Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
Methodology
- Systematic Review | Definition, Example, & Guide

Systematic Review | Definition, Example & Guide
Published on June 15, 2022 by Shaun Turney . Revised on November 20, 2023.
A systematic review is a type of review that uses repeatable methods to find, select, and synthesize all available evidence. It answers a clearly formulated research question and explicitly states the methods used to arrive at the answer.
They answered the question “What is the effectiveness of probiotics in reducing eczema symptoms and improving quality of life in patients with eczema?”
In this context, a probiotic is a health product that contains live microorganisms and is taken by mouth. Eczema is a common skin condition that causes red, itchy skin.
Table of contents
What is a systematic review, systematic review vs. meta-analysis, systematic review vs. literature review, systematic review vs. scoping review, when to conduct a systematic review, pros and cons of systematic reviews, step-by-step example of a systematic review, other interesting articles, frequently asked questions about systematic reviews.
A review is an overview of the research that’s already been completed on a topic.
What makes a systematic review different from other types of reviews is that the research methods are designed to reduce bias . The methods are repeatable, and the approach is formal and systematic:
- Formulate a research question
- Develop a protocol
- Search for all relevant studies
- Apply the selection criteria
- Extract the data
- Synthesize the data
- Write and publish a report
Although multiple sets of guidelines exist, the Cochrane Handbook for Systematic Reviews is among the most widely used. It provides detailed guidelines on how to complete each step of the systematic review process.
Systematic reviews are most commonly used in medical and public health research, but they can also be found in other disciplines.
Systematic reviews typically answer their research question by synthesizing all available evidence and evaluating the quality of the evidence. Synthesizing means bringing together different information to tell a single, cohesive story. The synthesis can be narrative ( qualitative ), quantitative , or both.
Here's why students love Scribbr's proofreading services
Discover proofreading & editing
Systematic reviews often quantitatively synthesize the evidence using a meta-analysis . A meta-analysis is a statistical analysis, not a type of review.
A meta-analysis is a technique to synthesize results from multiple studies. It’s a statistical analysis that combines the results of two or more studies, usually to estimate an effect size .
A literature review is a type of review that uses a less systematic and formal approach than a systematic review. Typically, an expert in a topic will qualitatively summarize and evaluate previous work, without using a formal, explicit method.
Although literature reviews are often less time-consuming and can be insightful or helpful, they have a higher risk of bias and are less transparent than systematic reviews.
Similar to a systematic review, a scoping review is a type of review that tries to minimize bias by using transparent and repeatable methods.
However, a scoping review isn’t a type of systematic review. The most important difference is the goal: rather than answering a specific question, a scoping review explores a topic. The researcher tries to identify the main concepts, theories, and evidence, as well as gaps in the current research.
Sometimes scoping reviews are an exploratory preparation step for a systematic review, and sometimes they are a standalone project.
Receive feedback on language, structure, and formatting
Professional editors proofread and edit your paper by focusing on:
- Academic style
- Vague sentences
- Style consistency
See an example
A systematic review is a good choice of review if you want to answer a question about the effectiveness of an intervention , such as a medical treatment.
To conduct a systematic review, you’ll need the following:
- A precise question , usually about the effectiveness of an intervention. The question needs to be about a topic that’s previously been studied by multiple researchers. If there’s no previous research, there’s nothing to review.
- If you’re doing a systematic review on your own (e.g., for a research paper or thesis ), you should take appropriate measures to ensure the validity and reliability of your research.
- Access to databases and journal archives. Often, your educational institution provides you with access.
- Time. A professional systematic review is a time-consuming process: it will take the lead author about six months of full-time work. If you’re a student, you should narrow the scope of your systematic review and stick to a tight schedule.
- Bibliographic, word-processing, spreadsheet, and statistical software . For example, you could use EndNote, Microsoft Word, Excel, and SPSS.
A systematic review has many pros .
- They minimize research bias by considering all available evidence and evaluating each study for bias.
- Their methods are transparent , so they can be scrutinized by others.
- They’re thorough : they summarize all available evidence.
- They can be replicated and updated by others.
Systematic reviews also have a few cons .
- They’re time-consuming .
- They’re narrow in scope : they only answer the precise research question.
The 7 steps for conducting a systematic review are explained with an example.
Step 1: Formulate a research question
Formulating the research question is probably the most important step of a systematic review. A clear research question will:
- Allow you to more effectively communicate your research to other researchers and practitioners
- Guide your decisions as you plan and conduct your systematic review
A good research question for a systematic review has four components, which you can remember with the acronym PICO :
- Population(s) or problem(s)
- Intervention(s)
- Comparison(s)
You can rearrange these four components to write your research question:
- What is the effectiveness of I versus C for O in P ?
Sometimes, you may want to include a fifth component, the type of study design . In this case, the acronym is PICOT .
- Type of study design(s)
- The population of patients with eczema
- The intervention of probiotics
- In comparison to no treatment, placebo , or non-probiotic treatment
- The outcome of changes in participant-, parent-, and doctor-rated symptoms of eczema and quality of life
- Randomized control trials, a type of study design
Their research question was:
- What is the effectiveness of probiotics versus no treatment, a placebo, or a non-probiotic treatment for reducing eczema symptoms and improving quality of life in patients with eczema?
Step 2: Develop a protocol
A protocol is a document that contains your research plan for the systematic review. This is an important step because having a plan allows you to work more efficiently and reduces bias.
Your protocol should include the following components:
- Background information : Provide the context of the research question, including why it’s important.
- Research objective (s) : Rephrase your research question as an objective.
- Selection criteria: State how you’ll decide which studies to include or exclude from your review.
- Search strategy: Discuss your plan for finding studies.
- Analysis: Explain what information you’ll collect from the studies and how you’ll synthesize the data.
If you’re a professional seeking to publish your review, it’s a good idea to bring together an advisory committee . This is a group of about six people who have experience in the topic you’re researching. They can help you make decisions about your protocol.
It’s highly recommended to register your protocol. Registering your protocol means submitting it to a database such as PROSPERO or ClinicalTrials.gov .
Step 3: Search for all relevant studies
Searching for relevant studies is the most time-consuming step of a systematic review.
To reduce bias, it’s important to search for relevant studies very thoroughly. Your strategy will depend on your field and your research question, but sources generally fall into these four categories:
- Databases: Search multiple databases of peer-reviewed literature, such as PubMed or Scopus . Think carefully about how to phrase your search terms and include multiple synonyms of each word. Use Boolean operators if relevant.
- Handsearching: In addition to searching the primary sources using databases, you’ll also need to search manually. One strategy is to scan relevant journals or conference proceedings. Another strategy is to scan the reference lists of relevant studies.
- Gray literature: Gray literature includes documents produced by governments, universities, and other institutions that aren’t published by traditional publishers. Graduate student theses are an important type of gray literature, which you can search using the Networked Digital Library of Theses and Dissertations (NDLTD) . In medicine, clinical trial registries are another important type of gray literature.
- Experts: Contact experts in the field to ask if they have unpublished studies that should be included in your review.
At this stage of your review, you won’t read the articles yet. Simply save any potentially relevant citations using bibliographic software, such as Scribbr’s APA or MLA Generator .
- Databases: EMBASE, PsycINFO, AMED, LILACS, and ISI Web of Science
- Handsearch: Conference proceedings and reference lists of articles
- Gray literature: The Cochrane Library, the metaRegister of Controlled Trials, and the Ongoing Skin Trials Register
- Experts: Authors of unpublished registered trials, pharmaceutical companies, and manufacturers of probiotics
Step 4: Apply the selection criteria
Applying the selection criteria is a three-person job. Two of you will independently read the studies and decide which to include in your review based on the selection criteria you established in your protocol . The third person’s job is to break any ties.
To increase inter-rater reliability , ensure that everyone thoroughly understands the selection criteria before you begin.
