better gaming experience [ 41 ].
- Smart homes : smart home appliances and products are in demand these days. The 5G network makes smart homes more real as it offers high-speed connectivity and monitoring of smart appliances. Smart home appliances are easily accessed and configured from remote locations using the 5G network as it offers very high-speed low latency communication.
- Smart cities: 5G wireless network also helps develop smart cities applications such as automatic traffic management, weather update, local area broadcasting, energy-saving, efficient power supply, smart lighting system, water resource management, crowd management, emergency control, etc.
- Industrial IoT: 5G wireless technology will provide lots of features for future industries such as safety, process tracking, smart packing, shipping, energy efficiency, automation of equipment, predictive maintenance, and logistics. 5G smart sensor technology also offers smarter, safer, cost-effective, and energy-saving industrial IoT operations.
- Smart Farming: 5G technology will play a crucial role in agriculture and smart farming. 5G sensors and GPS technology will help farmers track live attacks on crops and manage them quickly. These smart sensors can also be used for irrigation, pest, insect, and electricity control.
- Autonomous Driving: The 5G wireless network offers very low latency high-speed communication, significant for autonomous driving. It means self-driving cars will come to real life soon with 5G wireless networks. Using 5G autonomous cars can easily communicate with smart traffic signs, objects, and other vehicles running on the road. 5G’s low latency feature makes self-driving more real as every millisecond is essential for autonomous vehicles, decision-making is done in microseconds to avoid accidents.
- Healthcare and mission-critical applications: 5G technology will bring modernization in medicine where doctors and practitioners can perform advanced medical procedures. The 5G network will provide connectivity between all classrooms, so attending seminars and lectures will be easier. Through 5G technology, patients can connect with doctors and take their advice. Scientists are building smart medical devices which can help people with chronic medical conditions. The 5G network will boost the healthcare industry with smart devices, the internet of medical things, smart sensors, HD medical imaging technologies, and smart analytics systems. 5G will help access cloud storage, so accessing healthcare data will be very easy from any location worldwide. Doctors and medical practitioners can easily store and share large files like MRI reports within seconds using the 5G network.
- Satellite Internet: In many remote areas, ground base stations are not available, so 5G will play a crucial role in providing connectivity in such areas. The 5G network will provide connectivity using satellite systems, and the satellite system uses a constellation of multiple small satellites to provide connectivity in urban and rural areas across the world.
4. 5G Technologies
This section describes recent advances of 5G Massive MIMO, 5G NOMA, 5G millimeter wave, 5G IOT, 5G with machine learning, and 5G optimization-based approaches. In addition, the summary is also presented in each subsection that paves the researchers for the future research direction.
4.1. 5G Massive MIMO
Multiple-input-multiple-out (MIMO) is a very important technology for wireless systems. It is used for sending and receiving multiple signals simultaneously over the same radio channel. MIMO plays a very big role in WI-FI, 3G, 4G, and 4G LTE-A networks. MIMO is mainly used to achieve high spectral efficiency and energy efficiency but it was not up to the mark MIMO provides low throughput and very low reliable connectivity. To resolve this, lots of MIMO technology like single user MIMO (SU-MIMO), multiuser MIMO (MU-MIMO) and network MIMO were used. However, these new MIMO also did not still fulfill the demand of end users. Massive MIMO is an advancement of MIMO technology used in the 5G network in which hundreds and thousands of antennas are attached with base stations to increase throughput and spectral efficiency. Multiple transmit and receive antennas are used in massive MIMO to increase the transmission rate and spectral efficiency. When multiple UEs generate downlink traffic simultaneously, massive MIMO gains higher capacity. Massive MIMO uses extra antennas to move energy into smaller regions of space to increase spectral efficiency and throughput [ 43 ]. In traditional systems data collection from smart sensors is a complex task as it increases latency, reduced data rate and reduced reliability. While massive MIMO with beamforming and huge multiplexing techniques can sense data from different sensors with low latency, high data rate and higher reliability. Massive MIMO will help in transmitting the data in real-time collected from different sensors to central monitoring locations for smart sensor applications like self-driving cars, healthcare centers, smart grids, smart cities, smart highways, smart homes, and smart enterprises [ 44 ].
Highlights of 5G Massive MIMO technology are as follows:
- Data rate: Massive MIMO is advised as the one of the dominant technologies to provide wireless high speed and high data rate in the gigabits per seconds.
- The relationship between wave frequency and antenna size: Both are inversely proportional to each other. It means lower frequency signals need a bigger antenna and vise versa.

Pictorial representation of multi-input and multi-output (MIMO).
- MIMO role in 5G: Massive MIMO will play a crucial role in the deployment of future 5G mobile communication as greater spectral and energy efficiency could be enabled.
State-of-the-Art Approaches
Plenty of approaches were proposed to resolve the issues of conventional MIMO [ 7 ].
The MIMO multirate, feed-forward controller is suggested by Mae et al. [ 46 ]. In the simulation, the proposed model generates the smooth control input, unlike the conventional MIMO, which generates oscillated control inputs. It also outperformed concerning the error rate. However, a combination of multirate and single rate can be used for better results.
The performance of stand-alone MIMO, distributed MIMO with and without corporation MIMO, was investigated by Panzner et al. [ 47 ]. In addition, an idea about the integration of large scale in the 5G technology was also presented. In the experimental analysis, different MIMO configurations are considered. The variation in the ratio of overall transmit antennas to spatial is deemed step-wise from equality to ten.
The simulation of massive MIMO noncooperative and cooperative systems for down-link behavior was performed by He et al. [ 48 ]. It depends on present LTE systems, which deal with various antennas in the base station set-up. It was observed that collaboration in different BS improves the system behaviors, whereas throughput is reduced slightly in this approach. However, a new method can be developed which can enhance both system behavior and throughput.
In [ 8 ], different approaches that increased the energy efficiency benefits provided by massive MIMO were presented. They analyzed the massive MIMO technology and described the detailed design of the energy consumption model for massive MIMO systems. This article has explored several techniques to enhance massive MIMO systems’ energy efficiency (EE) gains. This paper reviews standard EE-maximization approaches for the conventional massive MIMO systems, namely, scaling number of antennas, real-time implementing low-complexity operations at the base station (BS), power amplifier losses minimization, and radio frequency (RF) chain minimization requirements. In addition, open research direction is also identified.
In [ 49 ], various existing approaches based on different antenna selection and scheduling, user selection and scheduling, and joint antenna and user scheduling methods adopted in massive MIMO systems are presented in this paper. The objective of this survey article was to make awareness about the current research and future research direction in MIMO for systems. They analyzed that complete utilization of resources and bandwidth was the most crucial factor which enhances the sum rate.
In [ 50 ], authors discussed the development of various techniques for pilot contamination. To calculate the impact of pilot contamination in time division duplex (TDD) massive MIMO system, TDD and frequency division duplexing FDD patterns in massive MIMO techniques are used. They discussed different issues in pilot contamination in TDD massive MIMO systems with all the possible future directions of research. They also classified various techniques to generate the channel information for both pilot-based and subspace-based approaches.
In [ 19 ], the authors defined the uplink and downlink services for a massive MIMO system. In addition, it maintains a performance matrix that measures the impact of pilot contamination on different performances. They also examined the various application of massive MIMO such as small cells, orthogonal frequency-division multiplexing (OFDM) schemes, massive MIMO IEEE 802, 3rd generation partnership project (3GPP) specifications, and higher frequency bands. They considered their research work crucial for cutting edge massive MIMO and covered many issues like system throughput performance and channel state acquisition at higher frequencies.
In [ 13 ], various approaches were suggested for MIMO future generation wireless communication. They made a comparative study based on performance indicators such as peak data rate, energy efficiency, latency, throughput, etc. The key findings of this survey are as follows: (1) spatial multiplexing improves the energy efficiency; (2) design of MIMO play a vital role in the enhancement of throughput; (3) enhancement of mMIMO focusing on energy & spectral performance; (4) discussed the future challenges to improve the system design.
In [ 51 ], the study of large-scale MIMO systems for an energy-efficient system sharing method was presented. For the resource allocation, circuit energy and transmit energy expenditures were taken into consideration. In addition, the optimization techniques were applied for an energy-efficient resource sharing system to enlarge the energy efficiency for individual QoS and energy constraints. The author also examined the BS configuration, which includes homogeneous and heterogeneous UEs. While simulating, they discussed that the total number of transmit antennas plays a vital role in boosting energy efficiency. They highlighted that the highest energy efficiency was obtained when the BS was set up with 100 antennas that serve 20 UEs.
This section includes various works done on 5G MIMO technology by different author’s. Table 5 shows how different author’s worked on improvement of various parameters such as throughput, latency, energy efficiency, and spectral efficiency with 5G MIMO technology.
Summary of massive MIMO-based approaches in 5G technology.
| Approach | Throughput | Latency | Energy Efficiency | Spectral Efficiency |
|---|---|---|---|---|
| Panzner et al. [ ] | Good | Low | Good | Average |
| He et al. [ ] | Average | Low | Average | - |
| Prasad et al. [ ] | Good | - | Good | Avearge |
| Papadopoulos et al. [ ] | Good | Low | Average | Avearge |
| Ramesh et al. [ ] | Good | Average | Good | Good |
| Zhou et al. [ ] | Average | - | Good | Average |
4.2. 5G Non-Orthogonal Multiple Access (NOMA)
NOMA is a very important radio access technology used in next generation wireless communication. Compared to previous orthogonal multiple access techniques, NOMA offers lots of benefits like high spectrum efficiency, low latency with high reliability and high speed massive connectivity. NOMA mainly works on a baseline to serve multiple users with the same resources in terms of time, space and frequency. NOMA is mainly divided into two main categories one is code domain NOMA and another is power domain NOMA. Code-domain NOMA can improve the spectral efficiency of mMIMO, which improves the connectivity in 5G wireless communication. Code-domain NOMA was divided into some more multiple access techniques like sparse code multiple access, lattice-partition multiple access, multi-user shared access and pattern-division multiple access [ 52 ]. Power-domain NOMA is widely used in 5G wireless networks as it performs well with various wireless communication techniques such as MIMO, beamforming, space-time coding, network coding, full-duplex and cooperative communication etc. [ 53 ]. The conventional orthogonal frequency-division multiple access (OFDMA) used by 3GPP in 4G LTE network provides very low spectral efficiency when bandwidth resources are allocated to users with low channel state information (CSI). NOMA resolved this issue as it enables users to access all the subcarrier channels so bandwidth resources allocated to the users with low CSI can still be accessed by the users with strong CSI which increases the spectral efficiency. The 5G network will support heterogeneous architecture in which small cell and macro base stations work for spectrum sharing. NOMA is a key technology of the 5G wireless system which is very helpful for heterogeneous networks as multiple users can share their data in a small cell using the NOMA principle.The NOMA is helpful in various applications like ultra-dense networks (UDN), machine to machine (M2M) communication and massive machine type communication (mMTC). As NOMA provides lots of features it has some challenges too such as NOMA needs huge computational power for a large number of users at high data rates to run the SIC algorithms. Second, when users are moving from the networks, to manage power allocation optimization is a challenging task for NOMA [ 54 ]. Hybrid NOMA (HNOMA) is a combination of power-domain and code-domain NOMA. HNOMA uses both power differences and orthogonal resources for transmission among multiple users. As HNOMA is using both power-domain NOMA and code-domain NOMA it can achieve higher spectral efficiency than Power-domain NOMA and code-domain NOMA. In HNOMA multiple groups can simultaneously transmit signals at the same time. It uses a message passing algorithm (MPA) and successive interference cancellation (SIC)-based detection at the base station for these groups [ 55 ].
Highlights of 5G NOMA technology as follows:

Pictorial representation of orthogonal and Non-Orthogonal Multiple Access (NOMA).
- NOMA provides higher data rates and resolves all the loop holes of OMA that makes 5G mobile network more scalable and reliable.
- As multiple users use same frequency band simultaneously it increases the performance of whole network.
- To setup intracell and intercell interference NOMA provides nonorthogonal transmission on the transmitter end.
- The primary fundamental of NOMA is to improve the spectrum efficiency by strengthening the ramification of receiver.
State-of-the-Art of Approaches
A plenty of approaches were developed to address the various issues in NOMA.
A novel approach to address the multiple receiving signals at the same frequency is proposed in [ 22 ]. In NOMA, multiple users use the same sub-carrier, which improves the fairness and throughput of the system. As a nonorthogonal method is used among multiple users, at the time of retrieving the user’s signal at the receiver’s end, joint processing is required. They proposed solutions to optimize the receiver and the radio resource allocation of uplink NOMA. Firstly, the authors proposed an iterative MUDD which utilizes the information produced by the channel decoder to improve the performance of the multiuser detector. After that, the author suggested a power allocation and novel subcarrier that enhances the users’ weighted sum rate for the NOMA scheme. Their proposed model showed that NOMA performed well as compared to OFDM in terms of fairness and efficiency.
In [ 53 ], the author’s reviewed a power-domain NOMA that uses superposition coding (SC) and successive interference cancellation (SIC) at the transmitter and the receiver end. Lots of analyses were held that described that NOMA effectively satisfies user data rate demands and network-level of 5G technologies. The paper presented a complete review of recent advances in the 5G NOMA system. It showed the comparative analysis regarding allocation procedures, user fairness, state-of-the-art efficiency evaluation, user pairing pattern, etc. The study also analyzes NOMA’s behavior when working with other wireless communication techniques, namely, beamforming, MIMO, cooperative connections, network, space-time coding, etc.
In [ 9 ], the authors proposed NOMA with MEC, which improves the QoS as well as reduces the latency of the 5G wireless network. This model increases the uplink NOMA by decreasing the user’s uplink energy consumption. They formulated an optimized NOMA framework that reduces the energy consumption of MEC by using computing and communication resource allocation, user clustering, and transmit powers.
In [ 10 ], the authors proposed a model which investigates outage probability under average channel state information CSI and data rate in full CSI to resolve the problem of optimal power allocation, which increase the NOMA downlink system among users. They developed simple low-complexity algorithms to provide the optimal solution. The obtained simulation results showed NOMA’s efficiency, achieving higher performance fairness compared to the TDMA configurations. It was observed from the results that NOMA, through the appropriate power amplifiers (PA), ensures the high-performance fairness requirement for the future 5G wireless communication networks.
In [ 56 ], researchers discussed that the NOMA technology and waveform modulation techniques had been used in the 5G mobile network. Therefore, this research gave a detailed survey of non-orthogonal waveform modulation techniques and NOMA schemes for next-generation mobile networks. By analyzing and comparing multiple access technologies, they considered the future evolution of these technologies for 5G mobile communication.
In [ 57 ], the authors surveyed non-orthogonal multiple access (NOMA) from the development phase to the recent developments. They have also compared NOMA techniques with traditional OMA techniques concerning information theory. The author discussed the NOMA schemes categorically as power and code domain, including the design principles, operating principles, and features. Comparison is based upon the system’s performance, spectral efficiency, and the receiver’s complexity. Also discussed are the future challenges, open issues, and their expectations of NOMA and how it will support the key requirements of 5G mobile communication systems with massive connectivity and low latency.
In [ 17 ], authors present the first review of an elementary NOMA model with two users, which clarify its central precepts. After that, a general design with multicarrier supports with a random number of users on each sub-carrier is analyzed. In performance evaluation with the existing approaches, resource sharing and multiple-input multiple-output NOMA are examined. Furthermore, they took the key elements of NOMA and its potential research demands. Finally, they reviewed the two-user SC-NOMA design and a multi-user MC-NOMA design to highlight NOMA’s basic approaches and conventions. They also present the research study about the performance examination, resource assignment, and MIMO in NOMA.
In this section, various works by different authors done on 5G NOMA technology is covered. Table 6 shows how other authors worked on the improvement of various parameters such as spectral efficiency, fairness, and computing capacity with 5G NOMA technology.
Summary of NOMA-based approaches in 5G technology.
| Approach | Spectral Efficiency | Fairness | Computing Capacity |
|---|---|---|---|
| Al-Imari et al. [ ] | Good | Good | Average |
| Islam et al. [ ] | Good | Average | Average |
| Kiani and Nsari [ ] | Average | Good | Good |
| Timotheou and Krikidis [ ] | Good | Good | Average |
| Wei et al. [ ] | Good | Average | Good |
4.3. 5G Millimeter Wave (mmWave)
Millimeter wave is an extremely high frequency band, which is very useful for 5G wireless networks. MmWave uses 30 GHz to 300 GHz spectrum band for transmission. The frequency band between 30 GHz to 300 GHz is known as mmWave because these waves have wavelengths between 1 to 10 mm. Till now radar systems and satellites are only using mmWave as these are very fast frequency bands which provide very high speed wireless communication. Many mobile network providers also started mmWave for transmitting data between base stations. Using two ways the speed of data transmission can be improved one is by increasing spectrum utilization and second is by increasing spectrum bandwidth. Out of these two approaches increasing bandwidth is quite easy and better. The frequency band below 5 GHz is very crowded as many technologies are using it so to boost up the data transmission rate 5G wireless network uses mmWave technology which instead of increasing spectrum utilization, increases the spectrum bandwidth [ 58 ]. To maximize the signal bandwidth in wireless communication the carrier frequency should also be increased by 5% because the signal bandwidth is directly proportional to carrier frequencies. The frequency band between 28 GHz to 60 GHz is very useful for 5G wireless communication as 28 GHz frequency band offers up to 1 GHz spectrum bandwidth and 60 GHz frequency band offers 2 GHz spectrum bandwidth. 4G LTE provides 2 GHz carrier frequency which offers only 100 MHz spectrum bandwidth. However, the use of mmWave increases the spectrum bandwidth 10 times, which leads to better transmission speeds [ 59 , 60 ].
Highlights of 5G mmWave are as follows:

