
Research Topics & Ideas: CompSci & IT
50+ Computer Science Research Topic Ideas To Fast-Track Your Project

Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you’ve landed on this post, chances are you’re looking for a computer science-related research topic , but aren’t sure where to start. Here, we’ll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software engineering.
NB – This is just the start…
The topic ideation and evaluation process has multiple steps . In this post, we’ll kickstart the process by sharing some research topic ideas within the CompSci domain. This is the starting point, but to develop a well-defined research topic, you’ll need to identify a clear and convincing research gap , along with a well-justified plan of action to fill that gap.
If you’re new to the oftentimes perplexing world of research, or if this is your first time undertaking a formal academic research project, be sure to check out our free dissertation mini-course. In it, we cover the process of writing a dissertation or thesis from start to end. Be sure to also sign up for our free webinar that explores how to find a high-quality research topic.
Overview: CompSci Research Topics
- Algorithms & data structures
- Artificial intelligence ( AI )
- Computer networking
- Database systems
- Human-computer interaction
- Information security (IS)
- Software engineering
- Examples of CompSci dissertation & theses
Topics/Ideas: Algorithms & Data Structures
- An analysis of neural network algorithms’ accuracy for processing consumer purchase patterns
- A systematic review of the impact of graph algorithms on data analysis and discovery in social media network analysis
- An evaluation of machine learning algorithms used for recommender systems in streaming services
- A review of approximation algorithm approaches for solving NP-hard problems
- An analysis of parallel algorithms for high-performance computing of genomic data
- The influence of data structures on optimal algorithm design and performance in Fintech
- A Survey of algorithms applied in internet of things (IoT) systems in supply-chain management
- A comparison of streaming algorithm performance for the detection of elephant flows
- A systematic review and evaluation of machine learning algorithms used in facial pattern recognition
- Exploring the performance of a decision tree-based approach for optimizing stock purchase decisions
- Assessing the importance of complete and representative training datasets in Agricultural machine learning based decision making.
- A Comparison of Deep learning algorithms performance for structured and unstructured datasets with “rare cases”
- A systematic review of noise reduction best practices for machine learning algorithms in geoinformatics.
- Exploring the feasibility of applying information theory to feature extraction in retail datasets.
- Assessing the use case of neural network algorithms for image analysis in biodiversity assessment
Topics & Ideas: Artificial Intelligence (AI)
- Applying deep learning algorithms for speech recognition in speech-impaired children
- A review of the impact of artificial intelligence on decision-making processes in stock valuation
- An evaluation of reinforcement learning algorithms used in the production of video games
- An exploration of key developments in natural language processing and how they impacted the evolution of Chabots.
- An analysis of the ethical and social implications of artificial intelligence-based automated marking
- The influence of large-scale GIS datasets on artificial intelligence and machine learning developments
- An examination of the use of artificial intelligence in orthopaedic surgery
- The impact of explainable artificial intelligence (XAI) on transparency and trust in supply chain management
- An evaluation of the role of artificial intelligence in financial forecasting and risk management in cryptocurrency
- A meta-analysis of deep learning algorithm performance in predicting and cyber attacks in schools

Topics & Ideas: Networking
- An analysis of the impact of 5G technology on internet penetration in rural Tanzania
- Assessing the role of software-defined networking (SDN) in modern cloud-based computing
- A critical analysis of network security and privacy concerns associated with Industry 4.0 investment in healthcare.
- Exploring the influence of cloud computing on security risks in fintech.
- An examination of the use of network function virtualization (NFV) in telecom networks in Southern America
- Assessing the impact of edge computing on network architecture and design in IoT-based manufacturing
- An evaluation of the challenges and opportunities in 6G wireless network adoption
- The role of network congestion control algorithms in improving network performance on streaming platforms
- An analysis of network coding-based approaches for data security
- Assessing the impact of network topology on network performance and reliability in IoT-based workspaces

Topics & Ideas: Database Systems
- An analysis of big data management systems and technologies used in B2B marketing
- The impact of NoSQL databases on data management and analysis in smart cities
- An evaluation of the security and privacy concerns of cloud-based databases in financial organisations
- Exploring the role of data warehousing and business intelligence in global consultancies
- An analysis of the use of graph databases for data modelling and analysis in recommendation systems
- The influence of the Internet of Things (IoT) on database design and management in the retail grocery industry
- An examination of the challenges and opportunities of distributed databases in supply chain management
- Assessing the impact of data compression algorithms on database performance and scalability in cloud computing
- An evaluation of the use of in-memory databases for real-time data processing in patient monitoring
- Comparing the effects of database tuning and optimization approaches in improving database performance and efficiency in omnichannel retailing
Topics & Ideas: Human-Computer Interaction
- An analysis of the impact of mobile technology on human-computer interaction prevalence in adolescent men
- An exploration of how artificial intelligence is changing human-computer interaction patterns in children
- An evaluation of the usability and accessibility of web-based systems for CRM in the fast fashion retail sector
- Assessing the influence of virtual and augmented reality on consumer purchasing patterns
- An examination of the use of gesture-based interfaces in architecture
- Exploring the impact of ease of use in wearable technology on geriatric user
- Evaluating the ramifications of gamification in the Metaverse
- A systematic review of user experience (UX) design advances associated with Augmented Reality
- A comparison of natural language processing algorithms automation of customer response Comparing end-user perceptions of natural language processing algorithms for automated customer response
- Analysing the impact of voice-based interfaces on purchase practices in the fast food industry

Topics & Ideas: Information Security
- A bibliometric review of current trends in cryptography for secure communication
- An analysis of secure multi-party computation protocols and their applications in cloud-based computing
- An investigation of the security of blockchain technology in patient health record tracking
- A comparative study of symmetric and asymmetric encryption algorithms for instant text messaging
- A systematic review of secure data storage solutions used for cloud computing in the fintech industry
- An analysis of intrusion detection and prevention systems used in the healthcare sector
- Assessing security best practices for IoT devices in political offices
- An investigation into the role social media played in shifting regulations related to privacy and the protection of personal data
- A comparative study of digital signature schemes adoption in property transfers
- An assessment of the security of secure wireless communication systems used in tertiary institutions
Topics & Ideas: Software Engineering
- A study of agile software development methodologies and their impact on project success in pharmacology
- Investigating the impacts of software refactoring techniques and tools in blockchain-based developments
- A study of the impact of DevOps practices on software development and delivery in the healthcare sector
- An analysis of software architecture patterns and their impact on the maintainability and scalability of cloud-based offerings
- A study of the impact of artificial intelligence and machine learning on software engineering practices in the education sector
- An investigation of software testing techniques and methodologies for subscription-based offerings
- A review of software security practices and techniques for protecting against phishing attacks from social media
- An analysis of the impact of cloud computing on the rate of software development and deployment in the manufacturing sector
- Exploring the impact of software development outsourcing on project success in multinational contexts
- An investigation into the effect of poor software documentation on app success in the retail sector
CompSci & IT Dissertations/Theses
While the ideas we’ve presented above are a decent starting point for finding a CompSci-related research topic, they are fairly generic and non-specific. So, it helps to look at actual dissertations and theses to see how this all comes together.
Below, we’ve included a selection of research projects from various CompSci-related degree programs to help refine your thinking. These are actual dissertations and theses, written as part of Master’s and PhD-level programs, so they can provide some useful insight as to what a research topic looks like in practice.
- An array-based optimization framework for query processing and data analytics (Chen, 2021)
- Dynamic Object Partitioning and replication for cooperative cache (Asad, 2021)
- Embedding constructural documentation in unit tests (Nassif, 2019)
- PLASA | Programming Language for Synchronous Agents (Kilaru, 2019)
- Healthcare Data Authentication using Deep Neural Network (Sekar, 2020)
- Virtual Reality System for Planetary Surface Visualization and Analysis (Quach, 2019)
- Artificial neural networks to predict share prices on the Johannesburg stock exchange (Pyon, 2021)
- Predicting household poverty with machine learning methods: the case of Malawi (Chinyama, 2022)
- Investigating user experience and bias mitigation of the multi-modal retrieval of historical data (Singh, 2021)
- Detection of HTTPS malware traffic without decryption (Nyathi, 2022)
- Redefining privacy: case study of smart health applications (Al-Zyoud, 2019)
- A state-based approach to context modeling and computing (Yue, 2019)
- A Novel Cooperative Intrusion Detection System for Mobile Ad Hoc Networks (Solomon, 2019)
- HRSB-Tree for Spatio-Temporal Aggregates over Moving Regions (Paduri, 2019)
Looking at these titles, you can probably pick up that the research topics here are quite specific and narrowly-focused , compared to the generic ones presented earlier. This is an important thing to keep in mind as you develop your own research topic. That is to say, to create a top-notch research topic, you must be precise and target a specific context with specific variables of interest . In other words, you need to identify a clear, well-justified research gap.
Fast-Track Your Research Topic
If you’re still feeling a bit unsure about how to find a research topic for your Computer Science dissertation or research project, check out our Topic Kickstarter service.
You Might Also Like:

Investigating the impacts of software refactoring techniques and tools in blockchain-based developments.
Steps on getting this project topic
I want to work with this topic, am requesting materials to guide.
Information Technology -MSc program
It’s really interesting but how can I have access to the materials to guide me through my work?
Investigating the impacts of software refactoring techniques and tools in blockchain-based developments is in my favour. May i get the proper material about that ?
BLOCKCHAIN TECHNOLOGY
I NEED TOPIC
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
My Homework Done
Expert Writing Services
- How It Works
- Buy homework
- Ace my homework
- Homework writers
- Homework help
- Assignment writing
- Homework Solutions
- Homework Answers
- No Need To Study
- High school
- McGraw-Hill Connect
- Myaccountinglab
- Precalculus
- Word Problem
- Computer Science
- Language arts
- Engineering
- Biochemistry
- Microbiology
Homework is easy with expert tips and advice. And even easier when you have an expert to do it for you.

100 Computer Science Topics For You Next Project

Table of Contents
Great computer science topics, interesting topics in computer science, computer science research topics for undergraduates, controversial topics in computer science, ph.d. research topics in computer science.
Are you looking for the best computer science topics for academic papers or essays? If yes, you’ve come to the right place. Here, you will find a list of research topics in computer science from which you can choose what to write about. Computer science entails the study of computational systems and computers. The work of computer scientists mostly revolves around software systems and software. This includes design, development, theory, and application.
Since computer science keeps evolving, new computer science research topics are always emerging. Educators ask students to write academic papers and essays on these topics to familiarize themselves with the subject. However, some learners have difficulties choosing research topics in computer science. That’s because they have many options to consider and these can bombard them. If you feel overwhelmed by the many computer science project topics that you have to choose from, consider this list of the best ideas from our experts who can get your homework done in no time.
To impress your educator and earn a superior grade, you need a captivating topic in computer science. This category has some of the best topics that will capture the attention of your educator and compel them to award you the top grade.
- What are search algorithms?
- Explain the evolution of search algorithms
- Discuss the hazards of most computer viruses
- Is SCRUM methodology the best computer science invention?
- How useful is networking in the development of future computer systems?
- How has artificial intelligence evolved over the years?
- How unique is software development for mobile gadgets?
- What are the pros and cons of cloud storage?
- Discuss the limits of computation and communication
- How can computer data security be improved?
- Discuss database management and architecture
- Explain the relationship between computer science and medicine
- Discuss the relationship between computer science and biotechnology
- Discuss privacy, memory, and security in the cloud storage era
- Give an overview of quantum computing
- What is the future of quantum computing?
- How can DDOS attacks be prevented?
- Discuss the DDOS attack hazard globally
- Why is having several programming languages important?
- How important is usability when it comes to human-computer interactions?
These are great research topics in computer science that will earn you the top grade if you research extensively and write your paper well. Nevertheless, pick a topic in this category if you find it interesting.
Perhaps, you’re looking for an interesting research topic in computer science for your paper or essay. Maybe you need a topic that will enable you to learn more about something you’re interested in while researching and writing. In that case, choose one of these interesting computer science research papers topics.
- Discuss the connection between human perception and virtual reality
- Discuss computer-assisted education’s future
- Discuss high-dimensional data modeling and computer science
- Explain the use of artificial intelligence and blockchain for algorithmic regulations
- Computer science: Declarative versus imperative languages
- Discuss blockchain technology and the banking industry
- Parallel computing and languages- Discuss
- Discuss the use of mesh generation in computational domains
- How can a persistent data structure be optimized?
- Explain the effects of machine architecture on the coding efficiency
- How can phishing be eliminated?
- Provide an overview of software security
- What are the most efficient protocols for cryptographic
- Explain the effects of computational thinking on science
- Network economics and game theory
- Discuss the systems programming languages development
- Discuss the computer graphics development
- Cyber-physical system versus sensor networks
- What is the non-photorealistic rendering case in computer science?
- Discuss the programming language and floating-point
If looking for interesting computer science topics from which you can get ideas for your thesis title, consider this category. You can also get a great topic for your speech in this category. Nevertheless, choose a topic that you will be happy to research and write about.
If pursuing an undergraduate program in computer science, you need a topic for your research project. The topic that you choose should help you accomplish your study goals. Here are some of the best undergraduate topics in computer science.
- Can computers understand natural and human language?
- Is two-way verification a premium technology for ensuring computer or internet security?
- How HTML5 technology affects websites
- What role do computers play in the development of operations research?
- What is the Internet of Things?
- How does the Internet of Things impact human life?
- Can AI diagnosis systems be an alternative to doctors?
- What are the benefits of VOIP phone systems?
- Can data mining help in fighting crime?
- What are the advantages and disadvantages of open-source software?
- Discuss the advanced web design technology and how it benefits visually impaired persons
- Discuss the applications and roles of artificial intelligence
- How important are micro-chips in lost pets tracing?
- How computer science help us understand time travel
- Computer gaming and virtual reality
- Discuss the advantages and disadvantages of blockchain technology
- Analyze ATMs and advanced bank security
- Advantages and disadvantages of Biometric systems
- How to improve human-computer interactions
- Discuss the advancement and evolution of torrents in the data sharing field
- Discuss the quality elements in digital forensics
- Explain the relationship between computer games and physics
- Discuss computer programs and programming- How does it work?
- What is ethical hacking?
- Is ethical hacking important?
- Discuss advanced computer programs and programming systems
- How important is big data analysis for an established business?
- Analyze the neutral networks and deep learning
- Discuss the fate of robotics, computers, and computing in the next ten years
- How do search engine algorithms work?
These are great computer science research paper topics for undergraduate students who chose computer science as major . But, each of these computer science essay topics requires extensive research and careful analysis of information. Therefore, be ready to spend some hours working if you choose any of these computer science topics for research.
Maybe you need a topic that will elicit mixed reactions from the audience. In that case, choose what to write about from these computer science controversial topics.
- Discuss the long-term effects of using computers for a long time.
- What are the negative and positive effects of growing up in a computer-driven world?
- Is there an OS that providers more privacy protection to people that use public internet services?
- What potential threats do the new computer viruses have?
- How does virtual reality impact human perception?
- What are the pros and cons of virtual reality?
- Explain the challenges facing data security
- Over-reliance on computers has made people less social
- Online medicine applications cannot substitute real doctors
- Discuss the future of the 5G wireless systems
These may be controversial research paper topics in computer science but they are interesting to research, write and read about. The most important thing is to take the time to research and analyze information before you write a paper or essay on any of these topics.
Do you need a topic for your post-graduate dissertation? If yes, this category has the best computer science thesis topics that you can choose from.
- Discuss the ethical questions that surround the use of big data banks to store human DNA
- Explain the ability of computers to process information faster than human brains
- Will human workers become obsolete due to the continued use of computer technologies?
- Are companies likely to embrace computer technologies more to run businesses after the coronavirus pandemic?
- Explain the role of computer science in solving health problems
- Discuss the future of quantum computers in detail
- Discuss how computer viruses work and the hazards associated with them
- How can robotics and artificial intelligence be used to enhance human capabilities?
- How effective is computer-assisted education?
- How to approach education using the latest computing technologies
- Discuss the business process modeling technology
- How does big data analytics work?
- Discuss how machine learning and pattern recognition works
- How can machine learning be used in the analysis of medical images?
- Discuss distributed computing and algorithms
- Audio, language, and speech processing
- Computer security and forensics
- Communication and computation limits
- Environments and programming languages
- Computer systems security and support for the digital democracy
This list comprises hot topics in computer science. Pick one of them and research it extensively to write a brilliant academic paper or essay.

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *

- Advisers & Contacts
- Bachelor of Arts & Bachelor of Science in Engineering
- Prerequisites
- Declaring Computer Science for AB Students
- Declaring Computer Science for BSE Students
- Class of '25, '26 & '27 - Departmental Requirements
- Class of 2024 - Departmental Requirements
- COS126 Information
- Important Steps and Deadlines
- Independent Work Seminars
- Guidelines and Useful Information
Undergraduate Research Topics
- AB Junior Research Workshops
- Undergraduate Program FAQ
- How to Enroll
- Requirements
- Certificate Program FAQ
- Interdepartmental Committee
- Minor Program
- Funding for Student Group Activities
- Mailing Lists and Policies
- Study Abroad
- Jobs & Careers
- Admissions Requirements
- Breadth Requirements
- Pre-FPO Checklist
- FPO Checklist
- M.S.E. Track
- M.Eng. Track
- Departmental Internship Policy (for Master's students)
- General Examination
- Fellowship Opportunities
- Travel Reimbursement Policy
- Communication Skills
- Course Schedule
- Course Catalog
- Research Areas
- Interdisciplinary Programs
- Technical Reports
- Computing Facilities
- Researchers
- Technical Staff
- Administrative Staff
- Graduate Students
- Undergraduate Students
- Graduate Alumni
- Climate and Inclusion Committee
- Resources for Undergraduate & Graduate Students
- Outreach Initiatives
- Resources for Faculty & Staff
- Spotlight Stories
- Job Openings
- Undergraduate Program
- Independent Work & Theses
Suggested Undergraduate Research Topics