If you’re writing a systematic review as a student for an assignment, you might not have a team. In this case, you’ll have to apply the selection criteria on your own; you can mention this as a limitation in your paper’s discussion.
You should apply the selection criteria in two phases:
- Based on the titles and abstracts : Decide whether each article potentially meets the selection criteria based on the information provided in the abstracts.
- Based on the full texts: Download the articles that weren’t excluded during the first phase. If an article isn’t available online or through your library, you may need to contact the authors to ask for a copy. Read the articles and decide which articles meet the selection criteria.
It’s very important to keep a meticulous record of why you included or excluded each article. When the selection process is complete, you can summarize what you did using a PRISMA flow diagram .
Next, Boyle and colleagues found the full texts for each of the remaining studies. Boyle and Tang read through the articles to decide if any more studies needed to be excluded based on the selection criteria.
When Boyle and Tang disagreed about whether a study should be excluded, they discussed it with Varigos until the three researchers came to an agreement.
Step 5: Extract the data
Extracting the data means collecting information from the selected studies in a systematic way. There are two types of information you need to collect from each study:
- Information about the study’s methods and results . The exact information will depend on your research question, but it might include the year, study design , sample size, context, research findings , and conclusions. If any data are missing, you’ll need to contact the study’s authors.
- Your judgment of the quality of the evidence, including risk of bias .
You should collect this information using forms. You can find sample forms in The Registry of Methods and Tools for Evidence-Informed Decision Making and the Grading of Recommendations, Assessment, Development and Evaluations Working Group .
Extracting the data is also a three-person job. Two people should do this step independently, and the third person will resolve any disagreements.
They also collected data about possible sources of bias, such as how the study participants were randomized into the control and treatment groups.
Step 6: Synthesize the data
Synthesizing the data means bringing together the information you collected into a single, cohesive story. There are two main approaches to synthesizing the data:
- Narrative ( qualitative ): Summarize the information in words. You’ll need to discuss the studies and assess their overall quality.
- Quantitative : Use statistical methods to summarize and compare data from different studies. The most common quantitative approach is a meta-analysis , which allows you to combine results from multiple studies into a summary result.
Generally, you should use both approaches together whenever possible. If you don’t have enough data, or the data from different studies aren’t comparable, then you can take just a narrative approach. However, you should justify why a quantitative approach wasn’t possible.
Boyle and colleagues also divided the studies into subgroups, such as studies about babies, children, and adults, and analyzed the effect sizes within each group.
Step 7: Write and publish a report
The purpose of writing a systematic review article is to share the answer to your research question and explain how you arrived at this answer.
Your article should include the following sections:
- Abstract : A summary of the review
- Introduction : Including the rationale and objectives
- Methods : Including the selection criteria, search method, data extraction method, and synthesis method
- Results : Including results of the search and selection process, study characteristics, risk of bias in the studies, and synthesis results
- Discussion : Including interpretation of the results and limitations of the review
- Conclusion : The answer to your research question and implications for practice, policy, or research
To verify that your report includes everything it needs, you can use the PRISMA checklist .
Once your report is written, you can publish it in a systematic review database, such as the Cochrane Database of Systematic Reviews , and/or in a peer-reviewed journal.
In their report, Boyle and colleagues concluded that probiotics cannot be recommended for reducing eczema symptoms or improving quality of life in patients with eczema. Note Generative AI tools like ChatGPT can be useful at various stages of the writing and research process and can help you to write your systematic review. However, we strongly advise against trying to pass AI-generated text off as your own work.
If you want to know more about statistics , methodology , or research bias , make sure to check out some of our other articles with explanations and examples.
- Student’s t -distribution
- Normal distribution
- Null and Alternative Hypotheses
- Chi square tests
- Confidence interval
- Quartiles & Quantiles
- Cluster sampling
- Stratified sampling
- Data cleansing
- Reproducibility vs Replicability
- Peer review
- Prospective cohort study
Research bias
- Implicit bias
- Cognitive bias
- Placebo effect
- Hawthorne effect
- Hindsight bias
- Affect heuristic
- Social desirability bias
A literature review is a survey of scholarly sources (such as books, journal articles, and theses) related to a specific topic or research question .
It is often written as part of a thesis, dissertation , or research paper , in order to situate your work in relation to existing knowledge.
A literature review is a survey of credible sources on a topic, often used in dissertations , theses, and research papers . Literature reviews give an overview of knowledge on a subject, helping you identify relevant theories and methods, as well as gaps in existing research. Literature reviews are set up similarly to other academic texts , with an introduction , a main body, and a conclusion .
An annotated bibliography is a list of source references that has a short description (called an annotation ) for each of the sources. It is often assigned as part of the research process for a paper .
A systematic review is secondary research because it uses existing research. You don’t collect new data yourself.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
Turney, S. (2023, November 20). Systematic Review | Definition, Example & Guide. Scribbr. Retrieved June 24, 2024, from https://www.scribbr.com/methodology/systematic-review/
Is this article helpful?

Shaun Turney
Other students also liked, how to write a literature review | guide, examples, & templates, how to write a research proposal | examples & templates, what is critical thinking | definition & examples, "i thought ai proofreading was useless but..".
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, automatically generate references for free.
- Knowledge Base
- Methodology
- Systematic Review | Definition, Examples & Guide
Systematic Review | Definition, Examples & Guide
Published on 15 June 2022 by Shaun Turney . Revised on 17 October 2022.
A systematic review is a type of review that uses repeatable methods to find, select, and synthesise all available evidence. It answers a clearly formulated research question and explicitly states the methods used to arrive at the answer.
They answered the question ‘What is the effectiveness of probiotics in reducing eczema symptoms and improving quality of life in patients with eczema?’
In this context, a probiotic is a health product that contains live microorganisms and is taken by mouth. Eczema is a common skin condition that causes red, itchy skin.
Table of contents
What is a systematic review, systematic review vs meta-analysis, systematic review vs literature review, systematic review vs scoping review, when to conduct a systematic review, pros and cons of systematic reviews, step-by-step example of a systematic review, frequently asked questions about systematic reviews.
A review is an overview of the research that’s already been completed on a topic.
What makes a systematic review different from other types of reviews is that the research methods are designed to reduce research bias . The methods are repeatable , and the approach is formal and systematic:
- Formulate a research question
- Develop a protocol
- Search for all relevant studies
- Apply the selection criteria
- Extract the data
- Synthesise the data
- Write and publish a report
Although multiple sets of guidelines exist, the Cochrane Handbook for Systematic Reviews is among the most widely used. It provides detailed guidelines on how to complete each step of the systematic review process.
Systematic reviews are most commonly used in medical and public health research, but they can also be found in other disciplines.
Systematic reviews typically answer their research question by synthesising all available evidence and evaluating the quality of the evidence. Synthesising means bringing together different information to tell a single, cohesive story. The synthesis can be narrative ( qualitative ), quantitative , or both.
Prevent plagiarism, run a free check.
Systematic reviews often quantitatively synthesise the evidence using a meta-analysis . A meta-analysis is a statistical analysis, not a type of review.
A meta-analysis is a technique to synthesise results from multiple studies. It’s a statistical analysis that combines the results of two or more studies, usually to estimate an effect size .
A literature review is a type of review that uses a less systematic and formal approach than a systematic review. Typically, an expert in a topic will qualitatively summarise and evaluate previous work, without using a formal, explicit method.
Although literature reviews are often less time-consuming and can be insightful or helpful, they have a higher risk of bias and are less transparent than systematic reviews.
Similar to a systematic review, a scoping review is a type of review that tries to minimise bias by using transparent and repeatable methods.
However, a scoping review isn’t a type of systematic review. The most important difference is the goal: rather than answering a specific question, a scoping review explores a topic. The researcher tries to identify the main concepts, theories, and evidence, as well as gaps in the current research.
Sometimes scoping reviews are an exploratory preparation step for a systematic review, and sometimes they are a standalone project.
