

What is an Argumentative Essay? How to Write It (With Examples)

We define an argumentative essay as a type of essay that presents arguments about both sides of an issue. The purpose is to convince the reader to accept a particular viewpoint or action. In an argumentative essay, the writer takes a stance on a controversial or debatable topic and supports their position with evidence, reasoning, and examples. The essay should also address counterarguments, demonstrating a thorough understanding of the topic.
Table of Contents
What is an argumentative essay .
- Argumentative essay structure
- Argumentative essay outline
- Types of argument claims
How to write an argumentative essay?
- Argumentative essay writing tips
- Good argumentative essay example
How to write a good thesis
- How to Write an Argumentative Essay with Paperpal?
Frequently Asked Questions
An argumentative essay is a type of writing that presents a coherent and logical analysis of a specific topic. 1 The goal is to convince the reader to accept the writer’s point of view or opinion on a particular issue. Here are the key elements of an argumentative essay:
- Thesis Statement : The central claim or argument that the essay aims to prove.
- Introduction : Provides background information and introduces the thesis statement.
- Body Paragraphs : Each paragraph addresses a specific aspect of the argument, presents evidence, and may include counter arguments. Articulate your thesis statement better with Paperpal. Start writing now!
- Evidence : Supports the main argument with relevant facts, examples, statistics, or expert opinions.
- Counterarguments : Anticipates and addresses opposing viewpoints to strengthen the overall argument.
- Conclusion : Summarizes the main points, reinforces the thesis, and may suggest implications or actions.

Argumentative essay structure
Aristotelian, Rogerian, and Toulmin are three distinct approaches to argumentative essay structures, each with its principles and methods. 2 The choice depends on the purpose and nature of the topic. Here’s an overview of each type of argumentative essay format.
| ) | ||
| : Introduce the topic. Provide background information. Present the thesis statement or main argument. | : Introduce the issue. Provide background information. Establish a neutral and respectful tone. | : Introduce the issue. Provide background information. Present the claim or thesis. |
| : Provide context or background information. Set the stage for the argument. | : Describe opposing viewpoints without judgment. Show an understanding of the different perspectives. | : Clearly state the main argument or claim. |
| : Present the main argument with supporting evidence. Use logical reasoning. Address counterarguments and refute them. | : Present your thesis or main argument. Identify areas of common ground between opposing views. | : Provide evidence to support the claim. Include facts, examples, and statistics. |
| : Acknowledge opposing views. Provide counterarguments and evidence against them. | : Present your arguments while acknowledging opposing views. Emphasize shared values or goals. Seek compromise and understanding. | : Explain the reasoning that connects the evidence to the claim. Make the implicit assumptions explicit. |
| : Summarize the main points. Reassert the thesis. End with a strong concluding statement. | : Summarize areas of agreement. Reiterate the importance of finding common ground. End on a positive note. | : Provide additional support for the warrant. Offer further justification for the reasoning. |
| Address potential counterarguments. Provide evidence and reasoning to refute counterclaims. | ||
| Respond to counterarguments and reinforce the original claim. | ||
| Summarize the main points. Reinforce the strength of the argument. |
Have a looming deadline for your argumentative essay? Write 2x faster with Paperpal – Start now!
Argumentative essay outline
An argumentative essay presents a specific claim or argument and supports it with evidence and reasoning. Here’s an outline for an argumentative essay, along with examples for each section: 3
1. Introduction :
- Hook : Start with a compelling statement, question, or anecdote to grab the reader’s attention.
Example: “Did you know that plastic pollution is threatening marine life at an alarming rate?”
- Background information : Provide brief context about the issue.
Example: “Plastic pollution has become a global environmental concern, with millions of tons of plastic waste entering our oceans yearly.”
- Thesis statement : Clearly state your main argument or position.
Example: “We must take immediate action to reduce plastic usage and implement more sustainable alternatives to protect our marine ecosystem.”
2. Body Paragraphs :
- Topic sentence : Introduce the main idea of each paragraph.
Example: “The first step towards addressing the plastic pollution crisis is reducing single-use plastic consumption.”
- Evidence/Support : Provide evidence, facts, statistics, or examples that support your argument.
Example: “Research shows that plastic straws alone contribute to millions of tons of plastic waste annually, and many marine animals suffer from ingestion or entanglement.”
- Counterargument/Refutation : Acknowledge and refute opposing viewpoints.
Example: “Some argue that banning plastic straws is inconvenient for consumers, but the long-term environmental benefits far outweigh the temporary inconvenience.”
- Transition : Connect each paragraph to the next.
Example: “Having addressed the issue of single-use plastics, the focus must now shift to promoting sustainable alternatives.”
3. Counterargument Paragraph :
- Acknowledgement of opposing views : Recognize alternative perspectives on the issue.
Example: “While some may argue that individual actions cannot significantly impact global plastic pollution, the cumulative effect of collective efforts must be considered.”
- Counterargument and rebuttal : Present and refute the main counterargument.
Example: “However, individual actions, when multiplied across millions of people, can substantially reduce plastic waste. Small changes in behavior, such as using reusable bags and containers, can have a significant positive impact.”
4. Conclusion :
- Restatement of thesis : Summarize your main argument.
Example: “In conclusion, adopting sustainable practices and reducing single-use plastic is crucial for preserving our oceans and marine life.”
- Call to action : Encourage the reader to take specific steps or consider the argument’s implications.
Example: “It is our responsibility to make environmentally conscious choices and advocate for policies that prioritize the health of our planet. By collectively embracing sustainable alternatives, we can contribute to a cleaner and healthier future.”

Types of argument claims
A claim is a statement or proposition a writer puts forward with evidence to persuade the reader. 4 Here are some common types of argument claims, along with examples:
- Fact Claims : These claims assert that something is true or false and can often be verified through evidence. Example: “Water boils at 100°C at sea level.”
- Value Claims : Value claims express judgments about the worth or morality of something, often based on personal beliefs or societal values. Example: “Organic farming is more ethical than conventional farming.”
- Policy Claims : Policy claims propose a course of action or argue for a specific policy, law, or regulation change. Example: “Schools should adopt a year-round education system to improve student learning outcomes.”
- Cause and Effect Claims : These claims argue that one event or condition leads to another, establishing a cause-and-effect relationship. Example: “Excessive use of social media is a leading cause of increased feelings of loneliness among young adults.”
- Definition Claims : Definition claims assert the meaning or classification of a concept or term. Example: “Artificial intelligence can be defined as machines exhibiting human-like cognitive functions.”
- Comparative Claims : Comparative claims assert that one thing is better or worse than another in certain respects. Example: “Online education is more cost-effective than traditional classroom learning.”
- Evaluation Claims : Evaluation claims assess the quality, significance, or effectiveness of something based on specific criteria. Example: “The new healthcare policy is more effective in providing affordable healthcare to all citizens.”
Understanding these argument claims can help writers construct more persuasive and well-supported arguments tailored to the specific nature of the claim.
If you’re wondering how to start an argumentative essay, here’s a step-by-step guide to help you with the argumentative essay format and writing process.
- Choose a Topic: Select a topic that you are passionate about or interested in. Ensure that the topic is debatable and has two or more sides.
- Define Your Position: Clearly state your stance on the issue. Consider opposing viewpoints and be ready to counter them.
- Conduct Research: Gather relevant information from credible sources, such as books, articles, and academic journals. Take notes on key points and supporting evidence.
- Create a Thesis Statement: Develop a concise and clear thesis statement that outlines your main argument. Convey your position on the issue and provide a roadmap for the essay.
- Outline Your Argumentative Essay: Organize your ideas logically by creating an outline. Include an introduction, body paragraphs, and a conclusion. Each body paragraph should focus on a single point that supports your thesis.
- Write the Introduction: Start with a hook to grab the reader’s attention (a quote, a question, a surprising fact). Provide background information on the topic. Present your thesis statement at the end of the introduction.
- Develop Body Paragraphs: Begin each paragraph with a clear topic sentence that relates to the thesis. Support your points with evidence and examples. Address counterarguments and refute them to strengthen your position. Ensure smooth transitions between paragraphs.
- Address Counterarguments: Acknowledge and respond to opposing viewpoints. Anticipate objections and provide evidence to counter them.
- Write the Conclusion: Summarize the main points of your argumentative essay. Reinforce the significance of your argument. End with a call to action, a prediction, or a thought-provoking statement.
- Revise, Edit, and Share: Review your essay for clarity, coherence, and consistency. Check for grammatical and spelling errors. Share your essay with peers, friends, or instructors for constructive feedback.
- Finalize Your Argumentative Essay: Make final edits based on feedback received. Ensure that your essay follows the required formatting and citation style.
Struggling to start your argumentative essay? Paperpal can help – try now!
Argumentative essay writing tips
Here are eight strategies to craft a compelling argumentative essay:
- Choose a Clear and Controversial Topic : Select a topic that sparks debate and has opposing viewpoints. A clear and controversial issue provides a solid foundation for a strong argument.
- Conduct Thorough Research : Gather relevant information from reputable sources to support your argument. Use a variety of sources, such as academic journals, books, reputable websites, and expert opinions, to strengthen your position.
- Create a Strong Thesis Statement : Clearly articulate your main argument in a concise thesis statement. Your thesis should convey your stance on the issue and provide a roadmap for the reader to follow your argument.
- Develop a Logical Structure : Organize your essay with a clear introduction, body paragraphs, and conclusion. Each paragraph should focus on a specific point of evidence that contributes to your overall argument. Ensure a logical flow from one point to the next.
- Provide Strong Evidence : Support your claims with solid evidence. Use facts, statistics, examples, and expert opinions to support your arguments. Be sure to cite your sources appropriately to maintain credibility.
- Address Counterarguments : Acknowledge opposing viewpoints and counterarguments. Addressing and refuting alternative perspectives strengthens your essay and demonstrates a thorough understanding of the issue. Be mindful of maintaining a respectful tone even when discussing opposing views.
- Use Persuasive Language : Employ persuasive language to make your points effectively. Avoid emotional appeals without supporting evidence and strive for a respectful and professional tone.
- Craft a Compelling Conclusion : Summarize your main points, restate your thesis, and leave a lasting impression in your conclusion. Encourage readers to consider the implications of your argument and potentially take action.

Good argumentative essay example
Let’s consider a sample of argumentative essay on how social media enhances connectivity:
In the digital age, social media has emerged as a powerful tool that transcends geographical boundaries, connecting individuals from diverse backgrounds and providing a platform for an array of voices to be heard. While critics argue that social media fosters division and amplifies negativity, it is essential to recognize the positive aspects of this digital revolution and how it enhances connectivity by providing a platform for diverse voices to flourish. One of the primary benefits of social media is its ability to facilitate instant communication and connection across the globe. Platforms such as Facebook, Twitter, and Instagram break down geographical barriers, enabling people to establish and maintain relationships regardless of physical location and fostering a sense of global community. Furthermore, social media has transformed how people stay connected with friends and family. Whether separated by miles or time zones, social media ensures that relationships remain dynamic and relevant, contributing to a more interconnected world. Moreover, social media has played a pivotal role in giving voice to social justice movements and marginalized communities. Movements such as #BlackLivesMatter, #MeToo, and #ClimateStrike have gained momentum through social media, allowing individuals to share their stories and advocate for change on a global scale. This digital activism can shape public opinion and hold institutions accountable. Social media platforms provide a dynamic space for open dialogue and discourse. Users can engage in discussions, share information, and challenge each other’s perspectives, fostering a culture of critical thinking. This open exchange of ideas contributes to a more informed and enlightened society where individuals can broaden their horizons and develop a nuanced understanding of complex issues. While criticisms of social media abound, it is crucial to recognize its positive impact on connectivity and the amplification of diverse voices. Social media transcends physical and cultural barriers, connecting people across the globe and providing a platform for marginalized voices to be heard. By fostering open dialogue and facilitating the exchange of ideas, social media contributes to a more interconnected and empowered society. Embracing the positive aspects of social media allows us to harness its potential for positive change and collective growth.
- Clearly Define Your Thesis Statement: Your thesis statement is the core of your argumentative essay. Clearly articulate your main argument or position on the issue. Avoid vague or general statements.
- Provide Strong Supporting Evidence: Back up your thesis with solid evidence from reliable sources and examples. This can include facts, statistics, expert opinions, anecdotes, or real-life examples. Make sure your evidence is relevant to your argument, as it impacts the overall persuasiveness of your thesis.
- Anticipate Counterarguments and Address Them: Acknowledge and address opposing viewpoints to strengthen credibility. This also shows that you engage critically with the topic rather than presenting a one-sided argument.
How to Write an Argumentative Essay with Paperpal?
Writing a winning argumentative essay not only showcases your ability to critically analyze a topic but also demonstrates your skill in persuasively presenting your stance backed by evidence. Achieving this level of writing excellence can be time-consuming. This is where Paperpal, your AI academic writing assistant, steps in to revolutionize the way you approach argumentative essays. Here’s a step-by-step guide on how to use Paperpal to write your essay:
- Sign Up or Log In: Begin by creating an account or logging into paperpal.com .
- Navigate to Paperpal Copilot: Once logged in, proceed to the Templates section from the side navigation bar.
- Generate an essay outline: Under Templates, click on the ‘Outline’ tab and choose ‘Essay’ from the options and provide your topic to generate an outline.
- Develop your essay: Use this structured outline as a guide to flesh out your essay. If you encounter any roadblocks, click on Brainstorm and get subject-specific assistance, ensuring you stay on track.
- Refine your writing: To elevate the academic tone of your essay, select a paragraph and use the ‘Make Academic’ feature under the ‘Rewrite’ tab, ensuring your argumentative essay resonates with an academic audience.
- Final Touches: Make your argumentative essay submission ready with Paperpal’s language, grammar, consistency and plagiarism checks, and improve your chances of acceptance.
Paperpal not only simplifies the essay writing process but also ensures your argumentative essay is persuasive, well-structured, and academically rigorous. Sign up today and transform how you write argumentative essays.
The length of an argumentative essay can vary, but it typically falls within the range of 1,000 to 2,500 words. However, the specific requirements may depend on the guidelines provided.
You might write an argumentative essay when: 1. You want to convince others of the validity of your position. 2. There is a controversial or debatable issue that requires discussion. 3. You need to present evidence and logical reasoning to support your claims. 4. You want to explore and critically analyze different perspectives on a topic.
Argumentative Essay: Purpose : An argumentative essay aims to persuade the reader to accept or agree with a specific point of view or argument. Structure : It follows a clear structure with an introduction, thesis statement, body paragraphs presenting arguments and evidence, counterarguments and refutations, and a conclusion. Tone : The tone is formal and relies on logical reasoning, evidence, and critical analysis. Narrative/Descriptive Essay: Purpose : These aim to tell a story or describe an experience, while a descriptive essay focuses on creating a vivid picture of a person, place, or thing. Structure : They may have a more flexible structure. They often include an engaging introduction, a well-developed body that builds the story or description, and a conclusion. Tone : The tone is more personal and expressive to evoke emotions or provide sensory details.
- Gladd, J. (2020). Tips for Writing Academic Persuasive Essays. Write What Matters .
- Nimehchisalem, V. (2018). Pyramid of argumentation: Towards an integrated model for teaching and assessing ESL writing. Language & Communication , 5 (2), 185-200.
- Press, B. (2022). Argumentative Essays: A Step-by-Step Guide . Broadview Press.
- Rieke, R. D., Sillars, M. O., & Peterson, T. R. (2005). Argumentation and critical decision making . Pearson/Allyn & Bacon.
Paperpal is a comprehensive AI writing toolkit that helps students and researchers achieve 2x the writing in half the time. It leverages 21+ years of STM experience and insights from millions of research articles to provide in-depth academic writing, language editing, and submission readiness support to help you write better, faster.
Get accurate academic translations, rewriting support, grammar checks, vocabulary suggestions, and generative AI assistance that delivers human precision at machine speed. Try for free or upgrade to Paperpal Prime starting at US$19 a month to access premium features, including consistency, plagiarism, and 30+ submission readiness checks to help you succeed.
Experience the future of academic writing – Sign up to Paperpal and start writing for free!
Related Reads:
- Empirical Research: A Comprehensive Guide for Academics
- How to Write a Scientific Paper in 10 Steps
- What is a Literature Review? How to Write It (with Examples)
- What is a Narrative Essay? How to Write It (with Examples)
Make Your Research Paper Error-Free with Paperpal’s Online Spell Checker
The do’s & don’ts of using generative ai tools ethically in academia, you may also like, how to write a research proposal: (with examples..., apa format: basic guide for researchers, how to choose a dissertation topic, how to write a phd research proposal, how to write an academic paragraph (step-by-step guide), maintaining academic integrity with paperpal’s generative ai writing..., research funding basics: what should a grant proposal..., how to write an abstract in research papers..., how to write dissertation acknowledgements, how to structure an essay.
Purdue Online Writing Lab Purdue OWL® College of Liberal Arts
Argumentative Essays

Welcome to the Purdue OWL
This page is brought to you by the OWL at Purdue University. When printing this page, you must include the entire legal notice.
Copyright ©1995-2018 by The Writing Lab & The OWL at Purdue and Purdue University. All rights reserved. This material may not be published, reproduced, broadcast, rewritten, or redistributed without permission. Use of this site constitutes acceptance of our terms and conditions of fair use.
What is an argumentative essay?
The argumentative essay is a genre of writing that requires the student to investigate a topic; collect, generate, and evaluate evidence; and establish a position on the topic in a concise manner.
Please note : Some confusion may occur between the argumentative essay and the expository essay. These two genres are similar, but the argumentative essay differs from the expository essay in the amount of pre-writing (invention) and research involved. The argumentative essay is commonly assigned as a capstone or final project in first year writing or advanced composition courses and involves lengthy, detailed research. Expository essays involve less research and are shorter in length. Expository essays are often used for in-class writing exercises or tests, such as the GED or GRE.
Argumentative essay assignments generally call for extensive research of literature or previously published material. Argumentative assignments may also require empirical research where the student collects data through interviews, surveys, observations, or experiments. Detailed research allows the student to learn about the topic and to understand different points of view regarding the topic so that she/he may choose a position and support it with the evidence collected during research. Regardless of the amount or type of research involved, argumentative essays must establish a clear thesis and follow sound reasoning.
The structure of the argumentative essay is held together by the following.
- A clear, concise, and defined thesis statement that occurs in the first paragraph of the essay.
In the first paragraph of an argument essay, students should set the context by reviewing the topic in a general way. Next the author should explain why the topic is important ( exigence ) or why readers should care about the issue. Lastly, students should present the thesis statement. It is essential that this thesis statement be appropriately narrowed to follow the guidelines set forth in the assignment. If the student does not master this portion of the essay, it will be quite difficult to compose an effective or persuasive essay.
- Clear and logical transitions between the introduction, body, and conclusion.
Transitions are the mortar that holds the foundation of the essay together. Without logical progression of thought, the reader is unable to follow the essay’s argument, and the structure will collapse. Transitions should wrap up the idea from the previous section and introduce the idea that is to follow in the next section.
- Body paragraphs that include evidential support.
Each paragraph should be limited to the discussion of one general idea. This will allow for clarity and direction throughout the essay. In addition, such conciseness creates an ease of readability for one’s audience. It is important to note that each paragraph in the body of the essay must have some logical connection to the thesis statement in the opening paragraph. Some paragraphs will directly support the thesis statement with evidence collected during research. It is also important to explain how and why the evidence supports the thesis ( warrant ).
However, argumentative essays should also consider and explain differing points of view regarding the topic. Depending on the length of the assignment, students should dedicate one or two paragraphs of an argumentative essay to discussing conflicting opinions on the topic. Rather than explaining how these differing opinions are wrong outright, students should note how opinions that do not align with their thesis might not be well informed or how they might be out of date.
- Evidential support (whether factual, logical, statistical, or anecdotal).
The argumentative essay requires well-researched, accurate, detailed, and current information to support the thesis statement and consider other points of view. Some factual, logical, statistical, or anecdotal evidence should support the thesis. However, students must consider multiple points of view when collecting evidence. As noted in the paragraph above, a successful and well-rounded argumentative essay will also discuss opinions not aligning with the thesis. It is unethical to exclude evidence that may not support the thesis. It is not the student’s job to point out how other positions are wrong outright, but rather to explain how other positions may not be well informed or up to date on the topic.
- A conclusion that does not simply restate the thesis, but readdresses it in light of the evidence provided.
It is at this point of the essay that students may begin to struggle. This is the portion of the essay that will leave the most immediate impression on the mind of the reader. Therefore, it must be effective and logical. Do not introduce any new information into the conclusion; rather, synthesize the information presented in the body of the essay. Restate why the topic is important, review the main points, and review your thesis. You may also want to include a short discussion of more research that should be completed in light of your work.
A complete argument
Perhaps it is helpful to think of an essay in terms of a conversation or debate with a classmate. If I were to discuss the cause of World War II and its current effect on those who lived through the tumultuous time, there would be a beginning, middle, and end to the conversation. In fact, if I were to end the argument in the middle of my second point, questions would arise concerning the current effects on those who lived through the conflict. Therefore, the argumentative essay must be complete, and logically so, leaving no doubt as to its intent or argument.
The five-paragraph essay
A common method for writing an argumentative essay is the five-paragraph approach. This is, however, by no means the only formula for writing such essays. If it sounds straightforward, that is because it is; in fact, the method consists of (a) an introductory paragraph (b) three evidentiary body paragraphs that may include discussion of opposing views and (c) a conclusion.
Longer argumentative essays
Complex issues and detailed research call for complex and detailed essays. Argumentative essays discussing a number of research sources or empirical research will most certainly be longer than five paragraphs. Authors may have to discuss the context surrounding the topic, sources of information and their credibility, as well as a number of different opinions on the issue before concluding the essay. Many of these factors will be determined by the assignment.

8 Effective Strategies to Write Argumentative Essays
In a bustling university town, there lived a student named Alex. Popular for creativity and wit, one challenge seemed insurmountable for Alex– the dreaded argumentative essay!
One gloomy afternoon, as the rain tapped against the window pane, Alex sat at his cluttered desk, staring at a blank document on the computer screen. The assignment loomed large: a 350-600-word argumentative essay on a topic of their choice . With a sigh, he decided to seek help of mentor, Professor Mitchell, who was known for his passion for writing.
Entering Professor Mitchell’s office was like stepping into a treasure of knowledge. Bookshelves lined every wall, faint aroma of old manuscripts in the air and sticky notes over the wall. Alex took a deep breath and knocked on his door.
“Ah, Alex,” Professor Mitchell greeted with a warm smile. “What brings you here today?”
Alex confessed his struggles with the argumentative essay. After hearing his concerns, Professor Mitchell said, “Ah, the argumentative essay! Don’t worry, Let’s take a look at it together.” As he guided Alex to the corner shelf, Alex asked,
Table of Contents
“What is an Argumentative Essay?”
The professor replied, “An argumentative essay is a type of academic writing that presents a clear argument or a firm position on a contentious issue. Unlike other forms of essays, such as descriptive or narrative essays, these essays require you to take a stance, present evidence, and convince your audience of the validity of your viewpoint with supporting evidence. A well-crafted argumentative essay relies on concrete facts and supporting evidence rather than merely expressing the author’s personal opinions . Furthermore, these essays demand comprehensive research on the chosen topic and typically follows a structured format consisting of three primary sections: an introductory paragraph, three body paragraphs, and a concluding paragraph.”
He continued, “Argumentative essays are written in a wide range of subject areas, reflecting their applicability across disciplines. They are written in different subject areas like literature and philosophy, history, science and technology, political science, psychology, economics and so on.
Alex asked,
“When is an Argumentative Essay Written?”
The professor answered, “Argumentative essays are often assigned in academic settings, but they can also be written for various other purposes, such as editorials, opinion pieces, or blog posts. Some situations to write argumentative essays include:
1. Academic assignments
In school or college, teachers may assign argumentative essays as part of coursework. It help students to develop critical thinking and persuasive writing skills .
2. Debates and discussions
Argumentative essays can serve as the basis for debates or discussions in academic or competitive settings. Moreover, they provide a structured way to present and defend your viewpoint.
3. Opinion pieces
Newspapers, magazines, and online publications often feature opinion pieces that present an argument on a current issue or topic to influence public opinion.
4. Policy proposals
In government and policy-related fields, argumentative essays are used to propose and defend specific policy changes or solutions to societal problems.
5. Persuasive speeches
Before delivering a persuasive speech, it’s common to prepare an argumentative essay as a foundation for your presentation.
Regardless of the context, an argumentative essay should present a clear thesis statement , provide evidence and reasoning to support your position, address counterarguments, and conclude with a compelling summary of your main points. The goal is to persuade readers or listeners to accept your viewpoint or at least consider it seriously.”
Handing over a book, the professor continued, “Take a look on the elements or structure of an argumentative essay.”
Elements of an Argumentative Essay
An argumentative essay comprises five essential components:
Claim in argumentative writing is the central argument or viewpoint that the writer aims to establish and defend throughout the essay. A claim must assert your position on an issue and must be arguable. It can guide the entire argument.
2. Evidence
Evidence must consist of factual information, data, examples, or expert opinions that support the claim. Also, it lends credibility by strengthening the writer’s position.
3. Counterarguments
Presenting a counterclaim demonstrates fairness and awareness of alternative perspectives.
4. Rebuttal
After presenting the counterclaim, the writer refutes it by offering counterarguments or providing evidence that weakens the opposing viewpoint. It shows that the writer has considered multiple perspectives and is prepared to defend their position.
The format of an argumentative essay typically follows the structure to ensure clarity and effectiveness in presenting an argument.
How to Write An Argumentative Essay
Here’s a step-by-step guide on how to write an argumentative essay:
1. Introduction
- Begin with a compelling sentence or question to grab the reader’s attention.
- Provide context for the issue, including relevant facts, statistics, or historical background.
- Provide a concise thesis statement to present your position on the topic.
2. Body Paragraphs (usually three or more)
- Start each paragraph with a clear and focused topic sentence that relates to your thesis statement.
- Furthermore, provide evidence and explain the facts, statistics, examples, expert opinions, and quotations from credible sources that supports your thesis.
- Use transition sentences to smoothly move from one point to the next.
3. Counterargument and Rebuttal
- Acknowledge opposing viewpoints or potential objections to your argument.
- Also, address these counterarguments with evidence and explain why they do not weaken your position.
4. Conclusion
- Restate your thesis statement and summarize the key points you’ve made in the body of the essay.
- Leave the reader with a final thought, call to action, or broader implication related to the topic.
5. Citations and References
- Properly cite all the sources you use in your essay using a consistent citation style.
- Also, include a bibliography or works cited at the end of your essay.
6. Formatting and Style
- Follow any specific formatting guidelines provided by your instructor or institution.
- Use a professional and academic tone in your writing and edit your essay to avoid content, spelling and grammar mistakes .
Remember that the specific requirements for formatting an argumentative essay may vary depending on your instructor’s guidelines or the citation style you’re using (e.g., APA, MLA, Chicago). Always check the assignment instructions or style guide for any additional requirements or variations in formatting.
Did you understand what Prof. Mitchell explained Alex? Check it now!
Fill the Details to Check Your Score

Prof. Mitchell continued, “An argumentative essay can adopt various approaches when dealing with opposing perspectives. It may offer a balanced presentation of both sides, providing equal weight to each, or it may advocate more strongly for one side while still acknowledging the existence of opposing views.” As Alex listened carefully to the Professor’s thoughts, his eyes fell on a page with examples of argumentative essay.
Example of an Argumentative Essay
Alex picked the book and read the example. It helped him to understand the concept. Furthermore, he could now connect better to the elements and steps of the essay which Prof. Mitchell had mentioned earlier. Aren’t you keen to know how an argumentative essay should be like? Here is an example of a well-crafted argumentative essay , which was read by Alex. After Alex finished reading the example, the professor turned the page and continued, “Check this page to know the importance of writing an argumentative essay in developing skills of an individual.”
Importance of an Argumentative Essay
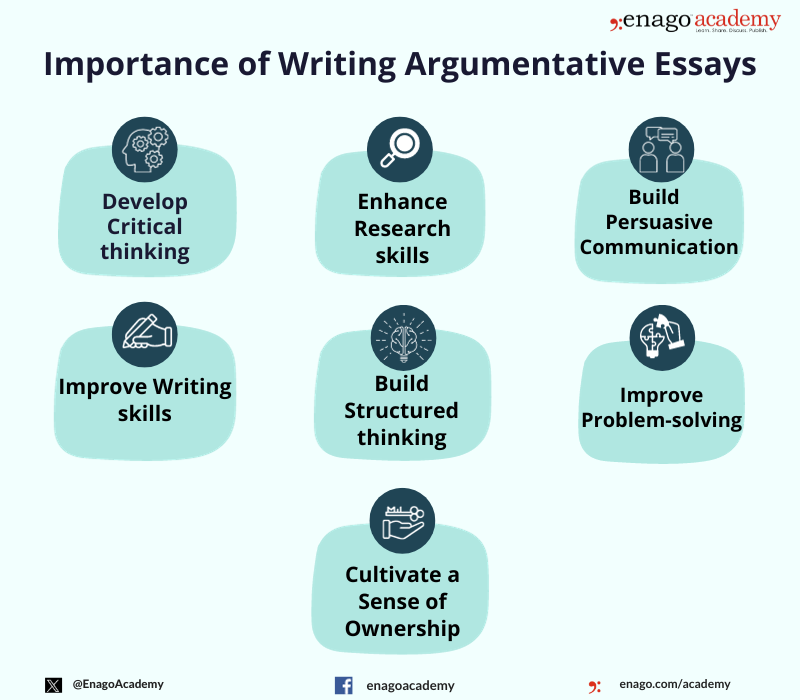
After understanding the benefits, Alex was convinced by the ability of the argumentative essays in advocating one’s beliefs and favor the author’s position. Alex asked,
“How are argumentative essays different from the other types?”
Prof. Mitchell answered, “Argumentative essays differ from other types of essays primarily in their purpose, structure, and approach in presenting information. Unlike expository essays, argumentative essays persuade the reader to adopt a particular point of view or take a specific action on a controversial issue. Furthermore, they differ from descriptive essays by not focusing vividly on describing a topic. Also, they are less engaging through storytelling as compared to the narrative essays.
Alex said, “Given the direct and persuasive nature of argumentative essays, can you suggest some strategies to write an effective argumentative essay?
Turning the pages of the book, Prof. Mitchell replied, “Sure! You can check this infographic to get some tips for writing an argumentative essay.”
Effective Strategies to Write an Argumentative Essay

As days turned into weeks, Alex diligently worked on his essay. He researched, gathered evidence, and refined his thesis. It was a long and challenging journey, filled with countless drafts and revisions.
Finally, the day arrived when Alex submitted their essay. As he clicked the “Submit” button, a sense of accomplishment washed over him. He realized that the argumentative essay, while challenging, had improved his critical thinking and transformed him into a more confident writer. Furthermore, Alex received feedback from his professor, a mix of praise and constructive criticism. It was a humbling experience, a reminder that every journey has its obstacles and opportunities for growth.
Frequently Asked Questions
An argumentative essay can be written as follows- 1. Choose a Topic 2. Research and Collect Evidences 3. Develop a Clear Thesis Statement 4. Outline Your Essay- Introduction, Body Paragraphs and Conclusion 5. Revise and Edit 6. Format and Cite Sources 7. Final Review
One must choose a clear, concise and specific statement as a claim. It must be debatable and establish your position. Avoid using ambiguous or unclear while making a claim. To strengthen your claim, address potential counterarguments or opposing viewpoints. Additionally, use persuasive language and rhetoric to make your claim more compelling
Starting an argument essay effectively is crucial to engage your readers and establish the context for your argument. Here’s how you can start an argument essay are: 1. Begin With an Engaging Hook 2. Provide Background Information 3. Present Your Thesis Statement 4. Briefly Outline Your Main 5. Establish Your Credibility
The key features of an argumentative essay are: 1. Clear and Specific Thesis Statement 2. Credible Evidence 3. Counterarguments 4. Structured Body Paragraph 5. Logical Flow 6. Use of Persuasive Techniques 7. Formal Language
An argumentative essay typically consists of the following main parts or sections: 1. Introduction 2. Body Paragraphs 3. Counterargument and Rebuttal 4. Conclusion 5. References (if applicable)
The main purpose of an argumentative essay is to persuade the reader to accept or agree with a particular viewpoint or position on a controversial or debatable topic. In other words, the primary goal of an argumentative essay is to convince the audience that the author's argument or thesis statement is valid, logical, and well-supported by evidence and reasoning.
Great article! The topic is simplified well! Keep up the good work
Excellent article! provides comprehensive and practical guidance for crafting compelling arguments. The emphasis on thorough research and clear thesis statements is particularly valuable. To further enhance your strategies, consider recommending the use of a counterargument paragraph. Addressing and refuting opposing viewpoints can strengthen your position and show a well-rounded understanding of the topic. Additionally, engaging with a community like ATReads, a writers’ social media, can provide valuable feedback and support from fellow writers. Thanks for sharing these insightful tips!
wow incredible ! keep up the good work
I love it thanks for the guidelines
Rate this article Cancel Reply
Your email address will not be published.

Enago Academy's Most Popular Articles

- Career Corner
Academic Webinars: Transforming knowledge dissemination in the digital age
Digitization has transformed several areas of our lives, including the teaching and learning process. During…

- Manuscripts & Grants
- Reporting Research
Mastering Research Grant Writing in 2024: Navigating new policies and funder demands
Entering the world of grants and government funding can leave you confused; especially when trying…

How to Create a Poster That Stands Out: Tips for a smooth poster presentation
It was the conference season. Judy was excited to present her first poster! She had…

- Diversity and Inclusion
- Industry News
6 Reasons Why There is a Decline in Higher Education Enrollment: Action plan to overcome this crisis
Over the past decade, colleges and universities across the globe have witnessed a concerning trend…

Academic Essay Writing Made Simple: 4 types and tips
The pen is mightier than the sword, they say, and nowhere is this more evident…
How to Effectively Cite a PDF (APA, MLA, AMA, and Chicago Style)

Sign-up to read more
Subscribe for free to get unrestricted access to all our resources on research writing and academic publishing including:
- 2000+ blog articles
- 50+ Webinars
- 10+ Expert podcasts
- 50+ Infographics
- 10+ Checklists
- Research Guides
We hate spam too. We promise to protect your privacy and never spam you.
- Publishing Research
- AI in Academia
- Promoting Research
- Infographics
- Expert Video Library
- Other Resources
- Enago Learn
- Upcoming & On-Demand Webinars
- Peer-Review Week 2023
- Open Access Week 2023
- Conference Videos
- Enago Report
- Journal Finder
- Enago Plagiarism & AI Grammar Check
- Editing Services
- Publication Support Services
- Research Impact
- Translation Services
- Publication solutions
- AI-Based Solutions
- Thought Leadership
- Call for Articles
- Call for Speakers
- Author Training
- Edit Profile
I am looking for Editing/ Proofreading services for my manuscript Tentative date of next journal submission:

In your opinion, what is the most effective way to improve integrity in the peer review process?
- Link to facebook
- Link to linkedin
- Link to twitter
- Link to youtube
- Writing Tips
How to Write an Argumentative Essay

4-minute read
- 30th April 2022
An argumentative essay is a structured, compelling piece of writing where an author clearly defines their stance on a specific topic. This is a very popular style of writing assigned to students at schools, colleges, and universities. Learn the steps to researching, structuring, and writing an effective argumentative essay below.
Requirements of an Argumentative Essay
To effectively achieve its purpose, an argumentative essay must contain:
● A concise thesis statement that introduces readers to the central argument of the essay
● A clear, logical, argument that engages readers
● Ample research and evidence that supports your argument
Approaches to Use in Your Argumentative Essay
1. classical.
● Clearly present the central argument.
● Outline your opinion.
● Provide enough evidence to support your theory.
2. Toulmin
● State your claim.
● Supply the evidence for your stance.
● Explain how these findings support the argument.
● Include and discuss any limitations of your belief.
3. Rogerian
● Explain the opposing stance of your argument.
● Discuss the problems with adopting this viewpoint.
● Offer your position on the matter.
● Provide reasons for why yours is the more beneficial stance.
● Include a potential compromise for the topic at hand.
Tips for Writing a Well-Written Argumentative Essay
● Introduce your topic in a bold, direct, and engaging manner to captivate your readers and encourage them to keep reading.
● Provide sufficient evidence to justify your argument and convince readers to adopt this point of view.
● Consider, include, and fairly present all sides of the topic.
● Structure your argument in a clear, logical manner that helps your readers to understand your thought process.
Find this useful?
Subscribe to our newsletter and get writing tips from our editors straight to your inbox.
● Discuss any counterarguments that might be posed.
● Use persuasive writing that’s appropriate for your target audience and motivates them to agree with you.
Steps to Write an Argumentative Essay
Follow these basic steps to write a powerful and meaningful argumentative essay :
Step 1: Choose a topic that you’re passionate about
If you’ve already been given a topic to write about, pick a stance that resonates deeply with you. This will shine through in your writing, make the research process easier, and positively influence the outcome of your argument.
Step 2: Conduct ample research to prove the validity of your argument
To write an emotive argumentative essay , finding enough research to support your theory is a must. You’ll need solid evidence to convince readers to agree with your take on the matter. You’ll also need to logically organize the research so that it naturally convinces readers of your viewpoint and leaves no room for questioning.
Step 3: Follow a simple, easy-to-follow structure and compile your essay
A good structure to ensure a well-written and effective argumentative essay includes:
Introduction
● Introduce your topic.
● Offer background information on the claim.
● Discuss the evidence you’ll present to support your argument.
● State your thesis statement, a one-to-two sentence summary of your claim.
● This is the section where you’ll develop and expand on your argument.
● It should be split into three or four coherent paragraphs, with each one presenting its own idea.
● Start each paragraph with a topic sentence that indicates why readers should adopt your belief or stance.
● Include your research, statistics, citations, and other supporting evidence.
● Discuss opposing viewpoints and why they’re invalid.
● This part typically consists of one paragraph.
● Summarize your research and the findings that were presented.
● Emphasize your initial thesis statement.
● Persuade readers to agree with your stance.
We certainly hope that you feel inspired to use these tips when writing your next argumentative essay . And, if you’re currently elbow-deep in writing one, consider submitting a free sample to us once it’s completed. Our expert team of editors can help ensure that it’s concise, error-free, and effective!
Share this article:
Post A New Comment
Got content that needs a quick turnaround? Let us polish your work. Explore our editorial business services.
6-minute read
How to Write a Nonprofit Grant Proposal
If you’re seeking funding to support your charitable endeavors as a nonprofit organization, you’ll need...
9-minute read
How to Use Infographics to Boost Your Presentation
Is your content getting noticed? Capturing and maintaining an audience’s attention is a challenge when...
8-minute read
Why Interactive PDFs Are Better for Engagement
Are you looking to enhance engagement and captivate your audience through your professional documents? Interactive...
7-minute read
Seven Key Strategies for Voice Search Optimization
Voice search optimization is rapidly shaping the digital landscape, requiring content professionals to adapt their...
Five Creative Ways to Showcase Your Digital Portfolio
Are you a creative freelancer looking to make a lasting impression on potential clients or...
How to Ace Slack Messaging for Contractors and Freelancers
Effective professional communication is an important skill for contractors and freelancers navigating remote work environments....

Make sure your writing is the best it can be with our expert English proofreading and editing.
- Resources Home 🏠
- Try SciSpace Copilot
- Search research papers
- Add Copilot Extension
- Try AI Detector
- Try Paraphraser
- Try Citation Generator
- April Papers
- June Papers
- July Papers

How To Write An Argumentative Essay

Table of Contents
Crafting a convincing argumentative essay can be challenging. You might feel lost about where to begin. But with a systematic approach and helpful tools that simplify sourcing and structuring, mastering good argumentative essay writing becomes achievable.
In this article, we'll explore what argumentative essays are, the critical steps to crafting a compelling argumentative essay, and best practices for essay organization.
What is an argumentative essay?
An argumentative essay asserts a clear position on a controversial or debatable topic and backs it up with evidence and reasoning. They are written to hone critical thinking, structure clear arguments, influence academic and public discourse, underpin reform proposals, and change popular narratives.
The fundamentals of a good argumentative essay
Let's explore the essential components that make argumentative essays compelling.
1 . The foundation: crafting a compelling claim for your argumentative essay
The claim is the cornerstone of your argumentative essay. It represents your main argument or thesis statement , setting the stage for the discussion.
A robust claim is straightforward, debatable, and focused, challenging readers to consider your viewpoint. It's not merely an observation but a stance you're prepared to defend with logic and evidence.
The strength of your essay hinges on the clarity and assertiveness of your claim, guiding readers through your argumentative journey.
2. The structure: Organizing your argument strategically
An effective argumentative essay should follow a logical structure to present your case persuasively. There are three models for structuring your argument essay:
- Classical: Introduce the topic, present the main argument, address counterarguments, and conclude . It is ideal for complex topics and prioritizes logical reasoning.
- Rogerian: Introduce the issue neutrally, acknowledge opposing views, find common ground, and seek compromise. It works well for audiences who dislike confrontational approaches.
- Toulmin: Introduce the issue, state the claim, provide evidence, explain the reasoning, address counterarguments, and reinforce the original claim. It confidently showcases an evidence-backed argument as superior.
Each model provides a framework for methodically supporting your position using evidence and logic. Your chosen structure depends on your argument's complexity, audience, and purpose.
3. The support: Leveraging evidence for your argumentative essay
The key is to select evidence that directly supports your claim, lending weight to your arguments and bolstering your position.
Effective use of evidence strengthens your argument and enhances your credibility, demonstrating thorough research and a deep understanding of the topic at hand.
4. The balance: Acknowledging counterarguments for the argumentative essay
A well-rounded argumentative essay acknowledges that there are two sides to every story. Introducing counterarguments and opposing viewpoints in an argument essay is a strategic move that showcases your awareness of alternative viewpoints.
This element of your argumentative essay demonstrates intellectual honesty and fairness, indicating that you have considered other perspectives before solidifying your position.
5. The counter: Mastering the art of rebuttal
A compelling rebuttal anticipates the counterclaims and methodically counters them, ensuring your position stands unchallenged. By engaging critically with counterarguments in this manner, your essay becomes more resilient and persuasive.
Ultimately, the strength of an argumentative essay is not in avoiding opposing views but in directly confronting them through reasoned debate and evidence-based.
How to write an argumentative essay
The workflow for crafting an effective argumentative essay involves several key steps:
Step 1 — Choosing a topic
Argumentative essay writing starts with selecting a topic with two or more main points so you can argue your position. Avoid topics that are too broad or have a clear right or wrong answer.
Use a semantic search engine to search for papers. Refine by subject area, publication date, citation count, institution, author, journal, and more to narrow down on promising topics. Explore citation interlinkages to ensure you pick a topic with sufficient academic discourse to allow crafting a compelling, evidence-based argument.
Seek an AI research assistant's help to assess a topic's potential and explore various angles quickly. They can generate both generic and custom questions tailored to each research paper. Additionally, look for tools that offer browser extensions . These allow you to interact with papers from sources like ArXiv, PubMed, and Wiley and evaluate potential topics from a broader range of academic databases and repositories.
Step 2 — Develop a thesis statement
Your thesis statement should clearly and concisely state your position on the topic identified. Ensure to develop a clear thesis statement which is a focused, assertive declaration that guides your discussion. Use strong, active language — avoid vague or passive statements. Keep it narrowly focused enough to be adequately supported in your essay.
The SciSpace literature review tool can help you extract thesis statements from existing papers on your chosen topic. Create a custom column called 'thesis statement' to compare multiple perspectives in one place, allowing you to uncover various viewpoints and position your concise thesis statement appropriately.
Ask AI assistants questions or summarize key sections to clarify the positions taken in existing papers. This helps sharpen your thesis statement stance and identify gaps. Locate related papers in similar stances.
Step 3 — Researching and gathering evidence
The evidence you collect lends credibility and weight to your claims, convincing readers of your viewpoint. Effective evidence includes facts, statistics, expert opinions, and real-world examples reinforcing your thesis statement.
Use the SciSpace literature review tool to locate and evaluate high-quality studies. It quickly extracts vital insights, methodologies, findings, and conclusions from papers and presents them in a table format. Build custom tables with your uploaded PDFs or bookmarked papers. These tables can be saved for future reference or exported as CSV for further analysis or sharing.
AI-powered summarization tools can help you quickly grasp the core arguments and positions from lengthy papers. These can condense long sections or entire author viewpoints into concise summaries. Make PDF annotations to add custom notes and highlights to papers for easy reference. Data extraction tools can automatically pull key statistics from PDFs into spreadsheets for detailed quantitative analysis.
Step 4 — Build an outline
The argumentative model you choose will impact your outline's specific structure and progression. If you select the Classical model, your outline will follow a linear structure. On the other hand, if you opt for the Toulmin model, your outline will focus on meticulously mapping out the logical progression of your entire argument. Lastly, if you select the Rogerian model, your outline should explore the opposing viewpoint and seek a middle ground.
While the specific outline structure may vary, always begin the process by stating your central thesis or claim. Identify and organize your argument claims and main supporting points logically, adding 2-3 pieces of evidence under each point. Consider potential counterarguments to your position. Include 1-2 counterarguments for each main point and plan rebuttals to dismantle the opposition's reasoning. This balanced approach strengthens your overall argument.
As you outline, consider saving your notes, highlights, AI-generated summaries, and extracts in a digital notebook. Aggregating all your sources and ideas in one centralized location allows you to quickly refer to them as you draft your outline and essay.
To further enhance your workflow, you can use AI-powered writing or GPT tools to help generate an initial structure based on your crucial essay components, such as your thesis statement, main arguments, supporting evidence, counterarguments, and rebuttals.
Step 5 — Write your essay
Begin the introductory paragraph with a hook — a question, a startling statistic, or a bold statement to draw in your readers. Always logically structure your arguments with smooth transitions between ideas. Ensure the body paragraphs of argumentative essays focus on one central point backed by robust quantitative evidence from credible studies, properly cited.
Refer to the notes, highlights, and evidence you've gathered as you write. Organize these materials so that you can easily access and incorporate them into your draft while maintaining a logical flow. Literature review tables or spreadsheets can be beneficial for keeping track of crucial evidence from multiple sources.
Quote others in a way that blends seamlessly with the narrative flow. For numerical data, contextualize figures with practical examples. Try to pre-empt counterarguments and systematically dismantle them. Maintain an evidence-based, objective tone that avoids absolutism and emotional appeals. If you encounter overly complex sections during the writing process, use a paraphraser tool to rephrase and clarify the language. Finally, neatly tie together the rationale behind your position and directions for further discourse or research.
Step 6 — Edit, revise, and add references
Set the draft aside so that you review it with fresh eyes. Check for clarity, conciseness, logical flow, and grammar. Ensure the body reflects your thesis well. Fill gaps in reasoning. Check that every claim links back to credible evidence. Replace weak arguments. Finally, format your citations and bibliography using your preferred style.
To simplify editing, save the rough draft or entire essay as a PDF and upload it to an AI-based chat-with-PDF tool. Use it to identify gaps in reasoning, weaker arguments requiring ample evidence, structural issues hampering the clarity of ideas, and suggestions for strengthening your essay.
Use a citation tool to generate citations for sources instantly quoted and quickly compile your bibliography or works cited in RIS/BibTex formats. Export the updated literature review tables as handy CSV files to share with co-authors or reviewers in collaborative projects or attach them as supplementary data for journal submissions. You can also refer to this article that provides you with argumentative essay writing tips .
Final thoughts
Remember, the strength of your argumentative essay lies in the clarity of your strong argument, the robustness of supporting evidence, and the consideration with which you treat opposing viewpoints. Refining these core skills will make you a sharper, more convincing writer and communicator.
You might also like

Boosting Citations: A Comparative Analysis of Graphical Abstract vs. Video Abstract

The Impact of Visual Abstracts on Boosting Citations

Introducing SciSpace’s Citation Booster To Increase Research Visibility

Want to create or adapt books like this? Learn more about how Pressbooks supports open publishing practices.
59 Introduction to Argumentative Writing
Joel Gladd and Amy Minervini
by Joel Gladd and Amy Minervini
Argumentative writing, also referred to as persuasive writing, is a cornerstone of any first-year writing course. We encounter arguments on daily basis, in both formal and informal contexts. Most of the time, however, we don’t realize how the arguments are actually working. This example developed by Ohio State’s University Library shows how a relatively informal argument may unfold. The dialogue has been annotated to show what kinds of rhetorical elements tend to appear in casual arguments.
As the example above shows, a number of elements typically play a role in most well-developed arguments:
- a question that doesn’t have a straightforward answer
- a claim that responds to the question
- one or more reasons for accepting the claim
- evidence that backs each reason
- objections & response to objections
We often employ many or all of these elements in everyday life, when debating current issues with friends and family. It just unfolds in a messier way than your academic essay will need to structure the conversation. However, even though academic persuasive essays rely on some techniques you’re already familiar with, certain strategies are less well-known, and even certain obvious elements, such as using “evidence” to back a claim, has a certain flavor in more formal environments that some students may not find obvious.
Different models have been proposed for how to best package the elements above. The three models most commonly employed in academic writing are the Aristotelian (classical) , Toulmin , and Rogerian , covered in this chapter. The proposal method is also included though this strategy focuses on solutions rather than problems.
Key Characteristics:
Argumentative writing generally exhibits the following:
- Presents a particular position/side of an issue
- Attempts to persuade the reader to the writer’s side
- Uses elements of rhetoric and strategies that include the integration of logos, pathos, ethos, and kairos in intentional and meaningful ways
- Presents information, data, and research as part of the evidence/support (logos)
- Relies on real-world stories and examples to nurture empathy (pathos)
- Leans on experts in their fields to cultivate credibility (ethos)
- Enlists or elicits a call to action (kairos)
- Presents and acknowledges opposing views
Contents within this Chapter:
- Elements of an Argument Essay
- Aristotelian (Classical) Argument Model
- Rogerian Argument Model
- Toulmin Argument Model
- Proposal Argument Model
- Counterargument and Response
- Generating Antithetical Points in Five Easy Steps
- Tips for Writing Argument Essays
Choosing & Using Sources: A Guide to Academic Research by Teaching & Learning, Ohio State University Libraries is licensed under a Creative Commons Attribution 4.0 International License , except where otherwise noted.
Introduction to Argumentative Writing Copyright © 2020 by Joel Gladd and Amy Minervini is licensed under a Creative Commons Attribution 4.0 International License , except where otherwise noted.
Share This Book

Choose Your Test
- Search Blogs By Category
- College Admissions
- AP and IB Exams
- GPA and Coursework
3 Key Tips for How to Write an Argumentative Essay
General Education

If there’s one writing skill you need to have in your toolkit for standardized tests, AP exams, and college-level writing, it’s the ability to make a persuasive argument. Effectively arguing for a position on a topic or issue isn’t just for the debate team— it’s for anyone who wants to ace the essay portion of an exam or make As in college courses.
To give you everything you need to know about how to write an argumentative essay , we’re going to answer the following questions for you:
- What is an argumentative essay?
- How should an argumentative essay be structured?
- How do I write a strong argument?
- What’s an example of a strong argumentative essay?
- What are the top takeaways for writing argumentative papers?
By the end of this article, you’ll be prepped and ready to write a great argumentative essay yourself!
Now, let’s break this down.

