- How it works

Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Computer Networking Dissertation Topics
Published by Carmen Troy at January 5th, 2023 , Revised On August 16, 2023
A dissertation is an essential aspect of completing your degree program. Whether you are pursuing your master’s or are enrolled in a PhD program, you will not be awarded a degree without successfully submitting a thesis. To ensure that your thesis is submitted successfully without any hindrances, you should first get your topic and dissertation outline approved by your professor. When approving, supervisors focus on a lot of aspects. However, relevance, recency, and conciseness of your topic play a huge role in accepting or rejecting your topic.
As a computer networking student, you have a variety of networking topics to choose from. With the field evolving with each passing day, you must ensure that your thesis covers recent computer networking topics and explores a relevant problem or issue. To help you choose the right topic for your dissertation, here is a list of recent and relevant computer networking dissertation topics.
2022 Computer Networking Dissertation Topics
Topic 1: an evaluation of the network security during machine to machine communication in iot.
Research Aim: The research aims to evaluate the network security issues associated with M2M communication in IoT.
Objectives:
- To evaluate the factors affecting the network security of IoT devices.
- To determine the methods for increasing data integrity in M2M communication against physical tampering and unauthorised monitoring.
- To evaluate the network security issues associated with M2M communication in IoT and offer suitable recommendations for improvement.
Topic 2: An analysis of the cybersecurity challenges in public clouds and appropriate intrusion detection mechanisms.
Research Aim: The aim of the research is to analyse the cybersecurity challenges in public clouds and the appropriate intrusion detection mechanisms.
Objectives:
- To analyse the types of cybersecurity threats impacting public clouds.
- To determine some of the competent intrusion detection techniques that can be used in cloud computing.
- To investigate the cybersecurity challenges in public clouds and offer mitigating with appropriate intrusion detection techniques.
Topic 3: Investigating the impact of SaaS cloud ERP on the scalability and cost-effectiveness of business.
Research Aim: The research aims to investigate the impact of SaaS cloud ERP on the scalability and cost-effectiveness of business.
- To analyse the benefits of SaaS ERP over traditional ERP.
- To evaluate the characteristics of SaaS architecture in cloud computing and determine its varieties.
- To investigate how SaaS cloud ERP impacts business scalability and cost-effectiveness.
Topic 4: An evaluation of the requirements of cloud repatriation and the challenges associated with it.
Research Aim: The research aims to evaluate the requirements of cloud repatriation in organisations and the associated challenges
- To analyse the key factors of cloud repatriation.
- To determine the challenges associated with cloud repatriation from public clouds.
- To evaluate the need for cloud repatriation in organisations and the associated complexities
Topic 5: An examination of the security mechanisms in decentralised networks and the ways of enhancing system robustness
Research Aim: The research aims to investigate the security mechanisms in decentralised networks and the ways of enhancing system robustness.
- To analyse the concept of decentralised networks and understand its difference from centralised networks.
- To analyse the security mechanisms in decentralised networks for determining how it offers visibility and traceability.
- To investigate the security mechanisms in decentralised networks and how system robustness can be increased for better privacy and security.
Computer Networking Dissertation Topics for 2021
Exploring the importance of computer networking in today’s era.
Research Aim: Even though computer networking has been practised for a few years now, its importance has increased immensely over the past two years. A few main reasons include the use of technology by almost every business and the aim to offer customers an easy and convenient shopping experience. The main aim of this research will be to explain the concepts of computer networking, its benefits, and its importance in the current era. The research will also discuss how computer networking has helped businesses and individuals perform their work and benefit from it. The research will then specifically state examples where computer networking has brought positive changes and helped people achieve what they want.
Wireless Networks in Business Settings – An Analysis
Research Aim: Wireless networks are crucial in computer networking. They help build networks seamlessly, and once the networks are set up on a wireless network, it becomes extremely easy for the business to perform its daily activities. This research will investigate all about wireless networks in a business setting. It will first introduce the various wireless networks that can be utilized by a business and will then talk about how these networks help companies build their workflow around it. The study will analyze different wireless networks used by businesses and will conclude how beneficial they are and how they are helping the business.
Understanding Virtual Private Networks – A Deep Analysis of their Challenges
Research Aim: Private virtual networks (VPN) are extremely common today. These are used by businesses and individuals alike. This research aims to understand how these networks operate and how they help businesses build strong and successful systems and address the challenges of VPNs. A lot of businesses do not adopt virtual private networks due to the challenges that they bring. This research will address these challenges in a way that will help businesses implement VPN successfully.
A Survey of the Application of Wireless Sensor Networks
Research Aim: Wireless sensor networks are self-configured, infrastructure-less wireless networks to pass data. These networks are now extremely popular amongst businesses because they can solve problems in various application domains and possess the capacity to change the way work is done. This research will investigate where wireless sensor networks are implemented, how they are being used, and how they are performing. The research will also investigate how businesses implement these systems and consider factors when utilizing these wireless sensor networks.
Computer Network Security Attacks – Systems and Methods to Respond
Research Aim: With the advent of technology today, computer networks are extremely prone to security attacks. A lot of networks have security systems in place. However, people with nefarious intent find one way to intrude and steal data/information. This research will address major security attacks that have impacted businesses and will aim to address this challenge. Various methods and systems will be highlighted to protect the computer networks. In addition to this, the research will also discuss various methods to respond to attacks and to keep the business network protected.
Preventing a Cyberattack – How Can you Build a Powerful Computer Network?
Research Aim: Cyberattacks are extremely common these days. No matter how powerful your network is, you might be a victim of phishing or hacking. The main aim of this research will be to outline how a powerful computer network can be built. Various methods to build a safe computer network that can keep data and information will be outlined, and the study will also highlight ways to prevent a cyberattack. In addition to this, the research will talk about the steps that should be taken to keep the computer network safe. The research will conclude with the best way and system to build a powerful and safe computer network.
Types of Computer Networks: A Comparison and Analysis
Research Aim: There are different types of computer networks, including LAN, WAN, PAN, MAN, CAN, SAN, etc. This research will discuss all the various types of computer networks to help readers understand how all these networks work. The study will then compare the different types of networks and analyze how each of them is implemented in different settings. The dissertation will also discuss the type of computer networks that businesses should use and how they can utilize them for their success. The study will then conclude which computer network is the best and how it can benefit when implemented.
Detecting Computer Network Attacks by Signatures and Fast Content Analysis
Research Aim: With technological advancement, today, many computer network attacks can be detected beforehand. While many techniques are utilized for detecting these attacks, the use of signatures and fast content analysis are the most popular ones. This research will explore these techniques in detail and help understand how they can detect a computer network attack and prevent it. The research will present different ways these techniques are utilised to detect an attack and help build powerful and safe computer networks. The research will then conclude how helpful these two techniques are and whether businesses should implement them.
Overview of Wireless Network Technologies and their Role in Healthcare
Research Aim: Wireless network technologies are utilised by several industries. Their uses and benefits have helped businesses resolve many business problems and assisted them in conducting their daily activities without any hindrance. This networking topic will help explore how wireless network technologies work and will talk about their benefits. This research aims to find out how wireless technologies help businesses carry out their daily routine tasks effortlessly. For this research, the focuas will be the healthcare industry. The study will investigate how wireless network technology has helped the healthcare sector and how it has benefited them to perform their daily tasks without much effort.
Setting up a Business Communication System over a Computer Network
Research Aim: Communication is an essential aspect of every business. Employees need to communicate effectively to keep the business going. In the absence of effective communication, businesses suffer a lot as the departments are not synchronized, and the operations are haphazard. This research will explore the different ways through which network technologies help conduct smooth and effective communication within organizations. This research will conclude how wireless networks have helped businesses build effective communication systems within their organization and how they have benefited from it. It will then conclude how businesses have improved and solved major business problems with the help of these systems.
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find computer networking dissertation topics.
To find computer networking dissertation topics:
- Follow industry news and emerging technologies.
- Investigate unresolved networking challenges.
- Review recent research papers.
- Explore IoT, cybersecurity, cloud computing.
- Consider real-world applications.
- Select a topic aligned with your expertise and career aspirations.
You May Also Like
Almost every discipline requires a dissertation as a prerequisite to research. Specifically, they state what the researcher hopes to accomplish with their study. Therefore, they must be as authentic as the originals.
The Law of the EU has gained a growing amount of academic attention, especially since the UK decided to leave the union. Concerns are growing about how EU law will continue to impact the UK constitution.
Need interesting and manageable mechanical engineering dissertation topics? Here are the trending mechanical engineering dissertation titles so you can choose the most suitable one.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works