How to Contact Faculty for IW/Thesis Advising
Send the professor an e-mail. When you write a professor, be clear that you want a meeting regarding a senior thesis or one-on-one IW project, and briefly describe the topic or idea that you want to work on. Check the faculty listing for email addresses.
Parastoo Abtahi, Room 419
Available for single-semester IW and senior thesis advising, 2023-2024
- Research Areas: Human-Computer Interaction (HCI), Augmented Reality (AR), and Spatial Computing
- Input techniques for on-the-go interaction (e.g., eye-gaze, microgestures, voice) with a focus on uncertainty, disambiguation, and privacy.
- Minimal and timely multisensory output (e.g., spatial audio, haptics) that enables users to attend to their physical environment and the people around them, instead of a 2D screen.
- Interaction with intelligent systems (e.g., IoT, robots) situated in physical spaces with a focus on updating users’ mental model despite the complexity and dynamicity of these systems.
Ryan Adams, Room 411
Research areas:
- Machine learning driven design
- Generative models for structured discrete objects
- Approximate inference in probabilistic models
- Accelerating solutions to partial differential equations
- Innovative uses of automatic differentiation
- Modeling and optimizing 3d printing and CNC machining
Andrew Appel, Room 209
- Research Areas: Formal methods, programming languages, compilers, computer security.
- Software verification (for which taking COS 326 / COS 510 is helpful preparation)
- Game theory of poker or other games (for which COS 217 / 226 are helpful)
- Computer game-playing programs (for which COS 217 / 226)
- Risk-limiting audits of elections (for which ORF 245 or other knowledge of probability is useful)
Sanjeev Arora, Room 407
- Theoretical machine learning, deep learning and its analysis, natural language processing. My advisees would typically have taken a course in algorithms (COS423 or COS 521 or equivalent) and a course in machine learning.
- Show that finding approximate solutions to NP-complete problems is also NP-complete (i.e., come up with NP-completeness reductions a la COS 487).
- Experimental Algorithms: Implementing and Evaluating Algorithms using existing software packages.
- Studying/designing provable algorithms for machine learning and implementions using packages like scipy and MATLAB, including applications in Natural language processing and deep learning.
- Any topic in theoretical computer science.
David August, Room 221
- Research Areas: Computer Architecture, Compilers, Parallelism
- Containment-based approaches to security: We have designed and tested a simple hardware+software containment mechanism that stops incorrect communication resulting from faults, bugs, or exploits from leaving the system. Let's explore ways to use containment to solve real problems. Expect to work with corporate security and technology decision-makers.
- Parallelism: Studies show much more parallelism than is currently realized in compilers and architectures. Let's find ways to realize this parallelism.
- Any other interesting topic in computer architecture or compilers.
Mark Braverman, 194 Nassau St., Room 231
Available for Spring 2024 single-semester IW, only
- Research Areas: computational complexity, algorithms, applied probability, computability over the real numbers, game theory and mechanism design, information theory.
- Topics in computational and communication complexity.
- Applications of information theory in complexity theory.
- Algorithms for problems under real-life assumptions.
- Game theory, network effects
- Mechanism design (could be on a problem proposed by the student)
Sebastian Caldas, 221 Nassau Street, Room 105
- Research Areas: collaborative learning, machine learning for healthcare. Typically, I will work with students that have taken COS324.
- Methods for collaborative and continual learning.
- Machine learning for healthcare applications.
Bernard Chazelle, 194 Nassau St., Room 301
- Research Areas: Natural Algorithms, Computational Geometry, Sublinear Algorithms.
- Natural algorithms (flocking, swarming, social networks, etc).
- Sublinear algorithms
- Self-improving algorithms
- Markov data structures
Danqi Chen, Room 412
Not available for IW or thesis advising, 2023-2024
- My advisees would be expected to have taken a course in machine learning and ideally have taken COS484 or an NLP graduate seminar.
- Representation learning for text and knowledge bases
- Pre-training and transfer learning
- Question answering and reading comprehension
- Information extraction
- Text summarization
- Any other interesting topics related to natural language understanding/generation
Marcel Dall'Agnol, Corwin 034
Available for single-semester and senior thesis advising, 2023-2024
- Research Areas: Theoretical computer science. (Specifically, quantum computation, sublinear algorithms, complexity theory, interactive proofs and cryptography)
Jia Deng, Room 423
Available for Fall 2023 single-semester IW, only
- Research Areas: Computer Vision, Machine Learning.
- Object recognition and action recognition
- Deep Learning, autoML, meta-learning
- Geometric reasoning, logical reasoning
Adji Bousso Dieng, Room 406
- Research areas: Vertaix is a research lab at Princeton University led by Professor Adji Bousso Dieng. We work at the intersection of artificial intelligence (AI) and the natural sciences. The models and algorithms we develop are motivated by problems in those domains and contribute to advancing methodological research in AI. We leverage tools in statistical machine learning and deep learning in developing methods for learning with the data, of various modalities, arising from the natural sciences.
Robert Dondero, Corwin Hall, Room 038
- Research Areas: Software engineering; software engineering education.
- Develop or evaluate tools to facilitate student learning in undergraduate computer science courses at Princeton, and beyond.
- In particular, can code critiquing tools help students learn about software quality?
Zeev Dvir, 194 Nassau St., Room 250
Not available for IW or thesis advising, 2023-2024.
- Research Areas: computational complexity, pseudo-randomness, coding theory and discrete mathematics.
- Independent Research: I have various research problems related to Pseudorandomness, Coding theory, Complexity and Discrete mathematics - all of which require strong mathematical background. A project could also be based on writing a survey paper describing results from a few theory papers revolving around some particular subject.
Benjamin Eysenbach, Room 416
- Research areas: reinforcement learning, machine learning. My advisees would typically have taken COS324.
- Using RL algorithms to applications in science and engineering.
- Emergent behavior of RL algorithms on high-fidelity robotic simulators.
- Studying how architectures and representations can facilitate generalization.
Christiane Fellbaum, 1-S-14 Green
No longer available for single-term IW and senior thesis advising, 2023-2024
- Research Areas: theoretical and computational linguistics, word sense disambiguation, lexical resource construction, English and multilingual WordNet(s), ontology
- Anything having to do with natural language--come and see me with/for ideas suitable to your background and interests. Some topics students have worked on in the past:
- Developing parsers, part-of-speech taggers, morphological analyzers for underrepresented languages (you don't have to know the language to develop such tools!)
- Quantitative approaches to theoretical linguistics questions
- Extensions and interfaces for WordNet (English and WN in other languages),
- Applications of WordNet(s), including:
- Foreign language tutoring systems,
- Spelling correction software,
- Word-finding/suggestion software for ordinary users and people with memory problems,
- Machine Translation
- Sentiment and Opinion detection
- Automatic reasoning and inferencing
- Collaboration with professors in the social sciences and humanities ("Digital Humanities")
Adam Finkelstein, Room 424
- Research Areas: computer graphics, audio.
Robert S. Fish, Corwin Hall, Room 037
No longer available for single-semester IW and senior thesis advising, 2023-2024
- Networking and telecommunications
- Learning, perception, and intelligence, artificial and otherwise;
- Human-computer interaction and computer-supported cooperative work
- Online education, especially in Computer Science Education
- Topics in research and development innovation methodologies including standards, open-source, and entrepreneurship
- Distributed autonomous organizations and related blockchain technologies
Michael Freedman, Room 308
- Research Areas: Distributed systems, security, networking
- Projects related to streaming data analysis, datacenter systems and networks, untrusted cloud storage and applications. Please see my group website at http://sns.cs.princeton.edu/ for current research projects.
Ruth Fong, Room 032
- Research Areas: computer vision, machine learning, deep learning, interpretability, explainable AI, fairness and bias in AI
- Develop a technique for understanding AI models
- Design a AI model that is interpretable by design
- Build a paradigm for detecting and/or correcting failure points in an AI model
- Analyze an existing AI model and/or dataset to better understand its failure points
- Build a computer vision system for another domain (e.g., medical imaging, satellite data, etc.)
- Develop a software package for explainable AI
- Adapt explainable AI research to a consumer-facing problem
Note: I am happy to advise any project if there's a sufficient overlap in interest and/or expertise; please reach out via email to chat about project ideas.
Tom Griffiths, Room 405
Research areas: computational cognitive science, computational social science, machine learning and artificial intelligence
Note: I am open to projects that apply ideas from computer science to understanding aspects of human cognition in a wide range of areas, from decision-making to cultural evolution and everything in between. For example, we have current projects analyzing chess game data and magic tricks, both of which give us clues about how human minds work. Students who have expertise or access to data related to games, magic, strategic sports like fencing, or other quantifiable domains of human behavior feel free to get in touch.
Aarti Gupta, Room 220
- Research Areas: Formal methods, program analysis, logic decision procedures
- Finding bugs in open source software using automatic verification tools
- Software verification (program analysis, model checking, test generation)
- Decision procedures for logical reasoning (SAT solvers, SMT solvers)
Elad Hazan, Room 409
- Research interests: machine learning methods and algorithms, efficient methods for mathematical optimization, regret minimization in games, reinforcement learning, control theory and practice
- Machine learning, efficient methods for mathematical optimization, statistical and computational learning theory, regret minimization in games.
- Implementation and algorithm engineering for control, reinforcement learning and robotics
- Implementation and algorithm engineering for time series prediction
Felix Heide, Room 410
- Research Areas: Computational Imaging, Computer Vision, Machine Learning (focus on Optimization and Approximate Inference).
- Optical Neural Networks
- Hardware-in-the-loop Holography
- Zero-shot and Simulation-only Learning
- Object recognition in extreme conditions
- 3D Scene Representations for View Generation and Inverse Problems
- Long-range Imaging in Scattering Media
- Hardware-in-the-loop Illumination and Sensor Optimization
- Inverse Lidar Design
- Phase Retrieval Algorithms
- Proximal Algorithms for Learning and Inference
- Domain-Specific Language for Optics Design
Kyle Jamieson, Room 306
- Research areas: Wireless and mobile networking; indoor radar and indoor localization; Internet of Things
- See other topics on my independent work ideas page (campus IP and CS dept. login req'd)
Alan Kaplan, 221 Nassau Street, Room 105
Research Areas:
- Random apps of kindness - mobile application/technology frameworks used to help individuals or communities; topic areas include, but are not limited to: first response, accessibility, environment, sustainability, social activism, civic computing, tele-health, remote learning, crowdsourcing, etc.
- Tools automating programming language interoperability - Java/C++, React Native/Java, etc.
- Software visualization tools for education
- Connected consumer devices, applications and protocols
Brian Kernighan, Room 311
- Research Areas: application-specific languages, document preparation, user interfaces, software tools, programming methodology
- Application-oriented languages, scripting languages.
- Tools; user interfaces
- Digital humanities
Zachary Kincaid, Room 219
- Research areas: programming languages, program analysis, program verification, automated reasoning
- Independent Research Topics:
- Develop a practical algorithm for an intractable problem (e.g., by developing practical search heuristics, or by reducing to, or by identifying a tractable sub-problem, ...).
- Design a domain-specific programming language, or prototype a new feature for an existing language.
- Any interesting project related to programming languages or logic.
Gillat Kol, Room 316
Aleksandra korolova, 309 sherrerd hall.
Available for single-term IW and senior thesis advising, 2023-2024
- Research areas: Societal impacts of algorithms and AI; privacy; fair and privacy-preserving machine learning; algorithm auditing.
Advisees typically have taken one or more of COS 226, COS 324, COS 423, COS 424 or COS 445.
Amit Levy, Room 307
- Research Areas: Operating Systems, Distributed Systems, Embedded Systems, Internet of Things
- Distributed hardware testing infrastructure
- Second factor security tokens
- Low-power wireless network protocol implementation
- USB device driver implementation
Kai Li, Room 321
- Research Areas: Distributed systems; storage systems; content-based search and data analysis of large datasets.
- Fast communication mechanisms for heterogeneous clusters.
- Approximate nearest-neighbor search for high dimensional data.
- Data analysis and prediction of in-patient medical data.
- Optimized implementation of classification algorithms on manycore processors.
Xiaoyan Li, 221 Nassau Street, Room 104
- Research areas: Information retrieval, novelty detection, question answering, AI, machine learning and data analysis.
- Explore new statistical retrieval models for document retrieval and question answering.
- Apply AI in various fields.
- Apply supervised or unsupervised learning in health, education, finance, and social networks, etc.
- Any interesting project related to AI, machine learning, and data analysis.
Wyatt Lloyd, Room 323
- Research areas: Distributed Systems
- Caching algorithms and implementations
- Storage systems
- Distributed transaction algorithms and implementations
Margaret Martonosi, Room 208
- Quantum Computing research, particularly related to architecture and compiler issues for QC.
- Computer architectures specialized for modern workloads (e.g., graph analytics, machine learning algorithms, mobile applications
- Investigating security and privacy vulnerabilities in computer systems, particularly IoT devices.
- Other topics in computer architecture or mobile / IoT systems also possible.
Jonathan Mayer, Sherrerd Hall, Room 307
- Research areas: Technology law and policy, with emphasis on national security, criminal procedure, consumer privacy, network management, and online speech.
- Assessing the effects of government policies, both in the public and private sectors.
- Collecting new data that relates to government decision making, including surveying current business practices and studying user behavior.
- Developing new tools to improve government processes and offer policy alternatives.
Andrés Monroy-Hernández, Room 405
- Research Areas: Human-Computer Interaction, Social Computing, Public-Interest Technology, Augmented Reality, Urban Computing
- Research interests:developing public-interest socio-technical systems. We are currently creating alternatives to gig work platforms that are more equitable for all stakeholders. For instance, we are investigating the socio-technical affordances necessary to support a co-op food delivery network owned and managed by workers and restaurants. We are exploring novel system designs that support self-governance, decentralized/federated models, community-centered data ownership, and portable reputation systems. We have opportunities for students interested in human-centered computing, UI/UX design, full-stack software development, and qualitative/quantitative user research.
- Beyond our core projects, we are open to working on research projects that explore the use of emerging technologies, such as AR, wearables, NFTs, and DAOs, for creative and out-of-the-box applications.
Christopher Moretti, Corwin Hall, Room 036
- Research areas: Distributed systems, high-throughput computing, computer science/engineering education
- Expansion, improvement, and evaluation of open-source distributed computing software.
- Applications of distributed computing for "big science" (e.g. biometrics, data mining, bioinformatics)
- Software and best practices for computer science education and study, especially Princeton's 126/217/226 sequence or MOOCs development
- Sports analytics and/or crowd-sourced computing
Radhika Nagpal, F316 Engineering Quadrangle
- Research areas: control, robotics and dynamical systems
Karthik Narasimhan, Room 422
- Research areas: Natural Language Processing, Reinforcement Learning
- Autonomous agents for text-based games ( https://www.microsoft.com/en-us/research/project/textworld/ )
- Transfer learning/generalization in NLP
- Techniques for generating natural language
- Model-based reinforcement learning
Arvind Narayanan, 308 Sherrerd Hall
Research Areas: fair machine learning (and AI ethics more broadly), the social impact of algorithmic systems, tech policy
Pedro Paredes, Corwin Hall, Room 041
My primary research work is in Theoretical Computer Science.
* Research Interest: Spectral Graph theory, Pseudorandomness, Complexity theory, Coding Theory, Quantum Information Theory, Combinatorics.
The IW projects I am interested in advising can be divided into three categories:
1. Theoretical research
I am open to advise work on research projects in any topic in one of my research areas of interest. A project could also be based on writing a survey given results from a few papers. Students should have a solid background in math (e.g., elementary combinatorics, graph theory, discrete probability, basic algebra/calculus) and theoretical computer science (226 and 240 material, like big-O/Omega/Theta, basic complexity theory, basic fundamental algorithms). Mathematical maturity is a must.
A (non exhaustive) list of topics of projects I'm interested in: * Explicit constructions of better vertex expanders and/or unique neighbor expanders. * Construction deterministic or random high dimensional expanders. * Pseudorandom generators for different problems. * Topics around the quantum PCP conjecture. * Topics around quantum error correcting codes and locally testable codes, including constructions, encoding and decoding algorithms.
2. Theory informed practical implementations of algorithms Very often the great advances in theoretical research are either not tested in practice or not even feasible to be implemented in practice. Thus, I am interested in any project that consists in trying to make theoretical ideas applicable in practice. This includes coming up with new algorithms that trade some theoretical guarantees for feasible implementation yet trying to retain the soul of the original idea; implementing new algorithms in a suitable programming language; and empirically testing practical implementations and comparing them with benchmarks / theoretical expectations. A project in this area doesn't have to be in my main areas of research, any theoretical result could be suitable for such a project.
Some examples of areas of interest: * Streaming algorithms. * Numeric linear algebra. * Property testing. * Parallel / Distributed algorithms. * Online algorithms. 3. Machine learning with a theoretical foundation
I am interested in projects in machine learning that have some mathematical/theoretical, even if most of the project is applied. This includes topics like mathematical optimization, statistical learning, fairness and privacy.
One particular area I have been recently interested in is in the area of rating systems (e.g., Chess elo) and applications of this to experts problems.
Final Note: I am also willing to advise any project with any mathematical/theoretical component, even if it's not the main one; please reach out via email to chat about project ideas.
Iasonas Petras, Corwin Hall, Room 033
- Research Areas: Information Based Complexity, Numerical Analysis, Quantum Computation.
- Prerequisites: Reasonable mathematical maturity. In case of a project related to Quantum Computation a certain familiarity with quantum mechanics is required (related courses: ELE 396/PHY 208).
- Possible research topics include:
1. Quantum algorithms and circuits:
- i. Design or simulation quantum circuits implementing quantum algorithms.
- ii. Design of quantum algorithms solving/approximating continuous problems (such as Eigenvalue problems for Partial Differential Equations).
2. Information Based Complexity:
- i. Necessary and sufficient conditions for tractability of Linear and Linear Tensor Product Problems in various settings (for example worst case or average case).
- ii. Necessary and sufficient conditions for tractability of Linear and Linear Tensor Product Problems under new tractability and error criteria.
- iii. Necessary and sufficient conditions for tractability of Weighted problems.
- iv. Necessary and sufficient conditions for tractability of Weighted Problems under new tractability and error criteria.
3. Topics in Scientific Computation:
- i. Randomness, Pseudorandomness, MC and QMC methods and their applications (Finance, etc)
Yuri Pritykin, 245 Carl Icahn Lab
- Research interests: Computational biology; Cancer immunology; Regulation of gene expression; Functional genomics; Single-cell technologies.
- Potential research projects: Development, implementation, assessment and/or application of algorithms for analysis, integration, interpretation and visualization of multi-dimensional data in molecular biology, particularly single-cell and spatial genomics data.
Benjamin Raphael, Room 309
- Research interests: Computational biology and bioinformatics; Cancer genomics; Algorithms and machine learning approaches for analysis of large-scale datasets
- Implementation and application of algorithms to infer evolutionary processes in cancer
- Identifying correlations between combinations of genomic mutations in human and cancer genomes
- Design and implementation of algorithms for genome sequencing from new DNA sequencing technologies
- Graph clustering and network anomaly detection, particularly using diffusion processes and methods from spectral graph theory
Vikram Ramaswamy, 035 Corwin Hall
- Research areas: Interpretability of AI systems, Fairness in AI systems, Computer vision.
- Constructing a new method to explain a model / create an interpretable by design model
- Analyzing a current model / dataset to understand bias within the model/dataset
- Proposing new fairness evaluations
- Proposing new methods to train to improve fairness
- Developing synthetic datasets for fairness / interpretability benchmarks
- Understanding robustness of models
Ran Raz, Room 240
- Research Area: Computational Complexity
- Independent Research Topics: Computational Complexity, Information Theory, Quantum Computation, Theoretical Computer Science
Szymon Rusinkiewicz, Room 406
- Research Areas: computer graphics; computer vision; 3D scanning; 3D printing; robotics; documentation and visualization of cultural heritage artifacts
- Research ways of incorporating rotation invariance into computer visiontasks such as feature matching and classification
- Investigate approaches to robust 3D scan matching
- Model and compensate for imperfections in 3D printing
- Given a collection of small mobile robots, apply control policies learned in simulation to the real robots.
Olga Russakovsky, Room 408
- Research Areas: computer vision, machine learning, deep learning, crowdsourcing, fairness&bias in AI
- Design a semantic segmentation deep learning model that can operate in a zero-shot setting (i.e., recognize and segment objects not seen during training)
- Develop a deep learning classifier that is impervious to protected attributes (such as gender or race) that may be erroneously correlated with target classes
- Build a computer vision system for the novel task of inferring what object (or part of an object) a human is referring to when pointing to a single pixel in the image. This includes both collecting an appropriate dataset using crowdsourcing on Amazon Mechanical Turk, creating a new deep learning formulation for this task, and running extensive analysis of both the data and the model
Sebastian Seung, Princeton Neuroscience Institute, Room 153
- Research Areas: computational neuroscience, connectomics, "deep learning" neural networks, social computing, crowdsourcing, citizen science
- Gamification of neuroscience (EyeWire 2.0)
- Semantic segmentation and object detection in brain images from microscopy
- Computational analysis of brain structure and function
- Neural network theories of brain function
Jaswinder Pal Singh, Room 324
- Research Areas: Boundary of technology and business/applications; building and scaling technology companies with special focus at that boundary; parallel computing systems and applications: parallel and distributed applications and their implications for software and architectural design; system software and programming environments for multiprocessors.
- Develop a startup company idea, and build a plan/prototype for it.
- Explore tradeoffs at the boundary of technology/product and business/applications in a chosen area.
- Study and develop methods to infer insights from data in different application areas, from science to search to finance to others.
- Design and implement a parallel application. Possible areas include graphics, compression, biology, among many others. Analyze performance bottlenecks using existing tools, and compare programming models/languages.
- Design and implement a scalable distributed algorithm.
Mona Singh, Room 420
- Research Areas: computational molecular biology, as well as its interface with machine learning and algorithms.
- Whole and cross-genome methods for predicting protein function and protein-protein interactions.
- Analysis and prediction of biological networks.
- Computational methods for inferring specific aspects of protein structure from protein sequence data.
- Any other interesting project in computational molecular biology.
Robert Tarjan, 194 Nassau St., Room 308
Available for single-semester IW and senior thesis advising, 2022-2023
- Research Areas: Data structures; graph algorithms; combinatorial optimization; computational complexity; computational geometry; parallel algorithms.
- Implement one or more data structures or combinatorial algorithms to provide insight into their empirical behavior.
- Design and/or analyze various data structures and combinatorial algorithms.
Olga Troyanskaya, Room 320
- Research Areas: Bioinformatics; analysis of large-scale biological data sets (genomics, gene expression, proteomics, biological networks); algorithms for integration of data from multiple data sources; visualization of biological data; machine learning methods in bioinformatics.
- Implement and evaluate one or more gene expression analysis algorithm.
- Develop algorithms for assessment of performance of genomic analysis methods.
- Develop, implement, and evaluate visualization tools for heterogeneous biological data.
David Walker, Room 211
- Research Areas: Programming languages, type systems, compilers, domain-specific languages, software-defined networking and security
- Independent Research Topics: Any other interesting project that involves humanitarian hacking, functional programming, domain-specific programming languages, type systems, compilers, software-defined networking, fault tolerance, language-based security, theorem proving, logic or logical frameworks.
Shengyi Wang, Postdoctoral Research Associate, Room 216
- Independent Research topics: Explore Escher-style tilings using (introductory) group theory and automata theory to produce beautiful pictures.
Kevin Wayne, Corwin Hall, Room 040
- Research Areas: design, analysis, and implementation of algorithms; data structures; combinatorial optimization; graphs and networks.
- Design and implement computer visualizations of algorithms or data structures.
- Develop pedagogical tools or programming assignments for the computer science curriculum at Princeton and beyond.
- Develop assessment infrastructure and assessments for MOOCs.
Matt Weinberg, 194 Nassau St., Room 222
- Research Areas: algorithms, algorithmic game theory, mechanism design, game theoretical problems in {Bitcoin, networking, healthcare}.
- Theoretical questions related to COS 445 topics such as matching theory, voting theory, auction design, etc.
- Theoretical questions related to incentives in applications like Bitcoin, the Internet, health care, etc. In a little bit more detail: protocols for these systems are often designed assuming that users will follow them. But often, users will actually be strictly happier to deviate from the intended protocol. How should we reason about user behavior in these protocols? How should we design protocols in these settings?
Huacheng Yu, Room 310
- data structures
- streaming algorithms
- design and analyze data structures / streaming algorithms
- prove impossibility results (lower bounds)
- implement and evaluate data structures / streaming algorithms
Ellen Zhong, Room 314
No longer available for single-term IW and senior thesis advising, 2023-2024
Opportunities outside the department
We encourage students to look in to doing interdisciplinary computer science research and to work with professors in departments other than computer science. However, every CS independent work project must have a strong computer science element (even if it has other scientific or artistic elements as well.) To do a project with an adviser outside of computer science you must have permission of the department. This can be accomplished by having a second co-adviser within the computer science department or by contacting the independent work supervisor about the project and having he or she sign the independent work proposal form.
Here is a list of professors outside the computer science department who are eager to work with computer science undergraduates.
Maria Apostolaki, Engineering Quadrangle, C330
- Research areas: Computing & Networking, Data & Information Science, Security & Privacy
Branko Glisic, Engineering Quadrangle, Room E330
- Documentation of historic structures
- Cyber physical systems for structural health monitoring
- Developing virtual and augmented reality applications for documenting structures
- Applying machine learning techniques to generate 3D models from 2D plans of buildings
- Contact : Rebecca Napolitano, rkn2 (@princeton.edu)
Mihir Kshirsagar, Sherrerd Hall, Room 315
Center for Information Technology Policy.
- Consumer protection
- Content regulation
- Competition law
- Economic development
- Surveillance and discrimination
Sharad Malik, Engineering Quadrangle, Room B224
Select a Senior Thesis Adviser for the 2020-21 Academic Year.
- Design of reliable hardware systems
- Verifying complex software and hardware systems
Prateek Mittal, Engineering Quadrangle, Room B236
- Internet security and privacy
- Social Networks
- Privacy technologies, anonymous communication
- Network Science
- Internet security and privacy: The insecurity of Internet protocols and services threatens the safety of our critical network infrastructure and billions of end users. How can we defend end users as well as our critical network infrastructure from attacks?
- Trustworthy social systems: Online social networks (OSNs) such as Facebook, Google+, and Twitter have revolutionized the way our society communicates. How can we leverage social connections between users to design the next generation of communication systems?
- Privacy Technologies: Privacy on the Internet is eroding rapidly, with businesses and governments mining sensitive user information. How can we protect the privacy of our online communications? The Tor project (https://www.torproject.org/) is a potential application of interest.
Ken Norman, Psychology Dept, PNI 137
- Research Areas: Memory, the brain and computation
- Lab: Princeton Computational Memory Lab
Potential research topics
- Methods for decoding cognitive state information from neuroimaging data (fMRI and EEG)
- Neural network simulations of learning and memory
Caroline Savage
Office of Sustainability, Phone:(609)258-7513, Email: cs35 (@princeton.edu)
The Campus as Lab program supports students using the Princeton campus as a living laboratory to solve sustainability challenges. The Office of Sustainability has created a list of campus as lab research questions, filterable by discipline and topic, on its website .
An example from Computer Science could include using TigerEnergy , a platform which provides real-time data on campus energy generation and consumption, to study one of the many energy systems or buildings on campus. Three CS students used TigerEnergy to create a live energy heatmap of campus .
Other potential projects include:
- Apply game theory to sustainability challenges
- Develop a tool to help visualize interactions between complex campus systems, e.g. energy and water use, transportation and storm water runoff, purchasing and waste, etc.
- How can we learn (in aggregate) about individuals’ waste, energy, transportation, and other behaviors without impinging on privacy?
Janet Vertesi, Sociology Dept, Wallace Hall, Room 122
- Research areas: Sociology of technology; Human-computer interaction; Ubiquitous computing.
- Possible projects: At the intersection of computer science and social science, my students have built mixed reality games, produced artistic and interactive installations, and studied mixed human-robot teams, among other projects.
David Wentzlaff, Engineering Quadrangle, Room 228
Computing, Operating Systems, Sustainable Computing.
- Instrument Princeton's Green (HPCRC) data center
- Investigate power utilization on an processor core implemented in an FPGA
- Dismantle and document all of the components in modern electronics. Invent new ways to build computers that can be recycled easier.
- Other topics in parallel computer architecture or operating systems
Explore your training options in 10 minutes Get Started
- Graduate Stories
- Partner Spotlights
- Bootcamp Prep
- Bootcamp Admissions
- University Bootcamps
- Coding Tools
- Software Engineering
- Web Development
- Data Science
- Tech Guides
- Tech Resources
- Career Advice
- Online Learning
- Internships
- Apprenticeships
- Tech Salaries
- Associate Degree
- Bachelor's Degree
- Master's Degree
- University Admissions
- Best Schools
- Certifications
- Bootcamp Financing
- Higher Ed Financing
- Scholarships
- Financial Aid
- Best Coding Bootcamps
- Best Online Bootcamps
- Best Web Design Bootcamps
- Best Data Science Bootcamps
- Best Technology Sales Bootcamps
- Best Data Analytics Bootcamps
- Best Cybersecurity Bootcamps
- Best Digital Marketing Bootcamps
- Los Angeles
- San Francisco
- Browse All Locations
- Digital Marketing
- Machine Learning
- See All Subjects
- Bootcamps 101
- Full-Stack Development
- Career Changes
- View all Career Discussions
- Mobile App Development
- Cybersecurity
- Product Management
- UX/UI Design
- What is a Coding Bootcamp?
- Are Coding Bootcamps Worth It?
- How to Choose a Coding Bootcamp
- Best Online Coding Bootcamps and Courses
- Best Free Bootcamps and Coding Training
- Coding Bootcamp vs. Community College
- Coding Bootcamp vs. Self-Learning
- Bootcamps vs. Certifications: Compared
- What Is a Coding Bootcamp Job Guarantee?
- How to Pay for Coding Bootcamp
- Ultimate Guide to Coding Bootcamp Loans
- Best Coding Bootcamp Scholarships and Grants
- Education Stipends for Coding Bootcamps
- Get Your Coding Bootcamp Sponsored by Your Employer
- GI Bill and Coding Bootcamps
- Tech Intevriews
- Our Enterprise Solution
- Connect With Us
- Publication
- Reskill America
- Partner With Us
- Resource Center
- Bachelor’s Degree
- Master’s Degree
The Top 10 Most Interesting Computer Science Research Topics
Computer science touches nearly every area of our lives. With new advancements in technology, the computer science field is constantly evolving, giving rise to new computer science research topics. These topics attempt to answer various computer science research questions and how they affect the tech industry and the larger world.
Computer science research topics can be divided into several categories, such as artificial intelligence, big data and data science, human-computer interaction, security and privacy, and software engineering. If you are a student or researcher looking for computer research paper topics. In that case, this article provides some suggestions on examples of computer science research topics and questions.
Find your bootcamp match
What makes a strong computer science research topic.
A strong computer science topic is clear, well-defined, and easy to understand. It should also reflect the research’s purpose, scope, or aim. In addition, a strong computer science research topic is devoid of abbreviations that are not generally known, though, it can include industry terms that are currently and generally accepted.
Tips for Choosing a Computer Science Research Topic
- Brainstorm . Brainstorming helps you develop a few different ideas and find the best topic for you. Some core questions you should ask are, What are some open questions in computer science? What do you want to learn more about? What are some current trends in computer science?
- Choose a sub-field . There are many subfields and career paths in computer science . Before choosing a research topic, ensure that you point out which aspect of computer science the research will focus on. That could be theoretical computer science, contemporary computing culture, or even distributed computing research topics.
- Aim to answer a question . When you’re choosing a research topic in computer science, you should always have a question in mind that you’d like to answer. That helps you narrow down your research aim to meet specified clear goals.
- Do a comprehensive literature review . When starting a research project, it is essential to have a clear idea of the topic you plan to study. That involves doing a comprehensive literature review to better understand what has been learned about your topic in the past.
- Keep the topic simple and clear. The topic should reflect the scope and aim of the research it addresses. It should also be concise and free of ambiguous words. Hence, some researchers recommended that the topic be limited to five to 15 substantive words. It can take the form of a question or a declarative statement.
What’s the Difference Between a Research Topic and a Research Question?
A research topic is the subject matter that a researcher chooses to investigate. You may also refer to it as the title of a research paper. It summarizes the scope of the research and captures the researcher’s approach to the research question. Hence, it may be broad or more specific. For example, a broad topic may read, Data Protection and Blockchain, while a more specific variant can read, Potential Strategies to Privacy Issues on the Blockchain.
On the other hand, a research question is the fundamental starting point for any research project. It typically reflects various real-world problems and, sometimes, theoretical computer science challenges. As such, it must be clear, concise, and answerable.
How to Create Strong Computer Science Research Questions
To create substantial computer science research questions, one must first understand the topic at hand. Furthermore, the research question should generate new knowledge and contribute to the advancement of the field. It could be something that has not been answered before or is only partially answered. It is also essential to consider the feasibility of answering the question.
Top 10 Computer Science Research Paper Topics
1. battery life and energy storage for 5g equipment.
The 5G network is an upcoming cellular network with much higher data rates and capacity than the current 4G network. According to research published in the European Scientific Institute Journal, one of the main concerns with the 5G network is the high energy consumption of the 5G-enabled devices . Hence, this research on this topic can highlight the challenges and proffer unique solutions to make more energy-efficient designs.
2. The Influence of Extraction Methods on Big Data Mining
Data mining has drawn the scientific community’s attention, especially with the explosive rise of big data. Many research results prove that the extraction methods used have a significant effect on the outcome of the data mining process. However, a topic like this analyzes algorithms. It suggests strategies and efficient algorithms that may help understand the challenge or lead the way to find a solution.
3. Integration of 5G with Analytics and Artificial Intelligence
According to the International Finance Corporation, 5G and AI technologies are defining emerging markets and our world. Through different technologies, this research aims to find novel ways to integrate these powerful tools to produce excellent results. Subjects like this often spark great discoveries that pioneer new levels of research and innovation. A breakthrough can influence advanced educational technology, virtual reality, metaverse, and medical imaging.
4. Leveraging Asynchronous FPGAs for Crypto Acceleration
To support the growing cryptocurrency industry, there is a need to create new ways to accelerate transaction processing. This project aims to use asynchronous Field-Programmable Gate Arrays (FPGAs) to accelerate cryptocurrency transaction processing. It explores how various distributed computing technologies can influence mining cryptocurrencies faster with FPGAs and generally enjoy faster transactions.
5. Cyber Security Future Technologies
Cyber security is a trending topic among businesses and individuals, especially as many work teams are going remote. Research like this can stretch the length and breadth of the cyber security and cloud security industries and project innovations depending on the researcher’s preferences. Another angle is to analyze existing or emerging solutions and present discoveries that can aid future research.
6. Exploring the Boundaries Between Art, Media, and Information Technology
The field of computers and media is a vast and complex one that intersects in many ways. They create images or animations using design technology like algorithmic mechanism design, design thinking, design theory, digital fabrication systems, and electronic design automation. This paper aims to define how both fields exist independently and symbiotically.
7. Evolution of Future Wireless Networks Using Cognitive Radio Networks
This research project aims to study how cognitive radio technology can drive evolution in future wireless networks. It will analyze the performance of cognitive radio-based wireless networks in different scenarios and measure its impact on spectral efficiency and network capacity. The research project will involve the development of a simulation model for studying the performance of cognitive radios in different scenarios.
8. The Role of Quantum Computing and Machine Learning in Advancing Medical Predictive Systems
In a paper titled Exploring Quantum Computing Use Cases for Healthcare , experts at IBM highlighted precision medicine and diagnostics to benefit from quantum computing. Using biomedical imaging, machine learning, computational biology, and data-intensive computing systems, researchers can create more accurate disease progression prediction, disease severity classification systems, and 3D Image reconstruction systems vital for treating chronic diseases.
9. Implementing Privacy and Security in Wireless Networks
Wireless networks are prone to attacks, and that has been a big concern for both individual users and organizations. According to the Cyber Security and Infrastructure Security Agency CISA, cyber security specialists are working to find reliable methods of securing wireless networks . This research aims to develop a secure and privacy-preserving communication framework for wireless communication and social networks.
10. Exploring the Challenges and Potentials of Biometric Systems Using Computational Techniques
Much discussion surrounds biometric systems and the potential for misuse and privacy concerns. When exploring how biometric systems can be effectively used, issues such as verification time and cost, hygiene, data bias, and cultural acceptance must be weighed. The paper may take a critical study into the various challenges using computational tools and predict possible solutions.
Other Examples of Computer Science Research Topics & Questions
Computer research topics.
- The confluence of theoretical computer science, deep learning, computational algorithms, and performance computing
- Exploring human-computer interactions and the importance of usability in operating systems
- Predicting the limits of networking and distributed systems
- Controlling data mining on public systems through third-party applications
- The impact of green computing on the environment and computational science
Computer Research Questions
- Why are there so many programming languages?
- Is there a better way to enhance human-computer interactions in computer-aided learning?
- How safe is cloud computing, and what are some ways to enhance security?
- Can computers effectively assist in the sequencing of human genes?
- How valuable is SCRUM methodology in Agile software development?
Choosing the Right Computer Science Research Topic
Computer science research is a vast field, and it can be challenging to choose the right topic. There are a few things to keep in mind when making this decision. Choose a topic that you are interested in. This will make it easier to stay motivated and produce high-quality research for your computer science degree .
Select a topic that is relevant to your field of study. This will help you to develop specialized knowledge in the area. Choose a topic that has potential for future research. This will ensure that your research is relevant and up-to-date. Typically, coding bootcamps provide a framework that streamlines students’ projects to a specific field, doing their search for a creative solution more effortless.
Computer Science Research Topics FAQ
To start a computer science research project, you should look at what other content is out there. Complete a literature review to know the available findings surrounding your idea. Design your research and ensure that you have the necessary skills and resources to complete the project.
The first step to conducting computer science research is to conceptualize the idea and review existing knowledge about that subject. You will design your research and collect data through surveys or experiments. Analyze your data and build a prototype or graphical model. You will also write a report and present it to a recognized body for review and publication.
You can find computer science research jobs on the job boards of many universities. Many universities have job boards on their websites that list open positions in research and academia. Also, many Slack and GitHub channels for computer scientists provide regular updates on available projects.
There are several hot topics and questions in AI that you can build your research on. Below are some AI research questions you may consider for your research paper.
- Will it be possible to build artificial emotional intelligence?
- Will robots replace humans in all difficult cumbersome jobs as part of the progress of civilization?
- Can artificial intelligence systems self-improve with knowledge from the Internet?
About us: Career Karma is a platform designed to help job seekers find, research, and connect with job training programs to advance their careers. Learn about the CK publication .
What's Next?
Get matched with top bootcamps
Ask a question to our community, take our careers quiz.

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *


- Onsite training
3,000,000+ delegates
15,000+ clients
1,000+ locations
- KnowledgePass
- Log a ticket
01344203999 Available 24/7
Best Computer Science Project Topics: Explained
Discover a wide range of Computer Science Project Topics explained in detail. This comprehensive blog helps students and researchers explore exciting project ideas, providing insights and inspiration for successful projects in the field of Computer Science.

Exclusive 40% OFF
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Share this Resource
- macOS Mojave Troubleshooting and Support Training
- Google G Suite Training
- OneDrive Training
- Computer Science Course

If you are in search of Computer Science Project Topics, this collection is just what you need to kickstart your journey. Discover a diverse collection of Computer Science Project Topics suitable for academic assignments, research projects, and real-world applications.
Table of Contents
1) Best Computer Science Project Topics
a) Face detection
b) Crime rate prediction
c) E-authentication system
d) Online auction system
e) Evaluation of academic performance
f) Symbol recognition
g) Weather forecasting application
h) Public News Droid
i) Online eBook master
j) Mobile wallet and merchant payment system
2) Conclusion
Best Computer Science Project Topics
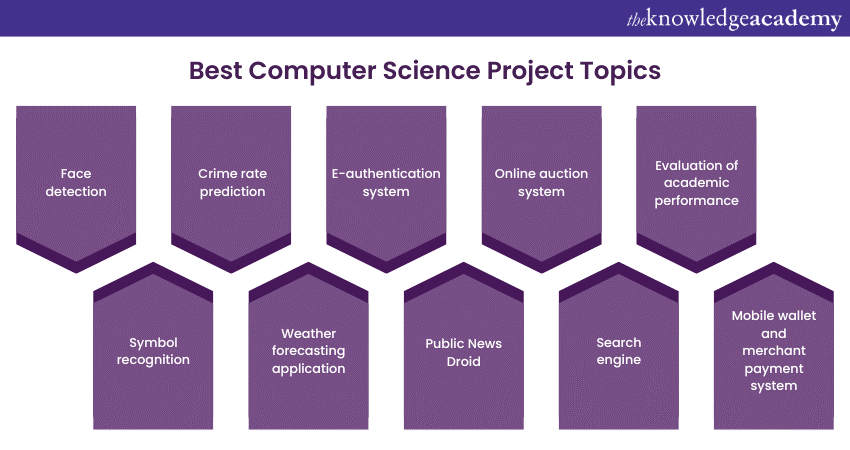
Face detection
It holds significant importance and serves various functions across multiple domains. Face detection technology has significantly enhanced the surveillance capabilities of authorities.
The fusion of face detection with biometrics and security technology has facilitated the recognition of individuals' facial features. It has enabled various processes, such as launching an application, ensuring security, and guiding the subsequent steps within an application.
Face detection technology employs facial algorithms to determine the extent of facial patterns. It possesses the capability to adapt and discern which facial attributes to identify and which to disregard.
One of the most promising computer science mini-project ideas for hands-on experimentation is the development of face detection software. This project involves creating a face detection program using the OpenCV library. The program is designed to detect faces in real time, whether from a webcam feed or video files stored on a local PC. Pre-trained XML classifiers are employed to detect and track faces, and you can extend its functionality to identify various objects using different classifiers.
To execute this program successfully, it is necessary to install the OpenCV library on your local machine and configure the paths for the XML classifier files appropriately.
Get foundational knowledge regarding computer systems and network programming with Computer Science And Fundamentals Training
Crime rate prediction
One of the most innovative computer science ideas is to develop a crime rate prediction system. As the name implies, this computer science project involves creating a system capable of analysing and forecasting crime rates in specific locations.
To function effectively, the system requires relevant data. It employs the K-means data mining algorithm for crime rate prediction. The K-means algorithm is adept at clustering co-offenders and organised crime groups by identifying pertinent crime patterns through hidden links, link prediction, and statistical analysis of crime data.
Crime rate prediction offers numerous advantages, including preemptive measures, culprit tracking, and informed decision-making. This methodology empowers decision-makers to foresee criminal activity and take law enforcement actions to minimise its consequences.
In doing so, stakeholders can enhance public satisfaction, elevate the quality of life, and, most importantly, identify negative externalities, enabling them to take corrective measures. Relevant agencies can optimise their resource utilisation. The crime prediction system expedites the dispensation of justice and contributes to reduced crime rates.
E-authentication system
Various authentication methods, such as OTPs, passwords, and biometrics, are available. These authentication systems enhance user experiences by eliminating the need for multiple setups and bolstering security, thus encouraging more users to embrace the technology.
E-authentication has gained widespread acceptance, serving purposes like accessing government services, online transactions, and various platforms. Users can safeguard their identities with e-authentication, offering a higher level of security.
This project is dedicated to constructing an e-authentication system which combines QR codes and OTPs to fortify security. It aims to prevent unauthorised access due to activities like shoulder surfing and misuse of login credentials. To use this system, users must initially register by providing essential details.
After registration, users can access the login module to authenticate their accounts using the email ID and password created during registration. Subsequently, users can choose between two authentication methods: QR (Quick Response) codes or OTPs (One-Time Passwords). Depending on the user's choice, the system generates either a QR code sent to the user's email, or an OTP delivered via SMS to the registered mobile number.
The system generates QR codes and OTPs randomly during login, enhancing security. However, it requires a consistent Internet connection for operation.
Online auction system
The online auction platform enables users to participate in auctions from any location, granting sellers the opportunity to showcase their products to a global audience.
Another valuable aspect of online auctions is the real-time feedback mechanism, which allows bidders to monitor price fluctuations as bids increase.
Buyers and bidders from around the world can log in at their convenience, irrespective of geographical time differences, ensuring they take advantage of opportunities.
In an online auction, buyers engage in transactions through competitive bidding, with each item having a starting price and a set closing time. The highest bidder for an item is declared the winner and becomes the item's owner.
This project involves the development of a secure online auction system employing a fraud detection method based on binary classification. To participate in an online auction, users are required to provide identification details such as PAN numbers, email addresses, license numbers, etc.
The system then screens, authenticates, and authorises users. Only authorised users are permitted to place bids. The system is designed to detect potential fraudulent users at an early stage, mitigating the risk of online fraud and scams. These introductory-level computer science projects are instrumental in establishing a strong foundation in fundamental programming concepts.
Get your End User Training and learn to work with text, graphics and other media
Evaluation of academic performance
Assessing academic performance serves as a means for educational institutions to monitor student progress. This not only contributes to enhancing individual student achievements but also aids in refining teaching methods and evaluating teacher effectiveness.
Educators can strategically outline teaching objectives to facilitate goal attainment. By doing so, teachers can identify and implement effective pedagogical techniques while discarding those that do not significantly benefit student performance.
One of the most captivating computer science project ideas entails creating an evaluation system capable of analysing students' academic performance using fuzzy logic. In this approach, three key parameters, namely attendance, internal marks, and external marks, are considered to determine the overall academic performance of a student. The application of fuzzy inference systems yields more precise results compared to conventional evaluation techniques.
Throughout the development of this computer science project, it is imperative to ensure that the accuracy of student information uploaded is maintained, devoid of any errors. Faulty data entry could result in inaccurate outcomes.
Symbol recognition
This computer science project is an outstanding choice for beginners. The project's objective is to develop a system capable of identifying symbols provided by the user. This symbol recognition system harnesses an image recognition algorithm to process images and detect symbols. Initially, the system converts RGB objects into grayscale images, which are subsequently transformed into black-and-white images.
Throughout this process, image processing techniques are employed to eliminate unwanted elements and environmental disturbances. The system also utilises optical character recognition, achieving an accuracy rate of 60-80 per cent.
Within this system, a designated directory stores all symbol templates. The images are of fixed size, ensuring accurate symbol recognition. These templates are maintained in a black-and-white format, and the system creates a dataset from them.
When a user inputs a query image into the system, it resizes the image, compares the resized image values to those of the template images in the dataset, and ultimately presents the results in textual format. Thus, while the system accepts image inputs, it provides output in a text-based format.
Get a complete understanding of Google Data Studio with our Google Data Studio Training and configure your reports easily.
Weather forecasting application
This is a beginner-level web development and programming app that will serve best as a project topic for CSE students. The main objective of the app is to create a web-based weather application that can provide real-time weather details (like current temperature and chances of rain) of a particular location. The app can also predict if the day will be rainy, cloudy, or sunny.
Developing a weather forecasting app is the best way to put your coding skills to the test. To create a weather forecasting app, you will need a stronghold on the basics of Web Development, HTML, CSS, and JavaScript. To provide the best backend performance, good knowledge of Node.js and express technologies is a must.
It is important to know how to use API calls to scoop out weather information from other websites and display relevant information in your app.
For the app’s best User Interface, you have to place an input text box in which the users can enter the location for which weather information is needed. As soon as the search button is hit, the weather forecast for the input location should pop out.
Public News Droid
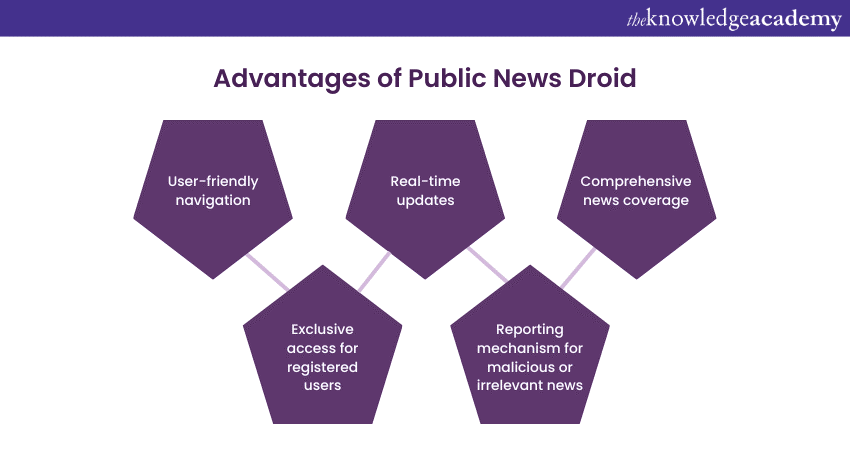
Public News Droid offers various advantages, including:
1) User-friendly navigation
2) Real-time updates
3) Comprehensive news coverage
4) Exclusive access for registered users
5) Reporting mechanism for malicious or irrelevant news
The system comprises two primary modules, one for administrators and one for users. Administrators oversee the accuracy and relevance of news and information. In cases of fake news or misuse, administrators can take corrective action to prevent the dissemination of irrelevant information.
Users, on the other hand, can access news and informative content specific to their respective localities, towns, or cities and contribute news related to other locations.
To use the application, users must complete the registration process and provide the necessary details. Once registered, users gain access to the latest news, the ability to refresh the app for updates, browse additional information, add news articles, and more. Users can also incorporate images and headlines for the news they submit. Mentioning computer science projects on your resume can make it stand out among others.
Learn how to make interactive dashboards with Building Interactive Dashboards Training and acquire skills to create labels and effective number formats
Search engine
The search engine proves incredibly valuable by enhancing brand visibility, enabling targeted advertising, boosting brand awareness, managing performance, and increasing website traffic, among other benefits.
Brands can expand their visibility by employing appropriate keywords and various strategies. They can harness the search engine's capabilities to outperform competitors and advance their business.
Enhanced brand visibility not only fosters authenticity but also drives revenue growth for the brand. This search engine is constructed using web annotation, representing one of the current trends in computer science projects. When users input specific words or phrases into the search engine, it automatically retrieves the most relevant pages containing those keywords, thanks to web annotation.
Web annotation greatly contributes to creating user-friendly applications, allowing users to add, modify, or remove information from web resources without altering the resources themselves.
This project utilises web annotation for both pages and images. When users input words, names, or phrases, the system retrieves information and images with corresponding annotations, presenting a list of results matching the user's input. Developing an effective algorithm is essential for generating query result pages or search result records based on user queries in this search engine.
Online eBook master
It is a compelling choice to delve into the development of an online eBook creator. This web-based eBook maker empowers users to design and generate eBooks without incurring any costs. The system consists of two key modules: an admin login and an author login. The admin functions encompass receiving user (author) requests, verifying their credentials, assessing finished eBooks, and fulfilling requests by dispatching the eBooks to the authors.
Users can register in the system via the author login. Upon providing essential information, users gain the capability to craft new books. They can define the book's content, title, page count, incorporate a book cover, and more.
Returning users can log in with their credentials and choose to either create new books or continue editing previously initiated (unfinished) eBooks. Authors are permitted to maintain a maximum of three incomplete eBooks concurrently, with the requirement to finalise at least one book before initiating a new project.
Mobile wallet and merchant payment system
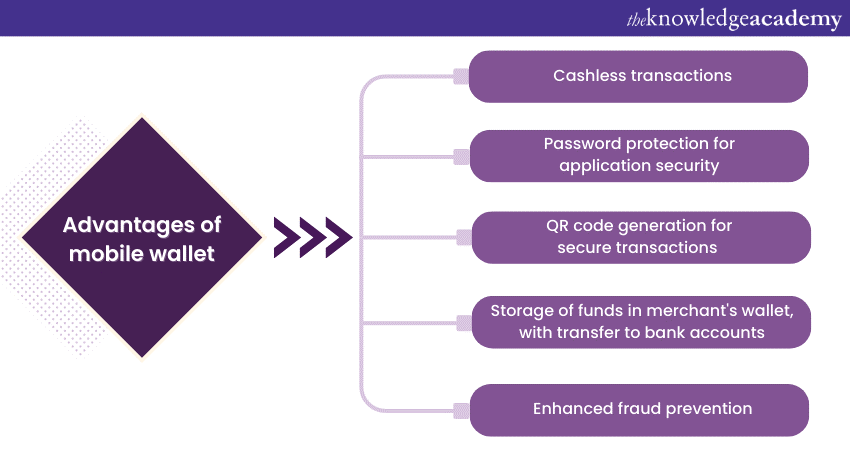
The mobile wallet offers a range of advantages, including:
1) Cashless transactions
2) Password protection for application security
3) QR code generation for secure transactions
4) Storage of funds in merchant's wallet, with transfer to bank accounts
5) Enhanced fraud prevention
The objective behind developing this app is to establish a secure, dependable, and efficient platform for financial transactions. The system generates unique QR code IDs for each transaction, and all passwords are encrypted using the AES Encryption Algorithm.
This application comprises two components: an Android application for merchants to scan QR codes and a consumer application for generating QR codes. The front-end development employs Android Studio, while the back end is supported by SQL Server.