Pictorial representation of millimeter wave.
- The 5G mmWave offer three advantages: (1) MmWave is very less used new Band, (2) MmWave signals carry more data than lower frequency wave, and (3) MmWave can be incorporated with MIMO antenna with the potential to offer a higher magnitude capacity compared to current communication systems.
In [ 11 ], the authors presented the survey of mmWave communications for 5G. The advantage of mmWave communications is adaptability, i.e., it supports the architectures and protocols up-gradation, which consists of integrated circuits, systems, etc. The authors over-viewed the present solutions and examined them concerning effectiveness, performance, and complexity. They also discussed the open research issues of mmWave communications in 5G concerning the software-defined network (SDN) architecture, network state information, efficient regulation techniques, and the heterogeneous system.
In [ 61 ], the authors present the recent work done by investigators in 5G; they discussed the design issues and demands of mmWave 5G antennas for cellular handsets. After that, they designed a small size and low-profile 60 GHz array of antenna units that contain 3D planer mesh-grid antenna elements. For the future prospect, a framework is designed in which antenna components are used to operate cellular handsets on mmWave 5G smartphones. In addition, they cross-checked the mesh-grid array of antennas with the polarized beam for upcoming hardware challenges.
In [ 12 ], the authors considered the suitability of the mmWave band for 5G cellular systems. They suggested a resource allocation system for concurrent D2D communications in mmWave 5G cellular systems, and it improves network efficiency and maintains network connectivity. This research article can serve as guidance for simulating D2D communications in mmWave 5G cellular systems. Massive mmWave BS may be set up to obtain a high delivery rate and aggregate efficiency. Therefore, many wireless users can hand off frequently between the mmWave base terminals, and it emerges the demand to search the neighbor having better network connectivity.
In [ 62 ], the authors provided a brief description of the cellular spectrum which ranges from 1 GHz to 3 GHz and is very crowed. In addition, they presented various noteworthy factors to set up mmWave communications in 5G, namely, channel characteristics regarding mmWave signal attenuation due to free space propagation, atmospheric gaseous, and rain. In addition, hybrid beamforming architecture in the mmWave technique is analyzed. They also suggested methods for the blockage effect in mmWave communications due to penetration damage. Finally, the authors have studied designing the mmWave transmission with small beams in nonorthogonal device-to-device communication.
This section covered various works done on 5G mmWave technology. The Table 7 shows how different author’s worked on the improvement of various parameters i.e., transmission rate, coverage, and cost, with 5G mmWave technology.
Summary of existing mmWave-based approaches in 5G technology.
| Approach | Transmission Rate | Coverage | Cost |
|---|---|---|---|
| Hong et al. [ ] | Average | Average | Low |
| Qiao et al. [ ] | Average | Good | Average |
| Wei et al. [ ] | Good | Average | Low |
4.4. 5G IoT Based Approaches
The 5G mobile network plays a big role in developing the Internet of Things (IoT). IoT will connect lots of things with the internet like appliances, sensors, devices, objects, and applications. These applications will collect lots of data from different devices and sensors. 5G will provide very high speed internet connectivity for data collection, transmission, control, and processing. 5G is a flexible network with unused spectrum availability and it offers very low cost deployment that is why it is the most efficient technology for IoT [ 63 ]. In many areas, 5G provides benefits to IoT, and below are some examples:
Smart homes: smart home appliances and products are in demand these days. The 5G network makes smart homes more real as it offers high speed connectivity and monitoring of smart appliances. Smart home appliances are easily accessed and configured from remote locations using the 5G network, as it offers very high speed low latency communication.
Smart cities: 5G wireless network also helps in developing smart cities applications such as automatic traffic management, weather update, local area broadcasting, energy saving, efficient power supply, smart lighting system, water resource management, crowd management, emergency control, etc.
Industrial IoT: 5G wireless technology will provide lots of features for future industries such as safety, process tracking, smart packing, shipping, energy efficiency, automation of equipment, predictive maintenance and logistics. 5G smart sensor technology also offers smarter, safer, cost effective, and energy-saving industrial operation for industrial IoT.
Smart Farming: 5G technology will play a crucial role for agriculture and smart farming. 5G sensors and GPS technology will help farmers to track live attacks on crops and manage them quickly. These smart sensors can also be used for irrigation control, pest control, insect control, and electricity control.
Autonomous Driving: 5G wireless network offers very low latency high speed communication which is very significant for autonomous driving. It means self-driving cars will come to real life soon with 5G wireless networks. Using 5G autonomous cars can easily communicate with smart traffic signs, objects and other vehicles running on the road. 5G’s low latency feature makes self-driving more real as every millisecond is important for autonomous vehicles, decision taking is performed in microseconds to avoid accidents [ 64 ].
Highlights of 5G IoT are as follows:

Pictorial representation of IoT with 5G.
- 5G with IoT is a new feature of next-generation mobile communication, which provides a high-speed internet connection between moderated devices. 5G IoT also offers smart homes, smart devices, sensors, smart transportation systems, smart industries, etc., for end-users to make them smarter.
- IoT deals with moderate devices which connect through the internet. The approach of the IoT has made the consideration of the research associated with the outcome of providing wearable, smart-phones, sensors, smart transportation systems, smart devices, washing machines, tablets, etc., and these diverse systems are associated to a common interface with the intelligence to connect.
- Significant IoT applications include private healthcare systems, traffic management, industrial management, and tactile internet, etc.
Plenty of approaches is devised to address the issues of IoT [ 14 , 65 , 66 ].
In [ 65 ], the paper focuses on 5G mobile systems due to the emerging trends and developing technologies, which results in the exponential traffic growth in IoT. The author surveyed the challenges and demands during deployment of the massive IoT applications with the main focus on mobile networking. The author reviewed the features of standard IoT infrastructure, along with the cellular-based, low-power wide-area technologies (LPWA) such as eMTC, extended coverage (EC)-GSM-IoT, as well as noncellular, low-power wide-area (LPWA) technologies such as SigFox, LoRa etc.
In [ 14 ], the authors presented how 5G technology copes with the various issues of IoT today. It provides a brief review of existing and forming 5G architectures. The survey indicates the role of 5G in the foundation of the IoT ecosystem. IoT and 5G can easily combine with improved wireless technologies to set up the same ecosystem that can fulfill the current requirement for IoT devices. 5G can alter nature and will help to expand the development of IoT devices. As the process of 5G unfolds, global associations will find essentials for setting up a cross-industry engagement in determining and enlarging the 5G system.
In [ 66 ], the author introduced an IoT authentication scheme in a 5G network, with more excellent reliability and dynamic. The scheme proposed a privacy-protected procedure for selecting slices; it provided an additional fog node for proper data transmission and service types of the subscribers, along with service-oriented authentication and key understanding to maintain the secrecy, precision of users, and confidentiality of service factors. Users anonymously identify the IoT servers and develop a vital channel for service accessibility and data cached on local fog nodes and remote IoT servers. The author performed a simulation to manifest the security and privacy preservation of the user over the network.
This section covered various works done on 5G IoT by multiple authors. Table 8 shows how different author’s worked on the improvement of numerous parameters, i.e., data rate, security requirement, and performance with 5G IoT.
Summary of IoT-based approaches in 5G technology.
| Approach | Data Rate | Security Requirement | Performance |
|---|---|---|---|
| Akpakwu et al. [ ] | Good | Average | Good |
| Khurpade et al. [ ] | Average | - | Average |
| Ni et al. [ ] | Good | Average | Average |
4.5. Machine Learning Techniques for 5G
Various machine learning (ML) techniques were applied in 5G networks and mobile communication. It provides a solution to multiple complex problems, which requires a lot of hand-tuning. ML techniques can be broadly classified as supervised, unsupervised, and reinforcement learning. Let’s discuss each learning technique separately and where it impacts the 5G network.
Supervised Learning, where user works with labeled data; some 5G network problems can be further categorized as classification and regression problems. Some regression problems such as scheduling nodes in 5G and energy availability can be predicted using Linear Regression (LR) algorithm. To accurately predict the bandwidth and frequency allocation Statistical Logistic Regression (SLR) is applied. Some supervised classifiers are applied to predict the network demand and allocate network resources based on the connectivity performance; it signifies the topology setup and bit rates. Support Vector Machine (SVM) and NN-based approximation algorithms are used for channel learning based on observable channel state information. Deep Neural Network (DNN) is also employed to extract solutions for predicting beamforming vectors at the BS’s by taking mapping functions and uplink pilot signals into considerations.
In unsupervised Learning, where the user works with unlabeled data, various clustering techniques are applied to enhance network performance and connectivity without interruptions. K-means clustering reduces the data travel by storing data centers content into clusters. It optimizes the handover estimation based on mobility pattern and selection of relay nodes in the V2V network. Hierarchical clustering reduces network failure by detecting the intrusion in the mobile wireless network; unsupervised soft clustering helps in reducing latency by clustering fog nodes. The nonparametric Bayesian unsupervised learning technique reduces traffic in the network by actively serving the user’s requests and demands. Other unsupervised learning techniques such as Adversarial Auto Encoders (AAE) and Affinity Propagation Clustering techniques detect irregular behavior in the wireless spectrum and manage resources for ultradense small cells, respectively.
In case of an uncertain environment in the 5G wireless network, reinforcement learning (RL) techniques are employed to solve some problems. Actor-critic reinforcement learning is used for user scheduling and resource allocation in the network. Markov decision process (MDP) and Partially Observable MDP (POMDP) is used for Quality of Experience (QoE)-based handover decision-making for Hetnets. Controls packet call admission in HetNets and channel access process for secondary users in a Cognitive Radio Network (CRN). Deep RL is applied to decide the communication channel and mobility and speeds up the secondary user’s learning rate using an antijamming strategy. Deep RL is employed in various 5G network application parameters such as resource allocation and security [ 67 ]. Table 9 shows the state-of-the-art ML-based solution for 5G network.
The state-of-the-art ML-based solution for 5G network.
| Author References | Key Contribution | ML Applied | Network Participants Component | 5G Network Application Parameter | |||||
|---|---|---|---|---|---|---|---|---|---|
| Alave et al. [ ] | Network traffic prediction | LSTM and DNN | ✓ | ✓ | * | ✓ | ✓ | ✓ | X |
| Bega et al. [ ] | Network slice admission control algorithm | Machine Learning and Deep Learing | ✓ | X | X | ✓ | ✓ | ✓ | X |
| Suomalainen et al. [ ] | 5G Security | Machine Learning | X | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Bashir et al. [ ] | Resource Allocation | Machine Learning | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | X |
| Balevi et al. [ ] | Low Latency communication | Unsupervised clustering | X | ✓ | X | ✓ | ✓ | ✓ | X |
| Tayyaba et al. [ ] | Resource Management | LSTM, CNN, and DNN | ✓ | ✓ | X | ✓ | ✓ | ✓ | ✓ |
| Sim et al. [ ] | 5G mmWave Vehicular communication | FML (Fast machine Learning) | X | ✓ | * | ✓ | ✓ | ✓ | X |
| Li et al. [ ] | Intrusion Detection System | Machine Learning | X | ✓ | X | ✓ | ✓ | ✓ | ✓ |
| Kafle et al. [ ] | 5G Network Slicing | Machine Learning | X | ✓ | X | ✓ | ✓ | ✓ | ✓ |
| Chen et al. [ ] | Physical-Layer Channel Authentication | Machine Learning | X | ✓ | X | X | X | X | ✓ |
| Sevgican et al. [ ] | Intelligent Network Data Analytics Function in 5G | Machine Learning | ✓ | X | ✓ | X | X | * | * |
| Abidi et al. [ ] | Optimal 5G network slicing | Machine Learning and Deep Learing | X | ✓ | X | ✓ | ✓ | ✓ | * |
Highlights of machine learning techniques for 5G are as follows:

Pictorial representation of machine learning (ML) in 5G.
- In ML, a model will be defined which fulfills the desired requirements through which desired results are obtained. In the later stage, it examines accuracy from obtained results.
- ML plays a vital role in 5G network analysis for threat detection, network load prediction, final arrangement, and network formation. Searching for a better balance between power, length of antennas, area, and network thickness crossed with the spontaneous use of services in the universe of individual users and types of devices.
In [ 79 ], author’s firstly describes the demands for the traditional authentication procedures and benefits of intelligent authentication. The intelligent authentication method was established to improve security practice in 5G-and-beyond wireless communication systems. Thereafter, the machine learning paradigms for intelligent authentication were organized into parametric and non-parametric research methods, as well as supervised, unsupervised, and reinforcement learning approaches. As a outcome, machine learning techniques provide a new paradigm into authentication under diverse network conditions and unstable dynamics. In addition, prompt intelligence to the security management to obtain cost-effective, better reliable, model-free, continuous, and situation-aware authentication.
In [ 68 ], the authors proposed a machine learning-based model to predict the traffic load at a particular location. They used a mobile network traffic dataset to train a model that can calculate the total number of user requests at a time. To launch access and mobility management function (AMF) instances according to the requirement as there were no predictions of user request the performance automatically degrade as AMF does not handle these requests at a time. Earlier threshold-based techniques were used to predict the traffic load, but that approach took too much time; therefore, the authors proposed RNN algorithm-based ML to predict the traffic load, which gives efficient results.
In [ 15 ], authors discussed the issue of network slice admission, resource allocation among subscribers, and how to maximize the profit of infrastructure providers. The author proposed a network slice admission control algorithm based on SMDP (decision-making process) that guarantees the subscribers’ best acceptance policies and satisfiability (tenants). They also suggested novel N3AC, a neural network-based algorithm that optimizes performance under various configurations, significantly outperforms practical and straightforward approaches.
This section includes various works done on 5G ML by different authors. Table 10 shows the state-of-the-art work on the improvement of various parameters such as energy efficiency, Quality of Services (QoS), and latency with 5G ML.
The state-of-the-art ML-based approaches in 5G technology.
| Approach | Energy Efficiency | Quality of Services (QoS) | Latency |
|---|---|---|---|
| Fang et al. [ ] | Good | Good | Average |
| Alawe et al. [ ] | Good | Average | Low |
| Bega et al. [ ] | - | Good | Average |
4.6. Optimization Techniques for 5G
Optimization techniques may be applied to capture NP-Complete or NP-Hard problems in 5G technology. This section briefly describes various research works suggested for 5G technology based on optimization techniques.
In [ 80 ], Massive MIMO technology is used in 5G mobile network to make it more flexible and scalable. The MIMO implementation in 5G needs a significant number of radio frequencies is required in the RF circuit that increases the cost and energy consumption of the 5G network. This paper provides a solution that increases the cost efficiency and energy efficiency with many radio frequency chains for a 5G wireless communication network. They give an optimized energy efficient technique for MIMO antenna and mmWave technologies based 5G mobile communication network. The proposed Energy Efficient Hybrid Precoding (EEHP) algorithm to increase the energy efficiency for the 5G wireless network. This algorithm minimizes the cost of an RF circuit with a large number of RF chains.
In [ 16 ], authors have discussed the growing demand for energy efficiency in the next-generation networks. In the last decade, they have figured out the things in wireless transmissions, which proved a change towards pursuing green communication for the next generation system. The importance of adopting the correct EE metric was also reviewed. Further, they worked through the different approaches that can be applied in the future for increasing the network’s energy and posed a summary of the work that was completed previously to enhance the energy productivity of the network using these capabilities. A system design for EE development using relay selection was also characterized, along with an observation of distinct algorithms applied for EE in relay-based ecosystems.
In [ 81 ], authors presented how AI-based approach is used to the setup of Self Organizing Network (SON) functionalities for radio access network (RAN) design and optimization. They used a machine learning approach to predict the results for 5G SON functionalities. Firstly, the input was taken from various sources; then, prediction and clustering-based machine learning models were applied to produce the results. Multiple AI-based devices were used to extract the knowledge analysis to execute SON functionalities smoothly. Based on results, they tested how self-optimization, self-testing, and self-designing are done for SON. The author also describes how the proposed mechanism classifies in different orders.
In [ 82 ], investigators examined the working of OFDM in various channel environments. They also figured out the changes in frame duration of the 5G TDD frame design. Subcarrier spacing is beneficial to obtain a small frame length with control overhead. They provided various techniques to reduce the growing guard period (GP) and cyclic prefix (CP) like complete utilization of multiple subcarrier spacing, management and data parts of frame at receiver end, various uses of timing advance (TA) or total control of flexible CP size.
This section includes various works that were done on 5G optimization by different authors. Table 11 shows how other authors worked on the improvement of multiple parameters such as energy efficiency, power optimization, and latency with 5G optimization.
Summary of Optimization Based Approaches in 5G Technology.
| Approach | Energy Efficiency | Power Optimization | Latency |
|---|---|---|---|
| Zi et al. [ ] | Good | - | Average |
| Abrol and jha [ ] | Good | Good | - |
| Pérez-Romero et al. [ ] | - | Average | Average |
| Lähetkangas et al. [ ] | Average | - | Low |
5. Description of Novel 5G Features over 4G
This section presents descriptions of various novel features of 5G, namely, the concept of small cell, beamforming, and MEC.
5.1. Small Cell
Small cells are low-powered cellular radio access nodes which work in the range of 10 meters to a few kilometers. Small cells play a very important role in implementation of the 5G wireless network. Small cells are low power base stations which cover small areas. Small cells are quite similar with all the previous cells used in various wireless networks. However, these cells have some advantages like they can work with low power and they are also capable of working with high data rates. Small cells help in rollout of 5G network with ultra high speed and low latency communication. Small cells in the 5G network use some new technologies like MIMO, beamforming, and mmWave for high speed data transmission. The design of small cells hardware is very simple so its implementation is quite easier and faster. There are three types of small cell tower available in the market. Femtocells, picocells, and microcells [ 83 ]. As shown in the Table 12 .
Types of Small cells.
| Types of Small Cell | Coverage Radius | Indoor Outdoor | Transmit Power | Number of Users | Backhaul Type | Cost |
|---|---|---|---|---|---|---|
| Femtocells | 30–165 ft 10–50 m | Indoor | 100 mW 20 dBm | 8–16 | Wired, fiber | Low |
| Picocells | 330–820 ft 100–250 m | Indoor Outdoor | 250 mW 24 dBm | 32–64 | Wired, fiber | Low |
| Microcells | 1600–8000 ft 500–250 m | Outdoor | 2000–500 mW 32–37 dBm | 200 | Wired, fiber, Microwave | Medium |
MmWave is a very high band spectrum between 30 to 300 GHz. As it is a significantly less used spectrum, it provides very high-speed wireless communication. MmWave offers ultra-wide bandwidth for next-generation mobile networks. MmWave has lots of advantages, but it has some disadvantages, too, such as mmWave signals are very high-frequency signals, so they have more collision with obstacles in the air which cause the signals loses energy quickly. Buildings and trees also block MmWave signals, so these signals cover a shorter distance. To resolve these issues, multiple small cell stations are installed to cover the gap between end-user and base station [ 18 ]. Small cell covers a very shorter range, so the installation of a small cell depends on the population of a particular area. Generally, in a populated place, the distance between each small cell varies from 10 to 90 meters. In the survey [ 20 ], various authors implemented small cells with massive MIMO simultaneously. They also reviewed multiple technologies used in 5G like beamforming, small cell, massive MIMO, NOMA, device to device (D2D) communication. Various problems like interference management, spectral efficiency, resource management, energy efficiency, and backhauling are discussed. The author also gave a detailed presentation of all the issues occurring while implementing small cells with various 5G technologies. As shown in the Figure 7 , mmWave has a higher range, so it can be easily blocked by the obstacles as shown in Figure 7 a. This is one of the key concerns of millimeter-wave signal transmission. To solve this issue, the small cell can be placed at a short distance to transmit the signals easily, as shown in Figure 7 b.

