
Research Topics & Ideas: Healthcare
100+ Healthcare Research Topic Ideas To Fast-Track Your Project

Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you’ve landed on this post, chances are you’re looking for a healthcare-related research topic , but aren’t sure where to start. Here, we’ll explore a variety of healthcare-related research ideas and topic thought-starters across a range of healthcare fields, including allopathic and alternative medicine, dentistry, physical therapy, optometry, pharmacology and public health.
NB – This is just the start…
The topic ideation and evaluation process has multiple steps . In this post, we’ll kickstart the process by sharing some research topic ideas within the healthcare domain. This is the starting point, but to develop a well-defined research topic, you’ll need to identify a clear and convincing research gap , along with a well-justified plan of action to fill that gap.
If you’re new to the oftentimes perplexing world of research, or if this is your first time undertaking a formal academic research project, be sure to check out our free dissertation mini-course. In it, we cover the process of writing a dissertation or thesis from start to end. Be sure to also sign up for our free webinar that explores how to find a high-quality research topic.
Overview: Healthcare Research Topics
- Allopathic medicine
- Alternative /complementary medicine
- Veterinary medicine
- Physical therapy/ rehab
- Optometry and ophthalmology
- Pharmacy and pharmacology
- Public health
- Examples of healthcare-related dissertations
Allopathic (Conventional) Medicine
- The effectiveness of telemedicine in remote elderly patient care
- The impact of stress on the immune system of cancer patients
- The effects of a plant-based diet on chronic diseases such as diabetes
- The use of AI in early cancer diagnosis and treatment
- The role of the gut microbiome in mental health conditions such as depression and anxiety
- The efficacy of mindfulness meditation in reducing chronic pain: A systematic review
- The benefits and drawbacks of electronic health records in a developing country
- The effects of environmental pollution on breast milk quality
- The use of personalized medicine in treating genetic disorders
- The impact of social determinants of health on chronic diseases in Asia
- The role of high-intensity interval training in improving cardiovascular health
- The efficacy of using probiotics for gut health in pregnant women
- The impact of poor sleep on the treatment of chronic illnesses
- The role of inflammation in the development of chronic diseases such as lupus
- The effectiveness of physiotherapy in pain control post-surgery

Topics & Ideas: Alternative Medicine
- The benefits of herbal medicine in treating young asthma patients
- The use of acupuncture in treating infertility in women over 40 years of age
- The effectiveness of homoeopathy in treating mental health disorders: A systematic review
- The role of aromatherapy in reducing stress and anxiety post-surgery
- The impact of mindfulness meditation on reducing high blood pressure
- The use of chiropractic therapy in treating back pain of pregnant women
- The efficacy of traditional Chinese medicine such as Shun-Qi-Tong-Xie (SQTX) in treating digestive disorders in China
- The impact of yoga on physical and mental health in adolescents
- The benefits of hydrotherapy in treating musculoskeletal disorders such as tendinitis
- The role of Reiki in promoting healing and relaxation post birth
- The effectiveness of naturopathy in treating skin conditions such as eczema
- The use of deep tissue massage therapy in reducing chronic pain in amputees
- The impact of tai chi on the treatment of anxiety and depression
- The benefits of reflexology in treating stress, anxiety and chronic fatigue
- The role of acupuncture in the prophylactic management of headaches and migraines
Topics & Ideas: Dentistry
- The impact of sugar consumption on the oral health of infants
- The use of digital dentistry in improving patient care: A systematic review
- The efficacy of orthodontic treatments in correcting bite problems in adults
- The role of dental hygiene in preventing gum disease in patients with dental bridges
- The impact of smoking on oral health and tobacco cessation support from UK dentists
- The benefits of dental implants in restoring missing teeth in adolescents
- The use of lasers in dental procedures such as root canals
- The efficacy of root canal treatment using high-frequency electric pulses in saving infected teeth
- The role of fluoride in promoting remineralization and slowing down demineralization
- The impact of stress-induced reflux on oral health
- The benefits of dental crowns in restoring damaged teeth in elderly patients
- The use of sedation dentistry in managing dental anxiety in children
- The efficacy of teeth whitening treatments in improving dental aesthetics in patients with braces
- The role of orthodontic appliances in improving well-being
- The impact of periodontal disease on overall health and chronic illnesses

Tops & Ideas: Veterinary Medicine
- The impact of nutrition on broiler chicken production
- The role of vaccines in disease prevention in horses
- The importance of parasite control in animal health in piggeries
- The impact of animal behaviour on welfare in the dairy industry
- The effects of environmental pollution on the health of cattle
- The role of veterinary technology such as MRI in animal care
- The importance of pain management in post-surgery health outcomes
- The impact of genetics on animal health and disease in layer chickens
- The effectiveness of alternative therapies in veterinary medicine: A systematic review
- The role of veterinary medicine in public health: A case study of the COVID-19 pandemic
- The impact of climate change on animal health and infectious diseases in animals
- The importance of animal welfare in veterinary medicine and sustainable agriculture
- The effects of the human-animal bond on canine health
- The role of veterinary medicine in conservation efforts: A case study of Rhinoceros poaching in Africa
- The impact of veterinary research of new vaccines on animal health
Topics & Ideas: Physical Therapy/Rehab
- The efficacy of aquatic therapy in improving joint mobility and strength in polio patients
- The impact of telerehabilitation on patient outcomes in Germany
- The effect of kinesiotaping on reducing knee pain and improving function in individuals with chronic pain
- A comparison of manual therapy and yoga exercise therapy in the management of low back pain
- The use of wearable technology in physical rehabilitation and the impact on patient adherence to a rehabilitation plan
- The impact of mindfulness-based interventions in physical therapy in adolescents
- The effects of resistance training on individuals with Parkinson’s disease
- The role of hydrotherapy in the management of fibromyalgia
- The impact of cognitive-behavioural therapy in physical rehabilitation for individuals with chronic pain
- The use of virtual reality in physical rehabilitation of sports injuries
- The effects of electrical stimulation on muscle function and strength in athletes
- The role of physical therapy in the management of stroke recovery: A systematic review
- The impact of pilates on mental health in individuals with depression
- The use of thermal modalities in physical therapy and its effectiveness in reducing pain and inflammation
- The effect of strength training on balance and gait in elderly patients
Topics & Ideas: Optometry & Opthalmology
- The impact of screen time on the vision and ocular health of children under the age of 5
- The effects of blue light exposure from digital devices on ocular health
- The role of dietary interventions, such as the intake of whole grains, in the management of age-related macular degeneration
- The use of telemedicine in optometry and ophthalmology in the UK
- The impact of myopia control interventions on African American children’s vision
- The use of contact lenses in the management of dry eye syndrome: different treatment options
- The effects of visual rehabilitation in individuals with traumatic brain injury
- The role of low vision rehabilitation in individuals with age-related vision loss: challenges and solutions
- The impact of environmental air pollution on ocular health
- The effectiveness of orthokeratology in myopia control compared to contact lenses
- The role of dietary supplements, such as omega-3 fatty acids, in ocular health
- The effects of ultraviolet radiation exposure from tanning beds on ocular health
- The impact of computer vision syndrome on long-term visual function
- The use of novel diagnostic tools in optometry and ophthalmology in developing countries
- The effects of virtual reality on visual perception and ocular health: an examination of dry eye syndrome and neurologic symptoms
Topics & Ideas: Pharmacy & Pharmacology
- The impact of medication adherence on patient outcomes in cystic fibrosis
- The use of personalized medicine in the management of chronic diseases such as Alzheimer’s disease
- The effects of pharmacogenomics on drug response and toxicity in cancer patients
- The role of pharmacists in the management of chronic pain in primary care
- The impact of drug-drug interactions on patient mental health outcomes
- The use of telepharmacy in healthcare: Present status and future potential
- The effects of herbal and dietary supplements on drug efficacy and toxicity
- The role of pharmacists in the management of type 1 diabetes
- The impact of medication errors on patient outcomes and satisfaction
- The use of technology in medication management in the USA
- The effects of smoking on drug metabolism and pharmacokinetics: A case study of clozapine
- Leveraging the role of pharmacists in preventing and managing opioid use disorder
- The impact of the opioid epidemic on public health in a developing country
- The use of biosimilars in the management of the skin condition psoriasis
- The effects of the Affordable Care Act on medication utilization and patient outcomes in African Americans
Topics & Ideas: Public Health
- The impact of the built environment and urbanisation on physical activity and obesity
- The effects of food insecurity on health outcomes in Zimbabwe
- The role of community-based participatory research in addressing health disparities
- The impact of social determinants of health, such as racism, on population health
- The effects of heat waves on public health
- The role of telehealth in addressing healthcare access and equity in South America
- The impact of gun violence on public health in South Africa
- The effects of chlorofluorocarbons air pollution on respiratory health
- The role of public health interventions in reducing health disparities in the USA
- The impact of the United States Affordable Care Act on access to healthcare and health outcomes
- The effects of water insecurity on health outcomes in the Middle East
- The role of community health workers in addressing healthcare access and equity in low-income countries
- The impact of mass incarceration on public health and behavioural health of a community
- The effects of floods on public health and healthcare systems
- The role of social media in public health communication and behaviour change in adolescents
Examples: Healthcare Dissertation & Theses
While the ideas we’ve presented above are a decent starting point for finding a healthcare-related research topic, they are fairly generic and non-specific. So, it helps to look at actual dissertations and theses to see how this all comes together.
Below, we’ve included a selection of research projects from various healthcare-related degree programs to help refine your thinking. These are actual dissertations and theses, written as part of Master’s and PhD-level programs, so they can provide some useful insight as to what a research topic looks like in practice.
- Improving Follow-Up Care for Homeless Populations in North County San Diego (Sanchez, 2021)
- On the Incentives of Medicare’s Hospital Reimbursement and an Examination of Exchangeability (Elzinga, 2016)
- Managing the healthcare crisis: the career narratives of nurses (Krueger, 2021)
- Methods for preventing central line-associated bloodstream infection in pediatric haematology-oncology patients: A systematic literature review (Balkan, 2020)
- Farms in Healthcare: Enhancing Knowledge, Sharing, and Collaboration (Garramone, 2019)
- When machine learning meets healthcare: towards knowledge incorporation in multimodal healthcare analytics (Yuan, 2020)
- Integrated behavioural healthcare: The future of rural mental health (Fox, 2019)
- Healthcare service use patterns among autistic adults: A systematic review with narrative synthesis (Gilmore, 2021)
- Mindfulness-Based Interventions: Combatting Burnout and Compassionate Fatigue among Mental Health Caregivers (Lundquist, 2022)
- Transgender and gender-diverse people’s perceptions of gender-inclusive healthcare access and associated hope for the future (Wille, 2021)
- Efficient Neural Network Synthesis and Its Application in Smart Healthcare (Hassantabar, 2022)
- The Experience of Female Veterans and Health-Seeking Behaviors (Switzer, 2022)
- Machine learning applications towards risk prediction and cost forecasting in healthcare (Singh, 2022)
- Does Variation in the Nursing Home Inspection Process Explain Disparity in Regulatory Outcomes? (Fox, 2020)
Looking at these titles, you can probably pick up that the research topics here are quite specific and narrowly-focused , compared to the generic ones presented earlier. This is an important thing to keep in mind as you develop your own research topic. That is to say, to create a top-notch research topic, you must be precise and target a specific context with specific variables of interest . In other words, you need to identify a clear, well-justified research gap.
Need more help?
If you’re still feeling a bit unsure about how to find a research topic for your healthcare dissertation or thesis, check out Topic Kickstarter service below.

You Might Also Like:

15 Comments
I need topics that will match the Msc program am running in healthcare research please
Hello Mabel,
I can help you with a good topic, kindly provide your email let’s have a good discussion on this.
Can you provide some research topics and ideas on Immunology?
Thank you to create new knowledge on research problem verse research topic
Help on problem statement on teen pregnancy
This post might be useful: https://gradcoach.com/research-problem-statement/
can you provide me with a research topic on healthcare related topics to a qqi level 5 student
Please can someone help me with research topics in public health ?
Hello I have requirement of Health related latest research issue/topics for my social media speeches. If possible pls share health issues , diagnosis, treatment.
I would like a topic thought around first-line support for Gender-Based Violence for survivors or one related to prevention of Gender-Based Violence
Please can I be helped with a master’s research topic in either chemical pathology or hematology or immunology? thanks
Can u please provide me with a research topic on occupational health and safety at the health sector
Good day kindly help provide me with Ph.D. Public health topics on Reproductive and Maternal Health, interventional studies on Health Education
may you assist me with a good easy healthcare administration study topic
May you assist me in finding a research topic on nutrition,physical activity and obesity. On the impact on children
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
Advertisement
Keeping pace with the healthcare transformation: a literature review and research agenda for a new decade of health information systems research
- Research Paper
- Open access
- Published: 17 July 2021
- Volume 31 , pages 901–921, ( 2021 )
Cite this article
You have full access to this open access article

- Nadine Ostern ORCID: orcid.org/0000-0003-3867-3385 1 ,
- Guido Perscheid 2 ,
- Caroline Reelitz 2 &
- Jürgen Moormann 2
7122 Accesses
9 Citations
1 Altmetric
Explore all metrics
A Correction to this article was published on 20 December 2021
This article has been updated
Accelerated by the coronavirus disease 2019 (Covid-19) pandemic, major and lasting changes are occuring in healthcare structures, impacting people's experiences and value creation in all aspects of their lives. Information systems (IS) research can support analysing and anticipating resulting effects.
The purpose of this study is to examine in what areas health information systems (HIS) researchers can assess changes in healthcare structures and, thus, be prepared to shape future developments.
A hermeneutic framework is applied to conduct a literature review and to identify the contributions that IS research makes in analysing and advancing the healthcare industry.
We draw an complexity theory by borrowing the concept of 'zooming-in and out', which provides us with a overview of the current, broad body of research in the HIS field. As a result of analysing almost 500 papers, we discovered various shortcomings of current HIS research.
Contribution
We derive future pathways and develop a research agenda that realigns IS research with the transformation of the healthcare industry already under way.
Similar content being viewed by others