Conclusion
This blog has presented a collection of innovative and captivating Computer Science Project Topics. You can use these ideas as a foundation to create a project. From Artificial Intelligence and Machine Learning to practical solutions in Cybersecurity and Web Development, these projects empower individuals to develop critical skills, expand their knowledge, and address real-world challenges.
Learn how to create and modify styles as well as templates with LibreOffice Training and customise menu content and toolbars
Frequently Asked Questions
Upcoming it security & data protection resources batches & dates.
Mon 22nd Jul 2024
Mon 28th Oct 2024
Get A Quote
WHO WILL BE FUNDING THE COURSE?
My employer
By submitting your details you agree to be contacted in order to respond to your enquiry
- Business Analysis
- Lean Six Sigma Certification
Share this course
Our biggest spring sale.

We cannot process your enquiry without contacting you, please tick to confirm your consent to us for contacting you about your enquiry.
By submitting your details you agree to be contacted in order to respond to your enquiry.
We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Or select from our popular topics
- ITIL® Certification
- Scrum Certification
- Change Management Certification
- Business Analysis Courses
- Microsoft Azure Certification
- Microsoft Excel & Certification Course
- Microsoft Project
- Explore more courses
Press esc to close
Fill out your contact details below and our training experts will be in touch.
Fill out your contact details below
Thank you for your enquiry!
One of our training experts will be in touch shortly to go over your training requirements.
Back to Course Information
Fill out your contact details below so we can get in touch with you regarding your training requirements.
* WHO WILL BE FUNDING THE COURSE?
Preferred Contact Method
No preference
Back to course information
Fill out your training details below
Fill out your training details below so we have a better idea of what your training requirements are.
HOW MANY DELEGATES NEED TRAINING?
HOW DO YOU WANT THE COURSE DELIVERED?
Online Instructor-led
Online Self-paced
WHEN WOULD YOU LIKE TO TAKE THIS COURSE?
Next 2 - 4 months
WHAT IS YOUR REASON FOR ENQUIRING?
Looking for some information
Looking for a discount
I want to book but have questions
One of our training experts will be in touch shortly to go overy your training requirements.
Your privacy & cookies!
Like many websites we use cookies. We care about your data and experience, so to give you the best possible experience using our site, we store a very limited amount of your data. Continuing to use this site or clicking “Accept & close” means that you agree to our use of cookies. Learn more about our privacy policy and cookie policy cookie policy .
We use cookies that are essential for our site to work. Please visit our cookie policy for more information. To accept all cookies click 'Accept & close'.

Global Dimensions of Intellectual Property Rights in Science and Technology (1993)
Chapter: 12 a case study on computer programs, 12 a case study on computer programs.
PAMELA SAMUELSON
HISTORICAL OVERVIEW
Phase 1: the 1950s and early 1960s.
When computer programs were first being developed, proprietary rights issues were not of much concern. Software was often developed in academic or other research settings. Much progress in the programming field occurred as a result of informal exchanges of software among academics and other researchers. In the course of such exchanges, a program developed by one person might be extended or improved by a number of colleagues who would send back (or on to others) their revised versions of the software. Computer manufacturers in this period often provided software to customers of their machines to make their major product (i.e., computers) more commercially attractive (which caused the software to be characterized as "bundled" with the hardware).
To the extent that computer programs were distributed in this period by firms for whom proprietary rights in software were important, programs tended to be developed and distributed through restrictive trade secret licensing agreements. In general, these were individually negotiated with customers. The licensing tradition of the early days of the software industry has framed some of the industry expectations about proprietary rights issues, with implications for issues still being litigated today.
In the mid-1960s, as programs began to become more diverse and complex, as more firms began to invest in the development of programs, and as
some began to envision a wider market for software products, a public dialogue began to develop about what kinds of proprietary rights were or should be available for computer programs. The industry had trade secrecy and licensing protection, but some thought more legal protection might be needed.
Phase 2: Mid-1960s and 1970s
Copyright law was one existing intellectual property system into which some in the mid-1960s thought computer programs might potentially fit. Copyright had a number of potential advantages for software: it could provide a relatively long term of protection against unauthorized copying based on a minimal showing of creativity and a simple, inexpensive registration process. 1 Copyright would protect the work's ''expression," but not the "ideas" it contained. Others would be free to use the same ideas in other software, or to develop independently the same or a similar work. All that would be forbidden was the copying of expression from the first author's work.
In 1964, the U.S. Copyright Office considered whether to begin accepting registration of computer programs as copyrightable writings. It decided to do so, but only under its "rule of doubt" and then only on condition that a full text of the program be deposited with the office, which would be available for public review. 2
The Copyright Office's doubt about the copyrightability of programs
arose from a 1908 Supreme Court decision that had held that a piano roll was not an infringing "copy" of copyrighted music, but rather part of a mechanical device. 3 Mechanical devices (and processes) have traditionally been excluded from the copyright domain. 4 Although the office was aware that in machine-readable form, computer programs had a mechanical character, they also had a textual character, which was why the Copyright Office decided to accept them for registration.
The requirement that the full text of the source code of a program be deposited in order for a copyright in the program to be registered was consistent with a long-standing practice of the Copyright Office, 5 as well as with what has long been perceived to be the constitutional purpose of copyright, namely, promoting the creation and dissemination of knowledge. 6
Relatively few programs, however, were registered with the Copyright Office under this policy during the 1960s and 1970s. 7 Several factors may have contributed to this. Some firms may have been deterred by the requirement that the full text of the source code be deposited with the office and made available for public inspection, because this would have dispelled its trade secret status. Some may have thought a registration certificate issued under the rule of doubt might not be worth much. However, the main reason for the low number of copyright registrations was probably that a mass market in software still lay in the future. Copyright is useful mainly to protect mass-marketed products, and trade secrecy is quite adequate for programs with a small number of distributed copies.
Shortly after the Copyright Office issued its policy on the registrability of computer programs, the U.S. Patent Office issued a policy statement concerning its views on the patentability of computer programs. It rejected the idea that computer programs, or the intellectual processes that might be embodied in them, were patentable subject matter. 8 Only if a program was
claimed as part of a traditionally patentable industrial process (i.e., those involving the transformation of matter from one physical state to another) did the Patent Office intend to issue patents for program-related innovations. 9
Patents are typically available for inventive advances in machine designs or other technological products or processes on completion of a rigorous examination procedure conducted by a government agency, based on a detailed specification of what the claimed invention is, how it differs from the prior art, and how the invention can be made. Although patent rights are considerably shorter in duration than copyrights, patent rights are considered stronger because no one may make, use, or sell the claimed invention without the patent owner's permission during the life of the patent. (Patents give rights not just against someone who copies the protected innovation, but even against those who develop it independently.) Also, much of what copyright law would consider to be unprotectable functional content ("ideas") if described in a book can be protected by patent law.
The Patent Office's policy denying the patentability of program innovations was consistent with the recommendations of a presidential commission convened to make suggestions about how the office could more effectively cope with an "age of exploding technology." The commission also recommended that patent protection not be available for computer program innovations. 10
Although there were some appellate decisions in the late 1960s and
early 1970s overturning Patent Office rejections of computer program-related applications, few software developers looked to the patent system for protection after two U.S. Supreme Court decisions in the 1970s ruled that patent protection was not available for algorithms. 11 These decisions were generally regarded as calling into question the patentability of all software innovations, although some continued to pursue patents for their software innovations notwithstanding these decisions. 12
As the 1970s drew to a close, despite the seeming availability of copyright protection for computer programs, the software industry was still relying principally on trade secrecy and licensing agreements. Patents seemed largely, if not totally, unavailable for program innovations. Occasional suggestions were made that a new form of legal protection for computer programs should be devised, but the practice of the day was trade secrecy and licensing, and the discourse about additional protection was focused overwhelmingly on copyright.
During the 1960s and 1970s the computer science research community grew substantially in size. Although more software was being distributed under restrictive licensing agreements, much software, as well as innovative ideas about how to develop software, continued to be exchanged among researchers in this field. The results of much of this research were published and discussed openly at research conferences. Toward the end of this period, a number of important research ideas began to make their way into commercial projects, but this was not seen as an impediment to research by computer scientists because the commercial ventures tended to arise after the research had been published. Researchers during this period did not, for the most part, seek proprietary rights in their software or software ideas, although other rewards (such as tenure or recognition in the field) were available to those whose innovative research was published.
Phase 3: The 1980s
Four significant developments in the 1980s changed the landscape of the software industry and the intellectual property rights concerns of those who developed software. Two were developments in the computing field; two were legal developments.
The first significant computing development was the introduction to the market of the personal computer (PC), a machine made possible by improvements in the design of semiconductor chips, both as memory storage
devices and as processing units. A second was the visible commercial success of some early PC applications software—most notably, Visicalc, and then Lotus 1-2-3—which significantly contributed to the demand for PCs as well as making other software developers aware that fortunes could be made by selling software. With these developments, the base for a large mass market in software was finally in place.
During this period, computer manufacturers began to realize that it was to their advantage to encourage others to develop application programs that could be executed on their brand of computers. One form of encouragement involved making available to software developers whatever interface information would be necessary for development of application programs that could interact with the operating system software provided with the vendor's computers (information that might otherwise have been maintained as a trade secret). Another form of encouragement was pioneered by Apple Computer, which recognized the potential value to consumers (and ultimately to Apple) of having a relatively consistent "look and feel" to the applications programs developed to run on Apple computers. Apple developed detailed guidelines for applications developers to aid in the construction of this consistent look and feel.
The first important legal development—one which was in place when the first successful mass-marketed software applications were introduced into the market—was passage of amendments to the copyright statute in 1980 to resolve the lingering doubt about whether copyright protection was available for computer programs. 13 These amendments were adopted on the recommendation of the National Commission on New Technological Uses of Copyrighted Works (CONTU), which Congress had established to study a number of "new technology" issues affecting copyrighted works. The CONTU report emphasized the written nature of program texts, which made them seem so much like written texts that had long been protected by copyright law. The CONTU report noted the successful expansion of the boundaries of copyright over the years to take in other new technology products, such as photographs, motion pictures, and sound recordings. It predicted that computer programs could also be accommodated in the copyright regime. 14
Copyright law was perceived by CONTU as the best alternative for protection of computer programs under existing intellectual property regimes. Trade secrecy, CONTU noted, was inherently unsuited for mass-marketed products because the first sale of the product on the open market would dispel the secret. CONTU observed that Supreme Court rulings had cast
doubts on the availability of patent protection for software. CONTU's confidence in copyright protection for computer programs was also partly based on an economic study it had commissioned. This economic study regarded copyright as suitable for protecting software against unauthorized copying after sale of the first copy of it in the marketplace, while fostering the development of independently created programs. The CONTU majority expressed confidence that judges would be able to draw lines between protected expression and unprotected ideas embodied in computer programs, just as they did routinely with other kinds of copyrighted works.
A strong dissenting view was expressed by the novelist John Hersey, one of the members of the CONTU commission, who regarded programs as too mechanical to be protected by copyright law. Hersey warned that the software industry had no intention to cease the use of trade secrecy for software. Dual assertion of trade secrecy and copyright seemed to him incompatible with copyright's historical function of promoting the dissemination of knowledge.
Another development during this period was that the Copyright Office dropped its earlier requirement that the full text of source code be deposited with it. Now only the first and last 25 pages of source code had to be deposited to register a program. The office also decided it had no objection if the copyright owner blacked out some portions of the deposited source code so as not to reveal trade secrets. This new policy was said to be consistent with the new copyright statute that protected both published and unpublished works alike, in contrast to the prior statutes that had protected mainly published works. 15
With the enactment of the software copyright amendments, software developers had a legal remedy in the event that someone began to mass-market exact or near-exact copies of the developers' programs in competition with the owner of the copyright in the program. Unsurprisingly, the first software copyright cases involved exact copying of the whole or substantial portions of program code, and in them, the courts found copyright infringement. Copyright litigation in the mid- and late 1980s began to grapple with questions about what, besides program code, copyright protects about computer programs. Because the "second-generation" litigation affects the current legal framework for the protection of computer programs, the issues raised by these cases will be dealt with in the next section.
As CONTU Commissioner Hersey anticipated, software developers did not give up their claims to the valuable trade secrets embodied in their programs after enactment of the 1980 amendments to the copyright statute.
To protect those secrets, developers began distributing their products in machine-readable form, often relying on "shrink-wrap" licensing agreements to limit consumer rights in the software. 16 Serious questions exist about the enforceability of shrink-wrap licenses, some because of their dubious contractual character 17 and some because of provisions that aim to deprive consumers of rights conferred by the copyright statute. 18 That has not led, however, to their disuse.
One common trade secret-related provision of shrink-wrap licenses, as well as of many negotiated licenses, is a prohibition against decompilation or disassembly of the program code. Such provisions are relied on as the basis of software developer assertions that notwithstanding the mass distribution of a program, the program should be treated as unpublished copyrighted works as to which virtually no fair use defenses can be raised. 19
Those who seek to prevent decompilation of programs tend to assert that since decompilation involves making an unauthorized copy of the program, it constitutes an improper means of obtaining trade secrets in the program. Under this theory, decompilation of program code results in three unlawful acts: copyright infringement (because of the unauthorized copy made during the decompilation process), trade secret misappropriation (because the secret has been obtained by improper means, i.e., by copyright
infringement), and a breach of the licensing agreement (which prohibits decompilation).
Under this theory, copyright law would become the legal instrument by which trade secrecy could be maintained in a mass-marketed product, rather than a law that promotes the dissemination of knowledge. Others regard decompilation as a fair use of a mass-marketed program and, shrink-wrap restrictions to the contrary, as unenforceable. This issue has been litigated in the United States, but has not yet been resolved definitively. 20 The issue remains controversial both within the United States and abroad.
A second important legal development in the early 1980s—although one that took some time to become apparent—was a substantial shift in the U.S. Patent and Trademark Office (PTO) policy concerning the patentability of computer program-related inventions. This change occurred after the 1981 decision by the U.S. Supreme Court in Diamond v. Diehr, which ruled that a rubber curing process, one element of which was a computer program, was a patentable process. On its face, the Diehr decision seemed consistent with the 1966 Patent Office policy and seemed, therefore, not likely to lead to a significant change in patent policy regarding software innovations. 21 By the mid-1980s, however, the PTO had come to construe the Court's ruling broadly and started issuing a wide variety of computer program-related patents. Only "mathematical algorithms in the abstract" were now thought unpatentable. Word of the PTO's new receptivity to software patent applications spread within the patent bar and gradually to software developers.
During the early and mid-1980s, both the computer science field and the software industry grew very significantly. Innovative ideas in computer science and related research fields were widely published and disseminated. Software was still exchanged by researchers, but a new sensitivity to intellectual property rights began to arise, with general recognition that unauthorized copying of software might infringe copyrights, especially if done with a commercial purpose. This was not perceived as presenting a serious obstacle to research, for it was generally understood that a reimplementation of the program (writing one's own code) would be
noninfringing. 22 Also, much of the software (and ideas about software) exchanged by researchers during the early and mid-1980s occurred outside the commercial marketplace. Increasingly, the exchanges took place with the aid of government-subsidized networks of computers.
Software firms often benefited from the plentiful availability of research about software, as well as from the availability of highly trained researchers who could be recruited as employees. Software developers began investing more heavily in research and development work. Some of the results of this research was published and/or exchanged at technical conferences, but much was kept as a trade secret and incorporated in new products.
By the late 1980s, concerns began arising in the computer science and related fields, as well as in the software industry and the legal community, about the degree of intellectual property protection needed to promote a continuation of the high level of innovation in the software industry. 23 Although most software development firms, researchers, and manufacturers of computers designed to be compatible with the leading firms' machines seemed to think that copyright (complemented by trade secrecy) was adequate to their needs, the changing self-perception of several major computer manufacturers led them to push for more and "stronger" protection. (This concern has been shared by some successful software firms whose most popular programs were being "cloned" by competitors.) Having come to realize that software was where the principal money of the future would be made, these computer firms began reconceiving themselves as software developers. As they did so, their perspective on software protection issues changed as well. If they were going to invest in software development, they wanted "strong'' protection for it. They have, as a consequence, become among the most vocal advocates of strong copyright, as well as of patent protection for computer programs. 24
CURRENT LEGAL APPROACHES IN THE UNITED STATES
Software developers in the United States are currently protecting software products through one or more of the following legal protection mechanisms: copyright, trade secret, and/or patent law. Licensing agreements often supplement these forms of protection. Some software licensing agreements are negotiated with individual customers; others are printed forms found under the plastic shrink-wrap of a mass-marketed package. 25 Few developers rely on only one form of legal protection. Developers seem to differ somewhat on the mix of legal protection mechanisms they employ as well as on the degree of protection they expect from each legal device.
Although the availability of intellectual property protection has unquestionably contributed to the growth and prosperity of the U.S. software industry, some in the industry and in the research community are concerned that innovation and competition in this industry will be impeded rather than enhanced if existing intellectual property rights are construed very broadly. 26 Others, however, worry that courts may not construe intellectual property rights broadly enough to protect what is most valuable about software, and if too little protection is available, there may be insufficient incentives to invest in software development; hence innovation and competition may be retarded through underprotection. 27 Still others (mainly lawyers) are confident that the software industry will continue to prosper and grow under the existing intellectual property regimes as the courts "fill out" the details of software protection on a case-by-case basis as they have been doing for the past several years. 28
What's Not Controversial
Although the main purpose of the discussion of current approaches is to give an overview of the principal intellectual property issues about which there is controversy in the technical and legal communities, it may be wise to begin with a recognition of a number of intellectual property issues as to which there is today no significant controversy. Describing only the aspects of the legal environment as to which controversies exist would risk creating a misimpression about the satisfaction many software developers and lawyers have with some aspects of intellectual property rights they now use to protect their and their clients' products.
One uncontroversial aspect of the current legal environment is the use of copyright to protect against exact or near-exact copying of program code. Another is the use of copyright to protect certain aspects of user interfaces, such as videogame graphics, that are easily identifiable as "expressive" in a traditional copyright sense. Also relatively uncontroversial is the use of copyright protection for low-level structural details of programs, such as the instruction-by-instruction sequence of the code. 29
The use of trade secret protection for the source code of programs and other internally held documents concerning program design and the like is similarly uncontroversial. So too is the use of licensing agreements negotiated with individual customers under which trade secret software is made available to licensees when the number of licensees is relatively small and when there is a reasonable prospect of ensuring that licensees will take adequate measures to protect the secrecy of the software. Patent protection for industrial processes that have computer program elements, such as the rubber curing process in the Diehr case, is also uncontroversial.
Substantial controversies exist, however, about the application of copyright law to protect other aspects of software, about patent protection for other kinds of software innovations, about the enforceability of shrink-wrap licensing agreements, and about the manner in which the various forms of legal protection seemingly available to software developers interrelate in the protection of program elements (e.g., the extent to which copyright and trade secret protection can coexist in mass-marketed software).
Controversies Arising From Whelan v. Jaslow
Because quite a number of the most contentious copyright issues arise from the Whelan v. Jaslow decision, this subsection focuses on that case. In the summer of 1986, the Third Circuit Court of Appeals affirmed a trial court decision in favor of Whelan Associates in its software copyright lawsuit against Jaslow Dental Laboratories. 30 Jaslow's program for managing dental lab business functions used some of the same data and file structures as Whelan's program (to which Jaslow had access), and five subroutines of Jaslow's program functioned very similarly to Whelan's. The trial court inferred that there were substantial similarities in the underlying structure of the two programs based largely on a comparison of similarities in the user interfaces of the two programs, even though user interface similarities were not the basis for the infringement claim. Jaslow's principal defense was that Whelan's copyright protected only against exact copying of program code, and since there were no literal similarities between the programs, no copyright infringement had occurred.
In its opinion on this appeal, the Third Circuit stated that copyright protection was available for the "structure, sequence, and organization" (sso) of a program, not just the program code. (The court did not distinguish between high- and low-level structural features of a program.) The court analogized copyright protection for program sso to the copyright protection available for such things as detailed plot sequences in novels. The court also emphasized that the coding of a program was a minor part of the cost of development of a program. The court expressed fear that if copyright protection was not accorded to sso, there would be insufficient incentives to invest in the development of software.
The Third Circuit's Whelan decision also quoted with approval from that part of the trial court opinion stating that similarities in the manner in which programs functioned could serve as a basis for a finding of copyright infringement. Although recognizing that user interface similarities did not necessarily mean that two programs had similar underlying structures (thereby correcting an error the trial judge had made), the appellate court thought that user interface similarities might still be some evidence of underlying structural similarities. In conjunction with other evidence in the case, the Third Circuit decided that infringement had properly been found.
Although a number of controversies have arisen out of the Whelan opinion, the aspect of the opinion that has received the greatest attention is the test the court used for determining copyright infringement in computer
program cases. The " Whelan test" regards the general purpose or function of a program as its unprotectable "idea." All else about the program is, under the Whelan test, protectable "expression'' unless there is only one or a very small number of ways to achieve the function (in which case idea and expression are said to be "merged," and what would otherwise be expression is treated as an idea). The sole defense this test contemplates for one who has copied anything more detailed than the general function of another program is that copying that detail was "necessary" to perform that program function. If there is in the marketplace another program that does the function differently, courts applying the Whelan test have generally been persuaded that the copying was unjustified and that what was taken must have been "expressive."
Although the Whelan test has been used in a number of subsequent cases, including the well-publicized Lotus v. Paperback case, 31 some judges have rejected it as inconsistent with copyright law and tradition, or have found ways to distinguish the Whelan case when employing its test would have resulted in a finding of infringement. 32
Many commentators assert that the Whelan test interprets copyright
protection too expansively. 33 Although the court in Whelan did not seem to realize it, the Whelan test would give much broader copyright protection to computer programs than has traditionally been given to novels and plays, which are among the artistic and fanciful works generally accorded a broader scope of protection than functional kinds of writings (of which programs would seem to be an example). 34 The Whelan test would forbid reuse of many things people in the field tend to regard as ideas. 35 Some commentators have suggested that because innovation in software tends to be of a more incremental character than in some other fields, and especially given the long duration of copyright protection, the Whelan interpretation of the scope of copyright is likely to substantially overprotect software. 36
One lawyer-economist, Professor Peter Menell, has observed that the model of innovation used by the economists who did the study of software for CONTU is now considered to be an outmoded approach. 37 Those econo-
mists focused on a model that considered what incentives would be needed for development of individual programs in isolation. Today, economists would consider what protection would be needed to foster innovation of a more cumulative and incremental kind, such as has largely typified the software field. In addition, the economists on whose work CONTU relied did not anticipate the networking potential of software and consequently did not study what provisions the law should make in response to this phenomenon. Menell has suggested that with the aid of their now more refined model of innovation, economists today might make somewhat different recommendations on software protection than they did in the late 1970s for CONTU. 38
As a matter of copyright law, the principal problem with the Whelan test is its incompatibility with the copyright statute, the case law properly interpreting it, and traditional principles of copyright law. The copyright statute provides that not only ideas, but also processes, procedures, systems, and methods of operation, are unprotectable elements of copyrighted works. 39 This provision codifies some long-standing principles derived from U.S. copyright case law, such as the Supreme Court's century-old Baker v. Selden decision that ruled that a second author did not infringe a first author's copyright when he put into his own book substantially similar ledger sheets to those in the first author's book. The reason the Court gave for its ruling was that Selden's copyright did not give him exclusive rights to the bookkeeping system, but only to his explanation or description of it. 40 The ordering and arrangement of columns and headings on the ledger sheets were part of the system; to get exclusive rights in this, the Court said that Selden would have to get a patent.
The statutory exclusion from copyright protection for methods, processes, and the like was added to the copyright statute in part to ensure that the scope of copyright in computer programs would not be construed too broadly. Yet, in cases in which the Whelan test has been employed, the courts have tended to find the presence of protectable "expression" when they perceive there to be more than a couple of ways to perform some function, seeming not to realize that there may be more than one "method" or "system" or "process" for doing something, none of which is properly protected by copyright law. The Whelan test does not attempt to exclude
methods or processes from the scope of copyright protection, and its recognition of functionality as a limitation on the scope of copyright is triggered only when there are no alternative ways to perform program functions.
Whelan has been invoked by plaintiffs not only in cases involving similarities in the internal structural design features of programs, but also in many other kinds of cases. sso can be construed to include internal interface specifications of a program, the layout of elements in a user interface, and the sequence of screen displays when program functions are executed, among other things. Even the manner in which a program functions can be said to be protectable by copyright law under Whelan . The case law on these issues and other software issues is in conflict, and resolution of these controversies cannot be expected very soon.
Traditionalist Versus Strong Protectionist View of What Copyright Law Does and Does Not Protect in Computer Programs
Traditional principles of copyright law, when applied to computer programs, would tend to yield only a "thin" scope of protection for them. Unquestionably, copyright protection would exist for the code of the program and the kinds of expressive displays generated when program instructions are executed, such as explanatory text and fanciful graphics, which are readily perceptible as traditional subject matters of copyright law. A traditionalist would regard copyright protection as not extending to functional elements of a program, whether at a high or low level of abstraction, or to the functional behavior that programs exhibit. Nor would copyright protection be available for the applied know-how embodied in programs, including program logic. 41 Copyright protection would also not be available for algorithms or other structural abstractions in software that are constituent elements of a process, method, or system embodied in a program.
Efficient ways of implementing a function would also not be protectable by copyright law under the traditionalist view, nor would aspects of software design that make the software easier to use (because this bears on program functionality). The traditionalist would also not regard making a limited number of copies of a program to study it and extract interface information or other ideas from the program as infringing conduct, because computer programs are a kind of work for which it is necessary to make a copy to "read" the text of the work. 42 Developing a program that incorporates interface information derived from decompilation would also, in the traditionalist view, be noninfringing conduct.
If decompilation and the use of interface information derived from the study of decompiled code were to be infringing acts, the traditionalist would regard copyright as having been turned inside out, for instead of promoting the dissemination of knowledge as has been its traditional purpose, copyright law would become the principal means by which trade secrets would be maintained in widely distributed copyrighted works. Instead of protecting only expressive elements of programs, copyright would become like a patent: a means by which to get exclusive rights to the configuration of a machine—without meeting stringent patent standards or following the strict procedures required to obtain patent protection. This too would seem to turn copyright inside out.
Because interfaces, algorithms, logic, and functionalities of programs are aspects of programs that make them valuable, it is understandable that some of those who seek to maximize their financial returns on software investments have argued that "strong" copyright protection is or should be available for all valuable features of programs, either as part of program sso or under the Whelan "there's-another-way-to-do-it" test. 43 Congress seems to have intended for copyright law to be interpreted as to programs on a case-by-case basis, and if courts determine that valuable features should be considered "expressive," the strong protectionists would applaud this common law evolution. If traditional concepts of copyright law and its purposes do not provide an adequate degree of protection for software innovation, they see it as natural that copyright should grow to provide it. Strong protectionists tend to regard traditionalists as sentimental Luddites who do not appreciate that what matters is for software to get the degree of protection it needs from the law so that the industry will thrive.
Although some cases, most notably the Whelan and Lotus decisions, have adopted the strong protectionist view, traditionalists will tend to regard these decisions as flawed and unlikely to be affirmed in the long run because they are inconsistent with the expressed legislative intent to have traditional principles of copyright law applied to software. Some copyright traditionalists favor patent protection for software innovations on the ground that the valuable functional elements of programs do need protection to create proper incentives for investing in software innovations, but that this protection should come from patent law, not from copyright law.
Controversy Over "Software Patents"
Although some perceive patents as a way to protect valuable aspects of programs that cannot be protected by copyright law, those who argue for patents for software innovations do not rely on the "gap-filling" concern alone. As a legal matter, proponents of software patents point out that the patent statute makes new, nonobvious, and useful "processes" patentable. Programs themselves are processes; they also embody processes. 44 Computer hardware is clearly patentable, and it is a commonplace in the computing field that any tasks for which a program can be written can also be implemented in hardware. This too would seem to support the patentability of software.
Proponents also argue that protecting program innovations by patent law is consistent with the constitutional purpose of patent law, which is to promote progress in the "useful arts." Computer program innovations are technological in nature, which is said to make them part of the useful arts to which the Constitution refers. Proponents insist that patent law has the same potential for promoting progress in the software field as it has had for promoting progress in other technological fields. They regard attacks on patents for software innovations as reflective of the passing of the frontier in the software industry, a painful transition period for some, but one necessary if the industry is to have sufficient incentives to invest in software development.
Some within the software industry and the technical community, however, oppose patents for software innovations. 45 Opponents tend to make two kinds of arguments against software patents, often without distinguishing between them. One set of arguments questions the ability of the PTO to deal well with software patent applications. Another set raises more fundamental questions about software patents. Even assuming that the PTO could begin to do a good job at issuing software patents, some question whether
innovation in the software field will be properly promoted if patents become widely available for software innovations. The main points of both sets of arguments are developed below.
Much of the discussion in the technical community has focused on "bad" software patents that have been issued by the PTO. Some patents are considered bad because the innovation was, unbeknownst to the PTO, already in the state of the art prior to the date of invention claimed in the patent. Others are considered bad because critics assert that the innovations they embody are too obvious to be deserving of patent protection. Still others are said to be bad because they are tantamount to a claim for performing a particular function by computer or to a claim for a law of nature, neither of which is regarded as patentable subject matter. Complaints abound that the PTO, after decades of not keeping up with developments in this field, is so far out of touch with what has been and is happening in the field as to be unable to make appropriate judgments on novelty and nonobviousness issues. Other complaints relate to the office's inadequate classification scheme for software and lack of examiners with suitable education and experience in computer science and related fields to make appropriate judgments on software patent issues. 46
A somewhat different point is made by those who assert that the software industry has grown to its current size and prosperity without the aid of patents, which causes them to question the need for patents to promote innovation in this industry. 47 The highly exclusionary nature of patents (any use of the innovation without the patentee's permission is infringing) contrasts sharply with the tradition of independent reinvention in this field. The high expense associated with obtaining and enforcing patents raises concerns about the increased barriers to entry that may be created by the patenting of software innovations. Since much of the innovation in this industry has come from small firms, policies that inhibit entry by small firms may not promote innovation in this field in the long run. Similar questions arise as to whether patents will promote a proper degree of innovation in an incremental industry such as the software industry. It would be possible to undertake an economic study of conditions that have promoted and are promoting progress in the software industry to serve as a basis for a policy decision on software patents, but this has not been done to date.
Some computer scientists and mathematicians are also concerned about patents that have been issuing for algorithms, 48 which they regard as dis-
coveries of fundamental truths that should not be owned by anyone. Because any use of a patented algorithm within the scope of the claims—whether by an academic or a commercial programmer, whether one knew of the patent or not—may be an infringement, some worry that research on algorithms will be slowed down by the issuance of algorithm patents. One mathematical society has recently issued a report opposing the patenting of algorithms. 49 Others, including Richard Stallman, have formed a League for Programming Freedom.
There is substantial case law to support the software patent opponent position, notwithstanding the PTO change in policy. 50 Three U.S. Supreme Court decisions have stated that computer program algorithms are unpatentable subject matter. Other case law affirms the unpatentability of processes that involve the manipulation of information rather than the transformation of matter from one physical state to another.
One other concern worth mentioning if both patents and copyrights are used to protect computer program innovations is whether a meaningful boundary line can be drawn between the patent and copyright domains as regards software. 51 A joint report of the U.S. PTO and the Copyright Office optimistically concludes that no significant problems will arise from the coexistence of these two forms of protection for software because copyright law will only protect program "expression" whereas patent law will only protect program "processes." 52
Notwithstanding this report, I continue to be concerned with the patent/ copyright interface because of the expansive interpretations some cases, particularly Whelan, have given to the scope of copyright protection for programs. This prefigures a significant overlap of copyright and patent law as to software innovations. This overlap would undermine important economic and public policy goals of the patent system, which generally leaves in the public domain those innovations not novel or nonobvious enough to be patented. Mere "originality" in a copyright sense is not enough to make an innovation in the useful arts protectable under U.S. law. 53
A concrete example may help illustrate this concern. Some patent lawyers report getting patents on data structures for computer programs.
The Whelan decision relied in part on similarities in data structures to prove copyright infringement. Are data structures "expressive" or "useful"? When one wants to protect a data structure of a program by copyright, does one merely call it part of the sso of the program, whereas if one wants to patent it, one calls it a method (i.e., a process) of organizing data for accomplishing certain results? What if anything does copyright's exclusion from protection of processes embodied in copyrighted works mean as applied to data structures? No clear answer to these questions emerges from the case law.
Nature of Computer Programs and Exploration of a Modified Copyright Approach
It may be that the deeper problem is that computer programs, by their very nature, challenge or contradict some fundamental assumptions of the existing intellectual property regimes. Underlying the existing regimes of copyright and patent law are some deeply embedded assumptions about the very different nature of two kinds of innovations that are thought to need very different kinds of protection owing to some important differences in the economic consequences of their protection. 54
In the United States, these assumptions derive largely from the U.S. Constitution, which specifically empowers Congress "to promote the progress of science [i.e., knowledge] and useful arts [i.e., technology], by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries." 55 This clause has historically been parsed as two separate clauses packaged together for convenience: one giving Congress power to enact laws aimed at promoting the progress of knowledge by giving authors exclusive rights in their writings, and the other giving Congress power to promote technological progress by giving inventors exclusive rights in their technological discoveries. Copyright law implements the first power, and patent law the second.
Owing partly to the distinctions between writings and machines, which the constitutional clause itself set up, copyright law has excluded machines
and other technological subject matters from its domain. 56 Even when described in a copyrighted book, an innovation in the useful arts was considered beyond the scope of copyright protection. The Supreme Court's Baker v. Selden decision reflects this view of the constitutional allocation. Similarly, patent law has historically excluded printed matter (i.e., the contents of writings) from its domain, notwithstanding the fact that printed matter may be a product of a manufacturing process. 57 Also excluded from the patent domain have been methods of organizing, displaying, and manipulating information (i.e., processes that might be embodied in writings, for example mathematical formulas), notwithstanding the fact that "processes" are named in the statute as patentable subject matter. They were not, however, perceived to be "in the useful arts" within the meaning of the constitutional clause.
The constitutional clause has been understood as both a grant of power and a limitation on power. Congress cannot, for example, grant perpetual patent rights to inventors, for that would violate the "limited times" provision of the Constitution. Courts have also sometimes ruled that Congress cannot, under this clause, grant exclusive rights to anyone but authors and inventors. In the late nineteenth century, the Supreme Court struck down the first federal trademark statute on the ground that Congress did not have power to grant rights under this clause to owners of trademarks who were neither "authors" nor "inventors." 58 A similar view was expressed in last year's Feist Publications v. Rural Telephone Services decision by the Supreme Court, which repeatedly stated that Congress could not constitutionally protect the white pages of telephone books through copyright law because to be an "author" within the meaning of the Constitution required some creativity in expression that white pages lacked. 59
Still other Supreme Court decisions have suggested that Congress could not constitutionally grant exclusive rights to innovators in the useful arts who were not true "inventors." 60 Certain economic assumptions are connected with this view, including the assumption that more modest innovations in the useful arts (the work of a mere mechanic) will be forthcoming without the grant of the exclusive rights of a patent, but that the incentives of patent rights are necessary to make people invest in making significant technological advances and share the results of their work with the public instead of keeping them secret.
One reason the United States does not have a copyright-like form of protection for industrial designs, as do many other countries, is because of lingering questions about the constitutionality of such legislation. In addition, concerns exist that the economic consequences of protecting uninventive technological advances will be harmful. So powerful are the prevailing patent and copyright paradigms that when Congress was in the process of considering the adoption of a copyright-like form of intellectual property protection for semiconductor chip designs, there was considerable debate about whether Congress had constitutional power to enact such a law. It finally decided it did have such power under the commerce clause, but even then was not certain.
As this discussion reveals, the U.S. intellectual property law has long assumed that something is either a writing (in which case it is protectable, if at all, by copyright law) or a machine (in which case it is protectable, if at all, by patent law), but cannot be both at the same time. However, as Professor Randall Davis has so concisely said, software is "a machine whose medium of construction happens to be text." 61 Davis regards the act of creating computer programs as inevitably one of both authorship and invention. There may be little or nothing about a computer program that is not, at base, functional in nature, and nothing about it that does not have roots in the text. Because of this, it will inevitably be difficult to draw meaningful boundaries for patents and copyrights as applied to computer programs.
Another aspect of computer programs that challenges the assumptions of existing intellectual property systems is reflected in another of Professor Davis's observations, namely, that "programs are not only texts; they also behave." 62 Much of the dynamic behavior of computer programs is highly functional in nature. If one followed traditional copyright principles, this functional behavior—no matter how valuable it might be—would be considered outside the scope of copyright law. 63 Although the functionality of program behavior might seem at first glance to mean that patent protection would be the obvious form of legal protection for it, as a practical matter, drafting patent claims that would adequately capture program behavior as an invention is infeasible. There are at least two reasons for this: it is partly because programs are able to exhibit such a large number and variety of states that claims could not reasonably cover them, and partly because of
the ''gestalt"-like character of program behavior, something that makes a more copyright-like approach desirable.
Some legal scholars have argued that because of their hybrid character as both writings and machines, computer programs need a somewhat different legal treatment than either traditional patent or copyright law would provide. 64 They have warned of distortions in the existing legal systems likely to occur if one attempts to integrate such a hybrid into the traditional systems as if it were no different from the traditional subject matters of these systems. 65 Even if the copyright and patent laws could be made to perform their tasks with greater predictability than is currently the case, these authors warn that such regimes may not provide the kind of protection that software innovators really need, for most computer programs will be legally obvious for patent purposes, and programs are, over time, likely to be assimilated within copyright in a manner similar to that given to "factual" and "functional" literary works that have only "thin" protection against piracy. 66
Professor Reichman has reported on the recurrent oscillations between states of under- and overprotection when legal systems have tried to cope with another kind of legal hybrid, namely, industrial designs (sometimes referred to as "industrial art"). Much the same pattern seems to be emerging in regard to computer programs, which are, in effect, "industrial literature." 67
The larger problems these hybrids present is that of protecting valuable forms of applied know-how embodied in incremental innovation that cannot successfully be maintained as trade secrets:
[M]uch of today's most advanced technology enjoys a less favorable competitive position than that of conventional machinery because the unpatentable, intangible know-how responsible for its commercial value becomes embodied in products that are distributed on the open market. A product of the new technologies, such as a computer program, an integrated circuit
design, or even a biogenetically altered organism may thus bear its know-how on its face, a condition that renders it as vulnerable to rapid appropriation by second-comers as any published literary or artistic work.
From this perspective, a major problem with the kinds of innovative know-how underlying important new technologies is that they do not lend themselves to secrecy even when they represent the fruit of enormous investment in research and development. Because third parties can rapidly duplicate the embodied information and offer virtually the same products at lower prices than those of the originators, there is no secure interval of lead time in which to recuperate the originators' initial investment or their losses from unsuccessful essays, not to mention the goal of turning a profit. 68
From a behavioral standpoint, investors in applied scientific know-how find the copyright paradigm attractive because of its inherent disposition to supply artificial lead time to all comers without regard to innovative merit and without requiring originators to preselect the products that are most worthy of protection. 69
Full copyright protection, however, with its broad notion of equivalents geared to derivative expressions of an author's personality is likely to disrupt the workings of the competitive market for industrial products. For this and other reasons, Professor Reichman argues that a modified copyright approach to the protection of computer programs (and other legal hybrids) would be a preferable framework for protecting the applied know-how they embody than either the patent or the copyright regime would presently provide. Similar arguments can be made for a modified form of copyright protection for the dynamic behavior of programs. A modified copyright approach might involve a short duration of protection for original valuable functional components of programs. It could be framed to supplement full copyright protection for program code and traditionally expressive elements of text and graphics displayed when programs execute, features of software that do not present the same dangers of competitive disruption from full copyright protection.
The United States is, in large measure, already undergoing the development of a sui generis law for protection of computer software through case-by-case decisions in copyright lawsuits. Devising a modified copyright approach to protecting certain valuable components that are not suitably protected under the current copyright regime would have the advantage of allowing a conception of the software protection problem as a whole, rather than on a piecemeal basis as occurs in case-by-case litigation in which the
skills of certain attorneys and certain facts may end up causing the law to develop in a skewed manner. 70
There are, however, a number of reasons said to weigh against sui generis legislation for software, among them the international consensus that has developed on the use of copyright law to protect software and the trend toward broader use of patents for software innovations. Some also question whether Congress would be able to devise a more appropriate sui generis system for protecting software than that currently provided by copyright. Some are also opposed to sui generis legislation for new technology products such as semiconductor chips and software on the ground that new intellectual property regimes will make intellectual property law more complicated, confusing, and uncertain.
Although there are many today who ardently oppose sui generis legislation for computer programs, these same people may well become among the most ardent proponents of such legislation if the U.S. Supreme Court, for example, construes the scope of copyright protection for programs to be quite thin, and reiterates its rulings in Benson, Flook, and Diehr that patent protection is unavailable for algorithms and other information processes embodied in software.
INTERNATIONAL PERSPECTIVES
After adopting copyright as a form of legal protection for computer programs, the United States campaigned vigorously around the world to persuade other nations to protect computer programs by copyright law as well. These efforts have been largely successful. Although copyright is now an international norm for the protection of computer software, the fine details of what copyright protection for software means, apart from protection against exact copying of program code, remain somewhat unclear in other nations, just as in the United States.
Other industrialized nations have also tended to follow the U.S. lead concerning the protection of computer program-related inventions by patent
law. 71 Some countries that in the early 1960s were receptive to the patenting of software innovations became less receptive after the Gottschalk v. Benson decision by the U.S. Supreme Court. Some even adopted legislation excluding computer programs from patent protection. More recently, these countries are beginning to issue more program-related patents, once again paralleling U.S. experience, although as in the United States, the standards for patentability of program-related inventions are somewhat unclear. 72 If the United States and Japan continue to issue a large number of computer program-related patents, it seems quite likely other nations will follow suit.
There has been strong pressure in recent years to include relatively specific provisions about intellectual property issues (including those affecting computer programs) as part of the international trade issues within the framework of the General Agreement on Tariffs and Trade (GATT). 73 For a time, the United States was a strong supporter of this approach to resolution of disharmonies among nations on intellectual property issues affecting software. The impetus for this seems to have slackened, however, after U.S. negotiators became aware of a lesser degree of consensus among U.S. software developers on certain key issues than they had thought was the case. Since the adoption of its directive on software copyright law, the European Community (EC) has begun pressing for international adoption of its position on a number of important software issues, including its copyright rule on decompilation of program code.
There is a clear need, given the international nature of the market for software, for a substantial international consensus on software protection issues. However, because there are so many hotly contested issues concerning the extent of copyright and the availability of patent protection for computer programs yet to be resolved, it may be premature to include very specific rules on these subjects in the GATT framework.
Prior to the adoption of the 1991 European Directive on the Protection of Computer Programs, there was general acceptance in Europe of copyright as a form of legal protection for computer programs. A number of nations had interpreted existing copyright statutes as covering programs. Others took legislative action to extend copyright protection to software. There was, however, some divergence in approach among the member nations of the EC in the interpretation of copyright law to computer software. 74
France, for example, although protecting programs under its copyright law, put software in the same category as industrial art, a category of work that is generally protected in Europe for 25 years instead of the life plus 50-year term that is the norm for literary and other artistic works. German courts concluded that to satisfy the "originality" standard of its copyright law, the author of a program needed to demonstrate that the program was the result of more than an average programmer's skill, a seemingly patentlike standard. In 'addition, Switzerland (a non-EC member but European nonetheless) nearly adopted an approach that treated both semiconductor chip designs and computer programs under a new copyright-like law.
Because of these differences and because it was apparent that computer programs would become an increasingly important item of commerce in the European Community, the EC undertook in the late 1980s to develop a policy concerning intellectual property protection for computer programs to which member nations should harmonize their laws. There was some support within the EC for creating a new law for the protection of software, but the directorate favoring a copyright approach won this internal struggle over what form of protection was appropriate for software.
In December 1988 the EC issued a draft directive on copyright protection for computer programs. This directive was intended to spell out in considerable detail in what respects member states should have uniform rules on copyright protection for programs. (The European civil law tradition generally prefers specificity in statutory formulations, in contrast with the U.S. common law tradition, which often prefers case-by-case adjudication of disputes as a way to fill in the details of a legal protection scheme.)
The draft directive on computer programs was the subject of intense debate within the European Community, as well as the object of some intense lobbying by major U.S. firms who were concerned about a number of issues, but particularly about what rule would be adopted concerning decompilation of program code and protection of the internal interfaces of
programs. Some U.S. firms, among them IBM Corp., strongly opposed any provision that would allow decompilation of program code and sought to have interfaces protected; other U.S. firms, such as Sun Microsystems, sought a rule that would permit decompilation and would deny protection to internal interfaces. 75
The final EC directive published in 1991 endorses the view that computer programs should be protected under member states' copyright laws as literary works and given at least 50 years of protection against unauthorized copying. 76 It permits decompilation of program code only if and to the extent necessary to obtain information to create an interoperable program. The inclusion in another program of information necessary to achieve interoperability seems, under the final directive, to be lawful.
The final EC directive states that "ideas" and "principles" embodied in programs are not protectable by copyright, but does not provide examples of what these terms might mean. The directive contains no exclusion from protection of such things as processes, procedures, methods of operation, and systems, as the U.S. statute provides. Nor does it clearly exclude protection of algorithms, interfaces, and program logic, as an earlier draft would have done. Rather, the final directive indicates that to the extent algorithms, logic, and interfaces are ideas, they are unprotectable by copyright law. In this regard, the directive seems, quite uncharacteristically for its civil law tradition, to leave much detail about how copyright law will be applied to programs to be resolved by litigation.
Having just finished the process of debating the EC directive about copyright protection of computer programs, intellectual property specialists in the EC have no interest in debating the merits of any sui generis approach to software protection, even though the only issue the EC directive really resolved may have been that of interoperability. Member states will likely have to address another controversial issue—whether or to what extent user interests in standardization of user interfaces should limit the scope of copyright
protection for programs—as they act on yet another EC directive, one that aims to standardize user interfaces of computer programs. Some U.S. firms may perceive this latter directive as an effort to appropriate valuable U.S. product features.
Japan was the first major industrialized nation to consider adoption of a sui generis approach to the protection of computer programs. 77 Its Ministry of International Trade and Industry (MITI) published a proposal that would have given 15 years of protection against unauthorized copying to computer programs that could meet a copyright-like originality standard under a copyright-like registration regime. MITI attempted to justify its proposed different treatment for computer programs as one appropriate to the different character of programs, compared with traditional copyrighted works. 78 The new legal framework was said to respond and be tailored to the special character of programs. American firms, however, viewed the MITI proposal, particularly its compulsory license provisions, as an effort by the Japanese to appropriate the valuable products of the U.S. software industry. Partly as a result of U.S. pressure, the MITI proposal was rejected by the Japanese government, and the alternative copyright proposal made by the ministry with jurisdiction over copyright law was adopted.
Notwithstanding their inclusion in copyright law, computer programs are a special category of protected work under Japanese law. Limiting the scope of copyright protection for programs is a provision indicating that program languages, rules, and algorithms are not protected by copyright law. 79 Japanese case law under this copyright statute has proceeded along lines similar to U.S. case law, with regard to exact and near-exact copying of program code and graphical aspects of videogame programs, 80 but there have been some Japanese court decisions interpreting the exclusion from protection provisions in a manner seemingly at odds with some U.S. Decisions.
The Tokyo High Court, for example, has opined that the processing flow of a program (an aspect of a program said to be protectable by U.S. law in the Whelan case) is an algorithm within the meaning of the copyright limitation provision. 81 Another seems to bear out Professor Karjala's prediction that Japanese courts would interpret the programming language limitation to permit firms to make compatible software. 82 There is one Japanese decision that can be read to prohibit reverse engineering of program code, but because this case involved not only disassembly of program code but also distribution of a clearly infringing program, the legality of intermediate copying to discern such things as interface information is unclear in Japan. 83
Other Nations
The United States has been pressing a number of nations to give "proper respect" to U.S. intellectual property products, including computer programs. In some cases, as in its dealings with the People's Republic of China, the United States has been pressing for new legislation to protect software under copyright law. In some cases, as in its dealings with Thailand, the United States has been pressing for more vigorous enforcement of intellectual property laws as they affect U.S. intellectual property products. In other cases, as in its dealings with Brazil, the United States pressed for repeal of sui generis legislation that disadvantaged U.S. software producers, compared with Brazilian developers. The United States has achieved some success in these efforts. Despite these successes, piracy of U.S.-produced software and other intellectual property products remains a substantial source of concern.
FUTURE CHALLENGES
Many of the challenges posed by use of existing intellectual property laws to protect computer programs have been discussed in previous sections. This may, however, only map the landscape of legal issues of widespread concern today. Below are some suggestions about issues as to which computer programs may present legal difficulties in the future.
Advanced Software Systems
It has thus far been exceedingly difficult for the legal system to resolve even relatively simple disputes about software intellectual property rights, such as those involved in the Lotus v. Paperback Software case. This does not bode well for how the courts are likely to deal with more complex problems presented by more complex software in future cases. The difficulties arise partly from the lack of familiarity of judges with the technical nature of computers and software, and partly from the lack of close analogies within the body of copyright precedents from which resolutions of software issues might be drawn. The more complex the software, the greater is the likelihood that specially trained judges will be needed to resolve intellectual property disputes about the software. Some advanced software systems are also likely to be sufficiently different from traditional kinds of copyrighted works that the analogical distance between the precedents and a software innovation may make it difficult to predict how copyright law should be applied to it. What copyright protection should be available, for example, to a user interface that responds to verbal commands, gestures, or movements of eyeballs?
Digital Media
The digital medium itself may require adaptation of the models underlying existing intellectual property systems. 84 Copyright law is built largely on the assumption that authors and publishers can control the manufacture and distribution of copies of protected works emanating from a central source. The ease with which digital works can be copied, redistributed, and used by multiple users, as well as the compactness and relative invisibility of works in digital form, have already created substantial incentives for developers of digital media products to focus their commercialization efforts on controlling the uses of digital works, rather than on the distribution of copies, as has more commonly been the rule in copyright industries.
Rules designed for controlling the production and distribution of copies may be difficult to adapt to a system in which uses need to be controlled. Some digital library and hypertext publishing systems seem to be designed to bypass copyright law (and its public policy safeguards, such as the fair use rule) and establish norms of use through restrictive access licensing
agreements. 85 Whether the law will eventually be used to regulate conditions imposed on access to these systems, as it has regulated access to such communication media as broadcasting, remains to be seen. However, the increasing convergence of intellectual property policy, broadcast and telecommunications policy, and other aspects of information policy seems inevitable.
There are already millions of people connected to networks of computers, who are thereby enabled to communicate with one another with relative ease, speed, and reliability. Plans are afoot to add millions more and to allow a wide variety of information services to those connected to the networks, some of which are commercial and some of which are noncommercial in nature. Because networks of this type and scope are a new phenomenon, it would seem quite likely that some new intellectual property issues will arise as the use of computer networks expands. The more commercial the uses of the networks, the more likely intellectual property disputes are to occur.
More of the content distributed over computer networks is copyrighted than its distributors seem to realize, but even as to content that has been recognized as copyrighted, there is a widespread belief among those who communicate over the net that at least noncommercial distributions of content—no matter the number of recipients—are "fair uses" of the content. Some lawyers would agree with this; others would not. Those responsible for the maintenance of the network may need to be concerned about potential liability until this issue is resolved.
A different set of problems may arise when commercial uses are made of content distributed over the net. Here the most likely disputes are those concerning how broad a scope of derivative work rights copyright owners should have. Some owners of copyrights can be expected to resist allowing anyone but themselves (or those licensed by them) to derive any financial benefit from creating a product or service that is built upon the value of their underlying work. Yet value-added services may be highly desirable to consumers, and the ability of outsiders to offer these products and services may spur beneficial competition. At the moment, the case law generally regards a copyright owner's derivative work right as infringed only if a recognizable block of expression is incorporated into another work. 86 How-
ever, the ability of software developers to provide value-added products and services that derive value from the underlying work without copying expression from it may lead some copyright owners to seek to extend the scope of derivative work rights.
Patents and Information Infrastructure of the Future
If patents are issued for all manner of software innovations, they are likely to play an important role in the development of the information infrastructure of the future. Patents have already been issued for hypertext navigation systems, for such things as latent semantic indexing algorithms, and for other software innovations that might be used in the construction of a new information infrastructure. Although it is easy to develop a list of the possible pros and cons of patent protection in this domain, as in the more general debate about software patents, it is worth noting that patents have not played a significant role in the information infrastructure of the past or of the present. How patents would affect the development of the new information infrastructure has not been given the study this subject may deserve.
Conflicts Between Information Haves and Have-Nots on an International Scale
When the United States was a developing nation and a net importer of intellectual property products, it did not respect copyright interests of any authors but its own. Charles Dickens may have made some money from the U.S. tours at which he spoke at public meetings, but he never made a dime from the publication of his works in the United States. Now that the United States is a developed nation and a net exporter of intellectual property products, its perspective on the rights of developing nations to determine for themselves what intellectual property rights to accord to the products of firms of the United States and other developed nations has changed. Given the greater importance nowadays of intellectual property products, both to the United States and to the world economy, it is foreseeable that there will be many occasions on which developed and developing nations will have disagreements on intellectual property issues.
The United States will face a considerable challenge in persuading other nations to subscribe to the same detailed rules that it has for dealing with intellectual property issues affecting computer programs. It may be easier for the United States to deter outright ''piracy" (unauthorized copying of the whole or substantially the whole of copyrighted works) of U.S. intellectual property products than to convince other nations that they must adopt the same rules as the United States has for protecting software.
It is also well for U.S. policymakers and U.S. firms to contemplate the possibility that U.S. firms may not always have the leading position in the world market for software products that they enjoy today. When pushing for very "strong" intellectual property protection for software today in the expectation that this will help to preserve the U.S. advantage in the world market, U.S. policymakers should be careful not to push for adoption of rules today that may substantially disadvantage them in the world market of the future if, for reasons not foreseen today, the United States loses the lead it currently enjoys in the software market.
As technological developments multiply around the globe—even as the patenting of human genes comes under serious discussion—nations, companies, and researchers find themselves in conflict over intellectual property rights (IPRs). Now, an international group of experts presents the first multidisciplinary look at IPRs in an age of explosive growth in science and technology.
This thought-provoking volume offers an update on current international IPR negotiations and includes case studies on software, computer chips, optoelectronics, and biotechnology—areas characterized by high development cost and easy reproducibility. The volume covers these and other issues:
- Modern economic theory as a basis for approaching international IPRs.
- U.S. intellectual property practices versus those in Japan, India, the European Community, and the developing and newly industrializing countries.
- Trends in science and technology and how they affect IPRs.
- Pros and cons of a uniform international IPRs regime versus a system reflecting national differences.
READ FREE ONLINE
Welcome to OpenBook!
You're looking at OpenBook, NAP.edu's online reading room since 1999. Based on feedback from you, our users, we've made some improvements that make it easier than ever to read thousands of publications on our website.
Do you want to take a quick tour of the OpenBook's features?
Show this book's table of contents , where you can jump to any chapter by name.
...or use these buttons to go back to the previous chapter or skip to the next one.
Jump up to the previous page or down to the next one. Also, you can type in a page number and press Enter to go directly to that page in the book.
Switch between the Original Pages , where you can read the report as it appeared in print, and Text Pages for the web version, where you can highlight and search the text.
To search the entire text of this book, type in your search term here and press Enter .
Share a link to this book page on your preferred social network or via email.
View our suggested citation for this chapter.
Ready to take your reading offline? Click here to buy this book in print or download it as a free PDF, if available.
Get Email Updates
Do you enjoy reading reports from the Academies online for free ? Sign up for email notifications and we'll let you know about new publications in your areas of interest when they're released.
2020 case study