Pictorial representation of communication with and without small cells.
5.2. Beamforming
Beamforming is a key technology of wireless networks which transmits the signals in a directional manner. 5G beamforming making a strong wireless connection toward a receiving end. In conventional systems when small cells are not using beamforming, moving signals to particular areas is quite difficult. Beamforming counter this issue using beamforming small cells are able to transmit the signals in particular direction towards a device like mobile phone, laptops, autonomous vehicle and IoT devices. Beamforming is improving the efficiency and saves the energy of the 5G network. Beamforming is broadly divided into three categories: Digital beamforming, analog beamforming and hybrid beamforming. Digital beamforming: multiuser MIMO is equal to digital beamforming which is mainly used in LTE Advanced Pro and in 5G NR. In digital beamforming the same frequency or time resources can be used to transmit the data to multiple users at the same time which improves the cell capacity of wireless networks. Analog Beamforming: In mmWave frequency range 5G NR analog beamforming is a very important approach which improves the coverage. In digital beamforming there are chances of high pathloss in mmWave as only one beam per set of antenna is formed. While the analog beamforming saves high pathloss in mmWave. Hybrid beamforming: hybrid beamforming is a combination of both analog beamforming and digital beamforming. In the implementation of MmWave in 5G network hybrid beamforming will be used [ 84 ].
Wireless signals in the 4G network are spreading in large areas, and nature is not Omnidirectional. Thus, energy depletes rapidly, and users who are accessing these signals also face interference problems. The beamforming technique is used in the 5G network to resolve this issue. In beamforming signals are directional. They move like a laser beam from the base station to the user, so signals seem to be traveling in an invisible cable. Beamforming helps achieve a faster data rate; as the signals are directional, it leads to less energy consumption and less interference. In [ 21 ], investigators evolve some techniques which reduce interference and increase system efficiency of the 5G mobile network. In this survey article, the authors covered various challenges faced while designing an optimized beamforming algorithm. Mainly focused on different design parameters such as performance evaluation and power consumption. In addition, they also described various issues related to beamforming like CSI, computation complexity, and antenna correlation. They also covered various research to cover how beamforming helps implement MIMO in next-generation mobile networks [ 85 ]. Figure 8 shows the pictorial representation of communication with and without using beamforming.

Pictorial Representation of communication with and without using beamforming.
5.3. Mobile Edge Computing
Mobile Edge Computing (MEC) [ 24 ]: MEC is an extended version of cloud computing that brings cloud resources closer to the end-user. When we talk about computing, the very first thing that comes to our mind is cloud computing. Cloud computing is a very famous technology that offers many services to end-user. Still, cloud computing has many drawbacks. The services available in the cloud are too far from end-users that create latency, and cloud user needs to download the complete application before use, which also increases the burden to the device [ 86 ]. MEC creates an edge between the end-user and cloud server, bringing cloud computing closer to the end-user. Now, all the services, namely, video conferencing, virtual software, etc., are offered by this edge that improves cloud computing performance. Another essential feature of MEC is that the application is split into two parts, which, first one is available at cloud server, and the second is at the user’s device. Therefore, the user need not download the complete application on his device that increases the performance of the end user’s device. Furthermore, MEC provides cloud services at very low latency and less bandwidth. In [ 23 , 87 ], the author’s investigation proved that successful deployment of MEC in 5G network increases the overall performance of 5G architecture. Graphical differentiation between cloud computing and mobile edge computing is presented in Figure 9 .

Pictorial representation of cloud computing vs. mobile edge computing.
6. 5G Security
Security is the key feature in the telecommunication network industry, which is necessary at various layers, to handle 5G network security in applications such as IoT, Digital forensics, IDS and many more [ 88 , 89 ]. The authors [ 90 ], discussed the background of 5G and its security concerns, challenges and future directions. The author also introduced the blockchain technology that can be incorporated with the IoT to overcome the challenges in IoT. The paper aims to create a security framework which can be incorporated with the LTE advanced network, and effective in terms of cost, deployment and QoS. In [ 91 ], author surveyed various form of attacks, the security challenges, security solutions with respect to the affected technology such as SDN, Network function virtualization (NFV), Mobile Clouds and MEC, and security standardizations of 5G, i.e., 3GPP, 5GPPP, Internet Engineering Task Force (IETF), Next Generation Mobile Networks (NGMN), European Telecommunications Standards Institute (ETSI). In [ 92 ], author elaborated various technological aspects, security issues and their existing solutions and also mentioned the new emerging technological paradigms for 5G security such as blockchain, quantum cryptography, AI, SDN, CPS, MEC, D2D. The author aims to create new security frameworks for 5G for further use of this technology in development of smart cities, transportation and healthcare. In [ 93 ], author analyzed the threats and dark threat, security aspects concerned with SDN and NFV, also their Commercial & Industrial Security Corporation (CISCO) 5G vision and new security innovations with respect to the new evolving architectures of 5G [ 94 ].
AuthenticationThe identification of the user in any network is made with the help of authentication. The different mobile network generations from 1G to 5G have used multiple techniques for user authentication. 5G utilizes the 5G Authentication and Key Agreement (AKA) authentication method, which shares a cryptographic key between user equipment (UE) and its home network and establishes a mutual authentication process between the both [ 95 ].
Access Control To restrict the accessibility in the network, 5G supports access control mechanisms to provide a secure and safe environment to the users and is controlled by network providers. 5G uses simple public key infrastructure (PKI) certificates for authenticating access in the 5G network. PKI put forward a secure and dynamic environment for the 5G network. The simple PKI technique provides flexibility to the 5G network; it can scale up and scale down as per the user traffic in the network [ 96 , 97 ].
Communication Security 5G deals to provide high data bandwidth, low latency, and better signal coverage. Therefore secure communication is the key concern in the 5G network. UE, mobile operators, core network, and access networks are the main focal point for the attackers in 5G communication. Some of the common attacks in communication at various segments are Botnet, message insertion, micro-cell, distributed denial of service (DDoS), and transport layer security (TLS)/secure sockets layer (SSL) attacks [ 98 , 99 ].
Encryption The confidentiality of the user and the network is done using encryption techniques. As 5G offers multiple services, end-to-end (E2E) encryption is the most suitable technique applied over various segments in the 5G network. Encryption forbids unauthorized access to the network and maintains the data privacy of the user. To encrypt the radio traffic at Packet Data Convergence Protocol (PDCP) layer, three 128-bits keys are applied at the user plane, nonaccess stratum (NAS), and access stratum (AS) [ 100 ].
7. Summary of 5G Technology Based on Above-Stated Challenges
In this section, various issues addressed by investigators in 5G technologies are presented in Table 13 . In addition, different parameters are considered, such as throughput, latency, energy efficiency, data rate, spectral efficiency, fairness & computing capacity, transmission rate, coverage, cost, security requirement, performance, QoS, power optimization, etc., indexed from R1 to R14.
Summary of 5G Technology above stated challenges (R1:Throughput, R2:Latency, R3:Energy Efficiency, R4:Data Rate, R5:Spectral efficiency, R6:Fairness & Computing Capacity, R7:Transmission Rate, R8:Coverage, R9:Cost, R10:Security requirement, R11:Performance, R12:Quality of Services (QoS), R13:Power Optimization).
| Approach | R1 | R2 | R3 | R4 | R5 | R6 | R7 | R8 | R9 | R10 | R11 | R12 | R13 | R14 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Panzner et al. [ ] | Good | Low | Good | - | Avg | - | - | - | - | - | - | - | - | - |
| Qiao et al. [ ] | - | - | - | - | - | - | - | Avg | Good | Avg | - | - | - | - |
| He et al. [ ] | Avg | Low | Avg | - | - | - | - | - | - | - | - | - | - | - |
| Abrol and jha [ ] | - | - | Good | - | - | - | - | - | - | - | - | - | - | Good |
| Al-Imari et al. [ ] | - | - | - | - | Good | Good | Avg | - | - | - | - | - | - | - |
| Papadopoulos et al. [ ] | Good | Low | Avg | - | Avg | - | - | - | - | - | - | - | - | - |
| Kiani and Nsari [ ] | - | - | - | - | Avg | Good | Good | - | - | - | - | - | - | - |
| Beck [ ] | - | Low | - | - | - | - | - | Avg | - | - | - | Good | - | Avg |
| Ni et al. [ ] | - | - | - | Good | - | - | - | - | - | - | Avg | Avg | - | - |
| Elijah [ ] | Avg | Low | Avg | - | - | - | - | - | - | - | - | - | - | - |
| Alawe et al. [ ] | - | Low | Good | - | - | - | - | - | - | - | - | - | Avg | - |
| Zhou et al. [ ] | Avg | - | Good | - | Avg | - | - | - | - | - | - | - | - | - |
| Islam et al. [ ] | - | - | - | - | Good | Avg | Avg | - | - | - | - | - | - | - |
| Bega et al. [ ] | - | Avg | - | - | - | - | - | - | - | - | - | - | Good | - |
| Akpakwu et al. [ ] | - | - | - | Good | - | - | - | - | - | - | Avg | Good | - | - |
| Wei et al. [ ] | - | - | - | - | - | - | - | Good | Avg | Low | - | - | - | - |
| Khurpade et al. [ ] | - | - | - | Avg | - | - | - | - | - | - | - | Avg | - | - |
| Timotheou and Krikidis [ ] | - | - | - | - | Good | Good | Avg | - | - | - | - | - | - | - |
| Wang [ ] | Avg | Low | Avg | Avg | - | - | - | - | - | - | - | - | - | - |
| Akhil Gupta & R. K. Jha [ ] | - | - | Good | Avg | Good | - | - | - | - | - | - | Good | Good | - |
| Pérez-Romero et al. [ ] | - | - | Avg | - | - | - | - | - | - | - | - | - | - | Avg |
| Pi [ ] | - | - | - | - | - | - | - | Good | Good | Avg | - | - | - | - |
| Zi et al. [ ] | - | Avg | Good | - | - | - | - | - | - | - | - | - | - | - |
| Chin [ ] | - | - | Good | Avg | - | - | - | - | - | Avg | - | Good | - | - |
| Mamta Agiwal [ ] | - | Avg | - | Good | - | - | - | - | - | - | Good | Avg | - | - |
| Ramesh et al. [ ] | Good | Avg | Good | - | Good | - | - | - | - | - | - | - | - | - |
| Niu [ ] | - | - | - | - | - | - | - | Good | Avg | Avg | - | - | - | |
| Fang et al. [ ] | - | Avg | Good | - | - | - | - | - | - | - | - | - | Good | - |
| Hoydis [ ] | - | - | Good | - | Good | - | - | - | - | Avg | - | Good | - | - |
| Wei et al. [ ] | - | - | - | - | Good | Avg | Good | - | - | - | - | - | - | - |
| Hong et al. [ ] | - | - | - | - | - | - | - | - | Avg | Avg | Low | - | - | - |
| Rashid [ ] | - | - | - | Good | - | - | - | Good | - | - | - | Avg | - | Good |
| Prasad et al. [ ] | Good | - | Good | - | Avg | - | - | - | - | - | - | - | - | - |
| Lähetkangas et al. [ ] | - | Low | Av | - | - | - | - | - | - | - | - | - | - | - |
8. Conclusions
This survey article illustrates the emergence of 5G, its evolution from 1G to 5G mobile network, applications, different research groups, their work, and the key features of 5G. It is not just a mobile broadband network, different from all the previous mobile network generations; it offers services like IoT, V2X, and Industry 4.0. This paper covers a detailed survey from multiple authors on different technologies in 5G, such as massive MIMO, Non-Orthogonal Multiple Access (NOMA), millimeter wave, small cell, MEC (Mobile Edge Computing), beamforming, optimization, and machine learning in 5G. After each section, a tabular comparison covers all the state-of-the-research held in these technologies. This survey also shows the importance of these newly added technologies and building a flexible, scalable, and reliable 5G network.
9. Future Findings
This article covers a detailed survey on the 5G mobile network and its features. These features make 5G more reliable, scalable, efficient at affordable rates. As discussed in the above sections, numerous technical challenges originate while implementing those features or providing services over a 5G mobile network. So, for future research directions, the research community can overcome these challenges while implementing these technologies (MIMO, NOMA, small cell, mmWave, beam-forming, MEC) over a 5G network. 5G communication will bring new improvements over the existing systems. Still, the current solutions cannot fulfill the autonomous system and future intelligence engineering requirements after a decade. There is no matter of discussion that 5G will provide better QoS and new features than 4G. But there is always room for improvement as the considerable growth of centralized data and autonomous industry 5G wireless networks will not be capable of fulfilling their demands in the future. So, we need to move on new wireless network technology that is named 6G. 6G wireless network will bring new heights in mobile generations, as it includes (i) massive human-to-machine communication, (ii) ubiquitous connectivity between the local device and cloud server, (iii) creation of data fusion technology for various mixed reality experiences and multiverps maps. (iv) Focus on sensing and actuation to control the network of the entire world. The 6G mobile network will offer new services with some other technologies; these services are 3D mapping, reality devices, smart homes, smart wearable, autonomous vehicles, artificial intelligence, and sense. It is expected that 6G will provide ultra-long-range communication with a very low latency of 1 ms. The per-user bit rate in a 6G wireless network will be approximately 1 Tbps, and it will also provide wireless communication, which is 1000 times faster than 5G networks.
Acknowledgments
Author contributions.
Conceptualization: R.D., I.Y., G.C., P.L. data gathering: R.D., G.C., P.L, I.Y. funding acquisition: I.Y. investigation: I.Y., G.C., G.P. methodology: R.D., I.Y., G.C., P.L., G.P., survey: I.Y., G.C., P.L, G.P., R.D. supervision: G.C., I.Y., G.P. validation: I.Y., G.P. visualization: R.D., I.Y., G.C., P.L. writing, original draft: R.D., I.Y., G.C., P.L., G.P. writing, review, and editing: I.Y., G.C., G.P. All authors have read and agreed to the published version of the manuscript.
This paper was supported by Soonchunhyang University.
Institutional Review Board Statement
Informed consent statement, data availability statement, conflicts of interest.
The authors declare no conflict of interest.
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
- Skip to primary navigation
- Skip to main content
- Skip to primary sidebar
- Skip to footer
Don't Miss a Post! Subscribe
- Guest Posts

- Educational AI
- Edtech Tools
- Edtech Apps
- Teacher Resources
- Special Education
- Edtech for Kids
- Buying Guides for Teachers

Educators Technology
Innovative EdTech for teachers, educators, parents, and students
4 Good AI Academic Search Engines
By Med Kharbach, PhD | Last Update: August 1, 2024
Since the launch of ChatGPT in late 2022, generative AI has taken center stage in technological innovation. This transformative technology is making steady inroads into all aspects of our lives, including education. We’ve witnessed a proliferation of AI tools enhancing both teaching and learning. Even established edtech platforms like Khan Academy, Kahoot, and Quizlet have embraced the AI revolution, integrating it into their systems. In essence, AI, and more specifically generative AI, is reshaping education in unprecedented ways.
As this generative AI revolution unfolded, I shifted the focus of my academic research to this emerging technology, becoming deeply interested in its educational potential. To this end, I authored a book titled “ ChatGPT for Teachers ,” which explains the fundamentals of generative AI, outlines practical prompting strategies for educators, and discusses the limitations of AI, especially within educational settings.
Currently, I’m working on another book that explores the use of AI in academic research. This post draws insights from this ongoing work. Today, I aim to share a collection of AI-powered academic search engines that will enable you to find research papers and journal articles with unprecedented ease. I often find myself wishing these tools had been available during my doctoral studies; they could have saved me considerable time and effort.

While these AI academic search engines are valuable at any stage of research, I find them particularly helpful in conducting literature reviews, which typically involve extensive exploration of existing scholarship. Using these AI tools will allow you to access relevant research materials more efficiently and organize your papers more effectively. You can also combine these with the PDF Chat Tools I covered in an earlier post to further streamline your research process.
AI Academic Search Engines
These AI-powered search engines are most beneficial during the initial stages of research, where you’re engaging in extensive literature review. They enable quicker access to relevant research materials and more efficient organization of papers. For an even more streamlined research process, consider combining these tools with the PDF Chat Tools I discussed in a previous post.
1. Semantic Scholar
Semantic Scholar is an AI-powered search engine for over 214 million scientific publications across all disciplines. It allows refined searches using filters such as journals, conferences, authors, publication formats, and date ranges. Results can be sorted by recency, relevance, or citation count. One standout feature is the “highly influential citations,” which identifies publications with significant impact based on a machine-learning model analyzing citations. Other features include saving papers to your library, creating author alerts for recent publications, and setting up topic alerts for new papers.
I’ve used Semantic Scholar for years, and the platform has integrated several AI features to enhance functionality. These include TLDR, which provides concise summaries for papers, and AI-powered paper recommendations based on your library. You can also explore topics with AI-generated definitions and related papers. The “Ask This Paper” feature lets you interact with a paper’s content by asking specific questions, and the Semantic Reader facilitates reading by offering citation cards, TLDR summaries, and a table of contents to help navigate between sections.
2. Consensus
Consensus is an AI-powered academic search engine that helps you quickly find relevant research papers. Simply input your research questions and enable the ‘Synthesize’ toggle. Consensus then synthesizes insights from a vast pool of academic papers and presents results in a user-friendly format, with each tile representing a single paper. Each tile includes information about the journal, authors, and citations, along with a grey box containing key insights from the paper or answers to your questions.
The ‘Study Snapshot’ is one of my favourite features. It provides an AI-generated summary of the paper’s population, sample size, methods, and outcomes. Clicking on the paper title reveals detailed information, including references, links to full texts, and quality metrics. Consensus also offers powerful research filters to refine searches by sample size, study design, methodology, and more, and includes paper quality indicators to assess credibility. This helps streamline the literature review process by extracting main insights and citing sources, allowing you to explore relevant literature and expand your research efficiently.
Elicit is an AI-powered academic search engine ideal for preparing literature reviews. Simply input your question, and Elicit synthesizes insights from relevant papers, providing titles, authors, journals, citations, summaries, and external links for further exploration. You can refine your search with filters such as publication year, journal quality, study type, PDF availability, and more. For example, using the ‘Abstract Keywords’ filter, Elicit returns papers with abstracts containing your specified keywords. Additionally, you can filter papers using over 30 predefined columns or create custom ones.
Elicit offers a library service to save and organize papers and a notebook feature to capture thoughts and highlights. You can upload PDFs to extract insights, aiding in reading papers. An interesting feature is the ‘List of Concepts,’ which allows you to search for related concepts across different papers. This helps you learn more about your research topic and discover new research avenues. Elicit excels at citing sources and provides comprehensive information to streamline your literature review process.
4. R Discovery
R Discovery is an AI tool designed to assist with academic research, making it easy to find relevant papers. Start by creating an account and customizing your feed by selecting your research area and adding topics or journals. This will generate a feed of research papers tailored to your interests. Each paper in the feed includes details like the abstract, DOI link, options to export to Zotero or Mendeley, an audio version, translation, and more. The ‘Similar Papers’ feature is particularly useful, providing an AI-curated collection of papers on the same topic, helping you discover relevant materials to enrich your research.
R Discovery also features a custom GPT called Ask GPT, allowing real-time interaction with the R Discovery bot inside ChatGPT. You can ask questions, and Ask GPT will fetch and synthesize answers from its extensive database of scientific and academic papers, providing a seamless way to enhance your literature review process.
Final thoughts
I hope you have found these tools helpful in navigating your academic research. Each of these AI-powered search engines can significantly streamline your literature review process, saving you time and effort. Stay tuned for my upcoming book on AI tools for academic research, which will be a treasure trove of resources and insights to enhance your research journey. From detailed guides to practical tips, this book will provide everything you need to leverage AI effectively in your academic work.

Join our mailing list
Never miss an EdTech beat! Subscribe now for exclusive insights and resources .