- Chancellor’s Message
Print Options
2023-24 edition, networked systems, ph.d..
The graduate program in Networked Systems is administered by faculty from two academic units: the Department of Computer Science (CS) in the Donald Bren School of Information and Computer Sciences and the Department of Electrical Engineering and Computer Science (EECS) in The Henry Samueli School of Engineering. The program offers an M.S. and a Ph.D. in Networked Systems.
The Networked Systems program provides education and research opportunities to graduate students in the areas of computer and telecommunication networks. Networked Systems include telephone, cable TV networks, wireless, mobile, ad hoc, and cellular phone networks, as well as the Internet. Networked Systems, as a field, is inherently interdisciplinary since it combines technology in software, hardware, and communications. As a result, it transcends traditional departmental boundaries. Networked Systems draws primarily from Computer Science, Computer Engineering, and Electrical Engineering. At UCI, these areas are housed in two departments: CS and EECS. The Networked Systems program unites the respective strengths of these two departments and provides integrated M.S. and Ph.D. programs in this area.
Program requirements include core, breadth, and concentration courses. Core courses are taken by all Networked Systems students and form a foundation for networking topics. Breadth courses may be selected from technical courses (including distributed systems, algorithms, data structures, operating systems, databases, random processes, and linear systems) and management and applications of technology (including educational technology, management of information technology, and social impact). Concentration courses may be selected from a long list including courses on networks, performance, middleware, communications, and operations research. Core, breadth, and concentration course lists are available on the Networked Systems website or from the Networked Systems Program Office.
Prospective graduate students apply directly to the Networked Systems program, specifying if they are pursing an M.S. or a Ph.D. Applicants who do not hold a bachelor’s degree in Computer Science, Computer Engineering, or Electrical Engineering may be required to take supplementary course work to obtain and demonstrate sufficient background in the field.
Applicants are evaluated on the basis of prior academic record and potential for creative research and teaching, as demonstrated in their application materials including official university transcripts, letters of recommendation, and statement of purpose.
Requirements
The Ph.D. requires the following 13 courses: three core courses; three courses chosen from the breadth course list, with at most two chosen from the Management and Applications of Technology list; four courses chosen from the concentration course lists, with at least one course chosen from at least three different concentrations; and three additional courses, chosen with the approval of the research advisor. Students must also complete two teaching practicum courses ( I&C SCI 399 ) and a dissertation.
Courses applied to the M.S. can also be applied to the Ph.D. Students who have taken similar graduate-level courses at another university may petition to apply these courses to the Ph.D. requirements. Ph.D. students who have served as teaching assistants, readers, or tutors at another university may petition to apply this experience toward the teaching practicum requirement. Normative time for advancement to candidacy is three years (two for students who entered with a master’s degree). Normative time for completion of the Ph.D. is six years (five for students who entered with a master’s degree), and maximum time permitted is seven years.
Send Page to Printer
Print this page.
Download Page (PDF)
The PDF will include all information unique to this page.
2023-2024 Catalogue
A PDF of the entire 2023-2024 catalogue.
- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support
- Top 5 Interesting Computer Network Research Topics
A computer network is a network of diverse computing hardware linked through different communication technologies to share various resources . The communication links of the network can be either wired (cables) or wireless (radio waves / IR signals).
This page shows you useful information on Computer Network Research Topics, Projects with Source Code, Research Areas, Project Topics, and Tools!!!
Moreover, the network can be differentiated in the characteristics of constrained resources, network structure, requests history/demand, communication technologies , and more. However, it is flexible to share resources, and it has some technical challenges in real-time development. Here, we have given you the common services that we offer for overcoming network issues.
Our Approaches and Services to Solving Computer Network Issues
- Communication technologies selection
- Communication protocols in the network
- Performing both conceptual and practical research
- Study in qualitative and quantitative aspects
- Simulation Models
- Proofs / Theorems / Prototypes Testing / Use Cases
- Experiments for Various Simulation Scenarios
- Graphical / Tabular Representation of Results
- Developing New Techniques
- Thinking Novel Ideas
- Multiple Evaluations
- IEEE Standards Refinement
The layering approach in networking is used to divide the message into various chunks . Basically, there are seven layers in the networking process where each layer has unique responsibilities. All these layers co-operatively work together to transfer the message from one end to another (i.e., source to destination ). Now, we can see the available layers and their function in sequential order.
What are the layers of computer networks?
- Physical Layer – Used for offering mechanical / electrical needs, distribute the bits through transmission medium
- Data Link Layer – Used for offering hop-to-hop distribution, arrange the bits into frames
- Network Layer – Used for offering internetworking, pass over the packets between source and destination
- Transport Layer – Used for offering error correction and process-to-process distribution
- Session Layer – Used for launching and manage temporary sessions
- Presentation Layer – Used for data translation, compression, and encryption
- Application Layer – User for users to access the network resources / services
With an aim to support wireless communications, numerous different technologies have been launched. Before selecting this technology, one should undergo deep study on which is more suitable for their computer network projects . Our research team will help you in both business/individual if you need the best guidance over that selection of innovative computer network research topics . Usually, we recommend the technology based on the requirement of your selected networking projects for final year students . For your information, here we have given you a few lists of communication technologies,
Communication Technologies in Computer Networks
- Wi-Fi and Wi-Max
- Radio Frequency Identification (RFID)
- Ultra-Wideband, Bluetooth and Zigbee
- Global Positioning System (GPS)
- Mobile Communication (4G, 5G, 5G Beyond and 6G)
- Radar and Satellite Communication
- 3GPP – LTE-M, EC-GSM and Narrowband-IoT
- Non-3GPP – Sigfox, Wieghtless and LoRa
In recent days, you can witness the gradual growth of computer networks in networking industries through many new developments. It includes so many technologies to portrait the actual networking industry’s performance. Here, we have given you some new networking technologies that are expected to master the next networking industries. .
Current Technologies in Computer Networks
- Artificial Intelligence (AI) and Cloud Repatriation
- Software Defined Networks
- Fog-Edge Computing
- UAV-Wireless Data Links
- Responsive Internet Architecture
- Multiple Cloud Services Technology
- Internet of Things and Inter-Networking
- Quantum and Serverless Computing
- 5G enabled Nano Technology
- Digital Twin and Machine Learning (ML)
- Digital Communications
- Network Communications Protocols
For illustrative purpose, Digital Communication work in accordance with enabling communication technologies, modulation, signal processing projects, channel modeling, and error control . Similarly, Network Communications Protocols take an in-charge of routing, resource allocation, data distribution, and medium access control.
Both technologies/areas have high capabilities in a different dimension of the networking process. And they are network designing, model construction, networking testing on testbeds, experimental analysis, and performance assessments. Our researchers have given you the currently ongoing of innovative computer network research topics mentioned below for your reference.
Latest Computer Network Research Topics
- Enhancing System Robustness in Decentralized Network
- Improving Network Quality of Services and Resource Usage
- SLA–Aware Resource Scheduling and Provisioning
- Network Architectures Design and Processes Management
How to develop computer networks projects with source code?
Basically, networking is a widespread process where network construction and deployment in the real world is a challenging job. So, the entire process is fragmented into different tasks where they are performed by a set of skilled networking engineers as follows,
- Software Developer – Design and build software applications
- Networking Experts – modeling the network structure
- Database Admin – Store and manage the network information
- Support Specialist – Analyze the connected entities of the system
- Programmer – Develop the suitable code works for achieving required performance
For research purposes, we can simulate the original network behavior and performance inappropriate simulation tools. Most importantly, it reduces the cost of real-time implementation and deployment.
Our developers have long-term experience in handling networking concepts . So, if you need the best Computer Networks Projects with Source Code support , you can approach our team. Below, we have also mentioned our qualified services in your project.
- We do both conceptual and practical study on recent research topics
- We design unique network simulation models, proof-of-concept prototypes and investigational testbeds
- We employ result guaranteed new technologies to upgrade and assess the existing standard of networking systems
- We develop own algorithm, protocols and hybrid techniques based on project requirements
- We precisely access the network performance using suitable network parameters for comparative study of different systems
Performance Analysis of Computer Networks
Now, we can see the performance measurement of the networking model. Through the sophisticated simulation tool / experimental testbeds , we can develop any kind of network scenario. Once the model is processed, then the efficiency of the model is verified by several metrics. Here, we have given you the metrics along with different modelling techniques .
- Medium Access Control – Retransmissions Delay, Collisions and Packet loss
- Network Protocols – Latency, Throughput and Packet loss
- RF Channel Models – Noise, Shadowing and Fading
- Spectrum (Sense and Observation) – Latency and Detection Trustworthiness
- Links and Transceivers – Block error ratio and Signal-to-Noise Ratio (SNR)
What is computer network simulation?
Simulate the network model based on the code of the software application . Through code, we can instruct the model to perform our project requirements. At the end of the simulation, it yields the overall performance and behaviour of the network in different dimensions and metrics. Further, it also measures the communication between the network entities.
Purposes of source code
The source code of software has the main responsibility to create strong basements for designing and simulating the network model . Through the code only, the developers can make the smart work to tackle the problem in a simplified way. Effective code work is also a part of the contribution in research.
Since your code can help for learning or reusability (other application development), for your clarity, our developers will explain the implementation of research methodologies while delivering Computer Networks Projects with Source Code . Below, we have given you the different simulations of real-time network models,
How does computer network simulation works?
- Plan and design the model
- Develop the suitable hypothesis model
- Forecast the hypothetical aspects
- Perform comparative study to improve the hypothesis
- Simulate the developed model
- Based on experimental results, relate and enhance the hypothesis / model
- Do the experiments and get the results
So far, we have discussed computer networks, network layers, communication technologies, current research areas, computer network research topics, project simulation, and performance estimation . Now, our development team has a list of widely used network simulator tools.
Network simulators let the users modify the simulator operations for their project needs. Then the users can analyze the system performance and entity behavior under different circumstances. Further, it supports communication standards/protocols like TCP, WLAN, CR, Wi-Max, WSN , and many more. Here, we have given you the list of a few best result yielding simulators which is more apt for computer network simulations,
- Component-based network simulator with graphical user interface support
- Allow to design traffic models, decentralized system, protocols, computer networks, multi-processors, and many more
- Further, it enables animated and responsive simulation in modular environs
- Empower to design and deploy network application, device and infrastructure
- Develop predictive model, protocol and communication networks to interpret the network functionalities
- Support both real-time wired and wireless models
- Allow to create Finite State Automata for figuring out the network behavior
- Easy to design and develop traffic models
- Utilize QualNet analyzer to understand the obtained simulated outcome
- Enabled OS: Linux and Windows
For instance, NS3 (network Simulator 3) is detailed here.
NS3 is one of the best simulation tools to design and simulate networking projects . With the help of this tool, we can virtually design different nodes through Helper classes. By the by, it enables the installation of internet stacks, applications, devices, and many more. Further, we can insert parameters in the channel for performance evaluation in implementing computer network research topics . And let them produce traffic at runtime and pass the packets from source to destination through the selected route path. The other special features are given as follows,
- Create pcap file to get the core information of the transmitting packets. For instance: Source IP, Sequence no, Destination IP, etc. Employ Wireshark tool to view the pcap.
- Trace the network route for assess number of packets send/receive. For this purpose, the trace files will be produced automatically to monitor whole network.
- Easy to plot the graph from obtained simulation outcome in with assurance of preciseness.
- Network Animator is released to depict the realistic view of the network through animation. It shows you the real structure and how the data are transferred between nodes.
To sum up, we have sufficient technical professionals to support you in all the latest research areas of computer networks . In addition, our developments also give you the best assistance in project development from tool selection to result in an assessment. So, if you need our reliable service computer network research topics, projects with source code then communicate our team.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.
MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.