A systematic review is a good choice of review if you want to answer a question about the effectiveness of an intervention , such as a medical treatment.
To conduct a systematic review, you’ll need the following:
- A precise question , usually about the effectiveness of an intervention. The question needs to be about a topic that’s previously been studied by multiple researchers. If there’s no previous research, there’s nothing to review.
- If you’re doing a systematic review on your own (e.g., for a research paper or thesis), you should take appropriate measures to ensure the validity and reliability of your research.
- Access to databases and journal archives. Often, your educational institution provides you with access.
- Time. A professional systematic review is a time-consuming process: it will take the lead author about six months of full-time work. If you’re a student, you should narrow the scope of your systematic review and stick to a tight schedule.
- Bibliographic, word-processing, spreadsheet, and statistical software . For example, you could use EndNote, Microsoft Word, Excel, and SPSS.
A systematic review has many pros .
- They minimise research b ias by considering all available evidence and evaluating each study for bias.
- Their methods are transparent , so they can be scrutinised by others.
- They’re thorough : they summarise all available evidence.
- They can be replicated and updated by others.
Systematic reviews also have a few cons .
- They’re time-consuming .
- They’re narrow in scope : they only answer the precise research question.
The 7 steps for conducting a systematic review are explained with an example.
Step 1: Formulate a research question
Formulating the research question is probably the most important step of a systematic review. A clear research question will:
- Allow you to more effectively communicate your research to other researchers and practitioners
- Guide your decisions as you plan and conduct your systematic review
A good research question for a systematic review has four components, which you can remember with the acronym PICO :
- Population(s) or problem(s)
- Intervention(s)
- Comparison(s)
You can rearrange these four components to write your research question:
- What is the effectiveness of I versus C for O in P ?
Sometimes, you may want to include a fourth component, the type of study design . In this case, the acronym is PICOT .
- Type of study design(s)
- The population of patients with eczema
- The intervention of probiotics
- In comparison to no treatment, placebo , or non-probiotic treatment
- The outcome of changes in participant-, parent-, and doctor-rated symptoms of eczema and quality of life
- Randomised control trials, a type of study design
Their research question was:
- What is the effectiveness of probiotics versus no treatment, a placebo, or a non-probiotic treatment for reducing eczema symptoms and improving quality of life in patients with eczema?
Step 2: Develop a protocol
A protocol is a document that contains your research plan for the systematic review. This is an important step because having a plan allows you to work more efficiently and reduces bias.
Your protocol should include the following components:
- Background information : Provide the context of the research question, including why it’s important.
- Research objective(s) : Rephrase your research question as an objective.
- Selection criteria: State how you’ll decide which studies to include or exclude from your review.
- Search strategy: Discuss your plan for finding studies.
- Analysis: Explain what information you’ll collect from the studies and how you’ll synthesise the data.
If you’re a professional seeking to publish your review, it’s a good idea to bring together an advisory committee . This is a group of about six people who have experience in the topic you’re researching. They can help you make decisions about your protocol.
It’s highly recommended to register your protocol. Registering your protocol means submitting it to a database such as PROSPERO or ClinicalTrials.gov .
Step 3: Search for all relevant studies
Searching for relevant studies is the most time-consuming step of a systematic review.
To reduce bias, it’s important to search for relevant studies very thoroughly. Your strategy will depend on your field and your research question, but sources generally fall into these four categories:
- Databases: Search multiple databases of peer-reviewed literature, such as PubMed or Scopus . Think carefully about how to phrase your search terms and include multiple synonyms of each word. Use Boolean operators if relevant.
- Handsearching: In addition to searching the primary sources using databases, you’ll also need to search manually. One strategy is to scan relevant journals or conference proceedings. Another strategy is to scan the reference lists of relevant studies.
- Grey literature: Grey literature includes documents produced by governments, universities, and other institutions that aren’t published by traditional publishers. Graduate student theses are an important type of grey literature, which you can search using the Networked Digital Library of Theses and Dissertations (NDLTD) . In medicine, clinical trial registries are another important type of grey literature.
- Experts: Contact experts in the field to ask if they have unpublished studies that should be included in your review.
At this stage of your review, you won’t read the articles yet. Simply save any potentially relevant citations using bibliographic software, such as Scribbr’s APA or MLA Generator .
- Databases: EMBASE, PsycINFO, AMED, LILACS, and ISI Web of Science
- Handsearch: Conference proceedings and reference lists of articles
- Grey literature: The Cochrane Library, the metaRegister of Controlled Trials, and the Ongoing Skin Trials Register
- Experts: Authors of unpublished registered trials, pharmaceutical companies, and manufacturers of probiotics
Step 4: Apply the selection criteria
Applying the selection criteria is a three-person job. Two of you will independently read the studies and decide which to include in your review based on the selection criteria you established in your protocol . The third person’s job is to break any ties.
To increase inter-rater reliability , ensure that everyone thoroughly understands the selection criteria before you begin.
If you’re writing a systematic review as a student for an assignment, you might not have a team. In this case, you’ll have to apply the selection criteria on your own; you can mention this as a limitation in your paper’s discussion.
You should apply the selection criteria in two phases:
- Based on the titles and abstracts : Decide whether each article potentially meets the selection criteria based on the information provided in the abstracts.
- Based on the full texts: Download the articles that weren’t excluded during the first phase. If an article isn’t available online or through your library, you may need to contact the authors to ask for a copy. Read the articles and decide which articles meet the selection criteria.
It’s very important to keep a meticulous record of why you included or excluded each article. When the selection process is complete, you can summarise what you did using a PRISMA flow diagram .
Next, Boyle and colleagues found the full texts for each of the remaining studies. Boyle and Tang read through the articles to decide if any more studies needed to be excluded based on the selection criteria.
When Boyle and Tang disagreed about whether a study should be excluded, they discussed it with Varigos until the three researchers came to an agreement.
Step 5: Extract the data
Extracting the data means collecting information from the selected studies in a systematic way. There are two types of information you need to collect from each study:
- Information about the study’s methods and results . The exact information will depend on your research question, but it might include the year, study design , sample size, context, research findings , and conclusions. If any data are missing, you’ll need to contact the study’s authors.
- Your judgement of the quality of the evidence, including risk of bias .
You should collect this information using forms. You can find sample forms in The Registry of Methods and Tools for Evidence-Informed Decision Making and the Grading of Recommendations, Assessment, Development and Evaluations Working Group .
Extracting the data is also a three-person job. Two people should do this step independently, and the third person will resolve any disagreements.
They also collected data about possible sources of bias, such as how the study participants were randomised into the control and treatment groups.
Step 6: Synthesise the data
Synthesising the data means bringing together the information you collected into a single, cohesive story. There are two main approaches to synthesising the data:
- Narrative ( qualitative ): Summarise the information in words. You’ll need to discuss the studies and assess their overall quality.
- Quantitative : Use statistical methods to summarise and compare data from different studies. The most common quantitative approach is a meta-analysis , which allows you to combine results from multiple studies into a summary result.
Generally, you should use both approaches together whenever possible. If you don’t have enough data, or the data from different studies aren’t comparable, then you can take just a narrative approach. However, you should justify why a quantitative approach wasn’t possible.
Boyle and colleagues also divided the studies into subgroups, such as studies about babies, children, and adults, and analysed the effect sizes within each group.
Step 7: Write and publish a report
The purpose of writing a systematic review article is to share the answer to your research question and explain how you arrived at this answer.
Your article should include the following sections:
- Abstract : A summary of the review
- Introduction : Including the rationale and objectives
- Methods : Including the selection criteria, search method, data extraction method, and synthesis method
- Results : Including results of the search and selection process, study characteristics, risk of bias in the studies, and synthesis results
- Discussion : Including interpretation of the results and limitations of the review
- Conclusion : The answer to your research question and implications for practice, policy, or research
To verify that your report includes everything it needs, you can use the PRISMA checklist .