Meet Med Kharbach, PhD
Dr. Med Kharbach is an influential voice in the global educational technology landscape, with an extensive background in educational studies and a decade-long experience as a K-12 teacher. Holding a Ph.D. from Mount Saint Vincent University in Halifax, Canada, he brings a unique perspective to the educational world by integrating his profound academic knowledge with his hands-on teaching experience. Dr. Kharbach's academic pursuits encompass curriculum studies, discourse analysis, language learning/teaching, language and identity, emerging literacies, educational technology, and research methodologies. His work has been presented at numerous national and international conferences and published in various esteemed academic journals.

Join our email list for exclusive EdTech content.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 26 July 2024
Adaptive hierarchical origami-based metastructures
- Yanbin Li ORCID: orcid.org/0000-0003-0870-4507 1 na1 ,
- Antonio Di Lallo 1 na1 ,
- Junxi Zhu 1 ,
- Yinding Chi 1 ,
- Hao Su ORCID: orcid.org/0000-0003-3299-7418 1 , 2 , 3 &
- Jie Yin ORCID: orcid.org/0000-0002-6297-1262 1
Nature Communications volume 15 , Article number: 6247 ( 2024 ) Cite this article
2538 Accesses
191 Altmetric
Metrics details
- Applied mathematics
- Mechanical engineering
Shape-morphing capabilities are crucial for enabling multifunctionality in both biological and artificial systems. Various strategies for shape morphing have been proposed for applications in metamaterials and robotics. However, few of these approaches have achieved the ability to seamlessly transform into a multitude of volumetric shapes post-fabrication using a relatively simple actuation and control mechanism. Taking inspiration from thick origami and hierarchies in nature, we present a hierarchical construction method based on polyhedrons to create an extensive library of compact origami metastructures. We show that a single hierarchical origami structure can autonomously adapt to over 10 3 versatile architectural configurations, achieved with the utilization of fewer than 3 actuation degrees of freedom and employing simple transition kinematics. We uncover the fundamental principles governing theses shape transformation through theoretical models. Furthermore, we also demonstrate the wide-ranging potential applications of these transformable hierarchical structures. These include their uses as untethered and autonomous robotic transformers capable of various gait-shifting and multidirectional locomotion, as well as rapidly self-deployable and self-reconfigurable architecture, exemplifying its scalability up to the meter scale. Lastly, we introduce the concept of multitask reconfigurable and deployable space robots and habitats, showcasing the adaptability and versatility of these metastructures.
Similar content being viewed by others

Large-scale modular and uniformly thick origami-inspired adaptable and load-carrying structures