- 1 Introduction
- 2 The case study
- 3 Every Term in the Case Study
- 4 Previous years case studies
- 5 References
Introduction [ edit ]
Higher-level students must write 3 papers. The case study is the third paper. Every year, the case study discusses a different topic. Students must become very very familiar with the case study . The IB recommends spending about a year studying this guide.
This page will help you organize and understand the 2020 case study .
The case study [ edit ]
Click here for the full pdf case study for 2021
Every Term in the Case Study [ edit ]
- Please visit our programming page to see a list of terms involved in blockchain .
Previous years case studies [ edit ]
- Click here for the 2019 case study
- Click here for the 2018 case study
- Click here for the 2017 case study
- Click here for the 2016 case study
References [ edit ]
- ↑ http://www.flaticon.com/
Devote time and attention to gaining knowledge of (an academic subject), especially by means of books
Give a sequence of brief answers with no explanation.
- Publications
- Conferences & Events
- Professional Learning
- Science Standards
- Awards & Competitions
- Daily Do Lesson Plans
- Free Resources
- American Rescue Plan
- For Preservice Teachers
- NCCSTS Case Collection
- Partner Jobs in Education
- Interactive eBooks+
- Digital Catalog
- Regional Product Representatives
- e-Newsletters
- Bestselling Books
- Latest Books
- Popular Book Series
- Prospective Authors
- Web Seminars
- Exhibits & Sponsorship
- Conference Reviewers
- National Conference • Denver 24
- Leaders Institute 2024
- National Conference • New Orleans 24
- Submit a Proposal
- Latest Resources
- Professional Learning Units & Courses
- For Districts
- Online Course Providers
- Schools & Districts
- College Professors & Students
- The Standards
- Teachers and Admin
- eCYBERMISSION
- Toshiba/NSTA ExploraVision
- Junior Science & Humanities Symposium
- Teaching Awards
- Climate Change
- Earth & Space Science
- New Science Teachers
- Early Childhood
- Middle School
- High School
- Postsecondary
- Informal Education
- Journal Articles
- Lesson Plans
- e-newsletters
- Science & Children
- Science Scope
- The Science Teacher
- Journal of College Sci. Teaching
- Connected Science Learning
- NSTA Reports
- Next-Gen Navigator
- Science Update
- Teacher Tip Tuesday
- Trans. Sci. Learning
MyNSTA Community
- My Collections
Case Studies: Computer Science
Narrow your search.
- Bioinformatics
All Computer Science Cases
A Bioinformatic Investigation of a Mysterious Meningoencephalitis
By Sari Matar, Dyan Anore, Basma Galal, Shawn Xiong
Is p53 a Smoking Gun?
By Michèle I. Shuster, Joann Mudge, Meghan Hill, Katelynn James, Gabriella A. DeFrancesco, Maria P. Chadiarakou, Anitha Sundararajan
Computers and Micronutrients
By Winyoo Chowanadisai, Bryant H. Keirns
The Stakeholders of Gorongosa National Park
By Andrea M.-K. Bierema, Sara D. Miller, Claudia E. Vergara
Seq’ ing the Cure: Standard Edition
By Heather B. Miller, Sabrina D. Robertson, Melissa C. Srougi
New Tricks for Old Drugs
By Carlos C. Goller, Stefanie H. Chen, Melissa C. Srougi
The Colors that Do Magic
By Ghizlane Bendriss, Ali Chaari, Kuei-Chiu Chen
Retinoblastoma
By Daniel B. Stovall
By Stefanie H. Chen, Carlos C. Goller, Melissa C. Srougi
Fatally Flawed?
By Amy C. Groth
100+ Computer Science Topics: A Comprehensive Guide

Computer Science is a vast and dynamic field that plays a fundamental role in today’s technological landscape. This blog aims to provide an overview of various computer science topics, from core concepts to specialized areas and emerging trends.
Whether you’re a student considering a computer science degree or someone interested in the latest developments in technology, this guide will help you navigate the world of computer science.
What Are The Core Concepts of Computer Science?
Table of Contents
Algorithms and Data Structures
At the heart of computer science lies the study of algorithms and data structures. Algorithms are step-by-step procedures for solving problems, and data structures are the ways we organize and store data.
They are crucial for problem-solving and efficient software development. Understanding algorithms and data structures is fundamental for any computer scientist.
Popular data structures include arrays, linked lists, trees, and hash tables, while common algorithms encompass sorting, searching, and graph algorithms. The data structure and method used can have a big influence on how well software runs.
Programming Languages
Computer science relies on a multitude of programming languages. From classics like C, C++, and Java to modern languages like Python and JavaScript, each language has its strengths and weaknesses.
The choice of programming language is based on the particular task at hand as well as elements like usability, performance, and library accessibility.
Learning multiple languages can make you a versatile programmer and open doors to different job opportunities. For instance, web development often requires JavaScript, while data science frequently employs Python.
How To Select Computer Science Topics?
Selecting computer science topics can be a daunting task, given the vastness of the field. Here are 10 steps to help you choose the right computer science topics:
- Identify Your Interests: Start by reflecting on one’s interests within computer science. Are you passionate about artificial intelligence, web development, cybersecurity, or data science? Knowing what excites you will make the selection process more manageable.
- Assess Your Knowledge: Consider your current knowledge and experience. If you’re a beginner, you may want to explore foundational topics like algorithms and data structures. For more advanced learners, specialized or emerging topics might be suitable.
- Research Current Trends: Stay updated (with trends) on the latest trends and emerging technologies in computer science. Read blogs, research papers, and news articles to understand what’s hot in the field. Topics like blockchain, quantum computing, and AI ethics are currently trending.
- Consider Your Career Goals: Think about your long-term career goals. If you aspire to become a data scientist, topics related to machine learning, data analysis, and big data are relevant. Tailor your choices to align with your career aspirations.
- Consult with Professors or Mentors: If you’re a student, reach out to your professors or mentors for guidance. They can recommend topics that match your skills and career goals and may even suggest research opportunities.
- Explore Core Concepts: Ensure you have a strong foundation by exploring core computer science concepts like algorithms, data structures, and programming languages. These fundamentals are essential for building expertise in other areas.
- Assess Practicality: Consider the practicality of the topic. Some topics may have limited real-world applications, while others can lead to tangible projects or research. Choose topics that allow you to apply your knowledge.
- Review Project Opportunities: If you’re looking to gain hands-on experience, assess the availability of projects related to your chosen topic. Many universities and online platforms offer project-based courses that can deepen your understanding.
- Balance Depth and Breadth: Strive for a balance between depth and breadth. While it’s essential to specialize in a particular area, computer science is an interdisciplinary field, and having a broad understanding can be valuable.
- Stay Flexible: Be open to changing your focus over time. As technology evolves, new topics emerge, and your interests may shift. Stay flexible and willing to adapt to the changing landscape of computer science.
Remember that selecting computer science topics is a personal and evolving process.
Your interests, career goals, and knowledge level will influence your choices. Keep learning, exploring, and adapting as you progress in your computer science journey.
100+ Computer Science Topics: Category Wise
- Sorting algorithms
- Graph algorithms
- Hashing techniques
- Binary search
- Tree data structures
- Python Programming
- JavaScript development
- C++ language features
- Functional programming
- Language paradigms
Artificial Intelligence and Machine Learning
- Neural networks
- Reinforcement learning
- Natural language processing
- Computer vision
- Deep learning frameworks
Cybersecurity
- Network security
- Ethical hacking
- Cryptography techniques
- Security Protocols
- Intrusion detection
Database Management
- SQL vs. NoSQL databases
- Query optimization
- Big Data technologies
- Database design principles
- Data warehousing
Computer Graphics and Visualization
- 3D rendering
- Animation techniques
- Virtual reality (VR)
- Augmented reality (AR)
- Computer-aided design (CAD)
Quantum Computing
- Quantum gates
- Quantum algorithms
- Quantum cryptography
- Quantum hardware
- Quantum supremacy
Internet of Things (IoT)
- IoT protocols
- Smart homes
- Industrial IoT
- Edge computing
- IoT security
Blockchain Technology
- Distributed ledger technology
- Smart contracts
- Cryptocurrency platforms
- Blockchain for supply chain
Computer Science Education
- Computer science degrees
- Online coding bootcamps
- Data science courses
- AI certifications
- MOOC platforms
Career Paths in Computer Science
- Software developer roles
- Data scientist jobs
- Network engineer careers
- Cybersecurity analyst positions
- Cloud computing specialists
Web Development
- Front-end development
- Back-end programming
- Full-stack development
- Responsive web design
- Web application frameworks

Operating Systems
- Linux distributions
- Windows internals
- Real-time operating systems
- File systems
- Process management
Computer Networks
- TCP/IP protocol suite
- Network topologies
- Wireless networks
- Network virtualization
- SDN and NFV
Software Engineering
- Agile methodologies
- DevOps practices
- Software testing
- Code quality and refactoring
- Project management tools
Data Science and Big Data
- Data preprocessing
- Machine learning pipelines
- Data visualization tools
- Hadoop and Spark
- Data analysis techniques
Game Development
- Game engines
- Unity and Unreal Engine
- Game design principles
- Game monetization strategies
- Mobile game development
Ethical AI and AI Ethics
- AI fairness
- AI accountability
- AI regulations
- AI for social good
Human-Computer Interaction (HCI)
- Usability testing
- User experience (UX) design
- HCI principles
- User interface (UI) guidelines
- Accessibility in HCI
Cloud Computing
- Cloud service providers
- Infrastructure as a Service (IaaS)
- Platform as a Service (PaaS)
- Serverless computing
- Cloud security
- Robotic sensors
- Robot control systems
- Swarm robotics
- Industrial robotics
- Humanoid robots
Emerging Trends and Technologies With Computer Science Topics
Utilizing the ideas of quantum physics, quantum computing is an interesting and relatively new topic that allows computations to be completed at rates that are not possible with traditional computers.
Drug research, optimization, and encryption are just a few of the industries that quantum computers have the potential to completely transform. Research in quantum computing is rapidly progressing, with companies like IBM and Google making significant strides.
The network of networked items and gadgets that gather and share data is referred to as the Internet of Things (IoT). From smart homes to industrial sensors, IoT is transforming the way we live and work. However, with the convenience and connectivity IoT offers, come concerns about security and privacy.
In order to solve these issues and guarantee the secure and effective operation of IoT devices, computer scientists will be essential as the Internet of Things grows.
Blockchain technology, known for its association with cryptocurrencies like Bitcoin, is finding applications in various sectors beyond finance. Blockchains provide secure and transparent ledgers for recording transactions and data.
Use cases range from supply chain management and voting systems to intellectual property protection.
As blockchain technology matures, computer scientists will find opportunities to develop innovative solutions and address its scalability and environmental concerns.
Computer Science Education and Career Paths
Computer science degrees and courses.
For those interested in pursuing a career in computer science, there are various educational paths to consider. These include bachelor’s, master’s, and Ph.D. programs, as well as online learning options.
When choosing a program, it’s essential to consider your goals, the curriculum, and the reputation of the institution.
Online learning platforms and coding bootcamps offer flexible options for acquiring computer science skills. They can be a good fit for those looking to pivot into a tech career or acquire specific programming skills.
Career Opportunities in Computer Science
Computer science offers a broad range of career opportunities. Job roles include software developer, data scientist, network engineer, cybersecurity analyst, and AI specialist, among others.
Salaries and job prospects vary depending on the role and your level of experience.
Computer science professionals are in demand in virtually every industry, from technology giants like Google and Amazon to healthcare, finance, and government agencies.
Computer science is a field of limitless potential and continuous growth. It underpins the technology that powers our world and shapes the future.
From the fundamentals of algorithms and data structures to the cutting-edge technologies of AI, quantum computing, and blockchain, computer science is a dynamic and ever-evolving discipline.
Whether you’re a student embarking on a computer science journey or a technology enthusiast exploring the latest trends, the diverse and exciting world of computer science offers something for everyone.
By staying informed and continually learning (with topics like computer science topics), you can contribute to the ongoing transformation of our digital landscape.
Related Posts

Top 10 Easy ways to improve programming skills for beginners
Programming skillsProgramming is a mixture of several skills which means it is not probable to study it in a speedy Period, relatively it will come…

How to Hire someone to do my Statistics Homework for Me?
Students ask to do my statistics homework for me. Although there are many online tutors or statistics homework service providing websites available to help you…

Top 40 Most Popular Case Studies of 2021
Two cases about Hertz claimed top spots in 2021's Top 40 Most Popular Case Studies
Two cases on the uses of debt and equity at Hertz claimed top spots in the CRDT’s (Case Research and Development Team) 2021 top 40 review of cases.
Hertz (A) took the top spot. The case details the financial structure of the rental car company through the end of 2019. Hertz (B), which ranked third in CRDT’s list, describes the company’s struggles during the early part of the COVID pandemic and its eventual need to enter Chapter 11 bankruptcy.
The success of the Hertz cases was unprecedented for the top 40 list. Usually, cases take a number of years to gain popularity, but the Hertz cases claimed top spots in their first year of release. Hertz (A) also became the first ‘cooked’ case to top the annual review, as all of the other winners had been web-based ‘raw’ cases.
Besides introducing students to the complicated financing required to maintain an enormous fleet of cars, the Hertz cases also expanded the diversity of case protagonists. Kathyrn Marinello was the CEO of Hertz during this period and the CFO, Jamere Jackson is black.
Sandwiched between the two Hertz cases, Coffee 2016, a perennial best seller, finished second. “Glory, Glory, Man United!” a case about an English football team’s IPO made a surprise move to number four. Cases on search fund boards, the future of malls, Norway’s Sovereign Wealth fund, Prodigy Finance, the Mayo Clinic, and Cadbury rounded out the top ten.
Other year-end data for 2021 showed:
- Online “raw” case usage remained steady as compared to 2020 with over 35K users from 170 countries and all 50 U.S. states interacting with 196 cases.
- Fifty four percent of raw case users came from outside the U.S..
- The Yale School of Management (SOM) case study directory pages received over 160K page views from 177 countries with approximately a third originating in India followed by the U.S. and the Philippines.
- Twenty-six of the cases in the list are raw cases.
- A third of the cases feature a woman protagonist.
- Orders for Yale SOM case studies increased by almost 50% compared to 2020.
- The top 40 cases were supervised by 19 different Yale SOM faculty members, several supervising multiple cases.
CRDT compiled the Top 40 list by combining data from its case store, Google Analytics, and other measures of interest and adoption.
All of this year’s Top 40 cases are available for purchase from the Yale Management Media store .
And the Top 40 cases studies of 2021 are:
1. Hertz Global Holdings (A): Uses of Debt and Equity
2. Coffee 2016
3. Hertz Global Holdings (B): Uses of Debt and Equity 2020
4. Glory, Glory Man United!
5. Search Fund Company Boards: How CEOs Can Build Boards to Help Them Thrive
6. The Future of Malls: Was Decline Inevitable?
7. Strategy for Norway's Pension Fund Global
8. Prodigy Finance
9. Design at Mayo
10. Cadbury
11. City Hospital Emergency Room
13. Volkswagen
14. Marina Bay Sands
15. Shake Shack IPO
16. Mastercard
17. Netflix
18. Ant Financial
19. AXA: Creating the New CR Metrics
20. IBM Corporate Service Corps
21. Business Leadership in South Africa's 1994 Reforms
22. Alternative Meat Industry
23. Children's Premier
24. Khalil Tawil and Umi (A)
25. Palm Oil 2016
26. Teach For All: Designing a Global Network
27. What's Next? Search Fund Entrepreneurs Reflect on Life After Exit
28. Searching for a Search Fund Structure: A Student Takes a Tour of Various Options
30. Project Sammaan
31. Commonfund ESG
32. Polaroid
33. Connecticut Green Bank 2018: After the Raid
34. FieldFresh Foods
35. The Alibaba Group
36. 360 State Street: Real Options
37. Herman Miller
38. AgBiome
39. Nathan Cummings Foundation
40. Toyota 2010
- Privacy Policy
Buy Me a Coffee