How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages
Research Topics & Ideas: CompSci & IT
50+ Computer Science Research Topic Ideas To Fast-Track Your Project

Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you’ve landed on this post, chances are you’re looking for a computer science-related research topic , but aren’t sure where to start. Here, we’ll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software engineering.
NB – This is just the start…
The topic ideation and evaluation process has multiple steps . In this post, we’ll kickstart the process by sharing some research topic ideas within the CompSci domain. This is the starting point, but to develop a well-defined research topic, you’ll need to identify a clear and convincing research gap , along with a well-justified plan of action to fill that gap.
If you’re new to the oftentimes perplexing world of research, or if this is your first time undertaking a formal academic research project, be sure to check out our free dissertation mini-course. In it, we cover the process of writing a dissertation or thesis from start to end. Be sure to also sign up for our free webinar that explores how to find a high-quality research topic.
Overview: CompSci Research Topics
- Algorithms & data structures
- Artificial intelligence ( AI )
- Computer networking
- Database systems
- Human-computer interaction
- Information security (IS)
- Software engineering
- Examples of CompSci dissertation & theses
Topics/Ideas: Algorithms & Data Structures
- An analysis of neural network algorithms’ accuracy for processing consumer purchase patterns
- A systematic review of the impact of graph algorithms on data analysis and discovery in social media network analysis
- An evaluation of machine learning algorithms used for recommender systems in streaming services
- A review of approximation algorithm approaches for solving NP-hard problems
- An analysis of parallel algorithms for high-performance computing of genomic data
- The influence of data structures on optimal algorithm design and performance in Fintech
- A Survey of algorithms applied in internet of things (IoT) systems in supply-chain management
- A comparison of streaming algorithm performance for the detection of elephant flows
- A systematic review and evaluation of machine learning algorithms used in facial pattern recognition
- Exploring the performance of a decision tree-based approach for optimizing stock purchase decisions
- Assessing the importance of complete and representative training datasets in Agricultural machine learning based decision making.
- A Comparison of Deep learning algorithms performance for structured and unstructured datasets with “rare cases”
- A systematic review of noise reduction best practices for machine learning algorithms in geoinformatics.
- Exploring the feasibility of applying information theory to feature extraction in retail datasets.
- Assessing the use case of neural network algorithms for image analysis in biodiversity assessment
Topics & Ideas: Artificial Intelligence (AI)
- Applying deep learning algorithms for speech recognition in speech-impaired children
- A review of the impact of artificial intelligence on decision-making processes in stock valuation
- An evaluation of reinforcement learning algorithms used in the production of video games
- An exploration of key developments in natural language processing and how they impacted the evolution of Chabots.
- An analysis of the ethical and social implications of artificial intelligence-based automated marking
- The influence of large-scale GIS datasets on artificial intelligence and machine learning developments
- An examination of the use of artificial intelligence in orthopaedic surgery
- The impact of explainable artificial intelligence (XAI) on transparency and trust in supply chain management
- An evaluation of the role of artificial intelligence in financial forecasting and risk management in cryptocurrency
- A meta-analysis of deep learning algorithm performance in predicting and cyber attacks in schools

Topics & Ideas: Networking
- An analysis of the impact of 5G technology on internet penetration in rural Tanzania
- Assessing the role of software-defined networking (SDN) in modern cloud-based computing
- A critical analysis of network security and privacy concerns associated with Industry 4.0 investment in healthcare.
- Exploring the influence of cloud computing on security risks in fintech.
- An examination of the use of network function virtualization (NFV) in telecom networks in Southern America
- Assessing the impact of edge computing on network architecture and design in IoT-based manufacturing
- An evaluation of the challenges and opportunities in 6G wireless network adoption
- The role of network congestion control algorithms in improving network performance on streaming platforms
- An analysis of network coding-based approaches for data security
- Assessing the impact of network topology on network performance and reliability in IoT-based workspaces