Rigidly flat-foldable class of lockable origami-inspired metamaterials with topological stiff states
Jigsaw puzzle design of pluripotent origami
Introduction.
Versatile shape-morphing capability is crucial for enabling multifunctionality in both biological and artificial systems, allowing them to adapt to diverse environments and applications 1 , 2 , 3 . For example, the mimic octopus can rapidly transform into up to 13 distinct volumetric shapes, mimicking various marine species 1 . In the realm of artificial systems, there has been a range of strategies proposed to create shape-morphing structures, including continuous forms of beams, plates, and shells 4 , 5 , 6 , bar-linkage networks or mechanical kinematic mechanisms 7 , 8 , 9 , 10 , 11 , 12 , 13 , folding or cutting-based origami/kirigami structures 12 , 14 , 15 , 16 , 17 , 18 , 19 , 20 , 21 , 22 , and reconfigurable robotic structures composed of assembled magnetic or jointed modules 23 , 24 , 25 , 26 , 27 , 28 . These structures have found broad applications in transformable architecture 21 , 29 , reconfigurable robotics 25 , 30 , biomedical devices 8 , 31 , flexible spacecraft 32 , 33 , multifunctional architected materials 20 , 34 , reprogrammable shape-morphing matter 6 , 35 , 36 , as well as deployable structures that can undergo dramatic volume change for convenient storage and transport 15 , 29 , 32 , 33 , 37 , 38 , 39 .
However, despite these advancements, artificial shape-morphing structures have yet to rival their biological counterparts in terms of the diversity of attainable volumetric shapes, as well as the efficiency and autonomy with which such versatile shape morphing can be achieved through simple actuation and control 6 , 23 , 24 , 26 , 27 , 35 , 36 . One of the primary challenges resides in the tradeoff between theoretically allowable versatility of shape-morphing, which encompasses the quantity and diversity/type of reconfigured shapes, and practical controllability in terms of actuation. For instance, while previously reported structures 11 , 23 , 24 , 26 , 27 , 28 , 36 have demonstrated the ability to change into a vast number of distinct shapes, they often require exceedingly complex actuation and control systems. This complexity can render the shape morphing process tedious, time-consuming, and energy-inefficient. On the other hand, certain structures may exhibit simpler reconfiguration kinematics 3 , 5 , 6 , 7 , 15 , 31 , 40 , 41 , 42 , enabling them to feasibly attain desired shapes. However, their specified structural forms may largely limit the achievable reconfigured shapes within few specific categories. These challenges, along with others such as complex reconfiguration kinematics, poor re-programmability, lack of inverse design capability, and limited functionality of the reconfigured shapes, as summarized in Supplementary Table 1 , could considerably impede the broad applications of shape-morphing structures in areas such as reconfigurable architecture, metamaterials, and robotics (see more details in Supplementary Note 1 ). The versatility of shape morphing is intricately linked to a structure’s mobility, i.e., the number of degrees of freedom (DOF). Theoretically, structures with a higher number of DOFs tend to exhibit greater versatility in shape morphing 11 , 23 , 24 , 25 , 26 , 27 , 35 , 36 . However, this very versatility in theory often makes it exceedingly difficult to actuate structures with higher DOFs, considering the potential need for distributed actuation of each DOF 25 .
Conventional rigid mechanism-based origami structures, constrained by their folding interconnections, are limited to morphing between their original and compact states due to one single DOF. This limitation simplifies actuation and deployment but sacrifices the potential for achieving a variety of shapes 12 , 13 , 16 , 18 , 22 , 38 , 40 , 43 . To address this limitation, recent advances have introduced modular origami metastructures composed of assembled polyhedron-shaped modules 26 , 36 , 39 , such as cubes and tetrahedrons, etc. These structures offer more than four mobilities. For example, recent studies demonstrated that a single unit cell consisting of six extruded cubes could transform into four different configurations using four distributed pneumatic actuators to control folding angles 39 . However, when scaling up to a 4 × 4 × 4 periodic meta-structures to achieve similar transformations, it requires a staggering 96 distributed actuators for each DOF 39 , resulting in low actuation efficiency. More recently, we proposed shape-morphing planar kinematic origami/kirigami modules composed of a closed-loop connection of eight cubes 36 . These modules can be manually transformed into over five different configurations via kinematic bifurcation. When assembled into a 5 × 5 array, they theoretically offer over 10,000 mobilities through bifurcation 36 . However, practically, they pose grand challenges in terms of actuation and control. Similarly, discrete kinematic cube-based modules are often assembled into lattice, chain, or hybrid architectures and used in robotic structures with higher DOFs for multifunctional modular reconfigurable robots 25 . Although these modular origami and robotic structures offer enhanced shape-morphing capabilities, they typically require control and actuation systems for each module. This complexity results in lengthy and intricate reconfiguration steps, as well as complex and time-consuming actuation, morphing kinematics, and reconfiguration paths, primarily due to their redundant DOFs 11 , 25 , 26 , 27 , 35 , 36 (Supplementary Table 1 and related discussions in Supplementary Note 1 ).
Drawing inspiration from planar thick-panel origami 12 , 18 , 22 , 36 and hierarchical materials/structures 44 , 45 , 46 , 47 in nature and engineering, here, we propose leveraging hierarchical architecture of spatial closed-loop mechanisms interconnected both within (locally) and across (globally) each hierarchical level to address the versatility-actuation tradeoff in an example system of highly reconfigurable hierarchical origami metastructures. As illustrated in Fig. 1 a, a base or level-1 structure is a spatial closed-loop mechanism consisting of n rigid linkages and n rotational hinges, an n R looped mechanism. Simply replacing each rigid linkage in a k R looped mechanism with the level-1 structure creates a level-2 “ k R” spatial looped flexible mechanism (Fig. 1b ), since each linkage becomes an n R looped mechanism, with k being the number of rotational hinges at level 2 (note that k is not necessarily equal to n ). The rotary hinges can employ origami line folds and the rigid links can take variously shaped structural elements, such as thick plates and polyhedrons (e.g., cubes, triangular or hexagonal prisms) (Fig. 1c ). The polyhedrons can be combinatorically connected at their edges using rotary hinges at each hierarchical level, offering extensive design space for diverse reconfigurable hierarchical metastructures (Fig. 1d – f and Supplementary Note 2 ).
Schematic illustrations of a level-1 metastructure composed of an n R spatial looped mechanism with n rotary hinges and n rigid linkages ( a ) and a level-2 metastructure composed of a “ k R” spatial looped mechanism at level 2 and n R looped mechanisms at level 1 ( b ). c The designs of rotary hinges and rigid linkages in the forms of respective origami line fold and different polyhedrons. d Illustration of two types of reconfigurable metastructures using planar and spatial tessellation of thin plates and prims, respectively. Examples of 3D-printed prototypes of self-reconfigurable level-1 ( e ) and level-2 ( f ) origami-based robotic metastructures actuated by electrical servomotors. Scale bar: 3 cm. The level-1 and level-2 metastructures are composed of closed-loop connections of 8 and 32 cubes, respectively. g Demonstration of the advantages of hierarchical looped mechanism in creating self-reconfigurable metastructures with versatile shape morphing under fewer reconfiguration DOFs (actuated servomotors) than 3.
We demonstrate the unprecedented properties of the metastructures arising from their hierarchical architecture of spatial closed-loop mechanisms. We find that hierarchical closed-loop mechanisms naturally introduce intricate geometric constraints that dramatically reduce the number of active DOFs required for shape morphing, even when involving a large number of structural elements (Fig. 1f, g ). Benefiting from this hierarchical coupling of closed-loop mechanisms, we show that these hierarchical origami metastructures can be efficiently actuated and controlled while achieving a wealth of versatile morphed shapes (over 10 3 ) through simple reconfiguration kinematics with low actuation DOF (≤3) (Fig. 1g ). The proposed construction strategy unlocks a vast design space by orchestrating combinatorial folding both within and across each hierarchical level, relying on spatial closed-loop bar-linkage mechanisms. It effectively overcomes the intrinsic limitations in our previous ad-hoc shape-morphing designs with similar structural elements 36 , including geometric frustrations, large number of DOF, and a lack of generalizability due to the use of units with specific shapes 13 (see Supplementary Note 1.2 for detailed comparison). Compared to the state-of-the-art shape-morphing systems 7 , 8 , 9 , 10 , 11 , 14 , 16 , 18 , 22 , 24 , 25 , 26 , 27 , 28 , 29 , 30 , 32 , 36 , 37 , 39 , 40 , 43 , 48 , our combinatorial and hierarchical origami-inspired design shows superior multi-capabilities, including high reconfiguration and actuation efficiency (requiring less time and fewer transition steps and actuations), simple kinematics and control, high (re)-programmability, a large number of achievable shapes, and potential multi-functionalities (see Supplementary Note 1.1 and Supplementary Table 1 for detailed comparison). We explore the underlying science of versatile shape morphing and actuation in the hierarchical origami metastructures, as well as their applications in self-reconfigurable robotics, rapidly self-deployable and transformable buildings, and multi-task reconfigurable space robots and infrastructure.
Hierarchical origami-based shape-morphing structures with combinatorial design capability
Figure 2a–c and Supplementary Figs. 1 – 3 illustrate the hierarchical approach employed to construct a category of planar thick-panel origami-based shape-morphing structures. In Fig. 2a , the level-1 structure represents an over-constrained rigid spatial bar-linkage looped mechanism, characterized by the number of linkages being equal to or greater than the connected bars. This structure consists of n (where n = 4, 6, 8) rigid cubes (Fig. 2a , i) serving as linkages interconnected by n hinge joints (i.e., line folds) at cube edges functioning as rotatable bars (see details in Fig. 2a , ii) 36 . These hinges are highlighted by yellow lines in Fig. 2a , iii. An example of a level-1 structure with n = 8 is shown in Fig. 2a , ii and iii, while additional examples with n = 4 and 6 are depicted in Supplementary Fig. 1a–c .
a–c Schematics of constructing level-1 ( a ), level-2 ( b ), and level-3 ( c ) reconfigurable and deployable structures using hierarchical closed-loop rigid bar (line hinges)-linkage (cubes) mechanisms (column ii) as different-leveled structural motifs (column iii). The representative morphed architectures with internal structural loops (ISLs) are shown in column iv. d Schematics of selected combinatorial designs by either combinatorically hinging two adjacent cubes at one of the four cube edge pairs at level 1 (i) and level 2 (ii) or flipping any level-1 structure with asymmetric hinge locations on top and bottom surfaces (ii) or combined. e Comparison of the maximum initial structural DOFs of different hierarchical structures composed of 4, 6, and 8 cubes at level 1. f Comparison of the combinatorically designed four categories of level-2 structures in ( b ) (insets and Supplementary Fig. 6 ) on the number of combinatorial level-2 hinge connections, reconfiguration modes, and morphed configurations with ISLs.
The connectivity between the cubes, namely the placement of the joints, dictates the spatial folding patterns of the structure (Supplementary Figs. 1 and 2 ). Broadly, the deployment follows four fundamental structural motifs, defined here as the mechanism-based connecting systems used to construct each leveled structure: one 2R chain-like mechanism and three 4R, 6R 10 , 18 , 22 , or 8R closed-loop mechanisms 41 , where n R denotes mechanisms with n rotational links and n rotatable (R) joints (see Supplementary Fig. 3 , and detailed definitions in Supplementary Note 3 ). For two adjacent cube faces, four potential edge locations exist to accommodate hinge joints (Fig. 2d , i). Consequently, a structure with n cubes theoretically allows for 4 n combinatorial sets of connections, offering an extensive design space for level-1 structures (Supplementary Fig. 4 ). Specially, we define this multiple design possibility by the placement of hinge joints in all leveled structures as their combinatorial design capability. As illustrated later, the combinatorial design capability of our proposed systems can be considerably expanded given the structural asymmetries and the multiple choices of structural motifs. Depending on the chosen connectivity, level-1 structures composed of n cubes exhibit an initial maximum number of 2 ( n = 4), 3 ( n = 6) and 5 ( n = 8) DOFs (Fig. 2e ), which can be utilized for morphing into a diverse array of distinct 3D architected structures (as exemplified in Fig. 2a , iv, and further elaborated in Supplementary Fig. 1 and Supplementary Movie 1 ).
By substituting the higher-level linkages with the lower-level basic or hierarchical structures (e.g., Fig. 2a–c , i–iii and Supplementary Fig. 3a, b ) in the four fundamental structural motifs (2R, 4R, 6R, and 8R), we can create a class of flexible spatial hierarchical mechanism-based origami structures by combinatorically choosing any type of the n R linkages as different-level structural motifs (Supplementary Fig. 3c ). Notably, the term “flexible spatial mechanism” refers to mechanical mechanisms with bars and linkages arranged in 3D space, where the length of linkages is not fixed and varies during reconfiguration. For example, Fig. 2c , ii illustrates a level-3 structure comprising 8R linkages at level 1, 4R linkages at level 2, and 2R linkages at level 3, denoted as <8R, 4R, 2R>. The sequence from left to right corresponds to the structural motifs used from lower-level structure to higher-level structure.
The associated level-2 structure is depicted in Fig. 2b and denoted as <8R, 4R>. Additional examples of hierarchical origami structures with varying numbers of cubes at level 1 are presented in Supplementary Figs. 2 , 5 and 6 . Upon deployment, these structures can continuously transform into a multitude of intricate architected forms featuring internal structural loops (ISLs): internal voids within reconfigured architected structures enclosed by boundary structural components (as illustrated in Fig. 2a–c , iv, Supplementary Figs. 5c and 6 ). These ISLs efficiently facilitate different-level kinematic bifurcations, where a singular configuration state triggers a sudden increase in structural DOFs, leading to additional subsequent reconfiguration branches. This is in sharp contrast to the counterparts composed of four cubes at level 1, which are primarily limited to simple chain-like configurations (Supplementary Fig. 2a ) despite having a greater number of initial DOFs in the hierarchical structures of <4R, 4R> and <4R, 4R, 4R> (Fig. 2e ).
Moreover, the design space of hierarchical structures can be considerably expanded by combinatorically (1) adjusting the connectivity at higher-level bars (Fig. 2d , ii) and (2) manipulating structural asymmetries at the lower-level linkages given the asymmetric patterned joints on the top and bottom surfaces across the thickness, e.g., simple upside-down flipping (see Fig. 2d , ii for an example of level 2 structure). As an illustration, the insets in Fig. 2f and Supplementary Fig. 5 show four selected categories of combinatorial <8R, 4R> level-2 structures created by flipping the level-1 8R linkages and modifying the connections at the level-2 joints. By employing combinatorial design strategies involving mechanism hierarchy, spatial fold patterning across multiple levels of bars, and folding asymmetries in the linkages, we can generate an extraordinary vast design space encompassing millions of configurations, even within a simple level-2 structure (see analysis in Supplementary Note 2 ).
Compared to state-of-the-art 2D 14 , 16 , 40 , 48 and 3D origami designs 12 , 18 , 22 , 36 , 42 including our previous ad-hoc design of specific tessellated closed-loop mechanism of cubes 36 , this hierarchical approach offers several advantages: Firstly, it largely broadens the range of designs by allowing combinatorial connections within and across each hierarchical mechanism, which are either disabled or severely limited in previous studies 12 , 18 , 22 , 36 , 42 . Secondly, it effectively avoids geometric frustration in our previous ad-hoc designs 36 , which refers to structural constraints arising from deformation incompatibility during deployment 44 , 45 . This avoidance is made possible by the compatible reconfigurations of differently leveled spatially looped mechanisms (Fig. 2a–c , ii). Thirdly, this fundamental design principle establishes a versatile structural platform that can be applied to various shaped building blocks, overcoming the limitations in our previous ad-hoc designs 36 and other studies associated with specific structural elements 22 , 26 , 36 , 38 , 39 , 42 . Fourthly, it possesses the intrinsic benefit of structural hierarchy 46 , 47 , 49 , favoring higher-level structures with greater diversity and quantity of actuated reconfigured shapes under simple control and actuation.
Within this extensive design space, designs of particular interest are those that exhibit high reconfiguration capabilities via collision-free kinematic paths involving only a few active structural DOF during shape-changing processes. Such designs enable rich shape-morphing capability with simple and reliable control. After comparison (Supplementary Note 2 ), we identified an optimal category composed of four identical <8R> type of level-1 structures (see Category 1 in Fig. 2f and Supplementary Fig. 5b , with detailed definitions provided in Supplementary Notes 2 and 3 ) to showcase their extensive shape-morphing behavior under few active DOF. These designs boast the highest structural symmetries and the largest number of ISLs, facilitating bifurcation and shape diversity (Fig. 2f ).
Continuously evolving versatile shape morphing
Figure 3a provides a comprehensive view of the shape-morphing configurations diagram of one exemplary optimal <8R, 4R> level-2 structure selected from Category 1 in Fig. 2b (see Fig. 3a , i for its hierarchical design details). These structures were fabricated by assembling the 3D-printed rigid square facets (in white) into hollow cubes via interlocking mechanisms and flexible printed line hinges made of rubber-like materials (in black) (Supplementary Fig. 7a , see “Methods” and Supplementary Movie 2 for details). This design not only facilitates straightforward assembly but also allows for easy disassembly and reassembly of facets into hierarchical structure (Supplementary Fig. 7b–d ). For clarity, configurations with folding angles that are multiples of 90° are displayed since these angles correspond to kinematic bifurcations, as discussed later.
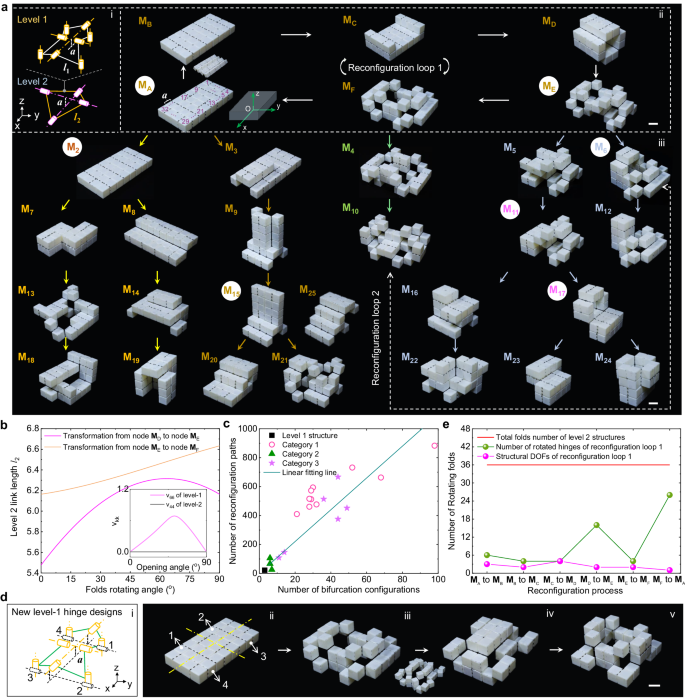
a Shape-morphing configurations diagram in the 3D-printed prototype exhibiting hierarchical transition tree-like features. The branches in the transition tree of represent the bifurcated configurations. Scale bar: 3 cm. b The variation of flexible level-2 link length with the opening angle of hinges during the shape transition from node M D to M E , and node M E to M F in reconfiguration loop 1 in ( a ). Inset shows the eigenvalues v kk as a function of the rotating angle in both level-1 and level-2 structures. c The relationship between the number of reconfiguration paths and the number of kinematic bifurcation configuration states for the combinatorically designed category I–III level-2 systems. d One selected combinatorial design of the shape-morphing level-2 structures by rearranging the level-1 hinges (i), and some of its representative reconfigured shapes (ii–v). Scale bar: 3 cm. e Comparison among the total number of hinges, the number of rotated joints, and the number of reconfiguration DOFs during the reconfiguration loop from node M A to M F and back to M A in ( a ).
With the inherent capacity for versatile shape changes provided by the level-1 linkage structure (Supplementary Fig. 7b ), the level-2 structure can continuously evolve, adopting various representative complex architectures along multiple reconfiguration paths (indicated by different colored lines in Fig. 3a ). Notably, these shapes bear a striking resemblance to trucks, trophies, tunnels, shelters, and various architectural structures (see more details in Supplementary Fig. 8 and representative reconfiguration processes in Supplementary Movie 3 ).
To systematically represent all reconfigured shapes and their corresponding shape transitions in Fig. 3a (ii), we employ a data-tree-like diagram (Supplementary Fig. 9 ), inspired by graph theory used in computer science to elucidate logical relationships among adjacent data nodes 50 (Supplementary Note 4 ). In this diagram, both nodes and line branches are assigned specific physical meanings, signifying individual reconfigured shapes and the relative shape-morphing kinematic pathways connecting them. As shown in Fig. 3a and Supplementary Fig. 9 , starting from a compact state (node M A ), the analyzed level-2 structure can traverse a closed-loop shape-morphing path (termed reconfiguration loop 1, RL-1, or a parent loop). Along this path, it transitions from simple chain-like structures (e.g., node M A → M B → M C → M D ) to intricate architectures featuring ISLs (e.g., node M D → M E → M F ). Subsequently, starting from node M E with ISLs, it can further transform into nodes M F , M 5 , M 6 , or return to M D ). Theoretically, this continuous evolution in shape arise from the varying link lengths of the flexible level-2 linkage as line folds exhibit changing folding angles (Fig. 3b and Supplementary Fig. 11 , see the analysis in Supplementary Notes 5 – 7.1 , which examines length variations in level-2 links during two representative shape-morphing processes from node M D to M E and from node M E to M F ).
Benefitting from both chain-like and closed-loop mechanisms embedded in the morphed structural configurations, the parent loop gives rise to several subtrees (e.g., at node M A , M B or M 2 , M E , and M F ). These subtrees, in turn, branch into more paths through kinematic bifurcations (e.g., at node M 11 , M 15 , and M 17 ), as depicted in the inset of Fig. 3b . These bifurcations can be accurately predicted based on the number of null eigenvalues v kk in the kinematics model (see Supplementary Note 7.2 for detailed theoretical analysis). Importantly, node M 6 and node M 10 , located in different subtrees, are interconnected to form another reconfiguration loop (i.e., RL-2). This allows for direct transformation between two configurations or nodes that traverse different subtrees efficiently, without the need to return to the initial configuration and repeat redundant transforming steps, as required in previous reconfigurable structures 11 , 14 , 16 , 23 , 24 , 25 , 26 , 28 , 36 . Comparable hierarchical transition tree structures featuring bifurcated branches and interconnected nodes are observed in most of the four categories of other combinatorial <8R, 4R> level-2 structures (Supplementary Fig. 11 ). These structures are obtained by rearranging multilevel joint locations on top or bottom surfaces or by flipping the level-1 linkage (as seen in the level-2 representative in Fig. 3d and Supplementary Fig. 7d , e ). Consequently, a multitude of versatile and distinct morphed configurations are generated (Supplementary Figs. 12 and 13 ) based on differing hinge connectivity.
Additionally, for all combinatorial designs (Supplementary Fig. 5b ), we observed that the number of reconfiguration paths increases approximately linearly with the number of bifurcated nodes or configurations (Fig. 3c ). Notably, starting from a defined fold pattern, the same level-2 structure can generate nearly 10 3 reconfiguration paths with approximately 100 bifurcation nodes, thereby bestowing extensive shape-morphing capabilities (see analysis in Supplementary Note 8 ). In comparison to previous designs 12 , 16 , 18 , 22 , 26 , 29 , 31 , 38 , 39 , 40 , 43 , 48 that offer only a few shape-morphing paths from a defined fold pattern, our hierarchical design strategy enables a high number ( N ~ 10–10 3 ) of kinematic transitions, demonstrating substantial versatility in generating numerous shapes and architectures.
Given that each reconfigured shape in Fig. 3a is defined by internal fold rotation angles that are multiples of 90°, we can accurately represent each shape by collecting spatial vectors v of the body center coordinates of all structural elements into a shape matrix M (see “Methods” for details). This matrix takes the explicit form M = ( v 1 , v 2 , v 3 , …, v n ) (with n = 32 for the level-2 structures shown in Fig. 3 and Supplementary Fig. 5 , see “Methods” and Supplementary Note 4 for details). Consequently, we can systematically annotate all reconfigured shapes in Fig. 3a using their corresponding shape matrices M k (with k as the shape index, see inset in Fig. 3a and Supplementary Fig. 9 ). Once the initial shape matrix M A is known, we can theoretically determine all the reconfigured shapes of the level-2 structure in Fig. 3a accordingly (see “Methods” for details). Importantly, this annotation approach is generalizable and can be applied to all other hierarchical origami metastructures presented in this work.
Remarkably, despite the level-2 structure’s total of 36 joints, only a small number of them are needed to drive the shape-morphing process, referred to as active reconfiguration DOF (Fig. 3e ). For example, when considering the multistep shape-morphing process from node M D to node M A , i.e., M D → M E → M F → M A in Fig. 3a , it exhibits only 2, 2 and 1 DOF, respectively, even though it involves the rotation of 16, 8, and 24 joints (Fig. 3e and more details in Supplementary Figs. 14 and 15 ). This is in contrast to our previous ad-hoc design of cube-based reconfigurable metastructures 36 . Despite the presence of multiple closed-chain loops, they often function as independent units that barely couple with each other during shape morphing due to the specific architecture design of these metastructures, which results in high mobilities over 10,000 36 , making it impossible for control and actuation. In contrast, the reduction in active joints in this work is due to the specific interconnectivity of the looped level-1 and level-2 structures as geometric constraints, which dramatically reduces the number of active joints required while enabling high reconfigurability. Additionally, the multilevel closed-loop interconnectivity simplifies the control of shape-morphing paths in terms of simple transition kinematics, as demonstrated below.
Simple transition kinematics during shape morphing
The transition kinematics describes the quantitative relationship among the folding angles during the shape morphing of hierarchical structures. In Fig. 4a , we utilize the transformation matrix T (d, γ) to describe the relative spatial relationship of the four links, where d is the shortest distance between adjacent joints, and γ is the opening angle between adjacent cube-based links, as shown in Fig. 4b, c and Supplementary Fig. 16 . For a looped mechanism, it holds that \({\sum }_{i=1}^{m}{{{{\bf{T}}}}}_{i}={{{\bf{I}}}}\) , where m = 8 and m = 4 for the level-1 and level-2 links, respectively, and I is the identity matrix (see Supplementary Note 6 for details). With such simple equations, we can readily derive the relationship among the joint angles for all the transition paths using the local Cartesian coordinate systems presented in Fig. 4c (see Supplementary Note 7.1 for details).
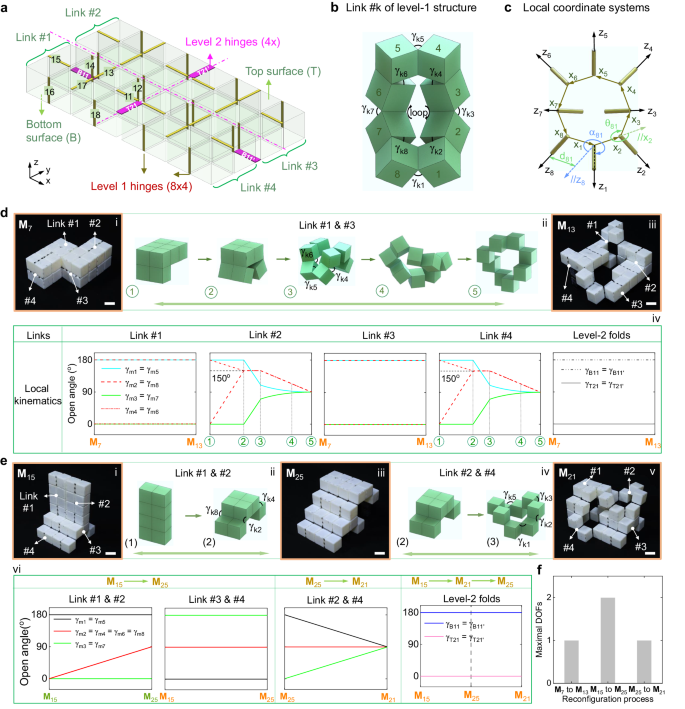
a Schematics of level-2 structures with labeled hinge connections on top and bottom surface. b Schematics of the opening angles γ kj ( k , j are integers with 1 ≤ k ≤ 4 and 1 ≤ j ≤ 8 denote the link and hinges opening angles, respectively) between adjacent cubes in level-1 structure. c Construction of eight local coordinate systems for the 8 hinges of level-1 structure. d The reconfiguration kinematics from node M 7 (i) to node M 13 (iii) in Fig. 3a, b : the involved shape-changing details of level-1 link #1 and #3 (ii) and variations of the rotating angles for all folds (iv). Scale bar: 3 cm. e The reconfiguration kinematics from node M 15 (i) to node M 21 (v) by bypassing node M 25 (iii) in Fig. 3a, b : the involved shape-changing links #1 and #2 for the process from node M 15 to M 25 (ii) and links #2 and #4 for the process from node M 25 to M 21 (iv) and variations of all folds during these two processes (vi). Scale bar: 3 cm. f Low reconfiguration DOFs for the reconfiguration process in ( d ) (1 DOF) and ( e ) (1 or 2 DOF(s)).
To illustrate the simplicity of transition kinematics, we select two representative reconfiguration paths (node M 7 → node M 13 and node M 15 → node M 21 in Fig. 3a ) that transform from simple chain-like structures to complex architectures with ISLs (“Methods”). Figure 4d, e shows their detailed transition kinematics for these paths. It is observed that both shape-morphing paths involve only local and stepwise transition kinematics. For example, when transitioning from node M 7 to M 13 (Fig. 4d , i and iii), only the joints in link #2 and #4 (Fig. 4d , i) are engaged in sequential rotations (Fig. 4d , ii), while the remaining joints in link #1, link #3, and level-2 joints remain stationary (Fig. 4d , iv) (see “Methods” for details). Similarly, the reconfiguration kinematics from node M 15 to M 21 , bypassing node M 25 , follows a straightforward linear angle relationship, as shown in Fig. 4e , i–vi. Despite these two reconfiguration processes representing the most complex shape morphing (see more details in Supplementary Figs. 17 and 18 ), they can be achieved using simple kinematics-based control. Moreover, Fig. 4f shows that the number of active DOFs for each step remains below 3 during these two reconfiguration processes, thanks to the specific looped interconnectivity of hierarchical structures. This is superior to previous designs, which either featured condensed 11 , 12 , 14 , 16 , 18 , 22 , 26 or completely discrete internal connections 25 , 27 .
Given the unveiled simple transition kinematics of hierarchical structure and the low number of active DOFs during shape morphing, next, we explore and demonstrate their potential applications such as autonomous robotic transformers with adaptive locomotion, rapidly deployable self-reconfigurable architectures, and multifunctional space robots.
Autonomous multigait robotic transformer
To achieve autonomous shape morphing in the hierarchical origami structure, we utilize servomotors to actuate the active joints, while passive joints are secured using metal pins (Fig. 5a , i). These servomotors are powered by onboard rechargeable batteries and controlled through a customized circuit board equipped with a Bluetooth signal receiver (Fig. 5a , ii, see more details in “Methods” and Supplementary Note 9 ). This setup enables untethered shape morphing via a developed remote control system (Fig. 5a , iii, see more details in Supplementary Figs. 19 – 21 and Supplementary Movies 4 and 8 ).
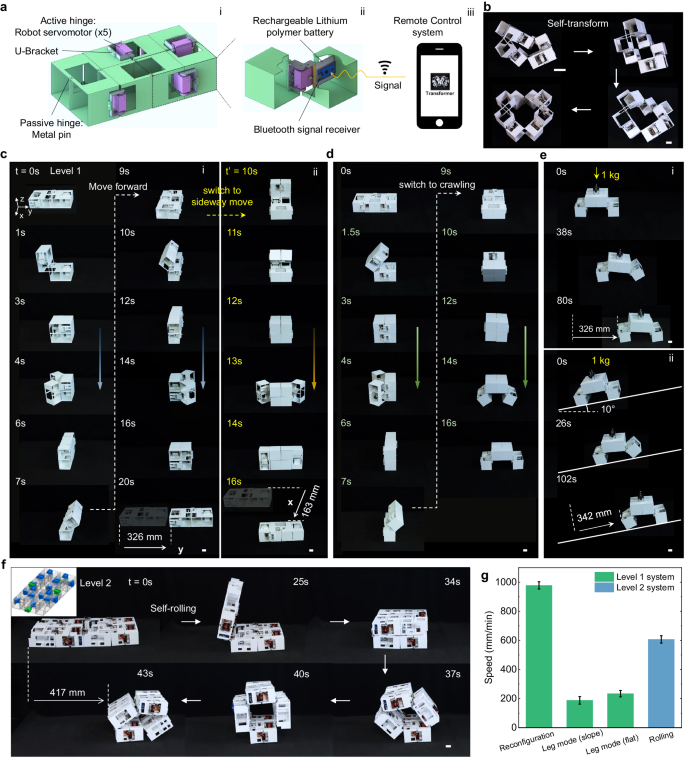
a Schematics of untethered actuation design details for the level 1 eight-cube-based structure: 5 electrically powered servomotors for active hinge rotation (i), onboard power system and Bluetooth wireless receiver to conduct reconfiguration order (ii) from customized remote control software (iii). b Demonstrated untethered shape morphing in the level-1 structure through looped mechanisms. c – e Shape transformation in level-1 structure for multigait locomotion. Scale bar: 3 cm. c Forward (i) and sideway locomotion (ii). d Locomotion gait switch from reconfiguration to legged walking; e Legged walking with carried payload on flat surface (i) and 10°-sloped surface (ii). f Demonstration of the specific positions of 22 active servomotors and the rolling locomotion of level-2 structure. Scale bar: 3 cm. g Locomotion speeds of both level-1 and level-2 structures in ( c – f ).
Thanks to the specific kinematics, even though there are a total number of 8 joints in a level-1 structure and 32 joints in a level-2 structure, only 5 (Fig. 5a ) and 22 (Fig. 5f ) servomotors are needed to accomplish all the reconfiguration paths in these structures (Fig. 5b–e in level 1, and Figs. 5 f and 6a–c in level 2, respectively, see details in Supplementary Fig. 22 ). Importantly, the number of active servomotors involved in the reconfiguration paths does not exceed 3 (Fig. 6d ). For the level-1 structure, it can rapidly and continuously transform from the compact planar state to 6R and 8R-looped linkage configurations via looped mechanisms within a few seconds (Fig. 5b and Supplementary Movie 4 ). Additionally, it can assume simple 2R chain-like configurations via chain-like mechanisms (Fig. 5c ).