What Is an Argumentative Essay?
An argumentative essay is a type of writing that presents the writer’s position or stance on a specific topic and uses evidence to support that position. The goal of an argumentative essay is to convince your reader that your position is logical, ethical, and, ultimately, right . In argumentative essays, writers accomplish this by writing:
- A clear, persuasive thesis statement in the introduction paragraph
- Body paragraphs that use evidence and explanations to support the thesis statement
- A paragraph addressing opposing positions on the topic—when appropriate
- A conclusion that gives the audience something meaningful to think about.
Introduction, body paragraphs, and a conclusion: these are the main sections of an argumentative essay. Those probably sound familiar. Where does arguing come into all of this, though? It’s not like you’re having a shouting match with your little brother across the dinner table. You’re just writing words down on a page!
...or are you? Even though writing papers can feel like a lonely process, one of the most important things you can do to be successful in argumentative writing is to think about your argument as participating in a larger conversation . For one thing, you’re going to be responding to the ideas of others as you write your argument. And when you’re done writing, someone—a teacher, a professor, or exam scorer—is going to be reading and evaluating your argument.
If you want to make a strong argument on any topic, you have to get informed about what’s already been said on that topic . That includes researching the different views and positions, figuring out what evidence has been produced, and learning the history of the topic. That means—you guessed it!—argumentative essays almost always require you to incorporate outside sources into your writing.

What Makes Argumentative Essays Unique?
Argumentative essays are different from other types of essays for one main reason: in an argumentative essay, you decide what the argument will be . Some types of essays, like summaries or syntheses, don’t want you to show your stance on the topic—they want you to remain unbiased and neutral.
In argumentative essays, you’re presenting your point of view as the writer and, sometimes, choosing the topic you’ll be arguing about. You just want to make sure that that point of view comes across as informed, well-reasoned, and persuasive.
Another thing about argumentative essays: they’re often longer than other types of essays. Why, you ask? Because it takes time to develop an effective argument. If your argument is going to be persuasive to readers, you have to address multiple points that support your argument, acknowledge counterpoints, and provide enough evidence and explanations to convince your reader that your points are valid.

Our 3 Best Tips for Picking a Great Argumentative Topic
The first step to writing an argumentative essay deciding what to write about! Choosing a topic for your argumentative essay might seem daunting, though. It can feel like you could make an argument about anything under the sun. For example, you could write an argumentative essay about how cats are way cooler than dogs, right?
It’s not quite that simple . Here are some strategies for choosing a topic that serves as a solid foundation for a strong argument.
Choose a Topic That Can Be Supported With Evidence
First, you want to make sure the topic you choose allows you to make a claim that can be supported by evidence that’s considered credible and appropriate for the subject matter ...and, unfortunately, your personal opinions or that Buzzfeed quiz you took last week don’t quite make the cut.
Some topics—like whether cats or dogs are cooler—can generate heated arguments, but at the end of the day, any argument you make on that topic is just going to be a matter of opinion. You have to pick a topic that allows you to take a position that can be supported by actual, researched evidence.
(Quick note: you could write an argumentative paper over the general idea that dogs are better than cats—or visa versa!—if you’re a) more specific and b) choose an idea that has some scientific research behind it. For example, a strong argumentative topic could be proving that dogs make better assistance animals than cats do.)
You also don’t want to make an argument about a topic that’s already a proven fact, like that drinking water is good for you. While some people might dislike the taste of water, there is an overwhelming body of evidence that proves—beyond the shadow of a doubt—that drinking water is a key part of good health.
To avoid choosing a topic that’s either unprovable or already proven, try brainstorming some issues that have recently been discussed in the news, that you’ve seen people debating on social media, or that affect your local community. If you explore those outlets for potential topics, you’ll likely stumble upon something that piques your audience’s interest as well.
Choose a Topic That You Find Interesting
Topics that have local, national, or global relevance often also resonate with us on a personal level. Consider choosing a topic that holds a connection between something you know or care about and something that is relevant to the rest of society. These don’t have to be super serious issues, but they should be topics that are timely and significant.
For example, if you are a huge football fan, a great argumentative topic for you might be arguing whether football leagues need to do more to prevent concussions . Is this as “important” an issue as climate change? No, but it’s still a timely topic that affects many people. And not only is this a great argumentative topic: you also get to write about one of your passions! Ultimately, if you’re working with a topic you enjoy, you’ll have more to say—and probably write a better essay .
Choose a Topic That Doesn’t Get You Too Heated
Another word of caution on choosing a topic for an argumentative paper: while it can be effective to choose a topic that matters to you personally, you also want to make sure you’re choosing a topic that you can keep your cool over. You’ve got to be able to stay unemotional, interpret the evidence persuasively, and, when appropriate, discuss opposing points of view without getting too salty.
In some situations, choosing a topic for your argumentative paper won’t be an issue at all: the test or exam will choose it for you . In that case, you’ve got to do the best you can with what you’re given.
In the next sections, we’re going to break down how to write any argumentative essay —regardless of whether you get to choose your own topic or have one assigned to you! Our expert tips and tricks will make sure that you’re knocking your paper out of the park.

The Thesis: The Argumentative Essay’s Backbone
You’ve chosen a topic or, more likely, read the exam question telling you to defend, challenge, or qualify a claim on an assigned topic. What do you do now?
You establish your position on the topic by writing a killer thesis statement ! The thesis statement, sometimes just called “the thesis,” is the backbone of your argument, the north star that keeps you oriented as you develop your main points, the—well, you get the idea.
In more concrete terms, a thesis statement conveys your point of view on your topic, usually in one sentence toward the end of your introduction paragraph . It’s very important that you state your point of view in your thesis statement in an argumentative way—in other words, it should state a point of view that is debatable.
And since your thesis statement is going to present your argument on the topic, it’s the thing that you’ll spend the rest of your argumentative paper defending. That’s where persuasion comes in. Your thesis statement tells your reader what your argument is, then the rest of your essay shows and explains why your argument is logical.
Why does an argumentative essay need a thesis, though? Well, the thesis statement—the sentence with your main claim—is actually the entire point of an argumentative essay. If you don’t clearly state an arguable claim at the beginning of your paper, then it’s not an argumentative essay. No thesis statement = no argumentative essay. Got it?
Other types of essays that you’re familiar with might simply use a thesis statement to forecast what the rest of the essay is going to discuss or to communicate what the topic is. That’s not the case here. If your thesis statement doesn’t make a claim or establish your position, you’ll need to go back to the drawing board.
Example Thesis Statements
Here are a couple of examples of thesis statements that aren’t argumentative and thesis statements that are argumentative
The sky is blue.
The thesis statement above conveys a fact, not a claim, so it’s not argumentative.
To keep the sky blue, governments must pass clean air legislation and regulate emissions.
The second example states a position on a topic. What’s the topic in that second sentence? The best way to keep the sky blue. And what position is being conveyed? That the best way to keep the sky blue is by passing clean air legislation and regulating emissions.
Some people would probably respond to that thesis statement with gusto: “No! Governments should not pass clean air legislation and regulate emissions! That infringes on my right to pollute the earth!” And there you have it: a thesis statement that presents a clear, debatable position on a topic.
Here’s one more set of thesis statement examples, just to throw in a little variety:
Spirituality and otherworldliness characterize A$AP Rocky’s portrayals of urban life and the American Dream in his rap songs and music videos.
The statement above is another example that isn’t argumentative, but you could write a really interesting analytical essay with that thesis statement. Long live A$AP! Now here’s another one that is argumentative:
To give students an understanding of the role of the American Dream in contemporary life, teachers should incorporate pop culture, like the music of A$AP Rocky, into their lessons and curriculum.
The argument in this one? Teachers should incorporate more relevant pop culture texts into their curriculum.
This thesis statement also gives a specific reason for making the argument above: To give students an understanding of the role of the American Dream in contemporary life. If you can let your reader know why you’re making your argument in your thesis statement, it will help them understand your argument better.

An actual image of you killing your argumentative essay prompts after reading this article!
Breaking Down the Sections of An Argumentative Essay
Now that you know how to pick a topic for an argumentative essay and how to make a strong claim on your topic in a thesis statement, you’re ready to think about writing the other sections of an argumentative essay. These are the parts that will flesh out your argument and support the claim you made in your thesis statement.
Like other types of essays, argumentative essays typically have three main sections: the introduction, the body, and the conclusion. Within those sections, there are some key elements that a reader—and especially an exam scorer or professor—is always going to expect you to include.
Let’s look at a quick outline of those three sections with their essential pieces here:
- Introduction paragraph with a thesis statement (which we just talked about)
- Support Point #1 with evidence
- Explain/interpret the evidence with your own, original commentary (AKA, the fun part!)
- Support Point #2 with evidence
- Explain/interpret the evidence with your own, original commentary
- Support Point #3 with evidence
- New paragraph addressing opposing viewpoints (more on this later!)
- Concluding paragraph
Now, there are some key concepts in those sections that you’ve got to understand if you’re going to master how to write an argumentative essay. To make the most of the body section, you have to know how to support your claim (your thesis statement), what evidence and explanations are and when you should use them, and how and when to address opposing viewpoints. To finish strong, you’ve got to have a strategy for writing a stellar conclusion.
This probably feels like a big deal! The body and conclusion make up most of the essay, right? Let’s get down to it, then.

How to Write a Strong Argument
Once you have your topic and thesis, you’re ready for the hard part: actually writing your argument. If you make strategic choices—like the ones we’re about to talk about—writing a strong argumentative essay won’t feel so difficult.
There are three main areas where you want to focus your energy as you develop a strategy for how to write an argumentative essay: supporting your claim—your thesis statement—in your essay, addressing other viewpoints on your topic, and writing a solid conclusion. If you put thought and effort into these three things, you’re much more likely to write an argumentative essay that’s engaging, persuasive, and memorable...aka A+ material.
Focus Area 1: Supporting Your Claim With Evidence and Explanations
So you’ve chosen your topic, decided what your position will be, and written a thesis statement. But like we see in comment threads across the Internet, if you make a claim and don’t back it up with evidence, what do people say? “Where’s your proof?” “Show me the facts!” “Do you have any evidence to support that claim?”
Of course you’ve done your research like we talked about. Supporting your claim in your thesis statement is where that research comes in handy.
You can’t just use your research to state the facts, though. Remember your reader? They’re going to expect you to do some of the dirty work of interpreting the evidence for them. That’s why it’s important to know the difference between evidence and explanations, and how and when to use both in your argumentative essay.
What Evidence Is and When You Should Use It
Evidence can be material from any authoritative and credible outside source that supports your position on your topic. In some cases, evidence can come in the form of photos, video footage, or audio recordings. In other cases, you might be pulling reasons, facts, or statistics from news media articles, public policy, or scholarly books or journals.
There are some clues you can look for that indicate whether or not a source is credible , such as whether:
- The website where you found the source ends in .edu, .gov, or .org
- The source was published by a university press
- The source was published in a peer-reviewed journal
- The authors did extensive research to support the claims they make in the source
This is just a short list of some of the clues that a source is likely a credible one, but just because a source was published by a prestigious press or the authors all have PhDs doesn’t necessarily mean it is the best piece of evidence for you to use to support your argument.
In addition to evaluating the source’s credibility, you’ve got to consider what types of evidence might come across as most persuasive in the context of the argument you’re making and who your readers are. In other words, stepping back and getting a bird’s eye view of the entire context of your argumentative paper is key to choosing evidence that will strengthen your argument.
On some exams, like the AP exams , you may be given pretty strict parameters for what evidence to use and how to use it. You might be given six short readings that all address the same topic, have 15 minutes to read them, then be required to pull material from a minimum of three of the short readings to support your claim in an argumentative essay.
When the sources are handed to you like that, be sure to take notes that will help you pick out evidence as you read. Highlight, underline, put checkmarks in the margins of your exam . . . do whatever you need to do to begin identifying the material that you find most helpful or relevant. Those highlights and check marks might just turn into your quotes, paraphrases, or summaries of evidence in your completed exam essay.
What Explanations Are and When You Should Use Them
Now you know that taking a strategic mindset toward evidence and explanations is critical to grasping how to write an argumentative essay. Unfortunately, evidence doesn’t speak for itself. While it may be obvious to you, the researcher and writer, how the pieces of evidence you’ve included are relevant to your audience, it might not be as obvious to your reader.
That’s where explanations—or analysis, or interpretations—come in. You never want to just stick some quotes from an article into your paragraph and call it a day. You do want to interpret the evidence you’ve included to show your reader how that evidence supports your claim.
Now, that doesn’t mean you’re going to be saying, “This piece of evidence supports my argument because...”. Instead, you want to comment on the evidence in a way that helps your reader see how it supports the position you stated in your thesis. We’ll talk more about how to do this when we show you an example of a strong body paragraph from an argumentative essay here in a bit.
Understanding how to incorporate evidence and explanations to your advantage is really important. Here’s why: when you’re writing an argumentative essay, particularly on standardized tests or the AP exam, the exam scorers can’t penalize you for the position you take. Instead, their evaluation is going to focus on the way you incorporated evidence and explained it in your essay.

Focus Area 2: How—and When—to Address Other Viewpoints
Why would we be making arguments at all if there weren’t multiple views out there on a given topic? As you do research and consider the background surrounding your topic, you’ll probably come across arguments that stand in direct opposition to your position.
Oftentimes, teachers will ask you to “address the opposition” in your argumentative essay. What does that mean, though, to “ address the opposition ?”
Opposing viewpoints function kind of like an elephant in the room. Your audience knows they’re there. In fact, your audience might even buy into an opposing viewpoint and be waiting for you to show them why your viewpoint is better. If you don’t, it means that you’ll have a hard time convincing your audience to buy your argument.
Addressing the opposition is a balancing act: you don’t want to undermine your own argument, but you don’t want to dismiss the validity of opposing viewpoints out-of-hand or ignore them altogether, which can also undermine your argument.
This isn’t the only acceptable approach, but it’s common practice to wait to address the opposition until close to the end of an argumentative essay. But why?
Well, waiting to present an opposing viewpoint until after you’ve thoroughly supported your own argument is strategic. You aren’t going to go into great detail discussing the opposing viewpoint: you’re going to explain what that viewpoint is fairly, but you’re also going to point out what’s wrong with it.
It can also be effective to read the opposition through the lens of your own argument and the evidence you’ve used to support it. If the evidence you’ve already included supports your argument, it probably doesn’t support the opposing viewpoint. Without being too obvious, it might be worth pointing this out when you address the opposition.

Focus Area #3: Writing the Conclusion
It’s common to conclude an argumentative essay by reiterating the thesis statement in some way, either by reminding the reader what the overarching argument was in the first place or by reviewing the main points and evidence that you covered.
You don’t just want to restate your thesis statement and review your main points and call it a day, though. So much has happened since you stated your thesis in the introduction! And why waste a whole paragraph—the very last thing your audience is going to read—on just repeating yourself?
Here’s an approach to the conclusion that can give your audience a fresh perspective on your argument: reinterpret your thesis statement for them in light of all the evidence and explanations you’ve provided. Think about how your readers might read your thesis statement in a new light now that they’ve heard your whole argument out.
That’s what you want to leave your audience with as you conclude your argumentative paper: a brief explanation of why all that arguing mattered in the first place. If you can give your audience something to continue pondering after they’ve read your argument, that’s even better.
One thing you want to avoid in your conclusion, though: presenting new supporting points or new evidence. That can just be confusing for your reader. Stick to telling your reader why the argument you’ve already made matters, and your argument will stick with your reader.

A Strong Argumentative Essay: Examples
For some aspiring argumentative essay writers, showing is better than telling. To show rather than tell you what makes a strong argumentative essay, we’ve provided three examples of possible body paragraphs for an argumentative essay below.
Think of these example paragraphs as taking on the form of the “Argumentative Point #1 → Evidence —> Explanation —> Repeat” process we talked through earlier. It’s always nice to be able to compare examples, so we’ve included three paragraphs from an argumentative paper ranging from poor (or needs a lot of improvement, if you’re feeling generous), to better, to best.
All of the example paragraphs are for an essay with this thesis statement:
Thesis Statement: In order to most effectively protect user data and combat the spread of disinformation, the U.S. government should implement more stringent regulations of Facebook and other social media outlets.
As you read the examples, think about what makes them different, and what makes the “best” paragraph more effective than the “better” and “poor” paragraphs. Here we go:
A Poor Argument
Example Body Paragraph: Data mining has affected a lot of people in recent years. Facebook has 2.23 billion users from around the world, and though it would take a huge amount of time and effort to make sure a company as big as Facebook was complying with privacy regulations in countries across the globe, adopting a common framework for privacy regulation in more countries would be the first step. In fact, Mark Zuckerberg himself supports adopting a global framework for privacy and data protection, which would protect more users than before.
What’s Wrong With This Example?
First, let’s look at the thesis statement. Ask yourself: does this make a claim that some people might agree with, but others might disagree with?
The answer is yes. Some people probably think that Facebook should be regulated, while others might believe that’s too much government intervention. Also, there are definitely good, reliable sources out there that will help this writer prove their argument. So this paper is off to a strong start!
Unfortunately, this writer doesn’t do a great job proving their thesis in their body paragraph. First, the topic sentence—aka the first sentence of the paragraph—doesn’t make a point that directly supports the position stated in the thesis. We’re trying to argue that government regulation will help protect user data and combat the spread of misinformation, remember? The topic sentence should make a point that gets right at that, instead of throwing out a random fact about data mining.
Second, because the topic sentence isn’t focused on making a clear point, the rest of the paragraph doesn’t have much relevant information, and it fails to provide credible evidence that supports the claim made in the thesis statement. For example, it would be a great idea to include exactly what Mark Zuckerberg said ! So while there’s definitely some relevant information in this paragraph, it needs to be presented with more evidence.
A Better Argument
This paragraph is a bit better than the first one, but it still needs some work. The topic sentence is a bit too long, and it doesn’t make a point that clearly supports the position laid out in the thesis statement. The reader already knows that mining user data is a big issue, so the topic sentence would be a great place to make a point about why more stringent government regulations would most effectively protect user data.
There’s also a problem with how the evidence is incorporated in this example. While there is some relevant, persuasive evidence included in this paragraph, there’s no explanation of why or how it is relevant . Remember, you can’t assume that your evidence speaks for itself: you have to interpret its relevance for your reader. That means including at least a sentence that tells your reader why the evidence you’ve chosen proves your argument.
A Best—But Not Perfect!—Argument
Example Body Paragraph: Though Facebook claims to be implementing company policies that will protect user data and stop the spread of misinformation , its attempts have been unsuccessful compared to those made by the federal government. When PricewaterhouseCoopers conducted a Federal Trade Commission-mandated assessment of Facebook’s partnerships with Microsoft and the makers of the Blackberry handset in 2013, the team found limited evidence that Facebook had monitored or even checked that its partners had complied with Facebook’s existing data use policies. In fact, Facebook’s own auditors confirmed the PricewaterhouseCoopers findings, despite the fact that Facebook claimed that the company was making greater attempts to safeguard users’ personal information. In contrast, bills written by Congress have been more successful in changing Facebook’s practices than Facebook’s own company policies have. According to The Washington Post, The Honest Ads Act of 2017 “created public demand for transparency and changed how social media companies disclose online political advertising.” These policy efforts, though thus far unsuccessful in passing legislation, have nevertheless pushed social media companies to change some of their practices by sparking public outrage and negative media attention.
Why This Example Is The Best
This paragraph isn’t perfect, but it is the most effective at doing some of the things that you want to do when you write an argumentative essay.
First, the topic sentences get to the point . . . and it’s a point that supports and explains the claim made in the thesis statement! It gives a clear reason why our claim in favor of more stringent government regulations is a good claim : because Facebook has failed to self-regulate its practices.
This paragraph also provides strong evidence and specific examples that support the point made in the topic sentence. The evidence presented shows specific instances in which Facebook has failed to self-regulate, and other examples where the federal government has successfully influenced regulation of Facebook’s practices for the better.
Perhaps most importantly, though, this writer explains why the evidence is important. The bold sentence in the example is where the writer links the evidence back to their opinion. In this case, they explain that the pressure from Federal Trade Commission and Congress—and the threat of regulation—have helped change Facebook for the better.
Why point out that this isn’t a perfect paragraph, though? Because you won’t be writing perfect paragraphs when you’re taking timed exams either. But get this: you don’t have to write perfect paragraphs to make a good score on AP exams or even on an essay you write for class. Like in this example paragraph, you just have to effectively develop your position by appropriately and convincingly relying on evidence from good sources.

Top 3 Takeaways For Writing Argumentative Essays
This is all great information, right? If (when) you have to write an argumentative essay, you’ll be ready. But when in doubt, remember these three things about how to write an argumentative essay, and you’ll emerge victorious:
Takeaway #1: Read Closely and Carefully
This tip applies to every aspect of writing an argumentative essay. From making sure you’re addressing your prompt, to really digging into your sources, to proofreading your final paper...you’ll need to actively and pay attention! This is especially true if you’re writing on the clock, like during an AP exam.
Takeaway #2: Make Your Argument the Focus of the Essay
Define your position clearly in your thesis statement and stick to that position! The thesis is the backbone of your paper, and every paragraph should help prove your thesis in one way or another. But sometimes you get to the end of your essay and realize that you’ve gotten off topic, or that your thesis doesn’t quite fit. Don’t worry—if that happens, you can always rewrite your thesis to fit your paper!
Takeaway #3: Use Sources to Develop Your Argument—and Explain Them
Nothing is as powerful as good, strong evidence. First, make sure you’re finding credible sources that support your argument. Then you can paraphrase, briefly summarize, or quote from your sources as you incorporate them into your paragraphs. But remember the most important part: you have to explain why you’ve chosen that evidence and why it proves your thesis.
What's Next?
Once you’re comfortable with how to write an argumentative essay, it’s time to learn some more advanced tips and tricks for putting together a killer argument.
Keep in mind that argumentative essays are just one type of essay you might encounter. That’s why we’ve put together more specific guides on how to tackle IB essays , SAT essays , and ACT essays .
But what about admissions essays? We’ve got you covered. Not only do we have comprehensive guides to the Coalition App and Common App essays, we also have tons of individual college application guides, too . You can search through all of our college-specific posts by clicking here.
Trending Now
How to Get Into Harvard and the Ivy League
How to Get a Perfect 4.0 GPA
How to Write an Amazing College Essay
What Exactly Are Colleges Looking For?
ACT vs. SAT: Which Test Should You Take?
When should you take the SAT or ACT?
Get Your Free

Find Your Target SAT Score
Free Complete Official SAT Practice Tests
How to Get a Perfect SAT Score, by an Expert Full Scorer
Score 800 on SAT Math
Score 800 on SAT Reading and Writing
How to Improve Your Low SAT Score
Score 600 on SAT Math
Score 600 on SAT Reading and Writing
Find Your Target ACT Score
Complete Official Free ACT Practice Tests
How to Get a Perfect ACT Score, by a 36 Full Scorer
Get a 36 on ACT English
Get a 36 on ACT Math
Get a 36 on ACT Reading
Get a 36 on ACT Science
How to Improve Your Low ACT Score
Get a 24 on ACT English
Get a 24 on ACT Math
Get a 24 on ACT Reading
Get a 24 on ACT Science
Stay Informed
Get the latest articles and test prep tips!

Ashley Sufflé Robinson has a Ph.D. in 19th Century English Literature. As a content writer for PrepScholar, Ashley is passionate about giving college-bound students the in-depth information they need to get into the school of their dreams.
Ask a Question Below
Have any questions about this article or other topics? Ask below and we'll reply!
Argumentative Essay Examples to Inspire You (+ Free Formula)
.webp)
Table of contents

Meredith Sell
Have you ever been asked to explain your opinion on a controversial issue?
- Maybe your family got into a discussion about chemical pesticides
- Someone at work argues against investing resources into your project
- Your partner thinks intermittent fasting is the best way to lose weight and you disagree
Proving your point in an argumentative essay can be challenging, unless you are using a proven formula.
Argumentative essay formula & example
In the image below, you can see a recommended structure for argumentative essays. It starts with the topic sentence, which establishes the main idea of the essay. Next, this hypothesis is developed in the development stage. Then, the rebuttal, or the refutal of the main counter argument or arguments. Then, again, development of the rebuttal. This is followed by an example, and ends with a summary. This is a very basic structure, but it gives you a bird-eye-view of how a proper argumentative essay can be built.

Writing an argumentative essay (for a class, a news outlet, or just for fun) can help you improve your understanding of an issue and sharpen your thinking on the matter. Using researched facts and data, you can explain why you or others think the way you do, even while other reasonable people disagree.

What Is an Argumentative Essay?
An argumentative essay is an explanatory essay that takes a side.
Instead of appealing to emotion and personal experience to change the reader’s mind, an argumentative essay uses logic and well-researched factual information to explain why the thesis in question is the most reasonable opinion on the matter.
Over several paragraphs or pages, the author systematically walks through:
- The opposition (and supporting evidence)
- The chosen thesis (and its supporting evidence)
At the end, the author leaves the decision up to the reader, trusting that the case they’ve made will do the work of changing the reader’s mind. Even if the reader’s opinion doesn’t change, they come away from the essay with a greater understanding of the perspective presented — and perhaps a better understanding of their original opinion.
All of that might make it seem like writing an argumentative essay is way harder than an emotionally-driven persuasive essay — but if you’re like me and much more comfortable spouting facts and figures than making impassioned pleas, you may find that an argumentative essay is easier to write.
Plus, the process of researching an argumentative essay means you can check your assumptions and develop an opinion that’s more based in reality than what you originally thought. I know for sure that my opinions need to be fact checked — don’t yours?
So how exactly do we write the argumentative essay?
How do you start an argumentative essay
First, gain a clear understanding of what exactly an argumentative essay is. To formulate a proper topic sentence, you have to be clear on your topic, and to explore it through research.
Students have difficulty starting an essay because the whole task seems intimidating, and they are afraid of spending too much time on the topic sentence. Experienced writers, however, know that there is no set time to spend on figuring out your topic. It's a real exploration that is based to a large extent on intuition.
6 Steps to Write an Argumentative Essay (Persuasion Formula)
Use this checklist to tackle your essay one step at a time:
.webp)
1. Research an issue with an arguable question
To start, you need to identify an issue that well-informed people have varying opinions on. Here, it’s helpful to think of one core topic and how it intersects with another (or several other) issues. That intersection is where hot takes and reasonable (or unreasonable) opinions abound.
I find it helpful to stage the issue as a question.
For example:
Is it better to legislate the minimum size of chicken enclosures or to outlaw the sale of eggs from chickens who don’t have enough space?
Should snow removal policies focus more on effectively keeping roads clear for traffic or the environmental impacts of snow removal methods?
Once you have your arguable question ready, start researching the basic facts and specific opinions and arguments on the issue. Do your best to stay focused on gathering information that is directly relevant to your topic. Depending on what your essay is for, you may reference academic studies, government reports, or newspaper articles.
Research your opposition and the facts that support their viewpoint as much as you research your own position . You’ll need to address your opposition in your essay, so you’ll want to know their argument from the inside out.
2. Choose a side based on your research
You likely started with an inclination toward one side or the other, but your research should ultimately shape your perspective. So once you’ve completed the research, nail down your opinion and start articulating the what and why of your take.
What: I think it’s better to outlaw selling eggs from chickens whose enclosures are too small.
Why: Because if you regulate the enclosure size directly, egg producers outside of the government’s jurisdiction could ship eggs into your territory and put nearby egg producers out of business by offering better prices because they don’t have the added cost of larger enclosures.
This is an early form of your thesis and the basic logic of your argument. You’ll want to iterate on this a few times and develop a one-sentence statement that sums up the thesis of your essay.
Thesis: Outlawing the sale of eggs from chickens with cramped living spaces is better for business than regulating the size of chicken enclosures.
Now that you’ve articulated your thesis , spell out the counterargument(s) as well. Putting your opposition’s take into words will help you throughout the rest of the essay-writing process. (You can start by choosing the counter argument option with Wordtune Spices .)

Counter argument:

There may be one main counterargument to articulate, or several. Write them all out and start thinking about how you’ll use evidence to address each of them or show why your argument is still the best option.
3. Organize the evidence — for your side and the opposition
You did all of that research for a reason. Now’s the time to use it.
Hopefully, you kept detailed notes in a document, complete with links and titles of all your source material. Go through your research document and copy the evidence for your argument and your opposition’s into another document.
List the main points of your argument. Then, below each point, paste the evidence that backs them up.
If you’re writing about chicken enclosures, maybe you found evidence that shows the spread of disease among birds kept in close quarters is worse than among birds who have more space. Or maybe you found information that says eggs from free-range chickens are more flavorful or nutritious. Put that information next to the appropriate part of your argument.
Repeat the process with your opposition’s argument: What information did you find that supports your opposition? Paste it beside your opposition’s argument.
You could also put information here that refutes your opposition, but organize it in a way that clearly tells you — at a glance — that the information disproves their point.
Counterargument: Outlawing the sale of eggs from chickens with too small enclosures will negatively affect prices and sales.
BUT: Sicknesses like avian flu spread more easily through small enclosures and could cause a shortage that would drive up egg prices naturally, so ensuring larger enclosures is still a better policy for consumers over the long term.
As you organize your research and see the evidence all together, start thinking through the best way to order your points.
Will it be better to present your argument all at once or to break it up with opposition claims you can quickly refute? Would some points set up other points well? Does a more complicated point require that the reader understands a simpler point first?
Play around and rearrange your notes to see how your essay might flow one way or another.
4. Freewrite or outline to think through your argument
Is your brain buzzing yet? At this point in the process, it can be helpful to take out a notebook or open a fresh document and dump whatever you’re thinking on the page.
Where should your essay start? What ground-level information do you need to provide your readers before you can dive into the issue?
Use your organized evidence document from step 3 to think through your argument from beginning to end, and determine the structure of your essay.
There are three typical structures for argumentative essays:
- Make your argument and tackle opposition claims one by one, as they come up in relation to the points of your argument - In this approach, the whole essay — from beginning to end — focuses on your argument, but as you make each point, you address the relevant opposition claims individually. This approach works well if your opposition’s views can be quickly explained and refuted and if they directly relate to specific points in your argument.
- Make the bulk of your argument, and then address the opposition all at once in a paragraph (or a few) - This approach puts the opposition in its own section, separate from your main argument. After you’ve made your case, with ample evidence to convince your readers, you write about the opposition, explaining their viewpoint and supporting evidence — and showing readers why the opposition’s argument is unconvincing. Once you’ve addressed the opposition, you write a conclusion that sums up why your argument is the better one.
- Open your essay by talking about the opposition and where it falls short. Build your entire argument to show how it is superior to that opposition - With this structure, you’re showing your readers “a better way” to address the issue. After opening your piece by showing how your opposition’s approaches fail, you launch into your argument, providing readers with ample evidence that backs you up.
As you think through your argument and examine your evidence document, consider which structure will serve your argument best. Sketch out an outline to give yourself a map to follow in the writing process. You could also rearrange your evidence document again to match your outline, so it will be easy to find what you need when you start writing.
5. Write your first draft
You have an outline and an organized document with all your points and evidence lined up and ready. Now you just have to write your essay.
In your first draft, focus on getting your ideas on the page. Your wording may not be perfect (whose is?), but you know what you’re trying to say — so even if you’re overly wordy and taking too much space to say what you need to say, put those words on the page.
Follow your outline, and draw from that evidence document to flesh out each point of your argument. Explain what the evidence means for your argument and your opposition. Connect the dots for your readers so they can follow you, point by point, and understand what you’re trying to say.
As you write, be sure to include:
1. Any background information your reader needs in order to understand the issue in question.
2. Evidence for both your argument and the counterargument(s). This shows that you’ve done your homework and builds trust with your reader, while also setting you up to make a more convincing argument. (If you find gaps in your research while you’re writing, Wordtune can help.

3. A conclusion that sums up your overall argument and evidence — and leaves the reader with an understanding of the issue and its significance. This sort of conclusion brings your essay to a strong ending that doesn’t waste readers’ time, but actually adds value to your case.
6. Revise (with Wordtune)
The hard work is done: you have a first draft. Now, let’s fine tune your writing.
I like to step away from what I’ve written for a day (or at least a night of sleep) before attempting to revise. It helps me approach clunky phrases and rough transitions with fresh eyes. If you don’t have that luxury, just get away from your computer for a few minutes — use the bathroom, do some jumping jacks, eat an apple — and then come back and read through your piece.
As you revise, make sure you …
- Get the facts right. An argument with false evidence falls apart pretty quickly, so check your facts to make yours rock solid.
- Don’t misrepresent the opposition or their evidence. If someone who holds the opposing view reads your essay, they should affirm how you explain their side — even if they disagree with your rebuttal.
- Present a case that builds over the course of your essay, makes sense, and ends on a strong note. One point should naturally lead to the next. Your readers shouldn’t feel like you’re constantly changing subjects. You’re making a variety of points, but your argument should feel like a cohesive whole.
- Paraphrase sources and cite them appropriately. Did you skip citations when writing your first draft? No worries — you can add them now. And check that you don’t overly rely on quotations. (Need help paraphrasing? Wordtune can help. Simply highlight the sentence or phrase you want to adjust and sort through Wordtune’s suggestions.)
- Tighten up overly wordy explanations and sharpen any convoluted ideas. Wordtune makes a great sidekick for this too 😉


Words to start an argumentative essay
The best way to introduce a convincing argument is to provide a strong thesis statement . These are the words I usually use to start an argumentative essay:
- It is indisputable that the world today is facing a multitude of issues
- With the rise of ____, the potential to make a positive difference has never been more accessible
- It is essential that we take action now and tackle these issues head-on
- it is critical to understand the underlying causes of the problems standing before us
- Opponents of this idea claim
- Those who are against these ideas may say
- Some people may disagree with this idea
- Some people may say that ____, however
When refuting an opposing concept, use:
- These researchers have a point in thinking
- To a certain extent they are right
- After seeing this evidence, there is no way one can agree with this idea
- This argument is irrelevant to the topic
Are you convinced by your own argument yet? Ready to brave the next get-together where everyone’s talking like they know something about intermittent fasting , chicken enclosures , or snow removal policies?
Now if someone asks you to explain your evidence-based but controversial opinion, you can hand them your essay and ask them to report back after they’ve read it.
Share This Article:
%20(1).webp)
8 Tips for E-commerce Copywriting Success (with Examples!)
.webp)
The Brand Strategy Deck You Need to Drive Social Media Results + 5 Examples

Grammarly Alternatives: Which Writing Assistant is the Best Choice for You?
Looking for fresh content, thank you your submission has been received.
Module 9: Academic Argument
The argumentative essay, learning objectives.
- Examine types of argumentative essays
Argumentative Essays
You may have heard it said that all writing is an argument of some kind. Even if you’re writing an informative essay, you still have the job of trying to convince your audience that the information is important. However, there are times you’ll be asked to write an essay that is specifically an argumentative piece.
An argumentative essay is one that makes a clear assertion or argument about some topic or issue. When you’re writing an argumentative essay, it’s important to remember that an academic argument is quite different from a regular, emotional argument. Note that sometimes students forget the academic aspect of an argumentative essay and write essays that are much too emotional for an academic audience. It’s important for you to choose a topic you feel passionately about (if you’re allowed to pick your topic), but you have to be sure you aren’t too emotionally attached to a topic. In an academic argument, you’ll have a lot more constraints you have to consider, and you’ll focus much more on logic and reasoning than emotions.

Figure 1 . When writing an argumentative essay, students must be able to separate emotion based arguments from logic based arguments in order to appeal to an academic audience.
Argumentative essays are quite common in academic writing and are often an important part of writing in all disciplines. You may be asked to take a stand on a social issue in your introduction to writing course, but you could also be asked to take a stand on an issue related to health care in your nursing courses or make a case for solving a local environmental problem in your biology class. And, since argument is such a common essay assignment, it’s important to be aware of some basic elements of a good argumentative essay.
When your professor asks you to write an argumentative essay, you’ll often be given something specific to write about. For example, you may be asked to take a stand on an issue you have been discussing in class. Perhaps, in your education class, you would be asked to write about standardized testing in public schools. Or, in your literature class, you might be asked to argue the effects of protest literature on public policy in the United States.
However, there are times when you’ll be given a choice of topics. You might even be asked to write an argumentative essay on any topic related to your field of study or a topic you feel that is important personally.
Whatever the case, having some knowledge of some basic argumentative techniques or strategies will be helpful as you write. Below are some common types of arguments.
Causal Arguments
- You write about how something has caused something else. For example, you might explore the increase of industrial pollution and the resulting decline of large mammals in the world’s ocean.
Evaluation Arguments
- You can write an argumentative evaluation of something as “good” or “bad,” but you also need to establish the criteria for “good” or “bad.” For example, you might evaluate a children’s book for your Introduction to Educational Theory class, but you would need to establish clear criteria for your evaluation for your audience.
Proposal Arguments
- With this type of writing, you need to propose a solution to a problem. First, you must establish a clear problem and then propose a specific solution to that problem. For example, you might argue for a removal of parking fines on students who use the parking deck on campus.
Narrative Arguments
- For this type of argument, you make your case by telling a story with a clear point related to your argument. For example, you might write a narrative about your negative experiences with standardized testing in order to make a case for reform.
Rebuttal Arguments
- In a rebuttal argument, you build your case around refuting an idea or ideas that have come before. In other words, your starting point is to challenge the ideas of the past. For this type of writing assignment, you have to explain what you are refuting first, and then you can expand on your new ideas or perspectives.
Definition Arguments
- In this type of argument, you use a definition as the starting point for making your case. For example, in a definition argument, you might argue that NCAA basketball players should be defined as professional players and, therefore, should be paid.
Essay Examples
- You can read more about an argumentative essay on the consequences of fast fashion . Read it and look at the comments to recognize strategies and techniques the author uses to convey her ideas.
- In this example, you’ll see a sample argumentative paper from a psychology class submitted in APA format. Key parts of the argumentative structure have been noted for you in the sample.
Link to Learning
For more examples of types of argumentative essays, visit the Argumentative Purposes section of the Excelsior OWL .
- Argumentative Essay. Provided by : Excelsior OWL. Located at : https://owl.excelsior.edu/rhetorical-styles/argumentative-essay/ . License : CC BY: Attribution
- Image of a man with a heart and a brain. Authored by : Mohamed Hassan. Provided by : Pixabay. Located at : https://pixabay.com/illustrations/decision-brain-heart-mind-4083469/ . License : Other . License Terms : https://pixabay.com/service/terms/#license

Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
- The four main types of essay | Quick guide with examples
The Four Main Types of Essay | Quick Guide with Examples
Published on September 4, 2020 by Jack Caulfield . Revised on July 23, 2023.
An essay is a focused piece of writing designed to inform or persuade. There are many different types of essay, but they are often defined in four categories: argumentative, expository, narrative, and descriptive essays.
Argumentative and expository essays are focused on conveying information and making clear points, while narrative and descriptive essays are about exercising creativity and writing in an interesting way. At university level, argumentative essays are the most common type.
| Essay type | Skills tested | Example prompt |
|---|---|---|
| Has the rise of the internet had a positive or negative impact on education? | ||
| Explain how the invention of the printing press changed European society in the 15th century. | ||
| Write about an experience where you learned something about yourself. | ||
| Describe an object that has sentimental value for you. |
In high school and college, you will also often have to write textual analysis essays, which test your skills in close reading and interpretation.
Instantly correct all language mistakes in your text
Upload your document to correct all your mistakes in minutes
Table of contents
Argumentative essays, expository essays, narrative essays, descriptive essays, textual analysis essays, other interesting articles, frequently asked questions about types of essays.
An argumentative essay presents an extended, evidence-based argument. It requires a strong thesis statement —a clearly defined stance on your topic. Your aim is to convince the reader of your thesis using evidence (such as quotations ) and analysis.
Argumentative essays test your ability to research and present your own position on a topic. This is the most common type of essay at college level—most papers you write will involve some kind of argumentation.
The essay is divided into an introduction, body, and conclusion:
- The introduction provides your topic and thesis statement
- The body presents your evidence and arguments
- The conclusion summarizes your argument and emphasizes its importance
The example below is a paragraph from the body of an argumentative essay about the effects of the internet on education. Mouse over it to learn more.
A common frustration for teachers is students’ use of Wikipedia as a source in their writing. Its prevalence among students is not exaggerated; a survey found that the vast majority of the students surveyed used Wikipedia (Head & Eisenberg, 2010). An article in The Guardian stresses a common objection to its use: “a reliance on Wikipedia can discourage students from engaging with genuine academic writing” (Coomer, 2013). Teachers are clearly not mistaken in viewing Wikipedia usage as ubiquitous among their students; but the claim that it discourages engagement with academic sources requires further investigation. This point is treated as self-evident by many teachers, but Wikipedia itself explicitly encourages students to look into other sources. Its articles often provide references to academic publications and include warning notes where citations are missing; the site’s own guidelines for research make clear that it should be used as a starting point, emphasizing that users should always “read the references and check whether they really do support what the article says” (“Wikipedia:Researching with Wikipedia,” 2020). Indeed, for many students, Wikipedia is their first encounter with the concepts of citation and referencing. The use of Wikipedia therefore has a positive side that merits deeper consideration than it often receives.
Here's why students love Scribbr's proofreading services
Discover proofreading & editing
An expository essay provides a clear, focused explanation of a topic. It doesn’t require an original argument, just a balanced and well-organized view of the topic.
Expository essays test your familiarity with a topic and your ability to organize and convey information. They are commonly assigned at high school or in exam questions at college level.
The introduction of an expository essay states your topic and provides some general background, the body presents the details, and the conclusion summarizes the information presented.
A typical body paragraph from an expository essay about the invention of the printing press is shown below. Mouse over it to learn more.
The invention of the printing press in 1440 changed this situation dramatically. Johannes Gutenberg, who had worked as a goldsmith, used his knowledge of metals in the design of the press. He made his type from an alloy of lead, tin, and antimony, whose durability allowed for the reliable production of high-quality books. This new technology allowed texts to be reproduced and disseminated on a much larger scale than was previously possible. The Gutenberg Bible appeared in the 1450s, and a large number of printing presses sprang up across the continent in the following decades. Gutenberg’s invention rapidly transformed cultural production in Europe; among other things, it would lead to the Protestant Reformation.
A narrative essay is one that tells a story. This is usually a story about a personal experience you had, but it may also be an imaginative exploration of something you have not experienced.
Narrative essays test your ability to build up a narrative in an engaging, well-structured way. They are much more personal and creative than other kinds of academic writing . Writing a personal statement for an application requires the same skills as a narrative essay.
A narrative essay isn’t strictly divided into introduction, body, and conclusion, but it should still begin by setting up the narrative and finish by expressing the point of the story—what you learned from your experience, or why it made an impression on you.
Mouse over the example below, a short narrative essay responding to the prompt “Write about an experience where you learned something about yourself,” to explore its structure.
Since elementary school, I have always favored subjects like science and math over the humanities. My instinct was always to think of these subjects as more solid and serious than classes like English. If there was no right answer, I thought, why bother? But recently I had an experience that taught me my academic interests are more flexible than I had thought: I took my first philosophy class.
Before I entered the classroom, I was skeptical. I waited outside with the other students and wondered what exactly philosophy would involve—I really had no idea. I imagined something pretty abstract: long, stilted conversations pondering the meaning of life. But what I got was something quite different.
A young man in jeans, Mr. Jones—“but you can call me Rob”—was far from the white-haired, buttoned-up old man I had half-expected. And rather than pulling us into pedantic arguments about obscure philosophical points, Rob engaged us on our level. To talk free will, we looked at our own choices. To talk ethics, we looked at dilemmas we had faced ourselves. By the end of class, I’d discovered that questions with no right answer can turn out to be the most interesting ones.
The experience has taught me to look at things a little more “philosophically”—and not just because it was a philosophy class! I learned that if I let go of my preconceptions, I can actually get a lot out of subjects I was previously dismissive of. The class taught me—in more ways than one—to look at things with an open mind.
A descriptive essay provides a detailed sensory description of something. Like narrative essays, they allow you to be more creative than most academic writing, but they are more tightly focused than narrative essays. You might describe a specific place or object, rather than telling a whole story.
Descriptive essays test your ability to use language creatively, making striking word choices to convey a memorable picture of what you’re describing.
A descriptive essay can be quite loosely structured, though it should usually begin by introducing the object of your description and end by drawing an overall picture of it. The important thing is to use careful word choices and figurative language to create an original description of your object.
Mouse over the example below, a response to the prompt “Describe a place you love to spend time in,” to learn more about descriptive essays.
On Sunday afternoons I like to spend my time in the garden behind my house. The garden is narrow but long, a corridor of green extending from the back of the house, and I sit on a lawn chair at the far end to read and relax. I am in my small peaceful paradise: the shade of the tree, the feel of the grass on my feet, the gentle activity of the fish in the pond beside me.
My cat crosses the garden nimbly and leaps onto the fence to survey it from above. From his perch he can watch over his little kingdom and keep an eye on the neighbours. He does this until the barking of next door’s dog scares him from his post and he bolts for the cat flap to govern from the safety of the kitchen.
With that, I am left alone with the fish, whose whole world is the pond by my feet. The fish explore the pond every day as if for the first time, prodding and inspecting every stone. I sometimes feel the same about sitting here in the garden; I know the place better than anyone, but whenever I return I still feel compelled to pay attention to all its details and novelties—a new bird perched in the tree, the growth of the grass, and the movement of the insects it shelters…
Sitting out in the garden, I feel serene. I feel at home. And yet I always feel there is more to discover. The bounds of my garden may be small, but there is a whole world contained within it, and it is one I will never get tired of inhabiting.
Prevent plagiarism. Run a free check.
Though every essay type tests your writing skills, some essays also test your ability to read carefully and critically. In a textual analysis essay, you don’t just present information on a topic, but closely analyze a text to explain how it achieves certain effects.
Rhetorical analysis
A rhetorical analysis looks at a persuasive text (e.g. a speech, an essay, a political cartoon) in terms of the rhetorical devices it uses, and evaluates their effectiveness.
The goal is not to state whether you agree with the author’s argument but to look at how they have constructed it.
The introduction of a rhetorical analysis presents the text, some background information, and your thesis statement; the body comprises the analysis itself; and the conclusion wraps up your analysis of the text, emphasizing its relevance to broader concerns.
The example below is from a rhetorical analysis of Martin Luther King Jr.’s “I Have a Dream” speech . Mouse over it to learn more.
King’s speech is infused with prophetic language throughout. Even before the famous “dream” part of the speech, King’s language consistently strikes a prophetic tone. He refers to the Lincoln Memorial as a “hallowed spot” and speaks of rising “from the dark and desolate valley of segregation” to “make justice a reality for all of God’s children.” The assumption of this prophetic voice constitutes the text’s strongest ethical appeal; after linking himself with political figures like Lincoln and the Founding Fathers, King’s ethos adopts a distinctly religious tone, recalling Biblical prophets and preachers of change from across history. This adds significant force to his words; standing before an audience of hundreds of thousands, he states not just what the future should be, but what it will be: “The whirlwinds of revolt will continue to shake the foundations of our nation until the bright day of justice emerges.” This warning is almost apocalyptic in tone, though it concludes with the positive image of the “bright day of justice.” The power of King’s rhetoric thus stems not only from the pathos of his vision of a brighter future, but from the ethos of the prophetic voice he adopts in expressing this vision.
Literary analysis
A literary analysis essay presents a close reading of a work of literature—e.g. a poem or novel—to explore the choices made by the author and how they help to convey the text’s theme. It is not simply a book report or a review, but an in-depth interpretation of the text.
Literary analysis looks at things like setting, characters, themes, and figurative language. The goal is to closely analyze what the author conveys and how.
The introduction of a literary analysis essay presents the text and background, and provides your thesis statement; the body consists of close readings of the text with quotations and analysis in support of your argument; and the conclusion emphasizes what your approach tells us about the text.
Mouse over the example below, the introduction to a literary analysis essay on Frankenstein , to learn more.
Mary Shelley’s Frankenstein is often read as a crude cautionary tale about the dangers of scientific advancement unrestrained by ethical considerations. In this reading, protagonist Victor Frankenstein is a stable representation of the callous ambition of modern science throughout the novel. This essay, however, argues that far from providing a stable image of the character, Shelley uses shifting narrative perspectives to portray Frankenstein in an increasingly negative light as the novel goes on. While he initially appears to be a naive but sympathetic idealist, after the creature’s narrative Frankenstein begins to resemble—even in his own telling—the thoughtlessly cruel figure the creature represents him as. This essay begins by exploring the positive portrayal of Frankenstein in the first volume, then moves on to the creature’s perception of him, and finally discusses the third volume’s narrative shift toward viewing Frankenstein as the creature views him.
If you want to know more about AI tools , college essays , or fallacies make sure to check out some of our other articles with explanations and examples or go directly to our tools!
- Ad hominem fallacy
- Post hoc fallacy
- Appeal to authority fallacy
- False cause fallacy
- Sunk cost fallacy
College essays
- Choosing Essay Topic
- Write a College Essay
- Write a Diversity Essay
- College Essay Format & Structure
- Comparing and Contrasting in an Essay
(AI) Tools
- Grammar Checker
- Paraphrasing Tool
- Text Summarizer
- AI Detector
- Plagiarism Checker
- Citation Generator
At high school and in composition classes at university, you’ll often be told to write a specific type of essay , but you might also just be given prompts.
Look for keywords in these prompts that suggest a certain approach: The word “explain” suggests you should write an expository essay , while the word “describe” implies a descriptive essay . An argumentative essay might be prompted with the word “assess” or “argue.”
The vast majority of essays written at university are some sort of argumentative essay . Almost all academic writing involves building up an argument, though other types of essay might be assigned in composition classes.
Essays can present arguments about all kinds of different topics. For example:
- In a literary analysis essay, you might make an argument for a specific interpretation of a text
- In a history essay, you might present an argument for the importance of a particular event
- In a politics essay, you might argue for the validity of a certain political theory
An argumentative essay tends to be a longer essay involving independent research, and aims to make an original argument about a topic. Its thesis statement makes a contentious claim that must be supported in an objective, evidence-based way.
An expository essay also aims to be objective, but it doesn’t have to make an original argument. Rather, it aims to explain something (e.g., a process or idea) in a clear, concise way. Expository essays are often shorter assignments and rely less on research.
The key difference is that a narrative essay is designed to tell a complete story, while a descriptive essay is meant to convey an intense description of a particular place, object, or concept.
Narrative and descriptive essays both allow you to write more personally and creatively than other kinds of essays , and similar writing skills can apply to both.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
Caulfield, J. (2023, July 23). The Four Main Types of Essay | Quick Guide with Examples. Scribbr. Retrieved July 31, 2024, from https://www.scribbr.com/academic-essay/essay-types/
Is this article helpful?