Afterword: Moving Forward in Healthcare Systems in the Twenty-First Century

From Substantialist to Process Metaphysics – Exploring Shifts in IS Research

Background Literature on the Adoption of Health Information Technologies
Avoid common mistakes on your manuscript.
Introduction
Particularly since the last decade, IT has opened up new opportunities for ‘ehealth’ through telemedicine and remote patient monitoring, alongside potential improvements in the cost-effectiveness and accessibility of health care (Chiasson & Davidson, 2004 ). Accordingly, health information systems (HIS) research has come to focus on how healthcare organizations invest in and then assimilate HIS, looking in particular at the impact of digitalization on healthcare costs, healthcare quality, and patient privacy (Chen et al., 2019 ; Park, 2016 ).
Less attention has been paid to issues such as mobile health, health information interchange, digital health communities, and services that change customer expectations and may lead to major disruptions (Chen et al., 2019 ; Park, 2016 ). These topics, however, are becoming increasingly important due to the penetration of the user and health market by external players, especially tech companies, providing services such as fitness trackers, and surveillance software for patient monitoring in hospitals (Gantori et al., 2020 ). Modern IT, thus, becomes a catalyst to provide greater operational efficiency, offering new possibilities for tech companies to build new health-centred business models and services (Park, 2016 ).
The ways in which tech companies are entering the healthcare industry can be seen amid the spread of coronavirus disease 2019 (Covid-19), which is pushing healthcare systems to the edge of their capacities (Worldbank, 2020 ). In this extraordinary condition, the pandemic has provided an additional opportunity for tech companies that were hitherto not active or not allowed to enter the healthcare industry (Gantori et al., 2020 ).
We are currently seeing how entering the healthcare market is actually taking place, particularly in the USA, where tech companies are increasingly offering services to help address some of the problems associated with Covid-19. Google’s subsidiary Verily, for instance, facilitates the automation of coronavirus symptom screening and provides actionable, up-to-date information that supports community-based decision-making (Landi, 2020 ). Although the collaboration with Verily assists the US government in tracking cases to identify the spread of the virus, it is reasonable to suggest that Verily probably did not launch the screening tool out of altruism. In fact, to receive preliminary screening results via the Verily app, citizens have to log into their personal Google account (Greenwood, 2020 ). This allows Verily to gain immense value by aggregating huge, structured data sets and analyse them to come up with new health services, such as better tools for disease detection, new data infrastructures, and insurance offerings that – for better or for worse – may outplay current healthcare providers and even disrupt whole healthcare ecosystems (CB Insights, 2018 ). Similarly, Amazon has started to provide cloud space through Amazon Web Services to store health surveillance data for the Australian government’s tracing app (Tillett, 2020 ), and Amazon Care, a division initially responsible for handling internal staff care needs, now cooperates with the Bill and Melinda Gates Foundation to distribute Covid-19 testing kits to US residents (Lee & Nilsson, 2020 ).
Looking at information systems (IS) researchers’ previous assessments of state-of-the-art healthcare-related IS literature reveals that most scholars seem to have little or no concern for the beginning of those potentially long-lasting changes that are occurring in the healthcare industry (Chen et al., 2019 ). This is worrying, considering that it is already apparent that the years ahead will be marked by economic volatility and social upheaval as well as direct and indirect health consequences, including sweeping transformations in many of the world’s healthcare systems.
While it is clear that recent developments and the push of tech and platform companies into the healthcare sector can significantly improve the quality of life for billions of people around the world, it will be accompanied by serious challenges for healthcare industries, governments, and individuals (Park, 2016 ). Technological advances are, for instance, giving rise to a plethora of smart, connected products and services, combining sensors, software, data, analytics, and connectivity in all kinds of ways, which in turns leads to a restructuring of health industry boundaries and the empowerment of novel actors, especially tech and platform companies such as IBM, Google, and Amazon (Park, 2016 ).
Observing those changes, we need to develop a general understanding of long-term trends such as digitalization and blurring industry boundaries. As the pandemic is only an amplifier of longer-lasting trends, it is likely that the consequences and exogenous effects on the healthcare industry will go far beyond the time of the current pandemic. Given these observations, we wonder whether the IS research domain is ready to capture, understand, and accompany these developments, which require a holistic view of the healthcare industry, its structures, and the interdependencies between incumbents and new entrants. Thus, we argue that it is now time to develop a more comprehensive understanding of these developments and to determine the role that IS research can play by asking: How can we prepare HIS research to capture and anticipate current developments in the healthcare industry?
To find answers to this question, our paper provides a literature overview of HIS research by ‘zooming in and zooming out’ (Gaskin et al., 2014 ) and by drawing on complexity theory (Benbya et al., 2020 ). Since a healthcare system, like the industry as a whole, can be understood as a complex, digital socio-technical system (Kernick & Mitchell, 2009 ; Therrien et al., 2017 ), zooming in and zooming out is a way to view, capture, and theorize the causes, dynamics, and consequences of a system’s complexity. Complex systems are characterized by adaptiveness, openness (Cilliers, 2001 ), and the diversity of actors and their mutual dependency in the system, meaning that outcomes and research span various levels within these systems, although the boundaries of socio-technical systems are elusive. Assuming that HIS research is just as complex as the socio-technical system investigated, we first zoom in, focusing on concrete research outcomes across levels (i.e., what we can actually observe). Zooming in is followed by zooming out, which means abstracting from the concrete level and embracing the strengths and disparities of overall HIS research on a higher level in which concrete research outcomes are embedded (Benbya et al., 2020 ). Using this approach, we can capture and understand the complexity of HIS research without losing sight of concrete research issues and topics that drive research in this field.
To do this, we chose a hermeneutic framework to guide us in a thorough review and interpretation of HIS literature and lead us to the following overarching observations: (i) The literature review determines the unique contribution that IS research plays in analysing and advancing the healthcare industry. However, it also shows that we are hardly prepared to take up current developments and anticipate their consequences. (ii) The reason for this unpreparedness is that we currently neglect the ecosystem perspective and thus ignore holistic approaches to resolve the striking number of interrelated issues in HIS research. (iii) Based on the unique insights of this literature review, our paper provides a research agenda in which we use complexity theory to discuss the consequences of current developments. This theory assists IS researchers not only to better understand developments and implications thereof for the healthcare industry (and thus HIS research) but also to create a meaningful impact on the future of this industry. Since we have limited our research explicitly to the IS domain, our results may not be generally applicable to other healthcare research domains and we do not claim to provide an overview of the literature in the field of HIS research. However, while IS researchers cannot solve the pandemic directly, preparing them by providing a new research agenda will support them in developing concepts and applications, thereby helping them to overcome the negative effects of the pandemic. In our opinion, it is particularly important that IS research, and especially HIS-related research, obtains a deeper understanding of the needed transformation that is caused by digitalization and the emergence of new players catalysed by the current pandemic.
The remainder of this paper is structured as follows. The next section is concerned with the hermeneutic framework used to conduct the systematic literature review. After explaining the hermeneutic approach and the research steps, we elaborate on the key findings by zooming in; that is, we focus on the key results that emerge from analysing and interpreting the literature for each of the phases defined in the course of the literature sorting process. We then concentrate on zooming out, emphasizing the patterns and interdependencies across phases, which helps us determine the state of HIS research. The results of both parts of the literature review – i.e., zooming in and zooming out (Benbya et al., 2020 ; Gaskin et al., 2014 ) – support us in identifying strengths, as well as drawbacks, in HIS research. On this basis, we develop a research agenda that provides future directions for how HIS research can evolve to anticipate the impending transformation of the healthcare industry.
Literature review: a hermeneutic approach
To answer our research question, we conducted a literature review based on hermeneutic understanding. In particular, we followed Boell and Cecez-Kecmanovic ( 2014 ). They proposed a hermeneutic philosophy as a theoretical foundation and methodological approach that focuses on the inherently interpretive processes in which a reader engages in an ever-expanding and deepening understanding of a relevant body of literature. Adopting a comprehensive literature review approach that addresses well-known issues resulting from applying structured literature review approaches (e.g., Webster & Watson, 2002 ), we strive toward the dual purpose of hermeneutic analysis – i.e., to synthesize and critically assess the body of knowledge (Boell & Cecez-Kecmanovic, 2014 ). We would like to emphasize that the hermeneutic approach to literature reviews is not in opposition to structured approaches. Rather, it addresses the weaknesses of structured approaches (i.e., that they view engagement with the literature as a routine task rather than as a process of intellectual development) and complements them with the hermeneutic perspective to create a holistic approach for conducting literature reviews.
Theoretical underpinning and research method
A methodological means for engaging in reciprocal interpretation of a whole and its constituent elements is the hermeneutic cycle (Bleicher, 2017 ), which consists of a mutually intertwined search and acquisition circle (Circle 1 in Fig. 1 ) and the wider analysis and interpretation circle (Circle 2 in Fig. 1 ) (Boell & Cecez-Kecmanovic, 2014 ). Figure 1 depicts the steps associated with the hermeneutic literature review. The search and acquisition circle is shown on the left of the figure, while the analysis and interpretation circle containing steps of meta and content analysis is depicted on the right. The two circles should be understood as an iterative procedure, the nature of which will be explained in the following.
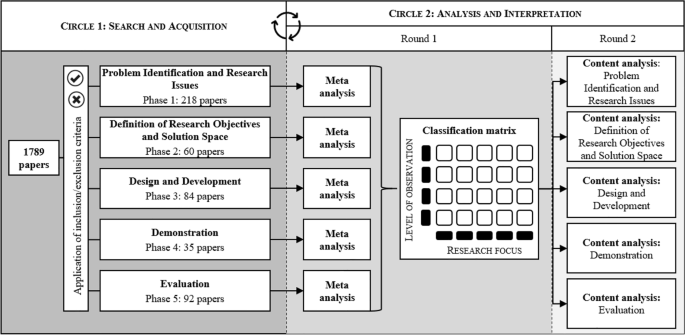
Hermeneutic procedure applied to the literature review
Circle 1: Search and acquisition
The hermeneutic literature review starts with the search and acquisition circle, which is aimed at finding, acquiring, and sorting relevant publications. In line with holistic thinking, we began with the identification of a rather small set of highly relevant literature (Boell & Cecez-Kecmanovic, 2014 ) and went on to identify further literature on the basis of progressively emerging keywords. This step is central to the hermeneutic approach and addresses a criticism on structured literature reviews, namely that they downplay the importance of reading and dialogical interaction between the literature and the reader in the literature search process, reducing it to a formalistic search, stifling academic curiosity, and threatening quality and critique in scholarship and research (Boell & Cecez-Kecmanovic, 2014 ; MacLure, 2005 ). Thus, while the search process remains formalized, as in pure structured approaches, the hermeneutic approach allows us to acquire more information about the problem at hand and to identify more relevant sources of information (Boell & Cecez-Kecmanovic, 2014 ).
Given our initial research question and the scope of the review, we began by searching for papers in the Association for Information System’s (AIS’s) eLibrary over a period of 30 years (1990 to 2019). We consider this database to be a source of the most significant publications in the field of HIS research with a focus on the IS research domain. Using the keywords ‘digital health’ and ‘digital healthcare service’, we identified an initial set of 54 papers based on the title, abstract, and keyword search. Engaging in a first round of the hermeneutic search and acquisition circle, we extended and refined these keywords by identifying emerging topics within the literature, as well as using backward and forward search (Webster & Watson, 2002 ). In particular, with each additional paper identified through backward and forward search, we compared keyword references in the papers to our list of keywords and added them if there was sufficient content delimitation. The decision to add a keyword was discussed with all authors until consensus was reached. This led us to a set of 12 keywords, including ‘electronic health’, ‘ehealth’, ‘mobile health’, ‘mhealth’, ‘health apps’, ‘tech health’, ‘healthcare services’, ‘healthcare informatics’, ‘medical informatics’, and ‘health data’.
The selection of publications being considered for our research comprised all journals belonging to the AIS eLibrary, the Senior Scholars’ Basket of Eight Journals (e.g., European Journal of Information Systems, Information Systems Research , and MIS Quarterly ), well-regarded journals following the analyses of Chiasson and Davidson ( 2004 ) and Chen et al. ( 2019 ) (e.g., Business & Information Systems Engineering , Communications of the ACM, and Decision Support Systems ), and the proceedings of the major AIS conferences (e.g., Americas Conference on Information Systems (AMCIS), International Conference on Information Systems (ICIS)). An overview of the selected journals and proceedings is provided in Appendix 1 .
Using our set of keywords, we searched for each keyword individually in the AIS eLibrary and the databases of the respective journals. Subsequently, we created a dataset and filtered out the duplicates, yielding a total number of 1,789 papers to be screened in the search and acquisition circle (Circle 1 in Fig. 1 ). Figure 2 provides an overview of this process by listing the total number of articles identified for each journal individually.
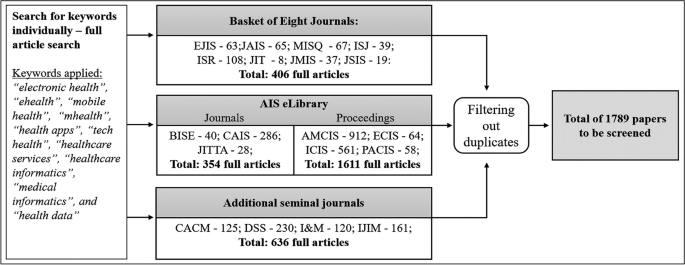
Steps of the search process to create the data set
The resulting 1,789 papers progressively passed through the intertwined hermeneutic circles. Because of the large number, we divided the papers at random into four equally sized groups and assigned them to each of the authors. Each author then screened the paper in his or her group. In the course of several rounds of discussion, decisions on the inclusion of keywords and articles in the literature review were made by all authors, based on the original recommendations of the author responsible for the respective group. To ensure rigor and transparency of the analysis and results, we kept a logbook in which all decisions of the authors and steps of the literature review were recorded (Humphrey, 2011 ).
Given the abundance of topics that were already apparent from titles and abstracts, we began to sort the publications (Boell & Cecez-Kecmanovic, 2014 ). The process of sorting proved to be challenging, as HIS research is diverse and tends to be eclectic (Agarwal et al., 2010 ). This is why researchers have developed frameworks for clustering and analysing HIS research (LeRouge et al., 2007 ). So far, however, no consent on a unified framework has emerged, and sorting is often strongly influenced by the authors’ views on HIS research (Agarwal et al., 2010 ; Fichman et al., 2011 ). For instance, Agarwal et al. ( 2010 ) predetermined health IT adoption and health IT impact as major themes associated with health ITs, acknowledging that this pre-categorization of research topics made a systematic review of the growing and increasingly complex HIS literature unfeasible. Consequently, we decided to sort the articles we had identified into groups inspired by and loosely related to the phases of design science research (DSR) (Peffers et al., 2008 ), which is an essential step in hermeneutics – i.e., defining guidelines to facilitate interpretive explication (Cole & Avison, 2007 ). DSR can be understood as a cumulative endeavour and, therefore, we understood HIS research as accumulative knowledge that can be reconstructed and consolidated using DSR phases as guidance (vom Brocke et al., 2015 ; vom Brocke et al., 2009 ). In particular, this helped us to sort the articles without prejudice to expected HIS research topics and clusters (Grondin, 2016 ).
In the past, researchers have used the DSR process in the context of literature reviews to identify advances in design science-related research outcomes (Offermann et al., 2010 ). In this paper, we use the DSR phases – in the sense of a rough guideline – as a neutral lens to classify articles according to their research outcomes. We thereby assume that HIS literature can be seen as an overall process, where research results and progress are built upon each other and can be classified into phases of problem identification and research issues , definition of research objectives and possible solution space , design and development of solutions , demonstration of research effectiveness, innovativeness and acceptance , and evaluation . These phases served as a guide to achieve an outcome-oriented, first-hand sorting of articles, while this approach also gave us the opportunity to take a bird's-eye view on HIS research. Note that we intentionally omitted the last step of DSR – i.e., communication – as we regard communication as present in all published articles. Based on our initial reading, we assigned all 1,789 papers to the phases and discussed this sorting in multiple rounds until all authors agreed on the assignments.
Simultaneously, we applied criteria for the inclusion and exclusion of articles. We included full papers published in the journals and conference proceedings belonging to our selection. We excluded articles that were abstract-only papers, research-in-progress papers, panel formats, or workshop formats, as well as papers without direct thematic reference to our research objective. Additionally, during the acquisition stage we stored selected papers in a separate database whenever they fulfilled certain quality criteria (e.g., for separate studies using the same dataset, such as a conference publication and a subsequent journal publication, we only used the articles with the most comprehensive reporting of data to avoid over-representation).
The authors read the resulting 489 papers to identify new core terms and keywords that were used in subsequent searches, which not only provided the link to the analysis and interpretation circle but also informed the literature search. For this purpose, each author read the papers and kept notes in the logbook that supported us in systematically recording the review process and allowed us to shift from concentrating on particular papers to focusing on scientific concepts (Boell & Cecez-Kecmanovic, 2014 ; Webster & Watson, 2002 ).
Circle 2: Analysis and interpretation
The search and acquisition circle formed part of the iterative procedure of analysis and interpretation, whereby the reading of individual papers was the key activity linking Circle 1 to the steps of Circle 2 (Boell & Cecez-Kecmanovic, 2014 ). Through orientational reading we gained a general understanding of the literature, thus laying the foundation for the subsequent steps of analysis and interpretation (Boell & Cecez-Kecmanovic, 2014 ).
Within the analysis and interpretation circle, two types of reviews were conducted for all identified and sorted articles: in a first round a meta-review, and in a second round a content analysis of the papers was performed. Meta-reviews are a useful tool for capturing and analysing massive quantities of knowledge using systematic measures and metrics. We followed Palvia et al. ( 2015 ), who proposed a structured method that is integrated into the hermeneutic approach. In particular, having identified and sorted the relevant research articles, we applied proposed review features, including methodological approach, level of observation, sample size, and research focus (Humphrey, 2011 ; Palvia et al., 2015 ) to map, classify, and analyse the publications (Boell & Cecez-Kecmanovic, 2014 ). In doing so, we slightly adapted the classic meta-analysis by focusing on meta-synthesis, which is similar to meta-analysis but follows an interpretive rather than a deductive approach. Whereas a classic meta-analysis tries to increase certainty in cause-and-effect conclusions, meta-synthesis seeks to understand and explain the phenomena of mainly qualitative work (Walsh & Downe, 2005 ). The results of the meta-synthesis provided the basis for our subsequent critical assessment of content. Furthermore, we created a classification matrix based on particularly salient features of the meta-review (i.e., levels of observation and research foci), which facilitated and standardized the content analysis.
Within the matrix, the levels of observation comprised infrastructure (e.g., information exchange systems, electronic health records), individuals (patients and users of digital health services), professionals (e.g., nurses and general practitioners), organizations (hospitals and other medical institutions), and an ecosystem level. The latter is defined as individuals, professionals, organizations, and other stakeholders integrated via a digital infrastructure and aiming to create a digital environment for networked services and organizations with common resources and expectations (Leon et al., 2016 ). To identify the most important concepts used by researchers, we discussed a variety of approaches to the derivation of research foci – i.e., areas containing related or similar concepts that are frequently used in research on HIS. Finally, six research focus areas emerged, covering all relevant research areas. To describe the core HIS research issues addressed by these foci, we used the following questions:
HIS strategy: What are the prerequisites for configuring, implementing, using, maintaining, and finding value in HISs?
HIS creation: How are HISs composed or developed?
HIS implementation: How are HISs implemented and integrated?
HIS use and maintenance: How can HISs be used and maintained once in place?
Consequences and value of HIS: What are the consequences and the added value of HISs?
HIS theorization: What is the intellectual contribution of HIS research?
We used the classification matrix as a tool for assigning publications and finding patterns across research articles and phases. In particular, we used open, axial, and selective coding (Corbin & Strauss, 1990 ) to analyse the content of articles in a second round of the analysis and interpretation circle. Each author individually assigned open codes to text passages while reading the identified research articles, noting their thoughts in the shared digital logbook that was used for constant comparative analysis. Once all authors had agreed on the open codes, axial coding – which is the process of relating the categories and subcategories (including their properties) to each other (Wolfswinkel et al., 2013 ) – was conducted by each author and then discussed until consent on codes was reached. Next, we conducted selective coding and discussed the codes until theoretical saturation was achieved (Corbin & Strauss, 1990 ; Matavire & Brown, 2008 ). For the sake of consistent terminology, we borrowed terms from Chen et al. ( 2019 ), who used multimethod data analysis to investigate the intellectual structure of HIS research. In particular, they proposed 22 major research themes, which we assigned to the initial codes whenever possible. In two rounds of discussion in which we compared the assignment of codes, two additional codes emerged, which left us with a total of 24 theme labels (Appendix 2 ). By discussing the codes at all stages of coding, theoretical saturation emerged, which is the stage at which no additional data are being found or properties of selective codes can be developed (Glaser & Straus, 1968 ; Saunders et al., 2018 ). In fact, independent from each other, all authors saw similar instances occurring over and over again, resulting in the same codes, making us confident that we had reached theoretical saturation (Saunders et al., 2018 ).
Finally, we entered the codes into the classification matrix, which allowed us to identify patterns based on the meta and content analysis. This enabled us to provide insights into the strengths and weaknesses of current HIS research; these are presented in the following section.
Zooming-in: key findings of the phase-based literature analysis
In the following, we ‘zoom in’ (Gaskin et al., 2014 ) by presenting key findings of the literature review for each phase, illustrated by means of the classification matrices. We assigned selective codes that emerged from the content analysis to the fields of the matrices, with the numbers in brackets indicating the frequency with which codes emerged. Note that, for the sake of clarity, we displayed only the most relevant research themes in the matrices and indicated the number of further papers using the reference ‘other themes.’ A complete list of research themes for each phase can be found in the appendix (Appendix 2 ). In the following, each table shows the classification matrix and selective codes that resulted from the meta and content analysis of papers in the respective phase. The shaded areas in the matrix show focused research themes (i.e., selective codes) and characteristics of research articles that gave way to clusters (i.e., collections of themes that appear frequently and/or characteristically for the respective focus).
Phase 1: Problem identification and research issues
Within the first phase, a large body of literature was found (218 articles). This phase encompasses articles that identify problems and novel research issues as a main outcome, with the aim of pointing out shortcomings and provoking further research. For instance, besides behavioural issues such as missing user acceptances or trust in certain HISs, the design and effectiveness of national health programs and/or HIS is a frequently mentioned topic. It should be noted, however, that literature assigned to this phase is extremely diverse in terms of research foci, levels of observation, and research themes, and hardly any gaps can be identified (Table 1 ).
The first cluster (1a) encompasses the research focus of HIS strategy, spanning all levels of observation and totalling 24 publications. HIS strategy appears to be of particular relevance to the levels of organization and infrastructure. Content-wise, the theme of health information interchange is of particular interest, referring, for example, to the development of a common data infrastructure (Ure et al., 2009 ), consumer-oriented health websites (Fisher et al., 2007 ), and security risks of inter-organizational data sharing (Zhang & Pang, 2019 ). HIS productivity and HIS security are the second most salient themes, focusing, for example, on measuring the effectiveness of fitness apps (Babar et al., 2018 ) and presenting challenges with regard to the interoperability of medical devices (Sametinger et al., 2015 ).
The second cluster (1b), comprising 25 publications, represents the ecosystem level and focuses mainly on national and cross-national HIS-related issues such as the relation between ICT penetration and access to ehealth technologies across the European Union (Currie & Seddon, 2014 ), as well as on the collaboration and involvement of different stakeholders (Chang et al., 2009 ; King, 2009 ). Most important here is health information interchange – e.g., the provision, sharing, and transfer of information (Bhandari & Maheshwari, 2009 ; Blinn & Kühne, 2013 ).
Cluster 1c covers the research focus of HIS use and maintenance, as well as the consequences of HIS. Whereas most papers addressing the HIS acceptance theme focus on professionals’ or patients’ acceptance of specific technological solutions, such as telemedicine (Djamsbi et al., 2009 ) or electronic health records (Gabel et al., 2019 ), papers assigned to health information interchange focus on topics related to information disclosure, such as self-tracking applications (Gimpel et al., 2013 ). Finally, the HIS outsourcing and performance theme concentrates on financial aspects in organizations, including potential for quality improvements and cost reductions (Setia et al., 2011 ; Singh et al., 2011 ).
Finally, the fourth cluster (1d) focuses on HIS theorizing with respect to the individual and infrastructure levels of observation. Although this cluster represents a range of theme labels (15), those addressing HIS acceptance, HIS patient-centred care, as well as health analytics and data mining predominate. Papers within the theme label HIS acceptance cover a wide range of topics, such as the acceptance of telehealth (Tsai et al., 2019 ) up to the usage intentions of gamified systems (Hamari & Koivisto, 2015 ). The same applies to the papers assigned to the theme labels of health analytics and data mining. Focusing on the infrastructure level of observation, the identified papers mostly review academic research on data mining in healthcare in general (Werts & Adya, 2000 ), through to the review of articles on the usage of data mining with regard to diabetes self-management (Idrissi et al., 2019 ). Papers on HIS patient-centred care mostly address the challenges and opportunities of patient-centred ehealth applications (Sherer, 2014 ).
Apart from these clusters, quite a few research articles refer to the infrastructure level of observation, addressing information sharing in general (Li et al., 2008 ), electronic medical records (George & Kohnke, 2018 ; Wessel et al., 2017 ), and security and privacy issues (Zafar & Sneha, 2012 ).
Most common in terms of research methods within this phase are case studies (57), followed by quantitative data analyses (50), theoretical discussions (29), and literature studies (14). In particular, case studies dominate when referring to the ecosystem or infrastructure level of observation, whereas quantitative analyses are conducted when individuals or professionals are at the centre of the discussion. However, and unsurprisingly given the considerable diversity of research themes within this phase, the variety of research methods is also quite large, ranging from field studies (Paul & McDaniel, 2004 ), to interviews (Knight et al., 2008 ), to multimethod research designs (Motamarri et al., 2014 ).
Phase 2: Definition of research objectives and solution space
The second phase of HIS research yielded a lower number of articles (45) compared to the phase of problem identification and research issues. The second phase comprises articles that focus on proposing possible solutions to existing problems – i.e., introducing theory-driven, conceptual designs of health ecosystems including health information interchange, as well as scenario analyses anticipating the consequences of HIS implementation on an organizational level. Based on the research foci and levels of observation, we identified three specific thematic clusters, as shown in Table 2 .
The first cluster (2a) comprises the ecosystem level of observation and encompasses eight publications. Besides a strong tendency toward theory-driven research, health information interchange is the most common theme. We found that the need to enable cooperation within networks and to ensure accurate data input was addressed in most of the literature. While a majority of studies focus on the application of HIS in networks within specific boundaries, such as medical emergency coordination (Sujanto et al., 2008 ) or Singapore’s crisis management in the fight against the SARS outbreak in 2003 (Devadoss & Pan, 2004 ), other studies, such as that by Aanestad et al. ( 2019 ), take an overarching perspective, addressing the need to break down silo thinking and to start working in networks. Following the question of why action research fails to persist over time, Braa et al. ( 2004 ) highlighted the role of network alignment, criticizing action research projects for failing to move beyond the prototyping phase and, therefore, failing to have any real impact.
Cluster 2b, encompassing nine publications, was derived from the observation that studies within the organizational level concentrated strongly on HIS use and maintenance and the consequences of HIS research. Herein, a vast array of topics was observed, such as the potential for cost reduction through HIS (Byrd & Byrd, 2009 ), the impact of HIS on product and process innovation in European hospitals (Arvanitis & Loukis, 2014 ), and the perceived effectiveness of security risk management in healthcare (Zafar et al., 2012 ). Moreover, we found that practice-oriented methods, such as mixed-method approaches, surveys, data analyses, and case studies, are used predominantly within this cluster. Focusing on the latter, most studies analyse particular scenarios by using a rather small sample of cases, for instance, Al-Qirim ( 2003 ) analysed factors influencing telemedicine success in psychiatry and dermatology in Norway.
The third cluster (2c) was derived from analysis of the HIS creation research focus (nine publications). Although health information interchange is the most represented in this cluster, a large number of further themes can be observed. Studies within this cluster predominantly address design aspects of system interoperability, focusing on data processing and data interchange between the actors. HISs mostly serve as a tool for the development or enhancement of decision support systems, such as for real-time diagnostics combining knowledge management with specific patient information (Mitsa et al., 2007 ) or clinical learning models incorporating decision support systems in the dosing process of initial drug selection (Akcura & Ozdemir, 2008 ).
Phase 3: Design and development
The design and development phase comprises 84 research articles concerned with the creation of novel IS artefacts (e.g., theories, models, instantiations). We thereby refer to Lee et al.’s ( 2015 ) definition of the IS artefact – i.e., the information, technology, and social artefact that forms an IS artefact by interacting. We assigned to this phase papers that are explicitly concerned with developing solutions for information exchange (e.g., design of messaging systems or knowledge systems in hospitals), technological artefacts (e.g., hardware or software used for generating electronic health records), and social artefacts that relate to social objects (e.g., design of national or international institutions and policies to control specific health settings and patient-centred solutions). Within the design and development phase, the analysis revealed two clusters (Table 3 ).
The first cluster (3a) was identified in the research focus of HIS creation (31 articles). Here, the most frequent research theme is HIS innovation followed by HIS and patient-centred care, HIS productivity, and health analytics and data mining. The focus is on specific contexts, mostly medical conditions and artefacts developed for their treatment, such as in the context of mental health/psychotherapy (Neben et al., 2016 ; Patel et al., 2018 ), diabetes (Lichtenberg et al., 2019 ), or obesity (Pletikosa et al., 2014 ). Furthermore, information infrastructures or architectures – for instance, for the process of drug prescription (Rodon & Silva, 2015 ), or for communication between healthcare providers and patients (Volland et al., 2014 ) – are represented.
The second aggregation of research articles is found in cluster 3b, focusing on theoretical aspects of HIS (32 articles). Again, these studies span all levels of observation (including infrastructure, individual, professional, organization, and ecosystem). Topics in this theme are diverse, ranging from HIS on a national level (Preko et al., 2019 ), to knowledge management in healthcare (Wu & Hu, 2012 ) to security of HIS (Kenny & Connolly, 2016 ).
Beyond both clusters, it is evident that during design and development, researchers do not deal with the consequences of HIS, nor does HIS strategy play an important role. Furthermore, only in the research focus of theorization is the ecosystem level of some relevance to other levels (e.g., the individual level). It should be noted that ecosystems are mostly referred to in terms of nations or communities, without any transnational or global perspective. Furthermore, the term ‘ecosystem’ has not been used in research, and within the other research focus areas, the ecosystem level is barely represented. Moreover, articles combining different perspectives of the single levels of observation on HIS – namely individuals (i.e., patients), professionals (i.e., medical staff), and organizations (e.g., hospitals) – are rare. During design and development, potential users are not typically integrated, whereas it is quite common to derive requirements and an application design from theory, only involving users afterwards – e.g., in the form of a field experiment (e.g., Neben et al., 2016 ).
Surprisingly, theoretical papers outweigh papers on practical project work, whereby the latter mostly focus on a description of the infrastructure or artefact (e.g., Dehling & Sunyaev, 2012 ; Theobalt et al., 2013 ; Varshney, 2004 ) or are based on (mostly single) case studies (e.g., Hafermalz & Riemer, 2016 ; Klecun et al., 2019 ; Ryan et al., 2019 ). Within the design and development phase, the generation of frameworks, research models, or taxonomies is prevalent (e.g., Preko et al., 2019 ; Tokar et al., 2015 ; Yang & Varshney, 2016 ).
Phase 4: Demonstration
This phase includes 35 articles related to presenting and elaborating on proposed solutions – e.g., how HIS can be implemented organization-wide (e.g., via integration into existing hospital-wide information systems), proposed strategies and health policies, as well as novel solutions that focus on health treatment improvements. Within the demonstration phase, we identified two clusters that emerged from the meta and content analyses (Table 4 ).
Cluster 4a (10 articles) is characterized by articles that focus on HIS issues related to the infrastructure level, spanning the research foci of HIS strategy, creation, and deployment. Content-wise, the cluster deals mainly with technical feasibility and desirability of HISs, including topics such as the configuration of modular infrastructures that support a seamless exchange of HISs within and between hospitals (Dünnebeil et al., 2013 ). Moreover, papers in this cluster address HIS practicability by determining general criteria that are important for the design of health information systems (Maheshwari et al., 2006 ) or conduct HIS application tests by carrying out prototypical implementations of communication infrastructures. In particular, the latter are tested and proven to meet specific technical standards to guarantee the frictionless transmission of health information data (Schweiger et al., 2007 ). In contrast, Heine et al. ( 2003 ) upscaled existing HIS solutions and tested the infrastructure in large, realistic scenarios.
Conversely, cluster 4b (11 articles) is mainly concerned with HIS use and maintenance, spanning several levels of observation – i.e., infrastructure, individuals, professionals, and organizations. Interestingly, papers in this cluster aim at efficiency and added value when looking at the infrastructure and organizational levels, whereas researchers are more interested in acceptance when focusing on the individual and professional use of HISs. Overall, cluster 4b is primarily concerned with organizational performance (e.g., increases in efficiency due to better communication and seamless transfer of patient health information) as well as user acceptance of new HISs.
Although the two clusters constitute a diverse set of literature and themes, it is apparent that research taking an ecosystem perspective is very rarely represented. Across the papers, only three are concerned with issues related to the ecosystem level. In particular, Lebcir et al. ( 2008 ) applied computer simulations in a theoretical demonstration as a decision support system for policy and decision-makers in the healthcare ecosystem. Abouzahra and Tan ( 2014 ) used a mixed-methods approach to demonstrate a model that supports clinical health management. Findikoglu and Watson-Manheim ( 2016 ) addressed the consequences of the implementation of electronic health records (EHR) systems in developing countries.
Phase 5: Evaluation
The fifth phase includes 92 publications with a focus on assessing existing or newly introduced HIS artefacts – i.e., concepts, policies, applications, and programs – thereby proving their innovativeness, effectiveness, or user acceptance. As Table 5 shows, three clusters were identified.
The main focus of publications in the evaluation phase is on the infrastructure level, where most papers are related to HIS creation and HIS use and maintenance. Therefore, together with the publications pigeonholed to HIS deployment and consequences of HIS, these articles were summarized as the first cluster (5a, comprising 53 articles). The assessment of national HIS programs, as well as mobile health solutions, are a frequent focus (10 papers). Articles on HIS use and maintenance are largely related to the professional, organizational, and ecosystem levels and were thus grouped as cluster 5b (10 articles). A third cluster (5c – 11 articles) emerged from research articles in HIS theorization. Here, papers at all levels of observation were found. Research focusing on areas such as HIS strategy and consequences of HIS are, with a few exceptions, not covered in the evaluation phase. Methods used include interviews, focus groups, and observations (e.g., Romanow et al., 2018 ). Experiments and simulation are rarely applied (e.g., Mun & Lee, 2017 ). The number of interviews shows a huge spread, starting with 12 and reaching a maximum of 150 persons interviewed.
Under the evaluation lens, the ecosystem perspective is covered by seven articles, but only three papers look at cases, while the others focus on theorization or consequences in terms of costs. Overall, popular topics in the evaluation phase include mobile health and the fields of electronic medical records (EMR) and EHR, e.g., Huerta et al. ( 2013 ); Kim and Kwon ( 2019 ). The authors cover these themes mostly from an HIS creation perspective; thus, they deal with concrete concepts, prototypes, or even implemented systems. In the evaluation phase, just nine papers deal with HIS innovation – a good example being Bullinger et al. ( 2012 ), who investigated the adoption of open health platforms. We may conclude that, in most cases, evaluation is related to more established technologies of HIS. As expected, most articles in this phase rely on practice-oriented/empirical work (as opposed to theory-driven/conceptual work). Just two papers (Ghanvatkar & Rajan, 2019 ; Lin et al., 2017 ) deal with health analytics and data mining, one of the emerging topics of HIS.
Zooming out: key findings of the literature analysis across phases
Having elaborated on the key findings within each phase of HIS research, we now ‘zoom out’ (Benbya et al., 2020 ; Gaskin et al., 2014 ) to recognize the bigger picture. Thereby, we ‘black-box’ the concrete research themes (e.g., HIS implementation, health analytics, HIS innovation) to focus on clusters across phases, highlighting the breadth that HIS research encompasses (Leroy et al., 2013 ). In particular, while we focused on analysing the main topics within the different phases of HIS research in the zoom-in section, we now abstract from those to perform a comparative analysis of emerging clusters across those phases by zooming out. We do so by comparing the different clusters, taking into account the aspects of the level of observation and the research foci, which gave us the opportunity to identify areas of strong emphasis and potential gaps.
In particular, each author first conducted this comparative analysis on their own and then discussed and identified the potential weaknesses together. This was done in two rounds of discussion. In particular, it became obvious which areas hold immense potential for further research in healthcare (especially the penetration of new, initially non-healthcare actors, such as tech companies or other providers pushing into the industry). We summarize these potentials for research by proposing four pathways that can help HIS research to broaden its focus so that we can better understand and contribute to current developments. Notably, we expect that these insights will help to assess the state-of-the-art of HIS research and its preparedness for dealing with the consequences of Covid-19 and further pandemics, as well as for coping with associated exogenous shocks.
In zooming out, we identified discrepancies between phase 1 (problem identification and research issues) and the subsequent phases. In particular, the diversity of topics was considerably lower when it came to how researchers determined strategies; created, demonstrated, used, and maintained HISs; and coped with the consequences thereof. We observed that researchers pointed to a diverse set of issues that span all levels of observation, especially in HIS theorization, focusing on topics such as trust in HIS, data analytics, and problems associated with the carrying out of national health programs. Surprisingly, although we can assume that researchers recognized the multidimensionality of issues as a motivation to conduct HIS research, they did not seem to approach HIS research issues in a comprehensive and consistent way.
To illustrate this assertion, we point to the ‘shift of clusters’ that can be observed when comparing the single phases, from problem identification to the evaluation of HIS. We note that clusters increasingly migrate ‘downwards’ (i.e., from the ecosystem level down to the infrastructure level) and become even fewer. In line with Braa et al. ( 2004 ), we suggest that extant HIS research has identified a multitude of interrelated issues but has faced problems in translating these approaches into concrete and holistic solutions. This is reflected in the lower number of, and reduced diversity in, clusters across research themes when we move through the HIS research phases. Thus, we conclude that future HIS research can be broadened by taking into account the following pathway:
HIS research is well-prepared and able to identify and theorize on systemic problems related to the healthcare industry. Nonetheless, it has the potential to address these problems more thoroughly – i.e., to find solutions that are as diverse as the problems and, thus, suitable for coping with issues in the healthcare industry characterized by the involvement of multiple actors, such as governments, healthcare providers, tech companies, and their interactions in diverse ecosystems (pathway 1).
As we have seen, HIS research has tended to focus on important but incremental improvements to existing infrastructures, particularly in the phases of demonstration and evaluation, with the aim of presenting new IS artefacts and conceptual or practical solutions. For instance, Choi and Tulu ( 2017 ) considered improvements in user interfaces to decrease the complexity of mobile health applications using incremental interface design changes and altering touch techniques. Similarly, Roehrig and Knorr ( 2000 ) designed patient-centred access controls that can be implemented in existing infrastructures to increase the privacy and security of EHRs and avoid malicious access and misuse of patient health information by third parties.
While we sincerely acknowledge these contributions and wish to emphasize the multitude of papers that are concerned with enhancements to existing infrastructures, we would like to shift the view to the major challenges in HIS research. These challenges include combating global and fast-spreading diseases (e.g., malaria, tuberculosis, Covid-19) and tracking health statuses accurately and efficiently, especially in developing countries. All of these challenges necessitate global and comprehensive solutions, spanning individuals, organizations, and nations, and have to be embedded in a global ecosystem (Winter & Butler, 2011 ). Such grand challenges are, by nature, not easy to cope with, and the intention to develop a comprehensive solution from the perspective of IS researchers seems almost misguided. However, HIS research is currently missing the opportunity to make an impact, despite the discipline’s natural intersection with essential aspects of the healthcare industry (i.e., its infrastructures, technologies, and stakeholders, and the interdependencies between these components). Thus, we assert that:
HIS research has often focused on necessary and incremental improvements to existing IS artefacts and infrastructures. We see potential in shifting this focus to developing solutions that combine existing IS artefacts to allow for exchange of information and the creation of open systems, which will enhance support for and understanding of the emergence of ecosystems (pathway 2).
By focusing on incremental improvements, HIS research has become extraordinarily successful in solving isolated issues, especially in relation to the problems of patients and health service providers (e.g., hospitals and general practitioners). However, we observed during our analysis that spillover effects were seldom investigated. When, for example, a new decision support system in a hospital was introduced, positive consequences for patients, such as more accurate diagnoses, were rarely of interest to the research. In fact, our meta-analysis revealed that the level of observation for the majority of papers matched the level of analysed effects. While it is valid to investigate productivity and efficiency gains by introducing a hospital-wide decision support system, we are convinced that spillover effects (for instance, on patients) should also be within the focus of HIS research. Therein, we suggest that HIS research has not focused primarily on patients and their well-being but on IS infrastructures and artefacts. However, patient well-being is the ultimate direct (or indirect) goal of any HIS research (by increasing the accuracy and shortening the time of diagnosis, improving treatment success rates, etc.). Thus, we propose that:
HIS research is experienced in solving isolated issues related to the daily processes of healthcare providers; however, we see much potential in considering the value that is delivered by focusing on patient-centricity (pathway 3).
Putting the patient at the centre of HIS research implies shifting the focus of researchers to the patient’s own processes. The question remains as to how HIS researchers can support patient-centricity. While this is only possible by understanding patients’ processes, we also see the need to understand the whole system – i.e., the ecosystem in which patients’ processes are embedded. The ecosystem perspective needs to consider networked services and organizations, including resources and how they interact with stakeholders of the healthcare industry (including patients). To date, we observe, across phases the ecosystem perspective has largely been neglected. To be precise, although HIS research seems to be aware of the multilevel aspects of healthcare issues in the problem identification phase, researchers appear to stop or are hindered from developing solutions that go beyond the development of prototypes (Braa et al., 2004 ). Thus, we find that:
HIS research is capable of theorizing on an ecosystem level (i.e., capturing the complexity of the socio-technical health system), but would benefit from increasing the transfer of these insights into research so as to develop holistic solutions (pathway 4).
Looking at the strengths of HIS research, the reviewed papers accentuate the unique contribution that IS researchers can make to better understand and design IS artefacts for the healthcare context. This has been achieved by analysing empirical data and exploring contextual influences through the application and elaboration of IS theories (LeRouge et al., 2007 ). At the same time, our literature review shows the incredible diversity and high level of complexity of issues related to HISs, indicating that we need solutions characterized by holism and the inclusion of multiple actors (i.e., an integrative ecosystem perspective). So far, by concentrating on incremental improvements to existing infrastructures HIS research has widely failed to reach the necessary holistic level.
We would like to emphasize that we recognize the value of all previous approaches. Yet, it is necessary to ask whether we as IS researchers are in a position to identify current developments in the healthcare industry and to anticipate the consequences triggered by pandemics or other waves of disease. We acknowledge that this will be difficult unless we take a more holistic view and try to understand connections in the health ecosystems. Regarding whether HIS research is in a position to capture and anticipate consequences of the current push of tech companies in the healthcare industry catalysed, for example, by Covid-19, we assert that this is hardly the case, even if IS research is well-placed to interpret the expected socio-technical changes and adaptations within healthcare. Given the enormous potential for disruption caused by, for instance, pandemics and its consequences, such as the intrusion of technology companies into the market, it is now time to question and redefine the role of HIS research so that it can generate decisive impacts on the developments in this industry.
- Research agenda
To support HIS research for the transformation of the healthcare industry, we develop a research agenda that is informed by complexity theory. This theory implies that complex, socio-technical systems such as the healthcare industry can fluctuate between different states, ranging from homogenous forms of coevolution (i.e., a state where emergent structures and processes become similar to each other) to chaotic systems that are characterized by increasing levels of tension, which might result in extreme outcomes such as catastrophes or crises (Benbya et al., 2020 ).
While coevolution and chaos represent possible extreme states, the current situation – i.e., the penetration of tech companies into the healthcare industry – is best described by the dynamic process of emergence. Emergence is characterized by a disequilibrium, which implies unpredictability of outcomes that may lead to new structures, patterns, and properties within a system characterized by self-organization and bursts of amplification (Benbya et al., 2020 ; Kozlowski et al., 2013 ). Given the dynamics resulting from this, it seems impossible to predict the future; however, it is not impossible to prepare for it.
In particular, the current dynamics within the healthcare industry necessitate an understanding of exponential progress, not as the ability to foresee well-defined events in space and time, but as an anticipation of the consequences of emerging states and dynamic adaptive behaviours within the industry (Benbya et al., 2020 ). The following research agenda for HIS research is thus structured along three key issues: anticipating the range of actors’ behaviours, determining boundaries and fostering collaboration in the healthcare industry, and creating sustainable knowledge ecosystems.
According to these key issues, Table 6 offers guiding questions for HIS researchers. Addressing all issues will contribute to an understanding of the entire healthcare industry and the development of holistic solutions for a multitude of health issues by involving different actors (e.g., patients, hospitals, professionals, governments, NGOs). However, we propose approaching the agenda stepwise, in the order of the key issues, first looking at the range of behaviours and consequences of current developments for actors, then focusing on the blurring lines of the healthcare industry, and finally investigating the dissemination and sharing of knowledge, which we see as the ultimate means to connect actors and infrastructures to create a joint ecosystem. Table 6 thereby provides key guiding statements and exemplary research questions for future HIS research that support researchers in taking one of the aforementioned pathways. We structured guiding statements along three major areas of improvement. In addition, we offer exemplary research questions to these statements, as well as inspiring studies from other industries that have faced similar challenges and have been studied and supported by researchers.
Area of improvement 1: Anticipating the range of actor behaviours
As healthcare systems are becoming more open – for example, through the penetration of new market actors and the use of increasingly comprehensive and advanced health technologies – accurately determining the boundaries of an industry and its key actors is becoming more difficult. To model these systems, we must carefully model every interaction in them (Benbya et al., 2020 ), which first requires HIS researchers to identify potential actors in the ecosystem rather than predetermining assumed industry boundaries. As actors are not always evident, we follow Benbya et al. ( 2020 ) in proposing Salthe’s ( 1985 ) three-level specification, assisting researchers in identifying actors at the focal level of what is actually observed (e.g., hospitals, patients, and general practitioners) and its relations with the parts described at the lower level (e.g., administrators and legal professionals), taking into account entities or processes at a higher level in which actors at the focal level are embedded (e.g., national health system structures and supporting industries, such as the pharmaceutical or tech industries). These examples are only illustrative, and criteria for levels have to be suggested and discussed for each research endeavour.
To anticipate future developments in the healthcare industry, we also need to analyse the strategies and interests of actors for joining or staying in the healthcare industry. This is especially important because, like other complex socio-technical systems, the healthcare industry is made up of large numbers of actors that influence each other in nonlinear ways, continually adapting to internal or external tensions (Holland et al., 1996 ). If tension rises above a certain threshold, we might expect chaos or extreme outcomes. As these are not beneficial for the actors in the system, the eventual goal is to align actors’ interests and strategies across a specific range of behaviour to foster coevolution. This allows for multi-layered ecosystems that encourage joint business strategies in competitive landscapes, as well as the alignment of business processes and IT across actors (Lee et al., 2013 ).
Area of improvement 2: Determining boundaries and fostering collaboration
Actors build the cornerstones of the healthcare industry. Thus, if we want to understand and capture its blurring boundaries, there is a need to understand the complex causality of interactions among heterogeneous actors. In particular, scholars have emphasized that, in complex systems, outcomes rarely have a single cause but rather result from the interdependence of multiple conditions, implying that there exist multiple pathways from an input to an output (Benbya et al., 2020 ). To capture interaction, we follow Kozlowski et al. ( 2013 ), who envisioned a positive feedback process including bottom-up dynamic interaction among lower-level actors (upward causation), which over time manifests at higher, collective levels, while higher-level actors influence interaction at lower levels (downward causation). As these kinds of causalities shape interaction within healthcare ecosystems as well as at their boundaries, HIS researchers need to account for multi-directional causality in the form of upward, downward, and circular causality (Benbya et al., 2020 ; Kim, 1992 ).
Understanding casualties among actors in the healthcare industry is important for harnessing the advantages of the blurring of boundaries – e.g., by making use of the emergent ecosystem for launching innovation cycles (Hacklin, 2008 ). However, first, HIS researchers increasingly need to consider the ecosystem perspective by investigating interactions among actors and the role of IS infrastructures in fostering collaborative health innovations. We propose a focus on radical innovation, which is necessary to address the diversity and interdependence of issues present in the healthcare industry by putting the patient at the core of all innovation efforts. HIS researchers, however, need to break down the boundaries between different innovation phases and innovation agencies, including a higher level of unpredictability and overlap in their time horizons (Nambisan et al., 2017 ). Notably, this requires actors in the healthcare industry to discover new meaning around advanced technologies and IS infrastructures whose design needs to facilitate shared meaning among a diverse set of actors, thereby fuelling radical digital innovations (Nambisan et al., 2017 ).
Area of improvement 3: Creating sustainable knowledge ecosystems
We define knowledge dissemination and sharing as the ultimate means of connecting actors and aligning actions within common frameworks to shape an inclusive healthcare ecosystem. Paving the way for inclusive healthcare ecosystems is thus necessary to address the current shortcomings of HIS research as elaborated in the previous section.
Addressing knowledge dissemination and sharing is thereby of the utmost importance as we look at the healthcare industry in the current phase of emergence. This means that the industry might go through several transition phases in which existing actors, structures, and causal relationships dissipate and new ones emerge, resulting in a different set of causal relationships and eventually altering knowledge claims (Benbya et al., 2020 ). Creating a permeable and sustainable knowledge management system is necessary to ensure the transfer of knowledge for the best outcomes for the patient while securing the intellectual property rights and competitive advantages of diverse actors such as hospitals and other healthcare providers.
To be precise, we argue that to design sustainable knowledge management systems, HIS researchers need to implement systems with structures that create mutual benefits – i.e., encourage knowledge dissemination and sharing (e.g., open innovation) by actors in the healthcare industry. In a comprehensive and sustainable knowledge management system, however, not only corporations but also patients should be encouraged to share knowledge. Using this information, researchers and health service providers will be enabled to create optimized infrastructures, processes, and products (e.g., for predictive algorithms that improve treatment accuracy, or for assessing the likelihood of the occurrence of certain diseases and even of pandemics). At the same time, the trustworthiness of predictions and the anonymity of health information (and thus privacy) must be ensured. Bridging this duality of data sharing and knowledge dissemination, on the one hand, and protection of health information, on the other, is therefore essential for future HIS research.
This paper analyses the HIS literature within the IS research domain, prompted by the question of whether IS researchers are prepared to capture and anticipate exogenous changes and the consequences of current developments in the healthcare industry. While this review is limited to insights into the IS research domain and does not claim to offer insights into the health literature in general or related publications (e.g., governmental publications), we disclose several shortcomings and three key issues. Based on these, we provide initial guidance on how IS research can develop so that it is prepared to capture the expected large and long-lasting changes from current and possible future pandemics as well as the necessary adaptation of global healthcare industries affecting human agencies and experiences in all dimensions. Thus, while adaptations in the healthcare industry are already emerging, IS researchers have yet to develop a more comprehensive view of the healthcare industry. For this purpose, we provide a research agenda that is structured in terms of three areas of improvement: anticipating the range of actors’ behaviours, determining boundaries and fostering collaborations among actors in the healthcare industry, and creating sustainable knowledge management systems. In particular, addressing these areas will assist IS researchers in balancing the shortcomings of current HIS research with the unique contribution that IS research plays in analysing, advancing, and managing the healthcare industry. We are confident that IS research is not only capable of anticipating changes and consequences but also of actively shaping the future of the healthcare industry by promoting sustainable healthcare ecosystems, cultivating structures of mutual benefit and cooperation between actors, and realigning IS research to face the imminent transformation of the healthcare industry. IS research cannot contribute directly to solving the current pandemic problems; however, it can contribute indirectly triggering timely adaptations of novel technologies in global health systems, and proposing new processes, business models, and systematic changes that will prepare health systems to cope with increasing digitalization and emerging players whose push into the market enabled by the exogenous effects triggered by the pandemic.
While we are confident that the proposed research agenda based on the analysis of HIS literature provides fruitful arrays for being prepared in anticipating the future role of IS research for the healthcare industry, our results need to be reflected in light of their shortcomings. First and foremost, we recognize that the selection of literature, which is limited to the IS research domain, excludes other contextual factors that are not primarily considered by IS researchers. Thus, we cannot assume completeness, providing instead a broad overview of current issues in HIS research. In addition, possible biases may have arisen due to the qualitative analysis approach used. By independently coding and discussing codes to the point of theoretical saturation, we are confident that we largely eliminated biases in the thematic analysis. However, data saturation could not be achieved. This means that further insights could have emerged through the addition of other database searches and journals with a broader scope. Additionally, the initial sorting of papers into single defined phases of DSR research restricted multiple assignments that could have led to different results. However, we consider sorting as a necessary step of abstraction, especially given the large number of papers analysed.
We deliberately considered IS research, for which we have developed an agenda for potential future research avenues. For each of those avenues, researchers should go deeper into the subject matter in order to examine the complexity of the paths shown and to include them in the analysis (e.g., through in-depth case studies). However, it is also clear from the issues identified that IS researchers cannot solve current challenges by working on the pathways alone. In fact, the issues identified in the research agenda are only the starting point for further research, which should address the proposed issues step by step and in cooperation with other research disciplines. The latter is likely to generate further and deeper-rooted problems, as well as, in turn, future paths for research. Nevertheless, we are confident that this paper provides an important first step in opening up HIS research to better understand current developments in the healthcare industry. Further, by following and enhancing the proposed research pathways, we believe that HIS research can contribute to and support changes already taking place in the healthcare industry.
Change history
20 december 2021.
A Correction to this paper has been published: https://doi.org/10.1007/s12525-021-00518-8
Aanestad, M., Vassilakopoulou, P., & Ovrelid, E. (2019). Collaborative innovation in healthcare: boundary resources for peripheral actors. International Conference on Information Systems (ICIS), 1 , 1–17.
Google Scholar
Abouzahra, M., & Tan, J. (2014). The multi-level impact of clinical decision support system: a framework and a call for mixed methods. Pacific Asia Conference on Information Systems (PACIS), 1–17.
Agarwal, R., Gao, G., DesRoches, C., & Jha, A. K. (2010). Digital transformation of healthcare: current status and the road ahead. Information Systems Research, 21 (4), 796–809. https://doi.org/10.1287/isre.1100.0327
Article Google Scholar
Akcura, M. T., & Ozdemir, Z. D. (2008). Physician learning and clinical decision support systems. Americas Conference on Information Systems (AMCIS) , 1–10.
Akkerman, S. F., & Bakker, A. (2011). Boundary crossing and boundary objects. Review of Educational Research, 81 (2), 132–169. https://doi.org/10.3102/0034654311404435
Al-Qirim, N. (2003). Championing telemedicine in New Zealand: the case of utilizing video conferencing in psychiatry and dermatology. Americas Conference on Information Systems (AMCIS), 1–10.
Arvanitis, S., & Loukis, E. (2014). An empirical investigation of the impact of ICT on innovation in European hospitals. European Conference on Information Systems (ECIS), 1–13.
Babar, Y., Chan, J., & Choi, B. (2018). "Run Forrest Run!": measuring the impact of app-enabled performance and social feedback on running performance. Pacific Asia Conference on Information Systems (PACIS 2018), 160.
Benbya, H., Nan, N., Tandriverdi, H., & Yoo, Y. (2020). Complexity and information systems research in the emerging digital world. MIS Quarterly , 44 (1), 1–17. https://doi.org/10.25300/MISQ/2020/13304
Bhandari, G., & Maheshwari, B. (2009). Toward an integrated health information system for collaborative decision making and resource sharing: findings from a Canadian study. Americas Conference on Information Systems (AMCIS), 648.
Bleicher, J. (2017). Contemporary Hermeneutics: Hermeneutics as method, philosophy, and critique (2nd ed.). Routledge.
Book Google Scholar
Blinn, N., & Kühne, M. (2013). Health information on the internet - state of the art and analysis. Business & Information Systems Engineering, 5 (4), 259–274. https://doi.org/10.1007/s12599-013-0274-4
Boell, S., & Cecez-Kecmanovic, D. (2014). A hermeneutic approach for conducting literature reviews and literature searches. Communication of the Association for Information Systems, 34 (12), 257–286. https://doi.org/10.17705/1CAIS.03412
Braa, J., Monteiro, E., & Sahay, S. (2004). Networks of action: sustainable health information systems across developing countries. MIS Quarterly, 28 (3), 337–362. https://doi.org/10.2307/25148643
Bullinger, A., Rass, M., & Moeslein, K. (2012). Towards open innovation in health care. European Conference on Information Systems (ECIS), 1–13.
Byrd, L., & Byrd, T. (2009). Examining the effects of healthcare technology on operational cost. Americas Conference on Information Systems (AMCIS), 1–10.
CB Insights. (2018). How Google Plans to Use AI to Reinvent the $3 Trillion US Healthcare Industry . https://www.distilnfo.com/lifesciences/files/2018/11/CB-Insights_Google-Strategy-Healthcare.pdf
Chang, I. C., Hwang, H. G., Hung, M. C., Kuo, K. M., & Yen, D. C. (2009). Factors affecting cross-hospital exchange of electronic medical records. Information & Management, 46 (2), 109–115. https://doi.org/10.1016/j.im.2008.12.004
Chen, L., Baird, A., & Straub, D. (2019). An analysis of the evolving intellectual structure of health information systems research in the information systems discipline. Journal of the Association for Information Systems , 20 (8), 1023–1074. https://doi.org/10.17705/1jais.00561
Chiasson, M. W., & Davidson, E. (2004). Pushing the contextual envelope: developing and diffusing IS theory for health information systems research. Information and Organization, 14 (3), 155–188. https://doi.org/10.1016/j.infoandorg.2004.02.001
Choi, W., & Tulu, B. (2017). Effective use of user interfaces and user experience in an mHealth application. Hawaii International Conference on System Sciences (HICSS), 3803–3812. https://doi.org/10.24251/HICSS.2017.460
Cole, M., & Avison, D. (2007). The potential of hermeneutics in information systems research. European Journal of Information Systems, 16 (6), 820–833. https://doi.org/10.1057/palgrave.ejis.3000725
Cilliers, P. (2001). Boundaries, hierarchies and networks in complex systems. International Journal of Innovation Management, 5 (2), 135–147. https://doi.org/10.1515/9781501502590-009
Corbin, J. M., & Strauss, A. (1990). Grounded theory research: procedures, canons, and evaluative criteria. Qualitative Sociology, 13 (1), 3–21. https://doi.org/10.1007/BF00988593
Currie, W. L., & Seddon, J. J. (2014). A cross-national analysis of eHealth in the European Union: some policy and research directions. Information & Management, 51 (6), 783–797. https://doi.org/10.1016/j.im.2014.04.004
Dehling, T., & Sunyaev, A. (2012). Architecture and design of a patient-friendly eHealth web application: patient information leaflets and supplementary services. Americas Conference on Information Systems (AMCIS), 1–8.
Devadoss, P., & Pan, S. L. (2004). Leveraging eGovernment infrastructure for crisis management: lessons from managing SARS outbreak in Singapore. Americas Conference on Information Systems (AMCIS), 1–10.
Djamsbi, S., Fruhling, A., & Loiacono, E. (2009). The influence of affect, attitude and usefulness in the acceptance of telemedicine systems. Journal of Information Technology Theory and Application, 10 (1), 1–38.
Dünnebeil, S., Krcmar, H., Sunyaev, A., Leimeister, J., & M. (2013). Modular architecture of value-added applications for German healthcare telematics. Business & Information Systems Engineering, 5, 3–16. https://doi.org/10.1007/s12599-012-0243-3
Enkel, E., & Gassmann, O. (2010). Creative imitation: exploring the case of cross-industry innovation. R&d Management, 40 (3), 256–270. https://doi.org/10.1111/j.1467-9310.2010.00591.x
Fichman, R. G., Kohli, R., & Krishnan, R. (2011). The role of information systems in healthcare: current research and future trends. Information Systems Research, 22 (3), 419–428. https://doi.org/10.2307/23015587
Findikoglu, M., & Watson-Manheim, M. B. (2016). Linking macro-level goals to micro-level routines: EHR-enabled transformation of primary care services. Journal of Information Technology, 31 (4), 382–400. https://doi.org/10.1057/s41265-016-0023-5
Fisher, J., Burstein, F., Lynch, K., Lazarenko, K., & McKemmish, S. (2007). Health information websites: is the health consumer being well-served? Americas Conference on Information Systems (AMCIS), 1–10.
Fisman, R., Branstetter, L. G., & Foley, C. F. (2004). Do stronger intellectual property rights increase international technology transfer? Empirical evidence from US firm-level panel data . The World Bank, Washington, DC. https://doi.org/10.1596/1813-9450-3305
Gabel, M., Foege, J. N., & Nuesch, S. (2019). The (In)Effectiveness of incentives - a field experiment on the adoption of personal electronic health records. International Conference on Information Systems (ICIS), 1–17.
Gantori, S., Issel, H., Donovan, P., Rose, B., Kane, L., Dennean, K., Ganter R., Sariyska, A., Wayne, G., Hyde, C., & Lee, A. (2020). Future of the Tech Economy . https://www.ubs.com/global/en/wealth-management/chief-investment-office/investment-opportunities/investing-in-the-future/2020/future-of-tech-economy.html
Gaskin, J., Berente, N., Lyytinen, K., & Yoo, Y. (2014). Toward generalizable sociomaterial inquiry. MIS Quarterly , 38 (3), 849–872. https://doi.org/10.25300/MISQ/2014/38.3.10
George, J. F., & Kohnke, E. (2018). Personal health record systems as boundary objects. Communication of the Association for Information Systems , 42 (1), 21–50. https://doi.org/10.17705/1CAIS.04202
Ghanvatkar, S., & Rajan, V. (2019). Deep recurrent neural networks for mortality prediction in intensive care using clinical time series at multiple resolution. International Conference on Information Systems (ICIS), 1–18.
Gimpel, H., Nißen, M., & Görlitz, R. A. (2013). Quantifying the quantified self: a study on the motivation of patients to track their own health. International Conference on Information Systems (ICIS), 1–17.
Glaser, B. G., Strauss, A. L., & Strutzel, E. (1968). The discovery of grounded theory; strategies for qualitative research. Nursing Research, 17 (4), 364.
Greenwood, F. (2020, March). Google Want Your Data in Exchange for a Coronavirus Test. Foreign Policy. https://foreignpolicy.com/2020/03/30/google-personal-health-data-coronavirus-test-privacy-surveillance-silicon-valley/
Grondin, J. (2016). What is the hermeneutical cycle? In N. Keane & C. Lawn (Eds.), The Blackwell Companion to Hermeneutics, 299–305. Oxford, UK: Blackwell Publishing.
Hacklin, F. (2008). Management of Convergence in Innovation: Strategies and Capabilities for Value Creation Beyond Blurring Industry Boundaries . Zurich, Switzerland: Physica.
Hafermalz, E., & Riemer, K. (2016). Negotiating distance: "presencing work” in a case of remote telenursing. International Conference on Information Systems(ICIS), 1–13.
Hamari, J., & Koivisto, J. (2015). Why do people use gamification services? International Journal of Information Management, 35 (4), 419–431. https://doi.org/10.1016/j.ijinfomgt.2015.04.006
Heine, C., Herrler, R., Petsch, M., & Anhalt, C. (2003). ADAPT: Adaptive Multi-Agent Process Planning and Coordination of Clinical Trials. Americas Conference on Information Systems (AMCIS), 1823–1834.
Holland, S., Phimphachanh, C., Conn, C., & Segall, M. (1996). Impact of economic and institutional reforms on the health sector in Laos: implications for health system management. IDS Publications, Institute of Development Studies, 28 , 133–154.
Huerta, T. R., Thompson, M. A., Ford, E. W., & Ford, W. F. (2013). Electronic health record implementation and hospitals’ total factor productivity. Decision Support Systems, 55 (2), 450–458. https://doi.org/10.1016/j.dss.2012.10.004
Humphrey, S. E. (2011). What does great meta-analysis look like? Organizational Psychology Review, 1 (2), 99–103. https://doi.org/10.1177/2041386611401273
Idrissi, T. E., Idri, A., & Bakkoury, Z. (2019). Systematic map and review of predictive techniques in diabetes self-management. International Journal of Information Management, 46 , 263–277. https://doi.org/10.1016/j.ijinfomgt.2018.09.011
Kenny, C., & Connolly, R. (2016). Drivers of health information privacy concern: a comparison study. Americas Conference on Information Systems (AMCIS), 1–10.
Kernick, D., & Mitchell, A. (2009). Working with lay people in health service research: a model of co-evolution based on complexity theory. Journal of Interprofessional Care, 24 (1), 31–40. https://doi.org/10.3109/13561820903012073
Kim, S. H., & Kwon, J. (2019). How Do EHRs and a meaningful use initiative affect breaches of patient information? Information Systems Research, 30 (4), 1107–1452. https://doi.org/10.1287/isre.2019.0858
Kim, S. (1992). Downward causation in emergentism and non-reductive physicalism. In A. Beckermann, H. Flohr, & J. Kim (Eds.). Emergence or Reduction. Essays on the Prospects of Nonreductive Physicalism (118–138). Berlin, Germany: de Gryuter.
King, N. (2009). An initial exploration of stakeholder benefit dependencies in ambulatory ePrescribing. Americas Conference on Information Systems (AMCIS), 1–10.
Klecun, E., Zhou, Y., Kankanhalli, A., Wee, Y. H., & Hibberd, R. (2019). The dynamics of institutional pressures and stakeholder behavior in national electronic health record implementations: a tale of two countries. Journal of Information Technology, 34 (4), 292–332. https://doi.org/10.1177/0268396218822478
Knight, J., Patrickson, M., & Gurd, B. (2008). Towards understanding apparent South Australian GP resistance to adopting Health Informatics systems. Australasian Conference on Information Systems (ACIS), 492–501.
Kozlowski, S. W. J., Chao, G. T., Grand, J. A., Braun, M. T., & Kulijanin, G. (2013). Advancing multilevel research design: capturing the dynamics of emergence. Organizational Research Methods, 16 (4), 581–615. https://doi.org/10.1177/1094428113493119
Landi, H. (2020, April). Alphabet’s Verily rolls out COVID screening tool for health systems . FierceHealthcare. https://www.fiercehealthcare.com/tech/alphabet-s-verily-rolls-out-covid-screening-tool-for-health-systems
Lebcir, R. M., Choudrie, J., Atum, R. A., & Corker, R. J. (2008). Examining HIV and tuberculosis using a decision support systems computer simulation model: the case of the Russian Federation. Americas Conference on Information Systems (AMCIS), 1–18.
Lee, D., & Nilsson, P. (2020, March). Amazon auditions to be “the new Red Cross” in Covid-19 crisis . Financial Times. https://www.ft.com/content/220bf850-726c-11ea-ad98-044200cb277f
Lee, A. S., Thomas, M., & Baskerville, R. L. (2015). Going back to basics in design science: from the information technology artifact to the information systems artifact. Information Systems Journal, 25 (1), 5–21. https://doi.org/10.1111/isj.12054
Lee, C. H., Venkatraman, N., Tanriverdi, H., & Iyer, B. (2013). Complementary-based hypercompetition in the software industry. Strategic Management Journal, 31 (13), 1431–1356. https://doi.org/10.1002/smj.895
Leon, M. C., Nieto-Hipolito, J. I., Garibaldi-Beltran, J., Amaya-Parra, G., Luque-Morales, P., Magana-Espinoza, P., & Aquilar-Velazco, J. (2016). Designing a model of a digital ecosystem for healthcare and wellness using the BM canvas. Journal of Medical Systems, 40 (6), 144–154. https://doi.org/10.1007/s10916-016-0488-3
LeRouge, C., Mantzana, V., & Wilson, E. V. (2007). Healthcare information systems research, revelations and visions. European Journal of Information Systems, 16 (6), 669–671. https://doi.org/10.1057/palgrave.ejis.3000712
Leroy, J., Cova, B., & Salle, R. (2013). Zooming in VS zooming out on value co-creation: consequences for BtoB research. Industrial Marketing Management, 42 (7), 1102–1111. https://doi.org/10.1016/j.indmarman.2013.07.006
Li, L., Jeng, L., Naik, H. A., Allen, T., & Frontini, M. (2008). Creation of environmental health information system for public health service: a pilot study. Information Systems Frontiers, 10 (5), 531–542. https://doi.org/10.1007/s10796-008-9108-1
Lichtenberg, S., Greve, M., Brendel, A. B., & Kolbe, L. M. (2019). Towards the design of a mobile application to support decentralized healthcare in developing countries – The case of diabetes care in eSwatini. Americas Conference on Information Systems (AMCIS), 1–10.
Lin, Y.-K., Chen, H., Brown, R. A., Li, S.-H., & Yang, H.-J. (2017). Healthcare predictive analytics for risk profiling in chronic care: a Bayesian multitask learning approach. MIS Quarterly , 41 (2), 473–495. https://doi.org/10.25300/MISQ/2017/41.2.07
MacLure, M. (2005). Clarity bordering on stupidity: where’s the quality in systematic review? Journal of Education Policy, 20 (4), 393–416. https://doi.org/10.4324/9780203609156
Maheshwari, M., Hassan, T., & Chatterjee, S. (2006). A framework for designing healthy lifestyle management information system. Americas Conference on Information Systems (AMCIS), 2811–2817.
Matavire, R., & Brown, I. (2008). Investigating the use of “Grounded Theory” in information systems research. Proceedings of the 2008 annual research conference of the South African Institute of Computer Scientists and Information Technologists on IT research in developing countries, 139–147. https://doi.org/10.1145/1456659.1456676
Mitsa, T., Fortier, P. J., Shrestha, A., Yang, G., & Dluhy, N. M. (2007). Information systems and healthcare XXI: a dynamic, client-centric, point-of-care system for the novice nurse. Communication of the Association for Information Systems , 19 , 740–761. https://doi.org/10.17705/1CAIS.01936
Motamarri, S., Akter, S., Ray, P., & Tseng, C.-L. (2014). Distinguishing “mHealth” from other healthcare services in a developing country: a study from the service quality perspective. Communication of the Association for Information Systems , 34 (1), 669–692. https://doi.org/10.17705/1CAIS.03434
Mun, C., & Lee, O. (2017). Integrated supporting platform for the visually impaired: using smart devices. International Conference on Information Systems (ICIS), 1–18.
Nambisan, S., Lyytinen, K., Majchrzak, A., & Song, M. (2017). Digital innovation management: reinventing innovation management research in a digital world. MIS Quarterly , 41 (1), 223–238. https://doi.org/10.25300/MISQ/2017/41:1.03
Neben, T., Seeger, A. M., Kramer, T., Knigge, S., White, A. J., & Alpers, G. W. (2016). Make the most of waiting: theory-driven design of a pre-psychotherapy mobile health application. Americas Conference on Information Systems (AMCIS), 1–10.
Nicholls-Nixon, C. L., & Jasinski, D. (1995). The blurring of industry boundaries: an explanatory model applied to telecommunications. Industrial and Corporate Change, 4 (4), 755–768. https://doi.org/10.1093/icc/4.4.755
Offermann, P., Blom, S., Schönherr, M., & Bub, U. (2010). Artifact types in information systems design science – a literature review. International Conference on Design Science Research in Information Systems, 77–92. https://doi.org/10.1007/978-3-642-13335-0_6
Palvia, P., Kakhki, M. D., Ghoshal, T., Uppala, V., & Wang, W. (2015). Methodological and topic trends in information systems research: a meta-analysis of IS journals. Communication of the Association for Information Systems , 37 (30), 630–650. https://doi.org/10.17705/1CAIS.03730
Park, H. A. (2016). Are we ready for the fourth industrial revolution? Yearbook of Medical Informatics , (1), 1–3. https://doi.org/10.15265/IY-2016-052
Patel, M., Shah, A., Shah, K., & Plachkinova, M. (2018). Designing a mobile app to help young adults develop and maintain mental well-being. Americas Conference on Information Systems (AMCIS), 1–10.
Paul, L. D., & McDaniel, R. R. J. (2004). A field study of the effect of interpersonal trust on virtual collaborative relationship performance. MIS Quarterly, 28 (2), 183–227. https://doi.org/10.2307/25148633
Peffers, K., Tuunanen, T., Rothenberger, M. A., & Chatterjee, S. (2008). A design science research methodology for information systems research. Journal of Management Information Systems, 24 (3), 45–78. https://doi.org/10.2753/MIS0742-1222240302
Pletikosa, I., Kowatsch, T., Büchter, D., Brogle, B., Dintheer, A., Wiegand, D., Durrer, D., l'Allemand-Jander, D., Schutz, Y., Maass, W. (2014). Health information system for obesity prevention and treatment of children and adolescents. European Conference on Information Systems (ECIS), 1–13.
Preko, M., Boateng, R., & Effah, J. (2019). Health informatics and brain drain mitigation in Ghana. Americas Conference on Information Systems (AMCIS), 1–10.
Rivard, P. E., Rosen, A. K., & Carroll, J. S. (2006). Enhancing patient safety through organizational learning: are patient safety indicators a step in the right direction? Health Services Research , 41(4p2), 1633–1653. https://doi.org/10.1111/j.1475-6773.2006.00569.x
Rodon, J., & Silva, L. (2015). Exploring the formation of a healthcare information infrastructure: hierarchy or meshwork? Journal of the Association for Information System, 16 (5), 394–417. https://doi.org/10.17705/1JAIS.00395
Roehrig, S., & Knorr, K. (2000). Toward a secure web based health care application. European Conference on Information Systems (ECIS), 1–8. https://doi.org/10.4018/978-1-930708-13-6.ch007
Romanow, D., Rai, A., & Keil, M. (2018). CPOE-Enabled Coordination: appropriation for deep structure use and impacts on patient outcomes. MIS Quarterly , 42 (1), 189–212. https://doi.org/10.25300/MISQ/2018/13275
Ryan, J., Doster, B., Daily, S., & Lewis, C. (2019). Seeking operational excellence via the digital transformation of perioperative scheduling. Americas Conference on Information Systems (AMCIS), 1–10.
Rycroft, R. W., & Kash, D. E. (2004). Self-organizing innovation networks: implications for globalization. Technovation, 24 (3), 187–197. https://doi.org/10.1016/S0166-4972(03)00092-0
Salthe, S. N. (1985). Evolving Hierarchical Systems . Columbia University Press. https://doi.org/10.7312/salt91068
Samentinger, J., Rozenblit, J., Lysecky, R., & Ott, P. (2015). Security challenges for medical devices. Communications of the Association for Information Systems, 58 (4), 74–82. https://doi.org/10.1145/2667218
Saunders, B., Sim, J., Kingstone, T., Baker, S., Waterfield, J., Bartlam, B., Burroughs, H., & Jinks, C. (2018). Saturation in qualitative research: exploring its conceptualization and operationalization. Quality & Quantity, 52 (4), 1893–1907. https://doi.org/10.1007/s11135-017-0574-8
Schweiger, A., Sunyaev, A., Leimeister, J. M., & Krcmar, H. (2007). Information systems and healthcare XX: toward seamless healthcare with software agents. Communications of the Association for Information Systems , 19 (33), 392–710. https://doi.org/10.17705/1CAIS.01933
Schwetschke, S., & Durugbo, C. (2018). How firms synergise: understanding motives and management of co-creation for business-to-business services. International Journal of Technology Management, 76 (3–4), 258–284. https://doi.org/10.1504/IJTM.2018.091289
Setia, P., Setia, M., Krishnan, R., & Sambamurthy, V. (2011). The effects of the assimilation and use of IT applications on financial performance in healthcare organizations. Journal of the Association for Information System , 12 (Special Issue), 274–298. https://doi.org/10.17705/1jais.0060
Shahmoradi, L., Safadari, R., & Jimma, W. (2017). Knowledge management implementation and the tools utilized in healthcare for evidence-based decision making: A systematic review. Ethiopian Journal of Health Sciences, 27 (5), 541–558. https://doi.org/10.4314/ejhs.v27i5.13
Sherer, S. A. (2014). Patients are not simply health it users or consumers: the case for “e Healthicant” applications. Communications of the Association for Information systems , 34(1), 17. https://doi.org/10.17705/1CAIS.03417 .
Singh, R., Mathiassen, L., Stachura, M. E., & Astapova, E. V. (2011). Dynamic capabilities in home health: IT-enabled transformation of post-acute care. Journal of the Association for Information System , 12 (2), 163–188. https://doi.org/10.17705/1jais.00257
Sujanto, F., F., B., Ceglowski, A., & Churilov, L. (2008). Application of domain ontology for decision support in medical emergency coordination. Americas Conference on Information Systems (AMCIS), 1–10.
Theobalt, A., Emrich, A., Werth, D., & Loos, P. (2013). A conceptual architecture for an ICT-based personal health system for cardiac rehabilitation. Americas Conference on Information Systems (AMCIS), 1–10.
Therrien, M.-C., Normandin, J.-M., & Denis, J.-L. (2017). Bridging complexity theory and resilience to develop surge capacity in health systems. Journal of Health Organisation and Management, 31 (1), 96–109. https://doi.org/10.1108/JHOM-04-2016-0067
Tillett, A. (2020, April). Amazon to store data from virus tracing app. Financial Review. https://www.afr.com/politics/federal/amazon-to-store-data-from-virus-tracing-app-20200424-p54mwq
Tokar, O., Batoroev, K., & Böhmann, T. (2015). A framework for analyzing patient-centered mobile applications for mental health. Americas Conference on Information Systems (AMCIS), 1–15.
Tsai, J. M., Cheng, M. J., Tsai, H. H., Hung, S. W., & Chen, Y. L. (2019). Acceptance and resistance of telehealth: the perspective of dual-factor concepts in technology adoption. International Journal of Information Management, 49 , 34–44. https://doi.org/10.1016/j.ijinfomgt.2019.03.003
Ure, J., Procter, R., Lin, Y. W., Hartswood, M., Anderson, S., Lloyd, S., Wardlaw, J., Gonzalez-Velez, H., & Ho, K. (2009). The development of data infrastructures for eHealth: a socio-technical perspective. Journal of the Association for Information Systems , 10 (5), 415–429. https://doi.org/10.17705/1jais.00197
Varshney, U. (2004). Using wireless networks for enhanced monitoring of patients. Americas Conference on Information Systems (AMCIS), 1–10. https://doi.org/10.1504/IJHTM.2005.007009
Volland, D., Korak, K., & Kowatsch, T. (2014). A health information system that extends healthcare professional-patient communication. European Conference on Information Systems (ECIS), 1–10.
vom Brocke, J., Simons, A., Reimer, K., Niehaves, B., Plattfaut, R., & Cleven, A. (2015). Standing on the shoulders of giants: challenges and recommendations of literature search in information systems research. Communications of the Association for Information Systems, 37 (1), 205–224. https://doi.org/10.17705/1CAIS.03709
vom Brocke, J., Simons, A., Niehaves, B., Reimer, K., Plattfaut, R., & Cleven, A. (2009): Reconstructing the giant: on the importance of rigour in documenting the literature search process. European Conference on Information Systems (ECIS) , 1–12.
Walsh, D., & Downe, S. (2005). Meta-synthesis method for qualitative research: a literature review, methodological issues in nursing. Journal of Advanced Nursing, 50 (2), 204–211. https://doi.org/10.1111/j.1365-2648.2005.03380.x
Webster, J., & Watson, R. T. (2002). Analyzing the past to prepare for the future: writing a literature review. MIS Quarterly, 26 (2), 13–23. https://doi.org/10.2307/4132319
Werts, N., & Adya, M. (2000). Data mining in healthcare: issues and a research agenda. Americas Conference on Information Systems (AMCIS), 98.
Wessel, L., Gersch, M., & Harloff, E. (2017). Talking past each other - a discursive approach to the formation of societal-level information pathologies in the context of the electronic health card in Germany. Business & Information Systems Engineering, 59 (1), 23–40. https://doi.org/10.1007/s12599-016-0462-0
Winter, S. J., & Butler, B. S. (2011). Creating bigger problems: grand challenges as boundary objects and the legitimacy of the information systems field. Journal of Information Technology, 26 (2), 99–108. https://doi.org/10.1057/jit.2011.6
Wolfswinkel, J. F., Furtmueller, E., & Wilderom, C. P. M. (2013). Using grounded theory as a method for rigorously reviewing literature. European Journal of Information Systems, 22 (1), 45–55. https://doi.org/10.1057/ejis.2011.51
Malpass, D., (2020, March). Coronavirus highlights the need to strengthen health systems. Worldbank Blogs. https://blogs.worldbank.org/voices/coronavirus-covid19-highlights-need-strengthen-health-systems
Wu, I.-L., & Hu, Y.-P. (2012). Examining knowledge management enabled performance for hospital professionals: a dynamic capability view and the mediating role of process capability. Journal of the Association for Information System , 13 (12), 976–999. https://doi.org/10.17705/1jais.00319
Yang, A., & Varshney, U. (2016). A taxonomy for mobile health implementation and evaluation. Americas Conference on Information Systems (AMCIS), 1–10.
Zafar, H., & Sneha, S. (2012). Ubiquitous healthcare information system: toward crossing the security chasm. Communication of the Association for Information Systems , 31 (9), 193–206. https://doi.org/10.17705/1CAIS.03109
Zhang, L., & Pang, M. S. (2019). Does sharing make my data more insecure? An empirical study on health information exchange and data breaches. International Conference on Information Systems (ICIS), 1–14.
Download references
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and affiliations.
Chair for Digitalization and Process Management, Philipps-University Marburg, Universitätsstraße 24, 35037, Marburg, Germany
Nadine Ostern
Frankfurt School of Finance & Management, ProcessLab, Adickesallee 32-34, 60322, Frankfurt am Main, Germany
Guido Perscheid, Caroline Reelitz & Jürgen Moormann
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Nadine Ostern .
Additional information
Responsible Editor: Shengnan Han
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The original online version of this article was revised: In this article the affiliation of authors are incorrect. Given here are the correct affiliations.
Supplementary Information
Below is the link to the electronic supplementary material.
Supplementary file1 (DOCX 195 KB)
Rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Ostern, N., Perscheid, G., Reelitz, C. et al. Keeping pace with the healthcare transformation: a literature review and research agenda for a new decade of health information systems research. Electron Markets 31 , 901–921 (2021). https://doi.org/10.1007/s12525-021-00484-1
Download citation
Received : 11 December 2020
Accepted : 26 May 2021
Published : 17 July 2021
Issue Date : December 2021
DOI : https://doi.org/10.1007/s12525-021-00484-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Health information systems research
JEL Classifications
- Find a journal
- Publish with us
- Track your research