Home » 500+ Computer Science Research Topics
500+ Computer Science Research Topics

Computer Science is a constantly evolving field that has transformed the world we live in today. With new technologies emerging every day, there are countless research opportunities in this field. Whether you are interested in artificial intelligence, machine learning, cybersecurity, data analytics, or computer networks, there are endless possibilities to explore. In this post, we will delve into some of the most interesting and important research topics in Computer Science. From the latest advancements in programming languages to the development of cutting-edge algorithms, we will explore the latest trends and innovations that are shaping the future of Computer Science. So, whether you are a student or a professional, read on to discover some of the most exciting research topics in this dynamic and rapidly expanding field.
Computer Science Research Topics
Computer Science Research Topics are as follows:
- Using machine learning to detect and prevent cyber attacks
- Developing algorithms for optimized resource allocation in cloud computing
- Investigating the use of blockchain technology for secure and decentralized data storage
- Developing intelligent chatbots for customer service
- Investigating the effectiveness of deep learning for natural language processing
- Developing algorithms for detecting and removing fake news from social media
- Investigating the impact of social media on mental health
- Developing algorithms for efficient image and video compression
- Investigating the use of big data analytics for predictive maintenance in manufacturing
- Developing algorithms for identifying and mitigating bias in machine learning models
- Investigating the ethical implications of autonomous vehicles
- Developing algorithms for detecting and preventing cyberbullying
- Investigating the use of machine learning for personalized medicine
- Developing algorithms for efficient and accurate speech recognition
- Investigating the impact of social media on political polarization
- Developing algorithms for sentiment analysis in social media data
- Investigating the use of virtual reality in education
- Developing algorithms for efficient data encryption and decryption
- Investigating the impact of technology on workplace productivity
- Developing algorithms for detecting and mitigating deepfakes
- Investigating the use of artificial intelligence in financial trading
- Developing algorithms for efficient database management
- Investigating the effectiveness of online learning platforms
- Developing algorithms for efficient and accurate facial recognition
- Investigating the use of machine learning for predicting weather patterns
- Developing algorithms for efficient and secure data transfer
- Investigating the impact of technology on social skills and communication
- Developing algorithms for efficient and accurate object recognition
- Investigating the use of machine learning for fraud detection in finance
- Developing algorithms for efficient and secure authentication systems
- Investigating the impact of technology on privacy and surveillance
- Developing algorithms for efficient and accurate handwriting recognition
- Investigating the use of machine learning for predicting stock prices
- Developing algorithms for efficient and secure biometric identification
- Investigating the impact of technology on mental health and well-being
- Developing algorithms for efficient and accurate language translation
- Investigating the use of machine learning for personalized advertising
- Developing algorithms for efficient and secure payment systems
- Investigating the impact of technology on the job market and automation
- Developing algorithms for efficient and accurate object tracking
- Investigating the use of machine learning for predicting disease outbreaks
- Developing algorithms for efficient and secure access control
- Investigating the impact of technology on human behavior and decision making
- Developing algorithms for efficient and accurate sound recognition
- Investigating the use of machine learning for predicting customer behavior
- Developing algorithms for efficient and secure data backup and recovery
- Investigating the impact of technology on education and learning outcomes
- Developing algorithms for efficient and accurate emotion recognition
- Investigating the use of machine learning for improving healthcare outcomes
- Developing algorithms for efficient and secure supply chain management
- Investigating the impact of technology on cultural and societal norms
- Developing algorithms for efficient and accurate gesture recognition
- Investigating the use of machine learning for predicting consumer demand
- Developing algorithms for efficient and secure cloud storage
- Investigating the impact of technology on environmental sustainability
- Developing algorithms for efficient and accurate voice recognition
- Investigating the use of machine learning for improving transportation systems
- Developing algorithms for efficient and secure mobile device management
- Investigating the impact of technology on social inequality and access to resources
- Machine learning for healthcare diagnosis and treatment
- Machine Learning for Cybersecurity
- Machine learning for personalized medicine
- Cybersecurity threats and defense strategies
- Big data analytics for business intelligence
- Blockchain technology and its applications
- Human-computer interaction in virtual reality environments
- Artificial intelligence for autonomous vehicles
- Natural language processing for chatbots
- Cloud computing and its impact on the IT industry
- Internet of Things (IoT) and smart homes
- Robotics and automation in manufacturing
- Augmented reality and its potential in education
- Data mining techniques for customer relationship management
- Computer vision for object recognition and tracking
- Quantum computing and its applications in cryptography
- Social media analytics and sentiment analysis
- Recommender systems for personalized content delivery
- Mobile computing and its impact on society
- Bioinformatics and genomic data analysis
- Deep learning for image and speech recognition
- Digital signal processing and audio processing algorithms
- Cloud storage and data security in the cloud
- Wearable technology and its impact on healthcare
- Computational linguistics for natural language understanding
- Cognitive computing for decision support systems
- Cyber-physical systems and their applications
- Edge computing and its impact on IoT
- Machine learning for fraud detection
- Cryptography and its role in secure communication
- Cybersecurity risks in the era of the Internet of Things
- Natural language generation for automated report writing
- 3D printing and its impact on manufacturing
- Virtual assistants and their applications in daily life
- Cloud-based gaming and its impact on the gaming industry
- Computer networks and their security issues
- Cyber forensics and its role in criminal investigations
- Machine learning for predictive maintenance in industrial settings
- Augmented reality for cultural heritage preservation
- Human-robot interaction and its applications
- Data visualization and its impact on decision-making
- Cybersecurity in financial systems and blockchain
- Computer graphics and animation techniques
- Biometrics and its role in secure authentication
- Cloud-based e-learning platforms and their impact on education
- Natural language processing for machine translation
- Machine learning for predictive maintenance in healthcare
- Cybersecurity and privacy issues in social media
- Computer vision for medical image analysis
- Natural language generation for content creation
- Cybersecurity challenges in cloud computing
- Human-robot collaboration in manufacturing
- Data mining for predicting customer churn
- Artificial intelligence for autonomous drones
- Cybersecurity risks in the healthcare industry
- Machine learning for speech synthesis
- Edge computing for low-latency applications
- Virtual reality for mental health therapy
- Quantum computing and its applications in finance
- Biomedical engineering and its applications
- Cybersecurity in autonomous systems
- Machine learning for predictive maintenance in transportation
- Computer vision for object detection in autonomous driving
- Augmented reality for industrial training and simulations
- Cloud-based cybersecurity solutions for small businesses
- Natural language processing for knowledge management
- Machine learning for personalized advertising
- Cybersecurity in the supply chain management
- Cybersecurity risks in the energy sector
- Computer vision for facial recognition
- Natural language processing for social media analysis
- Machine learning for sentiment analysis in customer reviews
- Explainable Artificial Intelligence
- Quantum Computing
- Blockchain Technology
- Human-Computer Interaction
- Natural Language Processing
- Cloud Computing
- Robotics and Automation
- Augmented Reality and Virtual Reality
- Cyber-Physical Systems
- Computational Neuroscience
- Big Data Analytics
- Computer Vision
- Cryptography and Network Security
- Internet of Things
- Computer Graphics and Visualization
- Artificial Intelligence for Game Design
- Computational Biology
- Social Network Analysis
- Bioinformatics
- Distributed Systems and Middleware
- Information Retrieval and Data Mining
- Computer Networks
- Mobile Computing and Wireless Networks
- Software Engineering
- Database Systems
- Parallel and Distributed Computing
- Human-Robot Interaction
- Intelligent Transportation Systems
- High-Performance Computing
- Cyber-Physical Security
- Deep Learning
- Sensor Networks
- Multi-Agent Systems
- Human-Centered Computing
- Wearable Computing
- Knowledge Representation and Reasoning
- Adaptive Systems
- Brain-Computer Interface
- Health Informatics
- Cognitive Computing
- Cybersecurity and Privacy
- Internet Security
- Cybercrime and Digital Forensics
- Cloud Security
- Cryptocurrencies and Digital Payments
- Machine Learning for Natural Language Generation
- Cognitive Robotics
- Neural Networks
- Semantic Web
- Image Processing
- Cyber Threat Intelligence
- Secure Mobile Computing
- Cybersecurity Education and Training
- Privacy Preserving Techniques
- Cyber-Physical Systems Security
- Virtualization and Containerization
- Machine Learning for Computer Vision
- Network Function Virtualization
- Cybersecurity Risk Management
- Information Security Governance
- Intrusion Detection and Prevention
- Biometric Authentication
- Machine Learning for Predictive Maintenance
- Security in Cloud-based Environments
- Cybersecurity for Industrial Control Systems
- Smart Grid Security
- Software Defined Networking
- Quantum Cryptography
- Security in the Internet of Things
- Natural language processing for sentiment analysis
- Blockchain technology for secure data sharing
- Developing efficient algorithms for big data analysis
- Cybersecurity for internet of things (IoT) devices
- Human-robot interaction for industrial automation
- Image recognition for autonomous vehicles
- Social media analytics for marketing strategy
- Quantum computing for solving complex problems
- Biometric authentication for secure access control
- Augmented reality for education and training
- Intelligent transportation systems for traffic management
- Predictive modeling for financial markets
- Cloud computing for scalable data storage and processing
- Virtual reality for therapy and mental health treatment
- Data visualization for business intelligence
- Recommender systems for personalized product recommendations
- Speech recognition for voice-controlled devices
- Mobile computing for real-time location-based services
- Neural networks for predicting user behavior
- Genetic algorithms for optimization problems
- Distributed computing for parallel processing
- Internet of things (IoT) for smart cities
- Wireless sensor networks for environmental monitoring
- Cloud-based gaming for high-performance gaming
- Social network analysis for identifying influencers
- Autonomous systems for agriculture
- Robotics for disaster response
- Data mining for customer segmentation
- Computer graphics for visual effects in movies and video games
- Virtual assistants for personalized customer service
- Natural language understanding for chatbots
- 3D printing for manufacturing prototypes
- Artificial intelligence for stock trading
- Machine learning for weather forecasting
- Biomedical engineering for prosthetics and implants
- Cybersecurity for financial institutions
- Machine learning for energy consumption optimization
- Computer vision for object tracking
- Natural language processing for document summarization
- Wearable technology for health and fitness monitoring
- Internet of things (IoT) for home automation
- Reinforcement learning for robotics control
- Big data analytics for customer insights
- Machine learning for supply chain optimization
- Natural language processing for legal document analysis
- Artificial intelligence for drug discovery
- Computer vision for object recognition in robotics
- Data mining for customer churn prediction
- Autonomous systems for space exploration
- Robotics for agriculture automation
- Machine learning for predicting earthquakes
- Natural language processing for sentiment analysis in customer reviews
- Big data analytics for predicting natural disasters
- Internet of things (IoT) for remote patient monitoring
- Blockchain technology for digital identity management
- Machine learning for predicting wildfire spread
- Computer vision for gesture recognition
- Natural language processing for automated translation
- Big data analytics for fraud detection in banking
- Internet of things (IoT) for smart homes
- Robotics for warehouse automation
- Machine learning for predicting air pollution
- Natural language processing for medical record analysis
- Augmented reality for architectural design
- Big data analytics for predicting traffic congestion
- Machine learning for predicting customer lifetime value
- Developing algorithms for efficient and accurate text recognition
- Natural Language Processing for Virtual Assistants
- Natural Language Processing for Sentiment Analysis in Social Media
- Explainable Artificial Intelligence (XAI) for Trust and Transparency
- Deep Learning for Image and Video Retrieval
- Edge Computing for Internet of Things (IoT) Applications
- Data Science for Social Media Analytics
- Cybersecurity for Critical Infrastructure Protection
- Natural Language Processing for Text Classification
- Quantum Computing for Optimization Problems
- Machine Learning for Personalized Health Monitoring
- Computer Vision for Autonomous Driving
- Blockchain Technology for Supply Chain Management
- Augmented Reality for Education and Training
- Natural Language Processing for Sentiment Analysis
- Machine Learning for Personalized Marketing
- Big Data Analytics for Financial Fraud Detection
- Cybersecurity for Cloud Security Assessment
- Artificial Intelligence for Natural Language Understanding
- Blockchain Technology for Decentralized Applications
- Virtual Reality for Cultural Heritage Preservation
- Natural Language Processing for Named Entity Recognition
- Machine Learning for Customer Churn Prediction
- Big Data Analytics for Social Network Analysis
- Cybersecurity for Intrusion Detection and Prevention
- Artificial Intelligence for Robotics and Automation
- Blockchain Technology for Digital Identity Management
- Virtual Reality for Rehabilitation and Therapy
- Natural Language Processing for Text Summarization
- Machine Learning for Credit Risk Assessment
- Big Data Analytics for Fraud Detection in Healthcare
- Cybersecurity for Internet Privacy Protection
- Artificial Intelligence for Game Design and Development
- Blockchain Technology for Decentralized Social Networks
- Virtual Reality for Marketing and Advertising
- Natural Language Processing for Opinion Mining
- Machine Learning for Anomaly Detection
- Big Data Analytics for Predictive Maintenance in Transportation
- Cybersecurity for Network Security Management
- Artificial Intelligence for Personalized News and Content Delivery
- Blockchain Technology for Cryptocurrency Mining
- Virtual Reality for Architectural Design and Visualization
- Natural Language Processing for Machine Translation
- Machine Learning for Automated Image Captioning
- Big Data Analytics for Stock Market Prediction
- Cybersecurity for Biometric Authentication Systems
- Artificial Intelligence for Human-Robot Interaction
- Blockchain Technology for Smart Grids
- Virtual Reality for Sports Training and Simulation
- Natural Language Processing for Question Answering Systems
- Machine Learning for Sentiment Analysis in Customer Feedback
- Big Data Analytics for Predictive Maintenance in Manufacturing
- Cybersecurity for Cloud-Based Systems
- Artificial Intelligence for Automated Journalism
- Blockchain Technology for Intellectual Property Management
- Virtual Reality for Therapy and Rehabilitation
- Natural Language Processing for Language Generation
- Machine Learning for Customer Lifetime Value Prediction
- Big Data Analytics for Predictive Maintenance in Energy Systems
- Cybersecurity for Secure Mobile Communication
- Artificial Intelligence for Emotion Recognition
- Blockchain Technology for Digital Asset Trading
- Virtual Reality for Automotive Design and Visualization
- Natural Language Processing for Semantic Web
- Machine Learning for Fraud Detection in Financial Transactions
- Big Data Analytics for Social Media Monitoring
- Cybersecurity for Cloud Storage and Sharing
- Artificial Intelligence for Personalized Education
- Blockchain Technology for Secure Online Voting Systems
- Virtual Reality for Cultural Tourism
- Natural Language Processing for Chatbot Communication
- Machine Learning for Medical Diagnosis and Treatment
- Big Data Analytics for Environmental Monitoring and Management.
- Cybersecurity for Cloud Computing Environments
- Virtual Reality for Training and Simulation
- Big Data Analytics for Sports Performance Analysis
- Cybersecurity for Internet of Things (IoT) Devices
- Artificial Intelligence for Traffic Management and Control
- Blockchain Technology for Smart Contracts
- Natural Language Processing for Document Summarization
- Machine Learning for Image and Video Recognition
- Blockchain Technology for Digital Asset Management
- Virtual Reality for Entertainment and Gaming
- Natural Language Processing for Opinion Mining in Online Reviews
- Machine Learning for Customer Relationship Management
- Big Data Analytics for Environmental Monitoring and Management
- Cybersecurity for Network Traffic Analysis and Monitoring
- Artificial Intelligence for Natural Language Generation
- Blockchain Technology for Supply Chain Transparency and Traceability
- Virtual Reality for Design and Visualization
- Natural Language Processing for Speech Recognition
- Machine Learning for Recommendation Systems
- Big Data Analytics for Customer Segmentation and Targeting
- Cybersecurity for Biometric Authentication
- Artificial Intelligence for Human-Computer Interaction
- Blockchain Technology for Decentralized Finance (DeFi)
- Virtual Reality for Tourism and Cultural Heritage
- Machine Learning for Cybersecurity Threat Detection and Prevention
- Big Data Analytics for Healthcare Cost Reduction
- Cybersecurity for Data Privacy and Protection
- Artificial Intelligence for Autonomous Vehicles
- Blockchain Technology for Cryptocurrency and Blockchain Security
- Virtual Reality for Real Estate Visualization
- Natural Language Processing for Question Answering
- Big Data Analytics for Financial Markets Prediction
- Cybersecurity for Cloud-Based Machine Learning Systems
- Artificial Intelligence for Personalized Advertising
- Blockchain Technology for Digital Identity Verification
- Virtual Reality for Cultural and Language Learning
- Natural Language Processing for Semantic Analysis
- Machine Learning for Business Forecasting
- Big Data Analytics for Social Media Marketing
- Artificial Intelligence for Content Generation
- Blockchain Technology for Smart Cities
- Virtual Reality for Historical Reconstruction
- Natural Language Processing for Knowledge Graph Construction
- Machine Learning for Speech Synthesis
- Big Data Analytics for Traffic Optimization
- Artificial Intelligence for Social Robotics
- Blockchain Technology for Healthcare Data Management
- Virtual Reality for Disaster Preparedness and Response
- Natural Language Processing for Multilingual Communication
- Machine Learning for Emotion Recognition
- Big Data Analytics for Human Resources Management
- Cybersecurity for Mobile App Security
- Artificial Intelligence for Financial Planning and Investment
- Blockchain Technology for Energy Management
- Virtual Reality for Cultural Preservation and Heritage.
- Big Data Analytics for Healthcare Management
- Cybersecurity in the Internet of Things (IoT)
- Artificial Intelligence for Predictive Maintenance
- Computational Biology for Drug Discovery
- Virtual Reality for Mental Health Treatment
- Machine Learning for Sentiment Analysis in Social Media
- Human-Computer Interaction for User Experience Design
- Cloud Computing for Disaster Recovery
- Quantum Computing for Cryptography
- Intelligent Transportation Systems for Smart Cities
- Cybersecurity for Autonomous Vehicles
- Artificial Intelligence for Fraud Detection in Financial Systems
- Social Network Analysis for Marketing Campaigns
- Cloud Computing for Video Game Streaming
- Machine Learning for Speech Recognition
- Augmented Reality for Architecture and Design
- Natural Language Processing for Customer Service Chatbots
- Machine Learning for Climate Change Prediction
- Big Data Analytics for Social Sciences
- Artificial Intelligence for Energy Management
- Virtual Reality for Tourism and Travel
- Cybersecurity for Smart Grids
- Machine Learning for Image Recognition
- Augmented Reality for Sports Training
- Natural Language Processing for Content Creation
- Cloud Computing for High-Performance Computing
- Artificial Intelligence for Personalized Medicine
- Virtual Reality for Architecture and Design
- Augmented Reality for Product Visualization
- Natural Language Processing for Language Translation
- Cybersecurity for Cloud Computing
- Artificial Intelligence for Supply Chain Optimization
- Blockchain Technology for Digital Voting Systems
- Virtual Reality for Job Training
- Augmented Reality for Retail Shopping
- Natural Language Processing for Sentiment Analysis in Customer Feedback
- Cloud Computing for Mobile Application Development
- Artificial Intelligence for Cybersecurity Threat Detection
- Blockchain Technology for Intellectual Property Protection
- Virtual Reality for Music Education
- Machine Learning for Financial Forecasting
- Augmented Reality for Medical Education
- Natural Language Processing for News Summarization
- Cybersecurity for Healthcare Data Protection
- Artificial Intelligence for Autonomous Robots
- Virtual Reality for Fitness and Health
- Machine Learning for Natural Language Understanding
- Augmented Reality for Museum Exhibits
- Natural Language Processing for Chatbot Personality Development
- Cloud Computing for Website Performance Optimization
- Artificial Intelligence for E-commerce Recommendation Systems
- Blockchain Technology for Supply Chain Traceability
- Virtual Reality for Military Training
- Augmented Reality for Advertising
- Natural Language Processing for Chatbot Conversation Management
- Cybersecurity for Cloud-Based Services
- Artificial Intelligence for Agricultural Management
- Blockchain Technology for Food Safety Assurance
- Virtual Reality for Historical Reenactments
- Machine Learning for Cybersecurity Incident Response.
- Secure Multiparty Computation
- Federated Learning
- Internet of Things Security
- Blockchain Scalability
- Quantum Computing Algorithms
- Explainable AI
- Data Privacy in the Age of Big Data
- Adversarial Machine Learning
- Deep Reinforcement Learning
- Online Learning and Streaming Algorithms
- Graph Neural Networks
- Automated Debugging and Fault Localization
- Mobile Application Development
- Software Engineering for Cloud Computing
- Cryptocurrency Security
- Edge Computing for Real-Time Applications
- Natural Language Generation
- Virtual and Augmented Reality
- Computational Biology and Bioinformatics
- Internet of Things Applications
- Robotics and Autonomous Systems
- Explainable Robotics
- 3D Printing and Additive Manufacturing
- Distributed Systems
- Parallel Computing
- Data Center Networking
- Data Mining and Knowledge Discovery
- Information Retrieval and Search Engines
- Network Security and Privacy
- Cloud Computing Security
- Data Analytics for Business Intelligence
- Neural Networks and Deep Learning
- Reinforcement Learning for Robotics
- Automated Planning and Scheduling
- Evolutionary Computation and Genetic Algorithms
- Formal Methods for Software Engineering
- Computational Complexity Theory
- Bio-inspired Computing
- Computer Vision for Object Recognition
- Automated Reasoning and Theorem Proving
- Natural Language Understanding
- Machine Learning for Healthcare
- Scalable Distributed Systems
- Sensor Networks and Internet of Things
- Smart Grids and Energy Systems
- Software Testing and Verification
- Web Application Security
- Wireless and Mobile Networks
- Computer Architecture and Hardware Design
- Digital Signal Processing
- Game Theory and Mechanism Design
- Multi-agent Systems
- Evolutionary Robotics
- Quantum Machine Learning
- Computational Social Science
- Explainable Recommender Systems.
- Artificial Intelligence and its applications
- Cloud computing and its benefits
- Cybersecurity threats and solutions
- Internet of Things and its impact on society
- Virtual and Augmented Reality and its uses
- Blockchain Technology and its potential in various industries
- Web Development and Design
- Digital Marketing and its effectiveness
- Big Data and Analytics
- Software Development Life Cycle
- Gaming Development and its growth
- Network Administration and Maintenance
- Machine Learning and its uses
- Data Warehousing and Mining
- Computer Architecture and Design
- Computer Graphics and Animation
- Quantum Computing and its potential
- Data Structures and Algorithms
- Computer Vision and Image Processing
- Robotics and its applications
- Operating Systems and its functions
- Information Theory and Coding
- Compiler Design and Optimization
- Computer Forensics and Cyber Crime Investigation
- Distributed Computing and its significance
- Artificial Neural Networks and Deep Learning
- Cloud Storage and Backup
- Programming Languages and their significance
- Computer Simulation and Modeling
- Computer Networks and its types
- Information Security and its types
- Computer-based Training and eLearning
- Medical Imaging and its uses
- Social Media Analysis and its applications
- Human Resource Information Systems
- Computer-Aided Design and Manufacturing
- Multimedia Systems and Applications
- Geographic Information Systems and its uses
- Computer-Assisted Language Learning
- Mobile Device Management and Security
- Data Compression and its types
- Knowledge Management Systems
- Text Mining and its uses
- Cyber Warfare and its consequences
- Wireless Networks and its advantages
- Computer Ethics and its importance
- Computational Linguistics and its applications
- Autonomous Systems and Robotics
- Information Visualization and its importance
- Geographic Information Retrieval and Mapping
- Business Intelligence and its benefits
- Digital Libraries and their significance
- Artificial Life and Evolutionary Computation
- Computer Music and its types
- Virtual Teams and Collaboration
- Computer Games and Learning
- Semantic Web and its applications
- Electronic Commerce and its advantages
- Multimedia Databases and their significance
- Computer Science Education and its importance
- Computer-Assisted Translation and Interpretation
- Ambient Intelligence and Smart Homes
- Autonomous Agents and Multi-Agent Systems.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

200+ Funny Research Topics

500+ Sports Research Topics

300+ American History Research Paper Topics

500+ Cyber Security Research Topics

500+ Environmental Research Topics

500+ Economics Research Topics
- Write my thesis
- Thesis writers
- Buy thesis papers
- Bachelor thesis
- Master's thesis
- Thesis editing services
- Thesis proofreading services
- Buy a thesis online
- Write my dissertation
- Dissertation proposal help
- Pay for dissertation
- Custom dissertation
- Dissertation help online
- Buy dissertation online
- Cheap dissertation
- Dissertation editing services
- Write my research paper
- Buy research paper online
- Pay for research paper
- Research paper help
- Order research paper
- Custom research paper
- Cheap research paper
- Research papers for sale
- Thesis subjects
- How It Works
100 Great Computer Science Research Topics Ideas for 2023
Being a computer student in 2023 is not easy. Besides studying a constantly evolving subject, you have to come up with great computer science research topics at some point in your academic life. If you’re reading this article, you’re among many other students that have also come to this realization.
Interesting Computer Science Topics
Awesome research topics in computer science, hot topics in computer science, topics to publish a journal on computer science.
- Controversial Topics in Computer Science
Fun AP Computer Science Topics
Exciting computer science ph.d. topics, remarkable computer science research topics for undergraduates, incredible final year computer science project topics, advanced computer science topics, unique seminars topics for computer science, exceptional computer science masters thesis topics, outstanding computer science presentation topics.
- Key Computer Science Essay Topics
Main Project Topics for Computer Science
- We Can Help You with Computer Science Topics
Whether you’re earnestly searching for a topic or stumbled onto this article by accident, there is no doubt that every student needs excellent computer science-related topics for their paper. A good topic will not only give your essay or research a good direction but will also make it easy to come up with supporting points. Your topic should show all your strengths as well.
Fortunately, this article is for every student that finds it hard to generate a suitable computer science topic. The following 100+ topics will help give you some inspiration when creating your topics. Let’s get into it.
One of the best ways of making your research paper interesting is by coming up with relevant topics in computer science . Here are some topics that will make your paper immersive:
- Evolution of virtual reality
- What is green cloud computing
- Ways of creating a Hopefield neural network in C++
- Developments in graphic systems in computers
- The five principal fields in robotics
- Developments and applications of nanotechnology
- Differences between computer science and applied computing
Your next research topic in computer science shouldn’t be tough to find once you’ve read this section. If you’re looking for simple final year project topics in computer science, you can find some below.
- Applications of the blockchain technology in the banking industry
- Computational thinking and how it influences science
- Ways of terminating phishing
- Uses of artificial intelligence in cyber security
- Define the concepts of a smart city
- Applications of the Internet of Things
- Discuss the applications of the face detection application
Whenever a topic is described as “hot,” it means that it is a trendy topic in computer science. If computer science project topics for your final years are what you’re looking for, have a look at some below:
- Applications of the Metaverse in the world today
- Discuss the challenges of machine learning
- Advantages of artificial intelligence
- Applications of nanotechnology in the paints industry
- What is quantum computing?
- Discuss the languages of parallel computing
- What are the applications of computer-assisted studies?
Perhaps you’d like to write a paper that will get published in a journal. If you’re searching for the best project topics for computer science students that will stand out in a journal, check below:
- Developments in human-computer interaction
- Applications of computer science in medicine
- Developments in artificial intelligence in image processing
- Discuss cryptography and its applications
- Discuss methods of ransomware prevention
- Applications of Big Data in the banking industry
- Challenges of cloud storage services in 2023
Controversial Topics in Computer Science
Some of the best computer science final year project topics are those that elicit debates or require you to take a stand. You can find such topics listed below for your inspiration:
- Can robots be too intelligent?
- Should the dark web be shut down?
- Should your data be sold to corporations?
- Will robots completely replace the human workforce one day?
- How safe is the Metaverse for children?
- Will artificial intelligence replace actors in Hollywood?
- Are social media platforms safe anymore?
Are you a computer science student looking for AP topics? You’re in luck because the following final year project topics for computer science are suitable for you.
- Standard browser core with CSS support
- Applications of the Gaussian method in C++ development in integrating functions
- Vital conditions of reducing risk through the Newton method
- How to reinforce machine learning algorithms.
- How do artificial neural networks function?
- Discuss the advancements in computer languages in machine learning
- Use of artificial intelligence in automated cars
When studying to get your doctorate in computer science, you need clear and relevant topics that generate the reader’s interest. Here are some Ph.D. topics in computer science you might consider:
- Developments in information technology
- Is machine learning detrimental to the human workforce?
- How to write an algorithm for deep learning
- What is the future of 5G in wireless networks
- Statistical data in Maths modules in Python
- Data retention automation from a website using API
- Application of modern programming languages
Looking for computer science topics for research is not easy for an undergraduate. Fortunately, these computer science project topics should make your research paper easy:
- Ways of using artificial intelligence in real estate
- Discuss reinforcement learning and its applications
- Uses of Big Data in science and medicine
- How to sort algorithms using Haskell
- How to create 3D configurations for a website
- Using inverse interpolation to solve non-linear equations
- Explain the similarities between the Internet of Things and artificial intelligence
Your dissertation paper is one of the most crucial papers you’ll ever do in your final year. That’s why selecting the best ethics in computer science topics is a crucial part of your paper. Here are some project topics for the computer science final year.
- How to incorporate numerical methods in programming
- Applications of blockchain technology in cloud storage
- How to come up with an automated attendance system
- Using dynamic libraries for site development
- How to create cubic splines
- Applications of artificial intelligence in the stock market
- Uses of quantum computing in financial modeling
Your instructor may want you to challenge yourself with an advanced science project. Thus, you may require computer science topics to learn and research. Here are some that may inspire you:
- Discuss the best cryptographic protocols
- Advancement of artificial intelligence used in smartphones
- Briefly discuss the types of security software available
- Application of liquid robots in 2023
- How to use quantum computers to solve decoherence problem
- macOS vs. Windows; discuss their similarities and differences
- Explain the steps taken in a cyber security audit
When searching for computer science topics for a seminar, make sure they are based on current research or events. Below are some of the latest research topics in computer science:
- How to reduce cyber-attacks in 2023
- Steps followed in creating a network
- Discuss the uses of data science
- Discuss ways in which social robots improve human interactions
- Differentiate between supervised and unsupervised machine learning
- Applications of robotics in space exploration
- The contrast between cyber-physical and sensor network systems
Are you looking for computer science thesis topics for your upcoming projects? The topics below are meant to help you write your best paper yet:
- Applications of computer science in sports
- Uses of computer technology in the electoral process
- Using Fibonacci to solve the functions maximum and their implementations
- Discuss the advantages of using open-source software
- Expound on the advancement of computer graphics
- Briefly discuss the uses of mesh generation in computational domains
- How much data is generated from the internet of things?
A computer science presentation requires a topic relevant to current events. Whether your paper is an assignment or a dissertation, you can find your final year computer science project topics below:
- Uses of adaptive learning in the financial industry
- Applications of transitive closure on graph
- Using RAD technology in developing software
- Discuss how to create maximum flow in the network
- How to design and implement functional mapping
- Using artificial intelligence in courier tracking and deliveries
- How to make an e-authentication system
Key Computer Science Essay Topics
You may be pressed for time and require computer science master thesis topics that are easy. Below are some topics that fit this description:
- What are the uses of cloud computing in 2023
- Discuss the server-side web technologies
- Compare and contrast android and iOS
- How to come up with a face detection algorithm
- What is the future of NFTs
- How to create an artificial intelligence shopping system
- How to make a software piracy prevention algorithm
One major mistake students make when writing their papers is selecting topics unrelated to the study at hand. This, however, will not be an issue if you get topics related to computer science, such as the ones below:
- Using blockchain to create a supply chain management system
- How to protect a web app from malicious attacks
- Uses of distributed information processing systems
- Advancement of crowd communication software since COVID-19
- Uses of artificial intelligence in online casinos
- Discuss the pillars of math computations
- Discuss the ethical concerns arising from data mining
We Can Help You with Computer Science Topics, Essays, Thesis, and Research Papers
We hope that this list of computer science topics helps you out of your sticky situation. We do offer other topics in different subjects. Additionally, we also offer professional writing services tailor-made for you.
We understand what students go through when searching the internet for computer science research paper topics, and we know that many students don’t know how to write a research paper to perfection. However, you shouldn’t have to go through all this when we’re here to help.
Don’t waste any more time; get in touch with us today and get your paper done excellently.
Leave a Reply Cancel reply
- IEEE CS Standards
- Career Center
- Subscribe to Newsletter
- IEEE Standards
- For Industry Professionals
- For Students
- Launch a New Career
- Membership FAQ
- Membership FAQs
- Membership Grades
- Special Circumstances
- Discounts & Payments
- Distinguished Contributor Recognition
- Grant Programs
- Find a Local Chapter
- Find a Distinguished Visitor
- Find a Speaker on Early Career Topics
- Technical Communities
- Collabratec (Discussion Forum)
- Start a Chapter
- My Subscriptions
- My Referrals
- Computer Magazine
- ComputingEdge Magazine
- Let us help make your event a success. EXPLORE PLANNING SERVICES
- Events Calendar
- Calls for Papers
- Conference Proceedings
- Conference Highlights
- Top 2024 Conferences
- Conference Sponsorship Options
- Conference Planning Services
- Conference Organizer Resources
- Virtual Conference Guide
- Get a Quote
- CPS Dashboard
- CPS Author FAQ
- CPS Organizer FAQ
- Find the latest in advanced computing research. VISIT THE DIGITAL LIBRARY
- Open Access
- Tech News Blog
- Author Guidelines
- Reviewer Information
- Guest Editor Information
- Editor Information
- Editor-in-Chief Information
- Volunteer Opportunities
- Video Library
- Member Benefits
- Institutional Library Subscriptions
- Advertising and Sponsorship
- Code of Ethics
- Educational Webinars
- Online Education
- Certifications
- Industry Webinars & Whitepapers
- Research Reports
- Bodies of Knowledge
- CS for Industry Professionals
- Resource Library
- Newsletters
- Women in Computing
- Digital Library Access
- Organize a Conference
- Run a Publication
- Become a Distinguished Speaker
- Participate in Standards Activities
- Peer Review Content
- Author Resources
- Publish Open Access
- Society Leadership
- Boards & Committees
- Local Chapters
- Governance Resources
- Conference Publishing Services
- Chapter Resources
- About the Board of Governors
- Board of Governors Members
- Diversity & Inclusion
- Open Volunteer Opportunities
- Award Recipients
- Student Scholarships & Awards
- Nominate an Election Candidate
- Nominate a Colleague
- Corporate Partnerships
- Conference Sponsorships & Exhibits
- Advertising
- Recruitment
- Publications
- Education & Career
CiSE Case Studies in Translational Computer Science
Call for department articles.
CiSE ‘s newest department explores how findings in fundamental research in computer, computational, and data science translate to technologies, solutions, or practice for the benefit of science, engineering, and society. Specifically, each department article will highlight impactful translational research examples in which research has successfully moved from the laboratory to the field and into the community. The goal is to improve understanding of underlying approaches, explore challenges and lessons learned, with the overarching aim to formulate translational research processes that are broadly applicable.
Computing and data are increasingly essential to the research process across all areas of science and engineering and are key catalysts for impactful advances and breakthroughs. Consequently, translating fundamental advances in computer, computational, and data science help to ensure that these emerging insights, discoveries, and innovations are realized.
Translational Research in Computer and Computational Sciences [1][2] refers the bridging of foundational and use-inspired (applied) research with the delivery and deployment of its outcomes to the target community, and supports bi-directional benefit in which delivery and deployment process informs the research.
Call for Department Contributions: We seek short papers that align with our recommended structure and detail the following aspects of the described research:
- Overview: A description of the research, what problem does it address, who is the target user community, what are the key innovations and attributes, etc.
- Translation Process: What was the process used to move the research from the laboratory to the application? How were outcomes fed back into the research, and over what time period did this occur? How was the translation supported?
- I mpact: What is the impact of the translated research, both on the CCDS research as well as the target domain(s)?
- Lessons Learned: What are the lessons learned in terms of both the research and the translation process? What were the challenges faced?
- Conclusion: Based on your experience, do you have suggestions for processes or support structures that would have made the translation more effective?
CiSE Department articles are typically up to 3,000 words (including abstract, references, author biographies, and tables/figures [which count as 250 words each]), and are only reviewed by the department editors.
To pitch or submit a department article, please contact the editors directly by emailing:
- Manish Parashar
- David Abramson
Additional information for authors can be found here.
- D. Abramson and M. Parashar, “Translational Research in Computer Science,” Computer , vol. 52, no. 9, pp. 16-23, Sept. 2019, doi: 10.1109/MC.2019.2925650.
- D. Abramson, M. Parashar, and P. Arzberger. “Translation computer science – Overview of the special issue,” J. Computational Sci. , 2020, ISSN 1877-7503, https://www.sciencedirect.com/journal/journal-of-computational-science/special-issue/10P6T48JS7B.
Recommended by IEEE Computer Society