Once your report is written, you can publish it in a systematic review database, such as the Cochrane Database of Systematic Reviews , and/or in a peer-reviewed journal.
A systematic review is secondary research because it uses existing research. You don’t collect new data yourself.
A literature review is a survey of scholarly sources (such as books, journal articles, and theses) related to a specific topic or research question .
It is often written as part of a dissertation , thesis, research paper , or proposal .
There are several reasons to conduct a literature review at the beginning of a research project:
- To familiarise yourself with the current state of knowledge on your topic
- To ensure that you’re not just repeating what others have already done
- To identify gaps in knowledge and unresolved problems that your research can address
- To develop your theoretical framework and methodology
- To provide an overview of the key findings and debates on the topic
Writing the literature review shows your reader how your work relates to existing research and what new insights it will contribute.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the ‘Cite this Scribbr article’ button to automatically add the citation to our free Reference Generator.
Turney, S. (2022, October 17). Systematic Review | Definition, Examples & Guide. Scribbr. Retrieved 24 June 2024, from https://www.scribbr.co.uk/research-methods/systematic-reviews/
Is this article helpful?

Shaun Turney
Other students also liked, what is a literature review | guide, template, & examples, exploratory research | definition, guide, & examples, what is peer review | types & examples.
Study Design 101: Systematic Review
- Case Report
- Case Control Study
- Cohort Study
- Randomized Controlled Trial
- Practice Guideline
- Systematic Review
- Meta-Analysis
- Helpful Formulas
- Finding Specific Study Types
A document often written by a panel that provides a comprehensive review of all relevant studies on a particular clinical or health-related topic/question. The systematic review is created after reviewing and combining all the information from both published and unpublished studies (focusing on clinical trials of similar treatments) and then summarizing the findings.
- Exhaustive review of the current literature and other sources (unpublished studies, ongoing research)
- Less costly to review prior studies than to create a new study
- Less time required than conducting a new study
- Results can be generalized and extrapolated into the general population more broadly than individual studies
- More reliable and accurate than individual studies
- Considered an evidence-based resource
Disadvantages
- Very time-consuming
- May not be easy to combine studies
Design pitfalls to look out for
Studies included in systematic reviews may be of varying study designs, but should collectively be studying the same outcome.
Is each study included in the review studying the same variables?
Some reviews may group and analyze studies by variables such as age and gender; factors that were not allocated to participants.
Do the analyses in the systematic review fit the variables being studied in the original studies?
Fictitious Example
Does the regular wearing of ultraviolet-blocking sunscreen prevent melanoma? An exhaustive literature search was conducted, resulting in 54 studies on sunscreen and melanoma. Each study was then evaluated to determine whether the study focused specifically on ultraviolet-blocking sunscreen and melanoma prevention; 30 of the 54 studies were retained. The thirty studies were reviewed and showed a strong positive relationship between daily wearing of sunscreen and a reduced diagnosis of melanoma.
Real-life Examples
Yang, J., Chen, J., Yang, M., Yu, S., Ying, L., Liu, G., ... Liang, F. (2018). Acupuncture for hypertension. The Cochrane Database of Systematic Reviews, 11 (11), CD008821. https://doi.org/10.1002/14651858.CD008821.pub2
This systematic review analyzed twenty-two randomized controlled trials to determine whether acupuncture is a safe and effective way to lower blood pressure in adults with primary hypertension. Due to the low quality of evidence in these studies and lack of blinding, it is not possible to link any short-term decrease in blood pressure to the use of acupuncture. Additional research is needed to determine if there is an effect due to acupuncture that lasts at least seven days.
Parker, H.W. and Vadiveloo, M.K. (2019). Diet quality of vegetarian diets compared with nonvegetarian diets: a systematic review. Nutrition Reviews , https://doi.org/10.1093/nutrit/nuy067
This systematic review was interested in comparing the diet quality of vegetarian and non-vegetarian diets. Twelve studies were included. Vegetarians more closely met recommendations for total fruit, whole grains, seafood and plant protein, and sodium intake. In nine of the twelve studies, vegetarians had higher overall diet quality compared to non-vegetarians. These findings may explain better health outcomes in vegetarians, but additional research is needed to remove any possible confounding variables.
Related Terms
Cochrane Database of Systematic Reviews
A highly-regarded database of systematic reviews prepared by The Cochrane Collaboration , an international group of individuals and institutions who review and analyze the published literature.
Exclusion Criteria
The set of conditions that characterize some individuals which result in being excluded in the study (i.e. other health conditions, taking specific medications, etc.). Since systematic reviews seek to include all relevant studies, exclusion criteria are not generally utilized in this situation.
Inclusion Criteria
The set of conditions that studies must meet to be included in the review (or for individual studies - the set of conditions that participants must meet to be included in the study; often comprises age, gender, disease type and status, etc.).
Now test yourself!
1. Systematic Reviews are similar to Meta-Analyses, except they do not include a statistical analysis quantitatively combining all the studies.
a) True b) False
2. The panels writing Systematic Reviews may include which of the following publication types in their review?
a) Published studies b) Unpublished studies c) Cohort studies d) Randomized Controlled Trials e) All of the above
Evidence Pyramid - Navigation
- Meta- Analysis
- Case Reports
- << Previous: Practice Guideline
- Next: Meta-Analysis >>

- Last Updated: Sep 25, 2023 10:59 AM
- URL: https://guides.himmelfarb.gwu.edu/studydesign101

- Himmelfarb Intranet
- Privacy Notice
- Terms of Use
- GW is committed to digital accessibility. If you experience a barrier that affects your ability to access content on this page, let us know via the Accessibility Feedback Form .
- Himmelfarb Health Sciences Library
- 2300 Eye St., NW, Washington, DC 20037
- Phone: (202) 994-2850
- [email protected]
- https://himmelfarb.gwu.edu

- Duke NetID Login
- 919.660.1100
- Duke Health Badge: 24-hour access
- Accounts & Access
- Databases, Journals & Books
- Request & Reserve
- Training & Consulting
- Request Articles & Books
- Renew Online
- Reserve Spaces
- Reserve a Locker
- Study & Meeting Rooms
- Course Reserves
- Pay Fines/Fees
- Recommend a Purchase
- Access From Off Campus
- Building Access
- Computers & Equipment
- Wifi Access
- My Accounts
- Mobile Apps
- Known Access Issues
- Report an Access Issue
- All Databases
- Article Databases
- Basic Sciences
- Clinical Sciences
- Dissertations & Theses
- Drugs, Chemicals & Toxicology
- Grants & Funding
- Interprofessional Education
- Non-Medical Databases
- Search for E-Journals
- Search for Print & E-Journals
- Search for E-Books
- Search for Print & E-Books
- E-Book Collections
- Biostatistics
- Global Health
- MBS Program
- Medical Students
- MMCi Program
- Occupational Therapy
- Path Asst Program
- Physical Therapy
- Researchers
- Community Partners
Conducting Research
- Archival & Historical Research
- Black History at Duke Health
- Data Analytics & Viz Software
- Data: Find and Share
- Evidence-Based Practice
- NIH Public Access Policy Compliance
- Publication Metrics
- Qualitative Research
- Searching Animal Alternatives
Systematic Reviews
- Test Instruments
Using Databases
- JCR Impact Factors
- Web of Science
Finding & Accessing
- COVID-19: Core Clinical Resources
- Health Literacy
- Health Statistics & Data
- Library Orientation
Writing & Citing
- Creating Links
- Getting Published
- Reference Mgmt
- Scientific Writing
Meet a Librarian
- Request a Consultation
- Find Your Liaisons
- Register for a Class
- Request a Class
- Self-Paced Learning
Search Services
- Literature Search
- Systematic Review
- Animal Alternatives (IACUC)
- Research Impact
Citation Mgmt
- Other Software
Scholarly Communications
- About Scholarly Communications
- Publish Your Work
- Measure Your Research Impact
- Engage in Open Science
- Libraries and Publishers
- Directions & Maps
- Floor Plans
Library Updates
- Annual Snapshot
- Conference Presentations
- Contact Information
- Gifts & Donations
- What is a Systematic Review?