Topics & Ideas: Database Systems
- An analysis of big data management systems and technologies used in B2B marketing
- The impact of NoSQL databases on data management and analysis in smart cities
- An evaluation of the security and privacy concerns of cloud-based databases in financial organisations
- Exploring the role of data warehousing and business intelligence in global consultancies
- An analysis of the use of graph databases for data modelling and analysis in recommendation systems
- The influence of the Internet of Things (IoT) on database design and management in the retail grocery industry
- An examination of the challenges and opportunities of distributed databases in supply chain management
- Assessing the impact of data compression algorithms on database performance and scalability in cloud computing
- An evaluation of the use of in-memory databases for real-time data processing in patient monitoring
- Comparing the effects of database tuning and optimization approaches in improving database performance and efficiency in omnichannel retailing
Topics & Ideas: Human-Computer Interaction
- An analysis of the impact of mobile technology on human-computer interaction prevalence in adolescent men
- An exploration of how artificial intelligence is changing human-computer interaction patterns in children
- An evaluation of the usability and accessibility of web-based systems for CRM in the fast fashion retail sector
- Assessing the influence of virtual and augmented reality on consumer purchasing patterns
- An examination of the use of gesture-based interfaces in architecture
- Exploring the impact of ease of use in wearable technology on geriatric user
- Evaluating the ramifications of gamification in the Metaverse
- A systematic review of user experience (UX) design advances associated with Augmented Reality
- A comparison of natural language processing algorithms automation of customer response Comparing end-user perceptions of natural language processing algorithms for automated customer response
- Analysing the impact of voice-based interfaces on purchase practices in the fast food industry

Topics & Ideas: Information Security
- A bibliometric review of current trends in cryptography for secure communication
- An analysis of secure multi-party computation protocols and their applications in cloud-based computing
- An investigation of the security of blockchain technology in patient health record tracking
- A comparative study of symmetric and asymmetric encryption algorithms for instant text messaging
- A systematic review of secure data storage solutions used for cloud computing in the fintech industry
- An analysis of intrusion detection and prevention systems used in the healthcare sector
- Assessing security best practices for IoT devices in political offices
- An investigation into the role social media played in shifting regulations related to privacy and the protection of personal data
- A comparative study of digital signature schemes adoption in property transfers
- An assessment of the security of secure wireless communication systems used in tertiary institutions
Topics & Ideas: Software Engineering
- A study of agile software development methodologies and their impact on project success in pharmacology
- Investigating the impacts of software refactoring techniques and tools in blockchain-based developments
- A study of the impact of DevOps practices on software development and delivery in the healthcare sector
- An analysis of software architecture patterns and their impact on the maintainability and scalability of cloud-based offerings
- A study of the impact of artificial intelligence and machine learning on software engineering practices in the education sector
- An investigation of software testing techniques and methodologies for subscription-based offerings
- A review of software security practices and techniques for protecting against phishing attacks from social media
- An analysis of the impact of cloud computing on the rate of software development and deployment in the manufacturing sector
- Exploring the impact of software development outsourcing on project success in multinational contexts
- An investigation into the effect of poor software documentation on app success in the retail sector
CompSci & IT Dissertations/Theses
While the ideas we’ve presented above are a decent starting point for finding a CompSci-related research topic, they are fairly generic and non-specific. So, it helps to look at actual dissertations and theses to see how this all comes together.
Below, we’ve included a selection of research projects from various CompSci-related degree programs to help refine your thinking. These are actual dissertations and theses, written as part of Master’s and PhD-level programs, so they can provide some useful insight as to what a research topic looks like in practice.
- An array-based optimization framework for query processing and data analytics (Chen, 2021)
- Dynamic Object Partitioning and replication for cooperative cache (Asad, 2021)
- Embedding constructural documentation in unit tests (Nassif, 2019)
- PLASA | Programming Language for Synchronous Agents (Kilaru, 2019)
- Healthcare Data Authentication using Deep Neural Network (Sekar, 2020)
- Virtual Reality System for Planetary Surface Visualization and Analysis (Quach, 2019)
- Artificial neural networks to predict share prices on the Johannesburg stock exchange (Pyon, 2021)
- Predicting household poverty with machine learning methods: the case of Malawi (Chinyama, 2022)
- Investigating user experience and bias mitigation of the multi-modal retrieval of historical data (Singh, 2021)
- Detection of HTTPS malware traffic without decryption (Nyathi, 2022)
- Redefining privacy: case study of smart health applications (Al-Zyoud, 2019)
- A state-based approach to context modeling and computing (Yue, 2019)
- A Novel Cooperative Intrusion Detection System for Mobile Ad Hoc Networks (Solomon, 2019)
- HRSB-Tree for Spatio-Temporal Aggregates over Moving Regions (Paduri, 2019)
Looking at these titles, you can probably pick up that the research topics here are quite specific and narrowly-focused , compared to the generic ones presented earlier. This is an important thing to keep in mind as you develop your own research topic. That is to say, to create a top-notch research topic, you must be precise and target a specific context with specific variables of interest . In other words, you need to identify a clear, well-justified research gap.
Fast-Track Your Research Topic
If you’re still feeling a bit unsure about how to find a research topic for your Computer Science dissertation or research project, check out our Topic Kickstarter service.
You Might Also Like:

Investigating the impacts of software refactoring techniques and tools in blockchain-based developments.
Steps on getting this project topic
I want to work with this topic, am requesting materials to guide.
Information Technology -MSc program
It’s really interesting but how can I have access to the materials to guide me through my work?
Investigating the impacts of software refactoring techniques and tools in blockchain-based developments is in my favour. May i get the proper material about that ?
BLOCKCHAIN TECHNOLOGY
I NEED TOPIC
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly

The Network Science PhD program is a pioneering interdisciplinary program that provides the tools and concepts aimed at understanding the structure and dynamics of networks arising from the interplay of human behavior, socio-technical infrastructures, information diffusion and biological agents.
In The News

Big Data and Science of Science
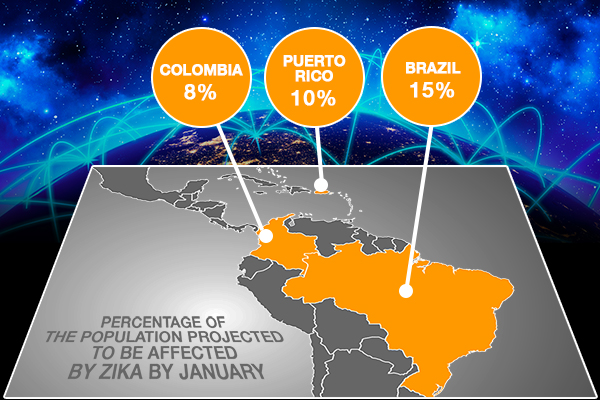
Zika Underreporting is Rife
Nation’s 1st Network Science PhD Program
The PhD in Network Science is a pioneering interdisciplinary program that provides the tools and concepts aimed at understanding the structure and dynamics of networks. Network Science research covers a broad range of topics, including: Control of Networks, Biological Networks, Spreading and Influence, Group-Decision Making, Social and Political Networks, Data and Graph Mining, and Network Geometry.
Northeastern University is a world leader in Network Science, and faculty affiliated with the program includes prominent leaders in the field such as Albert-László Barabási, Alessandro Vespignani, Tina Eliasi-Rad, and David Lazer. Graduates will be well-prepared to enter into a number of career paths, including industry research positions, government analyst positions, and post-doctoral or junior faculty positions in academic institutions. Students have the opportunity to work with some of the most prominent network scientists in the world. With frequent guest lecturers and workshop series, students have access to diverse scientists and global leaders in the field.
- Northeastern has several leading laboratories and centers in Network Science, with dozens of faculty, postdoctoral fellows, visiting faculty, and doctoral students
- Ph.D. students complete two research rotations with network science faculty
- Admitted PhD students receive full tuition scholarship and are supported with stipends or fellowships for the entire duration of their program
- Ph.D. students must complete and defend a dissertation that involves original research in Network Science
INTERDISCIPLINARY RESEARCH In-depth training in disciplines and programs essential to interdisciplinary research. Current concentrations are focused on the physical sciences (physics); social sciences (political science); health science (epidemiology); and computer and information sciences.
FOUNDATIONAL TRAINING Common, foundational training in all aspects of Network Science (e.g., approaches, languages, problems) beginning in the first year of graduate training to build an inherently interdisciplinary science and the next generation of researchers.
IDEAS + TECHNIQUES Learning to combine theoretical/ substantive questions with the appropriate tools and techniques for data collection and analyses. A key element will be combining ideas, techniques, and collaborations into the novel interdisciplinary approaches that are paramount to Network Science.
Network Science is establishing itself as major interdisciplinary research area with applications in data science and data analytics methodologies. Network scientists are employed in academia, government, and business. Applied network scientists work at Internet and social media companies.
Application Materials
- Online application
- Application fee
- Unofficial transcripts for all institutions attended (Official transcripts required upon acceptance of admission offer)
- Personal statement
- Three letters of recommendation
- GRE General – recommended, but not required
- Degree earned or in progress at an U.S. institution
- Degree earned or in progress at an institution where English is the only medium of instruction
- Official exam scores from either the TOEFL iBT, IELTS, or PTE exam
- Applicants seeking enrollment prior to the Fall 2023 term should apply through this link .
Application
Deadline for completed applications: December 1st
Applicants seeking enrollment prior to the Fall 2023 term should apply at the link under application materials below.
- Program Website
Request Information for PhD in Network Science