How Pump Storage Hydropower Can Supercharge the Energy Transition

7 Tips for Implementing an Effective Cyber GRC Program

A Conversation with Katerina Michou, Student Scholarship Recipient

Continuous Deployment: Trends and Predictions for 2024

How to Convince Your Boss to Send You to a Conference

The Importance Of MLOps in AI/ML

IEEE Computer Society Announces Recipients of 2024 Computer Pioneer Award

IEEE Computer Society Announces Call for Nominations for AI’s 10 to Watch Award
Put a stop to deadline pressure, and have your homework done by an expert.
201 Computer Science Topics (Updated for 2023)

If you are reading this, you are surely in need of some excellent computer science topics. The good news is that you have arrived at the right place. We have 201 brand new computer science topics that should work great in 2023. The even better news is that each and every one of these research topics in computer science is 100% free to use. You can reword our topics or use them as they are; it’s up to you.
Wondering why you need computer science research paper topics? The truth is that by using the best research paper topics in computer science, you get the chance to win some bonus points from your professor.
After all, who wouldn’t want to read papers on interesting topics in computer science or on some awesome computer science ethics topics? Your professor is bored of reading essays on the same old topics over and over again. Bring something fresh to the table and you’ll immediately stand out from your classmates. If the scope of your work allows, you can also check our technology topics . Without further ado, here is our list of research topics in computer science.
Best Computer Science Research Topics
Writing a research paper can be tough if you don’t pick the right topic. Here are some of the best computer science research topics you can find in 2023:
- How important is machine learning?
- The latest advancements in quantum computing
- The next level of the Internet
- Virtualization technologies
- Real-life applications of bioinformatics
- Introducing computer science in high school
- Define deep learning
- Describe MIMO OFDM wireless communication
Easy Topics in Computer Science
If you don’t want to spend too much time working on your paper, we suggest you pick one of our easy topics in computer science:
- What is a computer virus?
- Explain the TCP/IP protocol
- Explain how the microprocessor works
- The role of Random Access Memory
- Protecting endangered species using computers
- Describe a virtual reality device
- How does machine learning work?
- Explain the term “Neural Network”
Computer Security Topics
There are literally thousands of topics to discuss when it comes to computer security. We managed to narrow down the list of computer security topics to only the most interesting of them:
- Top 3 most dangerous viruses
- What is a Trojan Horse?
- The role of antivirus/firewall solutions
- In-depth analysis of ransomware
- Everything about the Mydoom virus
- Virus propagation methods
- The most secure passwords
- In-depth analysis of mobile protection
Hot Topics in Computer Science
Are you looking for the newest and most interesting topics? If you are, you should check out our hot topics in computer science:
- What is the Internet of Things?
- Semantic Web
- Bioinformatics
- Latest image processing algorithms
- Machine Learning
- Latest in Cloud Computing
- Artificial Intelligence breakthroughs
- Quantum Computing
Computer Science Research Topics for Undergraduates
Undergrads should avoid wasting time searching for topics and simply pick one of these free computer science research topics for undergraduates:
- Data Warehousing for the financial sector
- IoT applications in healthcare
- Data Warehousing in the retail services sector
- IoT applications in manufacturing
- Big data applications/algorithms
- SaaS vs PaaS
- Mobile ad hoc networks for vehicles
- Data mining: The Genetic algorithm
AP Computer Science Topics
Mastering the AP Computer Science A programming class is not easy. Fortunately, we have some AP computer science topics that can help you write a great paper in no time:
- Discuss computer-assisted education
- Novel emerging technologies in computer science
- Open-source vs. proprietary software
- Natural language processing real life applications
- Evaluating 3D models effectively
- Internet of Things applications in the medical field
- Discuss data security in a pharmacy
- What is mesh generation and what are its applications?
Computer Ethics Topics
Yes, there is such a thing as computer ethics. In fact, the subject is pretty vast, so you have plenty of computer ethics topics to choose from:
- Ethic problems with data mining
- Machine learning issues
- Internet of Things controversies
- AI security concerns
- Image processing and privacy concerns
- Quantum computing ethic problems
- Controversies surrounding robots
- Internet censorship
Computer Science and Robotics Topics
Computer science can be tightly linked to advances in robotics, so why don’t you write about one of our computer science and robotics topics:
- Social robots
- Machine learning in robotics
- Robot vision: AI applications
- Autonomous cars
- Are computers taking our jobs?
- Robots in the healthcare sector
- AI in the Mars Rovers
- Programming an industrial robot
Best Project Topics for Computer Science Student
If you are looking for the best project topics for computer science student, you are in luck. We have exactly what you need:
- Write a program in Java
- Create a Website in PHP and MySQL
- Write an Android app
- Explore Microsoft Mobile app ideas
- Graphical Interfaces in Java
- Java Server Faces applications
- Create a relational database
- Create a Web app
Controversial Topics in Computer Science
There are many controversial topics in computer science, but we managed to pick the best ones. Use any of them for free:
- Robots are stealing our jobs
- Privacy concerns on the Internet
- How safe are social networking platforms?
- Policing the Internet
- The role of the dark net
- Corporations using personal data
- Targeted ads
- Tracking cookies
Evolution of Computers Topics
If you are interested in writing about how things evolved since the first computers appeared on the market, we have some interesting evolution of computers topics for you:
- Describe the Fiber Distributed Data Interface (FDDI)
- What is a firewall and how does it work?
- What is an ExpressCard?
- How does an adapter card work?
- From the first computer to quantum computing
- The history of the Cloud
- The evolution of Denial of Service attacks
- Quantum computers
Computer Architecture Research Topics
Interested in discussing the functionality, organization and implementation of computer systems? You need our computer architecture research topics:
- What are reduced instruction set computers?
- Describe synchronous design
- Parallel hardware systems
- The Sun SPARK architecture
- Analyze data-driven nets
- Discuss functional programming methods
- Discuss micropipelines
- The Von Neumann architecture
Computer Science Thesis Topics
If you need to write a thesis in computer science, our writers have some excellent computer science thesis topics for you. Choose one:
- Quantum computing advancements
- The role of big data in the banking sector
- Artificial intelligence and computer security
- An in-depth analysis of an antivirus tool
- Image processing algorithms
- Discuss model-based reflex agents (AI)
- Discuss fuzzy logic systems
- Data mining in governmental agencies
Internet of Things Ideas
You’ve probably heard about the IoT, but didn’t really bother to investigate. Check out these Internet of Things ideas and impress your professor:
- The concept of a smart home
- What is the IoT?
- Internet of Things applications
- Internet of Things in manufacturing
- Product flow monitoring
- IoT in Quality Control
- The Ring doorbell camera
- Video streaming with IoT
Quantum Computing Ideas
Truth be told, quantum computing is one of the hottest ideas and works great for 2023. Pick one of our quantum computing ideas for free:
- Discuss a quantum algorithm
- What is quantum computing?
- Discuss adiabatic optimization
- Discuss quantum annealing
- Cryptography in quantum computing
- 5 requirements for quantum computing
- Quantum computing and financial modeling
- Implications for Artificial Intelligence
Computer Science Project Topics
So, you are interested in starting a computer science project. Pick one of these computer science project topics for free right now:
- Securing a workstation
- Face detection application
- An Android battery safer system
- Create your very own search engine
- Write a group chat app in Java
- Selenium browser automation applications
- Mitigate a DDoS attack
- Load balancing applications
Computer Engineering Research Topics
Researching good computer engineering topics can take hours. Why waste your time when we have some computer engineering research topics right here:
- Clustering in data mining
- The advantages of data mining
- The disadvantages of using big data
- Artificial intelligence in security applications
- Strong AI vs. Weak AI
- Pattern measurement in image processing
- Computer-aided image restoration methods
- DNA/RNA simulations using bioinformatics
Interesting Computer Science Topics
Want to make sure your professor notices your paper? No problem! Simply pick one of these interesting computer science topics:
- Green cloud computing
- Spectral clustering in data mining
- Fraud detection using big data
- AI uses of computer vision
- CNN Advanced Machine Learning
- Augmented reality vs. virtual reality
Computer Networks Topics
Writing about networks and networking never gets old. We have some highly interesting computer networks topics just for you:
- Create a network (practical project)
- Network security best practices
- The IPv6 protocol
- The TCP/IP protocol
- How does the Internet work?
- Banking computer networks
Current Topics in Computer Science
You are probably interested in writing about the newest and hottest topics, so here are some current topics in computer science:
- Define data science
- The 5G network
- What are swarm robots?
- NoSQL databases
- Programs creating programs
- Using computer science in biology
Cool Computer Security Research Topics
Do you want to impress your professor and secure a top grade? Pick one of our cool computer security research topics:
- Humans: the weak link in network security
- Analyzing the top 3 online scams
- Discuss endpoint security best practices
- IoT security
- What is a cyber security audit?
- Best algorithm for data encryption
- Ransomware and ways to prevent it
- Discuss unified user profiles
Computer Science Presentation Topics
Our team of ENL writers managed to put together an excellent list of computer science presentation topics for you:
- Importance of biometrics in computer security
- Windows vs. Linux vs. MacOS security
- DDoS attacks on vehicular ad hoc networks
- Describe a software-defined network
- Using artificial neural networks effectively
- Model-free versus model-based reinforcement learning
- The future of wireless: the 5G network
PhD Research Topics in Computer Science
Are you looking to start on your PhD but don’t know which topic to choose? We have some ideas of PhD research topics in computer science you might like:
- Database architecture: literature review
- Develop a novel search algorithm
- Creating a new network protocol
- Advanced computer vision in robots
- Write a deep learning algorithm
- Solving the decoherence problem with quantum computers
Computer Forensics Research Paper Topics
Ever wonder how law enforcement manages to catch cyber criminals? We have some of the best computer forensics research paper topics right here:
- Recovering data for computer forensics
- Identifying users on the darknet
- The Fourth Amendment and computer forensics
- Discuss digital steganography
- What is criminal profiling?
- Cyber surveillance
Artificial Intelligence Topics
AI is what everyone’s talking about right now, so it’s the perfect topic for 2023. Fortunately, we have some very nice artificial intelligence topics:
- What is reinforcement learning?
- Discuss recommender systems
- The 4 types of AI
- Is AI dangerous?
- Predicting housing price using AI
- AI in the medical profession
Interesting Cyber Security Ideas
Are you interested in cyber security? It’s an awesome field, we have to admit. Pick one of these interesting cyber security ideas and start writing:
- Best anti-virus system today
- Discuss secure passwords
- What is a brute force attack?
- The human element in cyber security
- Security awareness
- Working remotely security solutions
Trends in Computer Science Topics
If you like to analyze trends, computer science is one of the best subjects to try your hand on. Take a look at our trends in computer science topics:
- The appearance of Mini-VGA connectors
- Discuss multiprocessing in 2023
- How was the Small-Scale Experimental Machine built?
- Computers and education in 2023
- Computers and medicine in 2023
- The evolution of computing power
- What is a neural computer?
- The Internet of Things in 2023
Need More Computer Topics?
Didn’t find the computer topics you were looking for? No problem! In addition to our computer architecture topics, computer science controversial topics and PhD research topics in computer science, we can help students with many others. Professionals providing computer science homework help can quickly put together a list of unique computer related topics for you. All you have to do is ask.
If you need more computer science topics for research or if you just need some simple computer science essay topics, don’t hesitate to contact us. We can send you a list of original computer research topics in no time. Each one of our topics can win you a top grade.
So, what are you waiting for? Get your list of computer science research papers topics right now. Get in touch with us!

Get on top of your homework.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
We use cookies to enhance our website for you. Proceed if you agree to this policy or learn more about it.
- Essay Database >
- Essays Samples >
- Essay Types >
- Case Study Example
Computer Science Case Studies Samples For Students
4 samples of this type
WowEssays.com paper writer service proudly presents to you a free directory of Computer Science Case Studies aimed to help struggling students tackle their writing challenges. In a practical sense, each Computer Science Case Study sample presented here may be a guide that walks you through the crucial stages of the writing procedure and showcases how to develop an academic work that hits the mark. Besides, if you require more visionary help, these examples could give you a nudge toward an original Computer Science Case Study topic or inspire a novice approach to a threadbare issue.
In case this is not enough to quench the thirst for effective writing help, you can request customized assistance in the form of a model Case Study on Computer Science crafted by a pro writer from scratch and tailored to your particular requirements. Be it a simple 2-page paper or an in-depth, extended piece, our writers specialized in Computer Science and related topics will deliver it within the stated period. Buy cheap essays or research papers now!
Example Of Engineering Case Study
Reform movement: demolishing barriers between computer science and computer engineering in purdue university, example of case study on structure of computer systems, structure of computer systems, free google case study example, the mission and value of google company.
The corporate culture and mission of Google Company reflects a philosophy of creating money without doing wickedness or evil. Moreover, work must be challenging and fun. At Google, these beliefs dictate life. The Google’s Inc certified mission statement is arranging or organizing information of the world and making it globally useful and accessible (Corporate Information 3). It has a value of no retaliation. Google Company forbids retaliation against any employee within the firm who participates in or reports an investigation enquiry of a likely violation of their code (Google’s Corporate Information 10).
History of the Google Company
Don't waste your time searching for a sample.
Get your case study done by professional writers!
Just from $10/page
Case Study On Cobol And Legacy Systems
Password recovery email has been sent to [email protected]
Use your new password to log in
You are not register!
By clicking Register, you agree to our Terms of Service and that you have read our Privacy Policy .
Now you can download documents directly to your device!
Check your email! An email with your password has already been sent to you! Now you can download documents directly to your device.
or Use the QR code to Save this Paper to Your Phone
The sample is NOT original!
Short on a deadline?
Don't waste time. Get help with 11% off using code - GETWOWED
No, thanks! I'm fine with missing my deadline
For enquiries call:
+1-469-442-0620

- Programming
Latest Computer Science Research Topics for 2024
Home Blog Programming Latest Computer Science Research Topics for 2024
Everybody sees a dream—aspiring to become a doctor, astronaut, or anything that fits your imagination. If you were someone who had a keen interest in looking for answers and knowing the “why” behind things, you might be a good fit for research. Further, if this interest revolved around computers and tech, you would be an excellent computer researcher!
As a tech enthusiast, you must know how technology is making our life easy and comfortable. With a single click, Google can get you answers to your silliest query or let you know the best restaurants around you. Do you know what generates that answer? Want to learn about the science going on behind these gadgets and the internet?
For this, you will have to do a bit of research. Here we will learn about top computer science thesis topics and computer science thesis ideas.
Why is Research in Computer Science Important?
Computers and technology are becoming an integral part of our lives. We are dependent on them for most of our work. With the changing lifestyle and needs of the people, continuous research in this sector is required to ease human work. However, you need to be a certified researcher to contribute to the field of computers. You can check out Advance Computer Programming certification to learn and advance in the versatile language and get hands-on experience with all the topics of C# application development.
1. Innovation in Technology
Research in computer science contributes to technological advancement and innovations. We end up discovering new things and introducing them to the world. Through research, scientists and engineers can create new hardware, software, and algorithms that improve the functionality, performance, and usability of computers and other digital devices.
2. Problem-Solving Capabilities
From disease outbreaks to climate change, solving complex problems requires the use of advanced computer models and algorithms. Computer science research enables scholars to create methods and tools that can help in resolving these challenging issues in a blink of an eye.
3. Enhancing Human Life
Computer science research has the potential to significantly enhance human life in a variety of ways. For instance, researchers can produce educational software that enhances student learning or new healthcare technology that improves clinical results. If you wish to do Ph.D., these can become interesting computer science research topics for a PhD.
4. Security Assurance
As more sensitive data is being transmitted and kept online, security is our main concern. Computer science research is crucial for creating new security systems and tactics that defend against online threats.
Top Computer Science Research Topics
Before starting with the research, knowing the trendy research paper ideas for computer science exploration is important. It is not so easy to get your hands on the best research topics for computer science; spend some time and read about the following mind-boggling ideas before selecting one.
1. Integrated Blockchain and Edge Computing Systems: A Survey, Some Research Issues, and Challenges
Welcome to the era of seamless connectivity and unparalleled efficiency! Blockchain and edge computing are two cutting-edge technologies that have the potential to revolutionize numerous sectors. Blockchain is a distributed ledger technology that is decentralized and offers a safe and transparent method of storing and transferring data.
As a young researcher, you can pave the way for a more secure, efficient, and scalable architecture that integrates blockchain and edge computing systems. So, let's roll up our sleeves and get ready to push the boundaries of technology with this exciting innovation!
Blockchain helps to reduce latency and boost speed. Edge computing, on the other hand, entails processing data close to the generation source, such as sensors and IoT devices. Integrating edge computing with blockchain technologies can help to achieve safer, more effective, and scalable architecture.
Moreover, this research title for computer science might open doors of opportunities for you in the financial sector.
2. A Survey on Edge Computing Systems and Tools
With the rise in population, the data is multiplying by manifolds each day. It's high time we find efficient technology to store it. However, more research is required for the same.
Say hello to the future of computing with edge computing! The edge computing system can store vast amounts of data to retrieve in the future. It also provides fast access to information in need. It maintains computing resources from the cloud and data centers while processing.
Edge computing systems bring processing power closer to the data source, resulting in faster and more efficient computing. But what tools are available to help us harness the power of edge computing?
As a part of this research, you will look at the newest edge computing tools and technologies to see how they can improve your computing experience. Here are some of the tools you might get familiar with upon completion of this research:
- Apache NiFi: A framework for data processing that enables users to gather, transform, and transfer data from edge devices to cloud computing infrastructure.
- Microsoft Azure IoT Edge: A platform in the cloud that enables the creation and deployment of cutting-edge intelligent applications.
- OpenFog Consortium: An organization that supports the advancement of fog computing technologies and architectures is the OpenFog Consortium.
3. Machine Learning: Algorithms, Real-world Applications, and Research Directions
Machine learning is the superset of Artificial Intelligence; a ground-breaking technology used to train machines to mimic human action and work. ML is used in everything from virtual assistants to self-driving cars and is revolutionizing the way we interact with computers. But what is machine learning exactly, and what are some of its practical uses and future research directions?
To find answers to such questions, it can be a wonderful choice to pick from the pool of various computer science dissertation ideas.
You will discover how computers learn several actions without explicit programming and see how they perform beyond their current capabilities. However, to understand better, having some basic programming knowledge always helps. KnowledgeHut’s Programming course for beginners will help you learn the most in-demand programming languages and technologies with hands-on projects.
During the research, you will work on and study
- Algorithm: Machine learning includes many algorithms, from decision trees to neural networks.
- Applications in the Real-world: You can see the usage of ML in many places. It can early detect and diagnose diseases like cancer. It can detect fraud when you are making payments. You can also use it for personalized advertising.
- Research Trend: The most recent developments in machine learning research, include explainable AI, reinforcement learning, and federated learning.
While a single research paper is not enough to bring the light on an entire domain as vast as machine learning; it can help you witness how applicable it is in numerous fields, like engineering, data science & analysis, business intelligence, and many more.
Whether you are a data scientist with years of experience or a curious tech enthusiast, machine learning is an intriguing and vital field that's influencing the direction of technology. So why not dig deeper?
4. Evolutionary Algorithms and their Applications to Engineering Problems
Imagine a system that can solve most of your complex queries. Are you interested to know how these systems work? It is because of some algorithms. But what are they, and how do they work? Evolutionary algorithms use genetic operators like mutation and crossover to build new generations of solutions rather than starting from scratch.
This research topic can be a choice of interest for someone who wants to learn more about algorithms and their vitality in engineering.
Evolutionary algorithms are transforming the way we approach engineering challenges by allowing us to explore enormous solution areas and optimize complex systems.
The possibilities are infinite as long as this technology is developed further. Get ready to explore the fascinating world of evolutionary algorithms and their applications in addressing engineering issues.
5. The Role of Big Data Analytics in the Industrial Internet of Things
Datasets can have answers to most of your questions. With good research and approach, analyzing this data can bring magical results. Welcome to the world of data-driven insights! Big Data Analytics is the transformative process of extracting valuable knowledge and patterns from vast and complex datasets, boosting innovation and informed decision-making.
This field allows you to transform the enormous amounts of data produced by IoT devices into insightful knowledge that has the potential to change how large-scale industries work. It's like having a crystal ball that can foretell.
Big data analytics is being utilized to address some of the most critical issues, from supply chain optimization to predictive maintenance. Using it, you can find patterns, spot abnormalities, and make data-driven decisions that increase effectiveness and lower costs for several industrial operations by analyzing data from sensors and other IoT devices.
The area is so vast that you'll need proper research to use and interpret all this information. Choose this as your computer research topic to discover big data analytics' most compelling applications and benefits. You will see that a significant portion of industrial IoT technology demands the study of interconnected systems, and there's nothing more suitable than extensive data analysis.
6. An Efficient Lightweight Integrated Blockchain (ELIB) Model for IoT Security and Privacy
Are you concerned about the security and privacy of your Internet of Things (IoT) devices? As more and more devices become connected, it is more important than ever to protect the security and privacy of data. If you are interested in cyber security and want to find new ways of strengthening it, this is the field for you.
ELIB is a cutting-edge solution that offers private and secure communication between IoT devices by fusing the strength of blockchain with lightweight cryptography. This architecture stores encrypted data on a distributed ledger so only parties with permission can access it.
But why is ELIB so practical and portable? ELIB uses lightweight cryptography to provide quick and effective communication between devices, unlike conventional blockchain models that need complicated and resource-intensive computations.
Due to its increasing vitality, it is gaining popularity as a research topic as someone aware that this framework works and helps reinstate data security is highly demanded in financial and banking.
7. Natural Language Processing Techniques to Reveal Human-Computer Interaction for Development Research Topics
Welcome to the world where machines decode the beauty of the human language. With natural language processing (NLP) techniques, we can analyze the interactions between humans and computers to reveal valuable insights for development research topics. It is also one of the most crucial PhD topics in computer science as NLP-based applications are gaining more and more traction.
Etymologically, natural language processing (NLP) is a potential technique that enables us to examine and comprehend natural language data, such as discussions between people and machines. Insights on user behaviour, preferences, and pain areas can be gleaned from these encounters utilizing NLP approaches.
But which specific areas should we leverage on using NLP methods? This is precisely what you’ll discover while doing this computer science research.
Gear up to learn more about the fascinating field of NLP and how it can change how we design and interact with technology, whether you are a UX designer, a data scientist, or just a curious tech lover and linguist.
8. All One Needs to Know About Fog Computing and Related Edge Computing Paradigms: A Complete Survey
If you are an IoT expert or a keen lover of the Internet of Things, you should leap and move forward to discovering Fog Computing. With the rise of connected devices and the Internet of Things (IoT), traditional cloud computing models are no longer enough. That's where fog computing and related edge computing paradigms come in.
Fog computing is a distributed approach that brings processing and data storage closer to the devices that generate and consume data by extending cloud computing to the network's edge.
As computing technologies are significantly used today, the area has become a hub for researchers to delve deeper into the underlying concepts and devise more and more fog computing frameworks. You can also contribute to and master this architecture by opting for this stand-out topic for your research.
Tips and Tricks to Write Computer Research Topics
Before starting to explore these hot research topics in computer science you may have to know about some tips and tricks that can easily help you.
- Know your interest.
- Choose the topic wisely.
- Make proper research about the demand of the topic.
- Get proper references.
- Discuss with experts.
By following these tips and tricks, you can write a compelling and impactful computer research topic that contributes to the field's advancement and addresses important research gaps.
From machine learning and artificial intelligence to blockchain, edge computing, and big data analytics, numerous trending computer research topics exist to explore.
One of the most important trends is using cutting-edge technology to address current issues. For instance, new IIoT security and privacy opportunities are emerging by integrating blockchain and edge computing. Similarly, the application of natural language processing methods is assisting in revealing human-computer interaction and guiding the creation of new technologies.
Another trend is the growing emphasis on sustainability and moral considerations in technological development. Researchers are looking into how computer science might help in innovation.
With the latest developments and leveraging cutting-edge tools and techniques, researchers can make meaningful contributions to the field and help shape the future of technology. Going for Full-stack Developer online training will help you master the latest tools and technologies.
Frequently Asked Questions (FAQs)
Research in computer science is mainly focused on different niches. It can be theoretical or technical as well. It completely depends upon the candidate and his focused area. They may do research for inventing new algorithms or many more to get advanced responses in that field.
Yes, moreover it would be a very good opportunity for the candidate. Because computer science students may have a piece of knowledge about the topic previously. They may find Easy thesis topics for computer science to fulfill their research through KnowledgeHut.
There are several scopes available for computer science. A candidate can choose different subjects such as AI, database management, software design, graphics, and many more.

Ramulu Enugurthi
Ramulu Enugurthi, a distinguished computer science expert with an M.Tech from IIT Madras, brings over 15 years of software development excellence. Their versatile career spans gaming, fintech, e-commerce, fashion commerce, mobility, and edtech, showcasing adaptability in multifaceted domains. Proficient in building distributed and microservices architectures, Ramulu is renowned for tackling modern tech challenges innovatively. Beyond technical prowess, he is a mentor, sharing invaluable insights with the next generation of developers. Ramulu's journey of growth, innovation, and unwavering commitment to excellence continues to inspire aspiring technologists.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Programming Batches & Dates
12 Interesting Computer Science Project Ideas & Topics For Beginners [Latest 2024]
![best case study topics on computer science 12 Interesting Computer Science Project Ideas & Topics For Beginners [Latest 2024]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F09%2F909-Banner.png&w=1920&q=75)
In this article, you will learn 12 Interesting Computer Science Project Ideas & Topics For Beginners (2024).
- Face detection
- Online auction system
- Evaluation of academic performance
- e-Authentication system
- Cursor movement on object motion
- Crime rate prediction
- Android battery saver system
- Symbol recognition
- Public news droid
- Search engine
- Online eBook maker
- Mobile wallet with merchant payment
Read the full article to know more.
Computer Science Project Ideas
Computer Science skills are a highly sought-after skillset in IT/ITeS and STEM-related job roles. Some of the most coveted Computer Science skills in the modern industry include coding, computation, data processing, network information security, web architecture, algorithm design, storage systems & management, and mobile development. Learning these skills opens up new and exciting employment opportunities in the present and future workforce. So, if you are a computer science beginner, the best thing you can do is work on some real-time computer science project ideas . Relevant projects not only improve your practical knowledge but also improves your resume. To gain more weight, consider our free courses developed to increase your skills in a short duration.
Check Out upGrad’s Full Stack Development Bootcamp

We, here at upGrad, believe in a practical approach as theoretical knowledge alone won’t be of help in a real-time work environment. In this article, we will be exploring some interesting computer science project ideas which beginners can work on to put their Python knowledge to the test. In this article, you will find top computer science project ideas for beginners and mini-project topics for CSE 3rd year to get hands-on experience.
But first, let’s address the more pertinent question that must be lurking in your mind: why build computer science projects?
When it comes to careers in software development, it is a must for aspiring developers to work on their own projects. Developing real-world projects is the best way to hone your skills and materialize your theoretical knowledge into practical experience. But if you want to step up your game and learn real-life industry projects, assignments and case studies check out our Advanced Certificate Programme in DevOps where you can showcase your expertise and skills to potential employers using an e-portfolio.
You will need to acquaint yourself with new tools and technologies while working on a computer science project. The more you learn about cutting-edge development tools, environments, and libraries, the broader will be your scope for experimentation with your projects. The more you experiment with different computer science project ideas, and mini-project topics for CSE 3rd year, the more knowledge you gain.
Computer Science study encompasses programming , design, analysis, and theory. Hence, Computer Science project ideas involve designing and developing various application-based software products and solutions. So, if you wish to know about a few exciting Computer Science project ideas, this article is just what you need! But, if you want to accomplish more, and gain superiority, consider pursuing our Advanced Certificate Programme in Cyber Security designed for working professionals and provides 1:1 high-performance coaching.
Traditionally, different specialization fields opted for a theoretical and instructions-oriented approach. However, today, most job roles demand professionals who have hands-on industry experience. Computer Science is one such discipline where academic learning does not suffice – students need to undertake practical training through real-world Computer Science projects and assignments. It aims to impart students with practical knowledge of operating computer systems.
upGrad’s Exclusive Software Webinar for you –
Panel discussion on career progress in the IT industry
Our learners also read : Java free online courses !
So, here are a few mini project ideas for cse for beginners:
Top 12 Computer Science Project Ideas
This list of computer science project ideas for students is suited for beginners, and those just starting out with Python or Data Science in general or final year project topics for computer engineering in diploma . These computer science project ideas will get you going with all the practicalities you need to succeed in your career as a software developer.
Further, if you’re looking for computer science project ideas for the final year, this list should get you going. So, without further ado, let’s jump straight into some computer science project ideas that will strengthen your base and allow you to climb up the ladder.
1. Face detection

It is of high importance and it serves various purposes in many fields. Most importantly, the technology of face detection has increased the surveillance efforts of the authorities.
Face detection coupled with the technology of biometrics and security has helped to identify people’s faces which has resulted in various processes such as starting an app, security, or guiding what the next action steps of the application would be.
The technology of face detection uses facial algorithms to identify the reach of facial prints. The technology can adapt and recognize which facial features to detect and which ones to ignore.
One of the best mini project ideas for cse to start experimenting with your hands-on computer science projects for students is face detection software. This project focuses on building face detection software using the OpenCV library. The face detection program will be modeled in a way that it can detect faces in live stream videos from a webcam or video files stored in a PC’s local storage. The software uses pre-trained XML classifiers to detect faces in real time and track them. You can also use different classifiers to identify various objects through this detection program.
To run this program, you need to install the OpenCV library on your local machine. Also, it would be best if you created appropriate paths for the XML classifier files before executing the program.
Also, check out our free react js online courses
2. Online auction system

The online auction allows the users to procure the benefits of the auction from any geographical location. The sellers can showcase their products or services to buyers across the locations. This helps in wider reachability and a huge expansion of the business.
Another useful feature of online auctions is the instant feedback feature that allows the bidders to track the price increase due to higher bidding.
The bidders or buyers from across the globe can log in at any time of the day to track or bid. This way they do not lose out on the opportunity due to different geographical timelines.
In an online auction, buyers and sellers engage in transactional business, wherein buyers purchase items through price bidding. Here, the bids have a starting price and an ending time. Potential buyers who place the highest bidding price for an item are declared the winners and owners of particular items.
In this project, you will create a secure online auction system using the fraud detection method with binary classification. If a user wants to buy a product through an online auction, they must provide their identification details like PAN number, email address, license number, etc. The system will then screen the users, authenticate, and authorize them. Only authorized users can bid in the auction. The system will be designed to predict fraudulent users in the early stages, thereby eliminating the risk of online fraud and scams. These beginner-level computer science projects will help build a strong foundation for fundamental programming concepts.
Learn Online software development courses from the World’s top Universities. Earn Executive PG Programs, Advanced Certificate Programs, or Masters Programs to fast-track your career.
Explore Our Software Development Free Courses
3. evaluation of academic performance.