Types of Reviews
- Manuals and Reporting Guidelines
- Our Service
- 1. Assemble Your Team
- 2. Develop a Research Question
- 3. Write and Register a Protocol
- 4. Search the Evidence
- 5. Screen Results
- 6. Assess for Quality and Bias
- 7. Extract the Data
- 8. Write the Review
- Additional Resources
- Finding Full-Text Articles
Review Typologies
There are many types of evidence synthesis projects, including systematic reviews as well as others. The selection of review type is wholly dependent on the research question. Not all research questions are well-suited for systematic reviews.
- Review Typologies (from LITR-EX) This site explores different review methodologies such as, systematic, scoping, realist, narrative, state of the art, meta-ethnography, critical, and integrative reviews. The LITR-EX site has a health professions education focus, but the advice and information is widely applicable.
Review the table to peruse review types and associated methodologies. Librarians can also help your team determine which review type might be appropriate for your project.
Reproduced from Grant, M. J. and Booth, A. (2009), A typology of reviews: an analysis of 14 review types and associated methodologies. Health Information & Libraries Journal, 26: 91-108. doi:10.1111/j.1471-1842.2009.00848.x
|
|
|
|
|
|
|
|
| Aims to demonstrate writer has extensively researched literature and critically evaluated its quality. Goes beyond mere description to include degree of analysis and conceptual innovation. Typically results in hypothesis or mode | Seeks to identify most significant items in the field | No formal quality assessment. Attempts to evaluate according to contribution | Typically narrative, perhaps conceptual or chronological | Significant component: seeks to identify conceptual contribution to embody existing or derive new theory |
|
| Generic term: published materials that provide examination of recent or current literature. Can cover wide range of subjects at various levels of completeness and comprehensiveness. May include research findings | May or may not include comprehensive searching | May or may not include quality assessment | Typically narrative | Analysis may be chronological, conceptual, thematic, etc. |
|
| Map out and categorize existing literature from which to commission further reviews and/or primary research by identifying gaps in research literature | Completeness of searching determined by time/scope constraints | No formal quality assessment | May be graphical and tabular | Characterizes quantity and quality of literature, perhaps by study design and other key features. May identify need for primary or secondary research |
|
| Technique that statistically combines the results of quantitative studies to provide a more precise effect of the results | Aims for exhaustive, comprehensive searching. May use funnel plot to assess completeness | Quality assessment may determine inclusion/ exclusion and/or sensitivity analyses | Graphical and tabular with narrative commentary | Numerical analysis of measures of effect assuming absence of heterogeneity |
|
| Refers to any combination of methods where one significant component is a literature review (usually systematic). Within a review context it refers to a combination of review approaches for example combining quantitative with qualitative research or outcome with process studies | Requires either very sensitive search to retrieve all studies or separately conceived quantitative and qualitative strategies | Requires either a generic appraisal instrument or separate appraisal processes with corresponding checklists | Typically both components will be presented as narrative and in tables. May also employ graphical means of integrating quantitative and qualitative studies | Analysis may characterise both literatures and look for correlations between characteristics or use gap analysis to identify aspects absent in one literature but missing in the other |
|
| Generic term: summary of the [medical] literature that attempts to survey the literature and describe its characteristics | May or may not include comprehensive searching (depends whether systematic overview or not) | May or may not include quality assessment (depends whether systematic overview or not) | Synthesis depends on whether systematic or not. Typically narrative but may include tabular features | Analysis may be chronological, conceptual, thematic, etc. |
|
| Method for integrating or comparing the findings from qualitative studies. It looks for ‘themes’ or ‘constructs’ that lie in or across individual qualitative studies | May employ selective or purposive sampling | Quality assessment typically used to mediate messages not for inclusion/exclusion | Qualitative, narrative synthesis | Thematic analysis, may include conceptual models |
|
| Assessment of what is already known about a policy or practice issue, by using systematic review methods to search and critically appraise existing research | Completeness of searching determined by time constraints | Time-limited formal quality assessment | Typically narrative and tabular | Quantities of literature and overall quality/direction of effect of literature |
|
| Preliminary assessment of potential size and scope of available research literature. Aims to identify nature and extent of research evidence (usually including ongoing research) | Completeness of searching determined by time/scope constraints. May include research in progress | No formal quality assessment | Typically tabular with some narrative commentary | Characterizes quantity and quality of literature, perhaps by study design and other key features. Attempts to specify a viable review |
|
| Tend to address more current matters in contrast to other combined retrospective and current approaches. May offer new perspectives | Aims for comprehensive searching of current literature | No formal quality assessment | Typically narrative, may have tabular accompaniment | Current state of knowledge and priorities for future investigation and research |
|
| Seeks to systematically search for, appraise and synthesis research evidence, often adhering to guidelines on the conduct of a review | Aims for exhaustive, comprehensive searching | Quality assessment may determine inclusion/exclusion | Typically narrative with tabular accompaniment | What is known; recommendations for practice. What remains unknown; uncertainty around findings, recommendations for future research |
|
| Combines strengths of critical review with a comprehensive search process. Typically addresses broad questions to produce ‘best evidence synthesis’ | Aims for exhaustive, comprehensive searching | May or may not include quality assessment | Minimal narrative, tabular summary of studies | What is known; recommendations for practice. Limitations |
|
| Attempt to include elements of systematic review process while stopping short of systematic review. Typically conducted as postgraduate student assignment | May or may not include comprehensive searching | May or may not include quality assessment | Typically narrative with tabular accompaniment | What is known; uncertainty around findings; limitations of methodology |
|
| Specifically refers to review compiling evidence from multiple reviews into one accessible and usable document. Focuses on broad condition or problem for which there are competing interventions and highlights reviews that address these interventions and their results | Identification of component reviews, but no search for primary studies | Quality assessment of studies within component reviews and/or of reviews themselves | Graphical and tabular with narrative commentary | What is known; recommendations for practice. What remains unknown; recommendations for future research |
- << Previous: What is a Systematic Review?
- Next: Manuals and Reporting Guidelines >>
- Last Updated: Jun 18, 2024 9:41 AM
- URL: https://guides.mclibrary.duke.edu/sysreview
- Duke Health
- Duke University
- Duke Libraries
- Medical Center Archives
- Duke Directory
- Seeley G. Mudd Building
- 10 Searle Drive
- [email protected]
- SPECIAL COLLECTIONS
- COVID-19 Library Updates
- Make Appointment
Systematic Reviews (A How-To Guide): What is a Systematic Review?
What is a systematic review.
- Library Role
- Planning & Practicalities
- Protocol & Searching
- Results Management & Evaluation
- Publishing & Dissemination
- Further Reading & Guidance
Scope & Definitions
A systematic review is a particular type of evidence synthesis whose methodology seeks to maximize objectivity and transparency while minimizing bias in the identification, evaluation and use of information used to support an answer to a research question. Here below are some ways different authors have described the systematic review approach:
" A systematic review attempts to identify, appraise and synthesize all the empirical evidence that meets pre-specified eligibility criteria to answer a specific research question. Researchers conducting systematic reviews use explicit, systematic methods that are selected with a view aimed at minimizing bias, to produce more reliable findings to inform decision making " (Cochrane Library website: About Cochrane Reviews , 2022)
“ a review of existing research using explicitly, accountable rigorous research methods ” (Gough, Oliver & Thomas, 2017)
“ a set of transparent, orderly, structurally interrelated steps, carried out in a way that avoids bias and allows for peer review and independent verification. The SR addresses a clearly defined question. It uses a systematic, that is, logical, and explicit methodology to identify, select, and critically appraise relevant studies ” (Holly, Salmond & Saimbert, 2022)
“ a particular form of secondary study and aims to provide an objective and unbiased approach to finding relevant primary studies, and for extracting, aggregating and synthesizing the data from these .” (Kitchenham, Budgen & Brereton, 2016)
Methodologies (Variations & Options)
The details of systematic review methodology may vary across different fields of study, including, but not limited to: medicine, nursing, psychology, education, the social sciences, and increasingly in the fields of engineering and software development.