An official website of the United States government
Here’s how you know
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
Office of the Assistant Secretary for Planning and Evaluation
Health Information Technology (HIT)
Displaying 1 - 10 of 34. 10 per page. Page 1.
Health Information Technology Adoption and Utilization in Long-Term and Post-Acute Care Settings
Updated medicare ffs telehealth trends by beneficiary characteristics, visit specialty and state, 2019-2021, report to congress: current state of technology-enabled collaborative learning and capacity building models, health information exchange in long-term and post-acute care settings: final report, long-term and post-acute care providers engaged in health information exchange: final report, ehr payment incentives for providers ineligible for payment incentives and other funding study, assessing the status and prospects of state and local health department information technology infrastructure, web-based benefit access tools: mitigating barriers for special needs populations, web-based screeners and applications: potential tools for improving benefit access and program efficiency, promoting public benefits access through web-based tools and outreach: a national scan of efforts. volume ii: detailed summary tables of benefits access efforts.

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Health Information Technology
Health information technology (health IT) involves the processing, storage, and exchange of health information in an electronic environment. Widespread use of health IT within the health care industry will improve the quality of health care, prevent medical errors, reduce health care costs, increase administrative efficiencies, decrease paperwork, and expand access to affordable health care. It is imperative that the privacy and security of electronic health information be ensured as this information is maintained and transmitted electronically.
Cloud Computing

With the proliferation and widespread adoption of cloud computing solutions, HIPAA covered entities and business associates are questioning whether and how they can take advantage of cloud computing while complying with regulations protecting the privacy and security of electronic protected health information (ePHI). HHS has developed guidance to assist such entities, including cloud services providers (CSPs), in understanding their HIPAA obligations .
HIPAA Privacy Components of the Privacy and Security Toolkit
The materials below are the HIPAA privacy components of the Privacy and Security Toolkit developed in conjunction with the Office of the National Coordinator. The Privacy and Security Toolkit implements the principles in The Nationwide Privacy and Security Framework for Electronic Exchange of Individually Identifiable Health Information (Privacy and Security Framework). These guidance documents discuss how the Privacy Rule can facilitate the electronic exchange of health information.
- Privacy and Security Framework: Correction Principle and FAQs
- Privacy and Security Framework: Openness and Transparency Principle and FAQs
- Privacy and Security Framework: Individual Choice Principle and FAQs
- Privacy and Security Framework: Collection, Use, and Disclosure Limitation Principle and FAQs
- Privacy and Security Framework: Safeguards Principle and FAQs
- Privacy and Security Framework: Accountability Principle and FAQs
Learn more about the Privacy and Security Framework and view other documents in the Privacy and Security Toolkit, as well as other health information technology resources.