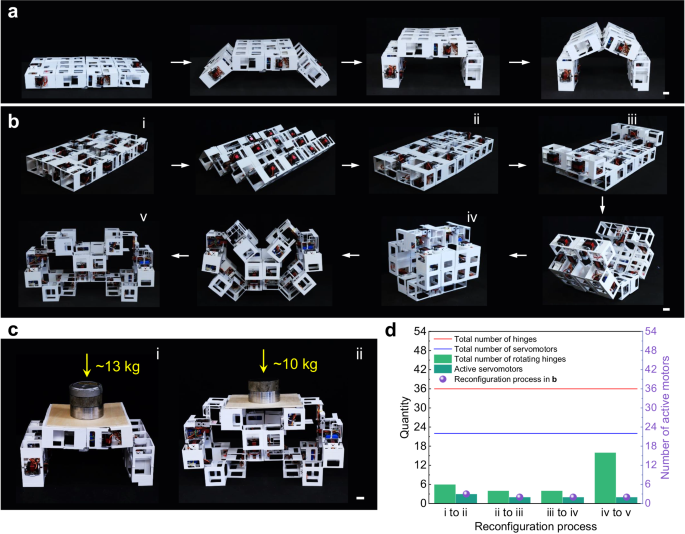
Self-deployment into bridge and/or shelter-frame-like ( a ) and fully open 4-story building-like structures ( b ) with high loading capacity of over 10 kg ( c ). Scale bar: 3 cm. d Comparison among the total number of hinges, the total number of servomotors, the rotated hinges, and the actively actuated servomotors during the shape transformation shown in ( b ).
Next, we delve into harnessing active shape morphing for autonomous robotic multigait (Fig. 5c–e ) and rolling (Fig. 5f ) locomotion. By following the chain-like reconfiguration loop path (Supplementary Fig. 7b ), the level-1 structure can repeatedly transform its body shape to achieve impressive multigait robotic locomotion. For instance, it can perform forward or backward locomotion (one cycle is shown in Fig. 5c , i) at a rapid speed of approximately 1000 mm/min (3.07 body length/min) (Fig. 5g ). Alternatively, it can change its movement direction from forward motion to sideway motion (Fig. 5c , ii) or switch its reconfiguration locomotion mode to a bipedal crawling mode (Fig. 5d and see more details in Supplementary Fig. 19c ). Moreover, it is capable of carrying some payload (around 1 kg, equivalent to its self-weight) and climbing sloped surfaces (10°, Fig. 5e ) at reduced speeds of approximately 225 mm/min and 190 mm/min (Fig. 5g ), respectively. Furthermore, a similar chain-like reconfiguration allows us to demonstrate rolling-based mobility in the level-2 structure (Fig. 5f and Supplementary Movie 5 ) at a speed of about 600 mm/min (Fig. 5g ).
Rapidly deployable and scalable self-reconfigurable architectures
Moreover, the compact level-2 structure can effectively self-transform and rapidly deploy into architectural forms resembling bridges, tunnels, and shelters (Fig. 6a, b and Supplementary Movie 6 ), both with and without internal looped structures. This transformation occurs within 2 min, a notable advance compared to previous studies that required several hours and complex algorithms 11 , 23 , 24 , 25 , 26 . Additionally, it can rapidly self-deploy into a fully open multi-story building-like structure, expanding its occupied volume fourfold (Fig. 6b , v). It can also quickly revert to a compact large cube (Fig. 6b , iv and Supplementary Movie 6 ). Due to its specific structural features (Supplementary Fig. 23 , see more details in Supplementary Note 10 ), the reconfigured level-2 structure can bear substantial loads without collapsing, such as approximately 13 kg (over 3.5 times its self-weight) for the bridge- or tunnel-like structures and about 10 kg (over 2.5 times its self-weight) for the multi-story structure (Fig. 6c ).
Notably, during the self-deployment from a compact planar structure to a complex multi-story open structure in Fig. 6b , the number of active motors remains low, never exceeding 3, despite the total number of 36 joints and 22 motors (Fig. 6d ). For example, during the reconfiguration from the compact cube to the fully open structure (Fig. 6b , iv–v), only 2 active servomotors drive the rotation of 16 joints (Fig. 6d ), demonstrating high reconfiguration efficiency.
As proof of concept, we demonstrate that these spatial hierarchical mechanism designs can be up-scaled to meter-sized buildings by assembling heavy-duty cardboard packing boxes (box side length 0.6 m). Starting from flat-packed cardboards with minimal space requirements, they can be rapidly assembled for easy deployment and reconfiguration into various structurally stable meter-scale tunnels, shelters, and multi-story open structures (Fig. 7a and Supplementary Movie 7 ). Remarkably, the total volume occupied by the deployed multi-story open architecture is 200 times larger than the initial volume of the flat-packed cardboards (Supplementary Fig. 24 ). Collectively, these properties make the proposed design promising for potential applications as temporary emergency shelters and other autonomously rapidly deployable and reconfigurable temporary buildings.
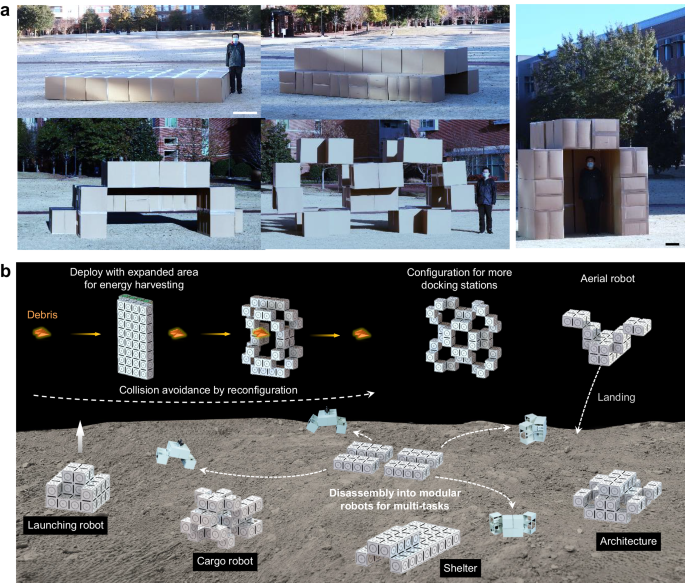
a Meter-scale demonstration of deployable, shape-morphing architectures using cubic packaging boxes (side length of 60 cm). Scale bar: 30 cm. b Schematics of potential conceptual applications in versatile reconfigurable space robots and habitats.
The hierarchical and combinatorial designs in both the links and joints at multiple levels of hierarchical structures provide an extensive design space for creating various spatial looped folding patterns and architected origami-inspired structures capable of shape morphing. It creates hierarchical origami-based metamaterials with (1) fewer active reconfiguration mobilities, (2) simple reconfiguration kinematics to facilitate practical control and actuation, and (3) rich shape-morphing capability adaptable to various applications. The hierarchical architecture couples the closed-loop mechanisms within and across each hierarchical level. Despite the large number of joints involved, the hierarchical looped mechanisms inherently impose geometric constraints that dramatically reduce the number of active DOFs required for shape morphing. This reduction greatly simplifies both actuation and control without sacrificing rich shape-morphing capability, which previously required the actuation of each DOF individually in reconfigurable origami metamaterials and robots. It also enables the feasibility of inverse designs, allowing for imitating target shapes and structures (Supplementary Figs. 20 , 25 and 26 , see theoretical details in Supplementary Note 11 ).
Our design strategy combines structural hierarchy with over-constrained looped kinematic mechanism without considering elastic deformation in the hinges and cubes. Practically, the elastic deformation or slack, especially in the hinges, could cause the system to be floppy or potentially deviate from the desired non-bifurcated and/or bifurcated kinematic paths. As demonstrated in the multimaterial 3D-printed level-2 structure in Fig. 3a , the soft hinges are printed thin with little stiffness to ensure almost free rotation. Thus, in addition to bending for rotation motion, the hinges also undergo certain twisting deformation, potentially causing the structure to deviate from their ideal kinematic paths. However, deviations occur only during the complex reconfiguration processes, e.g., from configuration M 7 to M 13 in Fig. 3a . Such deviations are suppressed when the reconfiguring structure exhibits structural symmetries, e.g., from configuration M D to Configuration M E in Fig. 3a preserving x - y and z - y plane symmetries. The slack can be avoided by fabricating hinges with a low ratio of bending stiffness to twisting stiffness. This will help to suppress its twisting deformation to follow the kinematic paths without making the structure overly floppy. For systems fabricated with high-precision rigid links and hinges, slack or elastic deformation can be minimized or eliminated, as demonstrated in the prototype of both level-1 and level-2 structures with 3D-printed rigid cubes and rigidly rotatable hinges in Fig. 5a . Similar to studied 2D rigidly foldable origami structures, the reconfiguration kinematics of the system becomes energy scale independent. Thus, the system can rigorously follow its bifurcated reconfiguration kinematic path via fewer number of actuation hinges to smoothly reconfigure into all desired configurations without any locking issues as demonstrated in Figs. 5 and 6 .
We note that there are several limitations of this work. First, the load bearing capacity of some reconfigured 3D architectures is still limited, which could hinder their practical engineering and structural applications, especially at meter scales. The load bearing capacity is dependent of not only the transformed architectures (see the free body diagrams of force analysis for example in Supplementary Fig. 23 ), but also the bending stiffness of both cubes and hinges and the structural designs of the hinges. The hinges are imitated with 3D-printed soft rubber-like materials or tapes with low bending rigidity that facilitate the bending and rotation motion but sacrifice the load-carrying capabilities. The load bearing capacity could be improved by using stronger materials with high bending rigidity or locking hinges or devices at either 90° or 180° folded angles. Second, the shape-morphing capability for robotic applications is limited to multi-gait motion demonstrated in this work. How to leverage the rich shape-morphing capability for diverse and adaptive robotic locomotion in unstructured environments remains to be uncovered. Third, the demonstration of self-deployment and self-reconfiguration is limited to centimeter-scale prototypes while the meter-scale demo is done manually due to the limitation of both power and servomotors. At large scales, the heavier self-weight of cubes cannot be neglected, which requires high-torque servomotors and high-power batteries to generate sufficient torque output to counter the gravity and drive the folding.
Moving forward, these limitations also open new opportunities for future researches in morphing matter. First, this work explores only a small region of the tremendous design space in morphing matter to showcase its potential. The vast combinatorial folding patterns arise from the combinatorial connections in the base units, as well as within and across each hierarchical mechanism (Supplementary Fig. 3 ). These combinatorial hierarchical mechanisms are generalizable and can be applied to construct similar reconfigurable hierarchical metastructures composed of any shape-morphing spatial closed-loop mechanism for easy actuation and control yet rich shape morphing. For example, the cube units can be replaced by other composed geometrical shapes, such as thick plates with substantially reduced thickness dimension, tetrahedrons, and triangular-shaped prisms, or extended to genuine volumetric 3D structures (examples are provided in Supplementary Figs. 27 and 28 , with more details in Supplementary Note 12 ).
Second, this work focuses on exploring the reconfiguration kinematics of the hierarchical origami systems by modeling the system as idealized hierarchical rigid mechanisms and neglecting the deformation in both the cubes and hinges. However, in scenarios when such elastic deformation are non-negligible, similar to the non-rigidly deformable origami metamaterials in origami engineering, the over-constrained looped kinematic mechanisms become energy scale dependent, considering the potentially involved complex deformation in the cubes, hinges, and architectures during reconfiguration such as bending, stretching, twisting, and shearing or combined. Consequently, it will transform the rigid mechanisms into both reconfigurable and deformable architected materials and structures, which couples kinematics with mechanics. Such coupling will enrich new kinematics, mechanics, transformed configurations, reconfiguration paths, and reprogrammable mechanical behaviors such as multistability and stiffness anisotropy. Specially, how the energy scale affects the kinematic bifurcated paths and how the coupled kinematic bifurcation and elasticity change both the reconfigurations and mechanical responses of bifurcated mechanical metamaterials remain to be uncovered. We envision such studies could also find broad applications in reprogrammable mechanical computing, mechanical memory, and mechanical metamaterials.
Third, considering these multi-capabilities in conjunction with scalability, modularity, and disassemblability, we envision diverse applications in robotics, architecture, and even in space. Figure 7b conceptually illustrates potential applications in multitask adaptive shape-morphing space robots and habitat (Supplementary Movie 8 ). The hierarchical origami architectures could be deployed with largely increased exposed surface areas for enhanced solar energy harvesting, and reconfigured to avoid debris collision or accommodate more docking stations. It could also serve as reconfigurable space habitat or be des-assembled into modular robots for multitask exploration. For large-sized structures, the feasibility of actuation in a space environment is considerably higher, primarily due to the absence of gravity and the absence of ground-based collisions that can impede complex shape-morphing processes on Earth.
Sample fabrication of cube-based origami structures
To demonstrate the shape morphing in cube-based origami structures, we used two ways to fabricate and assemble the hollow cubes. One is for quick shape-morphing demonstration by directly 3D printing individual cubes with cube size of 2 cm (Stratasys Connex Objet-260 with stiff materials of Vero PureWhite) and connecting them with adhesive plastic tapes (Scotch Magic Tape, 6122) as free-rotation hinges (Supplementary Figs. 5 , 8 and 11 – 13 ). The other is for easy assembly and disassembly demonstration by 3D printing Lego-like pieces of thin rigid plates (Fig. 3 ). Two types of thin plates were printed (Supplementary Fig. 7a ): one is a thin rigid plate with interlocking teeth (Vero PureWhite) for assembling into a hollow cube, the other is a connection piece composed of two connected thin rigid plates with soft hinges made of rubber-like materials (Agilus-black) through 3D multimaterial printing. The connection piece is used to connect two neighboring cubes at any selected hinge locations with the soft hinges facilitating the free rotation of cubes. The cube size is 3 cm.
Fabrication of autonomous robotic transformers
The cubes were 3D-printed with ABS printing materials (QIDI Tech X-Max 3D printer) with cube size of 81.5 mm and mass of 40 g. To ensure the compact contacts between the 3D-printed cube components, we created open areas at the joints positions and use the U-shaped bracket to hold electronic elements (Fig. 5a , i). Each motor (DSservo RDS3225) was powered by a 3.7 V LiPo battery and controlled via its specific control board (Adafruit ItsyBitsy nRF52840 Express). Additional chips were incorporated for accommodating the JST connector for the battery (Adafruit Pro Trinket LiIon/LiPoly Backpack Add-On) and for adaption of the supply voltage (SparkFun Logic Level Converter—Bi-Directional). The control boards were identified by a numeric ID and communicated with each other via Bluetooth by following a serial framework, where each controller receives the information from the previous one and sends them to the next one. More details can be found in Section S10 of Supplementary Information.
Fabrication of meter-scale samples
The cubes used in the meter-scale shape-morphing architectures in Fig. 7a were heavy-duty cardboard packing boxes (Recycled Shipping Box, Kraft) with dimensions of 0.6 m × 0.6 m × 0.6 m. Boxes were connected using the fiber-reinforced ultra-adhesive tape (BOMEI PACK Transparent Bi-Directional Filament Strapping Tape).
Fundamental principles governing the shape transformation
Given the mechanical kinematic mechanism’s structural features, the core of the shape transformations in these structures involves changes in the spatial positions of specific structural elements resulting from the directional rotations of internal hinges and their interconnections. Technically 10 , 22 , 51 , this operation can be mathematically modeled using a rotation matrix t (see details in Supplementary Note 4.2 ). Thus, the shape transformations of any leveled structures can be denoted as:
where M ′ represents the transformed shape from shape M , with both M and M ′ reflected in Fig. 3a and Supplementary Fig. 9 as M k , and t represents the mathematical operations between them. In our analysis, we initially build a fixed global Cartesian coordinate system at the bottom center of the original shape (see the inset at the initial shape in Fig. 3a , ii). Subsequently, we construct a local coordinate system at each fold to derive the body center coordinates of the rotated cube structural components (Supplementary Fig. 10a, b ) in each shape-morphing process. Mathematically, we can thus determine the new positions of the rotated cubes as follows:
where v n_local and v n_new represent the body center vectors of cube # n before and after shape morphing, respectively, in the local and fixed global coordinate systems. t n is a general functional form including all directional rotations of cube # n (Supplementary Fig. 10b–e ), see the systematic analytical details in Supplementary Note 4.2 . d n is the translational vector between the fixed global coordinate system and the local coordinate system of cube # n . Note that all shape matrices of the initial and reconfigured shapes are described in the fixed global coordinate systems.
We validate the theoretical framework by modeling the shape-morphing process of reconfiguration loop 1, i.e., from the initial shape M A to shape M F , passing through shapes M B , M C , M D and M E . The shape matrix of the initial shape is determined first in the fixed global coordinate system. Based on Eqs. ( 1 ) and ( 2 ), we rationally derive the new positions of the rotated cubes in new shapes accordingly. Specifically, we analyze the process from morphing from shape M D to shape M E , where a total of 24 cubes are involved. To provide a representative example, we select cube #20 and theoretically derive its new spatial positions. Subsequently, we compare these derived solutions with experimental results to validate our proposed theoretical framework.
Starting from the initial shape M A , we derive the shape matrix of M D , as expressed in Eq. ( 3 ). Consequently, in the fixed global coordinate system, we obtain the explicit spatial vector for cube #20 \({{{{\boldsymbol{v}}}}}_{20}^{{{{{\bf{M}}}}}_{D}}\) with \({{{{\boldsymbol{v}}}}}_{20}^{{{{{\bf{M}}}}}_{D}}={(1,3,1)}^{T}\) . During the shape-morphing process, cube #20 undergoes rotation along the x- axis within the locally built coordinate systems (Supplementary Fig. 10a , iv). To derive its new positions, we first calculate its spatial vector in the local coordinate systems, represented by \({{{{\boldsymbol{v}}}}}_{20\_local}^{{{{{\bf{M}}}}}_{D}}={(1,1,1)}^{T}\) . Utilizing a 90° x -directional rotation, we then derive its new coordinates in the global coordinate systems using Eq. ( 2 ) with explicit derivation details as:
Within the built fixed global coordinate systems, we extract the experimental result pertaining to the spatial position of cube #20 in the global coordinate system, denoted as \({{{{\boldsymbol{v}}}}}_{30}^{{{{{\bf{M}}}}}_{E}}={(1,3,-1)}^{T}\) . The theoretical model is in excellent agreement with the experimental result. In order to derive the shape matrices of shapes M D and M E in reconfiguration loop 1, we need firstly determine the shape matrix of the initial shape M A , which is presented with explicit components as:
Then, combining Eqs. ( 1 )–( 4 ), we can finally obtain the shape M D and shape M E as:
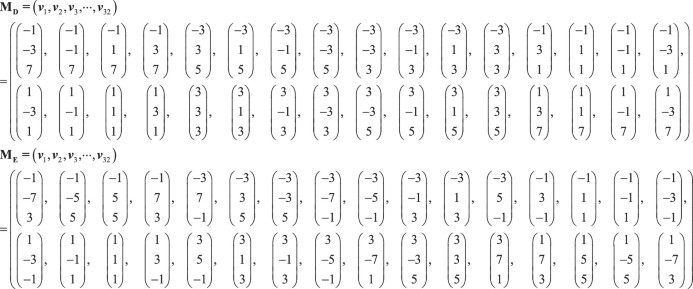
Reconfiguration kinematics in Fig. 4
The following gives the reconfiguration kinematic details for the morphing process shown in Fig. 4 d, e . Specially, we label the opening angles of four level-1 link structure as γ km ( k and m are integers with 1 ≤ k ≤ 4 as the k th link while 1 ≤ m ≤ 8 as the m th rotating folds between two adjacent cubes m and m + 1 ( m + 1 → 1 when m = 8), see details in Fig. 4a, b ), and the level-2 folds angles separately as γ B11 , γ B11’ , γ T21 and γ Τ21’ (Fig. 4a, b and B and T represent the bottom and top surfaces, respectively).
The selected two reconfiguration processes exhibit only local and stepwise transition kinematics. From shape M 7 to M 13 (Fig. 4d , i and iii), only the folds of links #2 and #4 (Fig. 4d , i) are involved with sequential rotations (Fig. 4d , ii) and the remaining folds of link #1, link #3 and the level-2 keep unchanged (Fig. 4d , iv). For kinematic details of the reconfigured links #2 and #4 shown in Fig. 4d , iv, during the initial process ① → ② , we only need to linearly change the folds angle γ m4,6 ( m = 2 or 4) from 180° to γ 0 (Here we set γ 0 as 150° while it ranges from 90° to 180°; see more details in Supplementary Fig. 17 ) and meanwhile linearly increase γ m2,8 from 0° to γ 0 . Then, in the following process ② → ③ , we can maintain folds angles γ m2,4,6,8 as γ 0 while both linearly decreasing γ m1,5 from 180° to sin -1 [(sin γ 0 ) 2 /(1 + (cos γ 0 ) 2 ] (≈ 109.5° for γ 0 = 150°) and augmenting γ m3,7 from 0° to 180°−sin −1 [(sin γ 0 ) 2 /(1 + (cos γ 0 ) 2 ] (≈ 70.5° for γ 0 = 150°). Lastly, for ③ → ④ → ⑤ , we can simultaneously transfigure links #2 and #4 as 8R-looped rigid linkage with kinematics as γ m1,5 = sin −1 [(sin γ m2 ) 2 /(1 + (cos γ m2 ) 2 ], γ m3,7 = 180°−sin −1 [(sin γ m2 ) 2 /(1 + (cos γ m2 ) 2 ] (γ m2 reducing from γ 0 to 90°) while γ m2 = γ m4 = γ m6 = γ m8 (see Supplementary Note 6 ) to reach shape M 13 . Moreover, as illustrated in Fig. 4e , vi that displays sequential and local kinematic features, we note that the reconfiguration kinematics from shape M 15 to M 21 by bypassing shape M 25 (Fig. 4e , i–v) are much simpler with only linear angle relationships.
Inverse design to imitate target shapes
Inverse design to imitate target shapes for special application scenarios can also be accessible for our hierarchical structures. However, the imitating process of our inverse design is different from previous designs by presetting material/structural patterns to purposely retain the target shapes. Our inverse design method is based on the selection algorithm from the reconfigured shape library by following several steps.
First is to build a database for the configuration library. Each cube can be treated as a spatial voxelated pixel with its geometrical center represented by a vector. Then, we can use a matrix to characterize a morphed shape, where the spatial positions of composed cubes are described by their corresponding vectors. For example, for all the combinatorically designed level-2 structures shown in Supplementary Fig. 5 , for one special design k , all its reconfigured shapes can be summarized into:
where M kn represent the mathematically expressed forms of the n th reconfigured shapes in the transition tree for the k th combinatorically designed level-2 structures.
Second is to compose all the combinatorically designed level-2 structures into the database matrix D in the form of:
where z stands for the maximum number of reconfigured shapes by the k th level-2 structure.
Third is to discretize the target shape into cube-shaped voxelated pixels and mathematically convert it into a mathematical matrix T .
Last is to find the shapes in the database that match for the target shape by comparing the matrix T with the components of database matrix, i.e., D ij . There are two criterions to find out the optimal imitated shape: (1) find the smallest value of the error function Errf defined as:
wherein || || represent the mode of matrix and usually \({\Vert {{{\bf{T}}}}-{{{{\bf{D}}}}}_{ij}\Vert }_{\max }\) is determined as \(\Vert {{{\bf{T}}}}\Vert+{\Vert {{{{\bf{D}}}}}_{ij}\Vert }_{\max }\) for simplicity. (2) The conditions that guarantee the imitated shapes whose cube pixels are with approximately the same absolute spatial positions with the target shape, i.e.:
Finally, we can obtain the most approximately imitated shape M km from the database. The inverse design method is briefly summarized in Supplementary Fig. 25 .
Simulation by customized software
A model has been developed for simulation in ROS-Gazebo (Supplementary Figs. 20 and 21 and Supplementary Movies 5 and 8 ). For simplicity, a single design composed of the four lateral faces of a cube is used to model every module of the robot. The connections between the modules are modeled as revolute joints (either passive or actuated). Additional blocks are used to replicate the positions and masses of the motors in the real system. Kinematic constraints are implemented to model the robot as a closed kinematic chain.
Data availability
The authors declare that the data supporting the findings of this study are available within the article and its Supplementary Information files. Source data are provided with this paper.
Code availability
The code used for the analyses is deposited via Zenodo at https://doi.org/10.5281/zenodo.12690922 .
Hanlon, R. T., Conroy, L.-A. & Forsythe, J. W. Mimicry and foraging behaviour of two tropical sand-flat octopus species off North Sulawesi, Indonesia. Biol. J. Linn. Soc. 93 , 23–38 (2008).
Article Google Scholar
Wells, M. J. Octopus: Physiology and Behaviour of an Advanced Invertebrate (Springer Science & Business Media, 2013).
Hwang, D. et al. Shape morphing mechanical metamaterials through reversible plasticity. Sci. Robot. 7 , eabg2171 (2022).
Article ADS PubMed Google Scholar
Chi, Y. et al. Bistable and multistable actuators for soft robots: structures, materials, and functionalities. Adv. Mater. 34 , 2110384 (2022).
Article CAS Google Scholar
Ford, M. J. et al. A multifunctional shape-morphing elastomer with liquid metal inclusions. Proc. Natl Acad. Sci. USA 116 , 21438–21444 (2019).
Article ADS CAS PubMed PubMed Central Google Scholar
Liu, K., Hacker, F. & Daraio, C. Robotic surfaces with reversible, spatiotemporal control for shape morphing and object manipulation. Sci. Robot. 6 , eabf5116 (2021).
Article PubMed Google Scholar
You, Z. & Pellegrino, S. Foldable bar structures. Int. J. Solids Struct. 34 , 1825–1847 (1997).
Leveziel, M., Haouas, W., Laurent, G. J., Gauthier, M. & Dahmouche, R. MiGriBot: a miniature parallel robot with integrated gripping for high-throughput micromanipulation. Sci. Robot. 7 , eabn4292 (2022).
You, Z. & Chen, Y. Motion Structures: Deployable Structural Assemblies of Mechanisms (Taylor & Francis, 2012).
Chen, Y., You, Z. & Tarnai, T. Threefold-symmetric Bricard linkages for deployable structures. Int. J. Solids Struct. 42 , 2287–2301 (2005).
Félix, D., Branco, J. M. & Feio, A. Temporary housing after disasters: a state of the art survey. Habitat Int. 40 , 136–141 (2013).
Lang, R. J., Tolman, K. A., Crampton, E. B., Magleby, S. P. & Howell, L. L. A review of thickness-accommodation techniques in origami-inspired engineering. Appl. Mech. Rev . 70 , 010805 (2018).
Gao, W., Huo, K., Seehra, J. S., Ramani, K. & Cipra, R. J. in 2014 IEEE/RSJ International Conference on Intelligent Robots and Systems 4598–4604 (IEEE, 2014).
Callens, S. J. & Zadpoor, A. A. From flat sheets to curved geometries: origami and kirigami approaches. Mater. Today 21 , 241–264 (2018).
Filipov, E. T., Tachi, T. & Paulino, G. H. Origami tubes assembled into stiff, yet reconfigurable structures and metamaterials. Proc. Natl Acad. Sci. USA 112 , 12321–12326 (2015).
Dudte, L. H., Vouga, E., Tachi, T. & Mahadevan, L. Programming curvature using origami tessellations. Nat. Mater. 15 , 583–588 (2016).
Article ADS CAS PubMed Google Scholar
Meloni, M. et al. Engineering origami: a comprehensive review of recent applications, design methods, and tools. Adv. Sci. 8 , 2000636 (2021).
Tachi, T. Rigid-foldable thick origami. Origami 5 , 253–264 (2011).
Tao, J., Khosravi, H., Deshpande, V. & Li, S. Engineering by cuts: how kirigami principle enables unique mechanical properties and functionalities. Adv. Sci. 10 , 2204733 (2023).
Bertoldi, K., Vitelli, V., Christensen, J. & Van Hecke, M. Flexible mechanical metamaterials. Nat. Rev. Mater. 2 , 1–11 (2017).
Reis, P. M., López Jiménez, F. & Marthelot, J. Transforming architectures inspired by origami. Proc. Natl Acad. Sci. USA 112 , 12234–12235 (2015).
Chen, Y., Peng, R. & You, Z. Origami of thick panels. Science 349 , 396–400 (2015).
Rus, D. & Vona, M. Crystalline robots: self-reconfiguration with compressible unit modules. Auton. Robots 10 , 107–124 (2001).
Murata, S. et al. M-TRAN: self-reconfigurable modular robotic system. IEEE/ASME Trans. Mechatron. 7 , 431–441 (2002).
Seo, J., Paik, J. & Yim, M. Modular reconfigurable robotics. Annu. Rev. Control Robot. Auton. Syst. 2 , 63–88 (2019).
Belke, C. H. & Paik, J. Mori: a modular origami robot. IEEE/ASME Trans. Mechatron. 22 , 2153–2164 (2017).
Zykov, V., Mytilinaios, E., Adams, B. & Lipson, H. Self-reproducing machines. Nature 435 , 163–164 (2005).
Li, S. et al. Particle robotics based on statistical mechanics of loosely coupled components. Nature 567 , 361–365 (2019).
Melancon, D., Gorissen, B., García-Mora, C. J., Hoberman, C. & Bertoldi, K. Multistable inflatable origami structures at the metre scale. Nature 592 , 545–550 (2021).
Rus, D. & Tolley, M. T. Design, fabrication and control of origami robots. Nat. Rev. Mater. 3 , 101–112 (2018).
Article ADS Google Scholar
Suzuki, H. & Wood, R. J. Origami-inspired miniature manipulator for teleoperated microsurgery. Nat. Mach. Intell. 2 , 437–446 (2020).
Pellegrino, S. Large retractable appendages in spacecraft. J. Spacecr. Rockets 32 , 1006–1014 (1995).
Puig, L., Barton, A. & Rando, N. A review on large deployable structures for astrophysics missions. Acta Astronaut. 67 , 12–26 (2010).
Xia, X., Spadaccini, C. M. & Greer, J. R. Responsive materials architected in space and time. Nat. Rev. Mater. 7 , 683–701 (2022).
Article ADS PubMed PubMed Central Google Scholar
Bai, Y. et al. A dynamically reprogrammable surface with self-evolving shape morphing. Nature 609 , 701–708 (2022).
Li, Y. & Yin, J. Metamorphosis of three-dimensional kirigami-inspired reconfigurable and reprogrammable architected matter. Mater. Today Phys. 21 , 100511 (2021).
Pellegrino, S. in Deployable Structures 1–35 (Springer, 2001).
Overvelde, J. T., Weaver, J. C., Hoberman, C. & Bertoldi, K. Rational design of reconfigurable prismatic architected materials. Nature 541 , 347–352 (2017).
Overvelde, J. T. et al. A three-dimensional actuated origami-inspired transformable metamaterial with multiple degrees of freedom. Nat. Commun. 7 , 1–8 (2016).
Felton, S., Tolley, M., Demaine, E., Rus, D. & Wood, R. A method for building self-folding machines. Science 345 , 644–646 (2014).
Wang, R., Song, Y. & Dai, J. S. Reconfigurability of the origami-inspired integrated 8R kinematotropic metamorphic mechanism and its evolved 6R and 4R mechanisms. Mech. Mach. Theory 161 , 104245 (2021).
Yang, Y., Zhang, X., Maiolino, P., Chen, Y. & You, Z. Linkage-based three-dimensional kinematic metamaterials with programmable constant Poisson’s ratio. Mater. Des. 233 , 112249 (2023).
Lee, D.-Y., Kim, J.-K., Sohn, C.-Y., Heo, J.-M. & Cho, K.-J. High-load capacity origami transformable wheel. Sci. Robot. 6 , eabe0201 (2021).
Cho, Y. et al. Engineering the shape and structure of materials by fractal cut. Proc. Natl Acad. Sci. USA 111 , 17390–17395 (2014).
Coulais, C., Sabbadini, A., Vink, F. & van Hecke, M. Multi-step self-guided pathways for shape-changing metamaterials. Nature 561 , 512–515 (2018).
Meza, L. R. et al. Resilient 3D hierarchical architected metamaterials. Proc. Natl Acad. Sci. USA 112 , 11502–11507 (2015).
Aizenberg, J. et al. Skeleton of Euplectella sp.: structural hierarchy from the nanoscale to the macroscale. Science 309 , 275–278 (2005).
Miyashita, S., Guitron, S., Li, S. & Rus, D. Robotic metamorphosis by origami exoskeletons. Sci. Robot. 2 , eaao4369 (2017).
Coulais, C., Teomy, E., de Reus, K., Shokef, Y. & van Hecke, M. Combinatorial design of textured mechanical metamaterials. Nature 535 , 529–532 (2016).
Whitley, D. A genetic algorithm tutorial. Stat. Comput. 4 , 65–85 (1994).
Howell, L. L. in 21st Century Kinematics: The 2012 NSF Workshop 189–216 (Springer, 2013).
Download references
Acknowledgements
J.Y. acknowledges the funding support from NSF (CMMI-2005374 and CMMI-2126072). H.S. acknowledges the funding support from NSF 2231419. The authors acknowledge the helpful discussions with Dr. K. Bertoldi and Dr. M. Yim.
Author information
These authors contributed equally: Yanbin Li, Antonio Di Lallo.
Authors and Affiliations
Department of Mechanical and Aerospace Engineering, North Carolina State University, Raleigh, NC, 27606, USA
Yanbin Li, Antonio Di Lallo, Junxi Zhu, Yinding Chi, Hao Su & Jie Yin
Lab of Biomechatronics and Intelligent Robotics, Joint NCSU/UNC Department of Biomedical Engineering, North Carolina State University, Raleigh, NC, USA
University of North Carolina at Chapel Hill, Chapel Hill, NC, USA
You can also search for this author in PubMed Google Scholar
Contributions
Y.L. and J.Y. proposed the idea. Y.L. conducted theoretical and numerical calculations. Y.L. and Y.C. designed and performed experiments on shape-morphing prototypes. A.D. and J.Z. designed and performed experiments on untethered actuation of shape-morphing prototypes. Y.L., A.D., H.S. and J.Y. wrote the paper. H.S. and J.Y. supervised the research. All the authors contributed to the discussion, data analysis, and editing of the manuscript.
Corresponding authors
Correspondence to Yanbin Li , Hao Su or Jie Yin .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Peer review
Peer review information.
Nature Communications thanks Evgueni Filipov and Damiano Pasini for their contribution to the peer review of this work. A peer review file is available.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Supplementary information, peer review file, description of additional supplementary files, supplementary movie 1, supplementary movie 2, supplementary movie 3, supplementary movie 4, supplementary movie 5, supplementary movie 6, supplementary movie 7, supplementary movie 8, source data, source data, rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Li, Y., Di Lallo, A., Zhu, J. et al. Adaptive hierarchical origami-based metastructures. Nat Commun 15 , 6247 (2024). https://doi.org/10.1038/s41467-024-50497-5
Download citation
Received : 28 November 2023
Accepted : 12 July 2024
Published : 26 July 2024
DOI : https://doi.org/10.1038/s41467-024-50497-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.