Evaluation of academic performance allows the institutions to track the student’s performance. This not only helps in enhancing the student’s performance but also improves the teaching techniques and teacher’s performance.
The teachers could chart out teaching objectives that help them in achieving those objectives. This way, the teachers can adopt the successful pedagogy and ignore those pedagogies that do not add value to the student’s performance.
This is one of the most interesting mini project ideas for cse which involves the creation of an evaluation system that can analyze the academic performance of students by utilizing the fuzzy logic method. In the fuzzy logic method, you will consider three parameters, namely, attendance, internal marks, and external marks, to evaluate the final academic performance of students of an institution. The fuzzy inference system is much more accurate than conventional techniques.
While developing this Computer Science project, make sure that the student information uploaded is correct (devoid of errors). Faulty data entry may lead to inaccurate results.
Looking to boost your job prospects in the tech industry? Discover the best online computer courses for job readiness and elevate your skills to meet the demands of today’s digital workforce.
4. e-Authentication system
There are various types of authentication systems such as OTP, password, biometrics, etc.
The authentication system allows for a better user experience without having the need for multiple setups. It is also useful for tightening security. The enhanced security features pave the way for more number of users to adopt the technology.
The e-authentication has seen wider adaptability. It is used to access government services, transactional processes, online platforms, and more. The users can secure their identity with the means of an e-authentication system, thus providing scope for higher security.
This project focuses on building an e-Authentication system using a combination of QR code and OTP for enhanced security. The e-Authentication system is designed to avoid the hacking of accounts through shoulder surfing and misuse of login credentials. To be able to use the system, a user has to first register in the system by entering the basic registration details (name, address, zip code, etc.).
Once the registration is complete, the user can access the login module to authenticate the account by entering the email id and password combination they used during registration. Then, the user can proceed to the next authentication step using either of the two options – QR (Quick Response) code or OTP (Time Password). As per the option selected by the user, the system will generate a QR Code or an OTP. While the QR code will be sent to the user’s mail id, the OTP will be sent via SMS to the registered mobile number of the user.
The system randomly generates the QR Code and OTP at the time of login. It makes the login more secure. However, to use this system, one always needs an active Internet connection.
5. Cursor movement on object motion
This is a project where you will design a cursor that can move through the desktop and perform actions based on hand gestures. The system’s object movement will be based on RGB (red, green, and blue) colour – it can detect RGB colour objects that will function as the mouse. It would help if you imported the Java AWT library to coordinate with the cursor. The system setting uses a webcam to track the movement of the red, green, and blue objects and based on the object movement patterns, accordingly trigger an event.
The cursor movement system will acquire a single frame from the video recorded by the webcam and flip the frame for the user to see. It converts the captured image into a binary image wherein the RGB objects will become white. The system further adds a bounding box around the object that the user can move throughout the display.
6. Crime rate prediction
There are various benefits attached to crime rate prediction, such as taking preventive measures, tracking the culprits, advanced decision-making processes, etc.
The methodology allows the decision-makers to predict the crime and perform law- enforcement measures to mitigate the repercussions.
This way, the stakeholders can provide satisfaction, increase their lifestyle experience and most importantly identify the negative externalities and take appropriate actions to curb them.
The stakeholders can allocate the budget based on the statistic, this helps in effective resource allocation. The concerned agencies can utilize their resources to better use. The crime prediction system helps in faster justice delivery and reduces crime rates.
This is one of the most innovative mini project ideas for cse . As the name suggests, this Computer Science project involves building a prediction system that can analyze and predict the crime rate of a particular location. Naturally, the system needs to be fed with relevant data. It uses the K-means data mining algorithm to predict the crime rate. The K-means algorithm can cluster co-offenders and organized crime groups by detecting relevant crime patterns via hidden links, link prediction, and statistical analysis of crime data.
It functions somewhat like this – the admin will feed the crime data into the system. The algorithm will analyze crime data stored in a database and extract information and patterns from it. It will then collate the crime groups based on the patterns found in the dataset. The clusters will be made based on factors like where the crime took place, which people were involved in the crime, and when the crime occurred.
7. Android battery saver system

The battery saver project is useful for the users to track the usage of the application. The users can track which of the applications are consuming the maximum energy.
This way the users can optimize their application management. The optimization of the application can limit the application usage, and this end up limiting the battery.
The battery saver in the mobile phone would also allow the users to procure the list of applications in one place, the consumption rate is also accurate.
This is of a simple computer science project yet an exciting one. The Android battery saver is designed to analyze the battery usage data from built-in classes and create a consolidated list of apps that drain the power of the Android phone. The system can also determine the battery level of the phone. In situations where the battery level is low, and numerous apps are consuming too much power, this system will trigger an alarm telling the user to force stop or close the apps that are drawing power.
While the battery saver system has no backend, it uses Android Studio as the frontend. Since the system feeds on data from an Android phone, it does not need a backend framework. The primary aim of this battery saver system is to notify users of the apps that are high on power consumption, thereby allowing them to take specific actions to stop battery drainage.
In-Demand Software Development Skills
8. symbol recognition .
This is one of the excellent computer science project ideas for beginners. The proposed project seeks to build a system that can recognize symbols inserted by the user. This symbol recognition system leverages an image recognition algorithm to process images and identify symbols. First, the system converts RGB objects into grayscale images which are then further converted into black-and-white images. During the process, image processing is applied to remove unwanted objects and environmental interference. The system further uses optical character recognition for recognizing the images with 60-80% accuracy. This is one of the interesting computer science projects.
In the system, all symbol templates will be stored in a specific directory. The size of each image is fixed to allow the easy recognition of the symbols with accuracy. The templates will remain in black-and-white form, and the system will create a dataset of these templates. When a user inputs a query image into the system, it will resize the query image, compare the resized image values against the template image values in the dataset, and finally display the result in text format. So, while the system takes inputs as images, it delivers output in a textual form.
Explore our Popular Software Engineering Courses
Read: Software Engineering Project Ideas
9. Public news droid
There are various benefits to adopting the public news droid as one of the most effective mini project ideas for cse , such as-
- Easy to navigate
- Instant updates
- The users receive all the news, even if they are not trendy or hyped about it.
- Accessible by the registered users
- Feature to report news if it is malicious, or irrelevant
This is one of the excellent computer science projects for beginners. The public news droid is an informative software application that informs users about the trending news, occurrences, and interesting events happening in and around their locality. Thus, the idea behind creating this information system is to keep the users informed about the happenings in their vicinity. The system uses Android Studio as the front end and SQL Server as the back end.
The system involves two modules, one for the admin and one for the user. The admin monitors the accuracy and relevancy of news and information. For instance, if the admin encounters fake news or app misuse, they can take necessary action to stop the spread of such irrelevant information. On the contrary, users can view news and informative articles only of their respective localities/towns/cities, and they can add news related to any other city. Mentioning computer science projects can help your resume look much more interesting than others.
To use the app, users need to register into the system to use this app and add all the necessary details. Once the registration process is successful, the user can see the latest news, refresh the app, browse for more information, add new information and upload it (within 450 words), and so on. Users can also add images and titles for the news they add.
10. Search engine

The search engine is highly useful, it helps in bringing the visibility of the brand, target-based ads, brand awareness, performance management, increasing website traffic, and more.
The brands can make their visibility grow by using proper keywords and using various other methodologies. Moreover, the brands can utilize the search engine to overcome the competition and grow their business.
The more people are able to see the brand, the better its authenticity would be. It will eventually result in the revenue growth of the brand.
This search engine is developed using web annotation. It is one of the trending computer science projects where when users enter specific words or phrases in a search engine, it automatically fetches the most relevant pages that contain those keywords. Web annotation makes it possible. Web annotation helps to make an application user-friendly. Thanks to web annotation, users can add, modify, and remove information from Web resources without altering the resource itself.
This project uses web annotation on pages and images. When the user enters words, names, or phrases in the system, it will fetch the information and pictures having the same annotation. Then the system displays a list of results that contain the image or content matching the user input. For this search engine, you need to use an effective algorithm to generate a query result page/search result records based on users’ queries.
11. Online eBook maker
One of the best ideas to start experimenting with your hands-on computer science projects for students is working on an online eBook maker. This online eBook maker will allow users to design and create eBooks free of cost. The system has two modules – admin login and author login. The admin can accept requests from users (authors), check and validate their details, evaluate completed eBooks, and process the request by mailing eBooks to the authors. Users can register in the system using the author login.
After filling in the necessary details, users can create new books, specify the context of books, add the title, and a number of pages, add a book cover, etc. Existing users can simply log in using their ID and password, and they can either create new books or resume editing the existing (unfinished) eBooks. Authors can keep only three incomplete eBooks at a time, of which they must complete at least one book before starting a new book.
12. Mobile wallet with merchant payment

There are various benefits attached to the mobile wallet, such as-
- Cashless payment
- The applications are protected with a password
- The QR code generation, allows the users to ensure safe transactions.
- The amount first gets stored to the merchant’s wallet, eventually reaching to their bank accounts.
- Reduces fraud detection
This can be an interesting and useful computer science project ideas. As you can guess by the name, this is a QR code scanning application designed for handling and facilitating liquid cash transactions between sellers (merchants) and consumers. The aim of building this app is to provide a secure, reliable, and efficient platform for monetary transactions on both ends. Each time, the system generates a unique QR code ID, and all passwords are encrypted using AES Encryption Algorithm.
There are two parts of this application – an Android application for merchants that can scan the QR code and the other part for the consumer for generating the QR Code. The front end uses Android Studio, and the back end uses SQL Server. This system functions something like this – when merchants scan the QR code generated by the app, the desired amount is transferred into their wallet which is easily transferable into their bank accounts. As for the consumers, they need to add money to their wallets via their credit/debit cards linked to their bank accounts. They can save the card details for future use. Merchants can also change their personal and bank details. And this is the perfect idea for your next computer science project!
Check out: Java Project Ideas & Topics
Some Bonus A-Level Computer Science Project Ideas
Basic hospital management system.
The hospital management system is useful for managing resources and operating the hospital effectively. The hospital management infrastructure is useful for managing patient details, infrastructure management, drugs management, dispensary, etc.
The staff trusts the hospital management application to run the day-to-day functions. Thus, technology becomes of high importance.
The health management system facilities in better decision-making and revenue management. Apart from serving the patients, the hospitals have to take care of the revenue for acquiring talented doctors and providing decent health facilities.
This is a programming and database management app designed as a centralized system for hospitals to digitize and handle huge data ( like patient details, appointments made, results of lab tests, patient diagnosis information, etc.). This is one of the best computer science project ideas that can add value to your resume.
Developing a hospital management system is easy for beginners. A functional and effective hospital management system can be created with a basic knowledge of HTML and CSS.
The system should be able to receive new entries, store them safely, and enable hospital staff and system administrators to access, and use the data.
You should develop the hospital management system in a way that should assign a unique ID to each patient registered at the hospital. The system must include all necessary details of hospital staff besides patients in a local database.
When the data increases, it becomes challenging for the staff and hospital administrator to find the required data of a particular patient or staff. So, it is important to have search functionality to make the search process across thousands of data much easier.
While it is enough to use the local storage to run the hospital management, you can also use a cloud database. Both of them have their pros and cons. You must leverage the advantages and disadvantages to make computer science topics more challenging and interesting. Check out this Github project for reference.
Real-time Weather Forecasting app
This is a beginner-level web development & programming app that will serve best as a mini-project topic for CSE third-year students or a final-year project for those pursuing diplomas in Computer science. The main objective of the app is to create a web-based weather application that can provide real-time weather details (like current temperature and chances of rain) of a particular location. The app can also predict if the day will be rainy, cloudy, or sunny.
Developing a weather forecasting app is the best way to put your coding skills to the test. To create a weather forecasting app, you will need a stronghold on the basics of web development, HTML, CSS, and JavaScript. For providing the best backend performance, good knowledge of Node.js and express technologies is a must.
It is important to know how to use API calls to scoop out weather information from other websites and display relevant information in your app.
For the app’s best User Interface, you have to place an input text box in which the users can enter the location for which weather information is needed. As soon as the search button is hit, the weather forecast for the input location should pop out. Check out this Github project for reference.
It is an interesting app that involves application designing & development, multi-thread processing, socket programming, and networking.
Such computer science topics aim at developing a chat application to facilitate instant messaging. Users can create personal accounts in the chat app from where messages can be sent to other chat app users. Check out this Github project for reference.
News Feed App
News feed applications make good examples of project ideas for computer science . Further, you will be equipped with knowledge of database and newsfeed algorithms as well as designing user interfaces. It is worth noting that you should start by collecting data from different sources which will help you to have a deep knowledge and project ideas for computer science, like topics including top 10 projects in computer science, projects for cse and mini projects for computer science students . There are many ways of getting this information related to major project topics for computer engineering , such as web scraping techniques, accessing APIs and even RSS feeds or any other final year project ideas for computer science students .
Once you get a dataset, you should process it and turn it to be readable for your app. Thus, some elementary NLP skills are required here. At last, an algorithm must choose which stories like, be project ideas for computer engineering the news feed will show out of all available information. For example, this can be determined based on topics such as user preferences, popularity, and the newest updates. Working as a news feed application will help you learn crucial skills needed in every software developer.
Optical Character Recognition System (OCR)
It may also be very interesting to work on project ideas for computer science of an optic character recognition system (OCR). Machine-readable text can also be produced using OCR technology from scanned text images. However, this might be a hard thing, especially considering the numerous types of fonts and layout formats that can be used especially when doing mega project topics for computer engineering.
However, a well-used OCR system can be a very powerful instrument which will be helping in making projects for computer science students . Besides being environmentally friendly, such a system can aid in cutting back on paper waste within companies since it facilitates fast searching through voluminous data and enhances workplace efficiency, when it is about final year projects for computer science students, or also capstone project ideas for computer science and innovative project ideas for computer science students . The best bet for you if your aim is working on a project which has substantial real-life significance would be an OCR system.
Library Management System
Computers are often utilised in libraries for record-keeping and maintaining the collection. This has made LMS a useful tool for library staff as it serves as a result. LMSs enable a library to track and control its books, e-books, journals, etc. The systems can, therefore, double up as circulation statistics storage devices and patron file databases.
An example of exciting project ideas for computer science or csp project topics, could be library management systems, simple project topics for computer science, which teach databases and information management. In addition, the process of creating an LMS can involve highly complicated operations using various kinds of advanced data arrays. In this regard, working with an LMS might be a great option through which you can improve your computer programming proficiency, in skills like design engineering project topics for computer engineering.
Virtual Private Network
Virtual Private Network makes project ideas for computer science for those who study computer science. Therefore, VPNs allow people to establish a private network connection with maximum security via the Internet. VPNs can be effective in terms of protecting and securing data, which is done by encrypting it and transmitting it to a specific VPN server through disguised traffic. People can also use VPNs to bypass internet censorship and access blocked sites. Therefore, VPNs have become increasingly popular because of this reason.
Computer science students have many options when choosing ways to set up a VPN. With some study, computer science students can create a working and user-friendly VPN.
Real-time web search engine
A good computer science project would be real-time online search engines. Such an endeavour aims at constructing a relevant search engine for accessing the contents of the World Wide Web (WWW) on a real-time basis. It would involve a large crew of computer science experts. Nevertheless, they will reap tremendous gains.
Such a search engine would be of great importance to all users of the Internet. This is very encouraging for this company and their developers as well. This makes search engines in real-time a good candidate for a challenging CS project that matters.
Task Management Application
One of the popular project ideas for computer science is an application for task management. This application will allow users to develop their tasks and schedules, assign deadlines, and track progress. Task creation and modification can also be simplified using a user-friendly interface like drag-and-drop functionality. It should have features like automatic task scheduling with reminders, interaction with email and calendar programs and sharing of tasks between users.
During the programme, students will learn about database design and development, user interface design and, finally, data structures and algorithms. In the end, one should strive to create an application which is not only functional but also easy to navigate.
Final-Year Project Ideas for Computer Science Students
Being a computer science student is an excellent chance for you to implement such initiatives using your knowledge and skills as project ideas for computer science. There is no limit to what one can come up with, ranging from creating new algorithms, designing applications, solving daily challenges and many more. Using these measures ensures that a company can avoid getting into unnecessary financial issues and, at the same time, improve its market value.
To get you started, here are the top innovative final-year project ideas for computer science students:
1. Advanced Reliable Real Estate Portal
As our world increasingly embraces digital transformation, the real estate sector is following suit by making its way into the online domain. Nevertheless, numerous obstacles persist in the online property buying and selling process. Authenticating the precision of listings poses a challenge, and there is frequently a shortage of transparency concerning associated fees.
As one of the best project ideas for computer science student, there lies an opportunity to develop a real estate portal that enhances reliability and transparency, facilitating seamless connections between buyers and sellers. This endeavor has the potential to transform the conventional methods of property transactions, streamlining the process and making it more efficient.
2. Image Processing by using Python
Python stands out as a versatile programming language applicable to a diverse array of tasks. Image processing is an area where Python excels. Leveraging Python, one can craft algorithms designed to enhance image quality or facilitate object identification within images. The potential applications of such capabilities extend to fields such as security or medicine.
3. Admission Enquiry Chat Bot Project
The university application procedure can be pretty intimidating, especially for international students. A possible solution is to develop a chatbot that assists prospective students throughout the admission process by addressing their inquiries and furnishing details about specific programs. This initiative would simplify the navigation of the university application process, enhancing transparency regarding admission requirements.
4. Android Smart City Travelling Project
As smart cities continue to emerge, the need for user-friendly apps facilitating efficient navigation within urban areas is on the rise. Consider creating an Android application designed to assist users in identifying the quickest route to their destinations by utilising real-time traffic data. This initiative has the potential to alleviate traffic congestion in cities, enhancing overall accessibility for individuals trying to reach their goals.
5. Secure Online Auction Portal Project
Online auction platforms are widely utilised for buying and selling goods over the Internet. Nonetheless, security apprehensions often arise during transactions on these websites. As a computer science student, you have the opportunity to develop a secure online auction portal that employs encryption to safeguard users’ personal information. This implementation would instil confidence in users engaging in online transactions, fostering a sense of security and potentially enhancing trust in auction websites.
6. Detection of Credit Card Fraud System
The surge in online shopping and transactions has led to a significant escalation in credit card fraud. Leveraging your computer science expertise, you can contribute to addressing this issue by creating a system capable of detecting fraudulent activity. These project ideas for computer science entails analysing data derived from credit card transactions and identifying patterns indicative of fraud. Once your system is developed, businesses can utilise it to prevent fraudulent transactions proactively.
7. Real Estate Search Based on the Data Mining
Engaging in the home buying or selling process can be protracted and intricate. Yet, as a computer science student, you possess the potential to simplify this procedure by crafting a real estate search engine employing data mining techniques. This endeavour involves gathering data from diverse sources, including MLS listings, and subsequently utilising analytical methods to discern trends and patterns. The insights derived from this information can then be utilised to assist buyers and sellers in discovering the ideal home.
8. Robotic Vehicle Controlled by Using Voice
Given the growing prevalence of voice-controlled devices, the development of voice-controlled robotic vehicles has garnered considerable attention. Encouraging computer science students to undertake such project ideas for computer science can contribute to advancing this technology. This involves creating a system where a robotic vehicle can be controlled through voice commands. The project entails designing and implementing software capable of interpreting voice commands and converting them into executable actions for the robotic vehicle.
9. Heart Disease Prediction: Final Year Projects for CSE
Heart disease stands as a prominent global cause of mortality. Nevertheless, early detection can significantly enhance the effectiveness of treatment for many cardiac conditions. As a computer science student, you have the opportunity to create a system that forecasts the likelihood of an individual developing heart disease, drawing insights from their medical history and various risk factors. This undertaking involves collecting data from medical records and employing machine learning algorithms to construct the predictive system.
10. Student Attendance by using Fingerprint Reader
Recording attendance in a classroom setting can be a laborious task, particularly in larger classes with list of projects for computer science students. As a computer science student, you have the opportunity to streamline this process by creating a fingerprint reader system that automates attendance tracking. This project entails designing and implementing software capable of reading fingerprints and subsequently comparing them to a database of students’ fingerprints. Upon a successful match, the student’s name will be automatically added to the attendance list.
11. Cloud Computing for Rural Banking Project
The objective of this initiative is to establish a streamlined and secure banking system for rural areas by leveraging cloud computing technology. The project encompasses the creation of a web-based application enabling users to access their accounts and conduct transactions online. Hosted on a remote server, the application will be reachable from any location with an internet connection. Additionally, the project will involve crafting a mobile app that allows users to manage their accounts conveniently on their smartphones.
12. Opinion Mining for Comment Sentiment Analysis
These project ideas for computer science entails the creation of a system capable of autonomously analysing the sentiment expressed in comments across online platforms, including news articles, blog posts, and social media. Utilising natural language processing techniques, the system will discern the sentiment of each comment and generate a corresponding report. Its application extends to monitoring public opinion on diverse topics and issues.
Tips For Beginners To Make Computer Science Projects More Innovative and Interesting:
While designing a computer science project, adopting creativity and making it more innovative may offer a rewarding experience for beginners. This may also draw significant attention to their capability and help them make a statement. Here are some tips that will assist beginners in infusing innovation into their mini project ideas for cse.
Explore More On Your Interests:
As the choice of the topic is one of the most important aspects for a beginner, it is essential to choose topics and ideas that genuinely interest an individual. Passion for a particular subject will drive your curiosity and boost motivation resulting in more innovative ideas.
Conduct Through Research:
Once you have chosen the topic, consider conducting in-depth research for securing a deep understanding of the existing technologies, solutions, and best practices for the project. This will help you to get significant insights into what has already been attempted before and how you can design a new approach to make it interesting.
Ideate And Brainstorm:
Random thoughts sometimes form the basis of the development of an innovative idea. Therefore take out some time for brainstorming and pen down all your random thoughts. This will lead you towards more creative thinking and making new innovations.
Put Emphasis On Practical Solutions:
Look for ways to address the challenges in the real world as a computer science project dealing with practical solutions would be more valued and create an impact.
Take Baby Steps:
For beginners to make a topic more interesting, the best idea would be to adapt bay steps. Begin with a scope that seems manageable at first and expand on it later. Focusing on solving specific problems first, along with the implementation of particular features efficiently, would help in gaining confidence and skills. After this, one may expand more to enhance the quality of the project and make it more innovative.
Consider Collaboration With Others:
Teamwork often leads to innovative ideas and solutions. Entering into a collaboration with fellow beginners or individuals who have gained considerable experience may often give rise to fresh perspectives and diverse project ideas.
Stay Updated With Market Trends:
Incorporation of the latest trends and advances in computer science projects will undoubtedly make it more interesting. Therefore it deems necessary to ensure acquaintance with the latest trends and advances in the oeuvre of computer science. Following blogs of the particular industry, exploring new technologies that are making waves as well as attending webinars may help one to remain updated.
Design for User Experience:
While developing the project, consider the user experience. A user-centric design, smooth navigation, and intuitive interface prove effective in enhancing the overall appeal of the project, retaining a sense of innovation.
Make Use Of Creative Visualisation:
If the project includes the representation of data, implement creative ways to visualize them. Unique visualization techniques can make your project unique and enhance comprehension of data.
The meaning of innovation doesn’t always necessarily mean the creation of something entirely new. It may also encompass finding unique ways in solving a particular problem, making improvements on existing solutions, or incorporating new technologies. It is by staying curious, ensuring an open mind towards learning, and enjoying the entire procedure that you can make your computer science project more innovative and interesting as a beginner.
Read our Popular Articles related to Software Development
Wrapping up.
These are some cool mini project ideas for cse that you can toy with! Once you finish with these simple computer science projects, and final year project topics for computer engineering in diploma , I suggest you go back, learn a few more concepts and then try the intermediate projects.
When you feel confident, you can then tackle advanced projects. If you wish to improve your python skills, you need to get your hands on these computer science project ideas . Working on real-world projects allows you to apply your knowledge and skills to practice. Also, if you can create a few of these Computer Science projects, you can add them to your resume – it will definitely help you to stand out among the crowd. I hope you will learn a lot while working on these computer science projects.
If you’re interested to learn more about Java, and full-stack software development, check out upGrad & IIIT-B’s Executive PG Programme in Software Development – Specialisation in Full Stack Development which is designed for working professionals and offers 500+ hours of rigorous training, 9+ projects, and assignments, IIIT-B Alumni status, practical hands-on capstone projects & job assistance with top firms.

Pavan Vadapalli
Something went wrong
Our Trending Software Engineering Courses
- Master of Science in Computer Science from LJMU
- Executive PG Program in Software Development Specialisation in Full Stack Development from IIIT-B
- Advanced Certificate Programme in Cyber Security from IIITB
- Full Stack Software Development Bootcamp
- Software Engineering Bootcamp from upGrad
Popular Software Development Skills
- React Courses
- Javascript Courses
- Core Java Courses
- Data Structures Courses
- ReactJS Courses
- NodeJS Courses
- Blockchain Courses
- SQL Courses
- Full Stack Development Courses
- Big Data Courses
- Devops Courses
- NFT Courses
- Cyber Security Courses
- Cloud Computing Courses
- Database Design Courses
- Crypto Courses
- Python Courses
Our Popular Software Engineering Courses
Frequently Asked Questions (FAQs)
A web architecture is the structure of a website, including its underlying servers, databases, networks, routers, and protocols. It is the design of the system that makes up the World Wide Web. It is also the management of the software and servers used to run websites. Web architecture is an important part of any web presence. It dictates how a user navigates from one website to another and influences the overall experience. It should focus on providing a positive online experience, and should always be used to enhance the overall user experience, but it should not be confused with the design of the website itself.
Data mining algorithms are a set of software tools and algorithms used to extract information from large amounts of data. They are used to determine which data points are most relevant in a given dataset and are used in a variety-generation algorithm, which is used to generate new lines of data. Data mining algorithms are the steps used to find patterns and trends in large data sets. They are important tools helping organizations make more informed decisions and better serve their customers. Data mining algorithms are used in a wide range of applications, including business intelligence, marketing, and fraud detection. They are also used to understand the behavior of large sets of data, to identify relationships and patterns, and to make predictions.
The need for effective e-authentication is due to the fact that users are increasingly using profile verification and sometimes password reset options to protect their accounts on online services, such as social networking sites, and to improve their online security more generally. The use of e-authentication is becoming a common way to prove identity when buying products or services. The process allows users to prove their identity using digital methods instead of traditional documents like ID cards. E-authentication is becoming more and more common, and there are a number of ways it is shaping our digital world.
Related Programs View All
Certification
40 Hrs Live, Expert-Led Sessions
2 High-Quality Practice Exams
View Program

Executive PG Program
IIIT-B Alumni Status

Master's Degree
40000+ Enrolled Learners

Job Assistance
32-Hr Training by Dustin Brimberry
Question Bank with 300+ Practice Qs
45 Hrs Live Expert-Led Training
Microsoft-Approved Curriculum
159+ Hours of Live Sessions
126+ Hours of Live Sessions
Fully Online
13+ Hrs Instructor-Led Sessions
Live Doubt-Solving Sessions

2 Unique Specialisations
300+ Hiring Partners
20+ Hrs Instructor-Led Sessions
16 Hrs Live Expert-Led Training
CLF-C02 Exam Prep Support

24 Hrs Live Expert-Led Training
4 Real-World Capstone Projects
17+ Hrs Instructor-Led Training
3 Real-World Capstone Projects
289 Hours of Self-Paced Learning
10+ Capstone Projects
490+ Hours Self-Paced Learning
4 Real-World Projects
690+ Hours Self-Paced Learning
Cloud Labs-Enabled Learning
288 Hours Self-Paced Learning
9 Capstone Projects
40 Hrs Live Expert-Led Sessions
2 Mock Exams, 9 Assessments

Executive PG Certification
GenAI integrated curriculum

Job Prep Support
Instructor-Led Sessions
Hands-on UI/UX
16 Hrs Live Expert-Led Sessions
12 Hrs Hand-On Practice
30+ Hrs Live Expert-Led Sessions
24+ Hrs Hands-On with Open Stack
2 Days Live, Expert-Led Sessions
34+ Hrs Instructor-Led Sessions
10 Real-World Live Projects
24 Hrs Live Expert-Led Sessions
16 Hrs Hand-On Practice
8 Hrs Instructor-Led Training
Case-Study Based Discussions
40 Hrs Instructor-Led Sessions
Hands-On Practice, Exam Support
24-Hrs Live Expert-Led Sessions
Regular Doubt-Clearing Sessions
Extensive Exam Prep Support
6 Hrs Live Expert-Led Sessions
440+ Hours Self-Paced Learning
400 Hours of Cloud Labs
15-Hrs Live Expert-Led Sessions
32 Hrs Live Expert-Led Sessions
28 Hrs Hand-On Practice
Mentorship by Industry Experts
24 Hrs Live Trainer-Led Sessions
Mentorship by Certified Trainers
Full Access to Digital Resources
16 Hrs Live Instructor-Led Sessions
80+ Hrs Hands-On with Cloud Labs
160+ Hours Live Instructor-Led Sessions
Hackathons and Mock Interviews
31+ Hrs Instructor-Led Sessions
120+ Hrs of Cloud Labs Access
35+ Hrs Instructor-Led Sessions
6 Real-World Live Projects
24+ Hrs Instructor-Led Training
Self-Paced Course by Nikolai Schuler
Access Digital Resources Library
300+ Hrs Live Expert-Led Training
90 Hrs Doubt Clearing Sessions
56 Hours Instructor-Led Sessions
78 Hrs Live Expert-Led Sessions
22 Hrs Live, Expert-Led Sessions
CISA Job Practice Exams
Explore Free Courses
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in Canada through this course.
Advance your career in the field of marketing with Industry relevant free courses
Build your foundation in one of the hottest industry of the 21st century
Master industry-relevant skills that are required to become a leader and drive organizational success
Build essential technical skills to move forward in your career in these evolving times
Get insights from industry leaders and career counselors and learn how to stay ahead in your career
Kickstart your career in law by building a solid foundation with these relevant free courses.
Stay ahead of the curve and upskill yourself on Generative AI and ChatGPT
Build your confidence by learning essential soft skills to help you become an Industry ready professional.
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in USA through this course.
Suggested Blogs
![best case study topics on computer science Scrum Master Salary in India: For Freshers & Experienced [2023]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F05%2F486.png&w=3840&q=75)
by Rohan Vats
05 Mar 2024
![best case study topics on computer science SDE Developer Salary in India: For Freshers & Experienced [2024]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F05%2F482-1.png&w=3840&q=75)
by Prateek Singh
29 Feb 2024
by venkatesh Rajanala
by Harish K
by Geetika Mathur
by spandita hati

28 Feb 2024

Case Study Topics in Computer Science PDF: A Comprehensive Guide for HR Professionals
Are you an HR professional searching for impactful case study topics in computer science? Look no further! In this article, we will provide you with a comprehensive guide on how to select the right case study topics for computer science, and how these topics can help you in your recruitment process.
Why Case Studies Matter in Computer Science Recruitment
Case studies are an excellent way to assess a candidate’s problem-solving skills, critical thinking ability, and technical expertise. They provide a glimpse into how a candidate thinks and works through complex problems and can be highly beneficial in determining whether a candidate is a good fit for the job.
How to Choose the Right Case Study Topics
Choosing the right case study topics can be challenging, but there are several things to consider. Firstly, ensure that the topic is relevant to the role you are hiring for. Secondly, select a topic that is challenging but not too complex, as you want to be able to assess the candidate’s ability to solve the problem without overwhelming them. Lastly, choose a topic that can showcase the candidate’s technical expertise.
Top Case Study Topics in Computer Science
To help you get started, we have compiled a list of the top case study topics in computer science:
- Developing a secure login system
- Creating an algorithm for sorting data
- Designing a database for an e-commerce website
- Developing a mobile application for a ride-sharing service
- Building a recommendation system for an online marketplace
How Algobash Can Help You
Algobash is a platform that offers a wide range of case study topics in computer science, as well as a comprehensive assessment tool that can help you evaluate a candidate’s skills and expertise. With Algobash, you can streamline your recruitment process and find the best candidates for the job.
In conclusion, case study topics in computer science can be highly effective in assessing a candidate’s skills and technical expertise. By selecting the right topics and using tools like Algobash, you can make your recruitment process more efficient and accurate.
Benefits of Using Automated Interview for Companies
Best platform for ai interview in indonesia, 10 interview questions and answers that job seekers should keep in mind.