Top 400 Information Technology Research Topics – Full Guide!
The field of IT is progressive and ever-changing due to the rapid development of hardware, software, and networking technologies. The demand for innovative research in IT has also continued to rise as businesses and organizations embrace digital systems and data-driven solutions.
Understanding the salient areas of study in IT will help professionals keep up with changes that arise and enable organizations to leverage emerging technologies effectively.
Cybersecurity, artificial intelligence, cloud computing , and big data analytics have emerged through IT research. These fundamental factors shape the modern technology landscape, giving rise to immense possibilities for boosting productivity, raising efficiency, and improving competitiveness across sectors.
However, companies wanting to navigate the complexities of today’s digital age and exploit new technological advances must examine some of the latest IT research topics.
Understanding Information Technology Research
Table of Contents
In the world of technology, research is a compass that helps us navigate its convoluted evolutions. For instance, Information Technology (IT) research has been conducted in computer science, software engineering, data analytics, and cybersecurity.
IT research involves systematic inquiry to advance knowledge, problem-solving, and innovation. This includes conducting rigorous experiments and analyzing results to unveil new theories or approaches that improve technologies or bring breakthroughs.
Therefore, interdisciplinarity is at the core of IT research, with collaboration cutting across various disciplines. Whether using AI to reinforce cyber security or big data analytics in healthcare, collaboration leads to solutions to complex problems.
This is because IT research is changing rapidly due to technological advances. Thus, researchers need to be up-to-date to make meaningful contributions.
Ethics are involved so that technology can be responsibly deployed. The researchers grapple with privacy, security, bias, and equity issues to ensure technology benefits society.
As a result of this publication and conferences, which enable dissemination of findings, leading to further innovations, collaboration has supported progress, hence speeding it up.
Understanding IT research is vital for leveraging technology to address societal challenges and foster positive change.
Recommended Readings: “ Top 109+ Media Bias Research Topics | Full Guide! “.
Picking the Right Topic to Research: The Key to Finding New Things
In the always-changing world of information technology, choosing the proper topic to research is like starting a smart path. It’s a big decision that sets where your hard work will go and how much your findings could mean.
Fitting with Industry Moves and Issues
Finding a research topic that fits current industry moves and big issues is important. By staying informed on the latest happenings and problems in the technology field, you can ensure your research stays useful and helps solve real-world troubles.
Growing Fresh Ideas and Practical Uses
Choosing a research topic that generates fresh ideas and practical applications is crucial. Your findings should not just add to school talks but also lead to real solutions that can be used in real situations, pushing technology forward and making work smoother.
Sparking Mind Curiosity and Excitement
Selecting a research topic that sparks your curiosity and excitement is essential. When you dive into an area that truly fascinates you, the research journey becomes more engaging, and your drive to uncover big insights is stronger.
Finding Gaps and Unexplored Areas
Finding gaps in existing knowledge or unexplored areas in the technology landscape can lead to big discoveries. Entering uncharted spaces can uncover fresh insights and meaningfully advance the field.
Considering Potential Wide Effect and Growth
Considering your research topic’s potential wide effect and growth is crucial. Will your findings have far-reaching effects across industries? Can your solutions grow and shift to address changing challenges? Evaluating these things can help you prioritize research areas with the greatest potential for big impact.
By carefully choosing the right research topic, you can open the door to discoveries, push technology forward, and contribute to the constant evolution of the technology information landscape.
Top 400 Information Technology Research Topics
The list of the top 400 information technology research topics is organized into different categories. Let’s examine it.
Artificial Intelligence (AI) and Machine Learning (ML)
- Easy AI: Explaining and Using
- Group Learning: Getting Better Together
- AI in Health: Diagnosing and Helping
- Robots Learning on Their Own
- Being Fair with Computers
- Talking to Computers in Normal Language
- AI Fighting Bad Guys on the Internet
- AI Driving Cars: How Safe Is It?
- Sharing What We’ve Learned with Other Machines
- AI in Schools: Computers Learning About You
Cybersecurity and Encryption
- Trusting Computers: How to Stay Safe
- Keeping Secrets Safe with Fancy Math
- Secret Codes Computers Use: Safe or Not?
- Spy Games: Watching Out for Bad Stuff
- Keeping Secrets, Even from Friends
- Your Body as Your Password: Is It Safe?
- Fighting Against Computer Ransomers
- Keeping Your Secrets Secret, Even When Sharing
- Making Sure Your Smart Stuff Isn’t Spying on You
- Insuring Against Computer Bad Luck
Data Science and Big Data
- Sharing Secrets: How to Be Safe
- Watching the World in Real-Time
- Big Data: Big Computers Handling Big Jobs
- Making Data Pretty to Look At
- Cleaning Up Messy Data
- Predicting the Future with Numbers
- Finding Patterns in Connected Dots
- Keeping Your Secrets Safe in Big Data
- Sharing Our Secrets Without Telling Anyone
- Helping the Planet with Numbers
Cloud Computing
- Computers Without a Home: Where Do They Live?
- Keeping Computers Close to Home
- Moving Our Stuff to New Homes
- Juggling Many Clouds at Once
- Making Computers That Live in the Cloud
- Keeping Clouds Safe from Bad Guys
- Keeping Clouds Safe from Sneaky Spies
- Making Sure Clouds Do What They’re Supposed To
- Computers Need Energy Too!
- Making the Internet of Things Even Smarter
Internet of Things (IoT)
- Smart Stuff Everywhere: How Does It Work?
- Watching Out for Bad Stuff in Smart Things
- Smart Stuff: Is It Safe?
- Taking Care of Smart Toys
- Making Smart Things That Don’t Need Batteries
- Making Smart Factories Even Smarter
- Smart Cities: Making Cities Better Places to Live
- Your Clothes Can Be Smart, Too!
- Helping Farmers with Smart Farming
- Keeping Secrets Safe in Smart Stuff
Human-Computer Interaction (HCI)
- Magic Glasses: How Do They Work?
- Making Computers Easy to Use
- Making Computers for Everyone
- Talking to Computers with Your Hands
- Making Sure Computers Are Nice to People
- Talking to Computers with Your Voice
- Playing with Computers, You Can Touch
- Trusting Computers to Drive for Us
- Computers That Understand Different People
- Making Computers That Read Our Minds
Software Engineering
- Making Computers Work Together Smoothly
- Building Computers from Tiny Pieces
- Playing Games to Make Computers Better
- Making Sure Computers Work Right
- Making Old Computers New Again
- Making Computers Like to Exercise
- Making Computers Easier to Understand
- Building Computers with Blueprints
- Making Sure Computers Don’t Get Sick
- Sharing Computer Secrets with Everyone
Mobile Computing
- Keeping Phones Safe from Bad Guys
- Making Apps for Every Kind of Phone
- Keeping Phones Safe in the Cloud
- Finding Your Way with Your Phone
- Paying with Your Phone: Safe or Not?
- Checking Your Health with Your Phone
- Seeing the World Through Your Phone
- Wearing Your Phone on Your Wrist
- Learning on the Go with Your Phone
- Making Phones Even Smarter with Clouds
Networking and Communications
- Making Sure Computers Can Talk to Each Other
- Making Computers Work Together Without Wires
- Making the Internet Faster for Everyone
- Getting More Internet Addresses for More Computers
- Cutting the Internet into Pieces
- Making the Internet Even More Invisible
- Talking to Computers with Light
- Making Sure Tiny Computers Talk to Each Other
- Sending Messages Even When It’s Hard
- Making the Radio Smarter for Computers
Bioinformatics and Computational Biology
- Reading Your DNA with Computers
- Making Medicine Just for You
- Meeting the Microscopic World with Computers
- Building Computer Models of Living Things
- Finding New Medicine with Computers
- Building Computer Models of Tiny Machines
- Making Family Trees for Living Things
- Counting Germs with Computers
- Making Big Lists of Living Things
- Making Computers Think Like Brains
Quantum Computing
- Making Computers Better at Some Math Problems
- Keeping Computers Safe from Small Mistakes
- Making Computers Even Harder to Spy On
- Making Computers Learn Faster with Quantum Tricks
- Making Fake Worlds for Computers to Explore
- Building Computers from Super-Cold Stuff
- Making Computers Cold to Think Better
- Making Computers Think Like Chemists
- Making the Internet Even Safer with Computers
- Showing Off What Computers Can Do Best
Green Computing
- Saving Energy with Computers
- Using Wind and Sun to Power Computers
- Making Phones Last Longer Without Plugging In
- Making Computers Kinder to the Planet
- Recycling Old Computers to Save the Earth
- Computers That Care About Their Trash
- Saving Energy in Big Rooms Full of Computers
- Making Computers Save Energy and Work Faster
- Counting the Trash from Computers
- Making Computers Kinder to the Planet’s Air
Information Systems
- Making Computers Work Together in Big Companies
- Making Computers Remember Their Friends
- Making Computers Share What They Know
- Making Computers Smart About Money
- Making Computers Send Presents to Their Friends
- Helping Computers Make Big Decisions
- Making Government Computers Talk to Each Other
- Making Computers Count Likes and Shares
- Assisting computers to Find What You Asked For
- Assisting companies to Keep Their Friends Happy
Semantic Web and Linked Data
- Making Computers Understand Each Other Better
- Making Computers Talk About Themselves
- Making the Internet More Friendly for Computers
- Helping Computers Find What They Need
- Making Computers Smarter by Talking to Each Other
- Making Computers Friends with Different Languages
- Making Computers Understand Different Ideas
- Making Computers Think Like Us
- Making Computers Smarter About Old Stuff
- Making Computers Share Their Secrets Safely
Social Computing and Online Communities
- Making Friends on the Internet
- Getting Good Suggestions from the Internet
- Making Computers Work Together to Solve Problems
- Learning from Your Friends on the Internet
- Stopping Fake News on the Internet
- Knowing How People Feel on the Internet
- Helping Each Other on the Internet During Emergencies
- Making Sure Computers Are Nice to Everyone
- Keeping Secrets on the Internet
- Making the Internet a Better Place for Everyone
Game Development and Virtual Worlds
- Making Games That Play Fair
- Letting Computers Make Their Fun
- Making Fake Worlds for Fun
- Learning with Games
- Making the Rules for Fun
- Watching How People Play Together
- Seeing Things That Aren’t There
- Letting Lots of People Play Together
- Making the Engines for Fun
- Playing Games to Learn
E-Learning and Educational Technology
- Making Learning Easy for Everyone
- Taking Classes on the Internet
- Learning from Your Computer’s Teacher
- Learning from What Computers Know
- Learning Anywhere with Your Computer
- Making Learning Fun with Games
- Learning Without a Real Lab
- Learning with Free Stuff on the Internet
- Mixing School with Your Computer
- Making School More Fun with Your Computer
Digital Forensics and Incident Response
- Solving Computer Mysteries
- Looking for Clues in Computers
- Finding Bad Guys on the Internet
- Looking for Clues on Phones and Tablets
- Hiding Clues on Computers
- Helping When Computers Get Sick
- Solving Mysteries While the Computer Is On
- Finding Clues on Your Smart Watch
- Finding Tools for Finding Clues
- Following the Rules When Solving Mysteries
Wearable Technology and Smart Devices
- Keeping Healthy with Smart Watches
- Making Clothes That Talk to Computers
- Listening to the Earth with Your Shirt
- Wearing Glasses That Show Cool Stuff
- Making Your Home Smarter with Your Phone
- Using Your Body to Unlock Your Phone
- Helping People Move with Special Shoes
- Assisting people to See with Special Glasses
- Making Your Clothes Do More Than Keep You Warm
- Keeping Secrets Safe on Your Smart Stuff
Robotics and Automation
- Making Friends with Robots
- Letting Robots Do the Hard Work
- Robots That Work Together Like Ants
- Learning Tricks from People
- Robots That Feel Like Jelly
- Helping Doctors and Nurses with Robots
- Robots That Help Farmers Grow Food
- Making Cars Without People
- Teaching Robots to Recognize Things
- Robots That Learn from Animals
Health Informatics
- Computers That Help Doctors Keep Track of Patients
- Sharing Secrets About Your Health with Other Computers
- Seeing the Doctor on Your Computer
- Keeping Track of Your Health with Your Phone
- Making Medicine Better with Computers
- Keeping Your Health Secrets Safe with Computers
- Learning About Health with Computers
- Keeping Health Secrets Safe on the Internet
- Watching Out for Germs with Computers
- Making Sure the Doctor’s Computer Plays Nice
Geographic Information Systems (GIS)
- Watching the World Change with Computers
- Making Maps on the Internet
- Seeing the World from Very Far Away
- Finding Hidden Patterns with Computers
- Making Cities Better with Computers
- Keeping Track of the Earth with Computers
- Keeping Track of Wild Animals with Computers
- Making Maps with Everyone’s Help
- Seeing the World in 3D
- Finding Things on the Map with Your Phone
Knowledge Management
- Helping Computers Remember Things
- Making Computers Talk About What They Know
- Finding Secrets in Big Piles of Data
- Helping Companies Remember What They Know
- Sharing Secrets with Computers at Work
- Making Computers Learn from Each Other
- Making Computers Talk About Their Friends
- Making Companies Remember Their Secrets
- Keeping Track of What Companies Know
Computational Linguistics and Natural Language Processing (NLP)
- Finding Out How People Feel on the Internet
- Finding Names and Places in Stories
- Making Computers Talk to Each Other
- Making Computers Answer Questions
- Making Summaries for Busy People
- Making Computers Understand Stories
- Making Computers Understand Pictures and Sounds
- Making Computers Learn New Words
- Making Computers Remember What They Read
- Making Sure Computers Aren’t Mean to Anyone
Information Retrieval and Search Engines
- Finding Stuff on the Internet
- Getting Suggestions from the Internet
- Finding Stuff at Work
- Helping Computers Find Stuff Faster
- Making Computers Understand What You Want
- Finding Stuff on Your Phone
- Finding Stuff When You’re Moving
- Finding Stuff Near Where You Are
- Making Sure Computers Look Everywhere for What You Want
Computer Vision
- Finding Stuff in Pictures
- Cutting Up Pictures
- Watching Videos for Fun
- Learning from Lots of Pictures
- Making Pictures with Computers
- Finding Stuff That Looks Like Other Stuff
- Finding Secrets in Medical Pictures
- Finding Out If Pictures Are Real
- Looking at People’s Faces to Know Them
Quantum Information Science
- Making Computers Learn Faster with Tricks
Social Robotics
- Robots That Help People Who Have Trouble Talking
- Robots That Teach People New Things
- Making Robots Work with People
- Helping Kids Learn with Robots
- Making Sure Robots Aren’t Mean to Anyone
- Making Robots Understand How People Feel
- Making Friends with Robots from Different Places
- Making Sure Robots Respect Different Cultures
- Helping Robots Learn How to Be Nice
Cloud Robotics
- Making Robots Work Together from Far Away
- Making Robots Share Their Toys
- Making Robots Do Hard Jobs in Different Places
- Making Robots Save Energy
- Making Robots Play Together Nicely
- Making Robots Practice Being Together
- Making Sure Robots Play Fair
- Making Robots Follow the Rules
Cyber-Physical Systems (CPS)
- Making Robots Work Together with Other Things
- Keeping Robots Safe from Small Mistakes
- Keeping Factories Safe from Bad Guys
- Making Sure Robots Respect Different People
- Making Sure Robots Work Well with People
- Keeping Robots Safe from Bad Guys
- Making Sure Robots Follow the Rules
Biomedical Imaging
- Taking Pictures of Inside You with Computers
- Seeing Inside You with Computers
- Cutting Up Pictures of Inside You
- Finding Problems Inside You with Computers
- Cutting Up Pictures and Putting Them Together
- Counting Inside You with Pictures
- Making Pictures to Help Doctors
- Making Lists from Pictures Inside You
- Making Sure Pictures of You Are Safe
Remote Sensing
- Watching Earth from Far Away with Computers
- Making Pictures of Earth Change
- Taking Pictures from Very High Up
- Watching Crops Grow with Computers
- Watching Cities Grow with Computers
- Watching Earth Change with Computers
- Watching Earth from Far Away During Emergencies
- Making Computers Work Together to See Earth
- Putting Pictures of Earth Together
- Making Sure Pictures of Earth Are Safe
Cloud Gaming
- Playing Games from Far Away
- Making Games Work Faster from Far Away
- Keeping Games Safe from Bad Guys
- Making Sure Everyone Can Play Together
- Making Games Faster from Far Away
- Watching People Play Games from Far Away
- Making Sure Games Look Good from Far Away
- Watching Games Get More Popular
Augmented Reality (AR)
- Making Glasses That Show Cool Stuff
- Making Cool Stuff for Glasses to Show
- Watching Glasses Follow You
- Watching Phones Show Cool Stuff
- Making Cool Stuff to Show with Phones
- Making Places Even Better with Phones
- Making Factories Even Better with Glasses
- Making Places Even Better with Glasses
- Making Sure Glasses Don’t Scare Anyone
Virtual Reality (VR)
- Making Glasses That Show Different Worlds
- Making Glasses That Follow Your Hands
- Making Therapy Fun with Glasses
- Making Learning Fun with Glasses
- Making Glasses That Make Jobs Safer
- Making Glasses That Show Your Friends
- Making Sure Glasses Are Friendly
- Making Glasses That Make Buildings Better
- Making Sure Glasses Aren’t Scary
Digital Twins
- Making Computers That Copy the Real World
- Making People Better with Computers
- Making Flying Safer with Computers
- Making Cars Safer with Computers
- Making Energy Better with Computers
- Making Buildings Better with Computers
- Making Cities Safer with Computers
- Making Sure Computers Copy the Real World Safely
- Making Computers Follow the Rules
Edge Computing
- Making Computers Work Faster Near You
- Keeping Computers Safe Near You
- Making Computers Work with Far-Away Computers
- Making Computers Work Fast with You
- Making Computers Work Together Near You
- Making Phones Work Faster Near You
- Making Computers Work Near You
- Making Computers Work in Busy Places
Explainable AI (XAI)
- Making Computers Explain What They Do
- Making Medicine Safer with Computers
- Making Money Safer with Computers
- Making Computers Safe to Drive Cars
- Making Computers Fair to Everyone
- Making Computers Explain What They Think
- Making Computers Easy to Understand
Blockchain and Distributed Ledger Technology (DLT)
- Making Secret Codes Computers Use
- Making Contracts Computers Can Understand
- Making Computers Share Secrets Safely
- Making Money Safe with Computers
- Making Computers Work Together Nicely
- Making Computers Keep Secrets Safe
- Making Computers Work Together Fairly
- Making Stuff Move Safely with Computers
Quantum Communication
- Making Computers Talk to Each Other Safely
- Making Computers Talk to Each Other from Far Away
- Making Computers Talk to Each Other in Secret
- Making Money Move Safely with Computers
This list covers a broad spectrum of topics within Information Technology, ranging from foundational concepts to cutting-edge research areas. Feel free to choose any topic that aligns with your interests and expertise for further exploration and study!
Emerging Trends in Information Technology Research
In the rapidly changing world of Computer Studies, keeping up with the latest trends is indispensable. Technology keeps changing, and so does research in computer studies. From awesome things like clever robots to how we can safeguard our online information, computer studies research is always discovering new ways to improve our lives. Therefore, let us delve into some of the most exciting new trends shaping computer studies’ future.
- Smart Computers:
Right now, smart computers are a hot item. They can learn from experience, recognize patterns, and even understand language like humans do. This helps in many areas, such as healthcare or finance. So researchers are working on making smart computers smarter yet so that they can make decisions alone and be fair to everyone.
- Fast Computing:
As more devices connect to the Internet, we need ways to process information quickly. Fast computing helps bring processing power closer to where the information comes from, making things quicker and more efficient. Thus, researchers have been figuring out how to improve fast computing, especially for analyzing real-time data.
- Keeping Things Safe:
With all the cool tech around, keeping our information safe from bad guys is important. We must develop methods to safeguard our data and networks from cyber attackers. In addition, they have also been considering how to ensure the privacy of our personal information so that only authorized individuals can access it.
- Fancy Computers:
The next big thing in computing is quantum computers. They can do calculations at a high speed that ordinary ones cannot. Researchers are working hard to achieve quantum computing because it could be useful in cracking codes and creating new drugs.
- New Ways of Doing Things Together:
Blockchain is an exciting technology that allows us to collaborate without a central authority. Its use in cryptocurrencies is quite popular but it has other applications too. Blockchain can be applied for purposes such as helping us discover where products come from, proving who we are on the internet, and making contracts that cannot be changed later on.
- Virtual Reality Adventures:
Entering a completely different world is what Virtual Reality (VR) and Augmented Reality (AR) do. The feeling of being in reality is what these two technologies create, which is not real. These researchers are working hard on making VRs and ARs better so that they can be used for learning, training, and amusement in more innovative ways.
In summary, computer studies research keeps changing with new trends such as smart computers, rapid computing, cybersecurity issues, high-end computers, collaboration platforms and immersive games or virtual reality escapades.
By exploring these trends and developing new ideas, researchers ensure that technology keeps improving and making our lives easier and more exciting.
How can I brainstorm research topics in information technology?
Start by identifying your areas of interest and exploring recent advancements in the field. Consider consulting with mentors or peers for suggestions and feedback.
What are some ethical considerations in AI research?
Ethical considerations in AI research include fairness, transparency, accountability, and privacy. Researchers should ensure their algorithms and models do not perpetuate bias or harm individuals.
How can I stay updated on emerging trends in IT research?
Follow reputable journals, conferences, and online forums dedicated to information technology. Engage with the academic community through discussions and networking events.
Similar Articles

How To Do Homework Fast – 11 Tips To Do Homework Fast
Homework is one of the most important parts that have to be done by students. It has been around for…

How to Write an Assignment Introduction – 6 Best Tips
In essence, the writing tasks in academic tenure students are an integral part of any curriculum. Whether in high school,…
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
This paper is in the following e-collection/theme issue:
Published on 31.5.2024 in Vol 26 (2024)
Vulnerability to Cyberattacks and Sociotechnical Solutions for Health Care Systems: Systematic Review
Authors of this article:

- Pius Ewoh, MBA ;
- Tero Vartiainen, PhD
School of Technology and Innovations, Information Systems Science, University of Vaasa, Vaasa, Finland
Corresponding Author:
Pius Ewoh, MBA
School of Technology and Innovations
Information Systems Science
University of Vaasa
Wolffintie 32
Vaasa, 65200
Phone: 358 414888477
Email: [email protected]
Background: Health care organizations worldwide are faced with an increasing number of cyberattacks and threats to their critical infrastructure. These cyberattacks cause significant data breaches in digital health information systems, which threaten patient safety and privacy.
Objective: From a sociotechnical perspective, this paper explores why digital health care systems are vulnerable to cyberattacks and provides sociotechnical solutions through a systematic literature review (SLR).
Methods: An SLR using the PRISMA (Preferred Reporting Items for Systematic Reviews and Meta-Analyses) was conducted by searching 6 databases (PubMed, Web of Science, ScienceDirect, Scopus, Institute of Electrical and Electronics Engineers, and Springer) and a journal ( Management Information Systems Quarterly ) for articles published between 2012 and 2022 and indexed using the following keywords: “(cybersecurity OR cybercrime OR ransomware) AND (healthcare) OR (cybersecurity in healthcare).” Reports, review articles, and industry white papers that focused on cybersecurity and health care challenges and solutions were included. Only articles published in English were selected for the review.
Results: In total, 5 themes were identified: human error, lack of investment, complex network-connected end-point devices, old legacy systems, and technology advancement (digitalization). We also found that knowledge applications for solving vulnerabilities in health care systems between 2012 to 2022 were inconsistent.
Conclusions: This SLR provides a clear understanding of why health care systems are vulnerable to cyberattacks and proposes interventions from a new sociotechnical perspective. These solutions can serve as a guide for health care organizations in their efforts to prevent breaches and address vulnerabilities. To bridge the gap, we recommend that health care organizations, in partnership with educational institutions, develop and implement a cybersecurity curriculum for health care and intelligence information sharing through collaborations; training; awareness campaigns; and knowledge application areas such as secure design processes, phase-out of legacy systems, and improved investment. Additional studies are needed to create a sociotechnical framework that will support cybersecurity in health care systems and connect technology, people, and processes in an integrated manner.
Introduction
Cybersecurity in health care systems entails the safeguarding of electronic information and assets against unauthorized access, use, and disclosure [ 1 ]. The main objective of cybersecurity in health care systems is to protect the privacy, integrity, and accessibility of health information to provide secure health care services. Despite the digital transformation in health care delivery, health care organizations are facing increasing challenges and crises, which include data breaches of patient health information and vulnerability in their critical infrastructure [ 2 ]. Research has highlighted that health care systems are becoming more vulnerable to cyberattacks as technology advances [ 3 ]. Furthermore, the internet and its diverse nature and connection to the delivery of telehealth and continuous health care services create multiple points of access for cyberattacks [ 4 , 5 ].
In high-income countries such as Finland, the United States, and the United Kingdom, integrated technology is used to monitor and manage health care systems. For instance, at least 10 to 15 medical devices are linked to each patient’s electronic bed in a public hospital [ 6 ]. These complexities increase the susceptibility of health care networks to cyberattacks [ 6 , 7 ]. Studies conducted through the simulation of medical devices have similarly revealed that pacemakers and pulse oximeters can be hacked and compromised without a physician’s knowledge [ 8 , 9 ]. Ransomware is another type of man-made malware that can disrupt health care systems by infecting computer systems, locking people out of their files, and then demanding a ransom payment in exchange for access to those files [ 10 , 11 ]. Cyberattackers can publish the exposed health information to the web or sell it on the dark web [ 12 ]. This type of attack can result in breaches of patient privacy, subjecting health care organizations to fines that are consistent with human health service regulations and European General Data Protection Regulation (GDPR) policies for data breaches. For example, research has shown that, between 2012 and 2022, more than US $128,244,290 million in fines were paid in the United States alone for violations of Health Insurance Portability and Accountability Act laws on data breaches against health care organizations [ 13 ]. Although these fines were derived from no less than 111 health care organizations, many organizations have failed to report breaches.
Cybersecurity education is seriously lacking [ 14 , 15 ]. Moreover, a critical problem with cybersecurity in health care systems is the lack of involvement or recruitment of people with expertise and training in cybersecurity [ 16 ], resulting in considerable neglect of the cybersecurity infrastructure [ 17 ]. A systematic literature review (SLR) revealed that, between 2018 and 2019, more than 24% of the data breaches in all industries happened within the health care context [ 18 , 19 ].
Between 2009 and 2021, the US Department of Health and Human Services office reported 4419 health care data breaches, resulting in >314 million health care records being lost, stolen, or exposed [ 20 ]. In 2015, an estimated 113.27 million records were stolen and exposed, and in 2021 alone, the US Department of Health and Human Services also reported at least 2 health care data leaks daily [ 13 ]. The statistics clearly show an upward trend in health care data breaches over the past 10 years [ 21 ]. When considering this trend on a global scale, the number of health information breaches could potentially reach into the billions of health records. Organizations such as Vaastimo Oy Finland; National Health Service trusts in the United Kingdom; Anthem, Inc; Premera Blue Cross; and Excellus Health Plan have been victims of these threats and breaches of health information. Breaches and vulnerabilities in health care delivery, human safety, and protection of sensitive information are deeply disconcerting. However, it can be argued that research solutions are fragmented and sparse. There is a gap in the knowledge areas of health care cybersecurity in the literature and in practice regarding the vulnerability of health care systems and the reasons for cyberattacks. The argument and motivation are that a holistic approach to security is needed because humans are the weakest link in the cyberattack chain [ 11 , 22 ].
Coventry and Branley [ 6 ] have highlighted the need for resilience and changes in their studies on human behavior, technology, and processes as part of a holistic solution to the problem of health care system vulnerability. The information, technology, processes, objectivity and values, skills and knowledge, management systems and structure, and other resources dimensions by Heeks [ 23 ] also point out that avoiding security design reality gaps requires approaching the security functionality of a health information system as a sociotechnical system and not as a technical system. Security by design, or secure design, is an approach to cybersecurity that enables organizations to automate their data security controls and formalize the design of their infrastructure so that they can build security into their IT management processes [ 24 , 25 ].
In this study, a sociotechnical approach is defined as the interaction between humans and technology with the aim of creating technically efficient organizational information systems and user satisfaction [ 26 ]. Furthermore, conceptualizations of this approach are concerned with 3 primary dimensions: the social environment, technical environment, and organizational environment [ 27 ]. Sociotechnical design is identified as an approach to connect the integration of systems while ensuring that the multifaceted challenges and complexities in smart health care are well managed [ 28 , 29 ]. Smart health care can be defined as care that is equipped with smart IT, such as Internet of Medical Things (IoMT) devices that have the capabilities to anticipate and diagnose patient diseases; respond to treatments; guide, manage, and improve user comfort; and provide security and entertainment via hospital management systems. According to Coiera [ 30 ], “if healthcare is to evolve at a pace that will meet the needs of society, it will need to embrace the science of sociotechnical design.” Therefore, the application of a sociotechnical perspective in health care cybersecurity in this study aimed at better understanding and mitigating the multifaceted challenges and poor uptake and performance of health care system security within health care organizations.
This existing gap in knowledge and practice was a major motivation for this SLR. It is necessary to connect the fragmented research and manage this knowledge gap regarding why health care systems are vulnerable to cyberattacks as the study by Coventry and Branley [ 6 ] did not address this aspect in detail. An SLR was conducted to develop proactive cybersecurity strategies to mitigate threats and vulnerabilities that result in health care data breaches by proposing sociotechnical solutions and recommendations. Furthermore, to link human behavior, technology, and processes as highlighted by Coventry and Branley [ 6 ] and supported by the narrative review by Mohan et al [ 31 ] for further research, these 3 core areas can be interpreted as a sociotechnical framework [ 27 ]. It is essential to mitigate the increase in breaches of health information and protect health care from cybercrime and cyberattacks on critical health care infrastructure. However, none of these studies have examined why health care systems are vulnerable to attack through a sociotechnical lens. On the basis of this knowledge gap identified in the literature, the following research questions (RQs) were raised: (1) Why are health care systems vulnerable to cyberattacks? (RQ 1) (2) How can health care systems be protected? (RQ 2).
The objective of this review was to explore from a sociotechnical approach why digital health care systems are vulnerable to cyberattacks, provide sociotechnical solutions, and identify the areas of health care systems that need further improvement.
Previous Literature Review
Regarding the existing literature on health care cybersecurity, our previous SLR identified the following review themes: (1) cybersecurity threats and trends: studies that provide solutions and insights into threats and trends have been conducted to address cybersecurity threats and trends in health care systems [ 2 , 6 , 11 , 17 , 32 , 33 ]; (2) cybersecurity vulnerability: some studies have also investigated the cybersecurity vulnerability of health care systems to provide solutions and future directions for health care services [ 22 , 34 - 36 ]; and (3) cybersecurity interceptions in health care: studies have also investigated cybersecurity interceptions with health care systems to protect the security posture of these systems [ 12 , 19 , 37 ]—Coventry and Branley [ 6 ] have highlighted the need for further studies on human behavior, technology, and processes to further investigate why health care systems are vulnerable and provide a holistic solution to this problem.
Therefore, there is a need for further studies to identify the reasons behind the increase in health information breaches in health care systems. This area of study through a sociotechnical lens is lacking. Accordingly, our SLR critically investigated why health care systems are vulnerable to cyberattacks and expanded this area of study from a sociotechnical point of view. This review is significant given the lack of SLRs on the areas linking human behavior, technology, and processes using a holistic approach from a sociotechnical viewpoint in this context and as the studies by Coventry and Branley [ 6 ] and Mohan et al [ 31 ] were based on narrative reviews.
Protocol and Registration
The PRISMA (Preferred Reporting Items for Systematic Reviews and Meta-Analyses) guidelines were followed to conduct our SLR using the checklist guide [ 38 ] ( Multimedia Appendix 1 ). The aim of this review was to identify the reasons why health care systems are vulnerable to cyberattacks and provide sociotechnical solutions. In the planning stage of this review, a protocol for the sources of information, search strategies, study selection, criteria for eligibility, and data collection processes was created, and this review was not registered.
Eligibility Criteria
A paper was selected for inclusion if it was published in English and comprised a full-text version of the manuscript, review paper, conference proceeding paper, report, news article or website, or white paper published between 2012 and 2022. The introduction, abstract, results, and discussion sections of the paper were checked by the authors for conformity with the study objectives and critical appraisal using the checklist guidelines before inclusion. Research papers were excluded if they were not relevant to the research areas—cybersecurity, cybercrime, ransomware, and health care. These criteria are presented in Textbox 1 .
Inclusion criteria
- Study types: published peer-reviewed and original research papers (empirical and conceptual papers)
- Bibliometric study types: white papers and cybersecurity news reports in line with health care and cybersecurity
- Period: papers published between 2012 and 2022
- Language: English
- Subjects and domain: computer sciences, health care, and cybersecurity
- Requirements for paper inclusion: full-text papers.
Exclusion criteria
- Study types: unpublished work, editorial letters, textbooks, and research in progress
- Language: any other languages
- Subjects: studies outside the domain of cybersecurity and health care
Information Sources
To identify original research papers and review papers on cybersecurity in health care systems published between 2012 and 2022, a total of 6 databases (Web of Science, ScienceDirect, Scopus, PubMed, Springer, and the Institute of Electrical and Electronics Engineers) and a journal ( Management Information Systems Quarterly ) were searched. Furthermore, bibliometric records such as website reports, white paper reports, and magazine reports that supported cybersecurity in health care were also collected for the review. As a means of verifying the papers identified in our search, we searched Google Scholar using a search string.
Search Strategy
The following search string and keywords were used: (“cybersecurity” OR “cybercrime OR ransomware”) AND (“health care”) OR (“cybersecurity in healthcare”). Multimedia Appendix 2 provides more information.
Data Extraction
A total of 70 papers were extracted and recorded in a Microsoft Excel (Microsoft Corp) spreadsheet. The extracted data included information such as author or authors, year of publication, method, problem, and solution. The first author independently charted the data and updated the table to ensure the quality of the key findings drawn from the papers based on the recommendations of the second author. Critical appraisal was conducted to ensure the quality of evidence and the relevance of the articles. The data retrieved from the selected articles were analyzed.
Data Synthesis
The data from the literature were analyzed and synthesized using qualitative themes, which are presented in the following sections. The data were analyzed to identify the causes of vulnerabilities; solutions provided in the literature; and areas of classification based on sociotechnical, technical, and social perspectives in health care systems.
Selection of Sources of Evidence
A total of 1257 papers were retrieved for the screening exercises. To determine whether the papers met our inclusion criteria regarding the topic domain, we began by scanning the abstracts and titles. The papers were reviewed by reading the full texts and determining their eligibility. Duplicated papers as well as those nonrelevant to cybersecurity, cybercrime, ransomware, and health care research were excluded. Furthermore, some papers were excluded after reading them in full and discovering that they were papers on research in progress. Finally, 70 papers were included in the analysis based on the eligibility criteria. Figure 1 illustrates the selection process.
The results of the SLR show the reasons why health care systems are vulnerable to cyberattacks and health care breaches. These reasons are the 5 vulnerability themes ( Figure 2 and Table 1 ). Furthermore, the 5 vulnerability themes were classified into social, technical, and sociotechnical approaches.

a ECRI: Emergency Care Research Institute.
b PECB: Professional Evaluation and Certification Board.
The results also revealed that >24% of the data breaches from all industry clusters originated in the health care sector alone ( Table 1 ) [ 19 , 21 , 84 ]. Other studies highlighted that organizations tend to spend more money on procuring new technology while committing only ≤5% of their budgets to the security of their critical health care systems [ 17 , 35 ]. Cybercriminals exploit health care systems due to the lack of investment, technology advancement as a result of digitalization, human error due to a lack of awareness and training, and old legacy systems, which enable cybercriminals to access valuable health information and sell it on the dark web for money and other gains [ 12 ]. The results reported a significant increase in data breaches and cyberattacks, with complex systems, IoMT devices, technology advancement, and network-connected end-point devices in complex connected heterogeneous health care systems identified as the major contributing factors.
The studies also identified a shortage of cybersecurity skills to contain cyberattacks or threats to health care organizations and systems [ 16 ]. The studies revealed that approximately 60% to 70% of health care organizations have witnessed breaches of health information without disclosure [ 85 ].
Human Error
Human error is a significant factor in the event of a cyberattack [ 11 , 22 ]. This shortcoming is one of the most crucial issues in health care systems as most cybercriminals use methods such as phishing to execute attacks with just a deceitful email. This is a social problem that can be addressed from a social approach. For example, human error posed a risk to the Geneva University Hospitals [ 86 ]. Table 1 shows that 11% (8/70) of the studies acknowledged human error as the primary social reason for health care system vulnerability. Human error is attributed to a lack of skills and is a major trend in this ever-changing technological landscape, playing a role in several cybersecurity breaches [ 56 ]. From a technological point of view, a lack of expertise from humans and threats from human-related events are responsible for >70% of data fraud and breaches in business organizations (McCue, A, unpublished data, May 2008) [ 80 ] because of the value of health information on the dark web [ 6 ] and breaches in business organizations (McCue, A, unpublished data, May 2008) [ 80 ]. Furthermore, human-related threats have recently emerged as a growing concern.
Old Legacy Systems
Old legacy systems have been the basis of system development from the dawn of the medical device, operating system, and embedded mobile device era. Legacy operating systems such as Windows ME, Windows 2000, MS-DOS, UNIX, and firmware provide the foundation for system development. However, these systems pose a significant threat to health care sectors and organizations in our current era. Table 1 shows that 16% (11/70) of the studies acknowledged the vulnerability of health care systems to attacks due to old legacy systems. Such attacks occur from a sociotechnical approach, with cybercriminals exploiting humans and technology. Many data breaches, system incompatibilities, and security risks in health care systems and sectors are associated with legacy systems. Similarly, our SLR found that 85% of medical organizations use outdated operating systems or infrastructure [ 12 , 16 ]. Furthermore, Fu and Blum [ 50 ] raised concerns about organizations relying on unsupported software, alluding to medical devices that run on Windows XP operating systems with service packs but lack security updates. In addition, the case of the National Health Service 2017 WannaCry malware, which interrupted health care operations and shut down numerous hospitals by infecting thousands of computers, was caused by Windows XP software [ 87 ]. The authorities had been informed about the bugs but failed to act due to negligence. When a medical device is compromised, cybercriminals use it as a gateway to abuse hospitals, health care system networks, and health information or data. Perriello [ 88 ] and Meggitt [ 89 ] highlighted another issue, Medijack , referring to hackers hijacking medical devices to construct a back entrance into a hospital network. As a result, the use of a network of old legacy medical devices for administrative processes and care delivery increases the opportunities for an attacker or cybercriminal to easily intrude into hospital or health care organization networks and exploit and compromise the network of medical devices and health information. In this era of rapid medical technological advancement, health care systems also lack built-in security safeguards. Legacy systems do not support new technologies, and so the network of medical equipment in intensive care units, recovery rooms, operating rooms, and electronic health records (EHRs) will lack proper and secure communication and interoperability. Outdated legacy systems and unsupported operating systems are vulnerable to high-speed attacks. Furthermore, these problems are attributable to the lack of important updates to health care infrastructure. To support our point, health and human services should provide more guidance on applying the National Institute of Standards and Technology framework to the health care industry and consider appropriate incentives that would allow health care organizations to phase out old vulnerable legacy systems [ 16 ].
Lack of Investment
Investment in the health sector will yield better outcomes and quality health care delivery. According to our analysis and results, the health care sector suffers from underinvestment, and crucial infrastructure and training for health care cybersecurity are disregarded [ 6 ], which is one of the primary causes of the increase in sensitive health information breaches. Investment can be seen in social (human) and technical (technology) aspects. As shown in the analysis in Table 1 , a total of 21% (15/70) of the studies acknowledged the lack of investment and advised both directly and indirectly regarding the necessity of cybersecurity investment in the health care industry [ 55 , 56 ]. The analysis acknowledged and revealed that the health care sector lagged more than other sectors in terms of health information protection and breaches. Furthermore, the findings of our SLR revealed that 80% to 85% of worldwide breaches occur in the health sector [ 4 ], whereas 45% to 90% of health care organizations have witnessed one or more threats or breaches [ 18 , 57 ]. Investment in critical infrastructure for health care and best practices in cyber hygiene will aid in the protection of health care systems from potential vulnerabilities. Proper investment will ensure the safeguarding of personal information and render health care systems more resilient to cyberattacks.
Complex Network-Connected End-Point Devices
Medical end-point devices have long served as a hospital’s backbone for treatment, diagnosis, and precision-based technological applications to complement health care service operations and management. To fully exploit their potential, the medical device development pattern has shifted from traditional-based medical device system development to a network of wireless, connected end-point technological devices with built-in communications and remote connectivity. Complex network-connected end-point devices have increased the cyberattack surfaces in conjunction with their complexity and technological systems as heterogeneity in nature of medical technology has evolved. Complex network devices are classified as a technical challenge from the perspective of technical security system design. The analysis in Table 1 shows that 51% (36/70) of the studies acknowledged network-connected end-point medical devices as the most significant technical reason for health care systems’ vulnerability to cyberattacks. The operational modes continue to evolve with more interconnections between new applications and devices such as cloud-based applications, third-party software, IoMT devices, and system networks in health care environments. Lechner [ 68 ] revealed that original equipment manufacturers are now creating interconnected medical devices without incorporating proper cybersecurity features into the development life cycle of medical and end-point device systems. The vulnerability of the end point requires urgent attention; otherwise, cybercriminals will continue to use the weakness of connected devices to access personal health information. According to research and cybersecurity stakeholders, wearables, implanted devices, and sensors may become the new targets of future exploits [ 6 , 8 ]. As shown in Table 1 , complex network-connected end-point medical devices also require medical technology security by design [ 72 , 90 ] as a solution strategy to protect critical health care infrastructure from breaches. In the past, medical device system development has primarily focused on critical performance and safety. Furthermore, the security aspects of these medical devices are not a factor during the planning and development process. The process indicates that developing traditional or stand-alone systems of noninterconnected devices was a suitable method for designing the traditional approach. These are the current legacy systems that lack interoperability, updates, security design, or compatibility. Furthermore, connected medical devices such as sensor-controlled drug infusion pumps, cardiac pacemakers, pulse oximeters, and network-connected x-ray machine components such as picture archiving and communication systems are vulnerable to cybersecurity threats and attacks [ 5 ]. To continue solving cybersecurity issues in medical devices, developers and actors must recognize the importance of the health care environment’s complex operations. In addition, there should be incident reports, an audit trail in the device system database, and paper-based documentation of technical vulnerabilities [ 34 ]. Medical device manufacturers such as security experts or systems integrators must address this issue because, with a single cyber vulnerability, cybercriminals or hackers can exploit medical technology connected to the internet, compromising data integrity, wearable sensor readings, protected health information, patient safety, and care outcomes [ 2 , 50 ]. When cyberattackers manipulate systems or deposit a virus, this could cause medical device software or systems to malfunction, resulting in abnormal effects or different readings from the systems, such as implantable medical devices that take and display incorrect readings [ 5 , 8 ].
Technology Advancement (Digitalization)
Technology advancement has enabled unique access and benefits to revolutionize health care systems in terms of precision. Modern medical care now relies on health care delivery organizations, including hospitals and clinics, built on a backbone of connected computer-based infrastructure. Over the past 30 years, the expansive integration of new health care technology has changed the face of medicine [ 53 ]. However, the rapid digitalization in health care delivery, where medical devices are intertwined in a digital network setting and system to ensure the precision of health care delivery with the use of IoMT and digital devices, has created gateway access for cyberattacks, risks, and vulnerabilities [ 37 , 81 ]. Table 1 shows that 14% (10/70) of the studies acknowledged technology advancement due to digital transformation as the reason why health care systems are vulnerable to cyberattacks. This type of attack and vulnerability usually occur from the technical areas of cyberattacks, for example, a technology error such as glitches and design errors. One example of vulnerability is St. Joseph Hospital in California, where the health information of 31,800 patients was made public through a basic internet search engine for >1 year without anyone noticing. The underlying issue was that security settings on the medical devices were not correctly configured [ 91 ]. As technology continues to evolve, IoMT will become more inseparable in health care service delivery, which will create more vulnerabilities if health care organizations continue to disregard cybersecurity threats without proactive readiness to address them in this era of Industry 4.0. These vulnerabilities pose threats to the security and privacy of human and health information.
Studies have shown the health care sector to be unequipped and lacking in investment [ 11 , 92 ]. For example, the use of electronic health technology, motivated by acts such as the Meaningful Use program introduced by the US government, has compelled many health care organizations to increase the use of digital technology in health care, such as EHRs and electronic data exchange, and comply with enhanced health care delivery management. Organizations began to focus on adopting new technology and spending less on security, creating part of the problem [ 32 ]. Technological advancements and a federal policy mandate ultimatum are 2 of the causes noted in this SLR that have increased health care industry exposure to cyberattacks and breaches of health information [ 17 ]. Therefore, an organization should have proper planning; be proactive instead of reactive; and ensure the protection of health technology, information, patient privacy, and security when implementing or adopting advanced technology [ 17 , 80 ]. One such process is to ensure that a medical technology statement of disclosure and liability is included during the procurement, integration, and adoption of a technology. Support services and maintenance during and after procurement and installation should be part of the procurement process. Furthermore, the device manufacturer should also consider security in product development planning. Digital technology should also have the capability to monitor and collate threats and patterns and log these in a risk assessment register for analysis and improvement or threat containment.
Causes of Vulnerabilities in Health Care Systems
Figure 3 shows the causes of vulnerabilities in health care systems, which complement the findings regarding health care vulnerability, and categorizes them accordingly. The following sections address these vulnerabilities.