Other determining factors for the systematic review methodology include: the nature of the information sources being used; the type of information collected; the specificity of the research question; the breadth or narrowness of the inclusion criteria, exclusion criteria and search strategy; and the particular research goals of the investigators (for additional guidance, refer to the " Further Reading & Guidance " section of this guide).
One of the most important variations on systematic review methodology is the ' meta-analysis '--a type of evidence synthesis that includes statistical analysis of information collected from multiple independent studies (e.g. from different clinical trials).
Systematic reviews may be published and disseminated in the form of journal articles, book chapters, graduate theses and dissertations, technical reports, conference proceedings, and other document types.
Defining Characteristics
The main attributes that systematic reviews have in common include:
- The goal of answering a clearly stated, predefined and focused research question
- The use of explicit predetermined criteria for determining the eligibility of information sources
- A systematized methodology and protocol that seek to maximize objectivity and minimize bias in the identification, selection and use of relevant information sources
- Exhaustive (comprehensive and thorough) searches that attempt to find all available information that could help support an answer to the predefined research question
- Rigorous evaluation of search results according to predefined quality criteria
- Reproducibility through transparency in reporting of all methods, results, and evaluation processes
- An overall time commitment of between six months to a year or more
- A project team of three or more people with appropriate subject expertise
If your goals or resources are not consistent with those listed above, a different review methodology may be a better fit for your project. Other evidence synthesis methodologies to consider may include: rapid review, scoping review, narrative literature review, or a methodology that incorporates elements of a systematic review approach but a lesser degree of rigor or exhaustiveness (see the " Planning & Logistics " section of this guide).
Explore Your Options with a Librarian
If in any doubt about the appropriateness of a systematic review methodology--or any other type of knowledge synthesis--for meeting your research goals, feel encouraged to discuss options with a librarian (bring along any collaborators and/or instructors in your project team).
Choosing the Right Type of Review
Before embarking on your project, here below is a decision-support tool offering guidance as to the appropriateness of the systematic review methodology for fulfilling your particular research goals:
What kind of review is right for you?
(Cornell University Library)
- Next: Library Role >>
- Last Updated: May 15, 2024 1:43 PM
- URL: https://libguides.depaul.edu/c.php?g=1258458
- Open access
- Published: 09 June 2012
Clarifying differences between review designs and methods
- David Gough 1 ,
- James Thomas 1 &
- Sandy Oliver 1
Systematic Reviews volume 1 , Article number: 28 ( 2012 ) Cite this article
103k Accesses
394 Citations
74 Altmetric
Metrics details
This paper argues that the current proliferation of types of systematic reviews creates challenges for the terminology for describing such reviews. Terminology is necessary for planning, describing, appraising, and using reviews, building infrastructure to enable the conduct and use of reviews, and for further developing review methodology. There is insufficient consensus on terminology for a typology of reviews to be produced and any such attempt is likely to be limited by the overlapping nature of the dimensions along which reviews vary. It is therefore proposed that the most useful strategy for the field is to develop terminology for the main dimensions of variation. Three such main dimensions are proposed: (1) aims and approaches (including what the review is aiming to achieve, the theoretical and ideological assumptions, and the use of theory and logics of aggregation and configuration in synthesis); (2) structure and components (including the number and type of mapping and synthesis components and how they relate); and (3) breadth and depth and the extent of ‘work done’ in addressing a research issue (including the breadth of review questions, the detail with which they are addressed, and the amount the review progresses a research agenda). This then provides an overarching strategy to encompass more detailed descriptions of methodology and may lead in time to a more overarching system of terminology for systematic reviews.
Peer Review reports
Research studies vary in many ways including the types of research questions they are asking, the reasons these questions are being asked, the theoretical and ideological perspectives underlying these questions, and in the research methods that they employ. Systematic reviews are a form of research; they are (and the theoretical and ideological perspectives underlying these methods) a way of bringing together what is known from the research literature using explicit and accountable methods [ 1 ]. Systematic methods of review have been successfully developed particularly for questions concerning the impact of interventions; these synthesize the findings of studies which use experimental controlled designs. Yet the logic of systematic methods for reviewing the literature can be applied to all areas of research; therefore there can be as much variation in systematic reviews as is found in primary research [ 2 , 3 ]. This paper discusses some of the important conceptual and practical differences between different types of systematic review. It does not aim to provide an overall taxonomy of all types of reviews; the rate of development of new approaches to reviewing is too fast and the overlap of approaches too great for that to be helpful. Instead, the paper argues that, for the present at least, it is more useful to identify the key dimensions on which reviews differ and to examine the multitude of different combinations of those dimensions. The paper also does not aim to describe all of the myriad actual and potential differences between reviews; this would be a task too large even for a book let alone a paper. The focus instead is on three major types of dimensions of difference. The first dimension is the aims and approaches of reviews; particularly in terms of their methodologies (their ontological and epistemological foundations and methods of synthesis). The second dimension is the structure and components of reviews. The third dimension is the breadth, depth, and extent of the work done by a review in engaging with a research issue. Once these three aspects of a review are clear, consideration can be given to more specific methodological issues such as methods of searching, identifying, coding, appraising, and synthesizing evidence. The aim of this paper is to clarify some of the major conceptual distinctions between reviews to assist the selection, evaluation, and development of methods for reviewing.
Clarifying the nature of variation in reviews
As forms of research, systematic reviews are undertaken according to explicit methods. The term ‘systematic’ distinguishes them from reviews undertaken without clear and accountable methods.
The history of systematic reviews is relatively recent [ 4 , 5 ] and despite early work on meta-ethnography [ 6 ], the field has been dominated by the development and application of statistical meta-analysis of controlled trials to synthesize the evidence on the effectiveness of health and social interventions. Over the past 10 years, other methods for reviewing have been developed. Some of these methods aim to extend effectiveness reviews with information from qualitative studies [ 7 ]. The qualitative information may be used to inform decisions made in the statistical synthesis or be part of a mixed methods synthesis (discussed later). Other approaches have been developed from a perspective which, instead of the statistical aggregation of data from controlled trials, emphasize the central role that theory can play in synthesizing existing research [ 8 , 9 ], address the complexity of interventions [ 10 ], and the importance of understanding research within its social and paradigmatic context [ 11 ]. The growth in methods has not been accompanied by a clear typology of reviews. The result is a complex web of terminology [ 2 , 12 ].
The lack of clarity about the range of methods of review has consequences which can limit their development and subsequent use. Knowledge or consensus about the details of specific methods may be lacking, creating the danger of the over-generalization or inappropriate application of the terminology being used. Also, the branding of different types of review can lead to over-generalizations and simplification with assumptions being made about differences between reviews that only apply to particular stages of a review or that are matters of degree rather than absolute differences. For example, concepts of quality assurance can differ depending upon the nature of the research question being asked. Similarly, infrastructure systems developed to enable the better reporting and critical appraisal of reviews, such as PRISMA [ 13 ], and for registration of reviews, such as PROSPERO [ 14 ] currently apply predominantly to a subset of reviews, the defining criteria of which may not be fully clear.
A further problem is that systematic reviews have attracted criticism on the assumption that systematic reviewing is applicable only to empirical quantitative research [ 15 ]. In this way, polarized debates about the utility and relevance of different research paradigms may further complicate terminological issues and conceptual understandings about how reviews actually differ from one another. All of these difficulties are heightened because review methods are undergoing a period of rapid development and so the methods being described are often being updated and refined.