Jack Caulfield
Other students also liked, how to write an argumentative essay | examples & tips, how to write an expository essay, how to write an essay outline | guidelines & examples, "i thought ai proofreading was useless but..".
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”
Argumentative Essay – Outline, Form, and Examples
What is an argumentative essay.
An argumentative essay requires the writer to investigate a specific topic by collecting and evaluating evidence to establish a position on the subject matter.
When preparing to compose a good argumentative essay, utilize the following steps:
Step 1: Select a topic.
Step 2: Identify a position.
Step 3: Locate appropriate resources.
Step 4: Identify evidence supporting the position. ( NOTE: If there is little evidence in support of the claim, consider re-examining the main argument.)

When gathering evidence, use credible sources . To determine the credibility of the source, consider authority, currency, accuracy, and objectivity:
Who is the author ? Are they an expert in the field? Has a reputable publisher published the work?
How current is the information in the source? Does the currency of the source matter? Does the age of the source impact the content? Is there newer information that disproves the source’s information?
Can other sources verify the accuracy of the information? Does the information contradict that found in other commonly accepted sources?
Is there any evidence of bias, or is the source objective ? Is the research sponsored by an organization that may skew the information?
The following are typically recognized as providing appropriate, credible research material:
Peer-reviewed journals/research papers
Government agencies
Professional organizations
Library databases
Reference books

Writers should avoid using the following sources:
Social media posts
Out-of-date materials
Step 5: Utilize the research to determine a thesis statement that identifies the topic, position, and support(s).
Step 6: Use the evidence to construct an outline, detailing the main supports and relevant evidence.

Argumentative essay outline
After gathering all of the necessary research, the next step in composing an argumentative essay focuses on organizing the information through the use of an outline:
Introduction
Attention Grabber/Hook
Background Information: Include any background information pertinent to the topic that the reader needs to know to understand the argument.
Thesis: State the position in connection to the main topic and identify the supports that will help prove the argument.
Topic sentence
Identify evidence in support of the claim in the topic sentence
Explain how the evidence supports the argument
Evidence 3 (Continue as needed)
Support 2 (Continue as needed)
Restate thesis
Review main supports
Concluding statement
Invite the audience to take a specific action.
Identify the overall importance of the topic and position.

How to write an argumentative essay
Regardless of the writer’s topic or point of view, an argumentative essay should include an introductory paragraph, body paragraphs, a conclusion, and works cited.
Background information
Body Paragraphs
Analysis of evidence
Rephrased thesis
Review of main ideas
Call to action
Works Cited

Argumentative essay introduction
The introduction sets the tone for the entire paper and introduces the argument. In general, the first paragraph(s) should attract the reader’s attention, provide relevant context, and conclude with a thesis statement.
To attract the reader's attention , start with an introductory device. There are several attention-grabbing techniques, the most common of which consist of the following:
The writer can emphasize the topic’s importance by explaining the current interest in the topic or indicating that the subject is influential.
Pertinent statistics give the paper an air of authority.
There are many reasons for a stimulating statement to surprise a reader. Sometimes it is joyful; sometimes it is shocking; sometimes it is surprising because of who said it.
An interesting incident or anecdote can act as a teaser to lure the reader into the remainder of the essay. Be sure that the device is appropriate for the subject and focus of what follows.
Provide the reader with relevant context and background information necessary to understand the topic.
Conclude with a thesis statement that identifies the overall purpose of the essay (topic and position). Writers can also include their support directly in the thesis, which outlines the structure of the essay for the reader.
Avoid the following when writing the introduction to argumentative writing:
Starting with dictionary definitions is too overdone and unappealing.
Do not make an announcement of the topic like “In this paper I will…” or “The purpose of this essay is to….”
Evidence supporting or developing the thesis should be in the body paragraphs, not the introduction.
Beginning the essay with general or absolute statements such as “throughout history...” or “as human beings we always...” or similar statements suggest the writer knows all of history or that all people behave or think in the same way.
Argumentative essay thesis
The thesis statement is the single, specific claim the writer sets out to prove and is typically positioned as the last sentence of the introduction . It is the controlling idea of the entire argument that identifies the topic, position, and reasoning.
When constructing a thesis for an argumentative paper, make sure it contains a side of the argument, not simply a topic. An argumentative thesis identifies the writer’s position on a given topic. If a position cannot be taken, then it is not argumentative thesis:
Topic: Capital punishment is practiced in many states.
Thesis: Capital punishment should be illegal.
While not always required, the thesis statement can include the supports the writer will use to prove the main claim. Therefore, a thesis statement can be structured as follows:
TOPIC + POSITION (+ SUPPORTS)
No Supports: College athletes (TOPIC) should be financially compensated (POSITION).
Supports: College athletes (TOPIC) should be financially compensated (POSITION) because they sacrifice their minds and bodies (SUPPORT 1), cannot hold
Argumentative essay body paragraphs
Body paragraphs can be of varying lengths, but they must present a coherent argument unified under a single topic. They are rarely ever longer than one page, double-spaced; usually they are much shorter.
Lengthy paragraphs indicate a lack of structure. Identify the main ideas of a lengthy paragraph to determine if they make more sense as separate topics in separate paragraphs.
Shorter paragraphs usually indicate a lack of substance; there is not enough evidence or analysis to prove the argument. Develop the ideas more or integrate the information into another paragraph.
The structure of an argumentative paragraph should include a topic sentence, evidence, and a transition.
The topic sentence is the thesis of the paragraph that identifies the arguable point in support of the main argument. The reader should know exactly what the writer is trying to prove within the paragraph by reading the first sentence.
The supporting evidence and analysis provide information to support the claim. There should be a balance between the evidence (facts, quotations, summary of events/plot, etc.) and analysis (interpretation of evidence). If the paragraph is evidence-heavy, there is not much of an argument; if it is analysis-heavy, there is not enough evidence in support of the claim.
The transition can be at the beginning or the end of a paragraph. However, it is much easier to combine the transition with the concluding observation to help the paragraphs flow into one another. Transitions in academic writing should tell the reader where you were, where you are going, and relate to the thesis.
Some essays may benefit from the inclusion of rebuttals to potential counterarguments of the writer’s position.
Argumentative essay conclusion
The conclusion should make readers glad they read the paper. It can suggest broader implications that will not only interest readers but also enrich their understanding in some way. There are three aspects to follow when constructing the conclusion: rephrase the thesis, synthesize information, and call the reader to action.
Rephrased the thesis in the first sentence of the conclusion. It must be in different words; do not simply write it verbatim.
Synthesize the argument by showing how the paper's main points support the argument.
Propose a course of action or a solution to an issue. This can redirect the reader's thought process to apply the ideas to their life or to see the broader implications of the topic.
Avoid the following when constructing the conclusion:
Beginning with an unnecessary, overused phrase such as "in conclusion," "in summary," or "in closing;" although these phrases can work in speeches, they come across as trite in writing
Introducing a new idea or subtopic in the conclusion
Making sentimental, emotional appeals that are out of character with the rest of the paper
Including evidence (quotations, statistics, etc.) that should be in the body of the paper
Argumentative essay examples
Examples of argumentative essays vary depending upon the type:
Academic essays differ based upon the topic and position. These essays follow a more traditional structure and are typically assigned in high school or college. Examples of academic argumentative essay topics include the following:
Advantages or disadvantages of social media
Animal testing
Art education
Benefit or detriment of homework
Capital punishment
Class warfare
Immigration
School uniforms
Universal healthcare
Violence in video games
Argumentative literary essays are typically more informal and do not follow the same structure as an academic essay. The following are popular examples of argumentative literary essays:
“Letter from Birmingham Jail” by Martin Luther King, Jr.
“Death of the Moth” by Virginia Woolf
“Shooting an Elephant” by George Orwell
“Thoughts for the Times on War and Death” by Sigmund Freud
“Does the Truth Matter? Science, Pseudoscience, and Civilization” by Carl Sagan
“Self-Reliance” by Ralph Waldo Emerson
- SAT BootCamp
- SAT MasterClass
- SAT Private Tutoring
- SAT Proctored Practice Test
- ACT Private Tutoring
- Academic Subjects
- College Essay Workshop
- Academic Writing Workshop
- AP English FRQ BootCamp
- 1:1 College Essay Help
- Online Instruction
- Free Resources
12 Essential Steps for Writing an Argumentative Essay (with 10 example essays)
Bonus Material: 10 complete example essays
Writing an essay can often feel like a Herculean task. How do you go from a prompt… to pages of beautifully-written and clearly-supported writing?
This 12-step method is for students who want to write a great essay that makes a clear argument.
In fact, using the strategies from this post, in just 88 minutes, one of our students revised her C+ draft to an A.
If you’re interested in learning how to write awesome argumentative essays and improve your writing grades, this post will teach you exactly how to do it.
First, grab our download so you can follow along with the complete examples.
Then keep reading to see all 12 essential steps to writing a great essay.
Download 10 example essays

Why you need to have a plan
One of the most common mistakes that students make when writing is to just dive in haphazardly without a plan.
Writing is a bit like cooking. If you’re making a meal, would you start throwing ingredients at random into a pot? Probably not!
Instead, you’d probably start by thinking about what you want to cook. Then you’d gather the ingredients, and go to the store if you don’t already have them in your kitchen. Then you’d follow a recipe, step by step, to make your meal.

Here’s our 12-step recipe for writing a great argumentative essay:
- Pick a topic
- Choose your research sources
- Read your sources and take notes
- Create a thesis statement
- Choose three main arguments to support your thesis statement —now you have a skeleton outline
- Populate your outline with the research that supports each argument
- Do more research if necessary
- Add your own analysis
- Add transitions and concluding sentences to each paragraph
- Write an introduction and conclusion for your essay
- Add citations and bibliography
Grab our download to see the complete example at every stage, along with 9 great student essays. Then let’s go through the steps together and write an A+ essay!
1. Pick a topic
Sometimes you might be assigned a topic by your instructor, but often you’ll have to come up with your own idea!
If you don’t pick the right topic, you can be setting yourself up for failure.
Be careful that your topic is something that’s actually arguable —it has more than one side. Check out our carefully-vetted list of 99 topic ideas .
Let’s pick the topic of laboratory animals . Our question is should animals be used for testing and research ?

Download our set of 10 great example essays to jump to the finished version of this essay.
2. Choose your research sources
One of the big differences between the way an academic argumentative essay and the version of the assignment that you may have done in elementary school is that for an academic argumentative essay, we need to support our arguments with evidence .
Where do we get that evidence?
Let’s be honest, we all are likely to start with Google and Wikipedia.
Now, Wikipedia can be a useful starting place if you don’t know very much about a topic, but don’t use Wikipedia as your main source of evidence for your essay.
Instead, look for reputable sources that you can show to your readers as proof of your arguments. It can be helpful to read some sources from either side of your issue.
Look for recently-published sources (within the last 20 years), unless there’s a specific reason to do otherwise.

Good places to look for sources are:
- Books published by academic presses
- Academic journals
- Academic databases like JSTOR and EBSCO
- Nationally-published newspapers and magazines like The New York Times or The Atlantic
- Websites and publications of national institutions like the NIH
- Websites and publications of universities
Some of these sources are typically behind a paywall. This can be frustrating when you’re a middle-school or high-school student.
However, there are often ways to get access to these sources. Librarians (at your school library or local public library) can be fantastic resources, and they can often help you find a copy of the article or book you want to read. In particular, librarians can help you use Interlibrary Loan to order books or journals to your local library!
More and more scientists and other researchers are trying to publish their articles for free online, in order to encourage the free exchange of knowledge. Check out respected open-access platforms like arxiv.org and PLOS ONE .
How do you find these sources?
If you have access to an academic database like JSTOR or EBSCO , that’s a great place to start.
Everyone can use Google Scholar to search for articles. This is a powerful tool and highly recommended!

Of course, if there’s a term you come across that you don’t recognize, you can always just Google it!
How many sources do you need? That depends on the length of your essay and on the assignment. If your instructor doesn’t give you any other guidance, assume that you should have at least three good sources.
For our topic of animal research, here’s a few sources that we could assemble:
Geoff Watts. “Animal Testing: Is It Worth It?” BMJ: British Medical Journal , Jan. 27, 2007, Vol. 334, No. 7586 (Jan. 27, 2007), pp. 182-184.
Kim Bartel Sheehan and Joonghwa Lee. “What’s Cruel About Cruelty Free: An Exploration of Consumers, Moral Heuristics, and Public Policy.” Journal of Animal Ethics , Vol. 4, No. 2 (Fall 2014), pp. 1-15.
Justin Goodman, Alka Chandna and Katherine Roe. “Trends in animal use at US research facilities.” Journal of Medical Ethics , July 2015, Vol. 41, No. 7 (July 2015), pp. 567-569.
Katy Taylor. “Recent Developments in Alternatives to Animal Testing.” In Animal Experimentation: Working Towards a Paradigm Change . Brill 2019.
Thomas Hartung. “Research and Testing Without Animals: Where Are We Now and Where Are We Heading?” In Animal Experimentation: Working Towards a Paradigm Change . Brill 2019.
Bonus: download 10 example essays now .
3. Read your sources and take notes
Once you have a nice pile of sources, it’s time to read them!
As we read, we want to take notes that will be useful to us later as we write our essay.
We want to be careful to keep the source’s ideas separate from our own ideas . Come up with a system to clearly mark the difference as you’re taking notes: use different colors, or use little arrows to represent the ideas that are yours and not the source’s ideas.
We can use this structure to keep notes in an organized way:
| Bibliographic details | – Specific evidence that the source uses – Ideas and themes in the source that seem useful | Figure out the main arguments in the source – Figure out the supporting arguments in the source – How does this source relate to the other sources that you’re using? Does it agree/disagree? Does it use the same or different evidence and reasoning? – What kind of bias does the author have? – Any other thoughts or observations |
Download a template for these research notes here .

For our topic of animal research, our notes might look something like this:
| Kim Bartel Sheehan and Joonghwa Lee. “What’s Cruel About Cruelty Free: An Exploration of Consumers, Moral Heuristics, and Public Policy.” Journal of Animal Ethics , Vol. 4, No. 2 (Fall 2014), pp. 1-15. | Because there are many definitions of the phrase “cruelty-free,” many companies “can (and do) use the term when the product or its ingredients were indeed tested on animals” (1). The authors compare “cruelty-free” to the term “fair trade.” There is an independent inspection and certification group (Flo-Cert) that reviews products labeled as “fair trade,” but there’s no analogous process for “cruelty-free” (2). Companies can also hire outside firms to test products and ingredients on animals (3). | → So anyone can just put that label on a product? Apparently, apart from in the European Union. That seems really easy to abuse for marketing purposes. |
| Andrew Knight. “Critically Evaluating Animal Research.” In . Brill 2019. | Knight cites “significant methodological flaws” in “most published animal experiments” (326). For example, “randomized allocation of animals to test groups was reported in only 12%” of a set of 271 studies—in the rest of the studies, researchers could select (whether consciously or not) weaker animals to serve as the control group, for example (326). Similarly, only 14% of papers in a different survey reported the use of blinding in making qualitative assessments of outcomes (327). The ARRIVE guidelines have been widely endorsed by leading research journals (including Nature, PLoS, and BioMed Central) and major UK funding agencies, and they’re part of the US National Research Council Institute for Laboratory Animal Research guidelines (330). But…compliance with the guidelines “remains poor” (330). | → Many people championing or opposing animal testing have their careers at stake. They’re either researchers who use animals as a fundamental part of their research, or they are working on alternatives to animal testing (like Harding). This seems like a potential problem with the debate. → So one way to improve the methodological quality of studies would be to encourage (or regulate) randomization and blinded assessment of outcomes. |
| (continued) Andrew Knight. “Critically Evaluating Animal Research.” In . Brill 2019. | Knight advocates that compliance with the ARRIVE guidelines and other standards “must become mandatory,” and that “compliance with such standards should be a necessary condition for security research funding and ethical approval; licensing of researchers, facilities, and experimental protocols; and publication of subsequent results” (331). Knight also argues that “prior to designing any new animal study, researchers should conduct a systematic review to collate, appraise, and synthesize all existing, good-quality evidence relating to their research questions,” and that this step should also be required by grant agencies, licensing bodies, and journals (332). He notes that systematic reviews are really helpful and should be funded more frequently (332). The article then covers impacts on laboratory animals—invasive procedures, stress, pain, and death (333). These aren’t very widely or clearly reported (333). | → This seems like a reasonable position. What would there be to lose from requiring compliance with these guidelines? I suppose it could make research more difficult or expensive to conduct—but probably it would weed out some bad research. → Good to remember that research requires money and is shaped by market forces—it’s not some neutral thing happening in an ivory tower. |
Grab our download to read the rest of the notes and see more examples of how to do thoughtful research!

4. Create a thesis
What major themes did you find in your reading? What did you find most interesting or convincing?
Now is the point when you need to pick a side on your topic, if you haven’t already done so. Now that you’ve read more about the issue, what do you think? Write down your position on the issue:
Animal testing is necessary but should be reduced.
Next, it’s time to add more detail to your thesis. What reasons do you have to support that position? Add those to your sentence.
Animal testing is necessary but should be reduced by eliminating testing for cosmetics, ensuring that any testing is scientifically sound, and replacing animal models with other methods as much as possible.
Add qualifiers to refine your position. Are there situations in which your position would not apply? Or are there other conditions that need to be met?
For our topic of animal research, our final thesis statement (with lead-in) might look something like this:
The argument: Animal testing and research should not be abolished, as doing so would upend important medical research and substance testing. However, scientific advances mean that in many situations animal testing can be replaced by other methods that not only avoid the ethical problems of animal testing, but also are less costly and more accurate. Governments and other regulatory bodies should further regulate animal testing to outlaw testing for cosmetics and other recreational products, ensure that the tests conducted are both necessary and scientifically rigorous, and encourage the replacement of animal use with other methods whenever possible.
The highlighted bit at the end is the thesis statement, but the lead-in is useful to help us set up the argument—and having it there already will make writing our introduction easier!
The thesis statement is the single most important sentence of your essay. Without a strong thesis, there’s no chance of writing a great essay. Read more about it here .
See how nine real students wrote great thesis statements in 9 example essays now.
5. Create three supporting arguments
Think of three good arguments why your position is true. We’re going to make each one into a body paragraph of your essay.
For now, write them out as 1–2 sentences. These will be topic sentences for each body paragraph.

For our essay about animal testing, it might look like this:
Supporting argument #1: For ethical reasons, animal testing should not be allowed for cosmetics and recreational products.
Supporting argument #2: The tests that are conducted with animals should be both necessary (for the greater good) and scientifically rigorous—which isn’t always the case currently. This should be regulated by governments and institutions.
Supporting argument #3: Governments and institutions should do more to encourage the replacement of animal testing with other methods.
Optional: Find a counterargument and respond to it
Think of a potential counterargument to your position. Consider writing a fourth paragraph anticipating this counterargument, or find a way to include it in your other body paragraphs.

For our essay, that might be:
Possible counterargument: Animal testing is unethical and should not be used in any circumstances.
Response to the counterargument: Animal testing is deeply entrenched in many research projects and medical procedures. Abruptly ceasing animal testing would upend the scientific and medical communities. But there are many ways that animal testing could be reduced.
With these three arguments, a counterargument, and a thesis, we now have a skeleton outline! See each step of this essay in full in our handy download .
6. Start populating your outline with the evidence you found in your research
Look through your research. What did you find that would support each of your three arguments?
Copy and paste those quotes or paraphrases into the outline. Make sure that each one is annotated so that you know which source it came from!
Ideally you already started thinking about these sources when you were doing your research—that’s the ideas in the rightmost column of our research template. Use this stuff too!
A good rule of thumb would be to use at least three pieces of evidence per body paragraph.
Think about in what order it would make most sense to present your points. Rearrange your quotes accordingly! As you reorder them, feel free to start adding short sentences indicating the flow of ideas .

For our essay about animal testing, part of our populated outline might look something like:
Argument #1: For ethical reasons, animal testing should not be allowed for cosmetics and recreational products.
Lots of animals are used for testing and research.
In the US, about 22 million animals were used annually in the early 1990s, mostly rodents (BMJ 1993, 1020).
But there are ethical problems with using animals in laboratory settings. Opinions about the divide between humans and animals might be shifting.
McIsaac refers to “the essential moral dilemma: how to balance the welfare of humans with the welfare of other species” (Hubel, McIsaac 29).
The fundamental legal texts used to justify animal use in biomedical research were created after WWII, and drew a clear line between experiments on animals and on humans. The Nuremburg Code states that “the experiment should be so designed and based on the results of animal experimentation and a knowledge of the natural history of the disease or other problem under study that the anticipated results will justify the performance of the experiment” (Ferrari, 197). The 1964 Declaration of the World Medical Association on the Ethical Principles for Medical Research Involving Human Subjects (known as the Helsinki Declaration) states that “Medical research involving human subjects must conform to generally accepted scientific principles, be based on a thorough knowledge of the scientific literature, other relevant sources of information, and adequate laboratory and, as appropriate, animal experimentation. The welfare of animals used for research must be respected” (Ferrari, 197).
→ Context? The Nuremberg Code is a set of ethical research principles, developed in 1947 in the wake of Nazi atrocities during WWII, specifically the inhumane and often fatal experimentation on human subjects without consent.
“Since the 1970s, the animal-rights movement has challenged the use of animals in modern Western society by rejecting the idea of dominion of human beings over nature and animals and stressing the intrinsic value and rights of individual animals” (van Roten, 539, referencing works by Singer, Clark, Regan, and Jasper and Nelkin).
“The old (animal) model simply does not fully meet the needs of scientific and economic progress; it fails in cost, speed, level of detail of understanding, and human relevance. On top of this, animal experimentation lacks acceptance by an ethically evolving society” (Hartung, 682).
Knight’s article summarizes negative impacts on laboratory animals—invasive procedures, stress, pain, and death (Knight, 333). These aren’t very widely or clearly reported (Knight, 333). → Reading about these definitely produces an emotional reaction—they sound bad.
Given this context, it makes sense to ban animal testing in situations where it’s just for recreational products like cosmetics.
Fortunately, animal testing for cosmetics is less common than we might think.
A Gallup poll published in 1990 found that 14% of people thought that the most frequent reason for using animals to test cosmetics for safety—but figures from the UK Home Office in 1991 found that less than 1% of animals were used for tests for cosmetics and toiletries (BMJ 1993, 1019). → So in the early 1990s there was a big difference between what people thought was happening and what actually was happening!
But it still happens, and there are very few regulations of it (apart from in the EU).
Because there are many definitions of the phrase “cruelty-free,” many companies “can (and do) use the term when the product or its ingredients were indeed tested on animals” (Sheehan and Lee, 1).
The authors compare “cruelty-free” to the term “fair trade.” There is an independent inspection and certification group (Flo-Cert) that reviews products labeled as “fair trade,” but there’s no analogous process for “cruelty-free” (Sheehan and Lee, 2). → So anyone can just put that label on a product? Apparently, apart from in the European Union. That seems really easy to abuse for marketing purposes.
Companies can also hire outside firms to test products and ingredients on animals (Sheehan and Lee, 3).
Animal testing for recreational, non-medical purposes should be banned, like it is in the EU.
Download the full example outline here .

7. Do more research if necessary
Occasionally you might realize that there’s a hole in your research, and you don’t have enough evidence to support one of your points.
In this situation, either change your argument to fit the evidence that you do have, or do a bit more research to fill the hole!
For example, looking at our outline for argument #1 for our essay on animal testing, it’s clear that this paragraph is missing a small but crucial bit of evidence—a reference to this specific ban on animal testing for cosmetics in Europe. Time for a bit more research!
A visit to the official website of the European Commission yields a copy of the law, which we can add to our populated outline:
“The cosmetics directive provides the regulatory framework for the phasing out of animal testing for cosmetics purposes. Specifically, it establishes (1) a testing ban – prohibition to test finished cosmetic products and cosmetic ingredients on animals, and (2) a marketing ban – prohibition to market finished cosmetic products and ingredients in the EU which were tested on animals. The same provisions are contained in the cosmetics regulation , which replaced the cosmetics directive as of 11 July 2013. The testing ban on finished cosmetic products applies since 11 September 2004. The testing ban on ingredients or combination of ingredients applies since 11 March 2009. The marketing ban applies since 11 March 2009 for all human health effects with the exception of repeated-dose toxicity, reproductive toxicity, and toxicokinetics. For these specific health effects, the marketing ban applies since 11 March 2013, irrespective of the availability of alternative non-animal tests.” (website of the European Commission, “Ban on animal testing”)
Alright, now this supporting argument has the necessary ingredients!
You don’t need to use all of the evidence that you found in your research. In fact, you probably won’t use all of it!
This part of the writing process requires you to think critically about your arguments and what evidence is relevant to your points .

8. Add your own analysis and synthesis of these points
Once you’ve organized your evidence and decided what you want to use for your essay, now you get to start adding your own analysis!
You may have already started synthesizing and evaluating your sources when you were doing your research (the stuff on the right-hand side of our template). This gives you a great starting place!
For each piece of evidence, follow this formula:
- Context and transitions: introduce your piece of evidence and any relevant background info and signal the logical flow of ideas
- Reproduce the paraphrase or direct quote (with citation )
- Explanation : explain what the quote/paraphrase means in your own words
- Analysis : analyze how this piece of evidence proves your thesis
- Relate it back to the thesis: don’t forget to relate this point back to your overarching thesis!
If you follow this fool-proof formula as you write, you will create clear, well-evidenced arguments.
As you get more experienced, you might stray a bit from the formula—but a good essay will always intermix evidence with explanation and analysis, and will always contain signposts back to the thesis throughout.
For our essay about animal testing, our first body paragraph might look like:
Every year, millions of animals—mostly rodents—are used for testing and research (BMJ 1993, 1020) . This testing poses an ethical dilemma: “how to balance the welfare of humans with the welfare of other species” (Hubel, McIsaac 29) . Many of the fundamental legal tests that are used to justify animal use in biomedical research were created in wake of the horrors of World War II, when the Nazi regime engaged in terrible experimentation on their human prisoners. In response to these atrocities, philosophers and lawmakers drew a clear line between experimenting on humans without consent and experimenting on (non-human) animals. For example, the 1947 Nuremberg Code stated that “the experiment should be so designed and based on the results of animal experimentation and a knowledge of the natural history of the disease or other problem under study that the anticipated results will justify the performance of the experiment” (Ferrari, 197) . Created two years after the war, the code established a set of ethical research principles to demarcate ethical differences between animals and humans, clarifying differences between Nazi atrocities and more everyday research practices. However, in the following decades, the animal-rights movement has challenged the philosophical boundaries between humans and animals and questioned humanity’s right to exert dominion over animals (van Roten, 539, referencing works by Singer, Clark, Regan, and Jasper and Nelkin) . These concerns are not without justification, as animals used in laboratories are subject to invasive procedures, stress, pain, and death (Knight, 333) . Indeed, reading detailed descriptions of this research can be difficult to stomach . In light of this, while some animal testing that contributes to vital medical research and ultimately saves millions of lives may be ethically justified, animal testing that is purely for recreational purposes like cosmetics cannot be ethically justified . Fortunately, animal testing for cosmetics is less common than we might think . In 1990, a poll found that 14% of people in the UK thought that the most frequent reason for using animals to test cosmetics for safety—but actual figures were less than 1% (BMJ 1993, 1019) . Unfortunately, animal testing for cosmetics is not subject to very much regulation . In particular, companies can use the phrase “cruelty-free” to mean just about anything, and many companies “can (and do) use the term when the product or its ingredients were indeed tested on animals” (Sheehan and Lee, 1) . Unlike the term “fair trade,” which has an independent inspection and certification group (Flo-Cert) that reviews products using the label, there’s no analogous process for “cruelty-free” (Sheehan and Lee, 2) . Without regulation, the term is regularly abused by marketers . Companies can also hire outside firms to test products and ingredients on animals and thereby pass the blame (Sheehan and Lee, 3) . Consumers trying to avoid products tested on animals are frequently tricked . Greater regulation of terms would help, but the only way to end this kind of deceit will be to ban animal testing for recreational, non-medical purposes . The European Union is the only governmental body yet to accomplish this . In a series of regulations, the EU first banned testing finished cosmetic products (2004), then testing ingredients or marketing products which were tested on animals (2009); exceptions for specific health effects ended in 2013 (website of the European Commission, “Ban on animal testing”) . The result is that the EU bans testing cosmetic ingredients or finished cosmetic products on animals, as well as marketing any cosmetic ingredients and products which were tested on animals elsewhere (Regulation 1223/2009/EU, known as the “Cosmetics Regulation”) . The rest of the world should follow this example and ban animal testing on cosmetic ingredients and products, which do not contribute significantly to the greater good and therefore cannot outweigh the cost to animal lives .
Edit down the quotes/paraphrases as you go. In many cases, you might copy out a great long quote from a source…but only end up using a few words of it as a direct quote, or you might only paraphrase it!
There were several good quotes in our previous step that just didn’t end up fitting here. That’s fine!
Take a look at the words and phrases highlighted in red. Notice how sometimes a single word can help to provide necessary context and create a logical transition for a new idea. Don’t forget the transitions! These words and phrases are essential to good writing.
The end of the paragraph should very clearly tie back to the thesis statement.
As you write, consider your audience
If it’s not specified in your assignment prompt, it’s always appropriate to ask your instructor who the intended audience of your essay or paper might be. (Your instructor will usually be impressed by this question!)
If you don’t get any specific guidance, imagine that your audience is the typical readership of a newspaper like the New York Times —people who are generally educated, but who don’t have any specialized knowledge of the specific subject, especially if it’s more technical.
That means that you should explain any words or phrases that aren’t everyday terminology!
Equally important, you don’t want to leave logical leaps for your readers to make. Connect all of the dots for them!
See the other body paragraphs of this essay, along with 9 student essays, here .
9. Add paragraph transitions and concluding sentences to each body paragraph
By now you should have at least three strong body paragraphs, each one with 3–5 pieces of evidence plus your own analysis and synthesis of the evidence.
Each paragraph has a main topic sentence, which we wrote back when we made the outline. This is a good time to check that the topic sentences still match what the rest of the paragraph says!
Think about how these arguments relate to each other. What is the most logical order for them? Re-order your paragraphs if necessary.
Then add a few sentences at the end of each paragraph and/or the beginning of the next paragraph to connect these ideas. This step is often the difference between an okay essay and a really great one!
You want your essay to have a great flow. We didn’t worry about this at the beginning of our writing, but now is the time to start improving the flow of ideas!
10. The final additions: write an introduction and a conclusion
Follow this formula to write a great introduction:
- It begins with some kind of “hook”: this can be an anecdote, quote, statistic, provocative statement, question, etc.
(Pro tip: don’t use phrases like “throughout history,” “since the dawn of humankind,” etc. It’s good to think broadly, but you don’t have to make generalizations for all of history.)
- It gives some background information that is relevant to understand the ethical dilemma or debate
- It has a lead-up to the thesis
- At the end of the introduction, the thesis is clearly stated
This makes a smooth funnel that starts more broadly and smoothly zeroes in on the specific argument.

Your conclusion is kind of like your introduction, but in reverse. It starts with your thesis and ends a little more broadly.
For the conclusion, try and summarize your entire argument without being redundant. Start by restating your thesis but with slightly different wording . Then summarize each of your main points.
If you can, it’s nice to point to the larger significance of the issue. What are the potential consequences of this issue? What are some future directions for it to go in? What remains to be explored?
See how nine students wrote introductions in different styles here .
11. Add citations and bibliography
Check what bibliographic style your instructor wants you to use. If this isn’t clearly stated, it’s a good question to ask them!
Typically the instructions will say something like “Chicago style,” “APA,” etc., or they’ll give you their own rules.
These rules will dictate how exactly you’ll write your citations in the body of your essay (either in parentheses after the quote/paraphrase or else with a footnote or endnote) and how you’ll write your “works cited” with the full bibliographic information at the end.
Follow these rules! The most important thing is to be consistent and clear.
Pro tip: if you’re struggling with this step, your librarians can often help! They’re literally pros at this. 🙂
Now you have a complete draft!
Read it from beginning to end. Does it make sense? Are there any orphan quotes or paraphrases that aren’t clearly explained? Are there any abrupt changes of topic? Fix it!
Are there any problems with grammar or spelling ? Fix them!
Edit for clarity.

Ideally, you’ll finish your draft at least a few days before it’s due to be submitted. Give it a break for a day or two, and then come back to it. Things to be revised are more likely to jump out after a little break!
Try reading your essay out loud. Are there any sentences that don’t sound quite right? Rewrite them!
Double-check your thesis statement. This is the make-or-break moment of your essay, and without a clear thesis it’s pretty impossible for an essay to be a great one. Is it:
- Arguable: it’s not just the facts—someone could disagree with this position
- Narrow & specific: don’t pick a position that’s so broad you could never back it up
- Complex: show that you are thinking deeply—one way to do this is to consider objections/qualifiers in your thesis
Try giving your essay to a friend or family member to read. Sometimes (if you’re lucky) your instructors will offer to read a draft if you turn it in early. What feedback do they have? Edit accordingly!
See the result of this process with 10 example essays now .
You’re done!
You did it! Feel proud of yourself 🙂
We regularly help students work through all of these steps to write great academic essays in our Academic Writing Workshop or our one-on-one writing tutoring . We’re happy to chat more about what’s challenging for you and provide you customized guidance to help you write better papers and improve your grades on writing assignments!
Want to see what this looks like when it’s all pulled together? We compiled nine examples of great student essays, plus all of the steps used to create this model essay, in this handy resource. Download it here !

Emily graduated summa cum laude from Princeton University and holds an MA from the University of Notre Dame. She was a National Merit Scholar and has won numerous academic prizes and fellowships. A veteran of the publishing industry, she has helped professors at Harvard, Yale, and Princeton revise their books and articles. Over the last decade, Emily has successfully mentored hundreds of students in all aspects of the college admissions process, including the SAT, ACT, and college application essay.
Privacy Preference Center
Privacy preferences.

In order to continue enjoying our site, we ask that you confirm your identity as a human. Thank you very much for your cooperation.
Argumentative essay characteristics structure and Language marks
Argumentative essay
An argumentative essay is a free topic text whose objective is to convince or persuade the reader of the ideas presented. Its purpose is to incite in the reader an inclination towards the author’s opinion. In other words , an argumentative essay will always contain elements of an expository essay, since it needs to explain its position on a certain problem or topic. The author, through coherently exposed concepts, will try to justify and demonstrate his reasons. Argumentative essay characteristics structure
Arguing is that, defending the ideas that have been exposed in the essay in a logical and orderly way. The author can even present contrary premises to dismantle them with his reasons, and give more force to his argument.
What is important about this type of essay is the author’s point of view, and the way in which he approaches the argument. They are usually of an academic nature and free subject , as already said, since they reflect the personal opinion of the author, where he tries to demonstrate their validity.
In any case, regardless of whether or not it manages to convince the reader, the argumentative essay will be a starting point to reflect on a topic.
Characteristics of the argumentative essay
An argumentative essay shares a literary language with other types of essay, and in that sense uses metaphors and other rhetorical figures to validate its thesis. It is a space where the subjectivity of the issuer fits , but also conceptual rigor.
In general, an argumentative essay has the following characteristics:
1-Point of view
The author’s point of view is presented in the introduction to the essay , through the thesis with which he adheres.
The analysis is an indissoluble part of the argument, since by contrasting ideas or contrasting the advantages and disadvantages, pros and cons of positions, the author gradually unravels why he assumes a certain position.
Language marks in the argumentative essay
In the argumentative essay, various literary resources can be used:
1-Connectors
It uses various argumentative connectors : to start the text, to add new ideas, include examples, draw conclusions, compare, contrast and finish.
- To begin the text, the connectors used are, for example: First of all, To begin, The idea of this essay, What we present… and the like.
- To add ideas and give them order, the following are used: Likewise, In this sense, On the other hand, In other words …, and to exemplify: For example, In fact, Specifically, etc.
- For the conclusions, the following are used: In other words , In conclusion, In short, In short.
- The comparison connectors : Likewise, Likewise, Likewise, Likewise, etc .; those of contrast: On the contrary, As opposed to. And to finish: Finally, Finally, To summarize, etc.
2-Qualifications and designations
Throughout the text, the author will rely on expressions that qualify and designate what he is arguing. An example would be: Argumentative essay characteristics structure
“A conservationist attitude is necessary on the part of all humanity to face a possible environmental catastrophe. The idea is that we can live together on the same planet ”.
3-Formal use of language
An essay is a literary text, and in that sense, the author will use careful language, respecting the grammatical rules and avoiding colloquialisms as much as possible that can make understanding difficult. That does not prevent the language from being close.
4-Coherence
From start to finish, the argumentative essay must present an internal coherence between the ideas. That is, you must respect an order when presenting the arguments, so that the reader can follow the reasoning.
What is an argumentative essay for?
In principle, an argumentative essay serves to convince readers of the thesis presented by the author. The essay, by definition, is a text that establishes a theme and reflects on it. Many times the subject discussed generates controversy, and hence the author argues in favor of his thesis.
And although it is the opinion of the author, in an argumentative essay what is important are the foundations it exposes, it is the way in which the issuer, in addition to informing the reader, reasons on the subject and supports his reasons.
This is how you can convince, by showing that your point of view is correct. It is not enough to argue, you must back it up with figures, quotes and other information , always saying where you got it from.
Structure of an argumentative essay
An argumentative essay has a similar structure to other types of essay: introduction, development or arguments and conclusion .
1-Introduction
In the introduction, the author will explain what the essay is about. It will do so in a way that engages the reader to keep reading . Apart from pointing out the general theme , it will also indicate which party is going to argue, whether it is for or against, and why.
2-Development or arguments
It is the body of the essay . The arguments are presented in paragraphs ; if there is more than one, ideally each paragraph corresponds to one argument. In any case, they must be very clear and explain precisely the reasoning, so as not to lose the reader.
There are one-page argumentative essays, and others that can be a complete book. It does not matter, the important thing is the clarity with which it is argued.
You can even present a rebuttal that offers ideas contrary to your thesis, and the author will counter-argue to demonstrate the validity of his reasons. It is a resource that many authors use to defend their ideas.
You have to start with the most important argument and end with the one that has less relevance, that indicates an order , determined by the author. Argumentative essay characteristics structure
3-Conclusion
In the conclusion, the author highlights the topic again but in the light of a larger context, showing the reader that thanks to his argumentation , understanding and opinion should change after reading.
A mistake that is made often, especially in writing thesis, is introducing new arguments. The conclusion should close the issue, not open a new controversy.
Taking into account that the essay is only a contribution, it is good to recognize and guide (in any case) the possible investigations that others want to carry out, starting from that initial reading .
How to do an argumentative essay step by step
1-choice of theme.
To write an argumentative essay, you must first select a topic about which you have knowledge or about which you feel some inclination.
Suppose we want to write about the effect that happiness (or feeling happy) has on the body and overall health. It interests us from a physiological point of view. So we would already have a tentative topic: “The effect of happiness on the body.”
2-Be documented
Although we have an idea on the subject , it is necessary to document as much as possible, to inquire in various sources. We must remember that, although we present a personal opinion, if we want to argue it must be with reasons, in this case, scientific.
What substances are produced in the brain when we feel happy? Can happiness be a constant state? Is it possible to feel happy even when you are going through difficulties? Is it possible to stay healthy by being happy?
By virtue of these questions , we will search for information, and for this we will resort to legitimate sources (neurological, psychological, scientific studies) that support our thesis.
The above questions can serve as a skeleton to order the preparation of the essay.
When we have the ideas in order , we will proceed to write a first draft, which will further define the topics to be discussed.
You have to be consistent: develop ideas in a logical way. That also means structuring the sentences logically, and then the paragraphs . If our thesis is that happiness has a specific effect on the body, we will have to argue step by step. Argumentative essay characteristics structure
For example, to establish the existence of hormones produced in the brain (endorphins) when the person feels good and happy, and also, the existence of substances that are toxic when the person is stressed, angry, sad or worried, which also produces the brain.
If the person becomes ill with these toxic substances, it is possible to think that benevolent substances can also heal the body. Hence, then, the importance of properly managing stress would be highlighted to prevent toxicity from deteriorating health.
The coherence of the essay , linguistic and stylistic cohesion, the succession of ideas and arguments, syntax and spelling will be thoroughly reviewed. If it is noticed that there is some “jump” in the order of the ideas, then it will be necessary to correct it.
It is advisable to make the initial outline and follow it, although it can be modified in the course of writing and review.
Example of argumentative essay
Next, we present an argumentative essay whose title is “To conserve the environment is to conserve human life on Earth.” To facilitate understanding, the beginning, development and conclusion are indicated.
In recent years, the environment has been the subject of discussion in several international meetings, where the most powerful powers in the world have come together to try to reach agreements that involve the most industrialized countries and those that pollute the most.
2-Development and arguments
Interestingly, the nations that pollute the most are currently the two strongest economic powers, China and the United States , followed by the European Union, India, Russia and Japan.
The objectives of these international agreements are to fight against global warming and climate change, and for this they agreed to reduce greenhouse gas emissions , since it is calculated that they are the cause of the increase in temperature on Earth.
China, which until at least 10 years ago did not seem to care about the pollution of its cities, has been one of the most important actors in the ratification of the Kyoto Protocol and the Paris Agreement , and at present, it is one of the countries that carry out large-scale production of infrastructure for the transition to solar energy and other renewable sources. Apparently, the Asian giant has understood the risks of climate change. Argumentative essay characteristics structure
However, the United States , one of the most powerful countries in the world, left these agreements after the arrival of Donald Trump to the presidency, claiming that they are a brake on the economic growth of his country.
It also alleges that the studies on climate change are not conclusive, and that it is more economical to continue exploiting coal mines and oil fields than to invest in energy production based on clean sources.
The immediate stance of the North American president is obvious, as well as the irresponsibility in discarding all the scientific work carried out by thousands of professionals, such as biologists, geologists, ecologists, who account for environmental deterioration.
If the temperature of the planet continues to rise, it will affect the ecological balance, from plants to larger animals , including humans.
Little by little the viability of human life will be restricted, the progressive desertification of the lands will cause the rivers to dry up. Water will be lacking, and what are we without water? Water is life, without water there is none: it is a simple equation. And if we talk about the pollution of the oceans, the problem goes on and on.
It is necessary to assume a proactive and responsible attitude in the conservation of the environment. It concerns us all equally, no country will be saved if we go to extinction. So both nations and individuals must take action on the matter.
It is not about believing or not in climate change. Climate change doesn’t make tornadoes, but it does make them stronger and more intense; it causes unforeseen floods, polar ice melts, species disappear.
In a century we have done what nature has not done in millions of years: destroy the conditions for human life to exist. If we want to continue living on Earth with water , food and air to breathe, we must make changes. Argumentative essay characteristics structure
The planet will go on without us. We can’t go on without him.
Related Articles
Types of languages in english with characteristics, persuasive speech characteristics and examples, popular texts characteristics and types with examples.