How Can Health Care Systems Be Protected?
This study summarizes how health care systems can be protected from cyber threats and cyberattacks and presented in Table 2 .
a Not applicable.
b IoMT: Internet of Medical Things.
c IoT: Internet of Things.
Human-Related Case Type and Challenges
The protection of health care systems from cyberattack-related vulnerabilities caused by human error, such as identity theft and health information breaches, requires by law that health care organizations inform the human health office, regulatory bodies, and data owners [ 93 ] to ensure compliance with ethical and privacy standard regulations [ 94 , 95 ]. A security compliance officer should also be employed to guide and ensure that proper cyber hygiene measures are in place to avoid such occurrences. It is important to ensure that health information is encrypted to assure that data are unusable and back up data offline and on the web. Furthermore, in cases in which a health care organization is saddled with challenges due to insecure human behavior, such as employee negligence, a lack of skills, and cyber warfare, the organization must ensure proper training of all staff [ 62 ] and implement awareness programs using a comprehensive guide to avert cyber threats [ 36 , 41 ]. This proposed solution requires a social approach in designing guidelines and training programs.
Old Legacy Systems Case Type and Challenges
Interoperability and compatibility challenges in medical devices stem from human-related activities within health care systems, potentially impacting the persistence of outdated legacy systems [ 50 ]. Therefore, to holistically protect health care systems, proposed solutions involve sociotechnical measures due to the old legacy in human work processes, organizational structures, and technology tasks, as mentioned by Offner et al [ 2 ]. Organizations should adhere to policies and standards linked to the old legacy, ensure proper updates and upgrades, and implement patches. Modern equipment that supports security and carries out updates must be procured to avert crises and phase out legacy systems [ 16 ].
Lack of Investment Case Type and Challenges
Investment in critical health care infrastructure is very important to ensure a health care ecosystem that is secure from cyberattacks and vulnerabilities. The susceptibility of health care to cyberattacks is a result of the underinvestment in and neglect of cybersecurity infrastructures. Kruse et al [ 17 ] also highlighted that a health organization invests ≤5% in cybersecurity but tends to focus on integrating and delivering care. It is important for a health care organization to invest in technology, human behavior, and processes [ 96 ] to protect sensitive and valuable health information from breaches and attacks.
Complex Network-Connected End-Point Devices Case Type and Challenges
The increase in health information breaches in hospitals is attributed to complex network-connected end-point devices, which are vulnerable to cyberattacks because sensor-based medical devices and system networks are interlinked and connected to the internet [ 8 ]. Internet of Things devices are vulnerable because they can be controlled through a media access control address and network. A proposed solution identified in this SLR highlighted that health care can be protected though proper encryption of data and installation of network defenders [ 3 ]. It is important that medical device simulation and assessment be performed through vulnerability analysis to ensure that devices are not tampered with or compromised [ 8 ].
Technology Advancement (Digitalization) Case Type and Challenges
Technology advancement has revolutionized the health care delivery process using digital technological processes. Manufactured medical devices enable patients to be diagnosed remotely, and physicians can administer care using telemedicine. However, technological advancements still lack security in the design of these devices because security is an afterthought during development, which makes them vulnerable to cyberattacks [ 5 ]. A proposed solution is that health care organizations must ensure that medical device security starts from the planning stage [ 68 ] and that device manufacturers maintain and manage security in the pre- and postmarket phases. This solution paradigm must be catalogued as a technical measure. Hospitals with modern-day smart care should leverage comprehensive guidelines and compliance with standards such as those of the International Organization for Standardization or International Electrotechnical Commission 27001 or 27002, as well as cyber hygiene to enable effective and efficient care delivery processes [ 4 , 11 ]. Therefore, the implementation of solutions should always adopt a sociotechnical approach [ 96 ].
Intervention Application Areas and Domain Counts for 2012 to 2022
The selected studies from this SLR that discussed and presented knowledge interventions and solutions applied in some health care sectors between 2012 and 2022 are categorized and presented in Table 3 .
a PECB: Professional Evaluation and Certification Board.
b HIPAA: Health Insurance Portability and Accountability Act.
c ECRI: Emergency Care Research Institute.
Knowledge Application Domains and Vulnerabilities
The vulnerabilities listed in Table 3 reveal that human error was associated with interventions linked to one of the knowledge application domains of training, awareness, education, and intelligence information sharing.
Employee training is important to avoid human factors or error challenges in health care. Table 3 shows the proposed solutions and interventions for training from 17% (12/70) of the studies. Figure 4 shows that training emerged in 2018 at 1% and increased to its peak between 2019 and 2021. However, this finding suggests the need for cybersecurity training in health care to manage human vulnerability challenges. This need is supported by the literature highlighting the importance of cybersecurity skills and education for health care professionals [ 16 ] and the need for investment in this area [ 17 ].

The solutions presented regarding educational intervention were derived from 3% (2/70) of the studies ( Table 3 ). Figure 4 shows that educational solutions emerged in 2017 and declined until 2020, when studies on educational intervention emerged. This finding is supported by research that shows a lack of educational skills [ 16 ]. Organizations must invest in educational training and skills to curb social and technical cybersecurity vulnerability in health care.
A total of 6% (4/70) of the studies in Table 3 presented solutions on awareness to address the vulnerability of human errors. This small number of studies has shown a decline and a lack of cybersecurity awareness program in health care systems. Figure 4 similarly shows that cybersecurity awareness emerged in 2016 and reached its peak at 2 studies. This has been validated by previous studies that indicate a lack of awareness programs and training [ 45 , 62 ].
Intelligence Information Sharing
Table 3 also shows that intelligence information sharing was a solution investigated in 7% (5/70) of the studies. It can be seen that information sharing emerged in 2014 and declined in 2015 before re-emerging in 2017 and 2018 at the rate of 1 study each year. This finding also shows that health care organizations should collaborate in training and intelligence information sharing to address cybersecurity challenges in health care.
The vulnerabilities listed in Table 3 reveal that old legacy systems were associated with interventions linked to the knowledge application domain of health policy and standards.
Health Policy and Standards
The knowledge intervention analysis indicates that 36% (25/70) of the studies acknowledged and were linked to health policy and standards ( Table 3 ). The analysis shows that governments and health care organizations have proposed more interventions or solutions regarding health policy and standards to regulate health care organizations. The policy studies shown in Figure 4 emerged in 2014 and continued to increase to their peak in 2018. Policies such as the Health Insurance Portability and Accountability Act, the GDPR, and the Health Information Technology for Economic and Clinical Health Act to engineer has helped to mitigate data breaches and vulnerabilities in health care organizations in addressing old legacy systems to avoid sanctions and fines in case of breaches. However, full implementation or enforcement of day-to-day monitoring in hospitals or health care organizations remains challenging.
The vulnerabilities listed in Table 1 reveal that a lack of investment was associated with interventions linked to the knowledge application domain of partnership.
Partnership
Partnership is key to sustaining and protecting health care systems from cybersecurity vulnerability [ 72 ]. When organizations fail to invest in critical cyber infrastructure, skills, and partnerships with governments and expert security organizations, it is likely that they will be vulnerable to cyberattacks and breaches of health information and lack the capability to protect health care systems from the vulnerability of underinvestment. Table 3 shows that partnership solutions were provided in 4% (3/70) of the studies, whereas Figure 4 shows that partnership emerged in 2018 and declined in 2021. There is a need for health care organizations to partner for better capability and structure to protect health care systems [ 64 ].
The vulnerabilities listed in Table 1 reveal that complex network-connected end-point devices were associated with interventions linked to the knowledge application domains of participatory design, network security, and encryption.
Participatory Design
Health care organizations and medical device manufacturers must jointly participate in designing processes and systems to avoid a sociotechnical design gap. This collaboration will help protect health care systems and increase the acceptability of organizational systems and productivity. Table 3 shows only 1 pertinent study in 2014. This infer that participatory design is one of the reasons for the vulnerabilities in complex network-connected end-point devices in health care systems. Health care systems comprise a complex environment that requires a sociotechnical and collaborative approach to addressing challenges [ 2 ].
Network Security
Network security solutions were covered in 23% (16/70) of the studies ( Table 3 ). A number of intervention solution studies were conducted in this domain. As shown in Figure 4 , the first increase was observed in 2014 with 4 studies, a decline to 2 studies was observed in 2017, and then the number of studies increased to 3 before a final decline to 2 studies in 2021. These studies still attest to the vulnerability of complex network-connected end-point devices, which require increased interventions to solve health care vulnerability challenges.
The encryption technological solution in this review was mentioned in 6% (4/70) of the studies. There was a limited number of solutions regarding encryption intervention in this review ( Figure 4 ). Encryption only emerged in 2014 with 2 studies, and there was a gap in studies until 2017 and 2018. This finding shows that health care organizations need to implement encryption technology to protect valuable health information from breaches and attacks [ 77 ].
The vulnerabilities listed in Table 1 reveal that technology advancement (digitalization) was associated with interventions linked to the knowledge application domains of machine learning, blockchain, and security design.
Machine Learning
Machine learning is a new area in which cybersecurity in health care systems is evolving. However, solutions were provided in only 11% (8/70) of the studies ( Table 3 ). This technology surfaced in 2014 according to Figure 4 . There was only 1 study in 2014 and 2015. No solutions were provided until 2018, and the number of interventions categorized under technology advancement increased from 2019 to 2021.
Blockchain technology is new and still lacking solutions according to this SLR, where only 1% (1/70) of the studies showed an effective intervention. Blockchain surfaced in 2019, as shown in Figure 4 . Additional solutions and interventions are needed as this area is promising and can be categorized under technology advancement (digitalization) as the key to protecting smart health care systems.
Security by Design
Security by design is a strategy that demands that health care organizations implement auto-based technology to protect digital health care systems. Table 3 shows that 9% (6/70) of the studies acknowledged security by design as a solution for technology advancement to prevent vulnerability in digital systems. Figure 4 shows studies on secure design in 2013 to 2014. There were no studies in 2015, whereas in 2016 to 2019, some studies provided interventions. There is a need for more solutions in this area to protect technological advancement or digital health care systems from vulnerability [ 68 ].
Summary of the Knowledge Application Domains and Vulnerabilities
In summary, the findings of this SLR indicate that interventions provided for the containment of health care cybersecurity vulnerabilities were limited over the past 11 years. This SLR also revealed that interventions regarding the rate of technological advancements in addressing health care cybersecurity challenges were inconsistent and lagging between 2012 and 2022. Findings also indicates that interventions in some of the mapped variables were scarce between 2012 and 2022 ( Table 3 ). Few or no solutions are provided to address the challenges in many domains regarding health care vulnerabilities.
Brief Summary of Findings
This SLR provided a synthesis of literature on cybersecurity in health care and identified the reasons why health care systems are vulnerable to cyberattacks. This review analyzed 70 published studies and identified 5 vulnerability themes of cybersecurity in health care systems and also proposed sociotechnical solutions for health care organizations.
The findings indicate that the extensive vulnerability of health care systems is due to internet-connected devices and software applications. Health care organizations face significant challenges, such as medical end-point device complexities and saturated wireless medical technology resulting in its difficulty in securing an interconnected technological landscape.
Importantly, many cyberattacks occur within this interconnected network without the health care organization’s awareness, contributing to health information breaches.
Our findings also underscore that the crucial role of investment in health care organizations is a key panacea for addressing cyberattacks and threats. Thus, lack of investment leverages the other vulnerabilities.
In addition, this study found that lack of adequate preparation for the potential threats or vulnerability in shifting to the digitalization of health care is also a contributing factor to most successful cyberattacks on health care organizations.
We found that human activity also played a major role in subjecting health care systems to cybercrimes. The decision of humans to develop medical devices, health software applications, management systems, and processes in an effective and secured manner is vital in safeguarding health information. However, there is a bit of disconnect in the human-centric design in health care system development, most importantly during the planning of procurement of medical technology and systems and the integration between health care organizations and stakeholders such as medical device developers, health care professionals, cybersecurity compliance officers, and system integration experts. Generally, the findings revealed that health care organizations lack adequate cybersecurity preparations during transitions to digitalization.
The findings also revealed that the health care cybersecurity knowledge application domain areas in Figure 4 depict that more intervention studies over the past 11 years were focused on health policy and standards.
In Table 4 , solutions are proposed from a sociotechnical perspective to counteract cybersecurity vulnerabilities in health care organizations.
Further findings on the vulnerabilities and implications for future research are discussed in the following sections.
Table 4 is an integrated table that is presented in a stand-alone view for health care system solutions from a sociotechnical viewpoint.
To protect health care systems from attacks and vulnerabilities, as shown in Table 4 , through the intervention of effective and noneffective studies, it can be seen that sociotechnical intervention studies classified invention most often and were the most effective. There are patterns and convergences between technical solutions and sociotechnical solutions in their domain of applications and solutions, such as a lack of investment, complex network-connected end-point devices, old legacy systems, and technology advancement, which lean toward interventions.
While we can consider human errors in human-computer interactions and technology usability from a human perspective, design and management can be approached through a sociotechnical perspective [ 96 ]. This approach also considers the final users of digital health care systems. Organizations would benefit from leveraging the sociotechnical solutions and guide in Table 4 in the case of cyberattacks attributed to human error by training all staff to respond using a comprehensive guide to avert cyber threats [ 62 ]. Challenges of technology, such as network-connected end-point devices and technology advancement for digitalization, should be addressed through network and security solutions and encryptions [ 6 , 67 ].
Hospitals with modern-day smart care should leverage their comprehensive guidelines and standard International Organization for Standardization or International Electrotechnical Commission 27001 and 27002 compliances.
Health care organizations should ensure and implement proper cyber hygiene to enable effective and efficient health care delivery processes [ 4 , 11 ]. They should increase their budget for critical cyber systems to address the lack of investment [ 17 ] and phase out old legacy systems by increasing investment. These actions will enable resilience and preparedness for future response plans and mitigations.
a AIDE: Assess, Identify, Develop, and Evaluate.
b Not applicable.
c ISA: information security awareness.
d ANT: actor-network theory.
e CERT RMM: Computer Emergency Response Team Resilience Management Model.
f IoMT: Internet of Medical Things.
g HIPAA: Health Insurance Portability and Accountability Act.
h GDPR: General Data Protection Regulation.
i HITECH: Health Information Technology for Economic and Clinical Health.
j FDA: Food and Drug Administration.
k NIST-CSF: National Institute of Standards and Technology Cybersecurity Framework.
l HICP: Health Industry Cybersecurity Practices.
m ITPOSOM: information, technology, processes, objectivity and values, skills and knowledge, management systems and structure, and other resources.
n EHR: electronic health record.
o e-PSG: electronic health record–specific patient safety goals.
p IoT: Internet of Things.
q FHSS: frequency-hopping spread spectrum.
r RSSI: received signal strength indicator.
s BYOD: bring your own device.
t PHR: personal health record.
u OCSVM: one-class support vector machine.
Implications for Future Research
Health care sectors have improved with policies and measures developed to control health information breaches and vulnerabilities. However, further research is needed in social and technical interception design, namely, the human factor. Managing complex end-point devices and investment on addressing health care vulnerability and breaches should be considered from a sociotechnical design and sustainability perspective.
Protecting Complex Network-Connected End-Point Devices
The protection of complex network-connected end-point devices for health care organizations involves several key measures. The network of interconnected medical end-point devices and the software systems that connect to the internet are becoming vulnerable to attacks and breaches. This is a growing issue; health care organizations tend to procure medical device technology without proper equipment planning and guidelines in place. This implies that security is overlooked and is not a major focus area. Examples include hospital beds connected to >10 medical devices, such as pulse oximeters, syringe pumps, and patient care monitors, which are connected devices and vulnerable to attacks [ 2 , 6 ].
To address this technical challenge, organizations can concentrate on developing advanced threat detection and mitigation techniques, such as network defenders tailored to intricate network-connected end-point devices in health care and the integration of artificial intelligence using machine learning algorithms to effectively identify and respond to emerging threats. Furthermore, the health care industry must take a sociotechnical approach [ 96 ] toward implementing standard guidelines and technical solutions via the protection of health care networks through planning and integrating network security protection and segmentation. In addition, health information exchange over the network should undergo steganography and encryption as a solution using blockchain technology. Therefore, the integration of a complex end-point medical device should use built-in security with alert response and communication in processes to monitor health care cybersecurity ecosystems for a healthy security posture.
Health care organizations should collaborate with security experts and health care professionals and implement user education and incidence response to catalog cyber vulnerability incidences for further analysis. The implication is that, if networks and end-point medical devices are not properly secured, this will lead to breaches of health information through the network, which will cause patient information to be hijacked by cybercriminals for political gains. Sponsored state actors may use this weakness to seize networks and systems of care delivery, demanding money from an organization before the latter can regain access. This approach will expose the health information of patients while they are receiving treatment and accessing health care services. This is an evolving challenge of the digital consequences of connected care. Building security through a design solution should be achieved from a sociotechnical approach as the human is the final user of systems of care.
Future research should focus on security by design before integrations of complex technology and design a simpler flow process with the disaggregation of complex network connections.
Increasing Investment in Cybersecurity
Investment in health care systems is critical to ensure the proper safeguarding of health care ecosystems from cyberattacks and vulnerabilities. To ensure efficient and secure health care, organizations should invest in human capital and technology to function effectively. An evaluation through research reveals that health care is lagging behind other sectors in terms of investment. This finding was confirmed by Kruse et al [ 17 ], who found that only 5% of health care investment is earmarked to protect health care, whereas a large percentage is allocated for health care delivery.
Insufficient investment in cybersecurity experts, awareness, and investment partnership plans will continue to subject health care employees to insecure behavior and result in a health care organization that is unprepared to mitigate cyber threats and other tactics used by attackers to disrupt evolving health care trends and patterns, particularly ransomware attacks.
Similarly, old legacy systems pose another security risk. Malicious actors can continue to exploit these systems to expose personal health information due to their limited capabilities and outdated organizational structure. Such vulnerability is worsened by a lack of investment in new cybersecurity infrastructure and computer devices to protect or process health information in a secure manner.
Health care organizations can engage in partnership with medical technology providers, application developers, and network solution integrators to develop strong systems and structures with seamless integration. Health care organizations should also develop and implement a framework for prioritizing cybersecurity investment based on risk assessments and threat intelligence. This approach can help identify the most critical areas of vulnerability within different departments, aiding organizations and policy makers in directing investments where they are most needed. Health care organizations should invest in humans and technology through training to ensure the development of necessary skills and investment in critical cyber infrastructure.
Awareness campaigns for patients and staff will help organizations recover from errors and breaches, whereas investment in technological security systems for health care will prepare health care organizations with the appropriate structure and system for resilience.
The findings presented in this paper are also highlighted in Table 4 . Investment challenges in health care cybersecurity should focus on a sociotechnical approach that involves human behavior, technology, and organizational processes and should not be segregated as a separate technical or social problem. Future research should focus on security and investment in smart health care for attaining sustainability and resilience.
Managing Technological Advancement
Health care industries and organizations have improved over the years and are continuing to forge the development of new capabilities, technological advances, and processes to manage the multifaceted challenges of health care cybersecurity. Complexity in technology advancement and networks of digital systems increase the number of attack surfaces, where cybercriminals take advantage of the digital gateway access and execute malicious software programmed with code, such as malware to compromise digital technology and health care system networks. However, technological development necessitates a proactive approach to cybersecurity, particularly when considering security-by-design principles.
Future research projects must concentrate on important areas to protect networks, systems, and applications against vulnerabilities. Health care organizations should collaborate with medical device manufacturers as part of the planning phase of procurement requirements to ensure specifications needs before the development of medical devices technology for seamless integration. Implanted devices, for instance, should be built with security by design and continuously updated when necessary. A 2-factor authentication security for critical medical technology is also necessary. In addition, it is important that health care organizations quantify the risk, ensure that proper National Institute of Standards and Technology and GDPR standard guidelines are followed, and conduct threat modeling and simulation to evaluate the protectability of health care systems as a guideline in managing cybersecurity vulnerability.
Collaborative (sociotechnical) efforts among academia, industry, and policy makers are essential to drive this research agenda forward and create a safer digital landscape for the future.
The technology procurement requirement and collaboration should consider the integration of social and technical processes during digital technology development with health care delivery processes.
Health care organizations can adopt a blockchain technology solution for the protection of health information and other applications such as EHR systems from malicious use and insider threats.
Future research should examine the use of blockchain for health care big data protection and processes to manage cybersecurity vulnerability.
Containing Human Error in Cybersecurity
Humans are at the receiving end of the cyberattack chain. An example is the case of the WannaCry attack that affected 150,000 computers. It was attributed to human error because humans were warned of the attack on Windows server legacy systems but they ignored the warning by clicking on malicious email links [ 38 , 43 ]. When an organization fails to train humans, cybercriminals take advantage of human weakness to exploit health care systems. Today, medical device manufacturers are building devices without considering humans as the final users or a participatory (sociotechnical) design approach. This is one factor of the clinical process and security dimension to protect critical infrastructure. Another factor is that, if a system is developed and does not start with security and support human usability, it becomes stressful for a human user to navigate the systems, which could cause them techno-stress, with the likelihood of mistakes. The health sector should use the Assess, Identify, Develop, and Evaluate technique to identify areas of human weakness, develop a new training method through simulations, and offer gamification training on issues such as phishing email deception and ransomware attacks. The implication is that, if humans are not trained, they will lead organizations to disaster because cybercriminals will continue to exploit the weakness of humans to cause more damage to health care systems. The consequences will include legal issues, fines, and possibly bankruptcy for health care organizations. Proper training and awareness campaigns should be implemented. Future research should focus on developing futuristic health care cybersecurity curriculums and training.
Practical Implications
Inadequate systems will cause health care systems and organizations to face increasing cyberattacks and setbacks in health information and patient safety. Moreover, a new trend reveals that, if implanted medical devices and technology are not protected, humans will be targeted by hackers seeking to make money or gain political power for ransom. However, implementation and adoption of the medical device security life cycle model [ 68 ] will protect medical devices, health information, patients, and organizations from harm and against future emerging threats. Thus, there is a need for the design of a cybersecurity sociotechnical framework toward sustaining smart health care systems.
Comparison With Prior Work
Previous narrative literature reviews by Coventry and Branley [ 6 ] and Mohan et al [ 31 ] highlight the need for an integrated approach in health care systems to address cybersecurity vulnerabilities. They emphasize the need for a comprehensive approach that connects human behavior, technology, and processes in a holistic way as a best strategy to tackle vulnerabilities, although the authors did not classify human behavior, technology, and processes from a sociotechnical lens. This systematic review supports their view by building and extending the literature on cybersecurity case challenge descriptions in all the tables in this paper to integrate human behavior, technology, and processes as a sociotechnical approach [ 2 , 23 , 26 - 28 ]. For example, an SLR conducted by Offner et al [ 2 ] reported that health care system vulnerability is a complex sociotechnical problem. Furthermore, for a health care organization to build resilience against cyberattacks and threats to avoid cybersecurity design gaps and vulnerabilities in the health care system, a strategic approach that integrates people, technology, and processes must be adopted [ 23 , 27 , 31 ]. The aforementioned aligns with the approach adopted in this study.
Different schools of thought have highlighted the key importance of investment in technology and humans to protect health care systems from cyberattacks and threats [ 6 , 8 , 11 , 19 , 36 , 56 ]. This corroborates our findings that cybersecurity investment plays a main role in health care systems.
This study also revealed that complex network-connected end-point devices were mentioned several times by different schools of thought. Moreover, existing literature has opined that complex network-connected end-point devices were the most mentioned vulnerability [ 5 , 17 , 18 , 35 , 53 ].
Furthermore, technology advancement through a digital transformation evolution has created precision, and managed health care delivery [ 32 , 94 ]. However, more effort is still required in designing security features in health care technology. This study highlighted that security by design is required for medical device technology in health care systems [ 9 , 34 , 68 ].
Health care organizations must ensure that the design of technology evolves with a secure design approach from conception to avoid breaches of health information by external and internal attackers [ 24 , 32 , 68 ].
The sociotechnical solutions in Table 4 will aid health care organizations in being resilient in dealing with vulnerabilities and cybersecurity breaches in health care systems through a comprehensive and holistic approach. The sociotechnical perspective defines the meaning and constructs of technology, humans and processes [ 6 , 19 , 31 , 36 , 37 ]. This approach is promising and effective in dealing with health care system and cybersecurity vulnerabilities.
Limitations
For this study, non–English-language articles on cybersecurity and health care were not included. Closed-access articles directly related to cybersecurity and health care were also not included. Textbooks linked to cybersecurity and health care were excluded. In addition, as cybersecurity is a broad topic, more time was needed for data analysis.
Conclusions
This study conducted an SLR (PRISMA guidelines) to investigate the body of literature on cybersecurity in health care systems because of the exponential increase in health information breaches and vulnerability issues surrounding medical device technology and networks. This study also examined why health care systems are vulnerable to cyberattacks and threats.
In this review, sociotechnical solutions and mitigation strategies were proposed to protect patient health information, medical devices, and the critical cyber infrastructure of health care organizations from attacks and threats. We identified human error, lack of investment, complex network-connected end-point devices, old legacy systems, and technological advancement due to rapid digitalization as the causes of data breaches and the vulnerability of digital health care systems to attacks and threats. This study also revealed that research in the areas of education, awareness, training, collaborative partnerships, blockchain, and machine learning for health care cybersecurity is underrepresented. In addition, there was inconsistency in the publication of intervention studies. There is a gap in intervention studies published between 2012 and 2013, as shown in this SLR, as well as breaks in research publications between 2012 and 2022, as illustrated in Table 3 and Figure 4 .
As shown in Table 1 , of the 70 papers published between 2012 and 2022 and reviewed in this study, only 8 (11%) carried out research in the areas of human error–related perspectives where health care systems are vulnerable to attacks. This finding clearly shows that considerably more studies are required on human factors. We also identified from this review that network-connected end-point devices are the most vulnerable challenge that causes health information breaches. However, stakeholders have rolled out interventions in the areas of health policy, health care system support (network security), and training. The support and training target operational activities and health care delivery while investment in cybersecurity critical infrastructure is disregarded. Rapid technology advancement has resulted to an increasing risk of cyberattacks and threats because most manufactured connected medical devices were not built with security in mind. With the possible sociotechnical solutions in Table 4 , we form conclusions about how to protect health care systems as a sociotechnical solution in relation to the gap in research on technology, human behavior, and processes.
Health care organizations must concede that efficient and effective cybersecurity cannot be addressed with a technological process only but must also evolve beyond technological operation to a sociotechnical process that calls for a comprehensive knowledge of the human elements.
The profound implication of our findings steps further from just the concept of security. It deems it necessary for a major change in the approach to health care security by shifting from a reactive measure of patching and mitigation toward an approach of proactiveness and integration of detailed mechanisms that depend on complex sociotechnical dynamics at play in the design and development processes across the health care systems.
Our review emphasized the importance of a mandatory collaboration and cross-disciplinary engagement among stakeholders in health care, technology policy, and academia. The inclusion of a team-based effort from stakeholders will foster an integrated solution that responds to the challenges of cybersecurity vulnerabilities in health care systems.
In addition, our findings also give prominence to the great significance of investment in health care systems, such as in cybersecurity technology, medical devices, networks, health care professionals, and cybersecurity professionals, in advancing health care organizations. Furthermore, investment is imperative in cybersecurity education and training programs that will provide health care professionals and organizations with the updated knowledge and skills to navigate the complexities of cybersecurity vulnerabilities constructively. Governments should provide additional financial incentives for health care organizations to facilitate cybersecurity sustainability in health care systems. Future research should explore the application of blockchain technology for safeguarding health care system data. Blockchain offers a secure decentralized architecture. Therefore, system developers should consider a human-centric design approach when integrating blockchain technology into health care systems.
By strengthening awareness culture, intelligence information sharing, and accountability in health care systems, health care organizations can equip their operations and workforce to become active front-runners in safeguarding patient data and health care critical infrastructure and assuring the confidentiality, availability, and integrity of health care systems. Consequently, our SLR implores for an exhaustive procedure regarding cybersecurity in health care that affirms and entwines the sociotechnical nature of the vulnerabilities and challenges. By merging a technical approach with human-centric strategies, health care organizations can protect health care systems from vulnerabilities and cyber threats and advance a culture of resilience, trust, and innovation in health care service delivery. The implications of this review present a sociotechnical solution for establishing more secure and resilient health care ecosystems. This paper provides health care organizations with a better understanding of and resilience to cyberattacks, threats, and vulnerabilities.
Acknowledgments
The author is grateful to the Finnish Cultural Foundation and University of Vaasa in Finland for their support in funding this research.
Conflicts of Interest
None declared.
PRISMA (Preferred Reporting Items for Systematic Reviews and Meta-Analyses) checklist guide.
Search strategy.
- Cybersecurity in healthcare. Health Insurance Portability and Accountability Act. URL: https://www.himss.org/resources/cybersecurity-healthcare [accessed 2024-05-05]
- Offner KL, Sitnikova E, Joiner K, MacIntyre CR. Towards understanding cybersecurity capability in Australian healthcare organisations: a systematic review of recent trends, threats and mitigation. Intell National Secur. Apr 22, 2020;35(4):556-585. [ FREE Full text ] [ CrossRef ]
- Frost. Medical Device and Network Security Coming to terms with the Internet of Medical Things (IoMT). -. 2024:2019. [ FREE Full text ]
- Karambelas C. Healthcare care technology: ransomware risk and protection. Am Bankruptcy Inst J. May 2020;39(5):30.
- Giansanti D. Cybersecurity and the digital-health: the challenge of this millennium. Healthcare (Basel). Jan 11, 2021;9(1):62. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Coventry L, Branley D. Cybersecurity in healthcare: a narrative review of trends, threats and ways forward. Maturitas. Jul 2018;113:48-52. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Walker T. Interoperability a must for hospitals, but it comes with risks. Managed Healthcare Executive. Dec 10, 2017. URL: https://www.managedhealthcareexecutive.com/view/interoperability-must-hospitals-it-comes-risks [accessed 2024-05-06]
- Dameff CJ, Selzer JA, Fisher J, Killeen JP, Tully JL. Clinical cybersecurity training through novel high-fidelity simulations. J Emerg Med. Feb 2019;56(2):233-238. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Klonoff DC. Cybersecurity for connected diabetes devices. J Diabetes Sci Technol. Apr 16, 2015;9(5):1143-1147. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Reshmi TR. Information security breaches due to ransomware attacks - a systematic literature review. Int J Inf Manag Data Insights. Nov 2021;1(2):100013. [ FREE Full text ] [ CrossRef ]
- Argaw ST, Bempong NE, Eshaya-Chauvin B, Flahault A. The state of research on cyberattacks against hospitals and available best practice recommendations: a scoping review. BMC Med Inform Decis Mak. Jan 11, 2019;19(1):10. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Zarour M, Alenezi M, Ansari MT, Pandey AK, Ahmad M, Agrawal A, et al. Ensuring data integrity of healthcare information in the era of digital health. Healthc Technol Lett. Jun 2021;8(3):66-77. [ FREE Full text ] [ CrossRef ] [ Medline ]
- What are the penalties for HIPAA violations? The HIPAA Journal. URL: https://www.hipaajournal.com/what-are-the-penalties-for-hipaa-violations-7096/ [accessed 2024-05-06]
- Mcnulty M, Kettani H. On cybersecurity education for non-technical learners. In: Proceedings of the 3rd International Conference on Information and Computer Technologies (ICICT). 2020. Presented at: ICICT 2020; March 9-12, 2020; San Jose, CA. URL: https://doi.org/10.1109/ICICT50521.2020.00072 [ CrossRef ]
- Ricci J, Breitinger F, Baggili I. Survey results on adults and cybersecurity education. Educ Inf Technol. Jul 11, 2018;24(1):231-249. [ FREE Full text ] [ CrossRef ]
- Sweeney E. Healthcare data breaches haven’t slowed down in 2017, and insiders are mostly to blame. Fierce Healthcare. Aug 3, 2017. URL: https://tinyurl.com/yn2m49y8 [accessed 2024-05-06]
- Kruse CS, Frederick B, Jacobson T, Monticone DK. Cybersecurity in healthcare: a systematic review of modern threats and trends. Technol Health Care. Feb 21, 2017;25(1):1-10. [ FREE Full text ] [ CrossRef ]
- Wasserman L, Wasserman Y. Hospital cybersecurity risks and gaps: review (for the non-cyber professional). Front Digit Health. 2022;4:862221. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Jalali MS, Razak S, Gordon W, Perakslis E, Madnick S. Health care and cybersecurity: bibliometric analysis of the literature. J Med Internet Res. Feb 15, 2019;21(2):e12644. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Healthcare data breach statistics. The HIPAA Journal. URL: https://www.hipaajournal.com/healthcare-data-breach-statistics/#:~:text=2021%20was%20a%20bad%20year,stolen%2C%20or%20otherwise%20impermissibly%20disclosed [accessed 2024-05-06]
- IBM report: cost of a data breach hits record high during pandemic. IBM. Jul 28, 2021. URL: https://tinyurl.com/euc26j9y [accessed 2024-05-06]
- Nifakos S, Chandramouli K, Nikolaou CK, Papachristou P, Koch S, Panaousis E, et al. Influence of human factors on cyber security within healthcare organisations: a systematic review. Sensors (Basel). Jul 28, 2021;21(15):5119. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Heeks R. Health information systems: failure, success and improvisation. Int J Med Inform. Feb 2006;75(2):125-137. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Casola V, De Benedictis A, Rak M, Villano U. Security-by-design in multi-cloud applications: an optimization approach. Inf Sci. Jul 2018;454-455:344-362. [ FREE Full text ] [ CrossRef ]
- Secure-by-design: shifting the balance of cybersecurity risk: principles and approaches for secure by design software. Cybersecurity and Infrastructure Security Agency. Oct 25, 2023. URL: https://www.cisa.gov/resources-tools/resources/secure-by-design [accessed 2024-05-06]
- Mumford E. The story of socio‐technical design: reflections on its successes, failures and potential. Inf Syst J. Sep 04, 2006;16(4):317-342. [ FREE Full text ] [ CrossRef ]
- Palvia SC, Sharma RS, Conrath DW. A socio-technical framework for quality assessment of computer information systems. Ind Manag Data Syst. 2001;101(5):237-251. [ FREE Full text ] [ CrossRef ]
- Atkinson C, Eldabi T, Paul RJ, Pouloudi A. Investigating integrated socio-technical approaches to health informatics. In: Proceedings of the 34th Annual Hawaii International Conference on System Sciences. 2001. Presented at: HICSS 2001; January 6, 2001; Maui, HI. URL: https://doi.org/10.1109/HICSS.2001.926578 [ CrossRef ]
- Altman R. Informatics in the care of patients: ten notable challenges. West J Med. Feb 1997;166(2):118-122. [ FREE Full text ] [ Medline ]
- Coiera E. Four rules for the reinvention of health care. BMJ. May 15, 2004;328(7449):1197-1199. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Mohan DN, Gowda SS, Vikyath IS. Cyber security in health care. Int J Res Eng Sci Manag. 2020;3(1):551-553. [ CrossRef ]
- Luna R, Rhine E, Myhra M, Sullivan R, Kruse CS. Cyber threats to health information systems: a systematic review. Technol Health Care. Jan 27, 2016;24(1):1-9. [ FREE Full text ] [ CrossRef ]
- Jalali MS, Russell B, Razak S, Gordon WJ. EARS to cyber incidents in health care. J Am Med Inform Assoc. Jan 01, 2019;26(1):81-90. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Williams P, Woodward A. Cybersecurity vulnerabilities in medical devices: a complex environment and multifaceted problem. Med Devices Evid Res. Jul 2015;8:305-316. [ FREE Full text ] [ CrossRef ]
- Safavi S, Meer AM, Melanie EK, Shukur Z. Cyber vulnerabilities on smart healthcare, review and solutions. In: Proceedings of the Cyber Resilience Conference (CRC). 2018. Presented at: CR 2018; November 13-15, 2018; Putrajaya, Malaysia. URL: https://doi.org/10.1109/CR.2018.8626826 [ CrossRef ]
- He Y, Aliyu A, Evans M, Luo C. Health care cybersecurity challenges and solutions under the climate of COVID-19: scoping review. J Med Internet Res. Apr 20, 2021;23(4):e21747. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Jalali MS, Kaiser JP. Cybersecurity in hospitals: a systematic, organizational perspective. J Med Internet Res. May 28, 2018;20(5):e10059. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Page MJ, McKenzie JE, Bossuyt PM, Boutron I, Hoffmann TC, Mulrow CD, et al. The PRISMA 2020 statement: an updated guideline for reporting systematic reviews. BMJ. Mar 29, 2021;372:n71. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Arndt RZ. For epic, interoperability comes from within. Modern Healthcare. Jan 29, 2018. URL: https://www.modernhealthcare.com/article/20180130/NEWS/180139993/for-epic-interoperability-comes-from-within [accessed 2024-05-06]
- Incident detection, email attacks continue to cause headaches for companies. Twitter. URL: https://twitter.com/SandraProske/status/967893399599796224 [accessed 2024-05-06]
- Mukherjee SY. Anthem’s historic 2015 health records breach was likely ordered by a foreign government. Fortune. Jan 10, 2017. URL: https://fortune.com/2017/01/09/anthem-cyber-attack-foreign-government/ [accessed 2024-05-06]
- 2017 cost of data breach study: United States. Ponemon Institute. Jun 13, 2017. URL: https://www.ponemon.org/news-updates/blog/security/2017-cost-of-data-breach-study-united-states.html [accessed 2024-05-06]
- Cost of a data breach report 2021. IBM Security. URL: https://info.techdata.com/rs/946-OMQ-360/images/Cost_of_a_Data_Breach_Report_2021.PDF [accessed 2024-05-06]
- Scott M, Wingfield N. Hacking attack has security experts scrambling to contain fallout. New York Times. May 13, 2017. URL: https://tinyurl.com/4weatd6e [accessed 2024-05-06]
- Gordon WJ, Wright A, Glynn RJ, Kadakia J, Mazzone C, Leinbach E, et al. Evaluation of a mandatory phishing training program for high-risk employees at a US healthcare system. J Am Med Inform Assoc. Jun 01, 2019;26(6):547-552. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Bouveret A. Cyber risk for the financial sector: a framework for quantitative assessment. SSRN. Preprint posted online July 16, 2018. [ FREE Full text ] [ CrossRef ]
- Top 10 health technology hazards for 2016. ECRI Institute. Nov 2015. URL: https://www.ecri.org/Resources/Whitepapers_and_reports/2016_Top_10_Hazards_Executive_Brief.pdf [accessed 2024-05-06]
- Faruki P, Bharmal A, Laxmi V, Ganmoor V, Singh Gaur M, Conti M, et al. Android security: a survey of issues, malware penetration, and defenses. IEEE Commun Surv Tutorials. 2015;17(2):998-1022. [ FREE Full text ] [ CrossRef ]
- Filkins B. Health care cyberthreat report: widespread compromises detected, compliance nightmare on horizon. SANS Institute. 2014. URL: https://asprtracie.hhs.gov/technical-resources/resource/3381/health-care-cyberthreat-report-widespread-compromises-detected-compliance-nightmare-on-horizon [accessed 2024-05-06]
- Fu K, Blum J. Controlling for cybersecurity risks of medical device software. Commun ACM. Oct 2013;56(10):35-37. [ FREE Full text ] [ CrossRef ]
- McHugh M. Medical device software and technology: the past, present and future. BEAI Spectrum, Biological and Clinical Engineers Association of Ireland. 2015. URL: https://arrow.tudublin.ie/scschcomart/38/ [accessed 2024-05-06]
- Newman LH. Medical devices are the next security nightmare. WIRED. Mar 2, 2017. URL: https://www.wired.com/2017/03/medical-devices-next-security-nightmare/ [accessed 2024-05-06]
- Tully J, Selzer J, Phillips JP, O'Connor P, Dameff C. Healthcare challenges in the era of cybersecurity. Health Secur. 2020;18(3):228-231. [ FREE Full text ] [ CrossRef ] [ Medline ]
- The state of ransomware in the US: report and statistics 2019. Emsisoft Malware Lab. Dec 12, 2019. URL: https://tinyurl.com/ykx5zjce [accessed 2024-05-06]
- The state of ransomware in the US: report and statistics 2020. Emsisoft Malware Lab. Jan 18, 2021. URL: https://www.emsisoft.com/en/blog/37314/the-state-of-ransomware-in-the-us-report-and-statistics-2020/ [accessed 2024-05-06]
- Branley-Bell D, Coventry L, Sillence E, Magalini S, Mari P, Magkanaraki A, et al. Your hospital needs you: eliciting positive cybersecurity behaviours from healthcare staff. Ann Disaster Risk Sci. 2020;3(1). [ FREE Full text ] [ CrossRef ]
- Information Commissioner's Office, National Cyber Security Centre, James M. New figures show large numbers of businesses and charities suffer at least one cyber attack in the past year. United Kingdom Government. Apr 25, 2018. URL: https://www.gov.uk/government/news/new-figures-show-large-numbers-of-businesses-and-charities-suffer-at-least-one-cyber-attack-in-the-past-year [accessed 2024-05-06]
- IT security in the era when everything can be hacked. Kaspersky Lab. URL: https://www.unodc.org/documents/organized-crime/cybercrime/cybercrime-april-2018/RUSSIAN_FED.pdf [accessed 2024-05-06]
- GDPR: getting ready for the new EU data protection regulation. PECB Insights. Apr 27, 2018. URL: https://insights.pecb.com/gdpr-compliance-getting-ready/ [accessed 2024-05-06]
- Rahman NA, Sairi IH, Zizi NA, Khalid F. The importance of cybersecurity education in school. Int J Inf Educ Technol. 2020;10(5):378-382. [ FREE Full text ] [ CrossRef ]
- Chowdhury N, Gkioulos V. Cyber security training for critical infrastructure protection: a literature review. Comput Sci Rev. May 2021;40:100361. [ FREE Full text ] [ CrossRef ]
- Coventry L, Branley-Bell D, Sillence E, Magalini S, Mari P, Magkanaraki A, et al. Cyber-risk in healthcare: exploring facilitators and barriers to secure behaviour. In: Proceedings of the HCI for Cybersecurity, Privacy and Trust 2020. 2020. Presented at: HCI-CPT 2020; July 19-24, 2020; Copenhagen, Denmark. URL: https://tinyurl.com/v2dbyrsx [ CrossRef ]
- Burns AJ, Johnson ME, Honeyman P. A brief chronology of medical device security. Commun ACM. Sep 22, 2016;59(10):66-72. [ FREE Full text ] [ CrossRef ]
- Chua JA. Cybersecurity in the healthcare industry - A collaborative approach. American Association for Physician Leadership. Jan 8, 2021. URL: https://www.physicianleaders.org/articles/cybersecurity-healthcare-industry-collaborative-approach [accessed 2024-05-06]
- Djenna A, Harous S, Saidouni DE. Internet of things meet internet of threats: new concern cyber security issues of critical cyber infrastructure. Appl Sci. May 17, 2021;11(10):4580. [ FREE Full text ] [ CrossRef ]
- Francis R. Medical devices that could put you at security risk. IDG Communications. Apr 27, 2017. URL: https://www.csoonline.com/article/561347/medical-devices-that-could-put-you-at-security-risk.html [accessed 2024-05-06]
- Handa A, Sharma A, Shukla SK. Machine learning in cybersecurity: a review. WIREs Data Min Knowl. Feb 17, 2019;9(4):e1306. [ FREE Full text ] [ CrossRef ]
- Lechner NH. Developing a compliant cybersecurity process for medical devices. In: Proceedings of the Central European Conference on Information and Intelligent Systems. 2018. Presented at: CECIIS 2018; September 19-21, 2018; Varaždin, Croatia. URL: https://www.proquest.com/openview/8a2a254a80f34ef64b55c71d5bac01d6/1?pq-origsite=gscholar&cbl=1986354
- Lewis CJ. Cybersecurity in healthcare. Utica College. 2014. URL: https://tinyurl.com/3usz5jat [accessed 2024-05-16]
- Lyon D. Making trade-offs for safe, effective, and secure patient care. J Diabetes Sci Technol. Mar 2017;11(2):213-215. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Mohan A. Cyber security for personal medical devices internet of things. In: Proceedings of the IEEE International Conference on Distributed Computing in Sensor Systems. 2014. Presented at: DCOSS 2014; May 26-28, 2014; Marina Del Rey, CA. URL: https://doi.org/10.1109/DCOSS.2014.49 [ CrossRef ]
- Baranchuk A, Refaat MM, Patton KK, Chung MK, Krishnan K, Kutyifa V, et al. Cybersecurity for cardiac implantable electronic devices: what should you know? J Am Coll Cardiol. Mar 20, 2018;71(11):1284-1288. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Perakslis E. Cybersecurity in health care. N Engl J Med. Jul 31, 2014;371(5):395-397. [ FREE Full text ] [ CrossRef ]
- Peterson A. Yes, terrorists could have hacked Dick Cheney’s heart. The Washington Post. Oct 21, 2013. URL: https://www.washingtonpost.com/news/the-switch/wp/2013/10/21/yes-terrorists-could-have-hacked-dick-cheneys-heart/ [accessed 2024-05-06]
- Sajedi H, Rahbar Yaghobi S. Information hiding methods for E-Healthcare. Smart Health. Mar 2020;15:100104. [ FREE Full text ] [ CrossRef ]
- Omotosho A, Adegbola O, Mikail OO, Emuoyibofarhe J. A secure electronic prescription system using steganography with encryption key implementation. Int J Comput Inform Technol. Sep 2014;03(5):980-986. [ CrossRef ]
- Singh Rayat A, Singh I, Singh K. Review on security challenges of data communication in IoT devices. Int J Electron Eng. 2019;11(2):406-415. [ FREE Full text ]
- Sittig DF, Singh H. Electronic health records and national patient-safety goals. N Engl J Med. Nov 08, 2012;367(19):1854-1860. [ FREE Full text ] [ CrossRef ]
- Snell E. Healthcare data breach costs highest for 7th straight year. Health IT Security. 2017. URL: https://healthitsecurity.com/news/healthcare-data-breach-costs-highestfor-7th-straight-year [accessed 2024-05-06]
- Bhuyan SS, Kabir UY, Escareno JM, Ector K, Palakodeti S, Wyant D, et al. Transforming healthcare cybersecurity from reactive to proactive: current status and future recommendations. J Med Syst. Apr 02, 2020;44(5):98. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Raina MacIntyre C, Engells TE, Scotch M, Heslop DJ, Gumel AB, Poste G, et al. Converging and emerging threats to health security. Environ Syst Decis. 2018;38(2):198-207. [ FREE Full text ] [ CrossRef ] [ Medline ]
- Filkins BL, Kim JY, Roberts B, Armstrong W, Miller MA, Hultner ML, et al. Privacy and security in the era of digital health: what should translational researchers know and do about it? Am J Transl Res. 2016;8(3):1560-1580. [ FREE Full text ] [ Medline ]
- Rodrigues JJ, de la Torre I, Fernández G, López-Coronado M. Analysis of the security and privacy requirements of cloud-based electronic health records systems. J Med Internet Res. Aug 21, 2013;15(8):e186. [ FREE Full text ] [ CrossRef ] [ Medline ]
- -. Verizon: 2019 data breach investigations report. Comput Fraud Secur. Jan 2019;2019(6). [ CrossRef ]
- 2022 cost of insider threats global report. Ponemon Institute. 2022. URL: https://protectera.com.au/wp-content/uploads/2022/03/The-Cost-of-Insider-Threats-2022-Global-Report.pdf [accessed 2024-05-06]
- Wagner S. The medical data of hundreds of HUG patients accessible on the internet. Ictjournal. 2019. URL: https://www.ictjournal.ch/news/2019-10-04/les-donnees-medicales-dune-centaines-de-patients-des-hug-accessibles-sur-internet [accessed 2019-10-04]
- Arapi K. The healthcare industry: evolving cyber threats and risks. Utica College. May 2018. URL: https://www.proquest.com/openview/6fb8d8f9984e83b682b5499fb1d36194/1?pq-origsite=gscholar&cbl=18750 [accessed 2024-05-06]
- Perriello B. ‘Medjack:’ hackers threaten hospitals using medical devices as back doors. MassDevice. Jun 5, 2015. URL: https://www.massdevice.com/medjack-hackers-threaten-hospitals-using-medical-devices-as-back-doors/ [accessed 2024-05-06]
- Meggitt S. MEDJACK attacks: the scariest part of the hospital. Tufts University. Dec 18, 2018. URL: https://www.cs.tufts.edu/comp/116/archive/fall2018/smeggitt.pdf [accessed 2024-05-06]
- Rajamäki J, Pirinen R. Towards the cyber security paradigm of ehealth: resilience and design aspects. AIP Conf Proc. Jun 5, 2017;1836(1). [ FREE Full text ] [ CrossRef ]
- Murphy S. Is cybersecurity possible in healthcare? National Cybersecur Institute J. 2015;1(3):49. [ FREE Full text ]
- Kioskli K, Fotis T, Mouratidis H. The landscape of cybersecurity vulnerabilities and challenges in healthcare: security standards and paradigm shift recommendations. In: Proceedings of the 16th International Conference on Availability, Reliability and Security. 2021. Presented at: ARES '21; August 17-20, 2021; Vienna, Austria. URL: https://doi.org/10.1145/3465481.3470033 [ CrossRef ]
- Tuttle I. Cyberdisaster: how the government compromised our security. National Review. Sep 9, 2016. URL: https://www.nationalreview.com/2016/09/opm-hack-house-oversight-committee-report/ [accessed 2024-05-08]
- Loi M, Christen M, Kleine N, Weber K. Cybersecurity in health – disentangling value tensions. J Inform Commun Ethics Soc. May 13, 2019;17(2):229-245. [ FREE Full text ] [ CrossRef ]
- Christen M, Gordijn B, Loi M. The ethics of cybersecurity. CrimRxiv. 2020. URL: https://www.crimrxiv.com/pub/s79bo1xu/release/1 [accessed 2024-05-06]
- Coles-Kemp L, Williams PA. Changing places: the need to alter the start point for information security design. Electron J Health Inform. 2014;8(2). [ FREE Full text ]
- Khaloufi H, Abouelmehdi K, Beni-hssane A, Saadi M. Security model for big healthcare data lifecycle. Procedia Comput Sci. 2018;141:294-301. [ FREE Full text ] [ CrossRef ]
- Holst C, Sukums F, Radovanovic D, Ngowi B, Noll J, Winkler AS. Sub-Saharan Africa—the new breeding ground for global digital health. Lancet Digit Health. Apr 2020;2(4):e160-e162. [ FREE Full text ] [ CrossRef ]
- Khando K, Gao S, Islam SM, Salman A. Enhancing employees information security awareness in private and public organisations: a systematic literature review. Comput Secur. Jul 2021;106:102267. [ FREE Full text ] [ CrossRef ]
- Winton R. Hollywood hospital pays $17,000 in bitcoin to hackers; FBI investigating. Los Angeles Times. Feb 18, 2016. URL: https://tinyurl.com/5yae788s [accessed 2024-05-06]
- Dobuzinskis A, Finkle J. California hospital makes rare admission of hack, ransom payment. Reuters. Feb 20, 2016. URL: https://www.reuters.com/article/idUSKCN0VS05M/ [accessed 2024-05-06]
- Bickers S, Dunlevy S, Minear T. Hackers are offering to sell the medicare details of Australians on the dark web, government confirms. News Corp Australia Network. Jul 4, 2017. URL: https://tinyurl.com/4ryf66v8 [accessed 2024-05-06]
- Zorabedian J. How malware works: anatomy of drive-by download web attack. Sophos News. Mar 26, 2014. URL: https://news.sophos.com/en-us/2014/03/26/how-malware-works-anatomy-of-a-drive-by-download-web-attack-infographic/ [accessed 2024-05-06]
- Omotosho A, Asanga U, Fakorede A. Electronic prescription system for pediatricians. Eur Sci J. 2017;13(18):426. [ FREE Full text ] [ CrossRef ]
- Chen B, Ren Z, Yu C, Hussain I, Liu J. Adversarial examples for CNN-based malware detectors. IEEE Access. 2019;7:54360-54371. [ FREE Full text ] [ CrossRef ]
Abbreviations
Edited by A Mavragani; submitted 03.03.23; peer-reviewed by R Marshall, V Perez Jover; comments to author 27.07.23; revised version received 17.10.23; accepted 08.03.24; published 31.05.24.
©Pius Ewoh, Tero Vartiainen. Originally published in the Journal of Medical Internet Research (https://www.jmir.org), 31.05.2024.
This is an open-access article distributed under the terms of the Creative Commons Attribution License (https://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work, first published in the Journal of Medical Internet Research, is properly cited. The complete bibliographic information, a link to the original publication on https://www.jmir.org/, as well as this copyright and license information must be included.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- JMIR Med Inform
- v.6(2); Apr-Jun 2018
Health Information Technology in Healthcare Quality and Patient Safety: Literature Review
Sue s feldman.
1 Department of Health Services Administration, The University of Alabama at Birmingham, Birmingham, AL, United States
Scott Buchalter
2 Pulmonary and Critical Care, The University of Alabama at Birmingham Medical Center, Birmingham, AL, United States
Leslie W Hayes
3 Department of Pediatrics, The University of Alabama at Birmingham Medical Center, Birmingham, AL, United States
The area of healthcare quality and patient safety is starting to use health information technology to prevent reportable events, identify them before they become issues, and act on events that are thought to be unavoidable. As healthcare organizations begin to explore the use of health information technology in this realm, it is often unclear where fiscal and human efforts should be focused.
The purpose of this study was to provide a foundation for understanding where to focus health information technology fiscal and human resources as well as expectations for the use of health information technology in healthcare quality and patient safety.
A literature review was conducted to identify peer-reviewed publications reporting on the actual use of health information technology in healthcare quality and patient safety. Inductive thematic analysis with open coding was used to categorize a total of 41 studies. Three pre-set categories were used: prevention, identification, and action. Three additional categories were formed through coding: challenges, outcomes, and location.
This study identifies five main categories across seven study settings. A majority of the studies used health IT for identification and prevention of healthcare quality and patient safety issues. In this realm, alerts, clinical decision support, and customized health IT solutions were most often implemented. Implementation, interface design, and culture were most often noted as challenges.
Conclusions
This study provides valuable information as organizations determine where they stand to get the most “bang for their buck” relative to health IT for quality and patient safety. Knowing what implementations are being effectivity used by other organizations helps with fiscal and human resource planning as well as managing expectations relative to cost, scope, and outcomes. The findings from this scan of the literature suggest that having organizational champion leaders that can shepherd implementation, impact culture, and bridge knowledge with developers would be a valuable resource allocation to consider.