700+ Seminar Topics for CSE (Computer Science) with ppt (2024)
Seminar Topics for Computer Science (CSE) with ppt and report (2024) : As technology is emerging day by day. new technologies are coming quickly. And Seminar topics for Computer Science are becoming must find for every student. There are lots of students in Computer Science and Engineering who need quick seminar topics for CSE with ppt and report.
Table of Contents
We understand the burden students are facing today. So we have made a huge collection of Seminar Topics for CSE with ppt and report.
I hope you will save a lot of time with these Seminar Topics for CSE with ppt.
Seminar Topics for Computer Science with ppt and report (2024)
Technical seminar topics for cse with abstract.
3D Printing
3D Printing is the process to develop a 3D printed object with the help of additive processes. Here, there are three-dimensional objects created by a 3D printer using depositing materials as per the digital model available on the system.
4G Technology
4G Technology can be defined as the fourth generation communication system that let users use broadband type speed without any need for Wi-Fi. It is simply called an advanced level radio system that makes the system efficient and quicker. Over the years, it has become an important part of people’s lives globally.
5 Pen PC Technology
5 Pen PC Technology is simply a cluster of gadget that comes with a great sort of features. It includes a virtual keyboard, projector, personal ID key, a pen-shaped mobile phone, and a camera scanner. Using this technology, an crystal clear digital copy of handwritten details can be created.
Android is an operating system created mainly for smartphone and tablets. It is a brilliant technology that allows the users to perform a variety of functions like using GPS for checking traffic areas, etc. Android is the mastermind behind everything ranging from top tablets to 5G phones.
AppleTalk is a networking protocol used in Mac computer systems and devices for making communication. It was originally introduced in 1984 by Apple and get replaced by TCP/IP in 2009 with the release of macOS X v10.6.
Blackberry Technology
Blackberry Technology is an integrated e-mail system provided by the Blackberry company in their handheld devices. Here, there is a unique PIN provided to every phone for identifying the device. This technology can even get accessed in an offline area without any need for wireless service.
Bluejacking
Bluejacking is a technique used by hackers to send messages to a different user with the help of Bluetooth connection. The most common use of this technology is sending unwanted images, text messages or sounds to other Bluetooth equipment in the network range.
Blue-ray Disc
Blu-Ray is an high-definition disc format that let the users see images with extreme level depth, detail, and color. It was released in 2006 as a successor to DVD for improving the experience of the users. This type of discs streams data at 36 megabits per second that is much fast than a DVD.
Cloud Computing
Cloud computing is an advanced method for delivering resources by utilizing the internet. This technology has made it possible to access their resources by saving them to a remote database. It eliminates the burden to store files on an external device.
CAD/CAM is well-known software whose main motive is to simply the design and machining process. It is simply collaboration between computers and machines that make the job of the designers as well as manufacturers easier. It is created after decades of research and testing process.
Cryptography
Cryptography is simply a technique for transforming the basic text into unintelligible ones and vice-versa. This amazing process not only gives protection to the data from online theft but also utilized for the user authentication process. It is used commonly in banking and e-commerce industry in various countries globally.
CORBA (Common Object Request Broker Architecture) is a special architecture whose main job is explaining a unique mechanism for better distribution of objects over a certain network. It let them make communication with each other without any platform and language boundary. This specification created by Object Management Group.
Geographic Information System
GIS fully abbreviated as Geographic Information System is an approach that collects, operate, and analyze data in the framework. There are many types of data integrated by this system along with the spatial location. Apart from that, there is lots of information that further visualized with the help of maps and 3D scenes.
Cyber Crime
Cyber crime is a crime form where the computer is utilized as a weapon. It includes things like spamming, hacking, phishing, etc. On top of that, computers are used for stealing personal data of individuals in these types of crimes. Despite the advancement in technology, the frequency of cyber crimes is increasing every year.
Computer Forensics
Computer Forensics is a technique that involve investigation and analysis processes for collecting and saving important pieces of evidence from certain computing equipment. The main use of these data is to present a strong case in the court of law. This process is performed by Forensic Computer Analysts.
Data Warehousing
Data Warehousing is a technique for gathering and controlling data from a great sort of resources with a motive to give useful insights on the business. This technology is used for connecting and analyzing business data so that it gets available to the businesses within a short time.
Database Management System (DBMS)
Database Management System is a special application package whose main motive is defining, manipulating, and controlling data. Due to this process, the developers no longer need to frame programs to maintain data. There are many fourth-generation query languages available on the internet for better interaction in a database.
Direct Memory Access (DMA )
Direct Memory Access is a computing technique used for the transfer of data from RAM in a computer to a different area in the system without CPU processing. In simple words, its main duty is to transfer or get data to or from main memory so that memory operations become faster.
Digital Watermarking
Digital Watermarking is an extensive technique for embedding data into different types of digital forms. It includes audio, video, images, and other similar objects. The majority of digital devices can easily read and detect digital watermarks by validating the original content.
Domain Name System (DNS)
The Domain Name System (DNS) can simply be called phonebook that comes with the information of domain names location is stored for further translation into IP addresses. In simple words, it translates the domain names into IP addresses allowing browsers to load resources on the internet.
Distributed Systems
A distributed system can be called a cluster of computer systems that work in collaboration with each other to look like as a single entity to the end-user. All the computers in the system are connected through a distribution middleware. The main purpose of this system is sharing various resources to the users with a single network.
Nanoparticles
A nanoparticle is a material used for making computer hardware components with a motive to boost the density of solid-state memory. The complete process is performed by followed a process known with the name of nanotechnology. It let the memory consume low power along with reducing chances of failure.
SCADA is a computer technology used for collecting and checking real-time data. It is fully abbreviated as Supervisory Control and Data Acquisition. The main purpose of this application can be founded in the telecommunications, energy, gas refining, and transportation industry.
LAN WAN MAN
LAN (Local Area Network) is a cluster of network devices that are connected with each other in the same building. MAN (Metropolitan Area Network) performs the same job but covers a large area than LAN like a city or town. WAN (Wide Area Network) covers a bigger area than both LAN and MAN.
A black hole is a fascinating object that is located in outer space. They have a very dense nature and a pretty solid gravitational attraction that even light can’t grasp after coming closer to them. Its existence was predicted first by Albert Einstein in 1916.
Distributed denial-of-service attack (DDoS)
Distributed Denial of Service (DDoS) is a DOS attack that includes a variety of compromised systems. It is often related to the Trojan which is a common form of malware. It includes attackers who transmit data to enjoy vulnerabilities harming the business systems.
E-ball Technology
E-Ball is a sphere-shaped computer system that comes with all features of a traditional computer but has a very smaller size. It even comes with a large screen display along with mouse and keyboard. It is designed in such a way that portability gets a great boost.
Enterprise Resource Planning (ERP)
Enterprise Resource Planning is a business modular software that created for integration of major functional areas in the business processes of the company in a unified area. It comes with core software components that are known as modules targeting major areas in businesses that include production, finance, accounting, and many more.
Extreme Programming (EP)
Extreme Programming (XP) is a software development process whose main mission is creating top-quality software matching needs of clients. It is pretty useful where there are software requirements that change on a dynamic basis. Also, this methodology is used in areas where risks result from fixed time projects
Biometric Security System
Biometric Security is a well-known security system that mainly utilized for authenticating and giving access to the company for verification of a person’s characteristics instantly. It is one of the most powerful techniques used for identity verification in various countries globally.
Common Gateway Interface (CGI)
The Common Gateway Interface (CGI) is a detailed specification that shows the way a program interact with an HTTP server. It works as a middleware between external databases and WWW servers. There are particular information and formatting processes performed by CGI software for WWW servers.
Carbon Nano Technology
The carbon nanotechnology is a process to control atom assembly of molecules at certain dimensions. The main material used for this process is Carbon nanobeads.
Middleware Technologies
The middleware technologies are an application that used making a connection between network requests created by a client for back-end data requested by them. It is a very common software used in the software world in both complexes as well as existing programs.
Invisibility Cloaks
Invisibility Cloaks also known as a clocking device is a method for steering light waves near a material to make it look invisible. There is a great role played by the viewer’s eyes and the instrument used on the level of visibility.
Computer Peripheral
A computer peripheral is a device whose main job is adding information and instructions in the system for storing and then transferring the process data to the user or a device that comes under the system’s administration. Some common examples of a computer peripheral are a printer, scanner, mouse, and keyboard.
Mobile Number Portability (MNP)
Mobile Number Portability (MNP) is an advanced level technology using which the mobile phone subscribers can change their cellular operator without changing their number. It was launched in Singapore about two decades ago, but since then expanded to almost every country across the globe. The complete process to change operator is very customer-friendly and easier.
HTML fully abbreviated as Hypertext Markup Language is a computer language that is mainly used for creating paragraphs, headings, links, blockquotes, and sections in a web page or applications. However, it isn’t a programming language and doesn’t come with the desired features for developing dynamic functionality.
Technical Seminar Topics for CSE
- IP Spoofing
- Mobile Phone Cloning
- Bluetooth Technology
- Mobile Computing
- Pill Camera
- Human Computer Interface
- Software Testing
- Data Mining
- Artificial Neural Network (ANN)
- Wireless Sensor Networks (WSN)
- Wireless Mesh Network
- Digital Light Processing
- Distributed Computing
- Night Vision Technology
- Wireless Application Protocol
- 4G Wireless System
- Artificial Eye
- Asynchronous Chips
- Graphics Processing Unit (GPU)
- Wireless Communication
- Agent Oriented Programming
- Autonomic Computing
- GSM (Global System for Mobile Communications)
- Interferometric Modulator (IMOD)
- Microsoft Surface
- Cryptography and Network Security
- 5G Technology
- FERROELECTRIC RAM (FRAM)
- Object Oriented Programming (OOP)
- Network Topology
- Project Loon
- Storage Area Network (SAN)
- Hybridoma Technology
- Ribonucleic Acid (RNA)
- Cryptocurrency
- Handheld Computers
- Specialized Structured Svms In Computer Vision
- Intel Centrino Mobile Technology
- Digital Audio Broadcasting
- Screenless Display
- Cloud Storage
- IP Telephony
- Microprocessor and Microcontrollers
- Strata Flash Memory
- Gaming Consoles
- The Qnx Real-Time Operating System
- High Performance DSP Architectures
- Tamper Resistance
- MiniDisc system
- XBOX 360 System
- Single Photo Emission Computerized Tomography (SPECT)
- Tactile Interfaces For Small Touch Screen
- Cooperative Linux
- Breaking the Memory Wall in MonetDB
- Synchronous Optical Networking
- Virtual Keyboard Typing
- Optical Networking and Dense Wavelength Division Multiplexing
- Driving Optical Network Evolution
- Low Energy Efficient Wireless Communication Network Design
- Hyper-Threading technology
- Money Pad The Future Wallet
- Remote Method Invocation (RMI)
- Goal-line technology
- Security And Privacy In Social Networks
- Yii Framework
- Digital Preservation
- Optical Storage Technology
- Nvidia Tesla Personal Supercomputer
- Dynamic Cache Management Technique
- Real-Time Task Scheduling
- Session Initiation Protocol (SIP)
- Conditional Access System
- Project Oxygen
- Big Data To Avoid Weather Related Flight Delays
- Operating Systems with Asynchronous Chips
- Predictive Analysis
- Sandbox (computer security)
- Network Address Translation
- Biometrics Based Authentication
Also See: 105+ Technical IEEE Seminar Topics for CSE
Best Seminar Topics for CSE
- Google Chrome OS
- Google Glass
- Intrusion Detection Systems (IDS)
- Jini Technology
- LAMP Technology
- Mind Reading
- Meta Search Engine
- Nanotechnology
- Network Security
- Operating System
- Restful Web Services
- SDLC (Software Development life cycle)
- Sixth Sense Technology
- Software Reuse
- Service Oriented Architecture (SOA)
- Steganography
- Search Engine Optimization(SEO)
- Tidal Energy
- UNIX Operating System
- Virtual Private Network (VP N)
- Voice over Internet Protocol (VoIP)
- Wearable Computing
- Holographic Memory
- Data Storage On Fingernail
- Green Computing
- Universal Serial Bus (USB)
- Computer Networks
- Agile Methodology
- Parts of a Computer
- Human Area Network Technology
- Smart Dustbins for Smart Cities
- Open Graphics Library (Open Gl)
- Elastic Quotas
- Java Server Pages Standard Tag Library (Jstl)
- Mobile Computing Framework
- Zenoss Core
- Smart Pixel Arrays
- Local Multipoint Distribution Service
- Nano Computing
- Quantum Cryptography
- Anonymous Communication
- NFC and Future
- Cluster Computing
- Fog Computing
- Intel Core I9 Processor
- Python Libraries for Data Science
- Google Project Loon
- 64-Bit Computing
- Holographic Versatile Disc (Hvd)
- Virtual Instrumentation
- 3G-vs-WiFi Interferometric Modulator (IMOD)
- Compositional Adaptation
- Wireless Networked Digital Devices
- Helium Drives
- Param 10000
- Palm Operating System
- Meteor Burst Communication
- Cyberterrorism
- Location-Aware Computing
- Programming Using Mono Software
- Utility Fog
- Terrestrial Trunked Radio
- Blockchain Technology
- Exterminator
- Internet Telephony Policy in INDIA
- Voice Portals
- The Callpaper Concept
- Google cloud computing (GCP)
- Web Scraping
- Edge Computing
- Compact peripheral component interconnect
- Health Technology
- Smart Card-Based Prepaid Electricity System
- Phase Change Memory – PCM
- Biometrics in SECURE e-transaction
- Wireless Chargers (Inductive charging)
- Bluetooth V2.1
- Virtual Surgery
Also See: 200+ Paper Presentation Topics For CSE
Seminar Topics for BCA, MSC (Computer Science) and M-Tech
- Genetic Engineering
- Grid Computing
- Optical Coherence Tomography
- Google Wave
- Wireless Fidelity(WiFi)
- Online Voting System
- Digital Jewellery
- Random Access Memory (RAM)
- Quantum Computing
- Digital Cinema
- Polymer Memory
- Rover Technology
- E-Paper Technology
- Image Processing
- Online/Internet Marketing
- Google App Engine
- Computer Virus
- Virus and Anti Viruses
- Artificial Intelligence (AI)
- Gi-Fi Technology
- Mobile Jammer
- X-MAX Technology
- Space Mouse
- Diamond Chip
- Linux Operating Systems
- Web Services on Mobile Platform
- Smart Memories
- Client Server Architecture
- Biometric Authentication Technology
- Smart Fabrics
- 3D Internet
- Bio-metrics
- Dual Core Processor
- Wireless Mark-up Language (WML)
- Transactional Memory
- Visible light communication
- MIND READING COMPUTER
- Eye Tracking Technology
- Confidential Data Storage and Deletion
- USB Microphone
- Pivothead video recording sunglasses
- Slammer Worm
- XML Encryption
- Compute Unified Device Architecture (CUDA)
- Integer Fast Fourier Transform
- Extensible Stylesheet Language
- Free Space Laser Communications
- AC Performance Of Nanoelectronics
- Graphical Password Authentication
- Infinite Dimensional Vector Space
- Near Field Communication(NFC)
- Holographic versetail disc
- Efficeon Processor
- Advanced Driver Assistance System (ADAS)
- Dynamic TCP Connection Elapsing
- Symbian Mobile Operating System
- Artificial Passenger
- RESTful Web Services
- Google Chrome Laptop or Chrome Book
- Focused Web Crawling for E-Learning Content
- Tango technology
- Distributed Interactive Virtual Environment
- Place Reminder
- Encrypted Hard Disks
- Bacterio-Rhodopsin Memory
- Zettabyte file System (ZFS)
- Generic Visual Perception Processor GVPP
- Teleportation
- Digital twin (DT)
- Apache Cassandra
- Microsoft Hololens
- Digital Currency
- Intrusion Tolerance
- Finger Reader
- DNA digital data storage
- Spatial computing
- Linux Kernel 2.6
- Packet Sniffers
- Personal Digital Assistant
- Dynamic TCP Connecting Elapsing
- Hyper Transport Technology
- Multi-Protocol Label Switching (MPLS)
- Natural Language Processing
- Self Defending Networks
- Optical Burst Switching
- Pervasive Computing
Top 10 Seminar topics for CSE
1. Embedded Systems
An embedded system can be called a combination of hardware and software that created for a particular function in a system. Some major locations of an embedded system are household appliances, medical devices, industrial machines, vending machines, mobile devices, and many more.
2. Digital Signature
A digital signature can be called an electronic signature used for guaranteeing the authenticity of a digital document. It is a very useful technique that mainly used for validating authenticity along with integrating certain software, a message or a document.
3. 3D Internet
3D Internet is a next level and advanced method where two powerful technologies- the Internet and 3D graphics are combined. The main purpose of this ultra-level technique is providing realistic 3D graphics with the help of internet. Also known as Virtual Worlds, this interactive and engaging system is used by top organizations like Microsoft, Cisco, IBM, etc.
4. Generations of Computer
The generations of computers are the advancement in technology that has resulted in creating lots of computer equipment over the years. There are five generations of computers that include vacuum tubes, transistors, microprocessors, artificial intelligence, and microprocessors.
5. Blue Eyes Technology
Blue Eyes is an advanced technology that created with a mission to develop computational machines with sensory powers. There is a non-obtrusive sensing technique used by this technology with the use of latest video cameras and microphones. In simple words, it is a machine that understands the requirements of users and what he/she needs to see.
6. History of Computers
Many people believe that computers arrived in the business world in the 19 th century, but the reality is the world computer first used in 1613. The earliest form of computers was the tally stick that was just an old memory used for writing numbers and messages. Since then, there are tons of revolutions that resulted in this business that results in the creation of present-day computers.
7. Nanomaterials
Nanomaterials are the chemical materials that are processed at a minimum dimension, i.e., 1-100nm. They are developed naturally and possess physical as well as chemical properties. These materials are used in a variety of industries are cosmetics, healthcare, and sports among others.
8. Search Engine
A search engine is an online software whose main purpose is searching a database having details regarding the query of the user. There is a complete list of results matching perfectly to the query provided by this software. Google is the best example of a search engine.
9. Firewall
Firewall is security equipment whose main aim is having an eye on the incoming and outgoing traffic in the network. Furthermore, it allows or block data packets according to rules set by the security. In a simple definition, we will say it is created for creating a bridge of internet network & incoming traffic with external sources like the internet.
10. DNA Computing
DNA Computing is a method of computations with the help of biological molecules. This technique doesn’t use basic silicon chips that are quite common in other computation processes. It was invented by American Computer scientist Leonard Adleman in 1994 and displayed the way molecules can be utilized for solving computational issues.
List of Latest Technologies in Computer Science
- Plan 9 Operating System
- FeTRAM: A New Idea to Replace Flash Memory
- Cloud drive
- PON Topologies
- Digital Scent Technology
- Integrated Services Digital Network (ISDN)
- Magnetoresistive Random Access Memory
- Cryptography Technology
- Sense-Response Applications
- Blade Servers
- Revolutions Per Minute, RPM
- Secure Shell
- Ovonic Unified Memory (OUM)
- Facebook Thrift
- Chameleon Chip
- Wiimote Whiteboard
- Scrum Methodology
- liquid cooling system
- Smart Client Application Development Using .Net
- Child Safety Wearable Device
- Tizen Operating System – One OS For Everything
- Surround Systems
- Trustworthy Computing
- Design and Analysis of Algoritms
- Digital Media Broadcasting
- Socks – Protocol (Proxy Server)
- Transient Stability Assessment Using Neural Networks
- Ubiquitous Computing
- Snapdragon Processors
- Datagram Congestion Control Protocol (Dccp)
- Graph Separators
- Facebook Digital Currency – Diem (Libra)
- Design And Implementation Of A Wireless Remote
- A Plan For No Spam
- Quantum machine learning
- Pivot Vector Space Approach in Audio-Video Mixing
- Image Guided Therapy (IGT)
- Distributed Operating Systems
- Orthogonal Frequency Division Multiplplexing
- Idma – The Future Of Wireless Technology
- Shingled Magnetic Recording
- Intel MMX Technology
- Data Scraping
- Itanium Processor
- Social Impacts Of Information Technology
- Digital Video Editing
- Wolfram Alpha
- Brain computer interface
- HelioSeal Technology
- JOOMLA and CMS
- Intelligent Cache System
- Structured Cabling
- Deep Learning
- Ethical Hacking on Hacktivism
- Data-Activated Replication Object Communications (DAROC)
- Strata flash Memory
- Controller Area Network (CAN bus)
- USB Type-C – USB 3.1
You are on Page 1
PAGE 1 || PAGE 2 || PAGE3 || PAGE4
It was all about Seminar Topics for CSE with ppt and report (2024). If you feel any problem regarding these seminar topics for computer science then feel free to ask us in the comment section below. Or if you liked it then please share it with your friends on facebook and other social media websites so that they can also take help from it.
108 Comments Already
please kindly assist me with a model on network for data hiding with encryption and steganographic algorithm for my research
Hello Danjuma, Data Hiding with encryption is called steganography. https://studymafia.org/steganography-seminar-ppt-with-pdf-report/ Go to this links and get it.
i need a ppt and documentation on secure atm by image processing topic plz send meon this email i thankful of u
Its Urgent Sir,I need Pollar pillow PPT and cicret bracelet PPT And Pdf….
hello sir /mam.. i want my seminar on topic hacking.all rhe information regarding this topic n d queries thar can arise from this topic…plz send me on my email id its urgent for me sir plzz
please am writing on gps tracking system i need help
Hello Zion https://studymafia.org/global-positioning-system-seminar-pdf-report-and-ppt/ Go to this link For GPS tracking system.
I need ppt and report for topic- “a watermarking method for digital speech self-recovery”. Please send
I need the report on the topic “low power DDR4 RAM ” can anyone help me with this…. plz share
I need a seminar report and ppt based on the topic, PRISM: fine grained resource aware scheduling for map reduce .
I need seminar report on salesforce technology.#ASAP
It is just an outdated topic Alok, Please move on to another topic, I am sorry but also this will not help you in your engineering.
sir i want ppt and report on DATA CROWDSOURCING
i need ppt report on mona secure multi -owner data sharing for dynamic groups in the cloud
I need the material on the role of social network in the society
I need the material on the impact of internet and associated problems in the society.
I need 5 seminar topics based on CSE that should be very easy and should be understandble to every one easily so plzz send me notification on my gmail…
Sir please send me latest seminar topics for computer science and engineering .I need 3 seminar topics based on cse that should be very easy and easy to understand to every one and also me,please sir send me ppt and documentation please sir don’t ignore me please sir because I give seminar on 09/07/2016 please sir understand, send ppts and documentations to my mail sir.I wait for your mail sir please sir don’t ignore me sir
if you got send for me sir
please i need material for ‘career in computer science for wealth presentation’
Go to this links https://studymafia.org/light-tree-seminar-report-with-ppt-and-pdf/
Thanks for the comment, I will upload your seminar soon here.
Hello Srinivas, here is your seminar of 5G Technology with ppt and pdf report that you requested. https://studymafia.org/5g-technology-ppt-and-pdf-seminar-report-free/ Go to this link
Hello Don, We do not provide any hacking ppt and report, but yes I can provide you Ethical hacking ppt and pdf report https://studymafia.org/ethical-hacking-seminar-ppt-with-pdf-report/ Go to this link
All These are related to computer science,still there are three more pages on it. https://studymafia.org/technical-ieee-seminar-topics-for-cse-with-ppt-and-pdf-report/ https://studymafia.org/latest-seminar-topics-for-cse/ https://studymafia.org/paper-presentation-topics-for-cse/ Go to these links.
Hello Azeez,Your seminar is on the website now 🙂 Have Fun 🙂
Go to these pages, https://studymafia.org/latest-seminar-topics-for-cse/ https://studymafia.org/paper-presentation-topics-for-cse/
Hello Roopa Go to this link https://studymafia.org/technical-ieee-seminar-topics-for-cse-with-ppt-and-pdf-report/
Hey Anuradha, I will provide you very soon, please give me some time.
Nice topic, Will upload soon.
It is live on the website 🙂
Hello Likitha, Please go to this link, it is on our website 🙂 https://studymafia.org/5g-technology-ppt-and-pdf-seminar-report-free/
all These are related to computer science,still there are three more pages on it. https://studymafia.org/technical-ieee-seminar-topics-for-cse-with-ppt-and-pdf-report/ https://studymafia.org/latest-seminar-topics-for-cse/ https://studymafia.org/paper-presentation-topics-for-cse/ – See more at: https://studymafia.org/seminar-topics-for-computer-science-with-ppt-and-report/#sthash.1kXifFkV.dpuf
Hello Doris, Computer science is a part of It world so all these seminars are related to IT World. Thanks
HELLO SIR CAN I GET SEMINAR TOPICS ON WEB DESIGN. THANKS
Hey Mimari, thanks for the comment, we got your request of web designing seminar, we will upload it soon 🙂
go to this link studymafia.org/li-fi-technology-seminar-ppt-with-pdf-report/
studymafia.org/blue-eyes-technology-seminar-ppt-with-pdf-report-2/
please kindly assist me with internet without ip address a new approach in computer architecture
sir i want to market servey report from ppt seminar
Hello Lakhan, I didn’t get your topic really.
Hello Divya Mam, go to this link studymafia.org/artificial-intelligence-ai-seminar-pdf-report-and-ppt/
Hello Sir..Can i have a seminar on google self driving car tech… including something related to cps.
hey can u upload a documentation on Cassandra.
please do i find to teach me how to write a complete program to solve the problem of simoutenous equation i mean the pseudocode the flowchart and a program using FORTRAN
hey can I have ppt and pdf on femtocell
sir !! i need seminar reports and ppts on following two topics, can i get them in urgent? please.. 1.Clouddrops 2.icloud 3.touchless touchscreen atleast reply me
I need seminar reports n ppt on following two topics 1. Augmented reality 2. Head maounted displays
go to this link https://studymafia.org/augmented-reality-seminar-and-ppt-with-pdf-report/
plsssssss provide plant leaf diesease identification system for android
Please provide ppt and report on “web mining algorithm using link analysis”
Please Mr Sumit Thakur i need project materials and software on Security Information System (for national civil defense) asap, please please please
It will be updated soon 🙂
go for google wave https://studymafia.org/google-wave-seminar-ppt-and-pdf-report/ or Search engine optimization https://studymafia.org/seo-seminar-ppt-with-pdf-report/
Thank you Mr.Sumit Thakur. I recently heard about Screenless displays. I think its not the latest one. What do you say?? if you have ppt and report of it mail me..
Hey….i want a ppt on deepweb and dark web urgntly with pdf report
I’ve been following your site for quite some time now and I must confess, you’re doing an amazing job here.
please I need three good project topic and possible materials on computer science.
GO to this link https://studymafia.org/firewall-seminar-report-with-ppt-and-pdf/
go to this link https://studymafia.org/firewall-seminar-report-with-ppt-and-pdf/
Hello Avni, Go to this link https://studymafia.org/computer-networks-seminar-pdf-report-ppt/
I need ppt and report on speed breakers and ditches
Hello Mr.Thakur I wanted ppt on data coloring. could you please provide it?
hello sir, I request a ppt and report for the topic “Millimeter wave wireless communications for IOT cloud supported autonomous vehicles:overview, design and challenges”
please send link to download seminar report and ppt for “understanding smartphone sensor and app data for enhancing security of secret questions”
Sir, pls i need ppt and report of “eye movement based human computer interaction” .its found in this site .. it’s very urgent
Go to this link https://studymafia.org/digital-signature-seminar-and-ppt-with-pdf-report/
Sir I need to Final Year IT Btech project report on website ‘Digital India Village Development’
sir plz provide me report on olap(online analytical processing)
Sir please i need a report for Interactive emotional lighting using physiological signals.
hello !!! please i am computer science student final year HERE is MY PROJECT TOPIC #ORTHOPAEDIC EXPERT SYSTEM i need a little knowledge about it someone help please
We are currently not working on projects.
Hello sir…i am a mca student..pls suggest me latest seminar topic and pls send me the seminar report on “Internet of BioNano things”.Send me on this email
Hello Jyo, I didn’t find anything related to your topic.
Hello Micheal, You seminar will be on our website soon.
Hello Pratyusha, Good topic, will be updated soon.
GO to this link https://studymafia.org/speech-recognition-seminar-ppt-and-pdf-report/
Hello Mam, Here are the links https://studymafia.org/4g-technology-seminar-and-ppt-with-pdf-report/ https://studymafia.org/5g-technology-ppt-and-pdf-seminar-report-free/
Will be updated soon
Sir,I want seminar report and PPT of the topic multi-touch interaction.
Hello sir!Could u please send me a ppt for am image based hair modeling and dynamic simulation method
I seriously need seminar topics for education in computer please I would be glad if my request is granted please send to my mail.
hello please i also need a topic about fog computing, IoT or Mikrotic please help me
hello Final Report for Foreign Students
We invite submissions of high quality and origin reports describing fully developed results or on-going foundational and applied work on the following topics of advanced algorithms in Natural Language Processing: in this topic ( Literature survey of short text similarity.) Reporting requirements: (1) Reports must not less 5 pages and exceed 8 pages, using IEEE two-column template. All papers should be in Adobe portable document format (PDF) format. Authors should submit their paper via electronic submission system. All papers selected for this conference are peer-reviewed and will be published in the regular conference proceedings by the IEEE Computer Society Press. Submissions must not be published or submitted for another conference. The best quality papers presented in the conference will be selected for journal special issues by creating an extended version. (2) No copy of any sentences from published papers. You may get zero score for some detected copy sentence.
please i need seminar paper on fog computing with go comparative study with full report
Hello Sir, Can you please help me out with presentation and report on the topic “Blind Aid Stick:Hurdle Recognition,Simulated Perception,Android Integrated Voice Based Cooperation via GPS Along with Panic Alert System”.
Hello,we have been ask to find research papers for certain topics regarding seminar presentation and then do comparative analysis.so please help with the topic “AI in control systems”.
Is there any topics related to routing. Please suggest me if there are.
hello sir please i need your help on a seminar topic Examination biometric verification case study of WAEC… thanks for understanding
Sir pls I need the ppt and report of review cash receipt generating system; challenges and merit
Hello sir please provide ppt and report on following two topics I get them in urgent please digital library mobile based network monitory system
please sir i need a ppt about modal logic in computer science
introduction of modal logic history of modal logic syntax of modal logic application of modal logic proof of modal logic
i need material on opportunities network and software defined network. please send as soon as possible. thank you sir
Please I need a full report on entrepredemic, please help me with it
I need a ppt on Expert Addmision System with flowchart.
please kindly help me with a proper write up on this seminar topic “I CLOUD”, Thank you for considering me.
Hello All my friends, I am not able to answer each your comment, so please come to our facebook fan page https://www.facebook.com/studymafia1/ where we can discuss your problems and can take new seminar request directly 🙂
sir , i need the ppt on topic:”Securing Mobile Healthcare Data: A Smart Card Based Cancelable Finger-Vein Bio-Cryptosystem” .
which is from ieee access ,and some links of videos to understand it .
plz replay me as soon as possible as im having the seminar with in this weak ,
Sir I need latest IEEE published papers seminar topics on any domain in cse
Sir! I need PPT and Documentation on this below Title. “Securing data with blockchain and Ai” So, please send me sir!
I want ppt and documentation on the topic CLOUD ROBOTICS
Sir could you please give me the PPT and Report for the topic Web Vulnerability Detection ,The Case of Cross-Site Request Forgery could u please help me send me the link where i can find ppt for this topic!!!
Hello Sir,thanks for the good work you’re doing.
Please I need seminar on “Security in Cloud Computing” thank you
U r doing a great work it helps most of the student. Sir I want Air cargo tracking system ppt and synopsis can u plz share the link where we can get ppt .
Thank you for your help, i really appreciate and acknowledge your effort. But am doing my own seminar on “Digital Currency Diffusion Policy in Nigeria” pls help. Thank you
Please I need something on Networking tools and Cable Management
I need ppt on blockchain
I want Q learning based teaching-learning optimization for distributed two stage hybrid flow shop scheduling with fuzzy processing time ppt with report for technical presentation please send me please I need it urgent pls
i need project report and presentation of ONLINE FOOD ORDERING SYSTEM.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Computer Science Essay Examples

Explore 15+ Brilliant Computer Science Essay Examples: Tips Included
Published on: May 5, 2023
Last updated on: Jan 30, 2024

Share this article
Do you struggle with writing computer science essays that get you the grades you deserve?
If so, you're not alone!
Crafting a top-notch essay can be a daunting task, but it's crucial to your success in the field of computer science.
For that, CollegeEssay.org has a solution for you!
In this comprehensive guide, we'll provide you with inspiring examples of computer science essays. You'll learn everything you need to know to write effective and compelling essays that impress your professors and get you the grades you deserve.
So, let's dive in and discover the secrets to writing amazing computer science essays!
On This Page On This Page -->
Computer Science Essays: Understanding the Basics
A computer science essay is a piece of writing that explores a topic related to computer science. It may take different forms, such as an argumentative essay, a research paper, a case study, or a reflection paper.
Just like any other essay, it should be well-researched, clear, concise, and effectively communicate the writer's ideas and arguments.
Computer essay examples encompass a wide range of topics and types, providing students with a diverse set of writing opportunities.
Here, we will explore some common types of computer science essays:
Middle School Computer Science Essay Example
College Essay Example Computer Science
University Computer Science Essay Example
Computer Science Extended Essay Example
Uiuc Computer Science Essay Example [
Computer Science Essay Examples For Different Fields
Computer science is a broad field that encompasses many different areas of study. For that, given below are some examples of computer science essays for some of the most popular fields within the discipline.
By exploring these examples, you can gain insight into the different types of essays within this field.
College Application Essay Examples Computer Science
The Future of Computers Technology
Historical Development of Computer Science
Young Children and Technology: Building Computer Literacy
Computer Science And Artificial Intelligence
Looking for more examples of computer science essays? Given below are some additional examples of computer science essays for readers to explore and gain further inspiration from.
Computer Science â My Choice for Future Career
My Motivation to Pursue Undergraduate Studies in Computer Engineering
Abstract Computer Science
Computer Science Personal Statement Example
Sop For Computer Science
Computer Science Essay Topics
There are countless computer science essay topics to choose from, so it can be challenging to narrow down your options.
However, the key is to choose a topic that you are passionate about and that aligns with your assignment requirements.
Here are ten examples of computer science essay topics to get you started:
- The impact of artificial intelligence on society: benefits and drawbacks
- Cybersecurity measures in cloud computing systems
- The Ethics of big data: privacy, bias, and Transparency
- The future of quantum computing: possibilities and challenges
- The Role of computer hardware in Healthcare: current applications and potential innovations
- Programming languages: a comparative analysis of their strengths and weaknesses
- The use of machine learning in predicting human behavior
- The challenges and solutions for developing secure and reliable software
- The Role of blockchain technology in improving supply chain management
- The use of data analytics in business decision-making.

Paper Due? Why Suffer? That's our Job!
Tips to Write an Effective Computer Science Essay
Writing an effective computer science essay requires a combination of technical expertise and strong writing skills. Here are some tips to help you craft a compelling and well-written essay:
Understand the Requirements: Make sure you understand the assignment requirements, including the essay type, format, and length.
- Choose a Topic: Select a topic that you are passionate about and that aligns with your assignment requirements.
- Create an Outline: Develop a clear and organized outline that highlights the main points and subtopics of your essay.
- Use Appropriate Language and Tone: Use technical terms and language when appropriate. But ensure your writing is clear, concise, and accessible to your target audience.
- Provide Evidence: Use relevant and credible evidence to support your claims, and ensure you cite your sources correctly.
- Edit and Proofread Your Essay: Review your essay for clarity, coherence, and accuracy. Check for grammatical errors, spelling mistakes, and formatting issues.
By following these tips, you can improve the quality of your computer science essay and increase your chances of success.
In conclusion, writing a computer science essay can be a challenging yet rewarding experience.
It allows you to showcase your knowledge and skills within the field and develop your writing and critical thinking abilities. By following the examples provided in this blog, you can create an effective computer science essay, which will meet your requirements.
If you find yourself struggling with the writing process, consider seeking essay writing help online from CollegeEssay.org.
Our AI essay writer can provide guidance and support in crafting a top-notch computer science essay.
So, what are you waiting for? Hire our computer science essay writing service today!
Nova A. (Literature, Marketing)
As a Digital Content Strategist, Nova Allison has eight years of experience in writing both technical and scientific content. With a focus on developing online content plans that engage audiences, Nova strives to write pieces that are not only informative but captivating as well.
Paper Due? Why Suffer? That’s our Job!

Legal & Policies
- Privacy Policy
- Cookies Policy
- Terms of Use
- Refunds & Cancellations
- Our Writers
- Success Stories
- Our Guarantees
- Affiliate Program
- Referral Program
- AI Essay Writer
Disclaimer: All client orders are completed by our team of highly qualified human writers. The essays and papers provided by us are not to be used for submission but rather as learning models only.

IMAGES
VIDEO
COMMENTS
The perception of danger in different cultures. The origins of bipolar disorder through the prism of domestic violence. Covid-19 and related anxiety cases among college students. The dangers of advertisements on children's TV networks. The negative influence of Instagram and distorted body image.
Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you've landed on this post, chances are you're looking for a computer science-related research topic, but aren't sure where to start.Here, we'll explore a variety of CompSci & IT-related research ideas and topic thought-starters ...
Computer security and forensics. Communication and computation limits. Environments and programming languages. Computer systems security and support for the digital democracy. This list comprises hot topics in computer science. Pick one of them and research it extensively to write a brilliant academic paper or essay.
Available for single-semester IW and senior thesis advising, 2023-2024. Research Areas: Human-Computer Interaction (HCI), Augmented Reality (AR), and Spatial Computing. Independent Research Topics: Input techniques for on-the-go interaction (e.g., eye-gaze, microgestures, voice) with a focus on uncertainty, disambiguation, and privacy.
Computer science research topics can be divided into several categories, such as artificial intelligence, big data and data science, human-computer interaction, security and privacy, and software engineering. If you are a student or researcher looking for computer research paper topics. In that case, this article provides some suggestions on ...
1) Best Computer Science Project Topics. a) Face detection. b) Crime rate prediction. c) E-authentication system. d) Online auction system. e) Evaluation of academic performance. f) Symbol recognition. g) Weather forecasting application. h) Public News Droid.
This thought-provoking volume offers an update on current international IPR negotiations and includes case studies on software, computer chips, optoelectronics, and biotechnology—areas characterized by high development cost and easy reproducibility. The volume covers these and other issues:
Higher-level students must write 3 papers. The case study is the third paper. Every year, the case study discusses a different topic. Students must become very very familiar with the case study. The IB recommends spending about a year studying this guide. This page will help you organize and understand the 2020 case study .
Keywords: applied statistics, data science, statistical thinking, case studies, education, computing 1Introduction A major challenge in the practice of teaching data sci- ... example topics covered in all case studies (TableS1). 1. Motivation. Each case study begins with a motivating data visualization. This idea originated from Dr. Mine
by Topic; by Level; by Type; Daily Do Lesson Plans; Free Resources; Blog; ... NCCSTS Case Studies; Case Studies Computer Science Narrow your search. Bioinformatics ... Dyan Anore, Basma Galal, Shawn Xiong. Case Study. Is p53 a Smoking Gun? By Michèle I. Shuster, Joann Mudge, Meghan Hill, Katelynn James, Gabriella A. DeFrancesco, Maria P ...
Conclusion. Computer science is a field of limitless potential and continuous growth. It underpins the technology that powers our world and shapes the future. From the fundamentals of algorithms and data structures to the cutting-edge technologies of AI, quantum computing, and blockchain, computer science is a dynamic and ever-evolving discipline.
The success of the Hertz cases was unprecedented for the top 40 list. Usually, cases take a number of years to gain popularity, but the Hertz cases claimed top spots in their first year of release. Hertz (A) also became the first 'cooked' case to top the annual review, as all of the other winners had been web-based 'raw' cases.
Computer Science Research Topics. Computer Science Research Topics are as follows: Using machine learning to detect and prevent cyber attacks. Developing algorithms for optimized resource allocation in cloud computing. Investigating the use of blockchain technology for secure and decentralized data storage. Developing intelligent chatbots for ...
Applications of computer science in medicine. Developments in artificial intelligence in image processing. Discuss cryptography and its applications. Discuss methods of ransomware prevention. Applications of Big Data in the banking industry. Challenges of cloud storage services in 2023.
Call for Department Articles . CiSE's newest department explores how findings in fundamental research in computer, computational, and data science translate to technologies, solutions, or practice for the benefit of science, engineering, and society.Specifically, each department article will highlight impactful translational research examples in which research has successfully moved from the ...
Fortunately, we have some AP computer science topics that can help you write a great paper in no time: Discuss computer-assisted education. Novel emerging technologies in computer science. Open-source vs. proprietary software. Natural language processing real life applications. Evaluating 3D models effectively.
4 samples of this type. WowEssays.com paper writer service proudly presents to you a free directory of Computer Science Case Studies aimed to help struggling students tackle their writing challenges. In a practical sense, each Computer Science Case Study sample presented here may be a guide that walks you through the crucial stages of the ...
It is not so easy to get your hands on the best research topics for computer science; spend some time and read about the following mind-boggling ideas before selecting one. 1. Integrated Blockchain and Edge Computing Systems: A Survey, Some Research Issues, and Challenges.
In this article, you will learn 12 Interesting Computer Science Project Ideas & Topics For Beginners (2024). Face detection. Online auction system. Evaluation of academic performance. e-Authentication system. Cursor movement on object motion. Crime rate prediction. Android battery saver system. Symbol recognition.
Secondly, select a topic that is challenging but not too complex, as you want to be able to assess the candidate's ability to solve the problem without overwhelming them. Lastly, choose a topic that can showcase the candidate's technical expertise. Top Case Study Topics in Computer Science. To help you get started, we have compiled a list ...
Words: 354 Pages: 2. Data Quality and Data Acquisition. As noted, the collected data will mainly be used by three players,…. Words: 290 Pages: 2. Data lifecycle Case Study. Data lifecycle can be described using one major attempt. Data lifecycle composes…. Words: 777 Pages: 3. Case Study on Chevron.
Technical Seminar Topics for CSE with Abstract. 3D Printing. 3D Printing is the process to develop a 3D printed object with the help of additive processes. Here, there are three-dimensional objects created by a 3D printer using depositing materials as per the digital model available on the system.
Here are ten examples of computer science essay topics to get you started: The impact of artificial intelligence on society: benefits and drawbacks. Cybersecurity measures in cloud computing systems. The Ethics of big data: privacy, bias, and Transparency. The future of quantum computing: possibilities and challenges.