Individual communication characteristics types examples
Leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Please input characters displayed above.
Essay Papers Writing Online
Why argumentative essay writers should be your go-to choice for persuasive and compelling content.

In the world of academic writing, the proficiency in crafting powerful argumentative essays holds immense value. However, being an accomplished writer in this genre requires more than just basic skills and knowledge. It demands a unique set of attributes that can captivate the reader’s attention and convey your message persuasively. Whether you are a novice or an experienced writer aiming to enhance your abilities, understanding the skills and characteristics essential to become a successful argumentative essay author can make a significant difference in your writing prowess.
Plan for Promoting a Product or Service

In this section, we will discuss the strategy and steps involved in promoting a product or service effectively. Advertising plays a crucial role in attracting potential customers and increasing sales. A well-executed promotional plan can enhance brand recognition, build customer loyalty, and drive business growth.
One of the key components of a successful promotion plan is identifying the target audience. Understanding the demographics, interests, and needs of the target market helps in tailor-making the promotional message and selecting the most effective marketing channels. Conducting market research, surveys, and analyzing customer data can provide valuable insights into the target audience and their preferences.
Another important aspect of promoting a product or service is choosing the right marketing channels. The advent of digital marketing has opened up numerous avenues for reaching the target audience. Social media platforms, search engine advertising, email marketing, content marketing, and influencer collaborations are some of the popular channels that can be utilized. Developing a multi-channel approach ensures wide coverage and maximizes the chances of reaching the target audience.
Creating compelling content is essential for capturing the attention of potential customers. Engaging and informative content that showcases the unique selling points of the product or service can generate interest and create a desire to learn more. Utilizing engaging visuals, persuasive copywriting, and storytelling techniques can make the promotional message stand out in a crowded market.
Building relationships with customers is crucial for long-term success. Offering personalized experiences, excellent customer service, and loyalty programs can foster a sense of loyalty and encourage repeat purchases. Word-of-mouth recommendations and positive reviews from satisfied customers can also play a significant role in promoting the product or service further.
| Steps for Promoting a Product or Service |
|---|
| 1. Identify the target audience |
| 2. Research and analyze the market |
| 3. Choose the appropriate marketing channels |
| 4. Create compelling content |
| 5. Build relationships with customers |
By following these steps and implementing a well-thought-out promotional plan, businesses can effectively market their products or services, increase brand visibility, and achieve their sales objectives.
Identify target audience
Understanding your audience is crucial for any writer, as it helps you tailor your message to effectively communicate and engage with them. When it comes to argumentative essays, identifying your target audience is equally important.
Knowing who your target audience is will help you determine the language, tone, and style of your essay. It will also help you choose the most persuasive arguments and evidence that will resonate with them. Identifying your target audience allows you to speak directly to their needs, interests, and concerns, making your essay more compelling and persuasive.
However, identifying your target audience in argumentative writing is not as simple as just categorizing them by demographics such as age, gender, or location. It goes beyond superficial characteristics and delves deeper into their values, beliefs, and attitudes. Understanding the mindset of your target audience will enable you to anticipate their potential objections and address them effectively, strengthening your argument and increasing your chances of persuading them.
Moreover, identifying your target audience also helps you determine the level of prior knowledge and understanding they have on the topic. This knowledge gap will shape the level of complexity and depth of your arguments and evidence. Whether your target audience is already familiar with the topic or completely new to it, tailoring your essay to their level of expertise will make your arguments more relatable and accessible.
In conclusion, identifying your target audience is a crucial step in crafting a successful argumentative essay. Understanding their values, beliefs, and knowledge level allows you to tailor your message to resonate with them, increasing your chances of persuading them. By taking the time to identify your target audience, you can create a more compelling and persuasive essay that effectively communicates your arguments.
Conduct market research
When it comes to being a successful writer, it’s important to have a deep understanding of your audience and their needs. Conducting market research can help you gain valuable insights into your target market, allowing you to tailor your arguments and writing style to meet their expectations.
Market research involves gathering and analyzing data about your target audience, including their demographics, preferences, and behaviors. This information can help you identify trends, patterns, and gaps in the market, which you can then use to inform your argumentative essay writing.
- Identify your target audience: Start by identifying the specific group of people you want to reach with your argumentative essay. Consider factors such as age, gender, occupation, education level, and interests.
- Collect data: Once you have identified your target audience, gather relevant data about them. This can be done through surveys, interviews, focus groups, or analyzing existing research and studies.
- Analyze the data: Once you have collected the data, analyze it to identify key insights and trends. Look for common themes, preferences, and behaviors that can help you understand your audience better.
- Identify gaps in the market: By analyzing the data, you may discover gaps or unmet needs in the market. This can present opportunities for you to position your argumentative essay in a unique and compelling way.
- Refine your arguments: Armed with the insights from your market research, you can now refine your arguments to better resonate with your target audience. Tailor your writing style, tone, and language to align with their preferences and interests.
Conducting market research is an ongoing process that can help you stay relevant and effective as an argumentative essay writer. By understanding your audience and their needs, you can create persuasive and compelling essays that have a greater impact.
Develop a unique selling proposition (USP)
When it comes to being a skilled and successful writer of persuasive essays, it is important to have more than just the necessary skills and characteristics. It is crucial to develop a unique selling proposition (USP) that sets you apart from other writers in the field.
A USP is a statement that highlights what makes you different and why clients and readers should choose you over others. It is a combination of your strengths, expertise, and unique approach to argumentative essay writing.
One way to develop your USP is by showcasing your ability to craft compelling arguments that resonate with readers. It is not enough to simply present facts and evidence. A successful argumentative essay writer goes beyond surface-level analysis and delves deep into the nuances of the topic, presenting thought-provoking insights that challenge commonly held beliefs.
Additionally, it is crucial to emphasize your ability to tailor your writing style and tone to suit the specific needs and preferences of your targeted audience. Whether you are writing for academics, professionals, or general readers, being able to adapt your writing to their level of understanding and engagement can make a significant difference in the impact of your essays.
Furthermore, your USP should highlight your commitment to thorough research and impeccable fact-checking. In an era of misinformation and fake news, being a reliable source of accurate information is a valuable asset. This can be achieved by citing reputable sources, conducting in-depth research, and presenting a well-supported argument that is grounded in evidence.
In conclusion, developing a unique selling proposition (USP) is crucial for becoming a successful argumentative essay writer. By showcasing your ability to craft compelling arguments, tailoring your writing style to your audience, and emphasizing your commitment to research and accuracy, you can differentiate yourself and attract clients and readers who value quality and expertise.
Create compelling content
When it comes to crafting an engaging and persuasive piece of writing, the ability to create captivating content is crucial. The art of producing compelling material lies in the writer’s skill to present information in an interesting and persuasive manner. By employing appealing language, captivating storytelling techniques, and well-researched supporting evidence, a writer can ensure that their content resonates with their target audience, making it more likely to be influential and convincing.
Utilize social media marketing
In today’s digital era, social media has become an essential tool for businesses to connect and engage with their target audience. By harnessing the power of social media marketing, companies can effectively promote their products or services, build brand awareness, and drive customer engagement.
Social media platforms such as Facebook, Twitter, Instagram, and LinkedIn offer businesses various opportunities to reach a wider audience and establish a strong online presence. Through strategic content creation and targeted advertising campaigns, companies can effectively communicate their value proposition and attract potential customers.
One of the key advantages of utilizing social media marketing is its cost-effectiveness compared to traditional marketing methods. By leveraging social media platforms, businesses can reach a large number of potential customers at a fraction of the cost, making it an ideal channel for startups and small businesses with limited marketing budgets.
In addition, social media marketing allows businesses to gather valuable insights about their target audience through analytics and feedback. By analyzing user behavior, engagement metrics, and customer feedback, companies can refine their marketing strategies, tailor their messaging, and optimize their campaigns for better results.
Furthermore, social media marketing enables businesses to foster a sense of community and loyalty among their customers. By regularly interacting with followers, responding to their comments and messages, and sharing valuable content, companies can build trust, enhance customer relationships, and encourage brand advocacy.
In conclusion, social media marketing is a powerful tool that businesses can utilize to effectively promote their products or services, reach a wider audience, and drive engagement. By incorporating social media into their marketing strategies, companies can stay ahead of the competition and establish a strong online presence in today’s digital landscape.
Implement email marketing campaigns
One of the essential strategies to promote a product or service effectively is to implement email marketing campaigns. This approach allows businesses to reach out to their target audience directly and communicate their message efficiently. By utilizing email marketing, companies can build customer relationships, increase brand awareness, and drive conversions.
Creating an effective email marketing campaign requires careful planning and execution. The first step is to develop a comprehensive email list of interested recipients. This can be achieved by using various methods, such as offering incentives for signing up, including opt-in forms on websites, or collecting email addresses at events or trade shows.
Once the email list is established, the next step is to create compelling and engaging content for the email campaign. This content should be tailored to the target audience and should include a clear call to action. Whether it is promoting a new product, announcing a sale, or sharing valuable information, the content should provide value to the recipients and encourage them to take action.
In addition to the content, the design and layout of the email should be visually appealing and consistent with the brand image. Using professional email templates or hiring a graphic designer can help ensure that the emails look polished and reflect the company’s branding guidelines.
After the email content and design are finalized, it is crucial to test the email before sending it out to the entire email list. This includes checking for any errors or broken links, as well as ensuring the email displays correctly on different devices and email clients. Testing the email allows for any necessary adjustments to be made before it is sent to the recipients.
Once the email is sent, it is important to track and analyze the results of the campaign. This can be done by monitoring open rates, click-through rates, and conversion rates. By analyzing this data, businesses can gain insights into the effectiveness of their email marketing campaigns and make informed decisions for future improvements.
In conclusion, implementing email marketing campaigns is a powerful tool for promoting products or services. By carefully planning and executing email campaigns, businesses can effectively communicate with their target audience and achieve their marketing goals.
Track and analyze results
Once you have mastered the skills and characteristics necessary to become a successful argumentative essay writer, it is essential to track and analyze the results of your work. This allows you to gain valuable insights into the effectiveness of your writing techniques and make improvements as needed.
Tracking the results of your argumentative essays involves keeping a record of various metrics such as the number of views, comments, and shares that your essays receive. By monitoring these metrics, you can determine the level of engagement and interest that your writing generates among readers.
Analyzing the results of your argumentative essays involves examining the data you have collected and identifying patterns and trends. This analysis can help you identify the strengths and weaknesses of your writing, allowing you to refine your skills and develop a more effective approach to crafting compelling arguments.
One effective way to track and analyze the results of your argumentative essays is to create a spreadsheet or use an online tool that allows you to log the relevant metrics. By regularly updating this log and reviewing the data, you can gain a better understanding of which topics, arguments, or writing styles resonate most with your audience.
Additionally, it can be beneficial to seek feedback from your readers or peers. Encourage them to provide their thoughts and opinions on your argumentative essays, as their insights can provide valuable perspectives and suggestions for improvement.
Overall, tracking and analyzing the results of your argumentative essays is an essential step in the ongoing development of your writing skills. By being proactive in monitoring your progress, you can continuously learn and grow as a writer, ensuring that your essays are both persuasive and impactful.
Related Post
How to master the art of writing expository essays and captivate your audience, convenient and reliable source to purchase college essays online, step-by-step guide to crafting a powerful literary analysis essay, unlock success with a comprehensive business research paper example guide, unlock your writing potential with writers college – transform your passion into profession, “unlocking the secrets of academic success – navigating the world of research papers in college”, master the art of sociological expression – elevate your writing skills in sociology.
Argumentative Essay Structure: A Comprehensive Guide
Introduction.
Writing an argumentative essay can seem like a daunting task, but with the right structure and approach, it becomes much more manageable. An argumentative essay is all about presenting a well-reasoned argument supported by evidence, and it’s essential to structure your essay effectively to convey your message convincingly. If you’re struggling with how to organize your thoughts, you might want to consider taking my class for a more in-depth understanding and personalized guidance.
Understanding the Basics
What is an argumentative essay.
An argumentative essay is a type of writing that requires you to take a position on a topic and support that position with evidence and reasoning. The goal is to persuade your reader to see things from your perspective.
Key Components of an Argumentative Essay
- Introduction : Introduces the topic and presents the thesis statement.
- Body Paragraphs : Each paragraph presents a separate piece of evidence supporting the thesis.
- Counterarguments and Rebuttals : Addressing opposing viewpoints and refuting them.
- Conclusion : Summarizes the main points and restates the thesis in light of the evidence presented.
Differences Between Argumentative and Persuasive Essays
While both aim to persuade the reader, an argumentative essay relies more on logic and evidence, whereas a persuasive essay may appeal more to emotions and personal beliefs.
Choosing a Topic
Importance of a strong topic.
A compelling topic is crucial for an argumentative essay. It should be debatable, relevant, and interesting to you and your audience.
Tips for Selecting a Topic
- Choose something you are passionate about.
- Ensure there is enough evidence available to support your argument.
- Pick a topic that is relevant to current events or ongoing debates.
Examples of Argumentative Essay Topics
- Should the death penalty be abolished?
- Is climate change the greatest threat to humanity?
- Do social media platforms negatively impact mental health?
Crafting a Thesis Statement
Definition of a thesis statement.
A thesis statement is a concise summary of the main point or claim of the essay. It typically appears at the end of the introduction.
Importance of a Strong Thesis
A strong thesis statement provides direction for the essay and makes a clear and specific argument.
How to Write an Effective Thesis Statement
- Be clear and specific.
- Take a definitive stance.
- Make sure it is debatable and not a statement of fact.
Introduction Paragraph
Hooking the reader.
Start with a hook to grab the reader’s attention. This could be a startling fact, a quote, or a rhetorical question.
Providing Background Information
Give the reader some context about the topic. This helps them understand the significance of the issue being discussed.
Presenting the Thesis Statement
Clearly state your thesis at the end of the introduction. This sets up the main argument that will be developed in the body of the essay.
Body Paragraphs
Structure of a body paragraph.
Each body paragraph should start with a topic sentence that introduces the main idea of the paragraph. This is followed by evidence and analysis.
Developing Arguments
Each paragraph should present a single argument that supports the thesis. Use logical reasoning and credible evidence to make your case.
Using Evidence and Examples
Support your arguments with facts, statistics, examples, and quotes from experts. This adds credibility to your essay.
Counterarguments and Rebuttals
Importance of addressing counterarguments.
Acknowledging and refuting opposing viewpoints shows that you have considered different perspectives and strengthens your argument.
How to Present Counterarguments
Introduce the counterargument fairly and respectfully. This demonstrates your understanding of the issue.
Crafting Effective Rebuttals
Refute the counterargument with evidence and reasoning. Explain why your position is more valid or preferable.
Conclusion Paragraph
Summarizing the main points.
Briefly recap the main points made in the body of the essay. This reinforces your argument.
Restating the Thesis
Restate your thesis in light of the evidence presented. This shows how the evidence supports your overall argument.
Providing a Final Thought or Call to Action
End with a strong closing statement. This could be a call to action, a prediction, or a thought-provoking question.
Transitions Between Paragraphs
Importance of smooth transitions.
Smooth transitions help the essay flow logically and make it easier for the reader to follow your argument.
Techniques for Effective Transitions
- Use transitional phrases (e.g., “Furthermore,” “In addition,” “However”).
- Refer back to previous points to create a logical link.
- Introduce the next point at the end of the current paragraph.
Examples of Transitional Phrases
- “In contrast…”
- “Moreover…”
- “As a result…”
Using Evidence
Types of evidence.
- Facts : Verifiable information.
- Statistics : Numerical data.
- Expert Opinions : Statements from authorities in the field.
- Examples : Specific instances that illustrate a point.
Integrating Evidence into Your Essay
Introduce evidence with a signal phrase, explain its relevance, and analyze it to show how it supports your argument.
Citing Sources Properly
Proper citation gives credit to the original authors and adds credibility to your essay. Follow the required citation style (e.g., APA, MLA).
Maintaining a Formal Tone
Importance of tone in an argumentative essay.
A formal tone helps to convey your argument with authority and professionalism.
Tips for Maintaining a Formal Tone
- Avoid slang and colloquialisms.
- Use precise and clear language.
- Write in the third person (e.g., “The study shows…” instead of “I think…”).
Common Pitfalls to Avoid
- Overusing complex vocabulary.
- Being overly emotional or biased.
- Straying from the main argument.
Editing and Proofreading
Importance of revising your essay.
Editing and proofreading help to refine your arguments, correct errors, and improve clarity.
Tips for Effective Editing
- Take a break before revising.
- Read your essay out loud.
- Use editing tools and checklists.
Common Errors to Watch For
- Grammatical mistakes.
- Spelling errors.
- Logical inconsistencies.
Formatting Your Essay
Proper essay format.
Follow the required formatting guidelines for your essay (e.g., font type, size, margins).
Guidelines for Formatting
- Use a standard font (e.g., Times New Roman, 12 pt).
- Double-space your text.
- Include a header with your name and page number.
Tips for a Clean and Professional Look
- Use headings and subheadings.
- Ensure consistent spacing and indentation.
- Include a title page if required.
Common Mistakes to Avoid
Overview of common errors.
- Failing to address counterarguments.
- Using weak or irrelevant evidence.
- Ignoring the importance of editing.
How to Avoid These Mistakes
- Plan and outline your essay before writing.
- Use credible sources for evidence.
- Allocate time for revising and proofreading.
Examples of Corrected Mistakes
- Corrected: “Evidence shows that climate change poses significant threats to global ecosystems.”
Writing an effective argumentative essay requires careful planning, a clear structure, and strong evidence. By following the guidelines outlined in this article, you can craft a compelling essay that persuades your readers to see things from your perspective. Remember, practice makes perfect, so keep honing your skills and experimenting with different topics and arguments.
How long should an argumentative essay be?
The length of an argumentative essay can vary, but it typically ranges from 1,500 to 2,500 words, depending on the complexity of the topic and the depth of analysis required.
Can I use first-person pronouns in an argumentative essay?
While it’s generally recommended to use third-person pronouns to maintain a formal tone, first-person pronouns can be used sparingly if they enhance the argument and clarity.
How many sources should I use?
The number of sources depends on the assignment requirements, but a well-researched argumentative essay typically includes at least 5-10 credible sources.
What is the difference between a fact and an opinion?
A fact is a statement that can be verified with evidence, while an opinion is a personal belief or judgment that may not be based on evidence.
How can I make my essay more persuasive?
To make your essay more persuasive, use strong evidence, address counterarguments, maintain a formal tone, and use clear and logical reasoning.
- Environment
- Science & Technology
- Business & Industry
- Health & Public Welfare
- Topics (CFR Indexing Terms)
- Public Inspection
- Presidential Documents
- Document Search
- Advanced Document Search
- Public Inspection Search
- Reader Aids Home
- Office of the Federal Register Announcements
- Using FederalRegister.Gov
- Understanding the Federal Register
- Recent Site Updates
- Federal Register & CFR Statistics
- Videos & Tutorials
- Developer Resources
- Government Policy and OFR Procedures
- Congressional Review
- My Clipboard
- My Comments
- My Subscriptions
- Sign In / Sign Up
- Site Feedback
- Search the Federal Register
The Federal Register
The daily journal of the united states government.
- Legal Status
This site displays a prototype of a “Web 2.0” version of the daily Federal Register. It is not an official legal edition of the Federal Register, and does not replace the official print version or the official electronic version on GPO’s govinfo.gov.
The documents posted on this site are XML renditions of published Federal Register documents. Each document posted on the site includes a link to the corresponding official PDF file on govinfo.gov. This prototype edition of the daily Federal Register on FederalRegister.gov will remain an unofficial informational resource until the Administrative Committee of the Federal Register (ACFR) issues a regulation granting it official legal status. For complete information about, and access to, our official publications and services, go to About the Federal Register on NARA's archives.gov.
The OFR/GPO partnership is committed to presenting accurate and reliable regulatory information on FederalRegister.gov with the objective of establishing the XML-based Federal Register as an ACFR-sanctioned publication in the future. While every effort has been made to ensure that the material on FederalRegister.gov is accurately displayed, consistent with the official SGML-based PDF version on govinfo.gov, those relying on it for legal research should verify their results against an official edition of the Federal Register. Until the ACFR grants it official status, the XML rendition of the daily Federal Register on FederalRegister.gov does not provide legal notice to the public or judicial notice to the courts.
Cybersecurity Labeling for Internet of Things
A Rule by the Federal Communications Commission on 07/30/2024
Document Details
Information about this document as published in the Federal Register .
Document Statistics
Published document.
This document has been published in the Federal Register . Use the PDF linked in the document sidebar for the official electronic format.
Enhanced Content - Table of Contents
This table of contents is a navigational tool, processed from the headings within the legal text of Federal Register documents. This repetition of headings to form internal navigation links has no substantive legal effect.
FOR FURTHER INFORMATION CONTACT:
Supplementary information:, a. eligible devices or products, b. oversight and management of the iot labeling program, c. cyberlabs, cla-run labs, and in-house testing labs, d. two-step process for obtaining authority to use the fcc iot label, e. consumer iot product cybersecurity criteria and standards, f. the fcc iot label (cyber trust mark and qr code), g. registry, h. continuing obligations of entities authorized to use the fcc iot label, i. audits, post-market surveillance, and enforcement, j. international reciprocal recognition of the cyber trust mark, k. consumer education, l. cost/benefit analysis, i. legal authority, ii. incorporation by reference, iii. procedural matters, iv. ordering clauses, list of subjects in 47 cfr part 8, final rules, subchapter a—general, part 8—safeguarding and securing the internet, subpart a—protections for internet openness, subpart b—cybersecurity labeling program for iot products, enhanced content - submit public comment.
- This feature is not available for this document.
Enhanced Content - Read Public Comments
Enhanced content - sharing.
- Email this document to a friend
Enhanced Content - Document Print View
- Print this document
Enhanced Content - Document Tools
These tools are designed to help you understand the official document better and aid in comparing the online edition to the print edition.
These markup elements allow the user to see how the document follows the Document Drafting Handbook that agencies use to create their documents. These can be useful for better understanding how a document is structured but are not part of the published document itself.
Enhanced Content - Developer Tools
This document is available in the following developer friendly formats:.
- JSON: Normalized attributes and metadata
- XML: Original full text XML
- MODS: Government Publishing Office metadata
More information and documentation can be found in our developer tools pages .
Official Content
- View printed version (PDF)
This PDF is the current document as it appeared on Public Inspection on 07/29/2024 at 8:45 am. It was viewed 0 times while on Public Inspection.
If you are using public inspection listings for legal research, you should verify the contents of the documents against a final, official edition of the Federal Register. Only official editions of the Federal Register provide legal notice of publication to the public and judicial notice to the courts under 44 U.S.C. 1503 & 1507 . Learn more here .
Federal Communications Commission.
Final rule.
In this document, the Federal Communications Commission (Commission or FCC) establishes a voluntary cybersecurity labeling program for wireless consumer Internet of Things, or IoT, products. The program will provide consumers with an easy-to-understand and quickly recognizable FCC IoT Label that includes the U.S. Cyber Trust Mark and a QR code linked to a dynamic, decentralized, publicly available registry of more detailed cybersecurity information. This program will help consumers make safer purchasing decisions, raise consumer confidence regarding the cybersecurity of the IoT products they buy, and encourage manufacturers to develop IoT products with security-by-design principles in mind.
Effective date: This rule is effective August 29, 2024.
Incorporation by reference: The incorporation by reference of certain material listed in the rule is approved by the Director of the Federal Register as of August 29, 2024.
Compliance date: Compliance with 47 CFR 8.208 , 8.209 , 8.212 , 8.214 , 8.215 , 8.217 , 8.218 , 8.219 , 8.220 , 8.221 , and 8.222 will not be required until the Office of Management and Budget has completed review under the Paperwork Reduction Act. The Commission will publish a document in the Federal Register announcing that compliance date.
Zoe Li, Cybersecurity and Communications Reliability Division, Public Safety and Homeland Security Bureau, (202) 418-2490, or by email to [email protected] .
For additional information concerning the Paperwork Reduction Act information collection requirements contained in this document, contact Nicole Ongele, Office of Managing Director, Performance and Program Management, 202-418-2991, or by email to [email protected] .
This is a summary of the Commission's Report and Order, PS Docket No. 23-239, adopted March 14, 2024, and released March 15, 2024. The full text of this document is available by downloading the text from the Commission's website at: https://docs.fcc.gov/public/attachments/FCC-24-26A1.pdf . When the FCC Headquarters reopens to the public, the full text of this document will also be available for public inspection and copying during regular business hours in the FCC Reference Center, 45 L Street NE, Washington, DC 20554. To request this document in accessible formats for people with disabilities ( e.g., Braille, large print, electronica files, audio format, etc.) or to request reasonable accommodations ( e.g., accessible format documents, sign language interpreters, CART, etc.), send an email to [email protected] or call the FCC's Consumer and Government Affairs Bureau at (202) 418-0530 (voice), (202) 418-0432 (TTY).
Congressional Review Act: The Commission has determined, and the Administrator of the Office of Information and Regulatory Affairs, Office of Management and Budget, concurs, that this rule is non-major under the Congressional Review Act, 5 U.S.C. 804(2) . The Commission will send a copy of the Order to Congress and the Government Accountability Office pursuant to 5 U.S.C. 801(a)(1)(A) .
1. With the Report and Order (Order), the Commission takes prompt and decisive measures to strengthen the nation's cybersecurity posture by adopting a voluntary cybersecurity labeling program for wireless IoT products. The Commission's IoT Labeling Program will provide consumers with an easy-to-understand and quickly recognizable FCC IoT Label that includes the U.S. Government certification mark (referred to as the U.S. Cyber Trust Mark) that provides assurances regarding the baseline cybersecurity of an IoT product, together with a QR code that directs consumers to a registry with specific information about the product. Consumers who purchase an IoT product that bears the FCC IoT Label can be assured that their product meets the minimum cybersecurity standards of the IoT Labeling Program, which in turn will strengthen the chain of connected IoT products in their own homes and as part of a larger national IoT ecosystem. The Order will help consumers make better purchasing decisions, raise consumer confidence with regard to the cybersecurity of the IoT products they buy to use in their homes and their lives, and encourage manufacturers of IoT products to develop products with security-by-design principles in mind.
2. In the Order, we set forth the framework by which the IoT Labeling Program will operate. We focus the IoT Labeling Program initially on IoT “products,” which we define to include one or more IoT devices and additional product components necessary to use the IoT device beyond basic operational features. Recognizing that a successful voluntary IoT Labeling Program will require close partnership and collaboration between industry, the Federal Government, and other stakeholders, we adopt an administrative framework for the IoT Labeling Program that capitalizes on the existing public, private, and academic sector work in this space, while ensuring the integrity of the IoT Labeling Program through oversight by the Commission.
3. Voluntary IoT Labeling Program. We establish a voluntary IoT Labeling Program for wireless consumer IoT products. While participation is voluntary, those that choose to participate must comply with the requirements of the IoT Labeling Program to receive authority to utilize the FCC IoT Label bearing the Cyber Trust Mark. The IoT Labeling Notice of Proposed Rulemaking (NPRM), 88 FR 58211 (August 25, 2023), sought comment on whether the proposed IoT Labeling Program should be voluntary, reasoning that “success of a cybersecurity labeling program will be dependent upon a willing, close partnership and collaboration between the federal government, industry, and other stakeholders.” The record shows substantial support for a voluntary approach. The Custom Electronic Design & Installation Association (CEDIA) suggests that IoT Labeling Program must be voluntary “for the program to gain momentum in the marketplace.” AIM, Inc. (AIM) suggests that the voluntary aspect of the IoT Labeling Program “will help drive adoption of the label by device producers.” Further, commenters suggest that a voluntary program will ensure the broadest reach, most efficiency, and widest access to a diversity of IoT technologies. We agree that a voluntary program will help drive adoption of the IoT Labeling Program, so that a willing, close partnership can be achieved. We also agree with the record that flexible, voluntary, risk-based best practices are the hallmarks of IoT security as it exists today and as it is being developed around the world. Additionally, we acknowledge the view that “consumer labeling is a difficult undertaking in any context,” especially Start Printed Page 61243 in the evolving area of cybersecurity, and that the “best approach is to start the Program with something achievable and effective.” We concur that willing participation will allow the IoT Labeling Program to be more easily achievable than requiring participation in a novel program. With the added imprimatur of a U.S. Government certification mark, the IoT Labeling Program will help distinguish products in the marketplace that meet minimum requirements and provide options to consumers.
4. We reject arguments that mandating participation in the IoT Labeling Program is necessary. While we recognize that a voluntary IoT Labeling Program may cause concern that smaller businesses with limited resources may choose not to participate, we believe the strong stakeholder engagement and collaboration that we expect to result from willing participation, and which is vital to establishing this new program, outweighs these risks. Further, while we acknowledge that, at least in the near term, allowing the IoT Labeling Program to be voluntary “could limit its adoption and impact,” we believe this risk is outweighed by the benefits that a voluntary program will garner, such as speed to market to hasten impact, efficiency of resources, and the likelihood that consumer demand will drive widespread adoption over time.
5. In adopting the IoT Labeling Program with the parameters discussed in the Order, we are establishing a collaborative effort between the Federal Government and relevant stakeholders in industry and the private sector. We emphasize that the Order is intended to provide the high-level programmatic structure that is reasonably necessary to establish the IoT Labeling Program and create the requirements necessary for oversight by the Commission, while leveraging the extensive work, labeling schemes, processes and relationships that have already been developed in the private sector. We also note that there is further development to be done by the private sector and other Federal agencies to implement the IoT Labeling Program and, as discussed below, expects many of the details not expressly addressed in the Order will be resolved through these separate efforts and by the authorities the Commission delegates to the Public Safety and Homeland Security Bureau (PSHSB or the Bureau).
6. The Order initially establishes the IoT Labeling Program for wireless consumer IoT products. We do not, however, foreclose the possibility of expanding the IoT Labeling Program in the future.
7. The record supports adopting an IoT Labeling Program that encompasses consumer-focused IoT products. We focus our IoT Labeling Program initially on consumer IoT products, rather than enterprise or industrial IoT products. Because medical devices regulated by the U.S. Food and Drug Administration (FDA) already are subject to statutory and regulatory cybersecurity requirements under other Federal laws more specifically focused on such devices, we do not include such devices in our IoT Labeling Program. In addition, we exclude from this program motor vehicles [ 1 ] and motor vehicle equipment (as defined in 49 U.S.C. 30102(8) given that the National Highway Traffic Safety Administration (NHTSA) “has the authority to promulgate motor vehicle safety regulations on cybersecurity and has enforcement authority to secure recalls of motor vehicles and motor vehicle equipment with a safety-related defect, including one involving cybersecurity flaws.” We also exclude from our IoT Labeling program any communications equipment on the Covered List that the Commission maintains pursuant to the Secure and Trusted Communications Networks Act and equipment produced by certain other entities as discussed below. Finally, our initial IoT Labeling Program will focus on wireless consumer IoT devices consistent with the core of our section 302 authority governing the interference potential of devices that emit radio frequency energy—and thus we exclude wired IoT devices at this time.
8. Definition of IoT Devices. Although we focus our IoT Labeling program on IoT “products,” to lay a foundation we must first address the definition of IoT “devices” because this definition is a building block of the IoT “product” definition. In this respect, we adopt the modified version of the National Institute of Standards and Technology (NIST) definition of “IoT device” that the Commission proposed in the IoT Labeling NPRM. Specifically, the IoT Labeling NPRM proposed defining an IoT device to include (1) an internet-connected device capable of intentionally emitting radio frequency (RF) energy that has at least one transducer (sensor or actuator) for interacting directly with the physical world, coupled with (2) at least one network interface ( e.g., Wi-Fi, Bluetooth) for interfacing with the digital world. This definition builds on NIST's definition by adding “internet-connected” as a requirement, because “a key component of IoT is the usage of standard internet protocols for functionality.” The modified definition adopted in the Order also adds that a device must be “capable of intentionally emitting RF energy,” because aspects of the Commission's authority recognizes the particular risks of harmful interference associated with such devices. It should be noted that we direct the Label Administrator to collaborate with Cybersecurity Label Administrators (CLAs) and other stakeholders ( e.g., cyber experts from industry, government, and academia) as appropriate and recommend within 45 days of publication of updates or changes to NIST guidelines, or adoption by NIST of new guidelines, to the FCC any appropriate modifications to the Labeling Program standards and testing procedures to stay aligned with the NIST guidelines.
9. The record supports this reasoning. For example, Consumer Reports states that “[i]f you're going to sell a device where some of the benefits come from having a cloud connection, an app, and connectivity, then those must also be secured.” Consumer Reports provides further support for the Commission's reasoning by noting that “connectivity may be so central to the functionality of the device that it may no longer be able to operate safely [without it].” TIC Council Americas similarly “agrees that `internet-connected' should be included in the definition of IoT devices.” We agree with these arguments and adopt the modified IoT device definition requiring “internet-connected” device element to assure consumers that the functionality of the IoT device or product displaying the Cyber Trust Mark is reasonably secure as well. As noted by ioXt Alliance, including “internet-connected” in the definition of IoT makes “sense if the program focuses on IoT products instead of devices because not all IoT devices are `internet-connected.' ” Because the IoT Labeling Program will be focused on the broader category of IoT consumer products and not devices, including “internet-connected” in the definition of IoT device is further justified.
10. We disagree with commenters who argue the Commission should adopt the NIST definition of a device without change. We acknowledge that the record indicates some concern regarding the internet-connected element of the Commission's proposed definition; however, we find these concerns to be misplaced. TIC Council Start Printed Page 61244 Americas, for example, supports adding “internet-connected” to the definition, but argues that “there are devices that are able to connect to non-internet connected networks, and that those devices should not be excluded from the program.” While we do not foreclose the possibility of expanding the IoT Labeling Program to devices on non-internet connected networks in the future, we focus initially on the more common category of internet-connected consumer IoT products. Others argue that “internet-connected” is too “situational,” with a concern that the device might become “disconnected from the internet and, therefore, no longer be an `IoT device.' ” We do not agree that “internet-connected device” must be interpreted so narrowly as to exclude from the IoT Labeling Program devices that may become disconnected from the internet. “internet-connected,” in terms of the IoT Labeling Program, applies to the functional capability of the device; if the device is capable of being connected to the internet, the fact that it may not be connected at any given point in time does not exclude its eligibility for participation in the IoT Labeling Program. Further, any potential concerns arising from requiring an IoT device be “internet-connected” for inclusion in the IoT Labeling Program are outweighed by the benefit of giving consumers further assurance that the security of their IoT device or product extends to the connected functionality that a consumer expects when making such a purchase. In this respect, including “internet-connected” in the definition of IoT device also recognizes the highest risk functional component of an IoT device that distinguishes “smart” devices from other devices a consumer may use, and allows the Cyber Trust Mark to more effectively support consumer expectations.
11. The record also supports adding an RF energy-emitting element to the IoT device definition, acknowledging the Commission's authority under section 302 governing the interference potential of devices that emit RF energy and can cause harmful interference to radio communications. We reject the argument that limiting the definition to RF-emitting devices may lead to marketplace confusion if a product does not bear the Cyber Trust Mark due solely to its lack of RF energy emissions. In the first instance, we note the need to launch an achievable IoT Labeling Program consistent with the Commission's core authority. We also note that the benefits that a focus on wireless products will have in elevating the overall cybersecurity posture of the IoT ecosystem, especially in view of the record indicating that the majority of IoT devices are wireless, outweigh the risks associated with concerns regarding marketplace confusion. In any case, there will be a number of products—both wired and wireless—that do not bear the Cyber Trust Mark while uptake occurs. We also anticipate that consumer education in this space will help alleviate these concerns.
12. We further disagree with the view that the capability of a device to emit RF radiation is “unrelated to the general, far-ranging cybersecurity concerns the Commission is confronting in this proceeding.” Instead, we agree with Comcast that interference caused by a [distributed denial of service] attack raises “the same policy concerns and has the same practical effect as interference caused by traditional means.” The Electronic Privacy Information Center (EPIC) explains how hackers exploit unpatched vulnerabilities to attack a large number of wireless devices, and turning them into signal jammers to take down mobile networks. The record thus bears out our view that cybersecurity vulnerabilities in wireless IoT devices could cause harmful interference to radio communications. Given Congress' direction to the Commission in section 302 of the Act to guard against the interference potential of wireless devices, requiring the element of “emitting RF energy interference” in the IoT device definition for the initial iteration of the IoT Labeling Program focuses on that core Commission authority without ruling out future action regarding wired IoT devices. Further, while we acknowledge that devices that unintentionally or incidentally emit RF radiation may also pose interference potential, we find that a focus initially on “intentional” radiators provides the ability of a nascent program to target products with the highest risk profile from among those that emit RF energy.
13. Definition of IoT Products. We adopt the NIST definition of an “IoT product.” Specifically, the IoT Labeling NPRM's proposed definition of IoT product is an “IoT device and any additional product components ( e.g., backend, gateway, mobile app) that are necessary to use the IoT device beyond basic operational features.” The record supports adopting the IoT product definition developed by NIST, with Garmin International, Inc. (Garmin) noting that a fundamental purpose of the IoT Labeling Program “is to inform consumers regarding device security as they evaluate potential IoT purchases. . . . [T]his purpose is best achieved by focusing on `consumer IoT products' as defined by NIST in NISTIR 8425.” Additionally, Kaiser Permanente states that adopting the NIST definition of IoT products will “promote consistency across federal agency programs and related industry norms and requirements.” Further, the Information Technology Industry Council (ITI) explained that the “Commission's implementation of the program will be more successful if it aligns as closely as possible to the definitions, processes and procedures already outlined by NIST.” We agree with these commenters, in that adopting NIST's IoT product definition will allow for consistency in the treatment of programmatic elements across the Federal Government, and allow the Commission to appropriately leverage the work existing in this space to promote the IoT Labeling Program's success. We also note that no commenters opposed the NIST definition of IoT products. For purposes of the IoT Labeling Program, when discussing IoT products and their “components” in the Order, we are using the NISTIR 8425 scoping definition of “components.” We believe that this definition allows the IoT Labeling Program to address the most relevant “package” components expected by consumers to be securable when making purchasing decisions, and encompasses the appropriate level of “component” pieces to address the functionalities that generate the most salient cybersecurity risks. [ 2 ] This view is supported by the record, with Consumer Technology Association (CTA) providing a proposed testing framework where “all individual components provided by the manufacturer should be in scope for testing,” including all components of the IoT product “that are necessary for the device to function in a normal use case scenario.”
14. IoT Devices vs. IoT Products. We find that the IoT Labeling Program should apply to “IoT products” as defined above, rather than being limited only to “IoT devices.” In the IoT Labeling NPRM, the Commission noted Start Printed Page 61245 that it was important to ensure that the IoT Labeling Program “would be sufficiently inclusive to be of value to consumers.” Since the Commission's adoption of the IoT Labeling NPRM, NIST has provided clarity in this realm by stating “the cybersecurity technical and non-technical outcomes defined in the NISTIR 8425 consumer profile apply to IoT products and not just IoT devices.” In addition, in reviewing the record, we believe applying the IoT Labeling Program to IoT products instead of IoT devices alone achieves these priorities because only by addressing the full functionality of a consumer product ( i.e., one or more IoT devices and any additional product components ( e.g., backend, gateway, mobile app) that are necessary to use the IoT device, beyond basic operational features) “including data communications links to components outside this scope but excluding those external components and any external third-party components that are outside the manufacturer's control” will provide consumers the necessary scope to satisfy the basic security expectation of the consumer and effectuate a discernable increase in the cybersecurity posture of the IoT ecosystem at large.
15. There is significant support in the record for an IoT product focus for the IoT Labeling Program. As explained by UL Solutions, applying the IoT Labeling Program to IoT products is necessary since “most IoT devices sold to consumers cannot be meaningfully used without additional components.” The Cybersecurity Coalition further supports this position by saying “IoT devices are typically part of a broader ecosystem of components that can have their own security issues, requiring `IoT cybersecurity' to extend beyond individual devices to be effective.” ITI notes an IoT product focus benefits consumers because it “will appropriately capture the relevant devices/components of the product that could be vulnerable to attack (and are always included in an IoT product, as NIST points out).” Applying the IoT Labeling Program to IoT products further benefits consumers by promoting consumer safety because it “encourages manufacturers to prioritize security across all components, ultimately leading to safer and more reliable IoT experiences for consumers.” Additionally, the record indicates that “the entire service which includes cloud infrastructure as well as apps or other ways to control or manage the device by the user, and not simply the physical device itself, is critical for an assessment of safety and security.” Further, focusing on IoT products aligns not only with the technical requirements of NISTIR 8425, but also “emerging requirements in Europe and the UK [United Kingdom], such as the EU [European Union] [Cyber Resilience Act], and EU Directives on consumer protections EU 2019/770, 771.” We agree and will apply the IoT Labeling Program to consumer IoT products, which provides for the greatest level of consumer benefit by prioritizing cybersecurity across the entirety of the consumer product, as compared to just the device, which is able to perform its full functionality only when working in conjunction with other product components.
16. We disagree with Samsung, CTIA—The Wireless Association (CTIA), LG Electronics, and CTA, who advocate focusing on IoT devices instead of IoT products. Samsung and CTIA argue that cybersecurity standards for devices are more mature than standards for products, and CTA argues that applying the FCC IoT Label to products would be more complex than devices. LG Electronics expresses concern that expanding to products “would require device manufacturers to attest to the security of product components that are outside of their control.” We do not agree that these rationales support limiting application of the IoT Labeling Program only to devices, rather than products. First, applying the IoT Labeling Program narrowly to IoT devices would run counter to NIST's guidance and considerable work in this space, upon which the Commission has relied for the basis for the IoT Labeling Program proposal. NIST's Profile of the IoT Core Baseline for Consumer IoT Products (NISTIR 8425), discussed above, provides fundamental IoT guidelines and applies to the broader product category, and the more recent NIST IoT Product Component Requirements Essay clearly states that the outcomes listed in NISTIR 8425 apply to consumer IoT products and not just IoT devices.
17. Further, regarding the notion that the IoT Labeling Program should be focused on IoT devices because existing standards for IoT devices are more readily available or achievable in the near term, we counter that the record shows existing IoT device standards can be leveraged to support assessing IoT products as well. As noted by commenter ITI, existing IoT industry standards “capture similar baseline themes” to the NIST criteria. In view of these similarities, the IoT Labeling Program can leverage these existing standards for IoT devices as building blocks, and tailor them in view of the IoT products being assessed. Accordingly, the need to realize the benefits of a product-level label weigh in favor of taking a small amount of time to get to product-based standards by leveraging existing device standards.
18. We also reject the argument that because “cybersecurity frameworks and testing programs have been developed to focus on device-level—rather than product-level—assessment” that a device-level IoT Labeling Program is the appropriate outcome. We note, for example, that ITI recommends recognizing IoT security assessments from our international partners, such as IoT assessments under the Cybersecurity Labelling Scheme (CLS) by Singapore's Cyber Security Agency, which assesses the overall IoT product, and not just a single device included in the IoT product. In this regard, the ability to recognize international efficiencies for IoT Labeling Program participants would be hindered by limiting the Cyber Trust Mark to the device level, as Singapore's CLS (and other evolving international standards) focus on product-level assessments.
19. Finally, applying the IoT Labeling Program to products enhances value to consumers without requiring manufacturers to be responsible for products or devices that are outside of their control. The record shows that a consumer's expectation of security extends to the entire IoT product they purchase. This consumer expectation is evidenced in the record by ITI, clarifying that “because consumers purchase, interact with, and view IoT merchandise not as component parts but as complete physical product . . . Consumers are primarily concerned with the entire physical product they are purchasing.” Additionally, as noted by UL Solutions, “most IoT devices sold to consumers cannot be meaningfully used without additional components.” In view of this need, a manufacturer seeking authority to affix the FCC IoT Label is expected to secure the whole IoT product, including the product's internal communication links connecting the different parts of the product to each other as well as the product's communication links that connect the IoT product to the outside world. We do not require manufacturers to be responsible for third-party products or devices (including apps) that are outside of their control; 2 Start Printed Page 61246 however, where a manufacturer allows third-party apps, for example, to connect to and they allow that application to control their IoT product, such manufacturer is responsible for the security of that connection link and the app if such app resides on the IoT product. Further, we agree with CTIA that if “a [p]roduct [c]omponent also support[s] other IoT Products through alternative features and interfaces, these alternative features and interfaces may, through risk-assessment, be considered as separate from and not part of the IoT Product for purposes of authorization.” Moreover, NIST enumerates the dangers of an IoT device-only focus, establishing that the “additional product components have access to the IoT device and the data it creates and uses-making them potential attack vectors that could impact the IoT device, customer, and others,” and that “these additional components can introduce new or unique risks to the IoT product.” Consumer expectations that the FCC IoT Label would apply to the entirety of the product purchased is further highlighted by Consumer Reports, explaining that “If everything is sold within a box, then everything in the box should be approved to use the mark.” Consumer Reports also notes that “[i]f the labeling programs were only to address the physical device and not other system components, consumers would likely be deceived as to the scope and efficacy of the program.” The record is adamant that the “Cyber Trust Mark must be trusted by consumers to be successful.” In view of the record, securing only a portion of an IoT product by just assessing a single IoT device included in the IoT product, instead of assessing the devices and components that comprise the IoT product holistically, could deceive consumers and go against consumer expectation that the technology being brought into their homes is reasonably secure. We weigh heavily the likelihood for consumer confusion should the device-only approach be taken, and accordingly we apply this consumer IoT Labeling Program to IoT products and not just IoT devices.
20. In sum, although there are relative advantages and disadvantages with either a narrow focus on IoT devices or a broader focus on IoT products, on balance we are persuaded to focus our initial IoT Labeling Program on IoT products. As explained above, we find commenters' concerns about encompassing full IoT products in our IoT Labeling Program to be overstated. At the same time, we see significant shortcomings with a narrower focus just on IoT devices. Weighing the totality of these considerations, we are persuaded that targeting the IoT Labeling Program on IoT products is the best approach at this time.
21. Consumer IoT Products vs. Enterprise IoT Products. The IoT Labeling Program applies to the labeling of consumer IoT products that are intended for consumer use, and does not include products that are primarily intended to be used in manufacturing, healthcare, industrial control, or other enterprise applications. While we do not foreclose expansion of the IoT Labeling Program at a later date, this initial scope will provide value to consumers most efficiently and expediently, without added complexity from the enterprise environment.
22. The record supports the IoT Labeling Program having a consumer IoT focus, with support provided by UL Solutions, the Cybersecurity Coalition, and the Connectivity Standards Alliance (CSA), among others. The FDA also suggests that IoT outside of the consumer scope may need “[g]reater and more tailored controls,” suggesting that different considerations might attend IoT with a purpose outside of that in the routine consumer realm. Additionally, commenters highlight the differing security needs of consumer and enterprise products. For example, UL Solutions notes that “IoT products intended for commercial or industrial settings are exposed to different types of threats than consumer products and often carry higher risk if breach, which necessitates different requirements.” CSA also highlights that “[e]nterprise device security approaches are often customized and vary based on the specific needs of the business.” We agree that applying the IoT Labeling Program to consumer IoT products will reduce complexity, which will bolster the likelihood of success when starting the new IoT Labeling Program.
23. The International Speech and Communication Association (ISCA) supports including enterprise IoT, stating that a broader scope will ensure the IoT Labeling Program remains flexible to the extent that the boundary between consumer and enterprise IoT is blurring. Further, ISCA and Abhishek Bhattacharyya note that attackers have more to gain from targeting enterprise settings. While there are considerable threat vectors and vulnerabilities associated with all classes of IoT products, [ 3 ] we agree with Everything Set, Inc., that focusing the IoT Labeling Program on household use of IoT products will be more useful and have greater impact, given that enterprises tend to have more time, resources, and expertise to devote to network security. They note further that many small- and medium-sized businesses also buy consumer devices, so a consumer-focused Cyber Trust Mark would be of utility to them, as well. We believe in the near term that a consumer focus will provide the most initial impact, and create a level of recognition and trust in the Cyber Trust Mark itself as the IoT Labeling Program progresses that could be leveraged to enterprise IoT at a later time, and we therefore defer consideration of the IoT Labeling Program's expansion.
24. Exclusion of Certain Devices/Products. As an initial matter, we exclude from the IoT Labeling Program medical devices regulated by the U.S. Food and Drug Administration (FDA). The Center for Devices and Radiological Health (within the FDA) expresses concern that the Commission's labeling IoT Labeling Program may lack controls and minimum criteria that it believes are necessary for IoT medical devices. In addition, the FDA is concerned that including medical devices in the IoT Labeling Program may cause consumer confusion and “potentially creates conflict where product manufacturers attempt to both qualify for the Cyber Trust Mark and comply with existing statutory and regulatory cybersecurity requirements under other federal laws, such as the Federal Food, Drug, and Cosmetic Act (FD&C Act).” These considerations persuade us to exclude FDA-regulated medical devices from our IoT Labeling Program, consistent with commenters' recommendations. In Start Printed Page 61247 addition, we exclude from this program motor vehicles and motor vehicle equipment given that the National Highway Traffic Safety Administration (NHTSA) “has the authority to promulgate motor vehicle safety regulations on cybersecurity and has enforcement authority to secure recalls of motor vehicles and motor vehicle equipment with a safety-related defect, including one involving cybersecurity flaws.”
25. Exclusion of Devices/Products Produced by Certain Entities. We adopt the following measures to promote national security in connection with the IoT Labeling Program. The IoT Labeling NPRM proposed to exclude from the IoT Labeling Program (1) any communications equipment on the Covered List maintained by the Commission pursuant to section 2 of the Secure and Trusted Communications Networks Act (STCNA); (2) any IoT device produced by an entity identified on the Covered List ( i.e., an entity named or any of its subsidiaries or affiliates) as producing “covered” equipment; and (3) any device or product from a company named on certain other lists maintained by other Federal agencies that represent the findings of a national security review. We now adopt all of these prohibitions as they relate to our decision to focus the IoT Labeling Program on consumer IoT products. Thus, any communications equipment identified on the Covered List, now or in the future, will be ineligible for the IoT Labeling Program, and any such product will be denied approval to use the Cyber Trust Mark. Furthermore, any additional products produced by an entity identified on the Covered List as producing “covered” equipment, or any product containing devices or product components produced by such an entity, will be ineligible for the IoT Labeling Program; this would include products that may not fit within the definition of “communications equipment” under STCNA. Only entities identified on the Covered List as producers of “covered” equipment—not those on the Covered List only because of their “covered” services—are subject to this prohibition. In addition, we adopt the proposal that IoT devices or products containing devices manufactured by companies named on the Department of Commerce's Entity List, named on the Department of Defense's List of Chinese Military Companies, or suspended or debarred from receiving Federal procurements or financial awards, including those published as ineligible for award on the General Service Administration's System for Award Management, will not be authorized to display the FCC IoT Label or participate in the IoT Labeling Program. Further, we exclude from the IoT Labeling Program any products containing devices produced or manufactured by these entities. We conclude that inclusion on these lists represents a determination by an agency charged with making national security determinations that a company's products lack the indicia of trustworthiness that the Cyber Trust Mark is intended to represent. Our action here thus supports and reinforces the steps we have taken in other proceedings to safeguard consumers and communications networks from equipment that poses an unacceptable risk to national security and that other Federal agencies have taken to identify potential concerns that could seriously jeopardize the national security and law enforcement interests of the United States.
26. With the exception of China's comments raising the same World Trade Organization (WTO) issue we rejected in the Report and Order applying the Covered List to the FCC equipment authorization program, the record overwhelmingly supports excluding from the IoT Labeling Program these products and devices produced by companies identified on the Covered List. Additionally, USTelecom, CTIA, CTA, Cybersecurity Coalition and Consumer Reports specifically support excluding from the IoT Labeling Program IoT devices that are manufactured by companies on the Covered List, but also urge the Commission to restrict any equipment manufactured by companies on additional Federal restricted lists, including those otherwise banned from Federal procurement. Consumer Reports agrees with excluding systems that include components included on the Covered List or similar lists from the IoT Labeling Program. Each of these lists represent the determination by relevant Federal agencies that the entities on the list may pose a national security threat within their respective areas, and as such we find that we cannot separately sanction their products as trustworthy via the IoT Labeling Program. While each list is designed to support specific prohibitions, their use here only excludes their contents from a voluntary program representing U.S. Government assessment of their security and does not prohibit any other use. Insofar as the FCC IoT Label reflects the FCC's signal to consumers about cybersecurity, it is reasonable for the FCC to take a cautious approach especially for those products for which relevant Federal agencies have expressed other security concerns.
27. Applicant Declaration Under Penalty of Perjury. To implement the Commission's goal of ensuring the Cyber Trust Mark is not affixed to products that pose a risk to national security or a risk to public safety, we require applicants seeking authorization to use the FCC IoT Label to provide a declaration under penalty of perjury that all of the following are true and correct:
(i) The product for which the applicant seeks to use the FCC IoT Label through cybersecurity certification meets all the requirements of the IoT Labeling Program.
(ii) The applicant is not identified as an entity producing covered communications equipment on the Covered List, established pursuant to § 1.50002 of the Commission's rules.
(iii) The product is not comprised of “covered” equipment on the Covered List.
(iv) The product is not produced by any entity, its affiliates, or subsidiaries identified on the Department of Commerce's Entity List, or the Department of Defense's List of Chinese Military Companies.
(v) The product is not owned or controlled by or affiliated with any person or entity that has been suspended or debarred from receiving Federal procurements or financial awards, to include all entities and individuals published as ineligible for award on the General Service Administration's System for Award Management.
(vi) The applicant has taken every reasonable measure to create a securable product.
(vii) The applicant will, until the support period end date disclosed in the registry, diligently identify critical vulnerabilities in our products and promptly issue software updates correcting them, unless such updates are not reasonably needed to protect against security failures.
(viii) The applicant will not elsewhere disclaim or otherwise attempt to limit the substantive or procedural enforceability of this declaration or of any other representations and commitments made on the FCC IoT Label or made for purposes of acquiring or maintaining authorization to use it.
28. If any applicant fails to make any of the above disclosures within 20 days after being notified of its noncompliance, such failure would result in termination of any improperly granted authorization to use the Label, and/or subject the applicant to other Start Printed Page 61248 enforcement measures. The applicant is required to update its declaration, or withdraw a not-yet granted application, if any of the applicant's circumstances impacting the declarations materially change while the application is pending.
29. Wireless Consumer IoT Devices vs. Wired Consumer IoT Devices. The Order adopts the IoT Labeling NPRM's proposal that the IoT Labeling Program apply initially to wireless consumer IoT devices. This is consistent with the IoT Labeling NPRM proposal to focus the scope of the IoT Labeling Program on intentional radiators that generate and emit RF energy by radiation or induction and exclude wired-only IoT devices, noting such devices are encompassed by the Commission's section 302 authority governing the interference potential of devices that emit RF energy and can cause harmful interference. We find that this distinction is appropriate, both because of the Commission's interest in keeping the scope of the IoT Labeling Program clear and manageable during its debut and because there is support in the record for wireless intentional radiators as most prevalent types of consumer IoT devices contemplated in the IoT Labeling NPRM. While we recognize that there are other types of RF devices—both unintentional and incidental radiators—that are subject to our jurisdiction, we are not including them in our IoT Labeling Program at this time.
30. We acknowledge there is substantial support in the record for including wired IoT consumer products within the scope of the IoT Labeling Program. Consumer Reports recommends including both wired and wireless IoT within the scope of the IoT Labeling Program, pointing out that wired IoT devices or products are vulnerable to cybersecurity threats just as wireless IoT devices or products are. Consumer Reports also points out that “while wireless devices are the majority of IoT devices, there are still almost 700 million wired IoT devices globally, and they are expected to grow by a 10% [compound annual growth rate] through 2027 according to IoT Analytics `State of IoT—Spring 2023 Report.' ” TÜV SÜD also encourages the Commission to cover both wired and wireless devices within the scope of the IoT Labeling Program, and AIM emphasizes the importance of the security of both wired and wireless IoT to the cybersecurity ecosystem. CTA further states that the Commission should not define the scope of the IoT Labeling Program in such a way as to exclude wired IoT products. The Association of Home Appliance Manufacturers (AHAM) points out that both wired and wireless IoT are included in the NIST definition.
31. While we agree that wired IoT products are susceptible to cyberattacks and similarly pose security risks to consumers and others, we find it to be in the public interest for the IoT Labeling Program to start with wireless consumer IoT products in view of the record indicating that “wireless devices are the majority of IoT devices,” which would indicate that a focus on this product segment will have a substantial impact on the overall IoT market. The record also supports this approach, with Keysight Technologies, Inc. concurring that “the program should include consumer RF IoT products initially.” Further, we do not agree with arguments that there may be an unintended perception that “[c]reating a program that would only certify wireless IoT devices would send an improper message that only wireless IoT devices are secure.” Instead, we believe that beginning with wireless IoT products is both feasible and can be adopted with more speed, providing more prompt benefit in the marketplace. Further, a more limited scope will streamline the initial rollout of the IoT Labeling Program, provide focus to the additional tasks necessary to stand up the program, and lay the groundwork for expansion, and we do not foreclose consideration including wired IoT products in the future. As such and as discussed below, we also defer consideration of our legal authority to consider wired products at this time.
32. Based on the comments filed regarding oversight and management of the IoT Labeling Program, the Commission finds it is in the public interest to continue to foster public-private collaboration, including with regard to the management and administration of the IoT Labeling Program, while ensuring the Commission retains ultimate control and oversight of the IoT Labeling Program. In this respect, providing a broad, unifying government oversight framework for existing private labeling schemes and other private efforts in this context will allow current participants in this ecosystem to capitalize on their existing investments and relationships in a way that not only promotes the overall effectiveness of the FCC's IoT Labeling Program and increases the security of the IoT ecosystem.