- Biodiversity
- Cities & society
- Land & water
- All research news
- All research topics
- Learning experiences
- Programs & partnerships
- All school news
- All school news topics
- In the media
- For journalists
Bronze Age technology could aid switch to clean energy
Stanford research finds the cost-effective thermal properties that make “firebricks” suitable for energy storage could speed up the world’s transition to renewable energy at low cost.

Technology with roots going back to the Bronze Age may offer a fast and inexpensive solution to help achieve the United Nations climate goal of net zero emissions by 2050, according to recent Stanford-led research in PNAS Nexus .
The technology involves assembling heat-absorbing bricks in an insulated container, where they can store heat generated by solar or wind power for later use at the temperatures required for industrial processes. The heat can then be released when needed by passing air through channels in the stacks of “firebricks,” thus allowing cement, steel, glass, and paper factories to run on renewable energy even when wind and sunshine are unavailable.
These systems, which several companies have recently begun to commercialize for industrial heat storage, are a form of thermal energy storage. The bricks are made from the same materials as the insulating bricks that lined primitive kilns and iron-making furnaces thousands of years ago. To optimize for heat storage instead of insulation, the materials are combined in different amounts.
Batteries can store electricity from renewable sources and provide electricity to generate heat on demand. “The difference between firebrick storage and battery storage is that the firebricks store heat rather than electricity and are one-tenth the cost of batteries,” said lead study author Mark Z. Jacobson , a professor of civil and environmental engineering in the Stanford Doerr School of Sustainability and School of Engineering . “The materials are much simpler too. They are basically just the components of dirt.”
High heat storage
Many industries require high-temperature heat for manufacturing. Temperatures in factories need to reach at least 1,300 degrees Celsius (nearly 2,400 degrees Fahrenheit) to produce cement, and 1,000 C (about 1,800 F) or hotter for glass, iron, and steelmaking. Today, about 17% of all carbon dioxide emissions worldwide stem from burning fossil fuels to produce heat for industrial processes, according to Jacobson and co-author Daniel Sambor ’s calculations. Generating industrial heat from renewable sources could all but eliminate these emissions.
“By storing energy in the form closest to its end use, you reduce inefficiencies in energy conversion,” said Sambor, a postdoctoral scholar in civil and environmental engineering. “It’s often said in our field that ‘if you want hot showers, store hot water, and if you want cold drinks, store ice’; so this study can be summarized as ‘if you need heat for industry, store it in firebricks.’”
Substantial savings
The researchers set out to examine the impact of using firebricks to store most industrial process heat in 149 countries in a hypothetical future where each country has transitioned to wind, geothermal, hydropower, and solar for all energy purposes. The 149 countries are responsible for 99.75% of global carbon dioxide emissions from fossil fuels. “Ours is the first study to examine a large-scale transition of renewable energy with firebricks as part of the solution,” Jacobson said. “We found that firebricks enable a faster and lower-cost transition to renewables, and that helps everyone in terms of health, climate, jobs, and energy security.”
The team used computer models to compare costs, land needs, health impacts, and emissions involved in two scenarios for a hypothetical future where 149 countries in 2050 are using renewables for all energy purposes. In one scenario, firebricks provide 90% of industrial process heat. In the other, there’s zero adoption of firebricks or other forms of thermal energy storage for industrial processes. In the no-firebrick scenario, the researchers assumed heat for industrial processes would come instead from electric furnaces, heaters, boilers, and heat pumps, with batteries used to store electricity for those technologies.
The researchers found the scenario with firebricks could cut capital costs by $1.27 trillion across the 149 countries compared with the scenario with no firebrick storage, while reducing demand for energy from the grid and the need for energy storage capacity from batteries.
Clean energy for cleaner air
Solutions for accelerating the transition to clean energy are also connected to human health. Previous research has shown that air pollution from burning fossil fuels causes millions of early deaths each year. “Every bit of combustion fuels we replace with electricity reduces that air pollution,” Jacobson said. “And because there is a limited amount of money to transition at a high speed, the lower the cost to the overall system, the faster we can implement it.”
Jacobson has spent his career understanding air pollution and climate problems and developing energy plans for countries, states, and cities to solve these problems. But his focus on firebricks is relatively new, inspired by a desire to identify effective solutions that could be adopted quickly.
“Imagine if we propose an expensive and difficult method of transitioning to renewable electricity – we’d have very few takers. But, if this will save money compared with a previous method, it will be implemented more rapidly,” he said. “What excites me is that the impact is very large, whereas a lot of technologies that I’ve looked at, they have marginal impacts. Here I can see a substantial benefit at low cost from multiple angles, from helping to reduce air pollution mortality to making it easier to transition the world to clean renewables.”
Jacobson is also a senior fellow at the Stanford Woods Institute for the Environment and the Precourt Institute for Energy .
Sambor was funded by the Engineer Research and Development Center.
Media Contacts
Mark z. jacobson, josie garthwaite, explore more.