PhD Topics in Computer Networks
PhD Topics in Computer Networks offer highly dedicated platform for you to acquire novel and inventive ideas from our world classy experts. . You don’t feel about your PhD research projects. We are always with you to provide the best guidance in each and every stage of your research. We began our service with the vision of provides grand opportunities for research scholars to accomplish their dream of research. Today, most scholars face more difficulties in the topic selection phase. They must get the best guide to provide the best solution in this critical stage.
We offer our complete guide for you, from your research topic selection to final research viva voce. These days, thousands of research colleagues are utilizing our PhD Topics in Computer Network service from all over the world. Are you interested in utilizing our Computer Networks service? You can approach our research institution immediately.
Topics in Computer Networks
PhD Topics in Computer Networks is our most excellent service to offer our best of best also for you to successfully accomplish PhD curriculum. We are experts of experts in computer networking with 10+ years of experience. After your research topic selection, first, we also provide our implementation plan depend on your requirements. Day by day, we provide our continuous training in the implementation phase to upgrade knowledge also in your research career. Our training is most helpful for you to shine in your career.
Through our guidance, you can also easily implement your highly sophisticated projects. We also provide our research guidance and also supports via our online and offline services. Now, we also highlighted some of the important aspects of computer networking.
Major Research Areas in Networking
- Mobile Ad Hoc Networks
- Wireless Mesh Networks
- Body Area Sensor Networks
- Cognitive Radio Networks
- 4G and 5G Networks
- Information Centric also in Wireless Networks
- Satellite Networks
- Wireless Sensor Networks
- Content Centric Wireless Sensor Networks
- Device to Device Communication
- IoT Wireless Networks
- Multiple Social Networks
- Vehicular Ad Hoc Networks
- Heterogeneous Networks
- Internet of Things
- IEEE 802.11, IEEE 802.15, also in IEEE 802.16
- Artificial Neural Networks
- Wireless Ad Hoc Networks
- Multi Hop Wireless Networks
Network Protocols
- Global State Routing Protocol
- Ad Hoc On Demand Distance Vector Protocol
- Light Weight Mobile also in Routing Protocol
- Landmark Ad Hoc Routing Protocol
- Destination Sequence Distance Vector also in Routing Protocol
- Optimized Link State also in Routing Protocol
- Multi Path Dynamic Source also in Routing Protocol
- Fisheye State Routing Protocol
- Adaptive Link State also in Routing Protocol
- Source Tree Adaptive Routing Protocol
Major Concepts in Computer Networks
Handover mechanism:.
- Inter Domain Handover Mechanism
- Fast Game Based Handoff also in Mechanism
- Multi-Criteria Vertical Handover Decision Model
- QHS Handover Mechanism
- User Placement Ushering Mechanism
- Optimized Vertical Handover also in Approach
- Collaborative Handover Mechanism
- Stealthy TDP Connection also in Mechanism
- Heterogeneous Handover Mechanism
- Session Initiation Routing Protocol
- FMPv6 Handover Mechanism
- Dynamic Duty Cycle Control Mechanism
Handover Types:
- Software Handover
- Hardware Handover
-Inter Cell Handover
-Intra Cell Handover
-Multilayer Handover
-Microcellular Handover
- Horizontal Handover
- Vertical Handover
Handover Protocols:
- Route Augmentation
- Multi Connection Re-Routing
- Autonomous Handover Authentication
- Full Connection also in Re-Routing
- 3GPP Handover
- Multicast Connection also in Re-Routing
- Partial Connection Re-Routing
Handover Decision Based on,
- Network Controlled Handover
- Mobile Assisted Handover
- Mobile Controlled Handover
- User preferences
- Mobility Management
- Mobile Network and also in Management
Issues in Handover:
- Rerouting Connection
- Point to Multi Point Connection
- Quality of Service
- Security issues
- Insufficient Communication
- Insufficient System Knowledge
Congestion Control:
Congestion types:.
- Instantaneous Congestion
- Flash Congestion
- Baseline Congestion
- Spiky Delay Congestion
Congestion Management:
- Network Congestion Avoidance
- Hierarchical and also in Distributed Control
- Optimal Congestion Management
- Network Congestion Control
- Resource Allocation
- Congestion Notification
- Environomic Optimization
- Smart Grid Distributed Optimal Control
- End System Flow Control
- Congestion Free Traffic Management
- Traffic Congestion Management
- Deregulated Power system
- Dynamic Segmentation
Congestion Control Mechanism:
- Congestion Free Routing
- Enhanced Congestion Detection and also in Avoidance
- Source Throttling Congestion Control also in Mechanism
- Upstream Hop also by Hop Congestion Control Protocol
- Congestion also Based Route Recovery Technique
- Congestion also in Adaptive AODV
- Agent Based Congestion Control Protocol
- Spectrum Aware Admission Control also in Mechanism
- Weighted Fairness Guaranteed also in Congestion Control Protocol
- Congestion Adaptive Routing Protocol
- Congestion Control and also Fairness Routing
- Cluster Based also in Congestion Control
- Gossip also Based Reservation Mechanism
- Discriminatory Mechanism
- Inference Aware also based on Congestion Control Protocol
Major Security Attacks and Mechanisms
Security attacks:.
- Node Isolation Attack
- Altered Routing Attack
- Cyber Crime Attack
- Black Hole Attack
- Sinkhole and also in Sybil Attack
- Cloning Attack
- Selective Forwarding also in Attack
- Jamming Attack
- Byzantine Attack
- Eavesdropping
- Smartphone Trojan Horse also in Attack
- Node Malfunction Attack
- Spoofing Attach
- Man also in Middle Attack
- Repudiation Attack
- Played Routing also based on Attack
- DNS Poisoning Attack
- MiTM Attack
- Wormhole Attack
- Impersonation also in Attack
- Denial of Service
- Jellyfish also based on Attack
- Industrial IoT Hack Attack
- Pink Sweep Attack
- De-Synchronization also in Attack
- Gray Hole Attack
- Teardrop Attack
- Secure Socket Layer also in Attack
Security Mechanism:
- Random Key Pre-Distribution
- Statistical Anomaly also Based Techniques
- Localized Authentication and also based on Encryption Protocol
- Secure Neighbor also Based Techniques
- Secure Route Delegation
- Digital Signature also Based Authentication
- Policy also Based Techniques
- Private User Data Protection also based on Mechanism
- Secure Border Gateway Protocol
- Adaptive Acknowledgement Technique
- T-N Threshold also Based Anti-Eavesdropping Network Coding Algorithm
- Unobtrusive User Authentication
- Secret Sharing Schemes
- Memory Traffic Shaping Mechanisms
- Bi-Directional Verification Scheme
- Key Policy Attribute also Based Encryption (KP-ABE) Technique
- Trust Based Distributed Intrusion Detection Mechanism
- Hardware Isolation also Based Security Mechanism
Collision Avoidance Mechanisms:
- Collision Force Suppression Mechanism
- Bayesian Inference Techniques
- Prior Trajectory Clustering
- Markov Chain Monte Carlo also in Methods
- Human Friendly Robot also in Mechanism
- Prior Scheduling Method
- Randomized Access Time
- Carrier Sense Multiple Access also with Collision Avoidance Mechanism