33. The Commission adopts the IoT Labeling NPRM proposal that the IoT Labeling Program be comprised of a single “program owner” responsible for the overall management and oversight of the IoT Labeling Program, with administrative support from one or more third-party administrators. NIST's white paper recommends one “scheme owner” responsible for managing the labeling program, determining its structure and management, and performing oversight to ensure the program is functioning consistently in keeping with overall objectives. We agree that it is appropriate for a single entity to perform these functions and find that the Commission will be the program owner of the IoT Labeling Program, and as such retains ultimate control over the program, and determines the program's structure. CSA highlights support in the record for having the Commission as the program owner, arguing that “[p]lacing the regulatory authority in the hands of the Commission and providing government-backed endorsement may strengthen trust with Consumers.” However, the NIST Cybersecurity White Paper also recommends the “scheme owner” be responsible for defining the conformity assessment requirements, developing the label and associated information, and conducting consumer outreach and education.
34. While the Commission as program owner will oversee the elements of the program, the program will be supported by Cybersecurity Label Administrators (Label Administrators or CLAs) who will manage certain aspects of the program and authorize use the FCC IoT Label as well as a Lead Administrator selected by the Bureau from among the CLAs, which will undertake additional duties including acting as the point of contact between the CLAs and the Commission. In addition, the Commission believes it is appropriate for a Lead Administrator, in collaboration with the CLAs and other stakeholders, to identify or develop, and recommend to the Commission for approval, the IoT specific standards and testing procedures, procedures for post-market surveillance, as well as design and placement of the label. The Lead Administrator will also be responsible for developing, in coordination with stakeholders, a consumer education plan and submitting the plan to the Bureau and engaging in consumer education. Each of these duties are discussed in depth below. The Cybersecurity Coalition recommends the Commission utilize a single administrator, rather than multiple administrators “to reduce the likelihood of conflict among administrators and simplify engagement with Start Printed Page 61249 manufacturers, consumers, and government agencies.” CTA, on the other hand, contemplates multiple administrators, suggesting that the Commission may consider leveraging “a consortium of scheme owners[ ] to ensure that the IoT Labeling Program is administered and issues are adjudicated in an effective, objective, and timely fashion.” We agree with CTA's reasoning, while also acknowledging the Cybersecurity Coalition's concern regarding potential conflict. Accordingly, the Bureau will select a Lead Administrator from among the CLA applicants to address conflicts.
35. As an initial matter, we have looked to the structure of, and experiences with, the Commission's equipment authorization program and rules in developing the IoT Labeling Program, as proposed and discussed in the IoT Labeling NPRM. We emphasize, however, that the IoT Labeling Program is new and distinct, and it will operate under its own rules and with new authorities specifically delegated to PSHSB. This is consistent with the record developed in the proceeding, in which many commenters urged the Commission to keep the equipment authorization and IoT Labeling programs separate. In addition, several commenters addressed whether obtaining a valid equipment authorization should be a pre-requisite for obtaining the Cyber Trust Mark, or whether obtaining approval to use the Cyber Trust Mark would be required as a condition for applying for an equipment authorization. We emphasize that our IoT Labeling Program is voluntary, and parties are required to follow the Commission's equipment authorization program regardless of whether or not they choose to participate in the IoT Labeling Program. We also clarify that there is no requirement to complete the equipment authorization process before qualifying for the Cyber Trust Mark; however, our existing part 2 rules will continue to prohibit the marketing of a device that does not have a valid equipment authorization.
36. We conclude that it is in the public interest and supported in the record to adopt the IoT Labeling Program structure recommended by NIST, with the modifications discussed above regarding third-party administrators that are overseen by the Commission as the program owner. This and the following paragraph preview the remaining roles and responsibilities for the IoT Labeling Program, which will be developed in depth in the remaining sections of the Order. The Commission also will be responsible for coordinating mutual recognition of the Cyber Trust Mark with international partners, coordinating with the Lead Administrator, Federal partners, industry, and other stakeholders on consumer education programs, and performing oversight to ensure the IoT Labeling Program is functioning properly. In addition, the Commission will specify the data to be included in a consumer-friendly registry that provides additional information about the security of the products approved to use the Cyber Trust Mark and is accessible through the QR Code that is required to accompany the Cyber Trust Mark. Further, the Commission will own and maintain the registration for the Cyber Trust Mark, which may only be used when the product has been appropriately tested and complies with the Commission's IoT Labeling Program requirements.
37. The Commission will approve qualified Cybersecurity Label Administrators (Label Administrators or CLAs) to manage certain aspects of the labeling program and be authorized by the Commission to license the Cyber Trust Mark to manufacturers whose products are in compliance with the Commission's IoT cybersecurity labeling rules. The Commission will also select a Lead Administrator, which will be responsible for carrying out additional administrative responsibilities, including but not limited to reviewing applications and recognizing qualified and accredited Cybersecurity Testing Laboratories (CyberLABs) and engaging in consumer education regarding the Cyber Trust Mark. The Lead Administrator will also collaborate with cyber experts from industry, government, academia, and other relevant sectors if needed to identify, develop, and maintain consumer IoT cybersecurity technical and conformity assessment standards that are based on NIST standards and guidance, that will be submitted to PSHSB for consideration and approval, and, subject to any required public notice and comment, adopted into the Commission's rules. The standards and testing procedures developed or identified in collaboration with CLAs and other stakeholders and submitted by the Lead Administrator for consideration by the Commission will, in turn, be used by accredited [ 4 ] testing labs recognized by the Lead Administrator—whether CyberLABs, [ 5 ] a CLA-run lab, or a testing lab internal to a company (in-house testing lab) for product testing.
38. Retaining key overarching functions within the Commission as discussed above will ensure the effective administration and oversight of this government program and protect the integrity of the FCC-owned Cyber Trust Mark, while perpetuating, where appropriate, the relevant efforts of the private sector that meet the goals and requirements of the program. We also agree with CSA that program ownership by the Commission will increase consumer confidence in the Cyber Trust Mark. In addition, the clear high-level oversight functions retained for the Commission ensures the Commission has meaningful decision-making control. Here, while the CLA(s) will recommend standards and testing procedures to be approved by the Commission as well as manage the day-to-day administrative functions assigned, the Commission will ultimately review, consider, and exercise judgment on whether the requirements are appropriate to support the Commission's program, and on how the program is ultimately administered.
39. We adopt the IoT Labeling NPRM's proposal that one or more qualified third-party administrators (Cybersecurity Labeling Administrators or CLAs) be designated by the Commission to manage certain aspects of the labeling program and be authorized to certify the application of the FCC IoT Label by manufacturers whose products are found to be in compliance with the Commission's IoT cybersecurity labeling rules and regulations. The record supports the Commission's adoption of a labeling program that is supported by CLAs. Start Printed Page 61250 According to TIC Council Americas, involving independent third-party administrators who verify that labeled products meet the program requirements will bring trust, consistency, and an impartial level playing field to the Cyber Trust Mark. The Cybersecurity Coalition, Widelity, and CSA highlight that utilizing experienced third-party administrators will allow the program to run more efficiently and will provide “the required expertise for the administration of the program.” CTA and other commenters also assert that the IoT Labeling Program will be best served if the Commission “leverage[s] the unique expertise and existing certification infrastructure offered by well-regarded industry organizations.” AHAM says that “[g]iven the volume and increasing numbers of IoT products on the market, [the] FCC needs to give manufacturers as many options as possible as far as obtaining the Cyber Trust mark” and that “third parties will play an important role in any successful program.”
40. CTA supports assigning certain responsibilities to one or more independent, ( i.e., neutral) third-party administrators which it refers to as “Authorized Scheme Owners.” However, the Commission disagrees with this descriptor insofar as some commenters are confused as to whether the “scheme owner” is the entity ultimately responsible for the program, or a third-party entity responsible for certain program administration functions or specified tasks under the ultimate direction of the Commission. To avoid confusion, the Commission refers to these third-party administrators as CLAs. These CLAs are neutral third parties independent of the applicant and within the context of a program overseen by the Commission.
41. We believe that authorizing one or more CLAs to handle the routine administration of the program will help to ensure a timely and consistent rollout of the program. In particular, several private entities have already implemented robust IoT cybersecurity labeling programs with established business processes in place to receive applications from IoT manufacturers and conduct conformity/standards testing against widely accepted cybersecurity guidelines ( e.g., NIST guidelines) or proprietary product profiles based on the NIST criteria. We anticipate a large number of entities will seek grants of authorization to use the FCC IoT Label and we are concerned that if we were to adopt a program limited to a single administrator, there may be bottlenecking delays in the processing of applications and a single administrator could result in a single point of failure in the program. Allowing multiple CLAs to execute the role of day-to-day administration of the program will provide for the simultaneous processing of a significant number of applications, provide redundancy of structure, and potentially foster competition in this space to better serve those seeking access to the label. In addition, leveraging the expertise of multiple existing program managers and using pre-existing systems and processes that meet our program specifications will minimize administrative delay, while promoting an efficient and timely rollout of the Cyber Trust Mark. This will also ensure that the Commission effectively utilizes the expertise of those entities who have made investments in their own cybersecurity labeling programs and have experience working with manufacturers and IoT conformity and standards testing, expediting the ability to provide consumers with a simple way to understand the relative security of the products and devices they purchase under a government-backed standard.
42. We recognize, however, that there is a need for a common interface between the CLAs and the Commission to facilitate ease of engagement and to conduct other initial tasks associated with the launch of the program. We delegate authority to PSHSB to review CLA applications, review CLA applications that also request consideration for Lead Administrator, select the Lead Administrator and manage changes in the Lead Administrator.
43. Lead Administrator Duties. The Lead Administrator will undertake the following duties in addition to the CLA duties outlined below:
a. interface with the Commission on behalf of the CLAs, including but not limited to submitting to the Bureau all complaints alleging a product bearing the FCC IoT Label does not meet the requirements of the Commission's labeling program;
b. conduct stakeholder outreach as appropriate;
c. accept, review, and approve or deny applications from labs seeking recognition as a lab authorized to perform the conformity testing necessary to support an application for authority to affix the FCC IoT Label, [ 6 ] and maintain a publicly available list of Lead Administrator-recognized labs and a list of labs that have lost their recognition;
d. within 90 days of release of the Public Notice announcing the Lead Administrator selection, the Lead Administrator shall, in collaboration with stakeholders ( e.g., cyber experts from industry, government, and academia) as appropriate:
i. submit to the Bureau recommendations identifying and/or developing the technical standards and testing procedures for the Commission to consider with regard to at least one class of IoT products eligible for the IoT Labeling Program. The Bureau will evaluate the recommendations, and if the Bureau approves of the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules;
ii. submit to the Bureau a recommendation on how often a given class of IoT products must renew their request for authority to bear the FCC IoT Label, which may be dependent on the type of product, and that such a recommendation be submitted in connection with the relevant standards recommendations for an IoT product or class of IoT products; The Bureau will evaluate the recommendations, and if the Bureau approves of the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules;
iii. submit to the Bureau recommendations on the design of the FCC IoT Label, including but not limited to labeling design and placement ( e.g., size and white spaces, product packaging.) The Bureau will evaluate the recommendations, and if the Bureau approves of the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules; and
iv. submit to the Bureau recommendations with regard to updates to the registry including whether the registry should be in additional languages, and if so, to recommend specific languages for inclusion;
v. submit to the Bureau recommendations on the design of the FCC IoT Label, including but not limited to labeling design and placement ( e.g., size and white spaces, product packaging, whether to include Start Printed Page 61251 the product support end date and other security and privacy information on the label.) The Bureau will evaluate the recommendations, and if the Bureau approves of the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules.
e. The Lead Administrator shall, in collaboration with CLAs and other stakeholders ( e.g., cyber experts from industry, government, and academia) as appropriate recommend within 45 days of publication of updates or changes to NIST guidelines, or adoption by NIST of new guidelines, to the FCC any appropriate modifications to the Labeling Program standards and testing procedures to stay aligned with the NIST guidelines;
f. submit to the Commission reports on CLAs' post-market surveillance activities and findings in the format and by the date specified by PSHSB;
g. develop in collaboration with stakeholders a consumer education campaign, submit the plan to the PSHSB, and participate in consumer education;
h. receive complaints about the Labeling Program, including but not limited to consumer complaints about the registry and coordinate with manufacturers to resolve any technical problems associated with consumers accessing the information in the registry;
i. facilitate coordination between CLAs; and
j. submit to the Commission any other reports upon request of the Commission or as required by Commission rule.
44. Cybersecurity Label Administrator Duties. CLA(s) are responsible for various administrative duties, including:
a. receive and evaluate applications and supporting data requesting authority to use the FCC IoT Label on the product subject to the application;
b. grant an application only if it meets all of the Commission's requirements to use the FCC IoT Label and authorize ( i.e., certify) the applicant to use the FCC IoT Label on the product subject to the application;
c. ensure that manufacturers make all required information accessible by the IoT registry;
d. participate in consumer education campaign in coordination with the Lead Administrator;
e. perform post-market surveillance activities, such as audits, in accordance with ISO/IEC 17065 and submit periodic reports to the Lead Administrator of their post-market surveillance activities and findings in the format and by the date specified by PSHSB; and
f. receive complaints alleging an IoT product does not support the cybersecurity criteria conveyed by the Cyber Trust Mark and refer these complaints to the Lead Administrator which will notify PSHSB. [ 7 ]
45. The record supports the use of CLAs to support a variety of tasks within the program's construct. ioXt Alliance supports utilizing CLAs for evaluating and certifying products for the Cyber Trust Mark. CTA supports utilizing CLAs to conduct program operations. The Cybersecurity Coalition and Kaiser Permanente also support utilizing CLAs for managing the day-to-day operations of the IoT Labeling Program. CSA argues that, “the day-to-day administration of the Cyber Trust Mark Program should be managed by a Third-Party Administrator, serving as the entity that grants permission to use the Program trademark to applicants.” In addition, ITI recommends that it should be the responsibility of the CLA to review or audit self-attestations and that “third-party administrators can and should play a key role in administering conformity assessment schemes.” CSA and CTIA further recommend adopting the IoT Labeling NPRM's proposal that a third-party administrator evaluate, accredit, or recognize the CyberLABs, and CSA also “recommends that the Commission hire a third-party administrator to operate the IoT Registry.” Finally, ioXt Alliance recommends that third-party administrators should also “vet companies and products during the certification process” to determine which products pose a threat to national security, based on Commission guidance. ioXt Alliance also notes in its comments that the “label design and associated information should be informed by the expertise of manufacturers and third-party administrators.”
46. Subject to Commission oversight, and consistent with recommendations in the record, the CLAs will evaluate and grant or deny requests for authority to use the FCC IoT Label on consumer IoT products in accordance with the IoT Labeling Program. Each administrator will be responsible for certifying that the consumer IoT products for which it authorizes a manufacturer to apply the FCC IoT Label are tested by an accredited testing lab, which as discussed further below may be a CyberLAB, the applicant's own in-house lab, or a CLA-run lab, and that the testing report demonstrates the product conforms to all Commission IoT labeling rules. The CLA will track each application it receives requesting authority to use the FCC IoT Label, and the disposition of all applications, including date of filing, date of acceptance as complete, the date and reason application is returned to applicant, and date of grant or denial. The CLAs will review each application they receive to ensure the application and supporting documents are provided and are sufficient to show the product conforms to all Commission rules and that it includes a compliance test report generated by an accredited and Lead Administrator-recognized testing lab ( e.g., third-party lab (CyberLAB), applicant's in-house testing lab, or CLA-run lab). If the application is deficient, it will not be granted until all necessary conditions are satisfied. If the application is complete and meets all of the Commission's requirements, the CLA will issue a cybersecurity labeling authorization ( i.e., cybersecurity certification) approving the applicant to affix the FCC IoT Label to the identified product.
47. In addition to its role as a CLA, the Lead Administrator must collaborate with CLAs and other stakeholders ( e.g., cyber experts from industry, government, and academia) as appropriate to develop or identify, and maintain, consumer IoT cybersecurity technical and conformity assessment standards to be met for each class of IoT product seeking authority to affix the FCC IoT Label on their product, which the Lead Administrator will submit to PSHSB for consideration and approval and, subject to any required public notice and comment, adoption into its rules. Adopting standards through consensus is supported by the record in this proceeding. [ 8 ] The Information Technology Industry Counsel (ITI) supports the Commission retaining ownership of the IoT Labeling Program and authorizing the “various industry-led, consensus standards, which can be used to gain approval for the Cyber Trust Mark.” ITI also notes that using industry-led, consensus standards will also limit the likelihood of legal challenges. UL Standards & Engagement Start Printed Page 61252 agrees that the FCC should use a “voluntary consensus-based standards development process” to create and update standards for the IoT Labeling Program. The U.S. Chamber of Commerce also supports a consensus-based approach urging the Commission “to track closely with public-private developments in IoT cybersecurity as well as industry-driven initiatives, such as the C2 Consensus on IoT Device Security Baseline Capabilities (C2 Consensus) and CTIA's cybersecurity certification program for IoT devices.” The Council to Secure the Digital Economy (CSDE), which is “composed of USTelecom, the Consumer Technology Association (CTA), and 13 global information and communications technology (ICT) companies—has also already convened technical experts from 19 leading organizations throughout the ICT sector to develop and advance industry consensus on baseline security capabilities for new devices,” including the C2 Consensus document, which provides guidance to the public and private sectors on IoT devices security. We agree with these recommendations that the Commission adopt standards following recommendations based on an industry-led consensus process, leveraging standards work already in process or completed, which will provide for the swift development and implementation of the IoT Labeling Program.
48. The Lead Administrator is to base the recommended technical standards and testing procedures on the NISTIR 8425, Profile of the IoT Core Baseline for Consumer IoT Products. As noted by ITI, there is “a suite of existing standards that might be leveraged to ensure that the outcomes NIST outlines can be met.” In addition, NIST's IoT Product Component Requirements Essay provides a summary of standards and guidance that NIST has initially identified as applicable to IoT devices and IoT product components, that the Lead Administrator may determine are applicable to the IoT Labeling Program. The Lead Administrator should evaluate and leverage existing work for efficiency and speed to market where appropriate in making its recommendations to the Commission.
49. The Lead Administrator in collaboration with stakeholders as appropriate will identify or develop IoT cybersecurity standards (or packages of standards) and testing procedures that they determine can be used to test that a product meets the NISTIR 8425 criteria for each class of products identified by the working group. The Lead Administrator will submit to the Bureau recommendations on a rolling basis as they are identified, but shall submit the initial set of recommendations no later than 90-days after release of the Public Notice selecting the Lead Administrator. We specify a timeframe here to ensure timeliness of initial standards and prompt launch of the program. Noting the work already ongoing on these issues, we also find such a timeframe to be reasonably achievable. The proposed standards (or packages of standards) and testing procedures must be approved by the Commission prior to implementation. The Commission delegates authority to PSHSB to evaluate and (after any required public notice and comment) approve (or not approve) the technical standards and testing procedures proposed by the Lead Administrator for use in the IoT Labeling Program and incorporate the approved standards and testing procedures by reference into the Commission's rules. The Commission further directs the Bureau to ensure the standards and testing procedures are relevant and appropriate to support the Commission's IoT Labeling Program.
50. Selecting CLAs. Each entity seeking authority to act as a CLA must file an application with the Commission for consideration by PSHSB, [ 9 ] which includes a description of its organization structure, an explanation of how it will avoid personal and organizational conflict when processing applications, a description of its processes for evaluating applications seeking authority to use the FCC IoT Label, and a demonstration of expertise that will be necessary to effectively serve as a CLA including, but not limited to:
1. Cybersecurity expertise and capabilities in addition to industry knowledge of IoT and IoT labeling requirements.
2. Expert knowledge of NIST's cybersecurity guidance, including but not limited to NIST's recommended criteria and labeling program approaches for cybersecurity labeling of consumer IoT products.
3. Expert knowledge of FCC rules and procedures associated with product compliance testing and certification.
4. Knowledge of Federal law and guidance governing the security and privacy of agency information systems.
5. Demonstration of ability to securely handle large volumes of information and demonstration of internal security practices.
6. Accreditation pursuant to all the requirements associated with ISO/IEC 17065 with the appropriate scope. [ 10 ] We recognize that CLAs cannot obtain accreditation to the FCC scope until after the Commission adopts standards and testing procedures. As such, the Commission will accept and conditionally approve CLA applications from entities that meet the other FCC program requirements and commit to obtain ISO/IEC 17065 accreditation with the appropriate scope within six (6) months of the effective date by the adopted standards and testing procedures. CLA approval to authorize use of the FCC IoT Label will be finalized upon receipt and demonstration to the Commission of ISO/IEC 17065 accreditation with the appropriate scope. [ 11 ]
7. Demonstrate implementation of controls to eliminate actual or potential conflicts of interests (including both personal and organizational), particularly with regard to commercially sensitive information, to include but not limited to, remaining impartial and unbiased and prevent them from giving preferential treatment to certain applications ( e.g., application line jumping) and from implementing heightened scrutiny of applications from entities not members or otherwise aligned with the CLA.
8. That the applicant is not owned or controlled by or affiliated with any entity identified on the Commission's Covered List or is otherwise prohibited from participating in the IoT Labeling Program. We will dismiss all CLA applications from an entity (company) identified on the Commission's Covered List, the Department of Commerce's Entity List, and the Department of Defense's List of Chinese Military Companies.
9. That the applicant is not owned or controlled by or affiliated with any person or entity that has been suspended or debarred from receiving Start Printed Page 61253 Federal procurements or financial awards, to include all entities and individuals published as ineligible for award on the General Service Administration's System for Award Management.
10. In addition to completing the CLA application information, entities seeking to be the Lead Administrator will submit a description of how they will execute the duties of the Lead Administrator, including:
a. their previous experience in IoT cybersecurity;
b. what role, if any, they have played in IoT labeling;
c. their capacity to execute the Lead Administrator duties outlined in the Order;
d. how they would engage and collaborate with stakeholders to identify or develop the Bureau recommendations discussed in the Order;
e. a proposed consumer education campaign; and
f. additional information the applicant believes demonstrates why they should be the Lead Administrator.
51. For items #7 and #8, we note that the record raises national security considerations when selecting a Label Administrator. For example, CTIA urges that the Commission “exclude all entities on the Covered List (not just those included on the list for producing equipment), all entities on the other lists identified in the IoT Labeling NPRM, as well as entities that are otherwise banned from federal procurement.” CTIA explains that these broad exclusions for program participation are necessary because of “the unique nature of the proposed labeling program—namely that it is both government-administered and voluntary—counsels in favor of painting with a broad brush on national security-based exclusions.” We agree with the commenters in the record, and consistent with our reasoning herein addressing the exclusion of certain products that would raise potential national security concerns, we also prohibit entities owned or controlled by or affiliated with entities that produce equipment found on the Covered List, as well as entities specified on the other lists referenced above or those suspended or debarred from receiving Federal procurements or financial awards from being a CLA in view of national security considerations and to insure the integrity of the IoT Labeling Program. Each of these lists represent the determination of relevant Federal agencies that the entities on the list may pose a national security threat within their respective areas, and as such we find that it is not in the public interest to permit these entities to provide assurances to the American public that products meet minimum cybersecurity standards. Importantly, we are only excluding the entities of the lists from a voluntary program under which the FCC approves their capability to oversee cybersecurity certification testing for purposes of the IoT Label. Insofar as the FCC IoT Label reflects the FCC's signal to consumers about cybersecurity, it is reasonable for us to take a cautious approach when approving entities to conduct the underlying product evaluations when relevant Federal agencies have expressed security concerns with the entity.
52. NCTA—The Internet & Television Association (NCTA) also suggests that “any `foreign entity of concern' as defined by the CHIPS Act should be ineligible for certification or recognition as a CyberLAB.” Further, ioXt Alliance recommends that the Commission “establish rules to ensure CyberLABs are not subject to undue influence by foreign adversaries.” We agree that it would be problematic for the U.S. to rely on the determination of entities controlled or affiliated with “foreign adversaries” as to the security of products approved to use the Cyber Trust Mark, and therefore the FCC will not recognize for purposes of the IoT Labeling Program any applicant that is an entity, its affiliate, or subsidiary owned or controlled by a “foreign adversary” country. A “foreign adversary” country is defined in the Department of Commerce's rule, 15 CFR 7.4 , and includes China (including Hong Kong), Cuba, Iran, North Korea, Russia, and Maduro Regime. We do not otherwise see a basis to preclude other foreign entities from serving as CLAs, but at this preliminary stage of establishing the IoT Labeling Program—where no international agreements are yet in place in this regard, and oversight details continue to be effectuated—we defer action in this regard. We delegate authority to PSHSB, in consultation with the Office of International Affairs (OIA), to evaluate and (after any appropriate public notice and comment) establish qualification criteria for any entity outside the United States to be approved to act as a CLA once any appropriate international agreements or other appropriate prerequisites are in place.
53. We decline to require that a CLA be a non-profit. The Cybersecurity Coalition recommends that the CLA be a non-profit entity, but did not elaborate on why, focusing their comments on having a neutral, independent third-party that followed consistent pricing guidelines and had industry experience and strong security practices. Researchers from the Northeastern University's College of Engineering similarly agreed that the Label Administrator should be a non-profit while emphasizing that the CLA should not have conflicts of interest. We decline, however, to require that the CLA be a non-profit organization, recognizing that there may be well-qualified companies that may be for-profit organizations or non-profit organizations that possess the other relevant qualifications. We agree with what appear to be the underlying concerns of the record, that the CLA be neutral, have the knowledge outlined above ( e.g., knowledge regarding FCC rules, IoT cybersecurity standards and testing procedures), and be free of conflicts. However, we believe that a company that satisfies the above requirements could carry out the CLA duties without being a non-profit organization. Moreover, expanding the pool of potential participants should increase the likelihood that a reasonable number of qualified entities apply to fulfill the specified roles. In addition, the record did not highlight reasons why a for-profit company would be incapable of fulfilling the role of label administrator.
54. Termination of CLA Authority. To address national security concerns, the authority of CLAs to grant applications to use the FCC IoT Label under the IoT Labeling Program will automatically terminate if the CLA subsequently becomes owned or controlled by or affiliated with an entity that produces equipment found on the Covered List, or otherwise added to any exclusionary list identified in this item as precluding authorization as a CLA. In addition, a CLA's authority may also be terminated for failure to uphold the required competencies or accreditations enumerated above. We delegate authority to PSHSB, to determine if a CLA's authority is to be terminated in the latter circumstance, and to terminate such authorization. [ 12 ] PSHSB, may identify such CLA deficiencies itself or receive notice from other entities, including other agencies, consumers, Start Printed Page 61254 and industry, that products granted authorization by a CLA do not accurately reflect the security posture of the product. Products authorized to use the FCC IoT Label by a disqualified CLA will be subject to the disqualification procedures described further below.
55. CLA Application Filing Window. We delegate authority to the Bureau to issue a Public Notice opening the initial filing window to receive applications from entities seeking authority to be recognized as a CLA (and Lead Administrator) under the IoT Labeling Program with instructions on how to apply and further details on the qualifications required of CLA applicants as well as the decision criteria used to select applicants. We also delegate to the Bureau authority to open additional filing windows or otherwise accept additional applications for authority to be recognized by the Bureau as a CLA when and as the Bureau determines it is necessary. Interested parties must establish they meet the requirements established in the Order. The Commission notes that it may refer applications to the U.S. Committee for the Assessment of Foreign Participation in the U.S. Telecommunications Sector (Team Telecom) for their review and consideration of national security and law-enforcement risks. We further delegate authority to PSHSB in coordination with the Office of the Managing Director (OMD) (specifically Office of the Chief Information Officer) and, to the extent necessary, the Office of General Counsel (OGC) (specifically the Senior Agency Official for Privacy), to receive and review each application for compliance with the criteria established in the Order. We also delegate to PSHSB authority to adopt additional criteria and administrative procedures necessary to efficiently select one or more independent, non-governmental entities, to act as CLA(s) and Lead Administrator. The Lead Administrator must provide equitable recommendations to the Commission to encourage the broadest possible participation of CLAs within the parameters of the FCC's rules. [ 13 ] We also delegate to PSHSB authority to adopt additional criteria and procedures in the event the Lead Administrator must be replaced or chooses to withdraw from its responsibilities. [ 14 ] We delegate authority to PSHSB to release a Public Notice announcing the CLA(s) selected by the Bureau and next steps for each entity, including but not limited the execution of appropriate documentation governing the details of the CLA's responsibilities. Moreover, we delegate to PSHSB and OMD authority to take any necessary steps, including adoption of additional procedures and any applicable fees after selection of the CLAs, if necessary to ensure compliance with the Communications Act or applicable government-wide statutes that are implicated by the IoT Labeling Program. Finally, we also delegate authority to PSHSB and OMD, in consultation with OGC, to take any additional actions necessary to preserve the Commission's rights to the Cyber Trust Mark under trademark and other applicable laws. Only entities who have followed the procedures required by PSHSB and OMD and executed relevant required documentation will be authorized by the Commission to accept and grant applications authorizing the use of the FCC IoT Label, which includes the Cyber Trust Mark and QR Code.
56. The Commission envisioned the role of CyberLABs as assessing IoT devices or products for compliance against IoT security standards, once developed. The Commission sought comment on whether the Commission or one of the authorized label administrators would evaluate, accredit, or recognize the CyberLABs, noting that it was seeking to ensure that CyberLABs have the necessary expertise and resources to properly test and assess whether IoT devices and products are in compliance with the IoT security standards. To become accredited and FCC-recognized for the proposed IoT Labeling Program, the Commission proposed the submission of applications demonstrating the applicant CyberLAB met the following requirements:
- Qualifications: The CyberLAB has technical expertise in cybersecurity testing and conformity assessment of IoT devices and products.
- Resources: The CyberLAB has the necessary equipment, facilities, and personnel to conduct cybersecurity testing and conformity assessment of IoT devices and products.
- Procedures: The CyberLAB has documented procedures for conformity assessment.
- Continued competence: Once accredited and recognized, CyberLABs would be periodically audited and reviewed to ensure they continue to comply with the IoT security standards and testing procedures.
57. We adopt our proposal to accept CyberLABs, in-house labs, and CLA-run labs, to test and assess IoT products for compliance with the consumer IoT standards that are established pursuant to the process described above to actualize the outcome of the NIST criteria. Rather than having the Commission or CLA evaluate or accredit a lab, however, we are persuaded that it is appropriate to recognize testing labs that have been accredited to ISO/IEC 17025 standards to conduct compliance testing that would support an application for authority to affix the FCC IoT Label. Consistent with standard practice for accreditation, the organization accrediting the testing labs must be recognized by the Bureau to perform such accreditation based on International Standard ISO/IEC 17011. We recognize that labs cannot be accredited or recognized in the context of this IoT Labeling Program until after the IoT cybersecurity standards have been approved by the Commission and incorporated into the Commission's rules. We delegate authority to PSHSB to publish a Public Notice, subject to any required notice and comment, outlining the specific standards CyberLABs, in-house labs, and CLA-run labs must meet to be recognized as qualified to conduct conformity testing to support applications seeking authority to use the FCC IoT Label. We also find it to be in the public interest for the Lead Administrator to review and recognize labs that meet these accreditation requirements and make a list of recognized labs publicly available. [ 15 ]
58. The Order agrees with CTIA that entities specializing in testing and certification will be valuable to program participants, and that such entities are likely to have the resources and expertise to evaluate IoT products in accordance with a standard. CTIA also notes, “a third-party certification model will help to lend credibility to the program” because CyberLABs can focus on the assessment aspects of the program in a way that helps ensure the Start Printed Page 61255 integrity of the IoT Labeling Program. The Order also agrees with CTA that leveraging accredited industry bodies to perform conformity assessments will “speed the establishment of the program and increase the program's ultimate quality.”
59. We agree with CSA's argument that the Commission should adopt a model where CyberLABs must be ISO/IEC 17025 accredited. CSA notes its confusion as to whether CyberLABs were intended to be “certification bodies” as defined by ISO/IEC 17065 or “evaluation laboratories” as defined by ISO/IEC 17025. We clarify that the proposal as envisioned by the IoT Labeling NPRM and adopted here is for CyberLABs, in-house labs, and CLA-run labs to function as a body responsible for assessing the security of IoT products ( i.e., testing lab). CSA proposes that such bodies hold ISO/IEC 17025 accreditations, as this model has been the basis for mutual recognition agreements in the cybersecurity industry, and we agree.
60. We note the objection of LG Electronics, which asserts that “[t]he CyberLAB concept described in the NPRM would almost certainly create a testing bottleneck” that would slow the process, and deter participation in the IoT Labeling Program. Instead, LG Electronics argues, self-certification is required to avoid these problems, although LG Electronics concedes that some compliance certification is required to participate in the IoT Labeling Program. As a nascent program, and as discussed above in connection with the envisioned process, we do not find it appropriate to adopt at this time a labeling path that does not include some level of laboratory testing in combination with an application to a CLA to ensure the product bearing the FCC IoT Label complies with the IoT Labeling Program's requirements. However, we recognize the benefits of time, efficiency and cost-savings associated with in-house testing and will allow the option for applicants to use an in-house testing labs, provided the lab is ISO/IEC 17025 accredited.
61. CyberLABs' Programmatic Role. CyberLABs will receive requests for conformance testing from manufacturers seeking to use the FCC IoT Label and will assess and test the products using the cybersecurity standards developed by industry and approved by the Commission and provide the applicant with a report of their findings. There was confusion in the record with how the term CyberLAB is to be applied. The Commission clarifies that the CyberLABs are laboratories whose role is limited to conducting compliance tests and generating reports. CyberLABs are not, in the organizational structure adopted in the Order, either certifying products or issuing authorization to use the FCC IoT Label. While the IoT Labeling NPRM defined a CyberLAB as an “authorization body” we remove that reference here as the term “authorization body” might be seen as referring to certification bodies, not laboratories. The role of CyberLABs is to conduct the required tests and generate test reports for use by the applicant in seeking CLA authorization to use the FCC IoT Label.
62. In-House Testing Lab. We also adopt an option for manufacturers to use an accredited and Lead Administrator-recognized in-house testing lab to perform the cybersecurity conformity testing for their IoT products, provided the in-house lab meets the same vigorous standards as the CyberLABs. In the IoT Labeling NPRM, the Commission sought comment on whether there is an avenue for “a comprehensive review that an IoT device or product compl[ies] with the IoT security standards.” We received significant support in the record for an in-house testing option. Samsung argues that, to encourage widespread adoption, the Commission must allow manufacturers an option to perform in-house testing to receive the label. The Cybersecurity Coalition urges the Commission to allow for in-house testing. We agree that an in-house testing option, for some manufacturers, will be more cost-effective, encourage participation in the IoT Labeling Program, and when combined with the filing of an application with a CLA can assure quality and trust in the IoT Labeling Program. However, we do require that in-house labs meet the same accreditation and recognition requirements as CyberLABs. In this respect, consumers may be assured that the label achieved on an in-house basis meets the same standards as those tested elsewhere, promoting consistency and reliance on the IoT Labeling Program generally. We also expect that ensuring a common baseline testing standard will ultimately aid in the ability to gain international recognition of the Cyber Trust Mark.
63. CLA-Run Testing Lab. We also recognize that CLAs may also have, or seek to have, their own in-house labs conduct conformity testing for applicants seeking certification to use the Mark. The Commission finds no need to limit the number of potential testing facilities by prohibiting CLA-run labs from also being considered recognized labs. Applicants who wish to do so, may file an application with an authorized CLA and request the services of the CLA's accredited and Lead Administrator-recognized lab. Again, the Commission requires CLA labs to meet the same accreditation and recognition requirements as CyberLABs. Only after a lab has been accredited by a recognized accreditation body may the lab file an application with the Lead Administrator seeking to be recognized as an approved cybersecurity testing lab. [ 16 ] As explained by the American Association for Laboratory Accreditation (A2LA), “[a]ccreditation is a means of determining the technical competence of conformity assessment organizations such as laboratories using qualified, third-party accreditation bodies. It assures federal government agencies as well as private sector organizations that assessments conducted by accreditation bodies are objective and reliable and that one can have confidence in the data generated by the accredited testing laboratory.” Recognizing that, whether an IoT product is evaluated by a CyberLAB, CLA-run lab, or an in-house lab there is a need to ensure equal rigor in the process, this requirement applies to in-house testing labs and third-party testing labs (CyberLABs and CLA-run labs). For ease of understanding, when we refer to CyberLABs below, we are including CyberLABs, in-house testing labs, and CLA-run labs.
64. In order to achieve recognition by the Lead Administrator, all labs seeking recognition under the Commission's IoT Labeling Program must submit evidence of accreditation in the form of an attestation from an accreditation body that the prospective lab has demonstrated:
1. Technical expertise in cybersecurity testing and conformity assessment of IoT devices and products. Compliance with all requirements associated with ISO/IEC 17025. If we determine that other ISO standards or other relevant requirements are missing, the Commission will provide guidance to industry on how they may be addressed. Start Printed Page 61256
2. Knowledge of FCC rules and procedures associated with IoT cybersecurity compliance testing and certification.
3. Necessary equipment, facilities, and personnel to conduct cybersecurity testing and conformity assessment of IoT devices and products.
4. Documented procedures for IoT cybersecurity conformity assessment.
5. Demonstrated implementation of controls to eliminate actual or potential conflicts of interests (including both personal and organizational), particularly with regard to commercially sensitive information.
6. That the applicant is not owned or controlled by or affiliated with any entity that produces equipment on the FCC Covered List or is otherwise prohibited from participating in the IoT Labeling Program. We will dismiss all applications from a company named on the Department of Commerce's Entity List, the Department of Defense's List of Chinese Military Companies.
7. That the applicant is not owned or controlled by or affiliated with any person or entity that has been suspended or debarred from receiving Federal procurements or financial awards, to include all entities and individuals published as ineligible for award on the General Service Administration's System for Award Management.
65. Once accredited and recognized, the lab will be periodically audited and reviewed by the Lead Administrator to ensure they continue to comply with the IoT security standards and testing procedures.
66. Concerning items #6 and #7, national security considerations must be considered when allowing testing labs to participate because of “the unique nature of the proposed labeling program.” As recommended in the record and consistent with our exclusions as to eligible products and eligibility to serve as a third-party administrator, all entities owned or controlled by or affiliated with entities that produce equipment found on the Covered List, as well as entities specified on the other U.S. Government exclusionary lists referenced above are prohibited from serving as a CyberLAB. Each of these lists represent the determination of relevant Federal agencies that the entities on the list may pose a national security threat within their respective areas, and as such we find that we cannot give U.S. Government endorsement to their security testing while claiming they pose such a threat. Insofar as the label reflects the FCC's signal to consumers about cybersecurity, it is reasonable for the FCC to take a cautious approach especially for those products for which relevant Federal agencies have expressed other security concerns with the testing lab.
67. NCTA also suggests also suggests that “any `foreign entity of concern' as defined by the CHIPS Act should be ineligible for certification or recognition as a CyberLAB.” Further, ioXt Alliance recommends that the Commission “establish rules to ensure CyberLABs are not subject to undue influence by foreign adversaries.” We agree that it would be problematic for the U.S. to rely on the determination of entities controlled or affiliated with “foreign adversaries” as to the security of products approved to use the Cyber Trust Mark, and therefore the Lead Administrator will not recognize for purposes of the IoT Labeling Program any testing lab that is an entity, its affiliate, or subsidiary owned or controlled by a “foreign adversary” country. A “foreign adversary” country is defined in the Department of Commerce's rule, 15 CFR 7.4 , and includes China (including Hong Kong), Cuba, Iran, North Korea, Russia, and Maduro Regime. Because of the role CLAs will play in the labeling program, we find that the concerns related to entities identified as “foreign adversaries” are equally applicable to entities acting as CLAs as they are testing labs. To avoid these issues, the record suggests requiring testing labs certify compliance with the Commission's rules, including the rules pertaining to the Covered List. Accordingly, we find it appropriate that each testing lab must certify to the truth and accuracy of all information included in its recognition application and immediately update the information if the information changes.
68. The Order notes that Garmin advocates even stricter measures on the testing labs, suggesting that the labs be “located in the U.S.” We decline to require physical location within the U.S. to avoid “unnecessarily limiting the pool of legitimate CyberLABs approved to conduct testing and conformity assessment for the Mark.” Further, the record indicates that this stricter approach “would vastly diminish manufacturers' abilities to select and access evaluation labs, conduct proper risk management and promote competition and diversity in the lab market.” Such a restriction might also unduly limit the ability of legitimate foreign corporations that do not raise national security concerns to participate in the IoT Labeling Program to the detriment of the goal of elevating the cybersecurity posture of those IoT devices sold in the U.S. and to promote international recognition of the Cyber Trust Mark. We delegate authority to the Bureau to adopt any additional criteria or procedures necessary with respect to labs located outside of the United States.
69. Terminating CyberLAB Testing Authority. To address national security concerns, the CyberLAB recognition afforded to entities under this IoT Labeling Program will be automatically terminated for entities that subsequently become affiliated with an entity that is owned or controlled by or affiliated with entities that produce equipment placed on the Covered List, or that are otherwise added to any exclusionary list identified in this item as precluding authorization as a CyberLAB. CyberLAB testing authority may also be terminated for failure to uphold the required competencies or accreditations enumerated above. We delegate authority to the Bureau to determine when a CyberLAB's authority is to be terminated, and to terminate such authorization. [ 17 ] The Bureau may identify such deficiencies itself or receive notice from other entities, including other agencies, consumers, and industry, that products tested by a CyberLAB do not accurately reflect the security posture of the product. Products authorized to use the FCC IoT Label by a disqualified CyberLAB will be subject to the disqualification procedures described further below.
70. Fees. To fulfill their role, as envisioned by the IoT Labeling NPRM, we authorize CyberLABs to charge reasonable fees to conduct the tasks adopted in the Order. The IoT Labeling NPRM proposed a fee calculation methodology adopted by the Commission in the 2020 Application Fee Report and Order, 86 FR 15026 (March 19, 2021), and sought comment on whether any oversight is needed by the Commission over such charges. We did not receive any comments on the suitability of the approach proposed in the IoT Labeling NPRM or detailed comments about the degree of oversight the Commission should conduct over Start Printed Page 61257 the charges. We recognize the Cybersecurity Coalition's comments that high fees would deter participation in the IoT Labeling Program. We anticipate that there will be multiple CyberLABs authorized through the approach adopted in the Order, and we believe that market competition will ensure fees are reasonable, competitive, and accessible while covering the costs incurred by the CyberLABs in performing their designated tasks. We believe this addresses the concerns raised by the Cybersecurity Coalition and renders the approach proposed in the IoT Labeling NPRM unnecessary. The National Association of Manufacturers (NAM) rightly indicates, however, that the fee structure for CyberLABs will necessitate “robust protections to ensure that CyberLABs focus on the underlying mission of protecting the public rather than boosting their revenues.” We delegate to the Bureau, in connection with OMD, to review and reconsider if necessary whether the level and structure of the fees should be regulated by the Commission.
71. The Commission adopts a two-step process for a manufacturer seeking authority to use the FCC IoT Label, which includes (1) product testing by an accredited and Lead Administrator-recognized lab ( e.g., CyberLAB, CLA lab, or an in-house lab) and (2) product label certification by a CLA. In the context of this IoT Labeling Program and as discussed in detail below, we find that in order to ensure the integrity of this nascent program, that the FCC IoT Label certification process will include a two-step process involving (1) the use of an accredited and Lead Administrator-recognized laboratory (CyberLAB, CLA lab, or in-house lab) to test the IoT product for compliance to FCC rules and generate a test report; and (2) an application to an FCC-recognized CLA ( i.e., an accredited certification body) to certify the product as fully compliant with all relevant FCC IoT Labeling Program rules.
72. The record is split on the processes the Commission should adopt for manufacturers to follow when seeking to use the FCC IoT Label, specifically with regard to whether it is necessary for a third-party to review and verify the product meets all of the IoT Labeling Program requirements, including product testing, or if the manufacturer should be afforded the opportunity to “self-declare” compliance and affix the FCC IoT Label without third-party verification.
73. UL Solutions, TÜV SÜD, and TIC Council Americas recommend that the Commission require all applications to be supported by conformity testing conducted by an accredited lab ( e.g., ISO/IEC 17025 accredited), and submitted to a third-party for verification of compliance with the Commission's program requirements. Others argue the Commission should accept a declaration of conformity or self-certification, while others recommend the Commission enter into agreements with each manufacturer to allow the manufacturer to conduct internal conformity testing of its products and self-certify compliance with the Commission's program requirements resulting in approval to use the Cyber Trust Mark without third-party involvement. CTA, for example, contemplates a “Manufacturer Self-Attestation Process” where manufacturers apply to the Commission for access to a “Mark Self-Attestation License Agreement” between the manufacturer and the FCC. Under this process, the manufacturer provides documentation showing how it complies with the NIST Criteria and if the Commission agrees with the documentation, the parties execute the agreement. The license agreement will identify the limits of the manufacturer's license authority, which may be corporate-wide, on a divisional basis, or for a specific product line.
74. To ensure the Cyber Trust Mark retains the highest level of integrity and consumer trust, we agree with commenters who caution against allowing testing by entities that are not accredited and recognized. We also agree with Garmin and AHAM, who recommend third-party verification of the information contained in a manufacturer's application to use the Cyber Trust Mark. UL Solutions notes that while the Commission's equipment authorization process allows some products that pose a low risk of RF interference to be approved via a Supplier's Declaration of Conformity (SDoC), there is no clear line to be drawn between low risk and high risk connected products when “IoT devices are significant targets for an ever- growing number of cybersecurity attacks.” In addition, UL Solutions points to the investigation conducted by the Government Accountability Office (GAO) into the ENERGY STAR program's initial reliance a supplier's declaration of conformity, which GAO found to be unreliable because GAO was able to obtain UL certification with blatantly non-conforming products.
75. The Commission disagrees with commenters who believe the IoT Labeling Program should offer different methods of conformity assessment based on varying levels of risk and potential impact on consumers because doing so adds an unnecessary and significant layer of complexity to the process. The Commission recognizes the view of Keysight, the National Electronic Manufacturers Association (NEMA), AIM, Whirlpool, AHAM, Consumer Reports, Garmin, NAM, ITI, and TIC Council Americas, who support self-attestation as an efficient and cost effective methodology for applicants to conduct conformity assessments. However, the Commission agrees with A2LA, which urges caution with self-attestations of conformity “due to the bias inherent in self-declaration.” We also take into serious consideration the 2010 GAO Report that found the ENERGY STAR program in effect at that time, which was “primarily a self-certification program relying on corporate honesty and industry self-policing to protect the integrity of the Energy Star label,” failed to require upfront third-party validation of manufacturers' self-reported claims of compliance with the program requirements, which resulted in the certification of bogus products as ENERGY STAR compliant. ENERGY STAR has since changed the manner in which it certifies products as ENERGY STAR compliant, stating that in order “[t]o ensure consumer confidence in the ENERGY STAR label and to protect the investment of ENERGY STAR partners, the U.S. Environmental Protection Agency (EPA) requires all ENERGY STAR products to be third-party certified. Products are tested in an EPA-recognized laboratory and reviewed by an EPA-recognized certification body before they can carry the label.”
76. As such, in light of the nascent nature of the IoT Labeling Program, lessons learned in the ENERGY STAR context, and the need to ensure that the Cyber Trust Mark garners sufficient trust by consumers to be viewed as providing accurate information and manufacturer participation, we find that allowing a path to “self-attestation” is not appropriate at this time. While such a path may provide for prompt time to market for the Cyber Trust Mark itself, the concerns regarding the Mark's integrity at this initial stage counsel against “self attestation.” Moreover, we anticipate that the benefits and level of efficiency afforded manufacturers by the ability to use in-house labs will mitigate the additional process associated with certification by a CLA, as discussed below.
77. We intend for the Cyber Trust Mark to serve as a reliable and trusted Start Printed Page 61258 way for consumers to quickly identify those products that meet the Commission's program requirements. To achieve this, the Commission must adopt sufficient controls over the IoT Labeling Program to ensure only those products that meet the Commission's requirements bear the Cyber Trust Mark. The Commission's second step of requiring an application be submitted to a CLA is a significant and important control to ensure that an independent disinterested third-party outside the manufacturer's control has reviewed the manufacturer's product application and supporting test report and verified that the product complies with the Commission's program requirements.
78. The second step of the application process is particularly important because, as discussed above, the Commission allows the first step (testing) to be completed by an accredited and recognized CyberLAB, a CLA lab, or the manufacturer's in-house lab. Requiring the manufacturer to submit an application with a CLA is an important control, particularly to ensure that all products, including those products whose conformity testing is conducted, and reports are generated, by the manufacturer's in-house lab, are subject to third-party scrutiny and oversight. As such, the Commission requires all entities seeking to use the FCC IoT Label must submit an application for authority to a CLA to use the FCC IoT Label that is supported by the appropriate report detailing the conformity testing conducted by a lab that is both accredited and Lead Administrator-recognized (CyberLAB, CLA lab, or manufacturer's in-house lab). Only entities who have received prior authorization from a CLA ( i.e., cybersecurity certification) are authorized to use the FCC IoT Label, which will ensure the IoT Labeling Program retains its integrity. [ 18 ] We further recognize that the CLA may charge a reasonable fee to cover the cost of reviewing the application and the costs of conducting the other tasks the CLA would perform. Once the IoT Labeling Program is established, we may revisit the issue of whether to adopt additional pathways to obtaining authority to use the FCC IoT Label.
79. The IoT Labeling NPRM sought comment on whether and how one or more third-party administrators should be utilized to manage the IoT Labeling Program, and whether the Commission should designate one or more administrators to authorize use of the label. Kaiser Permanente argues that the Commission should maintain ownership of the application process, as well as oversight and supervision of third parties administering the IoT Labeling Program. Garmin notes that the application process described in the IoT Labeling NPRM is unclear and worries that third-party involvement would require enormous effort, and cautioned that sharing sensitive information with a third-party administrator itself raises security concerns. However, the record was silent with respect to details about an application process. We agree that oversight and supervision of the IoT Labeling Program, including intaking applications, will require effort but believe a CLA is in the best position to streamline that process and, as noted, ensure the integrity of the process. We will require the CLA to have the ability to securely handle large volumes of information, which we believe should alleviate Garmin's concern. We outline the application process to use the FCC IoT Label below.
80. Before being able to display the Cyber Trust Mark, the applicant must determine their product is an eligible product under our rules; have their product tested by an accredited and Lead Administrator-recognized CyberLAB, CLA Lab, or manufacturer's in-house lab; obtain a report of conformity and compliance from the lab; and submit an application for authority to use the FCC IoT Label to an FCC-recognized CLA in accordance with their procedures. Using the CLAs' filing processes, entities seeking authority to use the FCC IoT Label will file an application to be developed by the Bureau. Each application must include a report of conformity issued by an accredited CyberLAB, accredited CLA lab, or accredited in-house lab whose testing and reporting is comparative in rigor to that completed by a CyberLAB. The CLA will review the application and supporting documentation to ensure it is complete and in compliance with the Commission's rules and will either grant or deny the application. If an application is granted, the CLA will provide the applicant with notification of the grant and authority to affix the FCC IoT Label to the product granted authorization.
81. Applications that do not meet the Commission's IoT Labeling Program will be denied by the CLA. If an application is denied, the CLA will provide the applicant with notification of the denial and an explanation of why it was denied. An applicant may only re-submit an application for a denied product if the CLA-identified deficiencies have been corrected. The applicant must indicate on its application that it is re-submitting the application after it was denied, the name of the CLA that denied the application, and the CLA's explanation of why it was denied. Failure to disclose the denial of an application for the same or substantially similar product will result in denial of the application for that product and the FCC will take other regulatory and/or legal action it deems appropriate.
82. Grant or denial of an application for authority to use the FCC IoT Label will be made by the CLA in the first instance. The CLA will return incomplete applications to the applicant or otherwise contact the applicant regarding the incomplete application, as soon as possible.
83. We delegate authority to the Bureau to issue a Public Notice after any necessary notice and public comment and after completing any process required under the Paperwork Reduction Act, providing further details on how to apply for authority to use the FCC IoT Label, including but not limited to informational elements of the application, additional details on filing requirements ( e.g., description or photograph of the label and how/where it will be affixed to the product), and how to request confidential treatment of submitted information. As the Commission anticipated in the NPRM, CLAs may charge reasonable fees for their services and to cover the costs of performing the administrative duties. The IoT Labeling NPRM proposed to follow the fee calculation methodology adopted by the Commission in the 2020 Application Fee Report and Order and requested comment on the proposal and any changes. We did not receive any comments on the suitability of this approach. We recognize the Cybersecurity Coalition's comments that high fees would deter participation in the IoT Labeling Program. We anticipate that there will be multiple administrators authorized through the approach adopted in the Order, and we believe that market competition will ensure fees are reasonable, competitive, and accessible while covering the costs incurred by the CLA in performing their designated tasks. We believe this addresses the concerns raised by the Cybersecurity Coalition and renders the approach proposed in the IoT Labeling NPRM unnecessary. We therefore reject Start Printed Page 61259 the NPRM's proposal. To the extent that the Lead Administrator may incur costs in performing its duties on behalf of the program as a whole, we expect these costs to be shared among CLAs as a whole. [ 19 ] We delegate to the Bureau, in connection with OMD, to consider these issues and provide guidance to the CLAs and Lead Administrator to ensure the fees do not become onerous, as indicated by the record.
84. Seeking Review of CLA Decision. Any party aggrieved by an action taken by a CLA must first seek review from the CLA, which must be filed with the CLA within 60 days from the date of the CLA's decision. A party aggrieved by an action taken by a CLA may, after seeking review by the CLA, seek review from the Commission. A request for Commission review must be filed with the Commission within 60 days from the date the CLA issues a decision on the party's request for review. In all cases of requests for review, the request for review shall be deemed filed on the postmark date. If the postmark date cannot be determined, the applicant must file a sworn affidavit stating the date that the request for review was mailed. Parties must adhere to the time periods for filing oppositions and replies set forth in 47 CFR 1.45 .
85. We delegate authority to PSHSB to consider and act upon requests for review of CLA decisions. Requests for review that raise novel questions of fact, law, or policy will be considered by the full Commission. An affected party may seek review of a decision issued under delegated authority pursuant to the rules set forth in part 1 of the Commission's rules. The Bureau will conduct de novo review of requests for review of decisions issued by a CLA. The Commission will conduct de novo review of requests for review of decisions by the CLA that involve novel questions of fact, law, or policy; provided, however, that the Commission will not conduct de novo review of decisions issued by the Bureau under delegated authority. The Bureau will, within 45 days, take action in response to a request for review of CLA decision that is properly before it. The Bureau may extend the time period for taking action on a request for review of a CLA decision for a period of up to 90 days. The Commission may also at any time, extend the time period for taking action of a request for review of a CLA decision pending before the Bureau. The Commission will issue a written decision in response to a request for review of a CLA decision that involves novel questions of fact, law, or policy within 45 days. The Commission may extend the time period for taking action on the request for review of a CLA decision. The Bureau also may extend action on a request for review of an CLA decision for a period of up to ninety days. While a party seeks review of a CLA decision, they are not authorized to use the FCC IoT Label until the Commission issues a final decision authorizing their use of the FCC IoT Label.
86. Technical Criteria for Consumer IoT Products. We adopt the IoT Labeling NPRM proposal that the NIST Core Baseline serve as the basis of the IoT Labeling Program. The NIST Core Baseline is based on product-focused cybersecurity capabilities (also referred to by NIST as “Outcomes”) rather than specific requirements, which NIST asserts provide the flexibility needed due to the diverse marketplace of IoT products, and we agree. As outlined in the IoT Labeling NPRM, the NIST criteria includes the following IoT product capabilities: (1) asset identification; (2) product configuration; (3) data protection; (4) interface access control; (5) software update; (6) cybersecurity state awareness; and the following IoT Product Developer Activities: (7) documentation; (8) information and query reception; (9) information dissemination; and (10) product education and awareness.
87. The record reflects broad support for adoption of the technical criteria presented in NISTIR 8425. For example, a coalition of industry stakeholders including the Association of Home Appliance Manufacturers, Connectivity Standards Alliance, Consumer Technology Association, CTIA Information Technology, Industry Council, National Electrical Manufacturers Association, Plumbing Manufacturers International Power Tool Institute, Security Industry Association, Telecommunications Industry Association, U.S. Chamber of Commerce, and USTelecom submitted a letter to the Commission supporting the establishment of “a voluntary program based on the technical criteria developed by [NIST], under NISTIR 8425.” UL Solutions supports adoption of the NISTIR 8425 criteria and asserts that there are several mature standards that can be drawn from that address the NISTIR 8425 criteria, such as UL 2900, UL 5500, and IEC 62443.
88. CTIA supports adoption of the NIST Core Baseline but urges the Commission not to prescribe any specific methodologies that testing programs or standards must use, other than to require that such programs or standards be consistent with NIST Core Baseline. CSA also supports adoption of the NIST Core Baseline but urges the Commission to refrain from developing its own standards for testing. Rather, CSA asserts that they have developed a certification program that meets the requirements of NISTIR 8425 and other relevant standards documents, including ETSI EN 303 645 and the Singapore Cybersecurity Labeling Scheme, and CTA indicates that they are working on American National Standards (ANS) documents that will “[d]efine a Framework that is a standardized and objective method of applying the Criteria in NISTIR 8425 to a candidate Scheme or to a manufacturer's proposal for self-attestation . . .” Garmin encourages the Commission to consider ETSI 303 645 standards, and commenters American Certification Body, Inc. and Consumer Reports encourage international standards such as those developed as a result of the EU Cyber Resiliency Act and UK's Product Security and Telecommunications Infrastructure Act. These commenters did not oppose referencing the NIST criteria.