Knowledge about the nature and strengths of different forms of review is necessary for: appropriate choice of review methods by those undertaking reviews; consideration of the importance of different issues of quality and relevance for each stage of a review; appropriate and accurate reporting and accountability of such review methods; interpretation of reviews; commissioning of reviews; development of procedures for assessing and undertaking reviews; and development of new methods.
Clarifying the nature of the similarities and differences between reviews is a first step to avoiding these potential limitations. A typology of review methods might be a solution. There are many diverse approaches to reviews that can be easily distinguished, such as statistical meta-analysis and meta-ethnography. A more detailed examination, however, reveals that the types of review currently described often have commonalities that vary across types of review and at different stages of a review. Three of these dimensions are described here. Exploring these dimensions also reveals how reviews differ in degree along these overlapping dimensions rather than falling into clear categories.
Review aims and approaches
Primary research and research reviews vary in their ontological, epistemological, ideological, and theoretical stance, their research paradigm, and the issues that they aim to address. In reviews, this variation occurs in both the method of review and the type of primary research that they consider. As reviews will include primary studies that address the focus of the review question, it is not surprising that review methods also tend to reflect many of the approaches, assumptions, and methodological challenges of the primary research that they include.
One indication of the aim and approach of a study is the research question which the study aims to answer. Questions commonly addressed by systematic reviews include: what is the effect of this intervention (addressed by, for example, the statistical meta-analysis of experimental trials); what is the accuracy of this diagnostic tool (addressed by, for example, meta-analysis of evaluations of diagnostic tests); what is the cost of this intervention (addressed by, for example, a synthesis of cost-benefit analyses); what is the meaning or process of a phenomena (addressed by, for example, conceptual synthesis such as meta-ethnography or a critical interpretative synthesis of ethnographic studies); what is the effect of this complex intervention (addressed by, for example, multi-component mixed methods reviews); what is the effect of this approach to social policy in this context (addressed by, for example, realist synthesis of evidence of efficacy and relevance across different policy areas); and what are the attributes of this intervention or activity (addressed by, for example, framework synthesis framed by dimensions explicitly linked to particular perspectives).
Although different questions drive the review process and suggest different methods for reviewing (and methods of studies included) there is considerable overlap in the review methods that people may select to answer these questions; thus the review question alone does not provide a complete basis for generating a typology of review methods.
Role of theory
There is no agreed typology of research questions in the health and social sciences. In the absence of such a typology, one way to distinguish research is in the extent that it is concerned with generating, exploring, or testing theory [ 16 ].
In addressing an impact question using statistical meta-analysis, the approach is predominantly the empirical testing of a theory that the intervention works. The theory being tested may be based on a detailed theory of change (logic model) or be a ‘black box’ where the mechanisms by which change may be affected are not articulated. The review may, in addition to testing theory, include methods to generate hypotheses about causal relations. Testing often (though not always) wants to add up or aggregate data from large representative samples to obtain a more precise estimate of effect. In the context of such reviews, searching aims to identify a representative sample of studies, usually by attempting to include all relevant studies in order to avoid bias from study selection (sometimes called ‘exhaustive’ searching). Theoretical work in such analyses is undertaken predominantly before and after the review, not during the review, and is concerned with developing the hypothesis and interpreting the findings.
In research examining processes or meanings the approach is predominantly about developing or exploring theory. This may not require representative samples of studies (as in aggregative reviews) but does require variation to enable new conceptual understandings to be generated. Searching for studies in these reviews adopts a theoretical approach to searching to identify a sufficient and appropriate range of studies either through a rolling sampling of studies according to a framework that is developed inductively from the emerging literature (akin to theoretical sampling in primary research) [ 17 ]; or through a sampling framework based on an existing body of literature (akin to purposive sampling in primary research) [ 18 ]. In both primary research and reviews, theoretical work is undertaken during the process of the research; and, just as with the theory testing reviews, the nature of the concepts may be relatively simple or very complex.
Aggregative and configurative reviews
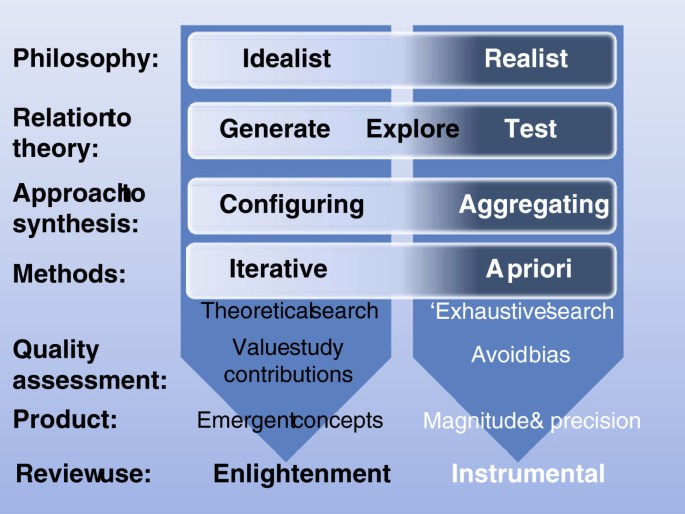
The distinction between research that tests and research that generates theory also equates to the distinction between review types made by Voils, Sandelowski and colleagues [ 19 , 20 ] (although we have been very influenced by these authors the detail of our use of these terms may differ in places). Reviews that are collecting empirical data to describe and test predefined concepts can be thought of as using an ‘aggregative’ logic. The primary research and reviews are adding up (aggregating) and averaging empirical observations to make empirical statements (within predefined conceptual positions). In contrast, reviews that are trying to interpret and understand the world are interpreting and arranging (configuring) information and are developing concepts (Figure 1 ). This heuristic also maps onto the way that the review is intended to inform knowledge. Aggregative research tends to be about seeking evidence to inform decisions whilst configuring research is seeking concepts to provide enlightenment through new ways of understanding.
Continua of approaches in aggregative and configurative reviews.
Aggregative reviews are often concerned with using predefined concepts and then testing these using predefined ( a priori ) methods. Configuring reviews can be more exploratory and, although the basic methodology is determined (or at least assumed) in advance, specific methods are sometimes adapted and selected (iteratively) as the research proceeds. Aggregative reviews are likely to be combining similar forms of data and so be interested in the homogeneity of studies. Configurative reviews are more likely to be interested in identifying patterns provided by heterogeneity [ 12 ].
The logic of aggregation relies on identifying studies that support one another and so give the reviewer greater certainty about the magnitude and variance of the phenomenon under investigation. As already discussed in the previous section, the approach to searching for studies to include (the search strategy) is attempting to be exhaustive or, if not exhaustive, then at least avoiding bias in the way that studies are found. Configuring reviews have the different purpose of aiming to find sufficient cases to explore patterns and so are not necessarily attempting to be exhaustive in their searching. (Most reviews contain elements of both aggregation and configuration and so some may require an unbiased set of studies as well as sufficient heterogeneity to permit the exploration of differences between them).
Aggregating and configuring reviews also vary in their approach to quality assurance. All reviews aim to avoid drawing misleading conclusions because of problems in the studies they contain. Aggregative reviews are concerned with a priori methods and their quality assurance processes assess compliance with those methods. As the basis of quality assurance is known a priori , many aspects of this can be incorporated into the inclusion criteria of the review and then can be further checked at a later quality assurance stage. The inclusion criteria may, for example, require only certain types of study with specific methodological features. There is less consensus in the practice of quality assessment in configurative reviews; some adopt a similar strategy to those employed in aggregative reviews, whereas others reject the idea that the quality of a study can be assessed through an examination of its method, and instead prioritize other issues, such as relevance to the review and the contribution the study can make in the review synthesis to testing or generating theory [ 21 – 23 ]. Some of the differences between aggregating and configuring reviews are shown in Figure 1 .