- Exponential Back Off Algorithm
- Single DOF Leg also based on Mechanism
- Motion Retargeting also in Method
- Spectrum Decision also based on Mechanism
- Collision Based Beacon Rate Adaptation Scheme
Advanced PhD Topics in Computer Networks
- Cyber Physical Systems for Estimate Physical Layer Security Outage also in Large-Scale MIMO Wireless Communications
- Matlab and XBee ZigBee Modules Utilization also for RSSI Localization Application
- Realized Respiration Monitoring System also Based on Low Power Wireless Piezoelectric Sensor in CMOS Process
- Random Linear Network and Deterministic Broadcasting also in Mobile Ad Hoc Networks
- Fully Depleted Silicon on Insulator Variable Capacitors also for Passive Wireless Radiation Detector
- Generate Alarm to Devising Solution also in Vehicle on Waterways Experiencing Vulnerable Swing
- Hybrid Application Mapping also by Symmetry Eliminating Design Space Exploration on Many Core Architectures
We are also aforesaid some information about computer networks such as research areas, network protocols, handover techniques and mechanisms, congestion control mechanisms security attacks and mechanisms, and latest research topics. We also believe that our reference is most useful for you. For more guidance, you can contact us 24/7 days.
“We breathe for invention, innovation and ingenious ideas”
“Get our help to get on to the right path of achievement”
Related Pages
Services we offer.
Mathematical proof
Pseudo code
Conference Paper
Research Proposal
System Design
Literature Survey
Data Collection
Thesis Writing
Data Analysis
Rough Draft
Paper Collection
Code and Programs
Paper Writing
Course Work
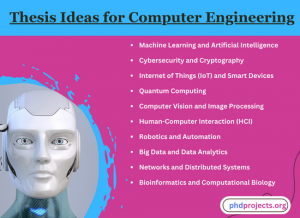
Thesis Ideas for Computer Engineering
In the computer engineering domain, various concepts are emerging in recent times that assist in conducting research. We stay updated every day on changes in technologies sew identify the correct research gaps and share with scholar proper ideas and trending topics for all areas of computer engineering. The following are some thesis topics and plans relevant to computer engineering field that we consider:
- Machine Learning and Artificial Intelligence: In machine learning and AI, we explore novel techniques or approaches. This can be based on building fresh frameworks for particular works, enhancing previous methods, or implementing AI to new regions of interest.
- Internet of Things (IoT) and Smart Devices: Here, our work is to concentrate on the combination and interaction of IoT devices. Topics related to this domain can incorporate energy performance in smart devices, improving safety in IoT, or the building of novel kinds of IoT approaches.
- Computer Vision and Image Processing: Specifically for object identification, image recognition, or 3D modeling, we aim to enhance or construct novel techniques.
- Robotics and Automation: Our project concentrates on the pattern and application of robotic frameworks and that comprise various topics such as drone innovations, self-driving vehicles, or robotic process automation.
- Networks and Distributed Systems: In networking, we intend to investigate latest subjects, including the construction of more robust protocols, enhancing network safety, or advancements in distributed computing.
- Cybersecurity and Cryptography: , In the cybersecurity field, our project researches innovative approaches such as building more efficient encryption techniques or novel tactics for preventing cyber assaults.
- Quantum Computing: We involve more into the evolving domain of quantum computing. This consists of quantum computer framework, technique creation, or quantum computing applications.
- Human-Computer Interaction (HCI): To enhance the communication among computers and humans, we explore novel approaches like augmented reality, virtual reality, and user interface design.
- Bioinformatics and Computational Biology: Our work intends to implement computer engineering norms to the biology domain, including creation of techniques for examining biological data or framing complicated biological models.
- Big Data and Data Analytics: For managing, processing and examining extensive datasets, we investigate new techniques. This can incorporate data visualization, machine learning algorithms, or the creation of novel data analysis tools.
Keep in mind that a proper thesis topic must be practical within the objective and accessible materials in addition to be creative and intriguing. Also it is significant to examine the possibility and importance of the topic in the latest trending approaches.
What is a good research question for thesis?
For a computer engineering-based thesis, the creation of an effective research query incorporates finding a particular issue or passionate region within the domain, and designing a query that must be achievable as well as crucial. Appropriate research key word plays a major role it acts a good research question as it attracts the readers. Get our thesis writing services done from subject professionals, we handle it perfectly that abides by your academic standards. Below, we suggest some well-defined research queries related to computer engineering across different regions where we provide major assistance:
- Machine Learning and AI: How can machine learning algorithms be optimized for energy efficiency in mobile devices without compromising performance?
- Internet of Things (IoT): How can IoT devices be made more secure against distributed denial-of-service (DDoS) attacks without significantly increasing their cost or complexity?
- Computer Vision and Image Processing: Can deep learning techniques improve the accuracy of real-time object detection in varied lighting and weather conditions?
- Robotics and Automation: What are the challenges and solutions for implementing collaborative robots (cobots) in small and medium-sized manufacturing enterprises?
- Networks and Distributed Systems: What new models of distributed computing can effectively leverage edge computing for faster data processing in IoT networks?
- Cybersecurity and Cryptography: What are the effective strategies to detect and mitigate advanced persistent threats in enterprise networks?
- Quantum Computing: What are the practical limitations of implementing Shor’s algorithm in current quantum computing models, and how can these limitations be overcome?
- Human-Computer Interaction (HCI): How does the integration of augmented reality in educational software impact the learning outcomes in STEM subjects for high school students?
- Big Data and Data Analytics: How can big data analytics be used to predict and mitigate traffic congestion in urban areas effectively?
- Bioinformatics and Computational Biology: How can computational models be improved to more accurately simulate protein folding in complex organisms?
It is essential to make sure that your research query is explicit, concentrated, and realistic within the research goal while structuring it. The query must be more particular to be solvable within your research but also sufficiently wide to be aligned with realistic and educational passion. It will direct your study to dedicate novel perceptions and expertise to the computer engineering domain.