89. We agree with Infineon, Consumer Reports, and NCTA and adopt NISTIR 8425 as the basis for the Commission's IoT Labeling Program. The consumer IoT environment is complicated by a significant number of different types of consumer IoT products. Adoption of the NIST criteria as the foundation of the IoT Labeling Program will result in a robust consumer IoT program that is sufficiently flexible that it can be applied across all types of consumer IoT products. The NIST criteria were developed through a multi-year effort between NIST and various stakeholders, and includes significant industry input and will continue to be updated by NIST as necessary. The Commission agrees with NIST's publication, which avers that the following NISTIR 8425 criteria identify the cybersecurity capabilities that consumers would expect manufacturers to address within the products they buy. NIST contemplates that most of the criteria concern the IoT product directly and are expected to be satisfied by software and/or hardware implemented in the IoT product (1-6 below) and other criteria apply to the IoT product developer (7-10 below). The following is the list of Start Printed Page 61260 the NIST IoT product capability criteria, NIST's brief description of each, and the NIST-identified cybersecurity utility for each:
(1) Asset Identification: The product can be uniquely identified by the customer and other authorized entities and the product uniquely identifies each IoT product component and maintains an up-todate inventory of connected product components
i. Cybersecurity Utility: The ability to identify IoT products and their components is necessary to support such activities as asset management for updates, data protection, and digital forensics capabilities for incident response.
(2) Product Configuration: The configuration of the IoT product is changeable, with an ability to restore a secure default setting, and changes can only be performed by authorized individuals, services, and other IoT product components.
i. Cybersecurity Utility: The ability to change aspects of how the IoT product functions can help customers tailor the IoT product's functionality to their needs and goals. Customers can configure their IoT products to avoid specific threats and risk they know about based on their risk appetite.
(3) Data Protection: The IoT product protects data store across all IoT product components and transmitted both between IoT product components and outside the IoT product from unauthorized access, disclosure, and modification.
i. Cybersecurity Utility: Maintaining confidentiality, integrity, and availability of data is foundational to cybersecurity for IoT products. Customers will expect that data are protected and that protection of data helps to ensure safe and intended functionality of the IoT product.
(4) Interface Access Control: The IoT product restricts logical access to local and network interfaces—and to protocols and services used by those interfaces—to only authorized individuals, services, and IoT product components.
i. Cybersecurity Utility: Enumerating and controlling access to all internal and external interfaces to the IoT product will help preserve the confidentiality, integrity, and availability of the IoT product, its components, and data by helping prevent unauthorized access and modification.
(5) Software Update: The software of all IoT product components can be updated by authorized individuals, services, and other IoT product components only by using a secure and configurable mechanism, as appropriate for each IoT product component.
i. Cybersecurity Utility: Software may have vulnerabilities discovered after the IoT product has been deployed; software update capabilities can help ensure secure delivery of security patches.
(6) Cybersecurity State Awareness: The IoT product supports detection of cybersecurity incidents affecting or affected by IoT product components and the data they store and transmit.
i. Cybersecurity Utility: Protection of data and ensuring proper functionality can be supported by the ability to alert the customer when the device starts operating in unexpected ways, which could mean that unauthorized access is being attempted, malware has been loaded, botnets have been created, device software errors have happened, or other types of actions have occurred that was not initiated by the IoT product user or intended by the developer.
The following is the list of NIST-identified IoT Product Developer Activities/Non-Technical Supporting Capabilities and their NIST-identified cybersecurity utility:
(7) Documentation: The IoT product developer creates, gathers, and stores information relevant to cybersecurity of the IoT product and its product components prior to customer purchase, and throughout the development of a product and its subsequent lifecycle.
i. Cybersecurity Utility: Generating, capturing, and storing important information about the IoT product and its development ( e.g., assessment of the IoT product and development practices used to create and maintain it) can help inform the IoT product developer about the product's actual cybersecurity posture.
(8) Information and Query Reception: The IoT product developer has the ability to receive information relevant to cybersecurity and respond to queries from the customer and others about information relevant to cybersecurity.
i. Cybersecurity Utility: As IoT products are used by customers, those customers may have questions or reports of issues that can help improve the cybersecurity of the IoT product over time.
(9) Information Dissemination: The IoT product developer broadcasts ( e.g., to the public) and distributes ( e.g., to the customer or others in the IoT product ecosystem) information relevant to cybersecurity.
i. Cybersecurity Utility: As the IoT product, its components, threats, and mitigations change, customers will need to be informed about how to securely use the IoT product.
(10) Product Education and Awareness: The IoT product developer creates awareness of and educates customers and others in the IoT product ecosystem about cybersecurity-related information ( e.g., considerations, features) related to the IoT product and its product components.
i. Cybersecurity Utility: Customers will need to be informed about how to securely use the device to lead to the best cybersecurity outcomes for the customers and the consumer IoT product marketplace.
90. Consumer IoT Product Standards. We find that standards are necessary to administer the IoT Labeling Program in a fair and equitable manner and to ensure the products with the FCC IoT Label have all been tested to the same standards to provide consumers with confidence that products bearing the FCC IoT Label include strong cybersecurity. Commenters generally agree with the adoption of standards based on NIST's Core Baseline for Consumer IoT products (NISTIR 8425). We take up the Cybersecurity Coalition's recommendation “that the Commission or a designated third-party administrator work with stakeholders to identify recognized standards that encompass the Core Baseline, or that offer equivalent controls.” NCTA also notes that “Standards Development Organizations (“SDOs”) and specification organizations are well-established organizations that can develop standards aligned with NIST guidelines and the Program's goals.” According to NIST, the NISTIR 8425 “ outcomes are guidelines that describe what is expected . . . but more specific information may be needed to define how to implement IoT products or product components so that they meet an outcome. Requirements define how a component can meet an outcome for a specific use case, context, technology, IoT product component etc. . . ..”
91. We reject CTIA's recommendation that the Commission refrain from adopting specific standards and solely rely on the NIST criteria. Rather, the Commission agrees with NIST and commenters that its criteria are general guidelines that must be further developed into a requirements document ( i.e., standards) and corresponding testing procedures, which will demonstrate how the product bearing the FCC IoT Label has met the NIST criteria and to ensure consistency of application across a class of products. ITI adds that the “Commission need not recreate [existing] work or develop its own standards but can leverage completed standards work for swift development Start Printed Page 61261 and implementation.” The integrity of the Cyber Trust Mark requires the Commission to adopt standards that provide for adequate and consistent testing of products to ensure that all products bearing the FCC IoT Label have demonstrated conformance to the identified standards that the Commission has approved as compliant with the NIST criteria. In addition, for the Commission's IoT Labeling Program to be fairly administered by the multiple CLAs, all products displaying the FCC's label must be tested against the same standards to ensure that all products displaying the FCC IoT Label conform to the Commission's standards.
92. Commenters such as TÜV SÜD agree that “the main requirement when perform[ing] testing for compliance is that the test need[s] to be reliable and always offer the same outcome when a product is tested in the same condition. In the current state of the NIST IoT criteria there is not enough detail[ ] in the standard, so there is the need to write a more detail[ed] test method/standard.” UL Solutions also “supports the use of the NISTIR 8425 criteria as the basis for the IoT Labeling Program. These criteria help establish a minimum security baseline suitable for consumer IoT products . . . However, as noted in paragraphs 27 and 28 [of the IoT Labeling NPRM ], these criteria must be defined by minimum IoT security requirements and standards to enable consistent and replicable product testing.” Moreover, Somos similarly agrees that leveraging existing standards for device definition and security guidelines are the fastest, most effective path to the definition of a secure ecosystem, that NIST 8425 standard is the appropriate starting point, and that “existing standards should allow for the Commission to quickly create its definitions and guidelines.” We agree with the Cybersecurity Coalition that “only those standards and best practices recognized by the labeling program should be eligible, in order to avoid the inclusion of non-credible or irrelevant frameworks that may undermine trust in the label.”
93. We further determine that, given the existing work in this space, the Commission should not undertake the initial development of the standards that underpin the NIST Core Baseline. Rather, as discussed in paragraph 56 above, we direct the Lead Administrator to undertake this task, and delegate authority to the Bureau to review and approve the consumer IoT cybersecurity standards and testing procedures that have been identified and/or developed by the Lead Administrator (after any appropriate public comment) that ensures the product to which a manufacturer seeks to affix the FCC IoT Label conforms to the NIST criteria. NIST's IoT Product Component Requirements Essay provides a summary of standards and guidance that NIST has initially identified as applicable to IoT devices and IoT product components, that the Lead Administrator may determine are applicable to the IoT Labeling Program. Moreover, the Lead Administrator may also determine existing standards or schemes that exist in the market already may be readily adaptable and leverage such work to meet the terms of the program.
94. The Commission recognizes that since a “product” for purposes of the IoT Labeling Program is comprised of at least one IoT device and any additional product components that are necessary to use the IoT device beyond basic operational features, there may be multiple standards ( e.g., a package of standards) applicable to a single IoT product ( e.g., standards applicable to IoT devices; mobile apps; networking equipment included with IoT devices; and cloud platforms). The Commission does not anticipate a single standard would be developed or identified to apply to all consumer IoT products. However, a single package of standards may be developed or identified for each product type or class as identified by the Lead Administrator and reviewed and approved by the Bureau. We also agree with the Cybersecurity Coalition that “participants should have discretion to include security features that go beyond standard requirements . . . So long as the additional security features do not conflict with conformity with the standard used for eligibility by the labeling program participants, participants should be encouraged to go beyond baseline requirements.”
95. We adopt the IoT Labeling NPRM's proposal to implement a single binary label with layering. As discussed in the IoT Labeling NPRM, “under a binary label construct, products will either qualify to carry the label or not qualify ( i.e., not be able to carry the label) and `layers' of the label would include the Commission's Cyber Trust Mark representing that the product or device has met the Commission's baseline consumer IoT cybersecurity standards and a scannable code ( e.g., QR Code) directing the consumer to more detailed information of the particular IoT product.”
96. We adopt a binary label because we believe that a label signaling that an IoT product has met the minimum cybersecurity requirements will be simplest for consumers to understand, especially as the label is introduced to and established for the public. The Cybersecurity Coalition supports a binary label, citing the benefits of a simple, consumer friendly nature and its potential to streamline the purchasing decision for consumers. Similarly, as LG Electronics points out, “[l]ike the ENERGY STAR program, a binary label specifying that a device has met a government standard—in this case for cybersecurity—will be enough to drive consumers and manufacturers toward more secure products,” while leaving manufacturers free to separately provide additional cybersecurity information about their products. And the Connectivity Standards Alliance supports the use of a single binary label with layering, as recommended by NIST, asserting that “[a]cademic studies have validated this approach.” Conversely, Canada advocates a multi-tiered approach to labeling to “lower barriers to entry into the labelling regime and facilitate trade and competition by ensuring Micro, Small and Medium Sized Enterprises (MSMEs), with fewer resources to meet a high level of cybersecurity,” and to “provide the incentives for a greater number of firms to innovate in IoT products and work on `climbing the ladder' of cybersecurity levels over time.” Another commenter suggests a multi-tiered label that would have different colors depending on the length of time the product is supported. Other commenters advocate a multi-tiered approach that need not be reflected in different Cyber Trust Marks, but in different information available when a consumer scans the QR code. A study by Carnegie Mellon University indicates that different types of labels of various complexities have varying levels of effectiveness, but does not contest the idea of a binary label. We also recognize that some international regimes, such as Singapore, use a multi-tiered label.
97. Although one could imagine myriad different approaches to labeling that each have relative advantages and disadvantages, on balance we are persuaded to rely on a binary label as we begin our IoT Labeling Program, consistent with NIST's recommended approach. We agree with the Cybersecurity Coalition that “the primary value of the IoT . . . labeling program is to better enable ordinary consumers to distinguish labeled products as likely providing better basic security than unlabeled products.” We believe a binary label meets this goal by Start Printed Page 61262 providing a clear indication that products with the label meet the Commission's cybersecurity requirements. We anticipate that promoting early consumer recognition of the FCC IoT Label—which we think is better advanced by a binary label—will, in turn, make consumers more attuned to cybersecurity issues and more receptive to additional cybersecurity information that manufacturers elect to provide apart from the FCC IoT Label and associated QR code. Thus, we believe that our use of a binary label still retains incentives for manufacturers to innovate and achieve higher levels of cybersecurity. Our approach to determining what cybersecurity standards will be applied also accommodates the potential for different requirements being necessary to meet the NIST baseline criteria in different contexts. To the extent that any multi-tiered labeling approach contemplated by commenters would allow manufacturers to obtain a label through lesser cybersecurity showings, that would be less effective at achieving the goals of our program. And to the extent that any multi-tiered labeling approach would require manufacturers to make heightened cybersecurity showings to achieve higher-tier labels, that is unlikely to lower barriers to participation in the IoT Labeling Program while also risking less understanding and acceptance of the FCC IoT Label by consumers. Because delay in moving forward with the IoT Labeling Program would have its own costs in pushing back the potential for benefits to consumers and device security, we also recognize the benefits of a binary label as more straightforward to implement, at least at the start of our IoT Labeling Program. Weighing all the relevant considerations, we are persuaded to move forward with a binary label at this time.
98. We require that products bearing the FCC IoT Label, which includes the Cyber Trust Mark, must also include the corresponding QR Code. Approval to use the Cyber Trust Mark is conditioned on the label also bearing the QR Code in accordance with the IoT Labeling Program's label standards. In addition, the FCC IoT Label must be easily visible to consumers ( e.g., on product packaging). This approach received considerable support in the record. We agree with USTelecom that “consumers should not have to open the package to get information because that could impact their ability to return the product.” Power Tool Institute, Inc. concurs that “[p]lacing a QR Code on the packaging is preferable to placing it on the device.” Notable pros of using a QR Code are providing “consumers with detailed information about a device or product,” enhancing the program's objective by providing real-time updates. However, some commenters raise concerns with the placement of the QR Code on the product packaging. Logitech urges the Commission to not require a QR Code in conjunction with the label, stating that it could crowd packaging, cause consumer confusion, and may cause confusion if retailers scan the wrong barcode when checking out a customer. We believe that as the label becomes established and recognized by consumers and retailers, the benefit of providing a QR Code linking to a registry populated with current information on the IoT product outweighs the potential for consumer confusion. We also believe the registry will be of value to consumers such that they will want to see it acknowledged in an easily accessible manner, which will override any potential difficulty retailers may have with scanning the incorrect code. Moreover, recognizing the realities of inventory turnover against the need for a cybersecurity label to be dynamic, the use of a QR Code-embedded URL in this context ensures that (1) if a consumer desires more information about the product than what the label itself signifies there is a simple means of access; and (2) information associated with the product's compliance with the IoT Labeling Program is current. We view these as relevant considerations to purchasing decisions, which requires easy access to such information “on the spot” rather than requiring a purchaser to independently seek it out.
99. We direct the Lead Administrator to collaborate with stakeholders as needed to recommend to the Commission standards for how the FCC IoT Label bearing the Cyber Trust Mark and the QR Code should be designed ( e.g., size and white spaces) and where such a label should be placed. This should include where the label could be placed on products where consumers may not see product packaging when shopping or after purchasing ( e.g., refrigerators, washing machines, dryers, dishwashers, etc.) and including where consumers purchase products online. The Lead Administrator and stakeholders should also examine whether the label design should include the date the manufacturer will stop supporting the product as well as whether including other security and privacy information ( e.g., sensor data collection) on the label would be useful to consumers. In addition, the Lead Administrator should address the use of the FCC IoT Label in store displays and advertising. [ 20 ] We recognize the current work being done by industry on an appropriate format for the label, including the Cybersecurity Label Design, which is part of CTA's American National Standards Institute (ANSI)-accredited standards program. As noted by CTA in its reply comments, the FCC specifies requirements for the use of the Cyber Trust Mark, but “there are several additional details needed regarding QR coding and resolution, white space for accurate recognition of QR codes, and more.” CTA states that the draft ANSI/CTA-2120 details lay out requirements for packaging, and we encourage the Lead Administrator to review and consider the work CTA's Cybersecurity Label Design working group (a subgroup of CTA's Cybersecurity and Privacy Management Committee) has completed in this regard. We agree that we should take into consideration the considerable work that has already been undertaken with respect to labeling design and placement and seek to leverage and benefit from this expertise by directing the Lead Administrator to seek feedback from a cross-section of relevant stakeholders who have been working on these issues. We delegate authority to PSHSB to review, approve (or not approve) the Lead Administrator-recommended labeling design and placement standards after any required public notice and comment process and if approved incorporate into the Commission's part 8 rules. The provisions of 47 CFR 2.935(a) (allowing the electronic display of “or other information that the Commission's rules would otherwise require to be shown on a physical label attached to the device”) do not apply to the FCC IoT Label. The Cyber Trust Mark may only be used as directed by part 8, notwithstanding 47 CFR 2.935 or any other rule.
100. We adopt our proposal from the IoT Labeling NPRM that the label include the Cyber Trust Mark and a QR Code that links to a decentralized publicly available registry containing Start Printed Page 61263 information supplied by entities authorized to use the FCC IoT Label ( e.g., manufacturers) through a common Application Programming Interface (API). The registry will include and display consumer-friendly information about the security of the product. We believe a publicly accessible registry furthers the Commission's mission of allowing consumers to understand the cybersecurity capabilities of the IoT devices they purchase. We also agree that it is important for the registry to be dynamic, so a consumer can be aware if a product loses authorization to use the FCC IoT Label or if the manufacturer is no longer providing security updates. There is robust support for the development of a publicly-accessible registry. We agree with NCTA that “the IoT Registry is foundational to the value and utility of the Cyber Trust Mark Program.” In the following paragraphs, we establish general parameters for registry information.
101. We adopt a decentralized registry that contains specific essential information that will be disclosed by the manufacturer, as discussed in further detail below. This essential information from the manufacturer will be provided to a consumer accessible application via the registry by utilizing a common API that is secure by design. When a consumer scans the QR Code, a consumer accessible application will access the registry using the common API and present the consumer with the information we require to be displayed from the registry. CTIA points out that a centralized registry containing all the information the Commission conceived in the IoT Labeling NPRM and by commenters in the record would be inordinately complex and costly. We agree, and endeavor to meet the policy goal of providing a transparent, accessible registry to the public through more efficient and less complicated means.
102. We agree with the Commission's assessment in the IoT Labeling NPRM that the registry's goal is to assist the public in understanding security-related information about the products that bear the Cyber trust Mark. CTIA confirms this view, stating “the Commission should focus on the [registry] as a means to provide consumers with information that is critical to the success of the program.” CTIA further proposes that we should allow each manufacturer to establish their own mechanisms for conveying this information to consumers. However, we acknowledge ioXt Alliance's concern that a completely manufacturer-driven approach could lead to inconsistencies, inaccuracies, or other difficulties for the consumer. To balance the need for a workable, streamlined registry that is consistent for consumers and meets the Commission's goals while easing the administrative burden inherent in a centralized registry, we require a common API that would provide access to the following essential information from the manufacture and display it to the consumer in a simple, uniform way:
- Product Name;
- Manufacturer name;
- Date product received authorization ( i.e., cybersecurity certification) to affix the label and current status of the authorization (if applicable);
- Name and contact information of the CLA that authorized use of the FCC IoT Label;
- Name of the lab that conducted the conformity testing;
- Instructions on how to change the default password (specifically state if the default password cannot be changed);
- Information (or link) for additional information on how to configure the device securely;
- Information as to whether software updates and patches are automatic and how to access security updates/patches if they are not automatic;
- The date until which the entity promises to diligently identify critical vulnerabilities in the product and promptly issue software updates correcting them, unless such an update is not reasonably needed to protect against cybersecurity failures ( i.e., the minimum support period); alternatively, a statement that the device is unsupported and that the purchaser should not rely on the manufacturer to release security updates;
- Disclosure of whether the manufacturer maintains a Hardware Bill of Materials (HBOM) and/or a Software Bill of Materials (SBOM); [ 21 ] and
- Additional data elements that the Bureau determines are necessary pursuant to the delegated authority discussed below.
103. To reduce potential burdens and focus on essential information, we pare back the scope of the registry from what the Commission proposed in the IoT Labeling NPRM. We agree with the Cybersecurity Coalition that “[t]he primary purpose of the label is to help consumers make informed purchasing decisions” and include in the registry information that is key to making a purchasing decision, without overwhelming the consumer. To this end, we agree with commenters who suggest that including the information proposed in the IoT Labeling NPRM may be too burdensome. NEMA, for example, expresses concern about the resources required for a registry containing a full catalogue of devices. CTIA agrees that the IoT registry envisioned by the IoT Labeling NPRM would “impose significant, unmeetable burdens” for participants and the manager of the registry, and encourages us to refine our approach. The Cybersecurity Coalition likewise expresses concern over the complexity of the proposed registry. We agree that the registry be “modest in its goals” and “limited to basic information that is uniform . . . and pragmatic and useful to the consumer.” We believe that a registry containing simple, easy to understand information will be most helpful to a consumer making a purchasing decision, but also see the value in allowing manufacturers to include a second registry page (following the consumer-focused page) to enable manufacturers to provide additional technical details designed for researchers, enterprise purchasers, and other expert consumers of the label. Focusing only on the most critical information will further facilitate the speedy establishment of the IoT Labeling Program and the registry itself.
104. In the interest of keeping information simple and establishing the database swiftly, we streamline the elements that should be included in the registry. We do require information about how to operate the device securely, including information about how to change the password, as it would help consumers understand the cybersecurity features of the products, how those products are updated or otherwise maintained by the manufacturer, and the consumer's role in maintaining the cybersecurity of the product. We do not require information about whether a product's security settings are protected against unauthorized changes as part of the initial rollout of the registry in an attempt to streamline the registry to address concerns that the registry would be too bulky or unfriendly to consumers. We recognize the value of ensuring the registry information is accessible to everyone, including those whose primary language is not English. Accordingly, we direct the Lead Administrator to recommend to the Bureau whether the registry should be in additional languages and if so, to recommend the specific languages for inclusion. We delegate authority to the Bureau to consider and adopt requirements in this regard upon review Start Printed Page 61264 of these recommendations. As the Association of Home Appliance Manufacturers points out, the location of the product's manufacture is redundant with existing legal requirements. We also do not require labels to include an expiration date at this time as it may not be an applicable requirement for every product, but we direct the Label Administrator to consider whether to recommend including the product support end date on labels for certain products, or category of products.
105. While we recognize the value of utilizing the registry to keep consumers informed about product vulnerabilities, we note CTIA and Garmin's concerns about listing unpatched vulnerabilities as not providing value to consumers, discouraging manufacturers from participating in the program, and tipping off bad actors. We agree that these concerns are significant and do not require detailed information about vulnerability disclosures in the registry at this time. Rather, we require disclosure only of whether a manufacturer maintains an SBOM and HBOM for supply chain security awareness. We agree with Consumer Reports, NYC Cyber Command Office of Technology and Innovation (NYC OTI), and the Cybersecurity Coalition that an SBOM should be considered as an element of the registry. We also note that Garmin's concern is with disclosing the specific contents of an SBOM to the public, which “could reveal confidential business relationships with companies, as well as provide a roadmap for attackers,” but this is not what we require here. Requiring participating manufacturers to disclose only the maintenance of an SBOM and HBOM, rather than the contents therein, indicates an added level of software and hardware security while also protecting potentially sensitive information. Further, while we agree with CTA that a searchable registry would have value for the public, we are mindful of the resources, costs, and time involved with creating a registry that is searchable by each of the elements identified in the IoT Labeling NPRM. In limiting the registry as we have, we address the concerns that the registry may be too complex to administer in the initial iteration of the IoT Labeling Program. As discussed above, the decentralized, API-driven registry we adopt in the Order addresses the complexity concerns raised in the record. We cabin our initial vision of the registry and direct the Bureau, as described further below, to consider ways to make the initial design of the registry modest, with potential to scale the registry as the IoT Labeling Program grows.
106. In this respect, we note that NIST's research suggests that “future work should be done to examine potential issues of including an expiry date on a label.” NIST cited studies conducted by the UK Government that consumers were confused about what the expiration date meant, and an Australian government study in which consumers thought the device would stop working after that date. The UK research did conclude, however, that continued manufacturer support was important to survey participants. Consumer Reports suggested an expiration date, if present, should be tied to an end-of-support date rather than a renewal date. NIST's research into the importance of support dates to consumers coupled with the potential confusion of expiration dates and the support from the record lead us to conclude an expiration date is not warranted. We do find, however, that the disclosure of a minimum support period and end date for the support period for the device is appropriate and will provide meaningful information to consumers on the manufacturer's commitment to provide patches or other support—a vital issue in a dynamic threat environment. To ensure that information about this support period remains accurate, and to encourage manufacturers to support their products for longer periods, manufacturers shall be able to extend the support period in the registry through a mechanism to be determined by the Lead Administrator, but which should be expeditious and require no further disclosures.
107. While we identify the defined set of data that is consistent across all manufacturers, we believe the information contained in the registry for a particular IoT product or product class may also depend on the standards and testing procedures adopted for each particular IoT product. As such, in the near term, we expect there will be additional registry data elements that are specific to an IoT product, or classes of IoT products, that are not yet ripe for decision. We also recognize that some of the information recommended by NIST in its consumer education recommendations, discussed in further detail below, may be valuable for consumers to see in the registry. Accordingly, while we provide a baseline of necessary information that must be displayed for an IoT product in the registry, regardless of class the IoT product belongs to, we delegate authority to the Bureau to determine, subject to any required public notice and comment processes, whether any additional disclosure fields, such as the manufacturer's access control protections ( e.g., information about passwords, multi-factor authentication), whether or not the data is encrypted while in motion and at rest (including in the home, app, and cloud), patch policies and security or privacy information are necessary, and if so, what should they be.
108. We disagree with commenters, such as LG Electronics, who suggest that manufacturers should have discretion over whether to include additional privacy and/or security information through a QR Code, URL, or other scannable mechanism insofar as it would require additional information in the registry. LG Electronics, though supportive of adding a variety of data to the registry, acknowledges it is unclear how much detail or what types of information would be of value to a consumer. We believe that allowing discretion over what information is included in the registry may overcrowd it, or engender consumer confusion. Rather, uniform registry elements will provide greater consistency for consumers and adoption of uniform registry elements is supported by the record. We make clear, however, that we do not otherwise restrict what information manufacturers may include or reference on their product packaging, so long as it does not interfere with or undermine the display of the FCC IoT Label.
109. We recognize that a decentralized registry relying on data derived through an API from manufacturers will require some oversight to ensure that the registry, when accessed by consumers using QR Codes, functions as described and displays the required information about individual products. We direct the Lead Administrator to receive and address any technical issues that arise in connection with displaying the registry through the QR Code, the associated API, and consumer complaints with respect to the registry. CSA recommends that the Commission engage a third-party with operating the registry for cost and efficiency reasons. CTA agrees that the Commission should use a third-party to host and manage the registry due to the resources required to establish the registry. We agree that, given the structure of the registry as we adopt in the Order, the Lead Administrator is in the best position to interface with manufacturers to ensure the smooth operation of the registry.
110. We also recognize that for a registry of this magnitude to be effectively and timely rolled out requires significant input and Start Printed Page 61265 coordination with industry partners. To determine how the registry should be structured to best meet the goals of the IoT Labeling Program as we adopt in the Order, we direct the Bureau to seek comment and consider, as part of a public process, the technical details involved with the operation of the registry. We delegate authority to the Bureau to adopt a Public Notice, subject to any required public notice and comment, establishing the structure of the registry; identifying the common API; how the API should be structured; how the API should be used; how the queried data will be displayed to the consumer; how manufacturers need to maintain and implement the API in connection with its interactions with the registry; what, if any, additional disclosure fields would be most beneficial to consumers in the future, as discussed above; how the data in the registry returned by the API should be presented to the consumer; how the costs involved in maintaining the registry will be handled; how often the registry should be updated; whether to require the manufacturer to list the product sensors, what data is collected, if the data is shared with third parties, or security or privacy issues and if data should be replicated; and whether data should be replicated in multiple repositories—by the relevant CLA(s) or vendors, for example—and publicly accessible via a single query point; and any other technical information needed to establish the registry as we adopt in the Order. The Bureau should consider how to reduce burdens on manufacturers in supporting the decentralized registry. We delegate authority to PSHSB in coordination with, at a minimum, OMD (specifically the Office of the Chief Information Officer) and, to the extent necessary OGC (specifically the Senior Agency Official for Privacy) to identify and impose any applicable security or privacy requirements arising from Federal law or Federal guidance for the registry and to approve or modify the recommendations regarding the functional elements of the registry listed above. We further delegate authority to PSHSB to publish a Public Notice, subject to any required public notice and comment, adopting and incorporating into the Commission's rules any additional requirements or procedures necessary to implement the Cyber Trust Mark registry.
111. We adopt the proposal in the IoT Labeling NPRM that applicants must renew their authority to use the FCC IoT Label. Entities authorized to use the FCC IoT Label are required to ensure the product bearing the FCC IoT Label continue to comply with the Commission's program requirements. We disagree with the Connected Consumer Device Security Council (CCDS) that no renewals should be required and the product should simply bear the last date of testing. Such an approach could severely impair consumer trust in the label, especially if a product bearing the FCC IoT Label is being sold as new but is far out of date as to its initial achievement of the Mark.
112. For those that support some interval of renewal, the record is divided with respect to whether IoT Labeling Program applicants should file for renewal each year, as proposed in the IoT Labeling NPRM. Consumer Reports and TÜV SÜD agree that annual renewal is appropriate. AHAM feels that an annual renewal application as the Commission proposed was unnecessary, or at minimum “unnecessarily rigid.” AHAM posits that a requirement to renew should only be triggered when a significant or substantive change is made to either the standard the manufacturer certifies to, or a significant design change to the product. Similarly, more durable IoT products (such as smart appliances) may need to be renewed less frequently. NAM argues that annual renewals are unnecessary for products that pose a limited risk. Kaiser Permanente believes higher-risk devices should be updated annually, and otherwise renewal should occur every three years. CCDS argues no annual testing is necessary, and the product should simply have the date it was authorized to bear the label that signals the product was compliant as of the initial date. CSA suggests limiting the need for annual testing, but suggests some kind of annual reporting should be required. We observe that other certifying bodies, such as ioXt Alliance, require annual renewal for products they certify and allow incentives for early renewal. Based on the record, we recognize the degrees of nuance attendant to the different types of products at issue. We agree with the notion that certain IoT products, depending on their lifespan and risk level, may need different standards for renewal to achieve the FCC IoT Label.
113. We task the Lead Administrator to collaborate with stakeholders and provide recommendations to PSHSB on how often a given class of IoT products must renew their request for authority to bear the FCC IoT Label, which may be dependent on the type of product, and that such a recommendation be submitted in connection with the relevant standards recommendations for an IoT product or class of products. In doing so, consideration should be given as to whether annual continuous compliance reports are acceptable for purposes of renewing, and how to effectively balance the need for industry flexibility and the need to ensure that consumers have up-to-date information about the product they are considering purchasing. Consideration should also be given to the fees incurred as part of a renewal process, as we agree with Kaiser Permanente that renewal fees must not be unduly burdensome or cost-prohibitive. We emphasize that renewals should occur frequently enough that a consumer can be sure that a product bearing the FCC IoT Label has reasonable cybersecurity protections in place, and some process must be in place to ensure accountability, even if annual testing is not required. We delegate authority to PSHSB to review, approve (if appropriate) and, subject to any required public notice and comment, incorporate by reference into the Commission's rules, the proposals from the Lead Administrator for renewal of authority to bear the FCC IoT Label.
114. We adopt the IoT Labeling NPRM's proposal to rely on a combination of administrative remedies and civil litigation to address non-compliance and direct the CLA(s) to conduct post-market surveillance. The purpose of this IoT Labeling Program is to provide reasonable assurances to the consumer that the products they bring into their homes have at least a minimum level of cybersecurity. The success of the IoT Labeling Program hinges on the label retaining its integrity as a trusted consumer resource. This requires vigorous review and enforcement to ensure that products bearing the Cyber Trust Mark are in compliance with the program standards. We further observe that the ISO/IEC 17065 standards require CLAs to perform appropriate post-market surveillance activities. We adopt post-market surveillance and civil enforcement, accordingly.
115. We find support in the record that the “Mark must be trusted by consumers to be successful” and “to gain consumer confidence and incentivize cybersecurity, the label must be backed by a robust enforcement program.” We agree with the EPIC's position that weak enforcement may result in unmet consumer expectations regarding a product's actual level of cybersecurity and “allow bad actors to take advantage of the goodwill created Start Printed Page 61266 by the cybersecurity program,” and take up its recommendation of independent, post-market audits accordingly. Whirlpool also supports regular market surveillance to find instances of unapproved use of the Cyber Trust Mark, as well as products that may have been certified but no longer meet program requirements. Whirlpool states that surveillance “should include random auditing . . . as well as sampling of some established percentage on a regular basis of certified products/devices.” The American Association for Laboratory Accreditation supports adopting the product surveillance standards established for Telecommunication Certification Bodies (TCBs) and in the EPA's ENERGY STAR program. We also agree with commenters who indicate that the Commission, CLAs, and possibly the Federal Trade Commission (FTC) should be able to receive complaints of noncompliant displays of the Cyber Trust Mark, which could result in auditing. We delegate authority to the Bureau, in coordination with the Consumer and Governmental Affairs Bureau, to determine the process for receiving and responding to complaints. CTA and Planar Systems also support random auditing. We agree that random audits, in addition to regular post-market surveillance will best serve to maintain consumer confidence in the Cyber Trust Mark. [ 22 ]
116. Post-market surveillance. We agree with the Cybersecurity Coalition that post-market surveillance of products receiving the Cyber Trust Mark should be a principal enforcement mechanism, and find that CLAs are in the best position to conduct post-market surveillance and random auditing, in accordance with ISO/IEC 17065. These activities are based on type testing a certain number of samples of the total number of product types which the CLA has certified. In addition, each CLA must be prepared to receive and address post-market surveillance from the public. If a CLA determines that a product fails to comply with the technical regulations for that product, the CLA will immediately notify the grantee and the Lead Administrator in writing. The grantee will have 20 days to provide a report to the CLA describing actions taken to correct the deficiencies. Continued deficiency after 20 days will result in termination of the grantee's approval to display the Cyber Trust Mark. A grantee's approval to display the Cyber Trust Mark may also be terminated subject to the 20 day cure period for false statements or representations found in their application or associated materials or if other conditions come to the attention of a CLA which would warrant initial refusal to authorize use of the FCC Label. Such terminations will protect the integrity of the FCC IoT Label and encourage accurate representations and disclosures in application materials that will enhance the reliability of the Labeling Program's operation, more generally.
117. We believe it is appropriate for the Lead Administrator, in collaboration with the CLAs and other stakeholders, to identify or develop, and recommend to the Commission for approval, the post market surveillance activities and procedures that CLAs will use for performing post-market surveillance. The recommendations should include specific requirements such as the number and types of samples that a CLA must test and the requirement that grantees submit, upon request by PSHSB or a CLA, a sample directly to the CLA to be evaluated for compliance at random or as needed. [ 23 ] We delegate authority to the Bureau to review the recommendations and, subject to any required public notice and comment, incorporate post market procedures into the Commission's rules. We also delegate authority to the Bureau to establish requirements (subject to any required public notice and comment) regarding post-market surveillance of products in any instances where the CLA that granted the authorization of the product is not available to conduct such post-market surveillance. The document will also address procedures to be followed if a grantee's approval to display the Cyber Trust Mark is terminated based on mandatory post-market surveillance or notice from the public, including disqualification from the IoT Labeling Program and potential further investigation into other products related to the manufacturer or the CyberLAB, as discussed below. Finally, the Lead Administrator will submit periodic reports to PSHSB of the CLAs' post-market surveillance activities and findings in the format and by the date specified by PSHSB.
118. The IoT Labeling NPRM sought comment on disqualification for nonconformity, referencing the Department of Energy's ENERGY STAR program, which sets out contractual Disqualification Procedures, including a 20 day period to dispute before a formal disqualification decision and what steps an ENERGY STAR partner must take after being formally disqualified ( e.g., removing references to ENERGY STAR in the product labeling, marketing). The IoT Labeling NPRM asked whether the IoT Labeling Program should adopt a similar process. We agree with EPIC and Planar Systems in supporting a “cure period [to] give[ ] good actors the opportunity to fix any issues without incurring penalties” and ” to address any discovered non-conformance as long as the manufacturer is acting in good faith.” Here, we adopt a cure period of 20 days, which is in line with the ENERGY STAR program.
119. EPIC also supports adopting disqualification procedures similar to ENERGY STAR's for non-compliance, including ceasing shipments of units displaying the label, ceasing the labeling of associated units, removing references to the label from marketing materials, and covering or removing labels on noncompliant units within the brand owner's control. It notes that the EPA also conducts retail store level assessments to identify mislabeled products and argues that a robust enforcement mechanism should include all of these actions. We delegate to the Bureau to consider whether such requirements should follow from termination of authority.
120. In addition, we find that a combination of enforcement procedures for non-compliance are available, including administrative remedies under the Communications Act and civil litigation trademark infringement or breach of contract. Administrative remedies may include, but are not limited to, show cause orders, forfeitures, consent decrees, cease and desist orders, and penalties. The Commission will pursue all available means to prosecute entities who improperly or fraudulently use the FCC IoT Label, which may include, but are not limited to, enforcement actions, legal claims of deceptive practices prosecuted through the FTC, [ 24 ] and legal Start Printed Page 61267 claims for trademark infringement or breach of contract. The record supports both administrative remedies to address consumer harm and civil enforcement actions for false use of the FCC IoT Label. We assert that this combination of enforcement mechanisms are best suited to protect consumer trust in the Cyber Trust Mark and incentivize participant compliance.
121. Cyber Trust Mark Demonstrates Adherence to Widely Accepted Industry Cybersecurity Standards. While we decline to preempt state law, we find that approval to use the Cyber Trust Mark on a particular product is an indicator of reasonableness and demonstrates adherence to widely accepted industry cybersecurity standards. While several commenters support Commission preemption of state laws, as well as adoption of liability protections for devices approved to display the Cyber Trust Mark, we decline to preempt state law and decline to implement a legal safe harbor beyond reiterating the Commission's view that achievement of FCC IoT Label is an indicium of reasonableness for entities whose products are compromised despite being approved to use the Cyber Trust Mark. We recognize that a more fulsome safe harbor provision may indeed incentivize participation in the IoT Labeling Program, as the U.S. Chamber of Commerce urges. However, on this record we are not persuaded that it would be feasible or prudent for the Commission to make liability pronouncements as to laws or standards outside the Commission's purview as would be necessary for a broader safe harbor in the absence of preemption. As EPIC observes, such a safe harbor could also decrease consumer trust in the label. In addition, several states have adopted legal safe harbors for entities that implement reasonable security measures ( e.g., voluntarily adopt recognized best practices such as NIST's and implement written security programs), and we defer to the states to determine whether approval to use the Cyber Trust Mark meets these State requirements. Given the uncertain interplay between qualification to use the Cyber Trust Mark and various state law regimes, coupled with the risk that such a safe harbor could decrease consumer trust in the label, we decline to preempt state liability requirements at this time.
122. We note the robust record highlighting the immense value to manufacturers of IoT products in international harmonization of cybersecurity standards. We agree with Widelity that “IoT devices are often manufactured and sold globally. As supply chains evolve, a consistent set of standards will support the rapid growth of innovation and security.” We further agree with Consumer Reports that “mutual recognition should only occur when the other program to be recognized has standards as stringent or more stringent” than the IoT Labeling Program.
123. We recognize several other countries already have an established national cyber IoT labeling program, including Singapore, Finland, and Germany. The record cites to these programs and highlights their features for consideration in developing the IoT Labeling Program. For example, the record explains how Singapore's CLS takes reference from the EN 303 645 standards developed by the European Telecommunications Standards Institute (ETSI). We note that other commenters have also recommended use of the ETSI EN 303 645 standards. Further, the record provides Finland's IoT labeling database as an example for developing our IoT registry. Several other countries have government activity around IoT devices or products. For example, Canada has a cybersecurity certification program for small and medium-sized organizations. As another example, South Korea has a IoT security certification system justified under Article 48-6 of their “Act on Promotion of Information and Communications Network Utilization and Information Protection” statute.
124. We also observe continuing developments in IoT security across the globe for consideration. The European Union Agency for Cybersecurity (ENISA) is currently developing a cybersecurity certification framework that would require certain products, services, and processes to adhere to specific requirements. Relatedly, the U.S. has signed an agreement for a joint roadmap between the Cyber Trust Mark and similar consumer labeling programs in the EU. Further, Japan has committed to work with the U.S. to “ensure interoperability” of its IoT labeling scheme currently under development.
125. We fully recognize the importance of ensuring international recognition of the IoT Labeling Program and reciprocity considerations underlie our decisions in the Order. We delegate authority to the Bureau and the FCC Office of International Affairs to work with other Federal agencies to develop international recognition of the Commission's IoT label and mutual recognition of international labels, where appropriate, as promptly as possible to enable recipients of the Cyber Trust Mark to realize the benefits an internationally recognized Cyber Trust Mark can have to promote global market access. Moreover, the proliferation in the marketplace both in the U.S. and abroad of products meeting a common baseline standard will elevate the overall global cybersecurity baseline for IoT and promote security-by-design approaches to smart products.
126. We adopt the IoT Labeling NPRM's proposal and base the IoT Labeling Program's consumer education requirements on the considerations NIST outlines in the NIST Cybersecurity White Paper due to its general applicability to an IoT label and in light of support from the record. The Lead Administrator will be responsible for developing a consumer education campaign that is based on the considerations recommended by NIST in the NIST Cybersecurity White Paper and discussed in greater detail below. In developing its consumer education plan, we task the Lead Administrator with considering ways to roll out a robust campaign with a reasonable national reach, including ways to make the consumer education accessible and whether education materials should be developed in multiple languages. We further task the Lead Administrator with considering the costs of conducting such outreach and how that outreach would be funded. Once developed, the Lead Administrator will submit this consumer education plan to the Bureau for consideration and for coordination in publicizing the benefits of the IoT Labeling Program. We recognize the importance of close collaboration between industry and delegate authority to the Bureau to consider and work with the Lead Administrator and other stakeholders to determine how the consumer education campaign would be executed and to execute the campaign. In addition and in furtherance of our expectation that the success of the IoT Labeling Program will be dependent on a close collaboration with the Federal Government, industry, and other relevant stakeholders, the Commission will coordinate as needed with relevant agencies, such as the Department of Homeland Security, Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation Start Printed Page 61268 (FBI), as well as the FTC, the Consumer Product Safety Commission (CPSC), and other industry stakeholders who have indicated a willingness to publicize the benefits of the IoT Labeling Program as part of their own consumer education activities.
127. We agree with CEDIA that consumer education will have a significant impact on meeting the IoT Labeling Program's goals. We further agree that adequate consumer education must inform consumers of the limitations of the Cyber Trust Mark as well as the benefits of having a product that meets baseline cybersecurity requirements, and we agree with CSA that consumers should understand that the label does not guarantee complete device security, but that such protections are an important component of risk management. As pointed out by the City of New York's Office of Technology and Innovation, an effective consumer education program would need to cover the risks and threats to “digital integration of [IoT] devices” and how those risks “can be lessened by helping operators, users, and consumers . . . learn the key elements of a strong IoT Cybersecurity posture.” We agree with commenters in the record that NIST's approach to consumer education is best, and note that no commenters opposed NIST's approach.
128. As the Commission acknowledged in the IoT Labeling NPRM, NIST has prepared a document identifying consumer education considerations as part of its analysis of a cybersecurity labeling program. In following with NIST's recommendations, the Commission believes consumers should have access to the following information as part of the IoT Labeling Program's consumer education plan:
(1) What the label means and does not mean, including that the label does not imply an endorsement of the product and that labeled products have not completely eliminated risk;
(2) What cybersecurity baselines must be met to obtain authority to affix the label, why they were included, and how those criteria address security risks;
(3) A glossary of applicable terms, written in plain English;
(4) General information about the conformity assessment process, including information about how the conformity assessment was conducted and the date the label was awarded to the product;
(5) The kinds of products eligible for the label and an easy way for consumers to identify labeled products;
(6) The current state of device labeling as new cybersecurity threats and vulnerabilities emerge;
(7) Security considerations for end-of-life IoT products and functionality implications if the product is no longer connected to the internet;
(8) Consumer's shared responsibility for securing the device software and how their actions (or inactions) can impact the product's software cybersecurity; and
(9) Contact information for the IoT Labeling Program and information on how consumers can lodge a complaint regarding a product label.
129. We recognize that some aspects of this consumer education campaign overlap other aspects of the IoT Labeling Program, such as the registry. We see no harm with including that information in the registry as well as the consumer education campaign. We also observe the importance of conducting what NIST describes as a “campaign” to establish and increase label recognition, and thus envision a Lead Administrator-led, multiple stakeholder engagement that puts NIST's recommendations into practice.
130. NIST has conducted research into the consumer perspective on the loss of manufacturer support in IoT products. The research suggests that proactive communication to consumers from the manufacturer with information about end-of-life support policies, the expected lifespan, and how to sign up for notifications about changes to support is an additional, important step. NIST also emphasizes the importance of consumer education about the meaning of the dates attached to a label, and cautions that this can confuse consumers as to the date's meaning. We agree with Consumer Reports that educating consumers about the meaning of support periods is an important aspect of consumer education. We believe that the recommendations identified by NIST in the NIST Cybersecurity White Paper, coupled with the consumer research done by NIST and industry, provide a strong model that the Lead Administrator can utilize in its consumer education campaign to meet the goals NIST and the record, discussed above, identify as important for a successful consumer education campaign.
131. To assist the Lead Administrator in promoting consumer education, the Commission will coordinate publicizing the benefits of the IoT Labeling Program with the relevant agencies, including the Department of Homeland Security, CISA, FBI, FTC, CPSC, and other industry stakeholders who have indicated a willingness to assist with consumer education. A coalition of trade associations advocates for a consumer education program led by the U.S. Government, but do not propose how to conduct outreach consistent with the Federal outreach concerns articulated in the IoT Labeling NPRM. We agree that a government outreach program is essential in a larger campaign to effectively inform consumers about the IoT Labeling Program, consistent with NIST's recommendations identified above. The Commission intends to work closely with CISA to make use of their “Secure our World” program. We agree with CTA that Federal consumer education efforts do not preclude independent communication and outreach programs. For example, the National Retail Foundation indicated their willingness to support consumer education efforts. While Everything Set, Inc. is concerned that outsized private sector involvement in consumer education might hurt the campaign's credibility, we believe that retail and manufacturer involvement in promoting the IoT Labeling Program and the limitations of the IoT Labeling Program are important to ensure widespread recognition of the Cyber Trust Mark in commerce. To promote consumer education and engage in a joint effort with industry and stakeholders to raise awareness of the label, the Commission will coordinate with the Lead Administrator, Executive Agencies, and other industry stakeholders who have indicated a willingness to publicize the benefits of the IoT Labeling Program as part of their own consumer education efforts.
132. Our analysis indicates that the expected benefits of the IoT Labeling Program greatly exceed the expected costs of the program. The expected benefits of the IoT Labeling Program include improved consumer cyber awareness; reduced vulnerability of products that could be used in cyberattacks both in people's homes and as part of a larger national IoT ecosystem; and increased manufacturer competition and relational benefits stemming from increased goodwill and product awareness. Consumers value the security of their devices, and the complexity of understanding whether IoT devices meet baseline security standards, and making informed purchases on that basis is a significant cost to consumers.
133. Consumer Benefit from Reduced Search Costs. The Cyber Trust Mark can lower consumer research costs by reducing the amount of time consumers spend researching the cybersecurity Start Printed Page 61269 characteristics of IoT products before making a purchase. We estimate that the Cyber Trust Mark will save consumers at least $60 million annually from reduced time spent researching cybersecurity features of potential purchases. We use the U.S. Department of Transportation (DOT)'s approach of valuing the time savings of travel to value the time savings to consumers of the Cyber Trust Mark. Our analysis relies on the share of households with a smart home device (which we note is only one segment of the IoT market likely to be impacted by the Order), the share of those households that are likely to devote time to investigating the cybersecurity of their connected products, and an estimate of their time value of researching cybersecurity characteristics of devices. First, we estimate that 49 million U.S. households own at least one IoT device from a market segment that likely will be impacted by the Cyber Trust Mark. Further, recent survey evidence suggests that 32% of households are invested in reducing their cybersecurity risk. We estimate each hour of time savings to be valued at $16 based on the median compensation in the U.S. and an individual's potential preference for researching products rather than working an additional hour. We note that this calculation only focuses on one segment of the IoT market, which may underestimate the time savings induced by the Order. We recognize that the exact time savings of utilizing the Cyber Trust Mark relative to searching for information online is unknown, so a lower end estimate of 15 minutes of time savings per year per household is used. We find a 15-minute time savings is consistent with the value of cybersecurity features disclosed in surveys. Given manufacturer and industry group comments showing support for consumer awareness and cybersecurity, we believe there would be sufficiently large enough immediate manufacturer participation in the IoT Labeling Program to incur these benefits in the first year of the program, and every year thereafter. Nationwide, the Cyber Trust Mark would result in a minimum of $60 million in time savings annually. [ 25 ]
134. A separate approach to calculating the benefit of the Cyber Trust Mark is to estimate the value consumers place on security and privacy features of IoT devices. A study submitted by Consumer Reports found that respondents valued individual security upgrades between $6 and $13. The study also found that devices were valued at around $34 more if they had a label emphasizing a bundle of the most protective security features. Given the difficulty consumers face in understanding what security and privacy features are included in a device, the Cyber Trust Mark would help consumers easily identify and choose products with features they value. For example, if the Cyber Trust Mark represented the most protective features associated with the label in the in the study, a consumer would benefit by $34 from purchasing a device with the Cyber Trust Mark over a device that did not display the Mark. Based on our estimate of 15 million households that would be impacted by the IoT labeling program, we estimate that the benefit to consumers, in terms of the added value of the Cyber Trust Mark, would be between $85 million and $500 million annually. While the exact security features that will be proposed by the Lead Administrator in collaboration with stakeholders are not yet determined, if the Cyber Trust Mark only emphasized the lowest valued security feature, the program would produce a benefit of at least $85 million.
135. Manufacturer Competitive and Reputational Benefits. Aside from the direct benefits to consumers, there are also wider benefits of the Cyber Trust Mark. Participating businesses benefit from product differentiation and quality signaling vis-a-vis competitors that do not participate in the IoT Labeling Program and from increased company goodwill and reduced risks related to cybersecurity incidents. By aligning minimum security practices with the proposed standards, and communicating those standards to consumers, manufacturers may be able to generate goodwill and reduce business loss after cybersecurity incidences. While we do not revisit our discussion of a safe harbor from liability as discussed above, we note that manufacturers may benefit from adopting security practices that are consistent with standards necessary to bear the Cyber Trust Mark. We highlight that there have been several instances where the Federal Trade Commission investigated and settled with firms due to poor security practices or inaccurate communication of their security practices. We merely note that a manufacturer that has gone through the process of obtaining the Cyber Trust Mark may benefit from likely having documented the security practices and attendant testing necessary to acquire the Mark.
136. Market-Wide Benefits of Reduced Cybersecurity Incidents. Insecure IoT products are often used in distributed denial-of-service (DDoS) attacks, which can be used to overwhelm websites to create a distraction during other cybersecurity crimes, or to request a ransom be paid to stop the attack. While we cannot quantify the expected benefits the Cyber Trust Mark may have on reducing the number of vulnerable devices and/or the potential reduction on their likelihood of being used in a cybersecurity attack, commenters do highlight improved security as one of the major benefits of this IoT Labeling Program. We do further emphasize this as a benefit that is likely to have significant impacts on firms in a wide range of industries.
137. Costs to IoT Labeling Program Participants. Only those entities who choose to participate will incur costs associated with the voluntary IoT Labeling Program. The specific costs of to participating manufacturers cannot be readily measured but are expected to include: conformity testing fees at a CyberLAB, CLA lab, or through in-house testing; CLA fees; internal compliance and filing costs; Cyber Trust Mark placement on product; costs incurred for API access as part of the QR Code; a customer information campaign; and adjustments to security practices necessary to meet the standards established for the Cyber Trust Mark. These costs are likely to vary depending on the standards and testing procedures proposed by the Lead Administrator as well as the extent of manufacturer participation. Any in-house testing lab will also be required to obtain accreditation to ISO/IEC standards and will incur the accreditation costs. We expect that manufacturers that choose to pursue this option may offset the accreditation costs with time savings, and potentially cost savings, associated with in-house testing.
138. Participating manufacturers will incur conformity testing, reporting costs, potential renewal fees, and Label Administrator processing fees, but the Commission's IoT Labeling Program is voluntary and we only expect manufacturers who would benefit from the program to participate in the long-run, further indicating that accrued benefits will exceed manufacturer costs. Furthermore, comments in the record show that many manufacturers and industry groups are in favor of consumer awareness and addressing cybersecurity concerns. This provides some indication that manufacturers perceive the benefits of participating in the IoT Labeling Program as outweighing the costs. We understand Start Printed Page 61270 that manufacturers' security practices for IoT products vary. Some manufacturers will find it beneficial to align their cybersecurity standards with the IoT Labeling Program's standards and apply for the Cyber Trust Mark. If a manufacturer decides not to participate in the program, then they will not experience any additional costs.
139. Cost of Registry Development and Administration. We attempt to estimate the cost of developing and administering the registry with currently available information, recognizing that our cost estimate is unable to incorporate pending issues that will be addressed by the Bureau as discussed above. While the cost to the Lead Administrator to manage the registry in accordance with the Bureau's pending determinations and as discussed above are forthcoming, we nevertheless attempt to estimate the costs of the Lead Administrator' administrative role in managing the registry as described above. Our estimate utilizes data submitted by Consumer Reports, which envisioned a centralized registry. We note that the registry, as adopted, will be less burdensome than the costs described by Consumer Reports in their estimates. [ 26 ] Our estimate to maintain registry components and review applications as part of the CLA duties, which aligns with the middle of the expert range based on commenter submissions, is approximately $5 million annually. The high-end estimate submitted by Consumer Reports is $10 million. Consumer Reports indicates that setting up a centralized registry could be done by one individual with a few contractors at a cost less than $200,000 a year. Depending on the requirements, the Lead CLA may still need to set up some minimal components of a registry and incur a small portion of these costs. The estimates on the annual administration costs are much less precise with the expert proposed estimate of between $100k and $10 million annually, with indication that the $10 million estimate is on the very high end. Staff calculate a more reasonable, but likely still high, estimate in the middle of that range, even accounting for the advanced technical expertise that would be required to review applications. For example, an organization relying on five lawyers, five electrical engineers, and five software developers in a full-time capacity would require $3 million annually in wage compensation. If we generously assume another $2 million in additional costs to accommodate ISO/IEC accreditation, contractors, facilities, and other resources, the total is $5 million. While these estimates are for a single administrator, we believe this is a reasonable estimate of the staffing costs that would be distributed among the CLAs to meet the requirements of reviewing applications.
140. The estimated high-end costs of administering the IoT Labeling Program annually ($10 million) are far less than the low-end estimate of annual benefits to consumers ($60 million) of just one aspect of the program. We further highlight that the benefits to manufacturers are likely to exceed manufacturer's participation costs. Together this indicates the total program benefits exceed costs. Because the initial startup costs are so low relative to the benefits, we do not compare the discounted values.
141. We adopt the IoT Labeling NPRM's tentative conclusion that the FCC has authority to adopt the IoT Labeling Program. We conclude that section 302 provides us with the authority to adopt a voluntary program for manufacturers seeking authority to affix the FCC-owned Cyber Trust Mark on wireless consumer IoT products that comply with the program requirements. In the IoT Labeling NPRM, the Commission sought comment on its authority under section 302 of the Act, along with other possible sources of authority. In particular, under section 302(a) of the Act, consistent with the public interest, convenience, and necessity, the Commission is authorized to make reasonable regulations (1) governing the interference potential of devices which in their operation are capable of emitting radio frequency energy by radiation, conduction, or other means in sufficient degree to cause harmful interference to radio communications; and (2) establishing minimum performance standards for home electronic equipment and systems to reduce their susceptibility to interference from radio frequency energy.