Stanford’s Sustainability Accelerator adds new targets
The Sustainability Accelerator in the Stanford Doerr School of Sustainability will support work in new areas including energy, climate adaptation, industry, and more.
- School planning

New climate and sustainability research efforts will focus on eight ‘Solution Areas’
The Stanford Doerr School of Sustainability will establish new research initiatives under topics including climate, water, energy, food, nature, and cities.

Solution Areas and research funding
A message from school leadership announcing solutions-oriented and scale-focused research funding opportunities to address pressing sustainability challenges.
Princeton University
White paper maps the course of blockchain research.
By The Office of Engineering Communication
August 7, 2024

In a series of conferences, the DeCenter has convened top federal regulators, experts in human rights, engineering, public policy, economics and ethics to identify and refine topics for research.
Hailing the promise and perils of blockchain, Princeton’s center for blockchain technology has released a comprehensive white paper charting the course of research into the technology. The paper focuses on three areas – technology, applications, and implications for society – and frames a series of research questions around the topics.
Collaboration across the broad reach of the university’s research community is central to the effort, said Jaswinder Pal (J.P.) Singh , the director of the Center for the Decentralization of Power through Blockchain Technology, known as the DeCenter.
“We take a fundamentally interdisciplinary approach to issues around blockchains and the decentralization of trust and power,” said Singh, Princeton’s Professor of Computer Science, Technology and Societal Change. “We believe the technology has substantial promise to reshape a number of areas in finance, business and society, but the applications are not yet well understood, and the inherently financialized nature of the area creates new societal implications and risks.”
The white paper, Decentralizing Power Through Blockchains: Key Research Questions Across Disciplines , is available on the center’s website .
Singh said the uses that technologists and entrepreneurs envision for blockchain technology could pose challenges for governments and international organizations.
“For these reasons, resolving some of the most important questions requires interdisciplinary collaboration across computer science, engineering, economics, political science, ethics and other social sciences and the humanities. The goal of this white paper is to identify some of these key questions,” he said. “At a moment when tremendous power has accrued to centralized institutions and corporations, and when citizens around the world are losing trust in their legacy institutions and in one another, it is urgent to understand both the power and limitations of these new technical, economic and social protocols that might distribute power and control differently.”
Blockchain combines cryptography and economic incentives to create a widely distributed record of agreed transactions to achieve trust without the need for central authority. The technology’s most widely known use is to create Bitcoin and similar cryptocurrencies, but researchers say it also offers potential uses in other areas of business, finance, government and society. Princeton University created the DeCenter to help understand the technology and study its societal and policy impacts.
The DeCenter has involved researchers, such as Matt Weinberg, an associate professor of computer science who is developing new algorithms related to blockchain technology, and Prateek Mittal, a professor of electrical and computer engineering who has studied efforts to create decentralized networks . The center has also turned to experts in philosophy such as Andrew Chignell, the Laurance S. Rockefeller Professor of Religion and the University Center for Human Values, who is working to understand the ethical implication of the technology, and in political science , such as Nolan McCarty, the Susan Dod Brown Professor of Politics and Public Affairs.
In a series of conferences, the DeCenter has convened top federal regulators, experts in human rights, engineering, public policy, economics and ethics to identify and refine topics for research. A central focus has been to foster collaboration across disciplines to identify key questions and areas that blockchain technology can address.
The Center plans to continue the collaborative work with its next conference scheduled for the spring of 2025.
Related News

Margaret Martonosi on the National Science Foundation and the value of public service

Pennsylvania policymakers underestimate public support for solar projects, survey says

Since 2008, innovation funds have fostered research in AI fairness, sustainable agriculture, drug discovery and more

Transforming troublesome seaweed into a feedstock of the future

Junior faculty awards recognize outstanding teaching and research

Meet SPOT the 'bot: Course explores learning to live with robots

Jaswinder Singh

Matt Weinberg

Prateek Mittal
Related departments and centers.

Computer Science

Electrical and Computer Engineering

Center for Decentralization of Power Through Blockchain Technology (DeCenter)
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Sustainability
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Precision home robots learn with real-to-sim-to-real
Press contact :.
Previous image Next image
At the top of many automation wish lists is a particularly time-consuming task: chores. The moonshot of many roboticists is cooking up the proper hardware and software combination so that a machine can learn “generalist” policies (the rules and strategies that guide robot behavior) that work everywhere, under all conditions. Realistically, though, if you have a home robot, you probably don’t care much about it working for your neighbors. MIT Computer Science and Artificial Intelligence Laboratory (CSAIL) researchers decided, with that in mind, to attempt to find a solution to easily train robust robot policies for very specific environments.
“We aim for robots to perform exceptionally well under disturbances, distractions, varying lighting conditions, and changes in object poses, all within a single environment,” says Marcel Torne Villasevil, MIT CSAIL research assistant in the Improbable AI lab and lead author on a recent paper about the work. “We propose a method to create digital twins on the fly using the latest advances in computer vision. With just their phones, anyone can capture a digital replica of the real world, and the robots can train in a simulated environment much faster than the real world, thanks to GPU parallelization. Our approach eliminates the need for extensive reward engineering by leveraging a few real-world demonstrations to jump-start the training process.”

Taking your robot home
RialTo, of course, is a little more complicated than just a simple wave of a phone and (boom!) home bot at your service. It begins by using your device to scan the target environment using tools like NeRFStudio, ARCode, or Polycam. Once the scene is reconstructed, users can upload it to RialTo’s interface to make detailed adjustments, add necessary joints to the robots, and more.
The refined scene is exported and brought into the simulator. Here, the aim is to develop a policy based on real-world actions and observations, such as one for grabbing a cup on a counter. These real-world demonstrations are replicated in the simulation, providing some valuable data for reinforcement learning. “This helps in creating a strong policy that works well in both the simulation and the real world. An enhanced algorithm using reinforcement learning helps guide this process, to ensure the policy is effective when applied outside of the simulator,” says Torne.
Testing showed that RialTo created strong policies for a variety of tasks, whether in controlled lab settings or more unpredictable real-world environments, improving 67 percent over imitation learning with the same number of demonstrations. The tasks involved opening a toaster, placing a book on a shelf, putting a plate on a rack, placing a mug on a shelf, opening a drawer, and opening a cabinet. For each task, the researchers tested the system’s performance under three increasing levels of difficulty: randomizing object poses, adding visual distractors, and applying physical disturbances during task executions. When paired with real-world data, the system outperformed traditional imitation-learning methods, especially in situations with lots of visual distractions or physical disruptions.
“These experiments show that if we care about being very robust to one particular environment, the best idea is to leverage digital twins instead of trying to obtain robustness with large-scale data collection in diverse environments,” says Pulkit Agrawal, director of Improbable AI Lab, MIT electrical engineering and computer science (EECS) associate professor, MIT CSAIL principal investigator, and senior author on the work.
As far as limitations, RialTo currently takes three days to be fully trained. To speed this up, the team mentions improving the underlying algorithms and using foundation models. Training in simulation also has its limitations, and currently it’s difficult to do effortless sim-to-real transfer and simulate deformable objects or liquids.
The next level
So what’s next for RialTo’s journey? Building on previous efforts, the scientists are working on preserving robustness against various disturbances while improving the model’s adaptability to new environments. “Our next endeavor is this approach to using pre-trained models, accelerating the learning process, minimizing human input, and achieving broader generalization capabilities,” says Torne.
“We’re incredibly enthusiastic about our 'on-the-fly' robot programming concept, where robots can autonomously scan their environment and learn how to solve specific tasks in simulation. While our current method has limitations — such as requiring a few initial demonstrations by a human and significant compute time for training these policies (up to three days) — we see it as a significant step towards achieving 'on-the-fly' robot learning and deployment,” says Torne. “This approach moves us closer to a future where robots won’t need a preexisting policy that covers every scenario. Instead, they can rapidly learn new tasks without extensive real-world interaction. In my view, this advancement could expedite the practical application of robotics far sooner than relying solely on a universal, all-encompassing policy.”
“To deploy robots in the real world, researchers have traditionally relied on methods such as imitation learning from expert data, which can be expensive, or reinforcement learning, which can be unsafe,” says Zoey Chen, a computer science PhD student at the University of Washington who wasn’t involved in the paper. “RialTo directly addresses both the safety constraints of real-world RL [robot learning], and efficient data constraints for data-driven learning methods, with its novel real-to-sim-to-real pipeline. This novel pipeline not only ensures safe and robust training in simulation before real-world deployment, but also significantly improves the efficiency of data collection. RialTo has the potential to significantly scale up robot learning and allows robots to adapt to complex real-world scenarios much more effectively.”
"Simulation has shown impressive capabilities on real robots by providing inexpensive, possibly infinite data for policy learning,” adds Marius Memmel, a computer science PhD student at the University of Washington who wasn’t involved in the work. “However, these methods are limited to a few specific scenarios, and constructing the corresponding simulations is expensive and laborious. RialTo provides an easy-to-use tool to reconstruct real-world environments in minutes instead of hours. Furthermore, it makes extensive use of collected demonstrations during policy learning, minimizing the burden on the operator and reducing the sim2real gap. RialTo demonstrates robustness to object poses and disturbances, showing incredible real-world performance without requiring extensive simulator construction and data collection.”
Torne wrote this paper alongside senior authors Abhishek Gupta, assistant professor at the University of Washington, and Agrawal. Four other CSAIL members are also credited: EECS PhD student Anthony Simeonov SM ’22, research assistant Zechu Li, undergraduate student April Chan, and Tao Chen PhD ’24. Improbable AI Lab and WEIRD Lab members also contributed valuable feedback and support in developing this project.
This work was supported, in part, by the Sony Research Award, the U.S. government, and Hyundai Motor Co., with assistance from the WEIRD (Washington Embodied Intelligence and Robotics Development) Lab. The researchers presented their work at the Robotics Science and Systems (RSS) conference earlier this month.
Share this news article on:
Related links.
- RialTo Project Page
- Pulkit Agrawal
- Marcel Torne Villasevil
- Computer Science and Artificial Intelligence Laboratory (CSAIL)
- MIT-IBM Watson AI Lab
- Department of Electrical Engineering and Computer Science
Related Topics
- Artificial intelligence
- Computer vision
- Personal robotics
- Electrical Engineering & Computer Science (eecs)
Related Articles
Multiple AI models help robots execute complex plans more transparently

New method uses crowdsourced feedback to help train robots

A more effective way to train machines for uncertain, real-world situations
Previous item Next item
More MIT News
A new model offers robots precise pick-and-place solutions
Read full story →

With sustainable cement, startup aims to eliminate gigatons of CO₂

3 Questions: Preparing students in MIT’s naval ROTC program

Going Dutch on climate

Helping robots practice skills independently to adapt to unfamiliar environments

Dimitris Bertsimas named vice provost for open learning
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram

IMAGES
VIDEO
COMMENTS
Abstract: Third generation (3G) mobile networks faces a ne w rival; so called 4G. An. astonishingly new network may be even more profitable. The goal of 4G is to replace the. current proliferation ...
the first commercia l 3G network in Japa n in Oct. 2001. 4G: 4G, the fourth-generation of wireless service, is an. enhancement from 3G a nd is presently the most extensive, widespread, expedit ...
Driven by the growing demand for quality assured mobility; new promising technologies have emerged, such as 4G and 5G networks, in order to meet users' needs. Indeed, 4G networks unceasingly seek to improve the offered services and to guarantee a certain level of quality of service (QoS) for users while moving with high speeds. On his side, 5G standard is on its way. Promising superfast speeds ...
This research paper presents an overview of 4G technology trends in the wireless technology market, a comparative overview of 4G v/s previous generation technologies it's architecture and its ...
Abstract. Based on the analysis of 4G communication network structure and key technologies, this paper expounds the 4 (6) communication structure, and studies the basic characteristics of 4G communication network, including: high speed, large capacity, the coexistence of different types of users, strong compatibility and flexibility, and the ...
The purpose of the research is a detailed study on 3G, 4G, and 5G network technologies. ... 3G and 4G technologies will difficult to handle the mobile traffics. 5G subscriptions are expecting to be commercial technology from 2020 onwards and it can assure 5G is capable of managing the mobile traffic. ... Papers. 6339. Full. Text Views. Alerts ...
Challenges. Hassan Gobjuka. Verizon. 919 hidden Ridge. Irving, TX 75038. Abstract. With the major wireless service providers planning to start deployment of 4G wireless networks by mid 2010, research and industry communities are racing against time to find solutions for some of the prominent still open. issues in 4G networks.
This paper explores the network architecture of 4G (4th Generation) and LTE (Long Term Evolution) wireless technologies, the mobile standards used by these technologies and key features, and the future of mobile communications in the longer term. — he earlier evolution of broadband wireless technologies is the consequence of growing demand in the world for best ever mobile Internet access ...
In this work, we provide a summary of several wireless telecommunications technologies, in particular, 4G, 5G, and 6G Networks, and a detailed comparison between them. Published in: 2022 5th International Conference on Contemporary Computing and Informatics (IC3I) Date of Conference: 14-16 December 2022. Date Added to IEEE Xplore: 22 March 2023.
In addition, the paper highlights the review of the technologies implemented for 4G and 5G mobile networks. Cellular networks have grown and improved immensely in recent years, in terms of customers, data speeds, outreached and other aspects. In both 4G and 5G technology, the mobile consumer has taken precedence above all others.
This survey paper contains a comprehensive overview of all the main key technologies that play an important role in the different releases spanned by LTE-Advanced so far. It also includes new concepts currently under discussion at 3GPP and research challenges that will pave the way towards B4G. The remainder of this paper is organized as follows.
The 4G wireless system, its architecture, security services, benefits and challenges of 4G wireless technology, assures the high mobility with high level speed of data rates and high capacity IP based services and application. . ABSTRACT Mobile Communication has been developed rapidly since last few decades. The growth of the wireless broadband technologies in the modern years was the answer ...
This paper discusses the different communication technologies present in the current communication system and coming in future 2020. The next evolution in the communication industry is coming 5G communication system that will start in approx. 2020. ... 4G, 5G, and 6G technology. The highest data rate of 6G is 70 Gbps, whereas the lowest data ...
This paper explores what 4G network technology actually is , along with some of the propositions in order to fully figure out the advantages and challenges of effectively implementing 4G. Index Terms— 4G network technologies, LTE, LTE Advanced, MIMO, WiMAX, wireless network, WiMAX2.0 —————————— ————————— 1.
The existence of 4G technologies is the indicator or valid proof of the rapid and massive growth of wireless communication technologies, which is propagated through 1G, 2G and 3G technology and 5G as an upcoming technology.4G networks are introduced with the main intention of customization of a flexible and ubiquitous service provision in the middle of 2012 based on digital broadband packet ...
2. Network Demands in the 4G-to-5G Evolution The 3rd Generation Partnership Project has developed and presented to the public the new LTE technology (Long Term Evolution) which is the basis for 4G. After the first workshop held in 2004 on the topic of the improvement of the 3G system, in the period that followed, different research-oriented
This paper is focused on the specification of future generations of wireless mobile communication networks. The paper throws light on the evolution and development of various generations of mobile wireless technology along with their significance and advantages of one over the other. 5G technologies will change the way most high-bandwidth users access their phones.
1. Introduction. Most recently, in three decades, rapid growth was marked in the field of wireless communication concerning the transition of 1G to 4G [1,2].The main motto behind this research was the requirements of high bandwidth and very low latency. 5G provides a high data rate, improved quality of service (QoS), low-latency, high coverage, high reliability, and economically affordable ...
Through a journey which started. about 40 years ago, cellular commu-. nications have experienced dramatic. changes and upgrades from 1G to 4G. Those transitions include the system. change from ...
Abstract. 4 G mobile networks have evolved to meet the ever-increasing demand and requirements of users. 4 G will provide comprehensive IP solutions, allowing users to access voice, data, and streaming multimedia services at any time, from any location. Nonetheless, this transition will introduce new vulnerabilities and threats to service ...
market. Under these circumstances, this paper will present about the current trends and its underlying technologies to implement the 4G mobile technology. This paper also shows some of the possible scenarios that will benefit the 4th generation technology. Keywords 4G Mobile Technologies, 3GPP Long Term Evolution, WiMAX,
II. 4g And 5g Difference a) First and foremost, while the LTE-based 4G networks are going through a rapid deployment, 5G networks mostly comprise of research papers and pilot projects. b) Wireless networks till 4G mostly focused on the availability of raw bandwidth, while 5G is aiming on
Consensus is an AI-powered academic search engine that helps you quickly find relevant research papers. Simply input your research questions and enable the 'Synthesize' toggle. Consensus then synthesizes insights from a vast pool of academic papers and presents results in a user-friendly format, with each tile representing a single paper.
Hierarchical origami-based shape-morphing structures with combinatorial design capability. Figure 2a-c and Supplementary Figs. 1-3 illustrate the hierarchical approach employed to construct a ...
standard. 5G will provide better speeds and coverage than the current 4 G. 5G operates with a 5 GHz signal and. is set to offer speeds of up to 1 Gb/s for tens of connections or tens of Mb/s for ...
Technology with roots going back to the Bronze Age may offer a fast and inexpensive solution to help achieve the United Nations climate goal of net zero emissions by 2050, according to recent Stanford-led research in PNAS Nexus.. The technology involves assembling heat-absorbing bricks in an insulated container, where they can store heat generated by solar or wind power for later use at the ...
The paper focuses on three areas - technology, applications, and implications for society - and frames a series of research questions around the topics. Collaboration across the broad reach of the university's research community is central to the effort, said Jaswinder Pal (J.P.) Singh , the director of the Center for the Decentralization ...
This work was supported, in part, by the Sony Research Award, the U.S. government, and Hyundai Motor Co., with assistance from the WEIRD (Washington Embodied Intelligence and Robotics Development) Lab. The researchers presented their work at the Robotics Science and Systems (RSS) conference earlier this month.
This research, and any access to it, is intended only for "wholesale clients" within the meaning of the Australian Corporations Act, unless otherwise agreed by Goldman Sachs. In producing research reports, members of Global Investment Research of Goldman Sachs Australia may attend site visits and other meetings hosted by the companies and other
The ChatGPT artificial intelligence technology generates answers to questions based on an outdated set of data and information downloaded from selected websites in 2021.