Computer Engineering Thesis Writing Services
phdprojects.org offers best Computer Engineering Thesis Writing Services, article writing, journal manuscript done by PhD professionals. We are a huge team of 100+ experts you can get your programming, code and simulation results with best explanation .More than 16+ programming languages ae well handled by our developers.
- Massive Multiple Access Based on Superposition Raptor Codes for Cellular M2M Communications
- Q-value Learning Automata (QvLA)-RACH Access Scheme for Cellular M2M Communications
- Class based dynamic priority scheduling for uplink to support M2M communications in LTE
- Modeling and Forecasting of Timescale Network Traffic Dynamics in M2M Communications
- Signal-Centric Predictive Medium Access Control for M2M Communications
- M2M meets D2D: Harnessing D2D interfaces for the aggregation of M2M data
- A lightweight framework for efficient M2M device management in oneM2M architecture
- Deriving Machine to Machine (M2M) Traffic Model from Communication Model
- Learning Automata Based Q-Learning RACH Access Scheme for Cellular M2M Communication
- System Behavior and Improvements for M2M Devices Using an Experimental Satellite Network
- Ad Hoc M2M communications and security based on 4G cellular system
- A dynamic access class barring scheme to balance massive access requests among base stations over the cellular M2M networks
- A GCICA Grant-Free Random Access Scheme for M2M Communications in Crowded Massive MIMO Systems
- Dimensioning approach to provision M2M services on legacy GPRS and UMTS Cellular Networks
- M2M communications: Enablement in 4G LTE, deployment considerations and evolution path to 5G
- A D2D cooperative relay scheme for machine-to-machine communication in the LTE-A cellular network
- Random Access Channel Management for Handling Massive Numbers of Machine-to-Machine Communication Device
- Energy Efficient Self-Reconfiguration Scheme for Visual Information Based M2M Communicatio
- Remote subscription management of M2M terminals in 4G cellular wireless networks
- A novel WiMAX ranging scheme for periodic M2M applications in smart grid
- Energy Efficient Resource Allocation for UAV-Served Energy Harvesting-Supported Cognitive Industrial M2M Networks
- Radio resource allocation in LTE-advanced cellular networks with M2M communications
- Signal-centric predictive polling for medium access control in M2M communications networks
- Low-Complexity Heuristic Algorithm for Power Allocation and Access Mode Selection in M2MNetworks
- Bit-interleaved polar-coded OFDM for low-latency M2M wireless communications
- A Novel Machine-to-Machine Communication Strategy Using Rateless Coding for the Internet of Things
- Regularity of movement based approach for M2M services discovery
- To random access or schedule? Optimum 3GPP licensed-assisted access for machine-to-machine communications
- Building communications system: Takenaka’s M2M platform for building management & application interface
- A Multi-Gbps, Energy Efficient, Contactless Data-Communication Link for Machine-to-Machine (M2M) Interaction with Rotational Freedom.
- Grouping Based Uplink Resource Allocation for Massive M2M Communications over LTE
- Exploiting Spatial and Temporal Correlations for Signal-Centric MAC in M2M Communication
- Power Control for Cognitive M2M Communications Underlaying Cellular With Fairness Concerns
- Wireless M2M Communication Networks for Smart Grid Application
- An energy-efficient scheme for WiFi-capable M2M devices in hybrid LTE network
- Service Characteristics-Oriented Joint ACB, Cell Selection, and Resource Allocation Scheme for Heterogeneous M2M Communication Networks
- Optimizing Data Aggregation for Uplink Machine-to-Machine Communication Networks
- Pattern Division Random Access (PDRA) for M2M Communications With Massive MIMO System
- Modeling and analysis for admission control of M2M communications using network calculus
- An energy efficient, fault tolerant and secure clustering scheme for M2M communication networks
- PHD Guidance
- PHD PROJECTS UK
- PHD ASSISTANCE IN BANGALORE
- PHD Assistance
- PHD In 3 Months
- PHD Dissertation Help
- PHD IN JAVA PROGRAMMING
- PHD PROJECTS IN MATLAB
- PHD PROJECTS IN RTOOL
- PHD PROJECTS IN WEKA
- PhD projects in computer networking
- COMPUTER SCIENCE THESIS TOPICS FOR UNDERGRADUATES
- PHD PROJECTS AUSTRALIA
- PHD COMPANY
- PhD THESIS STRUCTURE
- PHD GUIDANCE HELP
- PHD PROJECTS IN HADOOP
- PHD PROJECTS IN OPENCV
- PHD PROJECTS IN SCILAB
- PHD PROJECTS IN WORDNET
- NETWORKING PROJECTS FOR PHD
- THESIS TOPICS FOR COMPUTER SCIENCE STUDENTS
- IEEE JOURNALS IN COMPUTER SCIENCE
- OPEN ACCESS JOURNALS IN COMPUTER SCIENCE
- SCIENCE CITATION INDEX COMPUTER SCIENCE JOURNALS
- SPRINGER JOURNALS IN COMPUTER SCIENCE
- ELSEVIER JOURNALS IN COMPUTER SCIENCE
- ACM JOURNALS IN COMPUTER SCIENCE
- INTERNATIONAL JOURNALS FOR COMPUTER SCIENCE AND ENGINEERING
- COMPUTER SCIENCE JOURNALS WITHOUT PUBLICATION FEE
- SCIENCE CITATION INDEX EXPANDED JOURNALS LIST
- THOMSON REUTERS INDEXED JOURNALS
- DOAJ COMPUTER SCIENCE JOURNALS
- SCOPUS INDEXED COMPUTER SCIENCE JOURNALS
- SCI INDEXED COMPUTER SCIENCE JOURNALS
- SPRINGER JOURNALS IN COMPUTER SCIENCE AND TECHNOLOGY
- ISI INDEXED JOURNALS IN COMPUTER SCIENCE
- PAID JOURNALS IN COMPUTER SCIENCE
- NATIONAL JOURNALS IN COMPUTER SCIENCE AND ENGINEERING
- MONTHLY JOURNALS IN COMPUTER SCIENCE
- SCIMAGO JOURNALS LIST
- THOMSON REUTERS INDEXED COMPUTER SCIENCE JOURNALS
- RESEARCH PAPER FOR SALE
- CHEAP PAPER WRITING SERVICE
- RESEARCH PAPER ASSISTANCE
- THESIS BUILDER
- WRITING YOUR JOURNAL ARTICLE IN 12 WEEKS
- WRITE MY PAPER FOR ME
- PHD PAPER WRITING SERVICE
- THESIS MAKER
- THESIS HELPER
- DISSERTATION HELP UK
- DISSERTATION WRITERS UK
- BUY DISSERTATION ONLINE
- PHD THESIS WRITING SERVICES
- DISSERTATION WRITING SERVICES UK
- DISSERTATION WRITING HELP
- PHD PROJECTS IN COMPUTER SCIENCE
- DISSERTATION ASSISTANCE