Introduction
It has long been known and accepted that healthcare in the US is too expensive and the outcomes are less than predictable [ 1 ]. The turn of the century brought with it a realization that healthcare, like other industries, could use data to increase our awareness of seemingly uncontrollable costs and unpredictable outcomes. With almost two decades of compiling, analyzing, mashing up data, and trying to make sense of how the data inform multiple layers of healthcare, it is time to look beyond the awareness that the data provide, and instead develop an understanding of how to use the data for predictable and actionable purposes, especially with regard to healthcare quality and patient safety. The literature is mixed on the degree to which health information technology (IT) as a valuable suite of tools, applications, and systems that have contributed to actual savings and efficiencies [ 1 - 4 ]. However, the area of healthcare quality and patient safety lends itself to many of the same business intelligence and predictability advantages that are seen in the credit card industry [ 5 - 7 ].
Much like the Triple Aim of Healthcare, the credit card industry is working toward decreased costs (fraud), increased quality (better transactions), and increased satisfaction (happier merchants and happier cardholders). The credit card industry began using business intelligence to predict behavior that suggested fraud, developed process maps for transaction processing, and offered perks to merchants and cardholders. Just as the credit card industry learned from healthcare, healthcare can borrow from the credit card industry to use healthcare intelligence for prevention, identification, and action related to healthcare quality and patient safety events.
The Institute for Healthcare Improvement (IHI) suggests that reliability around healthcare is a three-part cycle of failure prevention, failure identification, and process redesign and defines reliability as “failure-free operation over time.” [ 8 ]. Other areas of healthcare have used information systems to provide continuous monitoring with real-time, or near real-time reporting as a means of achieving reliability [ 9 ]. As such, it makes sense to think about the role of health IT in reliability as it relates to healthcare quality and patient safety. A review of the literature suggests that healthcare organizations are using health IT for healthcare quality and patient safety and that they have replaced redesign in Figure 1 with action as shown in Figure 2 [ 10 - 12 ]. Action, in this case, allows for health IT to be implemented after a potential healthcare quality or patient safety event has occurred and does not necessarily require a redesign. Ordering alerts in the electronic health record are an example of action; the event has occurred (the order has been entered) and health IT in the form of an alert is initiated to stop the potentially unsafe order from being filled by the pharmacy.

Improving the reliability of healthcare.

Improving the reliability of healthcare quality and patient safety.
Having an understanding of this cycle helps to create awareness around where various applications of health IT find their “best fit” in improving the reliability of healthcare quality and patient safety. A distinct advantage of this being a “cycle” is that there is no defined beginning and ending point, but rather an insertion point. This is all to say that the cycle should not be interpreted as starting with prevention and ending with action.
Health Information Technology for Prevention of Quality and Safety Events
Health IT for prevention of quality and safety events involves the use of health IT to prevent a quality and safety event from even happening . Automated reminders and alerts are useful in providing essential information that supports safe and effective clinical decisions [ 13 ]. Such alerts in the electronic health record (EHR) are a standard mechanism for the use of health IT for prevention of potential missed quality and patient safety events. For example, immunization alerts have led to a 12% increase in well-child and a 22% increase in sick child immunization administration [ 14 ] and drug alerts have been associated with a 22% decrease in medication prescription errors [ 15 ]. Soft-stops can provide key information about a potential quality or patient safety issue. They may offer choices but usually, require only that the user acknowledge the alert to proceed.
A hard-stop, on the other hand, prevents the user from moving forward with an order or intervention that would be potentially dangerous to a patient. Hard-stops may allow continuation of the process, but only if significant required action is taken by the user, such as a call to or consultation with an expert (such as a pharmacist or a medical specialist). In some cases, soft-stops might be ignored or overridden because of such issues as alert fatigue, poor implementation, or poor interface design [ 16 , 17 ]. Hard-stops, when appropriately designed, have been shown to be more successful in changing an unsafe plan or preventing a potentially dangerous intervention [ 18 , 19 ].
Health Information Technology for Identification of Quality and Safety Events
Health IT for identification of quality and safety events involves health IT that is used to identify a quality and safety event when it is about to occur . Health insurance providers increasingly place pressure on healthcare systems to reduce the cost of care delivery and improve patient outcomes. This pressure may exist through tiered reimbursement structures, benefitting those systems which meet or exceed specific benchmarks of performance. Growing pressure from these payers takes the form of non-reimbursement for care determined by the payer to be unnecessary or in excess of “standard care.” Health IT can be used to find the EHR populations of patients for whom reimbursement might be lower than expected. One such example to consider is the length of stay for a particular procedure. While the use of health IT can produce reports and dashboards that are helpful for decision-making relative to reimbursement trends and practices for lengths of stay for that diagnosis, it is crucial that thoughtful consideration be given for appreciating any unintended consequences. For example, when reducing the length of stay, unintended readmissions are an important metric to follow.
Health Information Technology for Action in Quality and Safety Events
Health IT for action of quality and safety events involves health IT that is used to a ct on a quality and safety event once it has already occurred. That is to say that these are actions that were reported in the literature that were taken as a result of an event. Health IT for action differs from health IT for prevention in that the former is a reaction directly correlated to an event reported in the article, whereas the latter is reported in the article as a preemptive measure, in advance of an event.
Because of their standardization, there are several clinical care pathways that lend themselves to clinical decision support. One such clinical care pathway is sepsis. Despite nearly two decades of advances in early sepsis care, sepsis outcomes persist to be poor, and sepsis remains a leading cause of death worldwide and accounts for significant morbidity and mortality [ 20 ]. In light of this, there is a growing national push to increase early identification and treatment of sepsis with a goal of improving outcomes. Patients with sepsis are some of the most critically ill patients admitted to hospitals, and survival depends heavily upon timely and early administration of key interventions followed quickly by assessing and acting on results of these interventions [ 21 ]. Some examples include administration of IV antibiotics and aggressive IV fluids within one hour [ 21 ]. Examples of assessments of interventions include measuring specific physical and laboratory values that provide crucial information about the patient response. All too often, clinicians are faced with an overabundance of data, that while all necessary, may not be relevant to the issue at hand. For example, lab results might be presented in their entirety, when in practice, there are only 3 or 4 tests that will drive decision-making. The difficulty is how to separate the noise (non-essential at that moment) from the signal (essential at that moment). Health IT solutions, such as dashboards and other solutions can be used to ensure that essential data are in a primary viewing position and non-essential data in a secondary viewing position (perhaps on drill down, for example).
This paper will provide foundational knowledge and understanding for organizations of where to focus health IT fiscal and human resources. It will also provide information relative to some of the challenges that can be expected in implementing health IT for quality and patient safety.
This review of the literature took a structured approach using PubMed and a combination of keywords. Since PubMed indexes peer-reviewed articles from biomedical information, it was felt that this was the most appropriate and inclusive source. A healthcare-focused librarian, under the direction of all authors, conducted the literature search. The articles for final selection were discussed and decided upon among the authors. The structured approach was guided by the model illustrated in Figure 3 .

Literature search process.
The process to article inclusion involved three passes to collect publications related to health IT in quality and patient safety for peer-reviewed studies published between 2012-2017, inclusive. The first pass, (shown as “1” in Figure 3 ), used high-level keywords and returned 86 full-text articles. From the articles gathered, additional keywords were added to the search. After deduplication and citation review, the second pass (shown as “2” in Figure 3 ) added 67 unique full-text articles. After deduplication and citation review, the third pass (shown as “3” in Figure 3 ) added 11 unique full-text articles, for a total of 164 unique full text articles. Each article was further analyzed to identify the degree to which the article discussed health IT in healthcare quality and patient safety. To be considered for inclusion, the study needed to report on the actual use of health IT in healthcare quality and patient safety. Forty-one studies met these criteria. Those studies with their contributions to the results are shown in the results section of this paper.
Qualitative data analysis software (Atlas.ti 8 for Windows) was used in directed content analysis as a method to categorize and code the 41 studies relative to how health IT was used in healthcare quality and patient safety. All 41 documents were uploaded into the document manager in Atlas.ti as Primary Documents (PD). During this process, the article title was used as the PD name. Inductive thematic analysis with open coding was used under the three pre-set categories of prevention, identification, and action [ 22 ]. This allowed for capturing descriptions of how health IT was used in each circumstance.
For example, prevention included descriptions of any use of health IT to prevent quality issues or potential safety events, identification included any descriptions of the use of health IT to identify quality issues or safety events, and action included any descriptions of the use of health IT to act on quality issues or safety events that have occurred. When content was noted that did not fit into the three pre-set categories, an additional category was created. Additional categories were created to capture challenges relative to the use of health IT in quality and patient safety. Since some papers discussed how the use of health IT impacted health outcomes, an additional category was created for outcomes. Lastly, an additional category was created to capture the study settings or location.
The coding structure was agreed upon by all authors, and one author conducted the coding. After all of the studies were coded, two additional passes were made through the data. The first pass was to ensure that all information from the studies that should be coded was actually coded and coded to the correct code (ie, was a passage that described prevention actually coded to prevention?). The second pass was to consider sub-categories for consolidation. Six sub-categories were consolidated.
The purpose of examining co-occurrences is to understand what, if any, relation exists between concepts [ 22 , 23 ]. Within Atlas.ti, a co-occurrence table was run to find codes that co-occur across the literature, the purpose of which was to illuminate the areas most discussed. This table was then exported to Microsoft Excel for further analysis.
Network maps are a means by which analysis can be visualized in relationships to provide a different perspective on the codes, categories, etc., and with that visualization, provide a mechanism for moving codes around [ 22 ]. Those presented in the results do not differ from the final coding structure, but instead are used to provide a visual representation.
Literature reviews can be conducted using a qualitative approach [ 24 , 25 ] with the results displayed in a variety of ways to support models and show connections [ 22 ]. As such, this review presents qualitative findings to support the “improving the reliability of healthcare quality and patient safety” model introduced earlier in this paper and shows connections via network mappings in Figure 6 through Figure 7 and co-occurrences in Table 2 .

IDENTIFICATION Network Diagram (G=groundedness, D=density).

PREVENTION Network Diagram (G=groundedness, D=density).
a IT: information technology.
Table 1 provides a listing of the articles and their contribution in this results section to support the model ( Figure 2 ), network maps ( Figure 4 through Figure 7 ), and co-occurrences ( Table 2 ).
Article contribution to results (in alphabetical order). An “X” indicates the area of the results contribution and “—” indicates no contribution.

ACTION Network Diagram (G=groundedness, D=density).
From the 41 studies that fit the inclusion criteria, any element in which the authors discussed the use of health IT for healthcare quality and patient safety was identified, even if it did not fit into the three previously determined categories. This process yielded a total of 50 codes across five categories: action (7/41, 17.1%), challenges (12/41, 29.3%), identification (10/41, 24.4%), outcomes (5/41, 12.2%), and prevention (16/41, 39.0%) across seven study settings. Just under a quarter of the studies identified a study setting: anesthesia (2/41, 4.9%), behavioral health (1/41, 2.4%), emergency department (2/41, 4.9%), any intensive care unit (3/41, 7.3%), clinical diagnostic laboratory (1/41, 2.4%), pediatrics (2/41, 4.9), surgery (1/41, 2.4%).
Across all of the articles, there were 63 and 92 descriptions of the use of health IT for identification and prevention of healthcare quality and patient safety issues, respectively. Health IT for action and the challenges associated with health IT for healthcare quality and patient safety was described 41 and 43 times, respectively.
The findings from the literature review are presented by the categories outlined in the previously introduced model for improving the reliability of healthcare quality and patient safety.
The first exploration was across the literature that discussed health IT for prevention of quality and patient safety issues to see exactly how organizations were reporting health IT use to prevent a quality and safety event from even happening . The greatest areas of use were around alerts [ 30 , 31 , 44 , 56 , 58 ], clinical decision support [ 39 , 44 , 47 , 56 ], implementation [ 10 , 32 , 37 , 38 , 56 ], interface design [ 26 , 34 , 42 , 45 , 56 , 59 ], and customized health IT solutions [ 29 , 30 , 32 , 34 , 46 - 50 , 56 , 58 , 59 ]. Customized health IT solutions were anything that described the use of health IT but lacked any specificity beyond that described in this section. For example, this could be something as simple as checklists or as complex as algorithmic diagnostic trees. To clarify, alerts are a subset of clinical decision support. Since so many of the occurrences specified alerts and clinical decision support separately, these were coded separately. Clinical decision support, by definition, includes alerts, clinical care guidelines, condition-specific orders sets, clinical reports and/or summaries, documentation templates, diagnostic support, and clinical reference support. Implementation and interface design were each described in terms of having been poorly implemented or poorly designed and having implications on utility in healthcare quality and safety.
Identification
The next exploration was across the literature that discussed health IT for identification of quality and patient safety issues; in other words, how health IT was used to identify a quality and safety event when it is about to occur . In this regard, similar to prevention (but described differently in the included studies), alerts [ 26 , 30 , 31 , 44 , 56 , 58 ], clinical decision support [ 30 , 31 , 39 , 44 , 56 , 58 ], implementation [ 10 , 32 , 38 , 56 ], and customized health IT solutions [ 10 , 30 , 31 , 34 , 46 - 49 , 52 , 56 , 58 ] were most prominent. For example, alerts, clinical decision support, and customized health IT solutions were all described in the literature as having been implemented to identify a potential quality or patient safety issue, yet the literature also described how the implementation of these could have been better in terms of providing more training to those on the receiving end of the alerts, clinical decision support, or other customized health IT solutions.