142. Some commenters question our authority under section 302 to establish an IoT Labeling Program. The U.S. Chamber of Commerce cautions the Commission to not “overinterpret its harmful interference authority” under sections 302(a) and 333. CTIA argues that the Commission does not have the authority to regulate cybersecurity, but does not cite to section 302(a) or explain why the Commission's action in the Order does not fall within the scope of section 302(a) or any other section of the Communications Act. Others do not dispute the Commission's authority to adopt a voluntary program but argue that the Commission does not have the authority to make the IoT Labeling Program mandatory.
143. We agree with Comcast that Congress intended section 302 to be flexible enough “to address novel issues not yet on the legislative radar[.]” As Comcast further observes, “[t]he stated goal of the [IoT Labeling] Program is to `ensure that IoT devices have implemented certain minimum cybersecurity protocols to prevent their being hacked by bad actors who could cause the devices to cause harmful interference to radio communications,' which falls squarely within the Commission's remit under section 302(a).” Further, NYC OTI points out that IoT which “by design doesn't protect against the reception of spurious or unintended RF communications may be subject to a series of radio-layer attacks due to the lack of these protections” and thus is within our authority to regulate. A voluntary IoT Labeling Program thus assures consumers that certain cybersecurity standards are met to protect those devices from being used to generate interference to other devices.
144. In addition to our authority under section 302(a)(1), section 302(a)(2) authorizes the Commission to “establish minimum performance standards for home electronic equipment and systems to reduce their susceptibility to interference from radio frequency energy.” A voluntary program for consumer IoT products is encompassed within our authority to regulate home electronic equipment and their accompanying systems that render that home electronic equipment operational.
145. Section 302(a)(2) allows such regulations to apply to “the manufacture, import, sale, offer for sale, or shipment of such devices and home electronic equipment and systems[.]” The legislative history of section 302 also supports our conclusion. Congress adopted section 302 due to concerns about radio frequency interference to consumer electronic equipment:
In the market for home devices, however, good faith industry attempts to solve this interference have not always been as successful. . . . [T]he Conferees believe that Commission authority to impose appropriate regulations on home electronic equipment and systems is now necessary to insure that consumers' home electronic equipment and Start Printed Page 61271 systems will not be subject to malfunction due to [radio frequency interference].
146. Congress envisioned “home electronic equipment and systems” to include not only radio and television sets, but all types of electronics and their supporting systems used by consumers. Examples given by Congress were home burglar alarms, security systems, automatic garage door openers, record turntables, and sound systems. Congress clearly foresaw interference and disruption to consumer equipment and the systems that equipment was connected to as within the ambit of section 302 when it gave the Commission “exclusive jurisdiction” over matters involving radio frequency interference. The many alternatives available to the Commission to accomplish its duty under section 302 include directing manufacturers to meet “certain minimal standards” or utilizing labels.
147. We additionally conclude that our section 302(a) authority to adopt “reasonable regulations” governing the interference potential of devices capable of causing RF interference empowers us to choose specific approaches that advance goals of the Act in addition to the core concerns in section 302(a)(1) and (2). For one, as widely supported in the record, we rely on NIST's recommended IoT criteria (the NIST Core Baseline) as the foundation for the cybersecurity requirements to be applied under the IoT Labeling Program. Even if some elements or applications of those criteria could advance policies or interests in addition to guarding against the risk that exploited vulnerabilities in internet-connected wireless consumer IoT products could cause harmful interference, it would be neither prudent nor workable to try to segregate or disaggregate that package of criteria in an effort to isolate some product capabilities from others in an effort to narrow the Program's focus. To the contrary, maintaining the integrity of the cohesive package of NIST criteria advances the directive in section 302(a) to address the interference potential of wireless devices through “reasonable regulations.” Commenters point out, for example, that even when harmful interference to IoT products from cyberattacks “is not necessarily the traditional form of interference caused by devices operating in frequencies and at power levels not approved by the Commission[,]” it can implicate statutory policy concerns nonetheless. Under the circumstances here, we thus find it “reasonable” for our IoT Labeling Program to rely on the full package of IoT cybersecurity criteria that guard against the risk that the covered products cause harmful interference, and also guard against the risk of interference to those covered products—even in the case of non-RF interference—consistent with the policy goals underlying provisions such as sections 302(a) and 333 and of the Act. Our understanding of the reasonableness of our approach here also is informed by the public safety and national security goals in sections 1 and 4(n) of the Act. Thus, although we do not rely on additional provisions beyond section 302 as authority for the voluntary IoT Labeling Program we adopt in the Order, they inform our understanding of what regulatory approach to implementing section 302(a) is reasonable under these circumstances. [ 27 ]
148. Comcast also cites the legislative history of section 302(a) in support of our authority to establish an IoT Labeling Program. Congress agreed with a letter from the Commission that initial language that would have restricted section 302(a) to devices that cause harmful interference to “`commercial, aircraft, and public safety' radio communications” was too narrow. Congress instead adopted the current language: “reasonable regulations . . . consistent with the public interest, convenience, and necessity.” The Commission's authority under section 302 was designed by Congress to be “sufficiently broad to permit it to formulate rules relating to any service where interference from these devices is a serious problem.” Such language, it was believed, would be “sufficiently broad to permit it to formulate rules relating to any service where interference from these devices is a serious problem.” We conclude that a voluntary program with minimum standards to prevent radio interference to consumer IoT products is consistent with the text and history of section 302.
149. Further, we have previously imposed security requirements that prevent unauthorized parties from accessing and alerting technology to cause radio interference under our section 302 authority. In 2020, we required that access points to automated frequency coordination systems were secure so unauthorized parties could not alter the list of available frequencies and power levels sent to an access point. We agree with Comcast that our previous actions requiring end user devices to “contain security features sufficient to protect against modification of software and firmware by any unauthorized parties” and actions to secure unlicensed national information infrastructure devices are sufficiently analogous to this proceeding as to be supported by our section 302 authority.
150. Finally, consistent with our tentative conclusion in the IoT Labeling NPRM, we find that our section 302 authority enables us to rely on third parties in carrying out the implementation details of our Program. As the Commission pointed out in the NPRM, section 302(e) of the Act authorizes the Commission to delegate equipment testing and certification to private laboratories, and the Commission already has relied in part on third parties in carrying out its equipment authorization rules that likewise implement section 302 of the Act.
151. These final rules include regulatory text that is incorporated by reference. In accordance with requirements of 1 CFR 51.5 , the Commission describes the incorporated materials here. These final rules are incorporating by reference the following ISO/IEC standards: ISO/IEC 17011:2017(E), Conformity assessment—Requirements for accreditation bodies accrediting conformity assessment bodies, Second Edition, November 2017, ISO/IEC 17025:2017(E), General requirements for the competence of testing and calibration laboratories, Third Edition, November 2017, and ISO/IEC 17065:2012(E), Conformity assessment—Requirements for bodies certifying products, processes and services, First Edition, 2012-09-15, which establish international standards requirements for accreditation bodies accrediting conformity assessment bodies; general requirements for testing and calibration laboratories; and conformity assessment requirements for certifying products, processes, and services; respectively. Copies of these standards are available for purchase from the American National Standards Institute (ANSI) through its NSSN operation ( www.nssn.org ) at Customer Service, American National Standards Institute, 25 West 43rd Street, New York, NY 10036, telephone (212) 642-4900.
152. Paperwork Reduction Act. This document contains new and modified information collection requirements subject to the Paperwork Reduction Act of 1995 (PRA), Public Law 104-13 . It Start Printed Page 61272 will be submitted to the Office of Management and Budget (OMB) for review under section 3507(d) of the PRA. OMB, the general public, and other Federal agencies will be invited to comment on the new or modified information collection requirements contained in this proceeding. In addition, we note that pursuant to the Small Business Paperwork Relief Act of 2002, Public Law 107-198 , see 44 U.S.C. 3506(c)(4) , we previously sought specific comment on how the Commission might further reduce the information collection burden for small business concerns with fewer than 25 employees.
153. In this document, we have assessed the effects of the operational framework for a voluntary IoT cybersecurity labeling program. Since the IoT Labeling Program is voluntary, small entities who do not participate in the IoT Labeling Program will not be subject to any new or modified reporting, recordkeeping, or other compliance obligations. Small entities that choose to participate in the IoT Labeling Program by seeking authority to affix the Cyber Trust Mark on their products will incur recordkeeping and reporting as well as other obligations that are necessary to test their IoT products to demonstrate compliance with the requirements we adopt in the Order. We find that, for the Cyber Trust Mark to have meaning for consumers, the requirements for an IoT product to receive the Cyber Trust Mark must be uniform for both small businesses and other entities. Thus, the Commission continues to maintain the view we expressed in the IoT Labeling NPRM, that the significance of mark integrity, and building confidence among consumers that devices and products containing the Cyber Trust Mark label can be trusted to be cyber secure, necessitates adherence by all entities participating in the IoT Labeling Program to the same rules regardless of size.
154. Regulatory Flexibility Act Analysis. A Final Regulatory Flexibility Act (FRFA) Analysis for the final rules adopted in the Order was prepared and can be found as Exhibit B of the FCC's Report and Order, FCC 24-26, adopted March 15, 2024, at this link: https://docs.fcc.gov/public/attachments/FCC-24-26A1.pdf .
155. OPEN Government Data Act. The OPEN Government Data Act requires agencies to make “public data assets” available under an open license and as “open Government data assets,” i.e., in machine-readable, open format, unencumbered by use restrictions other than intellectual property rights, and based on an open standard that is maintained by a standards organization. This requirement is to be implemented “in accordance with guidance by the Director” of the OMB. The term “public data asset” means “a data asset, or part thereof, maintained by the Federal Government that has been, or may be, released to the public, including any data asset, or part thereof, subject to disclosure under the Freedom of Information Act (FOIA).” A “data asset” is “a collection of data elements or data sets that may be grouped together,” and “data” is “recorded information, regardless of form or the media on which the data is recorded.” We delegate authority, including the authority to adopt rules, to the Bureau, in consultation with the agency's Chief Data Officer and after seeking public comment to the extent it deems appropriate, to determine whether to make publicly available any data assets maintained or created by the Commission within the meaning of the OPEN Government Act pursuant to the rules adopted herein, and if so, to determine when and to what extent such information should be made publicly available. Such data assets may include assets maintained by a CLA or other third party, to the extent the Commission's control or direction over those assets may bring them within the scope of the OPEN Government Act, as interpreted in the light of guidance to be issued by OMB. [ 28 ] In doing so, the Bureau shall take into account the extent to which such data assets are subject to disclosure under the FOIA.
156. People with Disabilities. To request materials in accessible formats for people with disabilities (braille, large print, electronic files, audio format), send an email to [email protected] or call the Consumer & Governmental Affairs Bureau at 202-418-0530 (voice).
157. Accordingly, it is ordered that pursuant to the authority contained in sections 1, 2, 4(i), 4(n), 302, 303(r), 312, 333, and 503, of the Communications Act of 1934, as amended, 47 U.S.C. 151 , 152 , 154(i) , 154(n) , 302a , 303(r) , 312 , 333 , 503 ; the IoT Cybersecurity Improvement Act of 2020, 15 U.S.C. 278g-3a through 278g-3e ; the Report and Order is hereby adopted.
158. It is further ordered that the Office of the Managing Director, Performance Program Management, SHALL SEND a copy of the Report and Order in a report to be sent to Congress and the Government Accountability Office pursuant to the Congressional Review Act, see 5 U.S.C. 801(a)(1)(A) .
- Communications
- Consumer protection
- Cybersecurity
- Electronic products
- Incorporation by reference, internet
- Product testing and certification
- Telecommunications
Federal Communications Commission
Marlene Dortch,
For the reasons discussed in the preamble, the Federal Communications Commission amends 47 CFR subchapter A as follows:
1. Under the authority of 47 U.S.C. 151 , 152 , 153 , 154(i)-(j) , 160 , 163 , 201 , 202 , 206 , 207 , 208 , 209 , 214 , 215 , 216 , 217 , 218 , 219 , 220 , 230 , 251 , 254 , 256 , 257 , 301 , 303 , 304 , 307 , 309 , 310 , 312 , 316 , 332 , 403 , 501 , 503 , 522 , 1302 , revise the heading for subchapter A to read as follows:
2. The authority citation for part 8 continues to read as follows:
Authority: 47 U.S.C. 151 , 152 , 153 , 154 , 163 , 201 , 202 , 206 , 207 , 208 , 209 , 216 , 217 , 257 , 301 , 302a , 303 , 304 , 307 , 309 , 312 , 316 , 332 , 403 , 501 , 503 , 522 , 1302 , 1753 .
3. Revise the heading for part 8 to read as set forth above.
4. Designate §§ 8.1, 8.2, 8.3, and 8.6 as subpart A.
5. Add a heading for newly designated subpart A to read as follows:
6. Add subpart B to read as follows:
Certain material is incorporated by reference into this subpart with the approval of the Director of the Federal Register in accordance with 5 U.S.C. 552(a) and 1 CFR part 51 . All approved incorporation by reference (IBR) material is available for inspection at the Federal Communications Commission (FCC or Commission) and at the National Archives and Records Administration (NARA). Contact the FCC at the address indicated in 47 CFR 0.401(a) , phone: (202) 418-0270. For information on the availability of this material at NARA, visit www.archives.gov/federal-register/cfr/ibr-locations or email [email protected] . The material may be obtained from the International Electrotechnical Commission (IEC), IEC Central Office, 3, rue de Varembe, CH-1211 Geneva 20, Switzerland, Email: [email protected] , www.iec.ch .
(a) ISO/IEC 17011:2017(E), Conformity assessment—Requirements for accreditation bodies accrediting conformity assessment bodies, Second Edition, November 2017; IBR approved for § 8.217.
(b) ISO/IEC 17025:2017(E), General requirements for the competence of testing and calibration laboratories, Third Edition, November 2017; IBR approved for §§ 8.217; 8.220.
(c) ISO/IEC 17065:2012(E), Conformity assessment—Requirements for bodies certifying products, processes and services, First Edition, 2012-09-15; IBR approved for § 8.220.
Note 1 to § 8.201:
The standards listed in this section are co-published with the International Organization for Standardization (ISO), 1, ch. De la Voie-Creuse, CP 56, CH-1211, Geneva 20, Switzerland; www.iso.org ; Tel.: + 41 22 749 01 11; Fax: + 41 22 733 34 30; email: [email protected] .
Note 2 to § 8.201:
ISO publications can also be purchased from the American National Standards Institute (ANSI) through its NSSN operation ( www.nssn.org ), at Customer Service, American National Standards Institute, 25 West 43rd Street, New York, NY 10036, telephone (212) 642-4900.
In order to elevate the Nation's cybersecurity posture and provide consumers with assurances regarding their baseline cybersecurity, thereby addressing risks of harmful radiofrequency interference to and from consumer internet-connected (Internet of Things or IoT) products the Federal Communications Commission establishes a labeling program for consumer IoT products.
(a) Affiliate. For purposes of this subpart and the IoT labeling program, an affiliate is defined as a person that (directly or indirectly) owns or controls, is owned or controlled by, or is under common ownership or control with, another person. For purposes of this subpart, the term own means to own an equity interest (or the equivalent thereof) of more than 10 percent.
(b) Consumer IoT products. IoT products intended primarily for consumer use, rather than enterprise or industrial use. Consumer IoT products exclude medical devices regulated by the U.S. Food and Drug Administration (FDA) and excludes motor vehicles and motor vehicle equipment regulated by the National Highway Traffic Safety Administration (NHTSA).
(c) Cybersecurity Label Administrator (CLA). An accredited third-party entity that is recognized and authorized by the Commission to manage and administer the labeling program in accordance with the Commission's rules in this subpart.
(d) Cybersecurity Testing Laboratory (CyberLAB). Accredited third-party entities recognized and authorized by a CLA to assess consumer IoT products for compliance with requirements of the labeling program.
(e) Cyber Trust Mark. A visual indicator indicating a consumer IoT product complies with program requirements of the labeling program and the Commission's minimum cybersecurity requirements in this subpart.
(f) FCC IoT Label. A binary label displayable with a consumer IoT product complying with program requirements of the labeling program, the binary label bearing the Cyber Trust Mark, and a scannable QR code that directs consumers to a registry containing further information on the complying consumer IoT product.
(g) Intentional radiator. A device that intentionally generates and emits radiofrequency energy by radiation or induction.
(h) Internet-connected device. A device capable of connecting to the internet and exchanging data with other devices or centralized systems over the internet.
(i) IoT device. (1) An internet-connected device capable of intentionally emitting radiofrequency energy that has at least one transducer (sensor or actuator) for interacting directly with the physical world; coupled with
(2) At least one network interface ( e.g., Wi-Fi, Bluetooth) for interfacing with the digital world.
(j) IoT product. An IoT device and any additional product components ( e.g., backend, gateway, mobile app) that are necessary to use the IoT device beyond basic operational features, including data communications links to components outside this scope but excluding those external components and any external third-party components that are outside the manufacturer's control.
(k) Labeling program. A voluntary program for consumer IoT products that allows a complying consumer IoT product to display an FCC IoT Label.
(l) Lead Administrator. A CLA selected from among Cybersecurity Label Administrators (CLAs) to be responsible for carrying out additional administrative responsibilities of the labeling program.
(m) Product components. Hardware devices, plus supporting components that generally fall into three main types per NISTIR 8425: specialty networking/gateway hardware ( e.g., a hub within the system where the IoT device is used); companion application software ( e.g., a mobile app for communicating with the IoT device); and backends ( e.g., a cloud service, or multiple services, that may store and/or process data from the IoT device). Should a product component also support other IoT products through alternative features and interfaces, these alternative features and interfaces may, through risk-assessment, be considered as separate from and not part of the IoT product for purposes of authorization.
(n) Registry. Information presented to consumers about consumer IoT products that comply with the program requirements of the labeling program, the registry is publicly accessible through a link from the QR Code of the FCC IoT Label displayed with the complying consumer IoT product, and containing information about the complying consumer IoT product, manufacturer of the complying Start Printed Page 61274 consumer IoT product, and other information as required by the labeling program.
All consumer IoT products produced by sources listed in this subpart are prohibited from obtaining use of the FCC IoT Label under this subpart. This includes:
(a) All communications equipment on the Covered List, as established pursuant to 47 CFR 1.50002 ;
(b) All IoT products containing IoT devices or product components produced by entities listed in paragraph (c) or (d) of this section;
(c) IoT devices or IoT products produced by any entity, its affiliates, or subsidiaries identified on the Covered List as producing covered equipment, as established pursuant to 47 CFR 1.50002 ;
(d) IoT devices or IoT products produced by any entity, its affiliates, or subsidiaries identified on the Department of Commerce's Entity List, 15 CFR part 744 , supplement no. 4, and/or the Department of Defense's List of Chinese Military Companies, U.S. Department of Defense, Entities Identified as Chinese Military Companies Operating in the United States in Accordance with Section 1260H of the William M. (“Mac”) Thornberry National Defense Authorization Act for Fiscal Year 2021 ( Pub. L. 116-283 ), Tranche 2 (2022), https://media.defense.gov/2022/Oct/05/2003091659/-1/-1/0/1260H%20COMPANIES.PDF . and
(e) Products produced by any entity owned or controlled by or affiliated with any person or entity that has been suspended or debarred from receiving Federal procurements or financial awards, to include all entities and individuals published as ineligible for award on the General Service Administration's System for Award Management.
(a) Cybersecurity labeling authorization is an authorization issued by a Cybersecurity Label Administrator (CLA) and authorized under the authority of the Commission, which grants an applicant of a complying consumer IoT product to display the FCC IoT Label on the relevant packaging for the complying consumer product, based on compliance with the program requirements as determined by the CLA.
(b) Cybersecurity labeling authorization attaches to all units of the complying consumer IoT product subsequently marketed by the grantee that are identical (see § 8.206) to the sample determined to comply with the program requirements except for permissive changes or other variations authorized by the Commission.
As used in this subpart, the term identical means identical within the variation that can be expected to arise as a result of quantity production techniques.
In the case of a complying consumer IoT product that has been granted authorization to use the FCC IoT Label, the applicant to whom that grant of cybersecurity labeling authorization is issued is responsible for continued compliance with the program requirements for continued use of the FCC IoT Label.
(a) An application to certify the consumer IoT product as being compliant with the labeling program shall be submitted in writing to a Cybersecurity Labeling Administrator (CLA) in the form and format prescribed by the Commission. Each application shall be accompanied by all information required by this subpart.
(b) The applicant shall provide to the CLA in the application all information that the CLA requires to determine compliance with the program requirements of the labeling program.
(c) The applicant will provide a declaration under penalty of perjury that all of the following are true and correct:
(1) The product for which the applicant seeks to use the FCC IoT Label through cybersecurity certification meets all the requirements of the IoT labeling program.
(2) The applicant is not identified as an entity producing covered communications equipment on the Covered List, established pursuant to 47 CFR 1.50002 .
(3) The product is not comprised of “covered” equipment on the Covered List.
(4) The product is not produced by any entity, its affiliates, or subsidiaries identified on the Department of Commerce's Entity List, 15 CFR part 744 , supplement no. 4, and/or the Department of Defense's List of Chinese Military Companies, U.S. Department of Defense, Entities Identified as Chinese Military Companies Operating in the United States in Accordance with Section 1260H of the William M. (“Mac”) Thornberry National Defense Authorization Act for Fiscal Year 2021 ( Pub. L. 116-283 ), Tranche 2 (2022), https://media.defense.gov/2022/Oct/05/2003091659/-1/-1/0/1260H%20COMPANIES.PDF ; and
(5) The product is not owned or controlled by or affiliated with any person or entity that has been suspended or debarred from receiving Federal procurements or financial awards, to include all entities and individuals published as ineligible for award on the General Service Administration's System for Award Management as described in § 8.204.
(6) The applicant has taken every reasonable measure to create a securable product.
(7) The applicant will, until the support period end date disclosed in the registry, diligently identify critical vulnerabilities in our products and promptly issue software updates correcting them, unless such updates are not reasonably needed to protect against security failures.
(8) The applicant will not elsewhere disclaim or otherwise attempt to limit the substantive or procedural enforceability of this declaration or of any other representations and commitments made on the FCC IoT Label or made for purposes of acquiring or maintaining authorization to use it.
(d) The applicant shall provide a written and signed declaration to the CLA that all statements it makes in the application are true and correct to the best of its knowledge and belief.
(e) Each application, including amendments thereto, and related statements of fact and authorizations required by the Commission, shall be signed by the applicant or their authorized agent.
(f) The applicant declares the product is reasonably secure and will be updated through minimum support period for the product and the end date of the support period must be disclosed.
(g) The applicant shall declare under penalty of perjury that the consumer IoT product for which the applicant is applying for participation in the labeling program is not prohibited pursuant to § 8.204.
(h) If the identified listed sources under § 8.204 are modified after the date of the declaration required by paragraph (c) of this section but prior to grant of authorization to use the FCC IoT Label, then the applicant shall provide a new declaration as required by paragraph (c).
(i) The applicant shall designate an agent located in the United States for the purpose of accepting service of process on behalf of the applicant.
(1) The applicant shall provide a written attestation: Start Printed Page 61275
(i) Signed by both the applicant and its designated agent for service of process, if different from the applicant;
(ii) Acknowledging the applicant's consent and the designated agent's obligation to accept service of process in the United States for matters related to the applicable product, and at the physical U.S. address and email address of its designated agent; and
(iii) Acknowledging the applicant's acceptance of its obligation to maintain an agent for service of process in the United States for no less than one year after either the grantee has permanently terminated all marketing and importation of the applicable equipment within the U.S., or the conclusion of any Commission-related administrative or judicial proceeding involving the product, whichever is later.
(2) An applicant located in the United States may designate itself as the agent for service of process.
(j) Technical test data submitted to the CLA shall be signed by the person who performed or supervised the tests. The person signing the test data shall attest to the accuracy of such data. The CLA may require the person signing the test data to submit a statement showing that they are qualified to make or supervise the required measurements.
(k) Signed, as used in this section, means an original handwritten signature or any symbol executed or adopted by the applicant or CLA with the intent that such symbol be a signature, including symbols formed by computer-generated electronic impulses.
(a) A CLA will grant cybersecurity labeling authorization if it finds from an examination of the application and supporting data, or other matter which it may officially notice, that the consumer IoT product complies with the program requirements.
(b) Grants will be made in writing showing the effective date of the grant.
(c) Cybersecurity certification shall not attach to any product, nor shall any use of the Cyber Trust Mark be deemed effective, until the application has been granted.
(d) Grants will be effective from the date of authorization.
(e) The grant shall identify the CLA granting the authorization and the Commission as the issuing authority.
(f) In cases of a dispute, the Commission will be the final arbiter.
(a) An application that is not in accordance with the provisions of this subpart may be dismissed.
(b) Any application, upon written request signed by the applicant or their agent, may be dismissed prior to a determination granting or denying the authorization requested.
(c) If an applicant is requested to submit additional documents or information and fails to submit the requested material within the specified time period, the application may be dismissed.
If the CLA is unable to make the findings specified in § 8.209(a), it will deny the application. Notification of the denial to the applicant will include a statement of the reasons for the denial.
(a) Seeking review from a CLA. Any party aggrieved by an action taken by a CLA must first seek review from the CLA. The CLA should respond to appeals of their decisions in a timely manner and within 10 business days of receipt of a request for review.
(b) Seeking review from the Commission. A party aggrieved by an action taken by a CLA may, after seeking review by the CLA, seek review from the Commission.
(c) Filing deadlines. (1) An aggrieved party seeking review of a CLA decision by the CLA shall submit such a request within sixty (60) days from the date the CLA issues a decision. Such request shall be deemed submitted when received by the CLA.
(2) An aggrieved party seeking review of a CLA decision by the Commission shall file such a request within sixty (60) days from the date the CLA issues a decision on the party's request for review. Parties must adhere to the time periods for filing oppositions and replies set forth in 47 CFR 1.45 .
(d) Review by the Public Safety and Homeland Security Bureau or the Commission. (1) Requests for review of CLA decisions that are submitted to the Federal Communications Commission shall be considered and acted upon by the Public Safety and Homeland Security Bureau; provided, however, that requests for review that raise novel questions of fact, law or policy shall be considered by the full Commission.
(2) An aggrieved party may seek review of a decision issued under delegated authority by the Public Safety and Homeland Security Bureau pursuant to the rules set forth in 47 CFR part 1 .
(e) Standard of review. (1) The Public Safety and Homeland Security Bureau shall conduct de novo review of request for review of decisions issued by the CLA.
(2) The Federal Communications Commission shall conduct de novo review of requests for review of decisions by the CLA that involve novel questions of fact, law, or policy; provided, however, that the Commission shall not conduct de novo review of decisions issued by the Public Safety and Homeland Security Bureau under delegated authority.
(f) Time periods for Commission review of CLA decisions. (1) The Public Safety and Homeland Security Bureau shall, within forty-five (45) days, take action in response to a request for review of a CLA decision that is properly before it. The Public Safety and Homeland Security Bureau may extend the time period for taking action on a request for review of a CLA decision for a period of up to ninety days. The Commission may also at any time, extend the time period for taking action of a request for review of a CLA decision pending before the Public Safety and Homeland Security Bureau.
(2) The Commission shall issue a written decision in response to a request for review of a CLA decision that involves novel questions of fact, law, or policy within forty-five (45) days. The Commission may extend the time period for taking action on the request for review of a CLA decision. The Public Safety and Homeland Security Bureau also may extend action on a request for review of a CLA decision for a period of up to ninety days.
(g) No authorization pending CLA review. While a party seeks review of a CLA decision, they are not authorized to use the FCC IoT Label until the Commission issues a final decision authorizing their use of the FCC IoT Label.
(a) A grant of authorization to use the FCC IoT Label remains effective until set aside, revoked or withdrawn, rescinded, surrendered, or a termination date is otherwise established by the Commission.
(b) No person shall, in any advertising matter, brochure, etc., use or make reference to the FCC IoT Label or the Cyber Trust Mark in a deceptive or misleading manner.
When a complaint is filed directly with the Commission or submitted to the Commission by the Lead Administrator or other party concerning a consumer IoT product being non-compliant with the labeling program, and the Commission determines that the Start Printed Page 61276 complaint is justified, the Commission may require the grantee to investigate such complaint and report the results of such investigation to the Commission within 20 days. The report shall also indicate what action if any has been taken or is proposed to be taken by the grantee to correct the defect, both in terms of future production and with reference to articles in the possession of users, sellers, and distributors.
(a) For complying consumer IoT products granted authorization to use the FCC IoT Label, the grantee shall maintain the records listed as follows:
(1) A record of the original design and specifications and all changes that have been made to the complying consumer IoT product that may affect compliance with the standards and testing procedures of this subpart.
(2) A record of the procedures used for production inspection and testing to ensure conformance with the standards and testing procedures of this subpart.
(3) A record of the test results that demonstrate compliance with the appropriate regulations in this chapter.
(b) Records shall be retained for a two-year period after the marketing of the associated product has been permanently discontinued, or until the conclusion of an investigation or a proceeding if the grantee is officially notified that an investigation or any other administrative proceeding involving its product has been instituted.
(a) Grant of authorization to use the FCC IoT Label is automatically terminated by notice of the Bureau following submission of a report as specified in § 8.214 has not been adequately corrected:
(1) For false statements or representations made either in the application or in materials or response submitted in connection therewith or in records required to be kept by § 8.215.
(2) If upon subsequent inspection or operation it is determined that the consumer IoT product does not conform to the pertinent technical requirements in this subpart or to the representations made in the original application.
(3) Because of conditions coming to the attention of the Commission which would warrant it in refusing to grant authorization to use the FCC IoT Label.
(4) Because the grantee or affiliate has been listed as described in § 8.204.
(b) [Reserved]
(a) A CyberLAB providing testing of products seeking a grant of authorization to use the FCC IoT Label shall be accredited by a recognized accreditation body, which must attest that the CyberLAB has demonstrated:
(1) Technical expertise in cybersecurity testing and conformity assessment of IoT devices and products.
(2) Compliance with accreditation requirements based on ISO/IEC 17025 (incorporated by reference, see § 8.201).
(3) Knowledge of FCC rules and procedures associated with products compliance testing and cybersecurity certification.
(4) Necessary equipment, facilities, and personnel to conduct cybersecurity testing and conformity assessment of IoT devices and products.
(5) Documented procedures for conformity assessment.
(6) Implementation of controls to eliminate potential conflicts of interests, particularly with regard to commercially sensitive information.
(7) That the CyberLAB is not an organization, its affiliates, or subsidiaries identified by the listed sources of prohibition under § 8.204.
(8) That it has certified the truth and accuracy of all information it has submitted to support its accreditation.
(b) Once accredited or recognized the CyberLAB will be periodically audited and reviewed to ensure they continue to comply with the requirements of the ISO/IEC 17025 standard.
(c) The Lead Administrator will verify that the CyberLAB is not listed in any of the lists in § 8.204.
(d) The Lead Administrator will maintain a list of accredited CyberLABs that it has recognized, and make publicly available the list of accredited CyberLAB. Inclusion of a CyberLAB on the accredited list does not constitute Commission endorsement of that facility. Recognition afforded to a CyberLAB under the labeling program will be automatically terminated for entities that are subsequently placed on the Covered List, listed sources of prohibition under § 8.204, or of it, its affiliate, or subsidiary is owned or controlled by a foreign adversary country defined by the Department of Commerce in 15 CFR 7.4 .
(e) In order to be recognized and included on the list in paragraph (d) of this section, the accrediting organization must submit the information in paragraphs (e)(1) through (9) of this section to the Lead Administrator:
(1) Laboratory name, location of test site(s), mailing address and contact information;
(2) Name of accrediting organization;
(3) Scope of laboratory accreditation;
(4) Date of expiration of accreditation;
(5) Designation number;
(6) FCC Registration Number (FRN);
(7) A statement as to whether or not the laboratory performs testing on a contract basis;
(8) For laboratories outside the United States, details of the arrangement under which the accreditation of the laboratory is recognized; and
(9) Other information as requested by the Commission.
(f) A laboratory that has been accredited with a scope covering the measurements required for the types of IoT products that it will test shall be deemed competent to test and submit test data for IoT products subject to cybersecurity certification. Such a laboratory shall be accredited by a Public Safety and Homeland Security Bureau-recognized accreditation organization based on ISO/IEC 17025. The organization accrediting the laboratory must be recognized by the Public Safety and Homeland Security Bureau to perform such accreditation based on ISO/IEC 17011 (incorporated by reference, see § 8.201). The frequency for reassessment of the test facility and the information that is required to be filed or retained by the testing party shall comply with the requirements established by the accrediting organization, but shall occur on an interval not to exceed two years.
(a) A party wishing to become a laboratory accreditation body recognized by the Public Safety and Homeland Security Bureau (PSHSB or Bureau) must submit a written request to the Chief of PSHSB requesting such recognition. PSHSB will make a determination based on the information provided in support of the request for recognition.
(b) Applicants shall provide the information in paragraphs (b)(1) through (4) of this section as evidence of their credentials and qualifications to perform accreditation of laboratories that test equipment to Commission requirements, consistent with the requirements of § 8.217(e). PSHSB may request additional information, or showings, as needed, to determine the applicant's credentials and qualifications.
(1) Successful completion of an ISO/IEC 17011 peer review, such as being a signatory to an accreditation agreement that is acceptable to the Commission.
(2) Experience with the accreditation of conformity assessment testing laboratories to ISO/IEC 17025. Start Printed Page 61277
(3) Accreditation personnel/assessors with specific technical experience on the Commission cybersecurity certification rules and requirements.
(4) Procedures and policies developed for the accreditation of testing laboratories for FCC cybersecurity certification programs.
(a) An accredited third-party entity wishing to become a Cybersecurity Label Administrator (CLA) must file a written application with the Commission. The Commission may approve the written application for the accredited third-party entity to be recognized and authorized by the Commission as a CLA to manage and administer the labeling program by meeting the requirements of paragraph (b) of this section. An accredited third-party entity is recognized and authorized by the Commission to manage and administer the labeling program in accordance with the Commission's rules in this subpart.
(b) In the United States, the Commission, in accordance with its procedures, allows qualified accrediting bodies to accredit CLAs based on ISO/IEC 17065 and other qualification criteria. CLAs shall comply with the requirements in § 8.220.
(a) In general. CLAs designated by the Commission, or designated by another authority recognized by the Commission, shall comply with the requirements of this section. Each entity seeking authority to act as a CLA must file an application with the Commission for consideration by PSHSB, which includes a description of its organization structure, an explanation of how it will avoid personal and organizational conflict when processing applications, a description of its processes for evaluating applications seeking authority to use the FCC IoT Label, and a demonstration of expertise that will be necessary to effectively serve as a CLA including, but not limited to, the criteria in paragraph (c) of this section.
(b) Methodology for reviewing applications. (1) A CLA's methodology for reviewing applications shall be based on type testing as identified in ISO/IEC 17065 (incorporated by reference, see § 8.201).
(2) A CLA's grant of authorization to use the FCC IoT Label shall be based on the application with all the information specified in this part. The CLA shall review the application to determine compliance with the Commission's requirements in this subpart and shall issue a grant of product cybersecurity certification in accordance with § 8.208.
(c) Criteria for designation. (1) To be designated as a CLA under this section, an entity shall demonstrate cybersecurity expertise and capabilities in addition to industry knowledge of IoT and IoT labeling requirements.
(2) The entity shall demonstrate expert knowledge of National Institute of Standards and Technology's (NIST) cybersecurity guidance, including but not limited to NIST's recommended criteria and labeling program approaches for cybersecurity labeling of consumer IoT products.
(3) The entity shall demonstrate expert knowledge of FCC rules and procedures associated with product compliance testing and certification.
(4) The entity shall demonstrate knowledge of Federal law and guidance governing the security and privacy of agency information systems.
(5) The entity shall demonstrate an ability to securely handle large volumes of information and demonstrate internal security practices.
(6) To expedite initial deployment of the FCC labeling program, the Commission will accept and conditionally approve applications from entities seeking to be designated as a CLA provided they commit to obtain accreditation pursuant to all the requirements associated with ISO/IEC 17065 with the appropriate scope within six (6) months of the effective date by the adopted standards and testing procedures and otherwise meet the FCC's IoT Labeling Program requirements. The entity must also demonstrate implementation of controls to eliminate actual or potential conflicts of interests (including both personal and organizational), particularly with regard to commercially sensitive information. The Bureau will finalize the entity's application upon receipt and demonstration of ISO/IEC 17065 accreditation with the appropriate scope.
(7) The entity is not owned or controlled by or affiliated with any entity identified on the Commission's Covered List, listed sources of prohibition under § 8.204, or of it, its affiliate, or subsidiary is owned or controlled by a foreign adversary country defined by the Department of Commerce in 15 CFR 7.4 .
(8) The entity must demonstrate it has implemented controls to eliminate actual or potential conflicts of interests (including both personal and organizational), particularly with regard to commercially sensitive information, to include but not limited to, remaining impartial and unbiased and prevent them from giving preferential treatment to certain applications ( e.g., application line jumping) and from implementing heightened scrutiny of applications from entities not members or otherwise aligned with the CLA.
(d) External resources. (1) In accordance with the provisions of ISO/IEC 17065 the evaluation of a product, or a portion thereof, may be performed by bodies that meet the applicable requirements of ISO/IEC 17025, in accordance with the applicable provisions of ISO/IEC 17065 for external resources (outsourcing). Evaluation is the selection of applicable requirements and the determination that those requirements are met. Evaluation may be performed using internal CLA resources or external (outsourced) resources.
(2) A CLA shall not outsource review or decision activities.
(3) When external resources are used to provide the evaluation function, including the testing of products subject to labeling, the CLA shall be responsible for the evaluation and shall maintain appropriate oversight of the external resources used to ensure reliability of the evaluation. Such oversight shall include periodic audits of products that have been tested and other activities as required in ISO/IEC 17065 when a CLA uses external resources for evaluation.
(e) Commission approves a CLA. (1) The Commission will approve as a CLA:
(i) Any entity in the United States that meets the requirements of this section.
(ii) The Commission will not approve as a CLA any organization, its affiliates, or subsidiaries listed in the listed sources of prohibition under § 8.204.
(2) The Commission will withdraw its approval of a CLA if the CLA's designation or accreditation is withdrawn, if the Commission determines there is just cause for withdrawing the approval, or upon request of the CLA. The Commission will limit the scope of products that can be certified by a CLA if its accreditor limits the scope of its accreditation or if the Commission determines there is good cause to do so. The Commission will notify a CLA in writing of its intention to withdraw or limit the scope of the CLA's approval and provide at least 60 days for the CLA to respond.
(3) The Commission will notify a CLA in writing when it has concerns or evidence that the CLA is not carrying out its responsibilities under the labeling program in accordance with the Commission's rules in this subpart and policies and request that it explain and correct any apparent deficiencies. Start Printed Page 61278
(4) The Public Safety and Homeland Security Bureau shall provide notice to the CLA that the Bureau proposes to terminate the CLA's authority and provide the CLA a reasonable opportunity to respond (not more than 20 days) before reaching a decision on possible termination.
(5) If the Commission withdraws its recognition of a CLA, all grants issued by that CLA will remain valid unless specifically set aside or revoked by the Commission.
(6) A list of recognized CLAs will be published by the Commission.
(f) Scope of responsibility. (1) A CLA shall receive and evaluate applications and supporting data requesting authority to use the FCC IoT Label on the product subject to the application.
(2) A CLA shall grant authorization to use the FCC IoT Label with a complying consumer IoT product in accordance with the Commission's rules in this subpart and policies.
(3) A CLA shall accept test data from any Lead Administrator-recognized accredited CyberLAB, subject to the requirements in ISO/IEC 17065 and shall not unnecessarily repeat tests.
(4) A CLA may establish and assess fees for processing applications and other Commission-required tasks.
(5) A CLA may only act on applications that it has received or which it has issued a certification authorizing use of the FCC IoT Label.
(6) A CLA shall dismiss an application that is not in accordance with the provisions of this subpart or when the applicant requests dismissal, and may dismiss an application if the applicant does not submit additional information or test samples requested by the CLA.
(7) A CLA shall ensure that manufacturers make all required information accessible to the IoT registry.
(8) A CLA shall participate in a consumer education campaign in coordination with the Lead Administrator.
(9) A CLA shall receive complaints alleging a product bearing the FCC IoT Label does not support the cybersecurity criteria conveyed by the Cyber Trust Mark and refer these complaints to the Lead Administrator which will notify the Public Safety and Homeland Security Bureau.
(10) A CLA may not:
(i) Make policy, interpret unclear provisions of the statute or rules, or interpret the intent of Congress;
(ii) Grant a waiver of the rules in this subpart; or
(iii) Take enforcement actions.
(11) All CLA actions are subject to Commission review.
(g) Post-market surveillance requirements. (1) In accordance with ISO/IEC 17065, a CLA shall perform appropriate post-market surveillance activities. These activities shall be based on type testing a certain number of samples of the total number of product types for which the CLA has certified use of the Label.
(2) PSHSB may request that a grantee of authority to use the FCC IoT Label submit a product sample directly to the CLA that evaluated the grantee's application as part of the post market surveillance. Any product samples requested by the Commission and tested by the CLA will be counted toward a minimum number of samples that the CLA must test to meet its post market surveillance requirements.
(3) A CLA may also request a grantee submit samples of products that the CLA has certified to use the FCC IoT Label directly to the CLA.
(4) If during post market surveillance of a complying consumer IoT product, a CLA determines that the product fails to comply with the technical regulations (or other FCC requirements) for that product, the CLA shall immediately notify the grantee and the Commission in writing of its findings. The grantee shall provide a report to the CLA describing the actions taken to correct the situation, as provided in § 8.216, and the CLA shall provide a report of these actions to the Commission within 30 days.
(5) CLAs shall submit periodic reports to the Commission of their post-market surveillance activities and findings in a format and by a date specified by the Commission.
(a) Establishing a Lead Administrator. If more than one qualified entity is selected by the Commission to be a CLA, the Commission will select a Lead Administrator. The Lead Administrator shall:
(1) Interface with the Commission on behalf of the CLAs, including but not limited to submitting to the Bureau all complaints alleging a product bearing the FCC IoT Label does not meet the requirements of the Commission's labeling program;
(2) Coordinate with CLAs and moderate stakeholder meetings;
(3) Accept, review, and approve or deny applications from labs seeking recognition as a lab authorized to perform the conformity testing necessary to support an application for authority to affix the FCC IoT Label, and maintain a publicly available list of Lead Administrator-recognized labs and a list of labs that have lost their recognition;
(4) Within 90 days of election as Lead Administrator, the Lead Administrator will, in collaboration with the CLAs and stakeholders ( e.g., cyber experts from industry, government, and academia):
(i) Submit to the Bureau recommendations identifying and/or developing the technical standards and testing procedures for the Commission to consider with regard to at least one class of IoT products eligible for the IoT labeling program. The Bureau will evaluate the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules in this subpart;
(ii) Submit to the Bureau a recommendation on how often a given class of IoT products must renew their request for authority to bear the FCC IoT Label, which may be dependent on the type of product, and that such a recommendation be submitted in connection with the relevant standards recommendations for an IoT product or class of IoT products. The Bureau will evaluate the recommendations, and if the Bureau approves of the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules in this subpart;
(iii) Submit to the Bureau a recommendation on procedures for post market surveillance by the CLAs. The Bureau will evaluate the recommendations, and if the Bureau approves of the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules in this subpart;
(iv) Make recommendations to the Bureau with regard to updates to the registry including whether the registry should be in additional languages, and if so, to recommend specific languages for inclusion; and
(v) Submit to the Bureau recommendations on the design of the FCC IoT Label, including but not limited to labeling design and placement ( e.g., size and white spaces, product packaging) and whether to include the product support end date on labels for certain products or category of products. The Bureau will evaluate the recommendations, and if the Bureau approves of the recommendations, subject to any required public notice and comment, incorporate them by reference into the Commission's rules in this subpart;
(5) Within 45 days of publication of updates or changes to NIST guidelines, or adoption by NIST of new guidelines, Start Printed Page 61279 recommend in collaboration with CLAs and other stakeholders any appropriate modifications to the labeling program standards and testing procedures to stay aligned with the NIST guidelines;
(6) Submit to the Commission reports on CLAs' post-market surveillance activities and findings in the format and by the date specified by Public Safety and Homeland Security Bureau;
(7) Develop in collaboration with stakeholders a consumer education campaign, submit the plan to the Public Safety and Homeland Security Bureau, and participate in consumer education;
(8) Receive complaints about the labeling program, including but not limited to consumer complaints about the registry and coordinate with manufacturers to resolve any technical problems associated with consumers accessing the information in the registry;
(9) Facilitate coordination between CLAs; and
(10) Submit to the Commission any other reports upon request of the Commission or as required by Commission rules in this subpart.
(b) Criteria for designation. In addition to completing the CLA application information, entities seeking to be the Lead Administrator will submit a description of how they will execute the duties of the Lead Administrator, including:
(1) Their previous experience in IoT cybersecurity;
(2) What role, if any, they have played in IoT labeling;
(3) Their capacity to execute the Lead Administrator duties;
(4) How they would engage and collaborate with stakeholders to identify or develop the Bureau recommendations;
(5) A proposed consumer education campaign; and
(6) Additional information the applicant believes demonstrates why they should be the Lead Administrator.
(a) A grantee of authority to use the FCC IoT Label shall provide information about the complying consumer IoT product to the public. Information supplied by grantees shall be made available in a dynamic, decentralized, publicly accessible registry through a common Application Programming Interface (API) that is secure by design.
(b) A grantee of authority to use the FCC IoT Label shall publish the following information through the common API in the Registry:
(1) Product Name;
(2) Manufacturer name;
(3) Date the product received authorization ( i.e., cybersecurity certification) to affix the label and current status of the authorization (if applicable);
(4) Name and contact information of the CLA that authorized use of the FCC IoT Label;
(5) Name of the lab that conducted the conformity testing;
(6) Instructions on how to change the default password (specifically state if the default password cannot be changed);
(7) Information (or link) for additional information on how to configure the device securely;
(8) Information as to whether software updates and patches are automatic and how to access security updates/patches if they are not automatic;
(9) The date until which the entity promises to diligently identify critical vulnerabilities in the product and promptly issue software updates correcting them, unless such an update is not reasonably needed to protect against cybersecurity failures ( i.e., the minimum support period); alternatively, a statement that the device is unsupported and that the purchaser should not rely on the manufacturer to release security updates;
(10) Disclosure of whether the manufacturer maintains a Hardware Bill of Materials (HBOM) and/or a Software Bill of Materials (SBOM); and
(11) Additional data elements that the Bureau deems necessary.
1. Motor Vehicle “means a vehicle driven or drawn by mechanical power and manufactured primarily for use on public streets, roads, and highways, but does not include a vehicle operated only on a rail line.” 49 U.S.C. 30102(7) .
2. For purposes of the IoT Labeling Program, the NISTIR 8425 scoping definition of “components” falls into three main types: Specialty networking/gateway hardware ( e.g., a hub within the system where the IoT device is used); Companion application software ( e.g., a mobile app for communicating with the IoT device); and Backends ( e.g., a cloud service, or multiple services, that may store and/or process data from the IoT device). See NISTIR 8425 at 2. Our use of this scoping definition of “components” is intended only to apply to the IoT Labeling program. We note that Commission rules use the term “components” in a variety or contexts and different rule provisions, and we are not intending to affect the use of that term in those other contexts.
2. To further clarify, nothing in this item prohibits manufacturers from allowing product owners from installing the software of their choice, from disabling security features, or from replacing or modifying components of a product, including the firmware and software. An IoT manufacturer cannot be held responsible for the owner's decision to make such changes, just as a traditional product manufacturer cannot be responsible for the actions of a consumer who modifies the core mechanisms of a product and thereby risks rendering it unsafe. However, we reiterate that in order to be authorized to use the FCC IoT Label, manufacturers must meet the requirements of the program.
3. There are many types IoT devices and products, which may be divided into various categories or classes based on their purpose, application, and functionality. These classes of IoT devices and products include smart home ( e.g., smart thermostats, smart lights, smart locks, smart cameras), wearables ( e.g., fitness trackers, smart watches), and Healthcare ( e.g., remote patient monitoring devices, smart medical equipment). It is worth noting that not all IoT devices or products are created equal, in terms of features, security and the level of risk they present. Additionally, from security standpoint, an IoT product that is appropriate for consumer or home use may not be suitable for industrial or enterprise environment. These differences suggest the need for different security standards that distinguish between low-risk, medium-risk and high-risk applications. Our approach to identifying the specific cybersecurity standards to apply enables us to appropriately account for that in the case of particular wireless consumer products (or categories of such products) in our initial implementation of the IoT Labeling Program.
4. The organization(s) accrediting the prospective Label Administrators and testing labs must meet the requirements and conditions in ISO/IEC 17011. See 47 CFR 8.910(b)(1) ISO/IEC 17011:2004(E), “Conformity assessment—General requirements for accreditation bodies accrediting conformity assessment bodies,” First Edition, 2004-09-01, IBR approved for §§ 8.217(e) and 8.218(b).
5. There appeared to be some confusion in the record with the Commission's use of the term Cybersecurity Labeling Authorization Bodies. Specifically, the ANSI National Accreditation Board (ANAB) recommended the Commission reconsider the use of the term “CyberLAB” as the “implication that such organizations are laboratories could create market confusion.” ANAB Reply at 2. We disagree that the term CyberLAB may be confusing because these organizations are, in fact, laboratories/testing bodies that will be testing products to determine compliance with applicable standards. The CyberLABs, however, are not “certification bodies.” Rather, the entity that will be authorizing an applicant to use the Cyber Trust Mark on their product is the CLA, as described below. To ensure there is no confusion, the Commission has changed the term from Cybersecurity Labeling “Authorization Bodies” as these terms are reserved for accreditation bodies, to Cybersecurity Testing Laboratories, reflecting that the function of these labs is for testing and generating reports, and not certifying or issuing a label. We continue to use the short-form term “CyberLAB” to refer to these testing labs.
6. If the Lead Administrator, in addition to its administrative duties, intends to offer lab testing service (CLA-run lab), it must submit an application with PSHSB seeking FCC recognition as a lab authorized to perform conformity testing to support an application for authority to affix the FCC IoT Label. The Lead Administrator is not authorized to recognize its own cybersecurity testing lab. If approved by PSHSB, the Lead Administrator will add the name of its lab to the list of recognized labs.
7. This process does not foreclose the ability of consumers to file an informal complaint in accordance with the Commission's rules. See 47 CFR 1.716 through 1.719 . In the event an informal complaint is filed with the Commission, the complaint will be forwarded to the Lead Administrator for investigation and/or referral to the issuing CLA.
8. As below, we emphasize the importance of leveraging existing expertise in this space, and as such adopt as a criterion for consideration in selecting the lead administrator the ability to convene and develop consensus among stakeholders.
9. This approach necessitates a mechanism for the Commission to recognize administrators, and we accordingly adopt a rule doing so. See 47 CFR 8.219 . We model our approach on analogous elements of our equipment authorization rules, with which the Commission and industry have substantial experience, and which have proven workable in practice. See 47 CFR 2.949 . We delegate to PSHSB and OMD authority to take any necessary steps, including adoption of additional procedures and any applicable fees (pursuant to any required public notice and comment), as necessary to ensure compliance with the Communications Act with respect to any rules adopted here that contemplate the filing of applications directly with the Commission. 47 U.S.C. 158(c) .
10. The scope of CLA's ISO/IEC 17065 certification includes certifying IoT products and devices for compliance with FCC cybersecurity standards.
11. Consistent with standard practice for accreditation, the organization accrediting the CLAs must be recognized by the Bureau to perform such accreditation based on International Standard ISO/IEC 17011.
12. Because of the public safety importance of a CLA having the requisite qualifications and adhering to our rules when evaluating requests to use the FCC IoT Label, this process should proceed appropriately expeditiously to minimize any periods of time where a CLA continues to operate in that capacity once concerns have come to PSHSB's attention. In particular, PSHSB shall provide notice to the CLA that the Bureau proposes to terminate the CLA's authority and provide the CLA a reasonable opportunity to respond (not more than 20 days) before reaching a decision on possible termination. PSHSB may suspend the CLA's ability to issues labeling authorizations during the pendency of such consideration if appropriate.
13. We also agree with CTA in highlighting the importance of PSHSB's involvement in matters where the Lead Administrator and CLAs may share vested interests.
14. We recognize the potential raised by ioXt Alliance for anticompetitive preferences in recommendations made to the Bureau if a CLA is chosen as Lead Administrator.
15. To enable the Lead Administrator to compile a reliable and verifiable list, we require accredited CyberLABs to submit certain information to the Lead Administrator: (1) Laboratory name, location of test site(s), mailing address and contact information; (2) Name of accrediting organization; (3) Scope of laboratory accreditation; (4) Date of expiration of accreditation; (5) Designation number; (6) FCC Registration Number (FRN); (7) A statement as to whether or not the laboratory performs testing on a contract basis; (8) For laboratories outside the United States, details of the arrangement under which the accreditation of the laboratory is recognized; and (9) Other information as requested by the Commission.
16. This approach necessitates a mechanism for the Commission to recognize lab accreditation bodies, and we accordingly adopt a rule doing so. See 47 CFR 8.218 . We model our approach on analogous elements of our equipment authorization rules, with which the Commission and industry have substantial experience, and which have proven workable in practice. See 47 CFR 2.949 . We delegate to PSHSB and OMD authority to take any necessary steps, including adoption of additional procedures and any applicable fees (pursuant to any required public notice and comment), as necessary to ensure compliance with the Communications Act with respect to any rules adopted here that contemplate the filing of applications directly with the Commission. 47 U.S.C 158(c) .
17. Because of the public safety importance of a CyberLAB having the requisite qualifications and adhering to our rules when evaluating requests to use the FCC IoT Label, this process should proceed appropriately expeditiously to minimize any periods of time where a CyberLAB continues to operate in that capacity once concerns have come to PSHSB's attention. In particular, PSHSB shall provide notice to the CyberLAB that the Bureau proposes to terminate the CyberLAB's authority and provide the CyberLAB a reasonable opportunity to respond (not more than 20 days) before reaching a decision on possible termination. PSHSB may suspend the CLA's ability conduct product testing during the pendency of such consideration if appropriate.
18. In addition to the discussion in the text, we adopt certain rules to support the administration and integrity of the IoT Labeling Program, including governing the designation of agents for service of process and governing required signatures. See 47 CFR 8.208(i) , (k) . We model our approach on analogous elements of our equipment authorization rules, with which the Commission and industry have substantial experience, and which have proven workable in practice. See 47 CFR 2.911(d)(7) , (f) .
19. We recognize that many of the duties of the Lead Administrator benefit all the CLAs and the program as a whole, and we do not suggest that the costs associated with the duties of the Lead Administrator as described in the Order to be an exhaustive list of the shared costs we expect to be shared among CLAs as a whole.
20. The issue of where the FCC IoT Label would be placed was raised in the record. We agree that flexibility in placement is important in instances where the consumer might not see the product's packaging, such as in larger appliances, before purchasing the product. We recognize that some types of products might be customarily displayed in ways that make a one-size-fits-all approach inappropriate. As such, we agree with the ioXt Alliance's suggestion that we consider how the label may be placed in ways that will be helpful to a consumer, such as through an in-store display, advertisement on a screen, or website.
21. In addition to the declaration, the SBOM and HBOM will be made available upon request by the Commission, CyberLAB, and/or CLA.
22. To enable a meaningful audit process it will be important to be able to review certain key records, which we consequently will require grantees to retain records regarding the original design and specifications and all changes that have been made to the relevant consumer IoT product that may affect compliance with the IoT Labeling Program requirements; a record of the procedures used for production inspection and testing; and a record of the test results that demonstrate compliance. See 47 CFR 8.215 . We model our approach on analogous elements of our equipment authorization rules, with which the Commission and industry have substantial experience, and which have proven workable in practice. See 47 CFR 2.938(a) , (f) .
23. If necessary to accommodate the volume of auditing, a CLA may outsource some post-market surveillance testing to a recognized CyberLAB, but retains responsibility for the final review.
24. In addition, to further help safeguard the integrity of the IoT Labeling Program and the FCC IoT Label, we codify a rule that prohibits any person from, in any advertising matter, brochure, etc., using or making reference to the FCC IoT Label or the Cyber Trust Mark in a deceptive or misleading manner. See 47 CFR 8.213(b) . We model our approach on analogous elements of our equipment authorization rules, with which the Commission and industry have substantial experience, and which have proven workable in practice. See 47 CFR 2.927(c) .
25. $60 million = (15,000,000*$16*(15/60)) is the estimated value for 15 minutes of time savings nationwide.
26. The Consumer Reports proposed registry architecture includes a dataset that can store images and PDFs as well as allows for device manufacturers, retailers, security researchers and administrators to access the platform. The registry, as adopted, does not include these features and therefore would not incur the costs to develop and maintain them.
27. Because we conclude that section 302 of the Act authorizes our actions in the Order, we defer consideration of other sources of authority that the Communications Act may grant the Commission over this area.
28. OMB has not yet issued final guidance.
[ FR Doc. 2024-14148 Filed 7-29-24; 8:45 am]
BILLING CODE 6712-01-P
- Executive Orders
Reader Aids
Information.
- About This Site
- Accessibility
- No Fear Act
- Continuity Information
- Share full article
Advertisement
Supported by
The Ezra Klein Show
Are Democrats Right to Unite Around Kamala Harris?
A middle path for democrats, and for harris.
The transcript of this audio essay has been edited.
Last week, the Republican Party held its quadrennial convention in Milwaukee. My colleague Elias Isquith described it as a megachurch service held in a Vegas casino under the ever-watchful gaze of its living god. All that week, I heard: America First, America First, America First. But it was clear who came first: Donald J. Trump. This was a party that had persuaded itself that one man’s ambition, his insatiable, unquenchable lust for power, was self-sacrifice. That Trump cared not for himself, that he only cared for you.
Throughout that convention, Trump was spoken of in religious terms. He was a man persecuted on behalf of all who put their faith in him. A leader on a divine mission, chosen and protected by an almighty God. If you did not believe in him, you did not believe in America.
On the final night, shortly before Trump spoke, Hulk Hogan took the stage wearing a shirt emblazoned with the American flag. He sent the crowd into a frenzy as he ripped that shirt, tearing the flag on it in half, to reveal a Donald Trump campaign shirt beneath. It was all so unbearably literal.
In 2020 and early 2021, Donald Trump tried to overturn an election he lost. He used the power of the presidency to pressure state election officials. He whipped up a mob that stormed the Capitol and endangered the lives of the men and women he served with, including his own vice president. People died on that day. How did the Republican Party react to that? Ultimately, by submitting to Trump’s fantasies and resentments. Where was Mike Pence, the vice president from Donald Trump’s first term? He was in exile, replaced by JD Vance. Pence certified the 2020 election. Vance has said he would have backed Trump’s challenge.
There was no price Trump would not have paid to cling to power, and the message of the 2024 Republican convention was that there was no price the Republican Party would not pay to give Trump that power. The message of the 2024 Republican convention was simple: Donald Trump first.
What President Biden did on Sunday — that is what it looks like to put country first. What the Democratic Party did over the past few weeks — that is what it looks like to put country first. The catastrophe of the debate, for Biden, was that he couldn’t draw the true contrast between him and Trump: Instead of highlighting Trump’s narcissism and illiberalism, Biden highlighted Trump’s relative energy and vigor. On Sunday, though, Biden upended that. In one decision, he drew a very different contrast between him and Trump: Trump would not peaceably step aside even after losing an election. Biden stepped aside before the election because he understood that the party and the country are bigger than he is. Putting your own ambitions second — that’s what it looks like to actually put America first.
We are having trouble retrieving the article content.
Please enable JavaScript in your browser settings.
Thank you for your patience while we verify access. If you are in Reader mode please exit and log into your Times account, or subscribe for all of The Times.
Thank you for your patience while we verify access.
Already a subscriber? Log in .
Want all of The Times? Subscribe .