- [email protected]
- +91-97 91 62 64 69
Latest PhD Topics in Computer Science
Computer science is denoted as the study based on computer technology about both the software and hardware. In addition, computer science includes various fields with the fundamental skills that are appropriate and that are functional over the recent technologies and the interconnected world. We guide research scholars to design latest phd topics in computer science.
Introduction to Computer Science
In general, the computer science field is categorized into a range of sub-disciplines and developed disciplines . The computer science field has the extension of some notable areas such as.
- Scientific computing
- Software system
- Hardware system
- Computer Theory
We have an updated technical team to provide novel research ideas with the appropriate theorems, proofs, source code, and data about tools. So, the research scholars can communicate with our research experts in computer science for your requirements. Now, let us discuss the significant research areas that are used to select the latest PhD topics in computer science in the following.

Research Area in Computer Science
- Internet-based mobile ad hoc network (iMANET)
- Smartphone ad hoc network (SPANET)
- Mobile cloud computing
- Soft computing
- Context-aware computing
- Systems and cybernetics
- Learning technologies
- Internet computing
- Information forensics and security
- Dependable and secure computing
- Brain-computer interface
- Audio and language processing
- Wireless sensor networks
- Wireless body area network
- Visual cryptography
- Video streaming
- Vehicular network
- Ad hoc network
- Text mining
- Telecommunication engineering
- Software-defined networking
- Software reengineering
- Service computing (web service)
- Social sensor networks
- Network security and routing
- Cloud computing
- Computer vision and image processing
- Bioinformatics and biotechnology
- Big data and databases
- Cyber security
- Natural language processing
- Embedded systems
- Human-computer interaction
- Networks and security
Frequently, all the research areas in computer science are quite innovative. In addition, we focus on innovative computer science projects and examine all the sections of research works through the models, techniques, algorithms, mechanisms , etc. Now, it’s time to pay equal attention to the consequence of research protocols. So, let us take a glance over the notable protocols that are used in computer science-based projects along with their specifications.
Protocols in Computer Science
- Ad hoc on-demand distance vector is abbreviated as AODV and it is based on the loop-free routing protocol for the ad hoc networks. It is created for the self-starting environment with the mobile nodes along with various network features that include packet loss, link failure, and node mobility
- It is denoted as the reactive and proactive routing protocol in which the routes are revealed as per the necessity
- Dynamic source routing abbreviated as DSR is one of the routing protocols that is used for the functions of wireless mesh networks and it is parallel to the AODV in transmitting the node requests
The above-mentioned are the substantial research protocols along with their descriptions . Thus, you can just contact us to get the finest and latest PhD topics in computer science. Our research experts can help you in all aspects of your research. Now, you can refer to the following to know about the research trends in computer science.
Current Trends in Computer Science
- It is deployed in the process of detecting and segregating the zombie attack based on cloud computing
- Stenography technique is applied in the cloud computing process to develop the security in cloud data
- In the network process, the reduction of fault occurs through the enhancement of green cloud computing
- In cloud computing, the issues are based on load balancing through the usage of a weight-based scheme
- Homomorphic encryption is developed for key sharing and management
- It is deployed in the cloud computing to segregate the virtual side-channel attack
- It is used to develop the cloud data security and watermarking technique in the cloud computing
The following is about the guidelines for research scholars to prepare the finest research work provided by our experienced research professionals.
How to do Good Research in Computer Science?
- Initially, select the research area that you are interested in computer science
- After selecting an area, the researcher has to find an innovative research topic in computer science
- Select good ideas to enhance the state of art
- The real-time implementations are applied
- Possessions based on the selected approach have to be proved and that should be the enhancement of the existing process
- Software tools have to be developed to support the system
- Have to describe the systematic comparison with the other approaches which has the same issue and discuss the advantages and disadvantages of the research notion
- Results based on some research papers have to be accessible
Applications in Computer Science
Manet is deployed to identify some applications in the research areas that are highlighted in the following.
- Detecting the selective forwarding attack in the mobile as hoc networks
- Avoidance of congestion in the mobile ad hoc networks
- It is used in the trust and security-based mechanism of wormhole attack isolation based on Manet
- Scheme is evaluated with the recovery of mobile as hoc network
- Road safety
- Vehicular ad hoc communication
- Environment sensors
The following is the list of research applications in the field of image processing .
- Video processing
- Pattern recognition
- Color processing
- Robot vision
- Encoding and transmission
- Medical field
- Gamma-rayay imaging
In addition, we have highlighted some applications that are related to the bioinformatics research field.
- Modeling and simulation based on proteins, RNA, and DNA are created through tools based on bioinformatics
- It is used to compare the genetic data along with the assistance of bioinformatics tools
- It is deployed in the study of various aspects including protein regulation and expression
- Organization of biological data and text mining has a significant phase in the process
- It is used in the field of genetics for the mutation observation
More than above, the utmost research applications are available in real-time. In overall, it increases the inclusive efficiency in all aspects of the research features. In addition, our research experts have listed down the prominent research topics based on computer science.
- Network and security
- Distributed system
- High-performance computing
- Visualization and graphics
- Geographical information system
- Databases and data mining
- Architectures and compiler optimization
List of Few Latest and Trending Research Topics in Big Data
- The parallel multi-classification algorithm for big data using the extreme learning machine
- Disease prediction through machine learning through big data from the healthcare communities
- Nearest neighbor classification for high-speed big data streams using spark
- Privacy preserving big data publishing: A scalable k-anonymization approach using MapReduce
- Efficient and rapid machine learning algorithms for big data and dynamic varying systems
Software Engineering-Based Topics in Computer Science
- It is used to support team awareness and collaboration, distributed software development, open source communities, and software as the service
- Software modeling and reasoning
- The reasoning and modeling based on software along with the reasoning specifications in security and safety, analysis of model-driven software development, analysis of requirements modifications, and product timeline
- Dependencies of stakeholders
- Enterprise contexts
- Modeling and analysis of software requirements
Latest Computer Networking Topics for Research
- Data security in the local network through the distributed firewalls
- Efficient peer-to-peer keyword searching
- Tolerant routing on mobile ad hoc network
- Hybrid global-local indexing for efficient peer-to-peer information retrieval
- Application of genetic algorithms in network routing
- Bluetooth-based smart sensor networks
- ISO layering model
- Distributed processing and networks
- Delay tolerant network
- Wireless intelligent networking
- Network security and cryptography
The abovementioned are the contemporary and topical research topics based on the computer science research field. In addition, the research experts have highlighted the latest phd topics in computer science domain detailed in the following.
Area-Based Topics Process
- Human-robot interaction
- Digital fabrication
- Critical computing
- UI technologies
- Information visualization
- Information and communication technology and development (ICTD)
- Computer-supported cooperative work
- Computer-supported cooperative learning
- Augmented and virtual reality
- Shape modeling
- Geometry processing
- Computational imaging
- Computing fabrication
- Translating computational tools
- NLP and speech for healthcare and medicine
- Satisfiability in reasoning
- Sequential decision making
- Multi-agentnt system
- Cognitive robotics
- Knowledge representation
- Human motion analysis
- Computational photography
- Object recognition
- Physics-based modeling of shape and appearance
- Cognitive modeling of language acquisition and processing
- Applications of NLP in healthcare and medicine
- Formal perspectives on language
- Applications of NLP in social sciences and humanities
- Machine translation
- Speech processing
Now, let’s have a glance over the list of research tools that are used in the implementation of research in computer science.
Simulation Tools in Computer Science
For your information, our technical professionals from computer science backgrounds have given you some foremost research questions with answers, to what the researchers are looking for.
Research Questions Computer Science
How to implement ad hoc routing protocols using omnet++.
Oment++ environment is implemented through the adaptations and it is enabling for the contrast simulation results with the designs of the Manet application. The routing protocols such as DSR and AODV are used in the process and as the open source code.
How is Hadoop used in big data?
In general, Hadoop is considered as the java and open source framework that is deployed in the process of big data storing. Mapreduce programming model is deployed in Hadoop for the speed process of data storage.
What are the trending technologies in computer science?
- Artificial intelligence (AI)
- Everything as a service
- Human augmentation
- Big data analytics
- Intelligent process automation (IPA)
- Internet of behaviors (IoB)
- 5G technology
What are the major areas in the field of computer science?
- Theory of computing
- Bioinformatics
- Software engineering
- Programming languages
- Numerical analysis
- Vision and Graphics
- Human-computerer interaction
- Database systems
- Computer systems and network security
How to implement artificial intelligence in python?
Generally, this process includes four significant steps and they are highlighted in the following.
- Organizational and AI capabilities that are essential for digital transformation are apprehended
- Business ecosystem role, the potential for BMI, and current BM are comprehended
- Capabilities are enhanced and cultivated for the AI execution
- Internal is developed and organizational acceptance is reached
- Tensor flow
Taking everything into account, the research scholars can grasp any innovative and latest PhD topics in computer science from our research experts. Consequently, we guide research scholars in all stages. In the same way, we make discussions with you at all stages of the research work. So, scholars can closely track the research work from everywhere in the world. Additionally, our well-experienced research professionals will provide significant assistance throughout your research process.

Opening Hours
- Mon-Sat 09.00 am – 6.30 pm
- Lunch Time 12.30 pm – 01.30 pm
- Break Time 04.00 pm – 04.30 pm
- 18 years service excellence
- 40+ country reach
- 36+ university mou
- 194+ college mou
- 6000+ happy customers
- 100+ employees
- 240+ writers
- 60+ developers
- 45+ researchers
- 540+ Journal tieup
Payment Options

Our Clients

Social Links

- Terms of Use

Opening Time

Closing Time
- We follow Indian time zone


IMAGES
VIDEO
COMMENTS
2022 Computer Networking Dissertation Topics. Research Aim: The research aims to evaluate the network security issues associated with M2M communication in IoT. Objectives: To evaluate the factors affecting the network security of IoT devices. To determine the methods for increasing data integrity in M2M communication against physical tampering ...
The Networked Systems program provides education and research opportunities to graduate students in the areas of computer and telecommunication networks. Networked Systems include telephone, cable TV networks, wireless, mobile, ad hoc, and cellular phone networks, as well as the Internet. Networked Systems, as a field, is inherently ...
Wi-Fi and Wi-Max. Radio Frequency Identification (RFID) Ultra-Wideband, Bluetooth and Zigbee. Global Positioning System (GPS) Mobile Communication (4G, 5G, 5G Beyond and 6G) Radar and Satellite Communication. Low Power Wide Area Network (LPWAN) 3GPP – LTE-M, EC-GSM and Narrowband-IoT.
If you’ve landed on this post, chances are you’re looking for a computer science-related research topic, but aren’t sure where to start. Here, we’ll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software ...
AI4ME (BBC Prosperity Partnership) - PhD Studentship in Computer Networking & Distributed Systems. Lancaster University School of Computing & Communications. AI4ME is an exciting five-year EPSRC & BBC-funded Prosperity Partnership that is addressing the key challenges involved in creating and delivering personalised content at scale. Read more.
Nation’s 1st Network Science PhD Program. The PhD in Network Science is a pioneering interdisciplinary program that provides the tools and concepts aimed at understanding the structure and dynamics of networks. Network Science research covers a broad range of topics, including: Control of Networks, Biological Networks, Spreading and Influence ...
Research Topics: novel digital data and computational analyses for addressing societal challenges, analysis of online social networks and social media, intersection of AI and society, application of machine learning to social data, analysis of large-scale online data for social science applications, algorithmic fairness and bias
PhD Topics in Computer Networks is our most excellent service to offer our best of best also for you to successfully accomplish PhD curriculum. We are experts of experts in computer networking with 10+ years of experience. After your research topic selection, first, we also provide our implementation plan depend on your requirements.
The following are some thesis topics and plans relevant to computer engineering field that we consider: Machine Learning and Artificial Intelligence: In machine learning and AI, we explore novel techniques or approaches. This can be based on building fresh frameworks for particular works, enhancing previous methods, or implementing AI to new ...
Wireless intelligent networking. Network security and cryptography. The abovementioned are the contemporary and topical research topics based on the computer science research field. In addition, the research experts have highlighted the latest phd topics in computer science domain detailed in the following.