OUTCOMES Network Diagram (G=groundedness, D=density).
The third exploration was across the literature that discussed health IT for action on a quality and safety event once it has already occurred. That is to say that these are actions that were reported in the literature that were taken as a result of an event. In regards to action, the major areas were documentation [ 10 , 32 , 37 , 41 , 46 , 56 , 58 ], implementation [ 10 , 32 , 37 , 58 ], and culture [ 10 , 29 , 41 , 53 , 58 ] relative to the use of health IT.
The findings from the review of the literature show that implementation appeared in prevention, identification, and action. Implementation in general has been demonstrated in the literature as a challenge, and that was revealed in this literature review also. Culture was most often referred to as needing to create a culture of quality and patient safety in order for health IT to be embraced. Organizations that started working on culture change before implementation of health IT solutions suggested that health IT for acting on quality and patient safety events was more favorable. Therefore, the analysis was run with challenges which suggests the major areas are: culture, implementation, and interface design.
Co-occurrences
Employing the Improving the reliability of healthcare quality and patient safety model introduced in Figure 2 and adding challenges, six critical co-occurrences emerged (see Table 2 ).
As described earlier, co-occurrences expose relationships exists between concepts [ 22 , 23 ]. The top co-occurring codes in Table 2 create a macro level view of how health IT was most commonly used for quality and patient safety relative to the “improving the reliability of healthcare quality and patient safety” model introduced in Figure 2 . However, it is also important to understand the universe of ways in which organizations used health IT for quality and patient safety; in other words, the art of the possible when using health IT for quality and patient safety. Network maps provide a mechanism by which to visualize the connectedness of all data coded across all 41 articles included in this analysis. These maps, along with some quantitative information increase understanding at this universe level (macro and micro views).
In the network diagrams that follow (which also represent the coded categories and sub-categories), G signifies the level of groundedness of the particular code. Groundedness, in this case, indicates the frequency of the code relative to the code category. D signifies the level of density or connectedness of the particular code. Density, in this case, indicates the number of other codes to which this code is connected. For example, under ACTION, Figure 4 , the code action: culture shows G6, D2. ACTION is the code category and action: culture is the code “culture” under the ACTION code category (this coding structure helps to maintain alpha order). This can be read as the following: “Culture was described six times across all 41 papers relative to ACTION and is connected to two code categories total.” Because it would make the network diagrams unwieldy, not shown in the exhibits is the specificity around the groundedness or the density. See Figures 4 through Figure 7 .
Principal Findings
This scan of the literature is intended to inform practice. The information from this study could be useful as organizations determine where they stand to get the most “bang for their buck” relative to health IT for quality and patient safety. Centered around the Improving the Reliability of Healthcare Quality and Safety model introduced in Figure 2 and the macro level uses of health IT for quality and patient safety outlined in Table 2 , organizations in the planning stages may want to begin with alerts and clinical decision support, understanding that alerts are a subset of clinical decision support. This information also helps with resource planning. For example, implementation appeared in all three categories of the Improving the Reliability of Healthcare Quality and Safety model. Additionally, culture was shown to be a challenge. Organizational leaders know that changing culture can be a long and intensive process. The findings from this scan of the literature suggest that having organizational champion leaders that can shepherd implementation, impact culture, and bridge knowledge with developers would be a valuable resource allocation to consider.
Health IT must meet quality improvement at the intersection with care delivery. From a clinical perspective, this is experienced on several levels, and the solution depends, in part, on the clinical problem to be addressed. Some typical examples of health IT interventions illuminated in the findings include: (1) reminders and alerts, (2) decision support tools, (3) checklists (including order sets and protocols), and (4) soft- and hard-stops.
As noted, this scan of the literature is provided as a means to inform practice. It does not consider further model modification, and this represents an area of future research in the application of health IT for quality and patient safety.
Limitations
This study is limited in that it used PubMed as a single source for the searching and one coder coded all studies. A more comprehensive and systematic review would include multiple databases and multiple coders. Although all authors reviewed the codes, multiple coders would ensure intercoder reliability, which cannot be assured in this study. Additionally, since all studies reviewed did not include locations, generalizability to all areas of clinical care cannot be certain.
A review of the literature for this study concluded that organizations in the planning stages of using health IT to improve quality and safety may want to begin with reminders and alerts, decision support tools, and checklists.
Acknowledgments
The authors acknowledge and appreciate the careful, detailed, and thoughtful comments by the reviewers whose suggestions strengthened this paper.
Abbreviations
Conflicts of Interest: None declared.
Are you seeking one-on-one college counseling and/or essay support? Limited spots are now available. Click here to learn more.
54 Most Interesting Technology Research Topics for 2023
May 30, 2023
Scrambling to find technology research topics for the assignment that’s due sooner than you thought? Take a scroll down these 54 interesting technology essay topics in 10 different categories, including controversial technology topics, and some example research questions for each.
Social technology research topics
Whether you have active profiles on every social media platform, you’ve taken a social media break, or you generally try to limit your engagement as much as possible, you probably understand how pervasive social technologies have become in today’s culture. Social technology will especially appeal to those looking for widely discussed, mainstream technology essay topics.
- How do viewers respond to virtual influencers vs human influencers? Is one more effective or ethical over the other?
- Across social media platforms, when and where is mob mentality most prevalent? How do the nuances of mob mentality shift depending on the platform or topic?
- Portable devices like cell phones, laptops, and tablets have certainly made daily life easier in some ways. But how have they made daily life more difficult?
- How does access to social media affect developing brains? And what about mature brains?
- Can dating apps alter how users perceive and interact with people in real life?
- Studies have proven “doomscrolling” to negatively impact mental health—could there ever be any positive impacts?
Cryptocurrency and blockchain technology research topics
Following cryptocurrency and blockchain technology has been a rollercoaster the last few years. And since Bitcoin’s conception in 2009, cryptocurrency has consistently showed up on many lists of controversial technology topics.
- Is it ethical for celebrities or influential people to promote cryptocurrencies or cryptographic assets like NFTs ?
- What are the environmental impacts of mining cryptocurrencies? Could those impacts ever change?
- How does cryptocurrency impact financial security and financial health?
- Could the privacy cryptocurrency offers ever be worth the added security risks?
- How might cryptocurrency regulations and impacts continue to evolve?
- Created to enable cryptocurrency, blockchain has since proven useful in several other industries. What new uses could blockchain have?
Artificial intelligence technology research topics
We started 2023 with M3GAN’s box office success, and now we’re fascinated (or horrified) with ChatGPT , voice cloning , and deepfakes . While people have discussed artificial intelligence for ages, recent advances have really pushed this topic to the front of our minds. Those searching for controversial technology topics should pay close attention to this one.
- OpenAI –the company behind ChatGPT–has shown commitment to safe, moderated AI tools that they hope will provide positive benefits to society. Sam Altman, their CEO, recently testified before a US Senate He described what AI makes possible and called for more regulation in the industry. But even with companies like OpenAI displaying efforts to produce safe AI and advocating for regulations, can AI ever have a purely positive impact? Are certain pitfalls unavoidable?
- In a similar vein, can AI ever actually be ethically or safely produced? Will there always be certain risks?
- How might AI tools impact society across future generations?
- Countless movies and television shows explore the idea of AI going wrong, going back all the way to 1927’s Metropolis . What has a greater impact on public perception—representations in media or industry developments? And can public perception impact industry developments and their effectiveness?
Beauty and anti-aging technology
Throughout human history, people in many cultures have gone to extreme lengths to capture and maintain a youthful beauty. But technology has taken the pursuit of beauty and youth to another level. For those seeking technology essay topics that are both timely and timeless, this one’s a gold mine.
- With augmented reality technology, companies like Perfect allow app users to virtually try on makeup, hair color, hair accessories, and hand or wrist accessories. Could virtual try-ons lead to a somewhat less wasteful beauty industry? What downsides should we consider?
- Users of the Perfect app can also receive virtual diagnoses for skin care issues and virtually “beautify” themselves with smoothed skin, erased blemishes, whitened teeth, brightened under-eye circles, and reshaped facial structures. How could advancements in beauty and anti-aging technology affect self-perception and mental health?
- What are the best alternatives to animal testing within the beauty and anti-aging industry?
- Is anti-aging purely a cosmetic pursuit? Could anti-aging technology provide other benefits?
- Could people actually find a “cure” to aging? And could a cure to aging lead to longer lifespans?
- How might longer human lifespans affect the Earth?
Geoengineering technology research topics
An umbrella term, geoengineering refers to large-scale technologies that can alter the earth and its climate. Typically, these types of technologies aim to combat climate change. Those searching for controversial technology topics should consider looking into this one.
- What benefits can solar geoengineering provide? Can they outweigh the severe risks?
- Compare solar geoengineering methods like mirrors in space, stratospheric aerosol injection, marine cloud brightening, and other proposed methods. How have these methods evolved? How might they continue to evolve?
- Which direct air capture methods are most sustainable?
- How can technology contribute to reforestation efforts?
- What are the best uses for biochar? And how can biochar help or harm the earth?
- Out of all the carbon geoengineering methods that exist or have been proposed, which should we focus on the most?
Creative and performing arts technology topics
While tensions often arise between artists and technology, they’ve also maintained a symbiotic relationship in many ways. It’s complicated. But of course, that’s what makes it interesting. Here’s another option for those searching for timely and timeless technology essay topics.
- How has the relationship between art and technology evolved over time?
- How has technology impacted the ways people create art? And how has technology impacted the ways people engage with art?
- Technology has made creating and viewing art widely accessible. Does this increased accessibility change the value of art? And do we value physical art more than digital art?
- Does technology complement storytelling in the performing arts? Or does technology hinder storytelling in the performing arts?
- Which current issues in the creative or performing arts could potentially be solved with technology?
Cellular agriculture technology research topics
And another route for those drawn to controversial technology topics: cellular agriculture. You’ve probably heard about popular plant-based meat options from brands like Impossible and Beyond Meat . While products made with cellular agriculture also don’t require the raising and slaughtering of livestock, they are not plant-based. Cellular agriculture allows for the production of animal-sourced foods and materials made from cultured animal cells.
- Many consumers have a proven bias against plant-based meats. Will that same bias extend to cultured meat, despite cultured meat coming from actual animal cells?
- Which issues can arise from patenting genes?
- Does the animal agriculture industry provide any benefits that cellular agriculture may have trouble replicating?
- How might products made with cellular agriculture become more affordable?
- Could cellular agriculture conflict with the notion of a “ circular bioeconomy ?” And should we strive for a circular bioeconomy? Can we create a sustainable relationship between technology, capitalism, and the environment, with or without cellular agriculture?
Transportation technology research topics
For decades, we’ve expected flying cars to carry us into a techno-utopia, where everything’s shiny, digital, and easy. We’ve heard promises of super fast trains that can zap us across the country or even across the world. We’ve imagined spring breaks on the moon, jet packs, and teleportation. Who wouldn’t love the option to go anywhere, anytime, super quickly? Transportation technology is another great option for those seeking widely discussed, mainstream technology essay topics.
- Once upon a time, Lady Gaga was set to perform in space as a promotion for Virgin Galactic . While Virgin Galactic never actually launched the iconic musician/actor, soon, they hope to launch their first commercial flight full of civilians–who paid $450,000 a pop–on a 90-minute trip into the stars. And if you think that’s pricey, SpaceX launched three businessmen into space for $55 million in April, 2022 (though with meals included, this is actually a total steal). So should we be launching people into space just for fun? What are the impacts of space tourism?
- Could technology improve the way hazardous materials get transported?
- How can the 5.9 GHz Safety Band affect drivers?
- Which might be safer: self-driving cars or self-flying airplanes?
- Compare hyperloop and maglev Which is better and why?
- Can technology improve safety for cyclists?
Gaming technology topics
A recent study involving over 2000 children found links between video game play and enhanced cognitive abilities. While many different studies have found the impacts of video games to be positive or neutral, we still don’t fully understand the impact of every type of video game on every type of brain. Regardless, most people have opinions on video gaming. So this one’s for those seeking widely discussed, mainstream, and controversial technology topics.
- Are different types or genres of video games more cognitively beneficial than others? Or are certain gaming consoles more cognitively beneficial than others?
- How do the impacts of video games differ from other types of games, such as board games or puzzles?
- What ethical challenges and safety risks come with virtual reality gaming?
- How does a player perceive reality during a virtual reality game compared to during other types of video games?
- Can neurodivergent brains benefit from video games in different ways than neurotypical brains?
Medical technology
Advancements in healthcare have the power to change and save lives. In the last ten years, countless new medical technologies have been developed, and in the next ten years, countless more will likely emerge. Always relevant and often controversial, this final technology research topic could interest anyone.
- Which ethical issues might arise from editing genes using CRISPR-Cas9 technology? And should this technology continue to be illegal in the United States?
- How has telemedicine impacted patients and the healthcare they receive?
- Can neurotechnology devices potentially affect a user’s agency, identity, privacy, and/or cognitive liberty?
- How could the use of medical 3-D printing continue to evolve?
- Are patients more likely to skip digital therapeutics than in-person therapeutic methods? And can the increased screen-time required by digital therapeutics impact mental health
What do you do next?
Now that you’ve picked from this list of technology essay topics, you can do a deep dive and immerse yourself in new ideas, new information, and new perspectives. And of course, now that these topics have motivated you to change the world, look into the best computer science schools , the top feeders to tech and Silicon Valley , the best summer programs for STEM students , and the best biomedical engineering schools .
- College Success
- High School Success
Mariya holds a BFA in Creative Writing from the Pratt Institute and is currently pursuing an MFA in writing at the University of California Davis. Mariya serves as a teaching assistant in the English department at UC Davis. She previously served as an associate editor at Carve Magazine for two years, where she managed 60 fiction writers. She is the winner of the 2015 Stony Brook Fiction Prize, and her short stories have been published in Mid-American Review , Cutbank , Sonora Review , New Orleans Review , and The Collagist , among other magazines.
- 2-Year Colleges
- Application Strategies
- Best Colleges by Major
- Best Colleges by State
- Big Picture
- Career & Personality Assessment
- College Essay
- College Search/Knowledge
- Costs & Financial Aid
- Data Visualizations
- Dental School Admissions
- Extracurricular Activities
- Graduate School Admissions
- High Schools
- Homeschool Resources
- Law School Admissions
- Medical School Admissions
- Navigating the Admissions Process
- Online Learning
- Outdoor Adventure
- Private High School Spotlight
- Summer Program Spotlight
- Summer Programs
- Teacher Tools
- Test Prep Provider Spotlight
“Innovative and invaluable…use this book as your college lifeline.”
— Lynn O'Shaughnessy
Nationally Recognized College Expert
College Planning in Your Inbox
Join our information-packed monthly newsletter.
- Research Paper Guides
- Research Paper Topics
- 450+ Technology Research Topics & Ideas for Your Paper
- Speech Topics
- Basics of Essay Writing
- Essay Topics
- Other Essays
- Main Academic Essays
- Basics of Research Paper Writing
- Miscellaneous
- Chicago/ Turabian
- Data & Statistics
- Methodology
- Admission Writing Tips
- Admission Advice
- Other Guides
- Student Life
- Studying Tips
- Understanding Plagiarism
- Academic Writing Tips
- Basics of Dissertation & Thesis Writing
- Essay Guides
- Formatting Guides
- Basics of Research Process
- Admission Guides
- Dissertation & Thesis Guides
450+ Technology Research Topics & Ideas for Your Paper

Table of contents
Use our free Readability checker
Technology is like a massive puzzle where each piece connects to form the big picture of our modern lives. Be it a classroom, office, or a hospital, technology has drastically changed the way we communicate and do business. But to truly understand its role, we need to explore different technology research topics.
And that's where this blog will be handy! Powered by solid experience, our professional term paper writers gathered multiple technology research paper topics in literally any direction. Whether you're a student looking for an intriguing subject for your project or just a tech enthusiast trying to broaden your understanding, we've got your back. Dive into this collection of tech topics and see how technological progress is shaping our world.
What Are Technology Topics?
Technology is the application of scientific knowledge for practical purposes. It's the smartphone in your hand, the electric car on your street, and the spacecraft exploring Mars. It might also be the code that protects your online privacy and the microscope that uncovers mysteries of the human cell.
Technology permeates our lives, revolutionizing the way we communicate, learn, work, and play. But, beyond the gadgets and gizmos, there's a world of diverse technology research topics, ideas, concepts, and challenges.
Technology topics zoom in on these ideas, peeling back the layers of the tech universe. As a researcher, you might study how AI is changing healthcare, explore the ethical implications of robotics, or investigate the latest innovations in renewable energy. Your project should probe into the 'how,' the 'why,' and the 'what next' of the technology that is reshaping our world. So, whether you're dissecting the impact of EdTech on traditional learning or predicting the future of space exploration, research topics in technology are limitless.
Branches of Technology Research Paper Topics
Undoubtedly, the reach of technology is extensive. It's woven its way into almost every corner of our lives. Before we move to technological research topics, let’s first see just where technology has left its mark. So, here are some areas where technology is really shaking things up:
- Government services: E-governance, digital IDs, and digital voting are just a few examples of technology's application in government services.
- Finance: Fintech innovations include cryptocurrencies, mobile banking, robo-advising, and contactless payments.
- Education: Technology is used in a wide variety of educational contexts, from e-learning platforms and digital textbooks to educational games and virtual classrooms.
- Communication: Social media, video conferencing, instant messaging, and email are all examples of tech's role in communication.
- Healthcare: From electronic medical records and telemedicine to advanced imaging technology and robotic surgery, technology is surely transforming healthcare.
- Agriculture: Technological advancements are revolutionizing agriculture through precision farming, automated machinery, drones, and genetic engineering.
- Retail: It also influences retail through e-commerce, mobile payments, virtual fitting rooms, and personalized shopping experiences.
- Environment: Tech is used in climate modeling, conservation efforts, renewable energy, and pollution control.
These are far from all sectors where technology can be applied. But this list shows how diverse topics in technology can be.
How to Choose a Technology Research Topic?
Before you select any idea, it’s important to understand what a good technology research topic is. In a nutshell, a decent topic should be interesting, relevant, and feasible to research within your available resources and time. Make sure it’s specific enough, but not to narrow so you can find enough credible resources.
Your technology topic sets the course of your research. It influences the type and amount of information you'll search for, the methods you'll use to find it, and the way you'll interpret it. Ultimately, the right topic can make your research process not only more manageable but also more meaningful. But how to get started, you may ask. Don’t worry! Below we are going to share valuable tips from our thesis writers on how to choose a worthy topic about technology.
- Make research Study the latest trends and explore relevant technology news. Your task is to come up with something unique that’s not been done before. Try to look for inspiration in existing literature, scientific articles, or in past projects.
- Recognize your interests Start with what you are genuinely curious about in the field of technology. Passion can be a great motivator during the research process.
- Consider the scope You want a topic that is neither too broad nor too narrow. It should provide enough material to explore without being overwhelming.
- Check availability of resources Ensure there are sufficient trustworthy resources available for your chosen topic.
- Evaluate the relevance Your technology research idea should be pertinent to your field of study and resonate with current trends. This can make your research more valuable and engaging for your audience.
Top List of Technology Research Topics
Are you looking for the best research topics about technology? Stop by! Here, we’ve carefully collected the topic ideas to ignite your curiosity and support your research. Each topic offers various data sources, allowing you to construct well-supported arguments. So, let's discover these fascinating subjects together!
- AI's influence on healthcare.
- Challenges of cybersecurity in a connected world.
- Role of drones in modern agriculture.
- Could renewable energy replace fossil fuels?
- Impact of virtual reality on education.
- Blockchain's potential beyond cryptocurrencies.
- Ethical considerations in biotechnology.
- Can smart cities enhance quality of life?
- Autonomous vehicles – opportunities and threats.
- Robotics in manufacturing.
- Is big data changing decision-making processes?
- E-waste : Challenges and solutions.
- Role of IoT in smart homes.
- Implications of 5G technology.
- EdTech: A revolution in learning?
Good Technology Research Topics
Ready for another batch of inspiration? Get ready to discover great technology topics for a research paper across various disciplines. These ideas are designed to stimulate your creativity and provide substantial information for your research. So, let's explore these exciting themes together!
- Impact of nanotechnology on medicine.
- Harnessing quantum computing potential.
- Augmented reality in tourism.
- Can bioinformatics revolutionize disease prediction?
- Sustainability in tech product design.
- Darknet : A hidden side of the internet.
- How does technology influence human behavior?
- Assistive technology in special education.
- Are smart textiles transforming the fashion industry?
- Role of GIS in urban planning.
- Space tourism: A reality or fantasy?
- Potential of digital twins in engineering.
- How is telemedicine shaping healthcare delivery?
- Green IT : Addressing environmental issues.
- Impact of machine learning on finance.
Interesting Technology Research Paper Topics
For those craving intriguing angles and fresh ideas, we present these interesting topics in technology. This collection is filled with thought-provoking subjects that cover the lesser-known areas of technology. Each topic is concise, clear, and ready to spark a fascinating research journey!
- Cyber-physical systems in industry 4.0.
- Social implications of deepfake technology.
- Can gamification enhance learning outcomes?
- Neuromorphic computing: Emulating the human brain.
- Li-Fi : Light-based communication technology.
- Health risks of prolonged screen time.
- Quantum cryptography and secure communication.
- Role of technology in sustainable agriculture.
- Can we predict earthquakes with AI?
- Virtual influencers: A new trend in marketing.
- Tech solutions for wildlife conservation.
- Role of 3D printing in organ transplantation.
- Impact of automation on the job market.
- Cloud gaming: A new era in the gaming industry.
- Genomic editing: Possibilities and ethical concerns.
New Technology Research Topics
Understanding the fast-paced world of technology requires us to keep up with the latest developments. Hence, we bring you burning technology research paper topics. These ideas reflect the most recent trends and advances in technology, offering fresh perspectives for your research. Let's take a look at these compelling subjects!
- Potential of hyper automation in business processes.
- How is AI changing digital marketing?
- Brain-computer interfaces: The future of communication?
- Quantum supremacy : Fact or fiction?
- 5D data storage: Revolutionizing data preservation.
- Rise of voice technology in consumer applications.
- Using AI for mental health treatment.
- Implications of edge computing for IoT devices.
- Personalized learning with AI in education.
- Role of technology in reducing food waste.
- Digital twin technology in urban development.
- Impact of AI on patent law.
- Cybersecurity in the era of quantum computing.
- Role of VR in disaster management training.
- AI in talent recruitment: Pros and cons.
Unique Technology Research Topics
For those wanting to stand out with truly original research, we offer 100% authentic topics about technology. We understand that professors highly value unique perspectives. Below we've meticulously selected these technology paper topics to offer you something different. These are not your everyday technology subjects but rather unexpected gems ready to be explored.
- Digital ethics in AI application.
- Role of technology in countering climate change.
- Is there a digital divide in developing countries?
- Role of drones in disaster management.
- Quantum internet: Possibilities and challenges.
- Digital forensic techniques in cybersecurity.
- Impact of technology on traditional art forms.
- Biohacking: Can we really upgrade ourselves?
- Technology and privacy: An inevitable trade-off?
- Developing empathy through virtual reality.
- AI and creativity: Can machines be artists?
- Technology's impact on urban gardening.
- Role of technology in accessible tourism.
- Quantum biology: A frontier of science.
- Unmanned underwater vehicles: Opportunities and threats.
Informative Research Topics in Technology
If you are seeking comprehensive information on technologies, this selection will definitely provide you with insights. As you may know, every study should be backed up by credible sources. Technology topics for research papers below are very easy to investigate, so you will surely find a bunch of academic resources.
- Exploring adaptive learning systems in online education.
- Role of technology in modern archaeology.
- Impact of immersive technology on journalism.
- The rise of telehealth services.
- Green data centers: A sustainable solution?
- Cybersecurity in mobile banking.
- 3D bioprinting : A revolution in healthcare?
- How technology affects sleep quality.
- AI in music production: A new era?
- Technology's role in preserving endangered languages.
- Smart grids for sustainable energy use.
- The future of privacy in a digital world.
- Can technology enhance sports performance?
- Role of AR in interior design.
- How technology is transforming public libraries.
Controversial Research Topics on Technology
Technological field touches upon areas where technology, ethics, and society intersect and often disagree. This has sparked debates and, sometimes, conspiracy theories, primarily because of the profound implications technologies have for our future. Take a look at these ideas, if you are up to a more controversial research topic about technology:
- Facial recognition technology: Invasion of privacy?
- Tech addiction: Myth or reality?
- The ethics of AI in warfare.
- Should social media platforms censor content?
- Are cryptocurrencies a boon or a bane?
- Is technology causing more harm than good to our health?
- The bias in machine learning algorithms.
- Genetic engineering: Playing God or advancing science?
- Will AI replace human jobs?
- Net neutrality: Freedom of internet or control?
- The risk of AI superintelligence.
- Tech companies' monopoly: Beneficial or detrimental?
- Are we heading towards a surveillance society?
- AI in law enforcement: Safeguard or threat?
- Do we rely too much on technology?
Easy Technology Research Paper Topics
Who ever thought the tech field was only for the tech-savvy? Well, it's time to dispel that myth. Here in our collection of simple technology research topics, we've curated subjects that break down complex tech concepts into manageable chunks. We believe that every student should get a chance to run a tech related project without any hurdles.
- Impact of social media on interpersonal communication.
- Smartphones: A boon or a bane?
- How technology improves accessibility for people with disabilities.
- E-learning versus traditional learning.
- Impact of technology on travel and tourism.
- Pros and cons of online shopping.
- How has technology changed entertainment?
- Technology's role in boosting productivity at work.
- Online safety: How to protect ourselves?
- Importance of digital literacy in today's world.
- How has technology influenced the music industry?
- E-books vs printed books: A tech revolution?
- Does technology promote loneliness?
- Role of technology in shaping modern communication.
- The impact of gaming on cognitive abilities.
Technology Research Topics Ideas for Students
As an experienced paper writing service online that helps students all the time, we understand that every learner has unique academic needs. With this in mind, the next section of our blog is designed to cater specifically to different academic levels. Whether you're a high school student just starting to explore technology or a doctoral candidate delving deep into a specialized topic, we've got different technology topics arranged by complexity.
Technology Research Topics for High School Students
High school students are expected to navigate complex topics, fostering critical thinking and promoting in-depth exploration. The proposed research paper topics on technology will help students understand how tech advancements shape various sectors of society and influence human life.
- How have smartphones changed our communication?
- Does virtual reality in museums enhance visitor experience?
- Understanding privacy issues in social media.
- How has technology changed the way we listen to music?
- Role of technology in promoting fitness and healthy lifestyle.
- Advantages and disadvantages of online learning.
- Does excessive screen time affect sleep quality?
- Do video games affect academic performance?
- How do GPS systems work?
- How has technology improved animation in films?
- Pros and cons of using smart home devices.
- Are self-driving cars safe?
- Technology's role in modernizing local libraries.
- Can technology help us lead more sustainable lifestyles?
- Can technology help improve road safety for teenagers?
Technology Research Topics for College Students
Think technology research topics for college are all about rocket science? Think again! Our compilation of college-level tech research topics brings you a bunch of intriguing, conversation-stirring, and head-scratching questions. They're designed to let you sink into the world of technology while also pushing your academic boundaries. Time to dive in, explore, question, and take your own unique stance on hot-button issues.
- Biometrics in identity verification: A privacy risk?
- Impact of 5G on mobile gaming.
- Are wearable fitness devices a true reflection of health?
- Can machine learning help predict climate change effects?
- Are digital currencies disrupting traditional finance?
- Use of drones in search and rescue operations.
- Impact of e-learning on academic performance.
- Does artificial intelligence have a place in home security?
- What are the ethical issues surrounding robotic surgery?
- Are e-wallets a safer option for online transactions?
- How has technology transformed news dissemination?
- AI in language translation: How accurate can it be?
- Personalized advertising: Boon or bane for online users?
- Are smart classes making learning more interactive?
- Influence of technology on homemade crafts and DIY culture.
Technology Research Topics for University Students
Are you browsing for university technology research ideas? We've got you covered. Whether you're about to dig deep into high-tech debates, or just taking your first steps, our list of technology research questions is your treasure chest.
- Blockchain applications in ensuring academic integrity.
- Impact of quantum computing on data security.
- Are brain-computer interfaces a future communication tool?
- Does digital currency pose a threat to the global economy?
- Use of AI in predicting and managing natural disasters.
- Can biometrics replace traditional identification systems?
- Role of nanotechnology in waste management.
- Machine learning's influence on climate change modeling.
- Edge computing: Revolutionizing data processing?
- Is virtual reality in psychological therapy a viable option?
- Potential of synthetic biology in medical research.
- Quantum cryptography: An uncrackable code?
- Is space tourism achievable with current technology?
- Ethical implications of gene editing technologies.
- Artificial intelligence in governance.
Technology Research Paper Topics in Different Areas
In the next section, we've arranged a collection of technology research questions related to different areas like computer science, biotechnology, and medicine. Find an area you are interested in and look through subject-focused ideas and topics for a research paper on technology.
Technology Research Topics on Computer Science
Computer science is a field that has rapidly developed over the past decades. It deals with questions of technology's influence on society, as well as applications of cutting-edge technologies in various industries and sectors. Here are some computer science research topics on technology to get started:
- Prospects of machine learning in malware detection.
- Influence of cloud computing on business operations.
- Quantum computing: potential impacts on cryptography.
- Role of big data in personalized marketing.
- Can AI models effectively simulate human decision-making?
- Future of mobile applications: Towards augmented reality?
- Pros and cons of open source software development.
- Role of computer science in advancing virtual reality.
- Natural language processing: Transforming human-computer interaction?
- Developing secure e-commerce platforms: Challenges and solutions.
- Green computing : solutions for reducing energy consumption.
- Data mining in healthcare: An untapped opportunity?
- Understanding cyber threats in the internet of things.
- Algorithmic bias: Implications for automated decision-making.
- Role of neural networks in image recognition.
Information Technology Research Topics
Information technology is a dynamic field that involves the use of computers and software to manage and process information. It's crucial in today's digital era, influencing a range of industries from healthcare to entertainment. Here are some captivating information technology related topics:
- Impact of cloud technology on data management.
- Role of information technology in disaster management.
- Can artificial intelligence help improve data accuracy?
- Cybersecurity measures for protecting personal information.
- Evolving role of IT in healthcare administration.
- Adaptive learning systems: A revolution in education?
- E-governance : Impact on public administration.
- Role of IT in modern supply chain management.
- Bioinformatics and its role in personalized medicine.
- Is data mining an invasion of privacy?
- Can virtual reality enhance training and development programs?
- Role of IT in facilitating remote work.
- Smart devices and data security: A potential risk?
- Harnessing IT for sustainable business practices.
- How can big data support decision-making processes?
Technology Research Topics on Artificial Intelligence
Artificial Intelligence, or AI as we fondly call it, is all about creating machines that mimic human intelligence. It's shaping everything from how we drive our cars to how we manage our calendars. Want to understand the mind of a machine? Choose a topic about technology for a research paper from the list below:
- AI's role in detecting fake news.
- Chatbots in customer service: Are humans still needed?
- Algorithmic trading: AI's impact on financial markets.
- AI in agriculture: a step towards sustainable farming?
- Facial recognition systems: an AI revolution or privacy threat?
- Can AI outperform humans in creative tasks?
- Sentiment analysis in social media: how effective is AI?
- Siri, Alexa, and the future of AI.
- AI in autonomous vehicles: safety concern or necessity?
- How AI algorithms are transforming video games.
- AI's potential in predicting and mitigating natural disasters.
- Role of AI in combating cyber threats.
- Influence of AI on job recruitment and HR processes.
- Can AI help in advancing climate change research?
- Can machines make accurate diagnoses?
Technology Research Topics in Cybersecurity Command
Cybersecurity Command focuses on strengthening digital protection. Its goal is to identify vulnerabilities, and outsmart cyber threats. Ready to crack the code of the cybersecurity command? Check out these technology topics for research designed to take you through the tunnels of cyberspace:
- Cybersecurity strategies for a post-quantum world.
- Role of AI in identifying cyber threats.
- Is cybersecurity command in healthcare a matter of life and death?
- Is there any connection between cryptocurrency and cybercrime?
- Cyber warfare : The invisible battleground.
- Mitigating insider threats in cybersecurity command.
- Future of biometric authentication in cybersecurity.
- IoT security: command challenges and solutions.
- Cybersecurity and cloud technology: A secure match?
- Influence of blockchain on cybersecurity command.
- Machine learning's role in malware detection.
- Cybersecurity protocols for mobile devices.
- Ethics in cybersecurity: Hacking back and other dilemmas.
- What are some steps to recovery after a breach?
- Social engineering: Human factor in cybersecurity.
Technology Research Topics on Biotechnology
Biotechnology is an interdisciplinary field that has been gaining a lot of traction in the past few decades. It involves the application of biological principles to understand and solve various problems. The following research topic ideas for technology explore biotechnology's impact on medicine, environment, agriculture, and other sectors:
- Can GMOs solve global hunger issues?
- Understanding biotech's role in developing personalized medicine.
- Using biotech to fight antibiotic resistance.
- Pros and cons of genetically modified animals.
- Biofuels – are they really a sustainable energy solution?
- Ethical challenges in gene editing.
- Role of biotech in combating climate change.
- Can biotechnology help conserve biodiversity?
- Biotech in beauty: Revolutionizing cosmetics.
- Bioluminescence – a natural wonder or a biotech tool?
- Applications of microbial biotechnology in waste management.
- Human organ farming: Possibility or pipe dream?
- Biotech and its role in sustainable agriculture.
- Biotech advancements in creating allergy-free foods.
- Exploring the future of biotech in disease detection.
>> Read more: Biology Topics to Research
Technology Research Paper Topics on Genetic Engineering
Genetic engineering is an area of science that involves the manipulation of genes to change or enhance biological characteristics. This field has raised tremendous ethical debates while offering promising solutions in medicine and agriculture. Here are some captivating topics for a technology research paper on genetic engineering:
- Future of gene editing: Breakthrough or ethical dilemma?
- Role of CRISPR technology in combating genetic diseases.
- Pros and cons of genetically modified crops.
- Impact of genetic engineering on biodiversity.
- Can gene therapy provide a cure for cancer?
- Genetic engineering and the quest for designer babies.
- Legal aspects of genetic engineering.
- Use of genetic engineering in organ transplantation.
- Genetic modifications: Impact on human lifespan.
- Genetically engineered pets: A step too far?
- The role of genetic engineering in biofuels production.
- Ethics of genetic data privacy.
- Genetic engineering and its impact on world hunger.
- Genetically modified insects: Solution for disease control?
- Genetic engineering: A tool for biological warfare?
Reproduction Technology Research Paper Topics
Reproduction technology is all about the science that aids human procreation. It's a field teeming with innovation, from IVF advancements to genetic screening. Yet, it also stirs up ethical debates and thought-provoking technology topics to write about:
- Advances in in Vitro Fertilization (IVF) technology .
- The rise of surrogacy: Technological advancements and implications.
- Ethical considerations in sperm and egg donation.
- Genetic screening of embryos: A step forward or an ethical minefield?
- Role of technology in understanding and improving fertility.
- Artificial Wombs: Progress and prospects.
- Ethical and legal aspects of posthumous reproduction.
- Impact of reproductive technology on the LGBTQ+ community.
- The promise and challenge of stem cells in reproduction.
- Technology's role in preventing genetic diseases in unborn babies.
- Social implications of childbearing technology.
- The concept of 'designer babies': Ethical issues and future possibilities.
- Reproductive cloning: Prospects and controversies.
- Technology and the future of contraception.
- Role of AI in predicting successful IVF treatment.
Medical Technology Topics for a Research Paper
The healthcare field is undergoing massive transformations thanks to cutting-edge medical technology. From revolutionary diagnostic tools to life-saving treatments, technology is reshaping medicine as we know it. To aid your exploration of this dynamic field, we've compiled medical technology research paper topics:
- Role of AI in early disease detection.
- Impact of telemedicine on rural healthcare.
- Nanotechnology in cancer treatment: Prospects and challenges.
- Can wearable technology improve patient outcomes?
- Ethical considerations in genome sequencing.
- Augmented reality in surgical procedures.
- The rise of personalized medicine: Role of technology.
- Mental health apps: Revolution or hype?
- Technology and the future of prosthetics.
- Role of Big Data in healthcare decision making.
- Virtual reality as a tool for pain management.
- Impact of machine learning on drug discovery.
- The promise of medical drones for emergency response.
- Technology's role in combating antimicrobial resistance.
- Electronic Health Records (EHRs): Blessing or curse?
>> More ideas: Med Research Topics
Health Technology Research Topics
Health technology is driving modern healthcare to new heights. From apps that monitor vital stats to robots assisting in surgeries, technology's touch is truly transformative. Take a look at these topics related to technology applied in healthcare:
- Role of mobile apps in managing diabetes.
- Impact of health technology on patient privacy.
- Wearable tech: Fad or future of personal health monitoring?
- How can AI help in battling mental health issues?
- Role of digital tools in promoting preventive healthcare.
- Smart homes for the elderly: Boon or bane?
- Technology and its impact on health insurance.
- The effectiveness of virtual therapy sessions.
- Can health chatbots replace human doctors?
- Technology's role in fighting the obesity epidemic.
- The use of blockchain in health data management.
- Impact of technology on sleep health.
- Social media and its effect on mental health.
- Prospects of 3D printing in creating medical equipment.
- Tele-rehabilitation: An effective solution for physical therapy?
>> View more: Public Health Topics to Research
Communication Technology Research Topics
With technology at the helm, our ways of communicating are changing at an unprecedented pace. From simple text messages to immersive virtual conferences, technology has rewritten the rules of engagement. So, without further ado, let's explore these communication research ideas for technology that capture the essence of this revolution.
- AI chatbots: Re-defining customer service.
- The impact of 5G on global communication.
- Augmented Reality: The future of digital marketing?
- Is 'digital divide' hindering global communication?
- Social media's role in shaping public opinion.
- Can holographic communication become a reality?
- Influence of emojis in digital communication.
- The cybersecurity challenges in modern communication.
- Future of journalism in the digital age.
- How technology is reshaping political communication.
- The influence of streaming platforms on viewing habits.
- Privacy concerns in the age of instant messaging.
- Can technology solve the issue of language barriers?
- The rise of podcasting: A digital renaissance.
- Role of virtual reality in remote communication.
Research Topics on Technology in Transportation
Technology is the driving force behind the dramatic changes in transportation, making journeys safer, more efficient, and eco-friendly. Whether it's autonomous vehicles or the concept of Hyperloop, there are many transportation technology topics for a research paper to choose from:
- Electric vehicles: A step towards sustainable travel.
- The role of AI in traffic management.
- Pros and cons of autonomous vehicles.
- Hyperloop: An ambitious vision of the future?
- Drones in goods delivery: Efficiency vs. privacy.
- Technology's role in reducing aviation accidents.
- Challenges in implementing smart highways.
- The implications of blockchain in logistics.
- Could vertical takeoff and landing (VTOL) vehicles solve traffic problems?
- Impact of GPS technology on transportation.
- How has technology influenced public transit systems?
- Role of 5G in future transportation.
- Ethical concerns over self-driving cars.
- Technology in maritime safety: Progress and hurdles.
- The evolution of bicycle technology: From spokes to e-bikes.
Technology Research Paper Topics on Education
The intersection of technology and education is an exciting frontier with limitless possibilities. From online learning to interactive classrooms, you can explore various technology paper topics about education:
- How does e-learning affect student engagement?
- VR classrooms: A glimpse into the future?
- Can AI tutors revolutionize personalized learning?
- Digital textbooks versus traditional textbooks: A comparison.
- Gamification in education: Innovation or distraction?
- The impact of technology on special education.
- How are Massive Open Online Courses (MOOCs) reshaping higher education?
- The role of technology in inclusive education.
- Cybersecurity in schools: Measures and challenges.
- The potential of Augmented Reality (AR) in classroom learning.
- How is technology influencing homeschooling trends?
- Balancing technology and traditional methods in early childhood education.
- Risks and benefits of student data tracking.
- Can coding be the new literacy in the 21st century?
- The influence of social media on academic performance.
>> Learn more: Education Research Paper Topics
Relationships and Technology Research Topics
In the digital age, technology also impacts our relationships. It has become an integral part of how we communicate, meet people, and sustain our connections. Discover some thought-provoking angles with these research paper topics about technology:
- How do dating apps affect modern relationships?
- The influence of social media on interpersonal communication.
- Is technology enhancing or hindering long-distance relationships?
- The psychology behind online dating: A study.
- How do virtual reality environments impact social interaction?
- Social media friendships: Genuine or superficial?
- How does technology-mediated communication affect family dynamics?
- The impact of technology on work-life balance.
- The role of technology in sustaining long-term relationships.
- How does the 'always connected' culture influence personal boundaries?
- Cyberbullying and its effect on teenage relationships.
- Can technology predict compatibility in relationships?
- The effects of 'ghosting' in digital communication.
- How technology assists in maintaining relationships among elderly populations.
- Social media: A boon or bane for marital relationships?
Agriculture Technology Research Paper Topics
Modern agriculture is far from just tilling the soil and harvesting crops. Technology has made remarkable strides into the fields, innovating and improving agricultural processes. Take a glance at these technology research paper topic ideas:
- Can drone technology transform crop monitoring?
- Precision agriculture: Benefits and challenges.
- Aquaponics and the future of sustainable farming.
- How is artificial intelligence aiding in crop prediction?
- Impact of blockchain technology in food traceability.
- The role of IoT in smart farming.
- Vertical farming : Is it a sustainable solution for urban food supply?
- Innovations in irrigation technology for water conservation.
- Automated farming: A boon or a threat to employment in agriculture?
- How satellite imagery is improving crop disease detection.
- Biotechnology in crop improvement: Pros and cons.
- Nanotechnology in agriculture: Scope and limitations.
- Role of robotics in livestock management.
- Agricultural waste management through technology.
- Is hydroponics the future of farming?
Technological Research Topics on Environment
Our planet is facing numerous environmental challenges, and technology may hold the key to solving many of these. With innovations ranging from renewable energy sources to waste management systems, the realm of technology offers a plethora of research angles. So, if you're curious about the intersection of technology and environment, this list of research topics is for you:
- Innovations in waste management: A technology review.
- The role of AI in predicting climate change impacts.
- Renewable energy: Advancements in solar technology.
- The impact of electric vehicles on carbon emissions.
- Can smart agriculture help solve world hunger?
- Role of technology in water purification and conservation.
- The impact of IoT devices on energy consumption.
- Technology solutions for oil spills.
- Satellite technology in environmental monitoring.
- Technological advances in forest conservation.
- Green buildings: Sustainable construction technology.
- Bioengineering: A solution to soil erosion?
- Impact of nanotechnology on environmental conservation.
- Ocean clean-up initiatives: Evaluating existing technology.
- How can technology help in reducing air pollution?
>> View more: Environmental Science Research Topics
Energy & Power Technology Topics for Research Paper
Energy and power are two pivotal areas where technology is bringing unprecedented changes. You can investigate renewable energy sources or efficient power transmission. If you're excited about exploring the intricacies of energy and power advancements, here are some engaging technology topics for research papers:
- Assessing the efficiency of wind energy technologies.
- Power storage: Current and future technology.
- Solar panel technology: Recent advancements and future predictions.
- Can nuclear fusion be the answer to our energy crisis?
- Smart grid technology: A revolution in power distribution.
- Evaluating the impact of hydropower on ecosystems.
- The role of AI in optimizing power consumption.
- Biofuels vs. fossil fuels: A comparative study.
- Electric vehicle charging infrastructure: Technological challenges and solutions.
- Technology advancements in geothermal power.
- How is IoT technology helping in energy conservation?
- Harnessing wave and tidal energy: Technological possibilities.
- Role of nanotechnology in improving solar cell efficiency.
- Power transmission losses: Can technology provide a solution?
- Assessing the future of coal technology in the era of renewable energy.
Research Topics about Technology in Finance
The finance sector has seen drastic changes with the rise of technology, which has revolutionized the way financial transactions are conducted and services are offered. Consider these research topics in technology applied in the finance sector:
- Rise of cryptocurrency: An evaluation of Bitcoin's impact.
- Algorithmic trading: How does it reshape financial markets?
- Role of AI and machine learning in financial forecasting.
- Technological challenges in implementing digital banking.
- How is blockchain technology transforming financial services?
- Cybersecurity risks in online banking: Identifying solutions.
- FinTech startups: Disrupting traditional finance systems.
- Role of technology in financial inclusion.
- Assessing the impact of mobile wallets on the banking sector.
- Automation in finance: Opportunities and threats.
- Role of big data analytics in financial decision making.
- AI-based robo-advisors vs. human financial advisors.
- The future of insurance technology (InsurTech).
- Can technology solve the issue of financial fraud?
- Impact of regulatory technology (RegTech) in maintaining compliance.
>> More ideas: Finance Research Topics
War Technology Research Paper Topics
The nature of warfare has transformed significantly with the evolution of technology, shifting the battlegrounds from land, sea, and air to the realms of cyber and space. This transition opens up a range of topics to explore. Here are some research topics in the realm of war technology:
- Drones in warfare: Ethical implications.
- Cyber warfare: Assessing threats and defense strategies.
- Autonomous weapons: A boon or a curse?
- Implications of artificial intelligence in modern warfare.
- Role of technology in intelligence gathering.
- Satellite technology and its role in modern warfare.
- The future of naval warfare: Autonomous ships and submarines.
- Hypersonic weapons: Changing the dynamics of war.
- Impact of nuclear technology in warfare.
- Technology and warfare: Exploring the relationship.
- Information warfare: The role of social media.
- Space warfare: Future possibilities and implications.
- Bio-warfare: Understanding technology's role in development and prevention.
- Impact of virtual reality on military training.
- War technology and international law: A critical examination.
Food Technology Topics for Research Papers
Food technology is a field that deals with the study of food production, preservation, and safety. It involves understanding how various techniques can be applied to increase shelf life and improve nutrition value of foods. Check out our collection of food technology research paper topic ideas:
- Lab-grown meats: Sustainable solution or a mere hype?
- How AI is enhancing food safety and quality?
- Precision agriculture: Revolutionizing farming practices.
- GMOs: Assessing benefits and potential risks.
- Role of robotics in food manufacturing and packaging.
- Smart kitchens: Streamlining cooking through technology.
- Nanofood: Tiny technology, big impact.
- Sustainable food systems: Role of technology.
- Food traceability: Ensuring transparency and accountability.
- Food delivery apps: Changing the face of dining out.
- The rise of plant-based alternatives and their production technologies.
- Virtual and augmented reality in culinary experiences.
- Technology in mitigating food waste.
- Innovations in food packaging: Impact on freshness and sustainability.
- IoT in smart farming: Improving yield and reducing waste.
Entertainment Technology Topics
Entertainment technology is reinventing the ways we experience amusement. This industry is always presenting new angles for research and discussion, be it the rise of virtual reality in movies or the influence of streaming platforms on the music industry. Here's a list of unique research topics related to entertainment technology:
- Impact of virtual reality on the movie industry.
- Streaming platforms vs traditional media: A comparative study.
- Technology in music: Evolution and future prospects.
- eSports: Rise of a new form of entertainment.
- Augmented reality in theme parks.
- The transformation of theater with digital technology.
- AI and film editing: Redefining the art.
- The role of technology in the rise of independent cinema.
- Podcasts: Revolutionizing radio with technology.
- Immersive technologies in art exhibitions.
- The influence of technology on fashion shows and design.
- Livestreaming concerts: A new norm in the music industry?
- Drones in entertainment: Applications and ethics.
- Social media as an entertainment platform.
- The transformation of journalism in the era of digital entertainment.
Technology Research Questions
As we navigate the ever-changing landscape of technology, numerous intriguing questions arise. Below, we present new research questions about technology that can fuel your intellectual pursuit.
- What potential does quantum computing hold for resolving complex problems?
- How will advancements in AI impact job security across different sectors?
- In what ways can blockchain technology reform the existing financial systems?
- How is nanotechnology revolutionizing the field of medicine?
- What are the ethical implications surrounding the use of facial recognition technology?
- How will the introduction of 6G change our communication patterns?
- In what ways is green technology contributing to sustainable development?
- Can virtual reality transform the way we approach education?
- How are biometrics enhancing the security measures in today's digital world?
- How is space technology influencing our understanding of the universe?
- What role can technology play in solving the global water crisis?
- How can technology be leveraged to combat climate change effectively?
- How is technology transforming the landscape of modern agriculture?
- Can technological advancements lead to a fully renewable energy-dependent world?
- How does technology influence the dynamics of modern warfare?
Bottom Line on Research Topics in Technology
Technology is a rapidly evolving field, and there's always something new to explore. Whether you're writing for the computer sciences, information technology or food technology realm, there are endless ideas that you can research on. Pick one of these technology research paper topics and jumpstart your project.
Trust professionals to ‘ write a research paper for me !’ Our team of expert writers is ready to assist you in crafting an exceptional research paper on any topic. Just reach out, and we'll provide you with high-quality work tailored to your needs.