IMAGES
VIDEO
COMMENTS
Make a claim. Provide the grounds (evidence) for the claim. Explain the warrant (how the grounds support the claim) Discuss possible rebuttals to the claim, identifying the limits of the argument and showing that you have considered alternative perspectives. The Toulmin model is a common approach in academic essays.
When you're writing a persuasive essay, you need more than just an opinion to make your voice heard. Even the strongest stance won't be compelling if it's not structured properly and reinforced with solid reasoning and evidence. Learn what elements every argumentative essay should include and how to structure it depending on your audience in this easy step-by-step guide.
An argumentative essay presents a specific claim or argument and supports it with evidence and reasoning. Here's an outline for an argumentative essay, along with examples for each section: 3. 1. Introduction: Hook: Start with a compelling statement, question, or anecdote to grab the reader's attention.
The argumentative essay requires well-researched, accurate, detailed, and current information to support the thesis statement and consider other points of view. Some factual, logical, statistical, or anecdotal evidence should support the thesis. However, students must consider multiple points of view when collecting evidence.
An argumentative essay comprises five essential components: 1. Claim. Claim in argumentative writing is the central argument or viewpoint that the writer aims to establish and defend throughout the essay. A claim must assert your position on an issue and must be arguable. It can guide the entire argument.
An argumentative essay is a structured, compelling piece of writing where an author clearly defines their stance on a specific topic. This is a very popular style of writing assigned to students at schools, colleges, and universities. Learn the steps to researching, structuring, and writing an effective argumentative essay below. Requirements ...
In an academic argument, you'll have a lot more constraints you have to consider, and you'll focus much more on logic and reasoning than emotions. Figure 1. When writing an argumentative essay, students must be able to separate emotion based arguments from logic based arguments in order to appeal to an academic audience.
What is argumentative essay? The fundamentals of a good argumentative essay. Let's explore the essential components that make argumentative essays compelling. 1. The foundation: crafting a compelling claim for your argumentative essay. The claim is the cornerstone of your argumentative essay. It represents your main argument or thesis statement ...
Argumentative Essay Example 2. Malaria is an infectious disease caused by parasites that are transmitted to people through female Anopheles mosquitoes. Each year, over half a billion people will become infected with malaria, with roughly 80% of them living in Sub-Saharan Africa.
Key Characteristics: Argumentative writing generally exhibits the following: Presents a particular position/side of an issue; Attempts to persuade the reader to the writer's side; Uses elements of rhetoric and strategies that include the integration of logos, pathos, ethos, and kairos in intentional and meaningful ways
An argumentative essay is a type of writing that presents the writer's position or stance on a specific topic and uses evidence to support that position. The goal of an argumentative essay is to convince your reader that your position is logical, ethical, and, ultimately, right. In argumentative essays, writers accomplish this by writing:
Argumentative essay formula & example. In the image below, you can see a recommended structure for argumentative essays. It starts with the topic sentence, which establishes the main idea of the essay. Next, this hypothesis is developed in the development stage. Then, the rebuttal, or the refutal of the main counter argument or arguments.
The argument you are making should be clearly stated within your thesis statement. You should have several reasons or points of discussion that help you to support your argument. You will explain and support these reasons and points of discussion within the body paragraphs of your paper. As with all academic writing, you'll need to cite any ...
The argumentative essay is a genre of essay writing whose purpose is to argue a position. The standard argumentative essay requires extensive research on a topic and is structured in three main ...
Figure 1. When writing an argumentative essay, students must be able to separate emotion based arguments from logic based arguments in order to appeal to an academic audience. Argumentative essays are quite common in academic writing and are often an important part of writing in all disciplines. You may be asked to take a stand on a social ...
An essay is a focused piece of writing designed to inform or persuade. There are many different types of essay, but they are often defined in four categories: argumentative, expository, narrative, and descriptive essays. Argumentative and expository essays are focused on conveying information and making clear points, while narrative and ...
When preparing to compose a good argumentative essay, utilize the following steps: Step 1: Select a topic. Step 2: Identify a position. Step 3: Locate appropriate resources. Step 4: Identify evidence supporting the position.(NOTE: If there is little evidence in support of the claim, consider re-examining the main argument.)Steps to write an argumentative essay
Here's our 12-step recipe for writing a great argumentative essay: Pick a topic. Choose your research sources. Read your sources and take notes. Create a thesis statement. Choose three main arguments to support your thesis statement —now you have a skeleton outline.
An essay is a brief work of writing which presents a story, point of view, interpretation, or analysis. The argumentative essay definition, then, is an essay that relies on facts and evidence to ...
An argumentative essay shares a literary language with other types of essay, and in that sense uses metaphors and other rhetorical figures to validate its thesis. It is a space where the subjectivity of the issuer fits, but also conceptual rigor. In general, an argumentative essay has the following characteristics:
Overall, tracking and analyzing the results of your argumentative essays is an essential step in the ongoing development of your writing skills. By being proactive in monitoring your progress, you can continuously learn and grow as a writer, ensuring that your essays are both persuasive and impactful. Hire a professional argumentative essay ...
Writing an argumentative essay can seem like a daunting task, but with the right structure and approach, it becomes much more manageable. An argumentative essay is all about presenting a well-reasoned argument supported by evidence, and it's essential to structure your essay effectively to convey your message convincingly.
Did you know that educational test are much less accurate than what most people think? All over the USA, students are responsible for taking standardized test through their years of learning.
Argumentative Essay On Pro Life; Argumentative Essay On Pro Life. 426 Words 2 Pages. I am Kasey Conway, a sophomore at Naperville North High School in Naperville, Illinois. I am Pro-Life, and I am writing this letter regarding the act of abortion, and how it needs to be prevented and limited within our country. Furthermore, providing more ...
Argumentative Essay: The Legalization Of Marijuana. 1421 Words 6 Pages. A lot of people are for the legalization of marijuana, whether they enjoy using the plant themselves, or believe that it isn't as harmful as it is made out to be. An advocate for marijuana, Bill Hicks, said, "Why is marijuana against the law? It grows naturally upon our ...
Argumentative Essay: The Courts Should Use The Death Penalty. 810 Words 4 Pages. Some believe that the courts should use the death penalty on those who are going to be in prison for life. However, I am against it. The government should not be able to choose when your life should be ended. I just think that it is cruel and inhumane to use the ...
The body of the essay is composed of the author's arguments, supporting evidence details, and refutations. An argumentative essay has a three-part structure: an introduction, a body, and a evidence conclusion. There are up to three paragraphs in the essay's body. The essay's conclusion, which is one paragraph long, provides an outline of the ...
We reject the argument that limiting the definition to RF-emitting devices may lead to marketplace confusion if a product does not bear the Cyber Trust Mark due solely to its lack of RF energy emissions. ... and the more recent NIST IoT Product Component Requirements Essay clearly states that the outcomes listed in NISTIR 8425 apply to consumer ...
Argumentative Essay On Gang Rape; Argumentative Essay On Gang Rape. 500 Words 2 Pages. Gang crime, in particular joint enterprise offences are commonly linked with young BAME males. Yet, research by the Centre for Crime and Justice Studies, reveals the 'gang' label is disproportionately attributed to BAME individuals. It is for this reason ...
This audio essay for "The Ezra Klein Show" was produced by Claire Gordon. Fact-checking by Michelle Harris, with Kate Sinclair, Mary Marge Locker and Kristin Lin. Our senior engineer is Jeff Geld.