Joe Eckel is an expert on Dissertations writing. He makes sure that each student gets precious insights on composing A-grade academic writing.
You may also like

Researchers harness the power of artificial intelligence to match patients with the most effective antidepressant for their unique needs
Helping clinicians more effectively match patients with the optimal antidepressant using big data.
Researchers in George Mason University's College of Public Health have leveraged the power of artificial intelligence (AI) analytical models to match a patient's medical history to the most effective antidepressant, allowing patients to find symptom relief sooner. The free website, MeAgainMeds.com, provides evidence-based recommendations, allowing clinicians and patients to find the optimal antidepressant the first time.
"Many people with depression must try multiple antidepressants before finding the right one that alleviates their symptoms. Our website reduces the number of medications that patients are asked to try. The system recommends to the patient what has worked for at least 100 other patients with the same exact relevant medical history," said Farrokh Alemi, principal investigator and professor of health informatics at George Mason University's College of Public Health.
AI helped to simplify the very complex task of making thousands of guidelines easily accessible to patients and clinicians. The guidelines that researchers created are complicated because of the amount of clinical information that is relevant in prescribing an antidepressant; AI seamlessly simplifies the task.
With AI at its core, MeAgainMeds.com analyzes clinician or patient responses to a few anonymous medical history questions to determine which oral antidepressant would best meet the specific needs. The website does not ask for any personal identifiable information and it does not prescribe medication changes. Patients are advised to visit their primary health care provider for any changes in medication.
In 2018, the Centers for Disease Control reported that more than 13% of adults use antidepressants, and the number has only increased since the pandemic and other epidemics since 2020. This website could help millions of people find relief more quickly.
Alemi and his team analyzed 3,678,082 patients who took 10,221,145 antidepressants. The oral antidepressants analyzed were amitriptyline, bupropion, citalopram, desvenlafaxine, doxepin, duloxetine, escitalopram, fluoxetine, mirtazapine, nortriptyline, paroxetine, sertraline, trazodone, and venlafaxine. From the data, they created 16,770 subgroups of at least 100 cases, using reactions to prior antidepressants, current medication, history of physical illness, history of mental illness, key procedures, and other information. The subgroups and remission rates drive the AI to produce an evidence-based medication recommendation.
"By matching patients to the subgroups, clinicians can prescribe the medication that works best for people with similar medical history," said Alemi. The researchers and website recommend that patients who use the site take the information to their clinicians, who will ultimately decide whether to prescribe the recommended medicine.
Alemi and his team tested a protype version of the site in 2023, which they advertised on social media. At that time, 1,500 patients used the website. Their goal is to improve the website and expand its user base. The initial research was funded by the Commonwealth of Virginia and by the Robert Wood Johnson Foundation.
The researchers' most recent paper in a series of papers on response to antidepressants analyzed 2,467 subgroups of patients who had received psychotherapy. "Effectiveness of Antidepressants in Combination with Psychotherapy" was published online in T he Journal of Mental Health Policy and Economics in March 2024. Additional authors include Tulay G Soylu from Temple University, and Mary Cannon and Conor McCandless from Royal College of Surgeons in Dublin, Ireland.
- Today's Healthcare
- Patient Education and Counseling
- Diseases and Conditions
- Mental Health Research
- Neural Interfaces
- Information Technology
- Antidepressant
- Data mining
- Hyperthyroidism
- Scientific visualization
- Multiple sclerosis
- Occupational therapy
Story Source:
Materials provided by George Mason University . Original written by Mary Cunningham. Note: Content may be edited for style and length.
Journal Reference :
- Alemi F, Soylu TG, Cannon M, McCandless C. Effectiveness of Antidepressants in Combination with Psychotherapy . J Ment Health Policy Econ , 2024 Mar 1;27(1):3-12 [ abstract ]
Cite This Page :
Explore More
- How Statin Therapy May Prevent Cancer
- Origins of 'Welsh Dragons' Exposed
- Resting Brain: Neurons Rehearse for Future
- Observing Single Molecules
- A Greener, More Effective Way to Kill Termites
- One Bright Spot Among Melting Glaciers
- Martian Meteorites Inform Red Planet's Structure
- Volcanic Events On Jupiter's Moon Io: High Res
- What Negative Adjectives Mean to Your Brain
- 'Living Bioelectronics' Can Sense and Heal Skin
Trending Topics
Strange & offbeat.

- FREE WHITEPAPERS
- FEATURED ARTICLES
- FREE RESOURCES
- FREE eNEWSLETTER

Healthcare Technology Featured Article
- Medical Record Evolution: The Advantages and Disadvantages of Cloud-based Solutions in Patient Information Management

Understanding Cloud-Based Medical Records
What Is a Cloud-Based Medical Record?
Cloud-based medical records essentially refer to information management over the internet servers in regard to health; these said internet servers provide caregivers with the capability of accessing patients' data from locations with internet connections. The technology facilitates real-time updates and sharing of information on patients to make every step easier in delivering health care.
Looking to navigate the complexities of cloud architecture? Svitla offers an in-depth guide on the different types of cloud architecture including public, private, and hybrid models. Their expert insights can help you choose the right architecture that aligns with your healthcare needs, optimizing both security and accessibility. Discover how Svitla's tailored cloud solutions can transform your medical data management. Visit their website to learn more and get started with a consultation today! Advantages of Cloud-Based Solutions
The major strength of cloud-based systems remains that they are available on demand. The health care practitioners can easily access their patients' records from any part of the world and at any given time, hence helping provide the needed services either in emergencies or regular care management. Another advantage is that being flexible, the cloud-based systems are able to scale up accordingly; a health facility can isolate its growth level of storage need without having to invest in expensive capital. Most of the time, they.
Navigating the Challenges
Security Issues and Regulatory Compliance
One of the big concerns in the implementation of cloud-based medical records is security and preservation of the privacy of sensitive patient information. Cloud-stored health-related data must ensure strict regulation, much the same as that under the Health Insurance Portability and Accountability Act in the US, which has become a means of protection for patients' data. Healthcare providers will have to satisfy themselves that their cloud service provider has put in place strong security through encryption of data and secure user authentication mechanisms that would foil compromise attempts.
Implementation and Operational Issues
Moving to a cloud-based system can definitely be quite intimidating. It would involve a complete overhaul or change in the existing IT infrastructure and, additionally, training the medical staff so that they become adept at working with the new system. Indeed, updating the old systems presents a real headache from time to time, which calls for skilled IT support. Costs and efforts bound in that are generally substantial up-front but are usually worth that by long-term savings and improvements in operational efficiency.
FAQ and Response
1. Definition of Cloud-Based Medical Record System
A cloud-based medical record system basically refers to some digital technique through which health information is put on the internet, allowing access, management, and sharing in that respective data.
2. How does the cloud benefit healthcare providers?
Cloud computing allows the healthcare provider an increase in flexibility, scalability, and on-demand access to patient records, which helps improve care coordination regarding the patients and to minimize these operational costs.
3. What security threats are applicable to cloud-based solutions in health care?
In this respect, security risks loom due to data breach, unauthorized entrance, and data loss. Compliance with the laws and other legal standards leads away from these occurrences.
4. How can problems related to the difficulties of adopting cloud technology by healthcare providers be alleviated?
The difficulties could also be combated by selecting good cloud services with strong security, preparing staff through training well in advance, and proper integration into the systems.
5. What do health care providers need to think about when contracting for hosted services for medical records in the cloud?
Healthcare providers should, therefore, subscribe to cloud services that have robust data security, full adherence to healthcare regulation, reliable customer support, and proven capability in the integration with existing care applications.
The automation of medical records using cloud technology represents a step change in healthcare data management. The associated benefits are sure to accrue through operational efficiencies and patient care, but the challenges still require deft handling for success. With constant evolution in the cloud technology landscape, this adoption in healthcare shall further grow and transform medical records management into a different level.
SHARE THIS ARTICLE
Healthcare technology related articles.
- Strategies for Success: 5 Ways of Improving Hospital Efficiency and Patient Outcomes
- Smoothening Healthcare Revenue Cycle Management: Addressing Staffing Shortfalls
- The Role of Assistive Technology in Enhancing Independence for People with Disabilities
- Explore the Advantages of Using Telehealth Video Calls
- Transforming Healthcare: The Power of Software Development in Medical Field
From White Paper Library
- The language of innovation: Why and how to gain your customers' trust with your AI and digital
- Exploring CX strategy and technology adoption: A decision-maker's chart
- Transforming Customer Experience
- RingCentral RingCX overview
- RingCX Digital Engagement Datasheet
MedHealth RSS
- Healthcare Providers
- IT Professionals
- Electronic Records
- Healthcare Innovation
- Medical Devices
- Mobile & Connected Health

- Alzheimer's disease & dementia
- Arthritis & Rheumatism
- Attention deficit disorders
- Autism spectrum disorders
- Biomedical technology
- Diseases, Conditions, Syndromes
- Endocrinology & Metabolism
- Gastroenterology
- Gerontology & Geriatrics
- Health informatics
- Inflammatory disorders
- Medical economics
- Medical research
- Medications
- Neuroscience
- Obstetrics & gynaecology
- Oncology & Cancer
- Ophthalmology
- Overweight & Obesity
- Parkinson's & Movement disorders
- Psychology & Psychiatry
- Radiology & Imaging
- Sleep disorders
- Sports medicine & Kinesiology
- Vaccination
- Breast cancer
- Cardiovascular disease
- Chronic obstructive pulmonary disease
- Colon cancer
- Coronary artery disease
- Heart attack
- Heart disease
- High blood pressure
- Kidney disease
- Lung cancer
- Multiple sclerosis
- Myocardial infarction
- Ovarian cancer
- Post traumatic stress disorder
- Rheumatoid arthritis
- Schizophrenia
- Skin cancer
- Type 2 diabetes
- Full List »
share this!
May 29, 2024
This article has been reviewed according to Science X's editorial process and policies . Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
peer-reviewed publication
trusted source
Proof-of-concept study pioneers new brain imaging technique through a transparent skull implant
by Keck School of Medicine of USC

In the first study of its kind, researchers from the Keck School of Medicine of USC and the California Institute of Technology (Caltech) designed and implanted a transparent window in the skull of a patient, then used functional ultrasound imaging (fUSI) to collect high-resolution brain imaging data through the window.
Their preliminary findings , published in Science Translational Medicine , suggest that this sensitive, non-invasive approach could open new avenues for patient monitoring and clinical research , as well as broader studies of how the brain functions.
"This is the first time anyone had applied functional ultrasound imaging through a skull replacement in an awake, behaving human performing a task," said Charles Liu, MD, Ph.D., a professor of clinical neurological surgery, urology and surgery at the Keck School of Medicine and director of the USC Neurorestoration Center.
"The ability to extract this type of information noninvasively through a window is pretty significant, particularly since many of the patients who require skull repair have or will develop neurological disabilities. In addition, 'windows' can be surgically implanted in patients with intact skulls if functional information can help with diagnosis and treatment."
The research participant, 39-year-old Jared Hager, sustained a traumatic brain injury (TBI) from a skateboarding accident in 2019. During emergency surgery , half of Hager's skull was removed to relieve pressure on his brain, leaving part of his brain covered only with skin and connective tissue. Because of the pandemic, he had to wait more than two years to have his skull restored with a prosthesis.
During that time, Hager volunteered for earlier research conducted by Liu, Jonathan Russin, MD, associate surgical director of the USC Neurorestoration Center, and another Caltech team on a new type of brain imaging called fPACT.
The experimental technique had been done on soft tissue, but could only be tested on the brain in patients like Hager who were missing a part of their skull. When the time came for implanting the prosthesis, Hager again volunteered to team up with Liu and his colleagues, who designed a custom skull implant to study the utility of fUSI—which cannot be done through the skull or a traditional implant—while repairing Hager's injury.
Before the reconstructive surgery, the research team tested and optimized fUSI parameters for brain imaging, using both a phantom (a scientific device designed to test medical imaging equipment) and animal models. They then collected fUSI data from Hager while he completed several tasks, both before his surgery and after the clear implant was installed, finding that the window offered an effective way to measure brain activity.
Functional brain imaging, which collects data on brain activity by measuring changes in blood flow or electrical impulses, can offer key insights about how the brain works, both in healthy people and those with neurological conditions.
But current methods, such as functional magnetic resonance imaging (fMRI) and intracranial electroencephalography (EEG) leave many questions unanswered. Challenges include low resolution, a lack of portability or the need for invasive brain surgery. fUSI may eventually offer a sensitive and precise alternative.
"If we can extract functional information through a patient's skull implant, that could allow us to provide treatment more safely and proactively," including to TBI patients who suffer from epilepsy, dementia, or psychiatric problems, Liu said.
A new frontier for brain imaging
As a foundation for the present study, Liu has collaborated for years with Mikhail Shapiro, Ph.D. and Richard Andersen, Ph.D., of Caltech, to develop specialized ultrasound sequences that can measure brain function, as well as to optimize brain-computer interface technology, which transcribes signals from the brain to operate an external device.
With these pieces in place, Liu and his colleagues tested several transparent skull implants on rats, finding that a thin window made from polymethyl methacrylate (PMMA)—which resembles plexiglass—yielded the clearest imaging results. They then collaborated with a neurotechnology company, Longeviti Neuro Solutions, to build a custom implant for Hager.
Before surgery, the researchers collected fUSI data while Hager did two activities: solving a "connect-the-dots" puzzle on a computer monitor and playing melodies on his guitar. After the implant was installed, they collected data on the same tasks, then compared the results to determine whether fUSI could provide accurate and useful imaging data.
"The fidelity of course decreased, but importantly, our research showed that it's still high enough to be useful," Liu said. "And unlike other brain-computer interface platforms, which require electrodes to be implanted in the brain, this has far less barriers to adoption."
fUSI may offer finer resolution than fMRI and unlike intracranial EEG, it does not require electrodes to be implanted inside the brain. It is also less expensive than those methods and could provide some clinical advantages for patients over non-transparent skull implants, said Russin, who is also an associate professor of neurological surgery at the Keck School of Medicine and director of cerebrovascular surgery at Keck Hospital of USC.
"One of the big problems when we do these surgeries is that a blood clot can form underneath the implant, but having a clear window gives us an easy way to monitor that," he said.
Refining functional ultrasound technology
In addition to better monitoring of patients, the new technique could offer population-level insights about TBI and other neurological conditions. It could also allow scientists to collect data on the healthy brain and learn more about how it controls cognitive, sensory, motor and autonomic functions.
"What our findings show is that we can extract useful functional information with this method," Liu said. "The next step is: What specific functional information do we want, and what can we use it for?"
Until the new technologies undergo clinical trials, fUSI and the clear implant are experimental. In the meantime, the research team is working to improve their fUSI protocols to further enhance image resolution . Future research should also build on this early proof-of-concept study by testing more participants to better establish the link between fUSI data and specific brain functions, the researchers said.
"Jared is an amazing guy," said Liu, who is continuing to collaborate with the study participant on refining new technologies, including laser spectroscopy, which measures blood flow in the brain. "His contributions have really helped us explore new frontiers that we hope can ultimately help many other patients."
Explore further
Feedback to editors

Almost 1 in 3 Americans know someone who's died from a drug overdose
10 hours ago

Antibody discovery promises new hope in influenza B battle, paves way for universal vaccine
14 hours ago

Eye-tracking techniques could help primary care providers diagnose autism sooner, more accurately
May 31, 2024

This self-powered sensor could make MRIs more efficient

Not eating can hinder weight loss, study in fruit flies suggests

Neuroscience research suggests ketones can enhance cognitive function and protect brain networks

New research finds antidepressants may help deliver other drugs into the brain

Mediterranean diet tied to one-fifth lower risk of death in women

Scientists find new method to enhance efficacy of bispecific antibodies for solid tumors

Cardiomyocytes study discovers new way to regenerate damaged heart cells
Related stories.

Doctors can now watch spinal cord activity during surgery
Mar 7, 2024

New approach to brain imaging leaves skulls intact in mice
Sep 5, 2022

Musk's Neuralink says issue in brain implant fixed
May 9, 2024

Musk says patient moves cursor with brain implant
Feb 21, 2024

Ultrasound enables less-invasive brain-machine interfaces
Nov 30, 2023

Neuralink shows quadriplegic playing chess with brain implant
Mar 21, 2024
Recommended for you
Researchers identify a genetic cause of intellectual disability affecting tens of thousands

New avenues to developing personalized treatments for schizophrenia
May 30, 2024

How does the word 'not' affect what we understand? Scientists find negation mitigates our interpretation of phrases
Let us know if there is a problem with our content.
Use this form if you have come across a typo, inaccuracy or would like to send an edit request for the content on this page. For general inquiries, please use our contact form . For general feedback, use the public comments section below (please adhere to guidelines ).
Please select the most appropriate category to facilitate processing of your request
Thank you for taking time to provide your feedback to the editors.
Your feedback is important to us. However, we do not guarantee individual replies due to the high volume of messages.
E-mail the story
Your email address is used only to let the recipient know who sent the email. Neither your address nor the recipient's address will be used for any other purpose. The information you enter will appear in your e-mail message and is not retained by Medical Xpress in any form.
Newsletter sign up
Get weekly and/or daily updates delivered to your inbox. You can unsubscribe at any time and we'll never share your details to third parties.
More information Privacy policy
Donate and enjoy an ad-free experience
We keep our content available to everyone. Consider supporting Science X's mission by getting a premium account.
E-mail newsletter
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Scientists identify mechanism behind drug resistance in malaria parasite
Press contact :.

Previous image Next image
Share this news article on:
Related links.
- Peter Dedon
- Antimicrobial Resistance Interdisciplinary Research Group
- Singapore-MIT Alliance for Research and Technology (SMART)
- Department of Biological Engineering
Related Topics
- Drug resistance
- Antibiotics
- Biological engineering
- Drug development
- International initiatives
- Collaboration
Related Articles

Satellite-based method measures carbon in peat bogs

Newly discovered bacterial communication system aids antimicrobial resistance

SMART launches research group to advance AI, automation, and the future of work

A novel combination therapy counters antibiotic-resistant Mycobacterium abscessus infections
Previous item Next item
More MIT News

MIT Corporation elects 10 term members, two life members
Read full story →

Diane Hoskins ’79: How going off-track can lead new SA+P graduates to become integrators of ideas

Chancellor Melissa Nobles’ address to MIT’s undergraduate Class of 2024

Noubar Afeyan PhD ’87 gives new MIT graduates a special assignment

Commencement address by Noubar Afeyan PhD ’87

President Sally Kornbluth’s charge to the Class of 2024
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram

IMAGES
VIDEO
COMMENTS
The results showed that papers related to forecasting the future of health information technology were mostly a literature review, and the time horizon was up to 10 years in most of these studies. In the health information technology foresight group, most of the studies used a combination of techniques, such as scenario building and Delphi ...
Although the benefits of EHR are well-received and Health Information Technology for Economic and Clinical Health (HITECH) Act encourages the use of EHR to improve care quality and efficiency, prior studies show mixed results of implementing EHR. 3 Recent studies suggest that full adoption of EHR might not be sufficient to ensure the benefits of EHRs; instead, meaningful use 4 or meaningful ...
Here, we'll explore a variety of healthcare-related research ideas and topic thought-starters across a range of healthcare fields, including allopathic and alternative medicine, dentistry, physical therapy, optometry, pharmacology and public health. NB - This is just the start….
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on HEALTH INFORMATION TECHNOLOGY. Find methods information, sources, references or conduct a literature ...
Introduction. We can understand digital health as a response to a health landscape becoming more uncertain and complex on a global scale (Benis et al. 1).On top of the rising threat of non-communicable diseases like diabetes and hypertension, there is an upsurge of adverse health impacts resulting from pollution, climate change, and migration. 2 Global and national health reform efforts, such ...
Overview. This journal presents research on the application of computer science principles, information science principles, information technology, and communication technology to healthcare and everyday wellness, highlighting novel technical contributions in computing-oriented healthcare informatics. The journal explores three major tracks ...
Health Informatics Journal is an international peer-reviewed journal. All papers submitted to Health Informatics Journal are subject to peer review by members of a carefully appointed editorial board. The journal operates a conventional double-blind … | View full journal description. This journal is a member of the Committee on Publication ...
Health information technology (HIT) is the hardware, software, and systems that comprise the input, transmission, use, extraction, and analysis of information in the healthcare sector. The end-users of this technology include not only patients, physicians, and other front-line healthcare providers, but also medical researchers, healthcare insurance companies, public health agencies, regulatory ...
Digital health interventions refer to the use of digital technology and connected devices to improve health outcomes and healthcare delivery. This includes telemedicine, electronic health records, wearable devices, mobile health applications, and other forms of digital health technology. To this end, several research and developmental activities in various fields are gaining momentum. For ...
September 1996. ·. 14 Reads. C P Liberty. Since its inception in 1992, the associate degree program in health information management (HIM) of the University of Alaska Southeast has been distance ...
Health information system deployment has been driven by the transformation and digitalization currently confronting healthcare. The need and potential of these systems within healthcare have been tremendously driven by the global instability that has affected several interrelated sectors. Accordingly, many research studies have reported on the inadequacies of these systems within the ...
The field of health care information technology has grown rapidly around the world in recent years. Hospital and clinic use of mobile devices, medical information databases, remote medicine, and computerized provider order entry (CPOE) are each a different management-oriented topic selected by Master's in Health Informatics students.
Background Accelerated by the coronavirus disease 2019 (Covid-19) pandemic, major and lasting changes are occuring in healthcare structures, impacting people's experiences and value creation in all aspects of their lives. Information systems (IS) research can support analysing and anticipating resulting effects. Aim The purpose of this study is to examine in what areas health information ...
December 18, 2023. This paper provides an overview of Health Information Technology (HIT) adoption and utilization in long-term and post-acute care (LTPAC) settings. This study found that LTPAC have adopted electronic health records (EHRs) to support clinical and business needs. Interoperable exchange of health information however is not ...
New research on information technology from Harvard Business School faculty on issues including the HealthCare.gov fiasco, online privacy concerns, and the civic benefits of technologies that utilize citizen-created data. Page 1 of 60 Results →. 23 Apr 2024. Cold Call Podcast.
Health information technology (health IT) involves the processing, storage, and exchange of health information in an electronic environment. Widespread use of health IT within the health care industry will improve the quality of health care, prevent medical errors, reduce health care costs, increase administrative efficiencies, decrease paperwork, and expand access to affordable health care.
Health Information Technology. Health information technology (HIT) consists of those electronic systems that record, transfer and store both patient and clinical operations information. Important aspects of HIT under study include how electronic medical records might be used to improve patient care by reducing medical errors through changes in ...
The list of the top 400 information technology research topics is organized into different categories. Let's examine it. Artificial Intelligence (AI) and Machine Learning (ML) Easy AI: Explaining and Using. Group Learning: Getting Better Together. AI in Health: Diagnosing and Helping. Robots Learning on Their Own.
Background: Health care organizations worldwide are faced with an increasing number of cyberattacks and threats to their critical infrastructure. These cyberattacks cause significant data breaches in digital health information systems, which threaten patient safety and privacy. Objective: From a sociotechnical perspective, this paper explores why digital health care systems are vulnerable to ...
A literature review was conducted to identify peer-reviewed publications reporting on the actual use of health information technology in healthcare quality and patient safety. Inductive thematic analysis with open coding was used to categorize a total of 41 studies. Three pre-set categories were used: prevention, identification, and action.
Artificial intelligence technology research topics. We started 2023 with M3GAN's box office success, and now we're fascinated (or horrified) with ChatGPT, voice cloning, and deepfakes. While people have discussed artificial intelligence for ages, recent advances have really pushed this topic to the front of our minds.
Technology topics for research papers below are very easy to investigate, so you will surely find a bunch of academic resources. Exploring adaptive learning systems in online education. Role of technology in modern archaeology. Impact of immersive technology on journalism. The rise of telehealth services.
The area of technology for information is among the most modern technological advancements in the 21st century. Each year, technology-based devices get smaller, faster, and more sophisticated. In reality, the phone you use holds more information than the huge computers that took a human to the moon! Technological innovation has streamlined ...
Researchers in George Mason University's College of Public Health have leveraged the power of artificial intelligence (AI) analytical models to match a patient's medical history to the most ...
The current trend of healthcare solutions in cloud technology has already revolutionized the way medical records are maintained. It is being brought into reality with the highest degree ever on access and efficiency at its best. This article discusses numerous gains and, at the same time, major challenges that come with cloud technology in managing patient data.
NIA provides health information informed by research and reviewed by experts to help you learn about healthy aging and common health conditions in older adults. Browse our health topics below. You can also explore: Free print and PDF publications ; Information for health professionals; Infographics, videos, and more; Browse A-Z Health Topics
Credit: CC0 Public Domain. In the first study of its kind, researchers from the Keck School of Medicine of USC and the California Institute of Technology (Caltech) designed and implanted a ...
In a paper titled "tRNA modification reprogramming contributes to artemisinin resistance in Plasmodium falciparum", published in the journal Nature Microbiology, researchers from SMART's Antimicrobial Resistance (AMR) interdisciplinary research group documented their discovery: A change in a single tRNA, a small RNA molecule that is involved in translating genetic information from RNA to ...
The green living issues that arise as a result of smart home use in the context of sustainability consumption, at a time when smart homes are being built that can improve the management of electricity, water, gas consumption, and when their use offers the opportunity to raise awareness of caring for health and achieving wellbeing, became the basis for writing this article. This paper explores ...