Although the logics of aggregating and configuring research findings demand different methods for reviewing, a review often includes components of both. A meta-analysis may contain a post hoc interpretation of statistical associations which may be configured to generate hypotheses for future testing. A configurative synthesis may include some components where data are aggregated (for example, framework synthesis) [ 24 , 25 ]. Examples of reviews that are predominantly aggregative, configurative, or with high degrees of both aggregation and configuring are given in Table 1 (and for a slightly different take on this heuristic see Sandelowski et al. [ 20 ]).
Similarly, the nature of a review question, the assumptions underlying the question (or conceptual framework), and whether the review aggregates or configures the results of other studies may strongly suggest which methods of review are appropriate, but this is not always the case. Several methods of review are applicable to a wide range of review approaches. Both thematic [ 26 ] and framework synthesis [ 24 , 25 ] which identify themes within narrative data can, for example, be used with both aggregative and configurative approaches to synthesis.
Reviews that are predominantly aggregative may have similar epistemological and methodological assumptions to much quantitative research and there may be similar assumptions between predominantly configurative reviews and qualitative research. However, the quantitative/qualitative distinction is not precise and does not reflect the differences in the aggregative and configurative research processes; quantitative reviews may use configurative processes and qualitative reviews can use aggregative processes. Some authors also use the terms conceptual synthesis for reviews that are predominantly configurative, but the process of configuring in a review does not have to be limited to concepts; it can also be the arrangement of numbers (as in subgroup analyses of statistical meta-analysis). The term ‘interpretative synthesis’ is also used to describe reviews where meanings are interpreted from the included studies. However, aggregative reviews also include interpretation, before inspection of the studies to develop criteria for including studies, and after synthesis of the findings to develop implications for policy, practice, and further research. Thus, the aggregate/configure framework cannot be thought of as another way of expressing the qualitative/quantitative ‘divide’; it has a more specific meaning concerning the logic of synthesis, and many reviews have elements of both aggregation and configuration.
Further ideological and theoretical assumptions
In addition to the above is a range of issues about whose questions are being asked and the implicit ideological and theoretical assumptions driving both them and the review itself. These assumptions determine the specific choices made in operationalizing the review question and thus determine the manner in which the review is undertaken, including the research studies included and how they are analyzed. Ensuring that these assumptions are transparent is therefore important both for the execution of the review and for accountability. Reviews may be undertaken to inform decision-making by non-academic users of research such as policymakers, practitioners, and other members of the public and so there may be a wide range of different perspectives that can inform a review [ 27 , 28 ]. The perspectives driving the review will also influence the findings of the review and thereby clarify what is known and not known (within those perspectives) and thus inform what further primary research is required. Both reviewer and user perspectives can thus have an ongoing influence in developing user-led research agendas. There may be many different agendas and thus a plurality of both primary research and reviews of research on any given issue.
A further fundamental issue that is related to the types of questions being asked and the ideological and theoretical assumptions underlying them is the ontological and epistemological position taken by the reviewers. Aggregative reviews tend to assume that there is (often within disciplinary specifications/boundaries) a reality about which empirical statements can be made even if this reality is socially constructed (generalizations); in other words they take a ‘realist’ philosophical position (a broader concept than the specific method of ‘realist synthesis’). Some configurative reviews may not require such realist assumptions. They take a more relativist idealist position; the interest is not in seeking a single ‘correct’ answer but in examining the variation and complexity of different conceptualizations [ 12 , 29 ]. These philosophical differences can be important in understanding the approach taken by different reviewers just as they are in understanding variation in approach (and debates about research methods) in primary research. These differences also relate to how reviews are used. Aggregative reviews are often used to make empirical statements (within agreed conceptual perspectives) to inform decision making instrumentally whilst configuring reviews are often used to develop concepts and enlightenment [ 30 ].
Structure and components of reviews
As well as varying in their questions, aims, and philosophical approach, reviews also vary in their structure. They can be single reviews that synthesize a specific literature to answer the review question. They may be maps of what research has been undertaken that are products in their own right and also a stage on the way to one or more syntheses. Reviews can also contain multiple components equating to conducting many reviews or to reviewing many reviews.
Systematic maps
To some degree, most reviews describe the studies they contain and thus provide a map or account of the research field. Some reviews go further than this and more explicitly identify aspects of the studies that help describe the research field in some detail; the focus and extent of such description varying with the aims of the map. Maps are useful products in their own right but can also be used to inform the process of synthesis and the interpretation of the synthesis [ 3 , 30 ]. Instead of automatically undertaking a synthesis of all included studies, an analysis of the map may lead to a decision to synthesize only a subset of studies, or to conduct several syntheses in different areas of the one map. A broader initial review question and a narrower subsequent review question allows the synthesis of a narrower subset of studies to be understood within the wider literature described in terms of research topics, primary research methods, or both. It also allows broader review questions to create a map for a series of reviews (Figure 2 ) or mixed methods reviews (Figure 3 ). In sum, maps have three main purposes of: (i) describing the nature of a research field; (ii) to inform the conduct of a synthesis; and (iii) to interpret the findings of a synthesis [ 3 , 31 ].The term ‘scoping review’ is also sometimes used in a number of different ways to describe (often non-systematic) maps and/or syntheses that rapidly examine the nature of the literature on a topic area [ 32 , 33 ]; sometimes as part of the planning for a systematic review.
A map leading to several syntheses.
A mixed method review with three syntheses.
- Mixed methods reviews
The inclusion criteria of a review may allow all types of primary research or only studies with specific methods that are considered most appropriate to best address the review question. Including several different methods of primary research in a review can create challenges in the synthesis stage. For example, a review asking about the impact of some life experience may examine both randomized controlled trials and large data sets on naturally occurring phenomena (such as in large scale cohort studies). Another strategy is to have sub-reviews that ask questions about different aspects of an issue and which are likely to consider different primary research [ 34 , 35 ]. For example, a statistical meta-analysis of impact studies compared with a conceptual synthesis of people’s views of the issue being evaluated [ 34 , 35 ]. The two sub-reviews can then be combined and contrasted in a third synthesis as in Figure 3 . Mixed methods reviews have many similarities with mixed methods in primary research and there are therefore numerous ways in which the products of different synthesis methods may be combined [ 35 ].
Mixed knowledge reviews use a similar approach but combine data from previous research with other forms of data; for example a survey of practice knowledge about an issue (Figure 4 ).
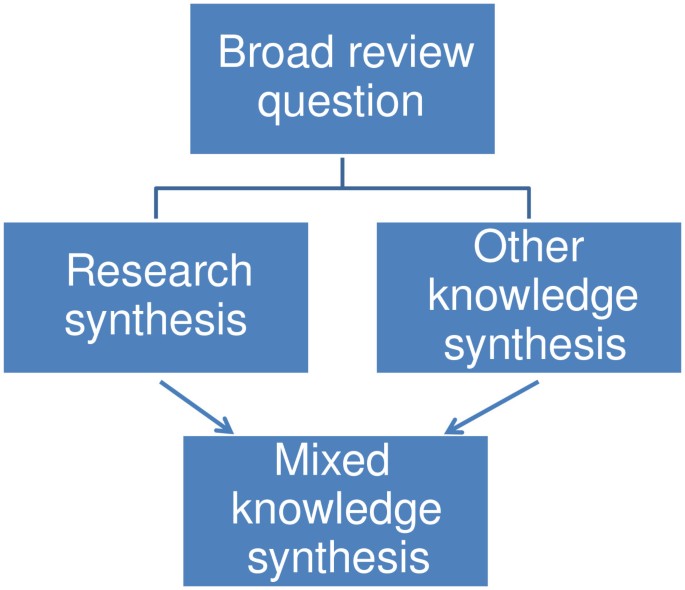
Mixed knowledge review.
Another example of a mixed methods review is realist synthesis [ 9 ] that examines the usefulness of mid-level policy interventions across different areas of social policy by unpacking the implicit models of change, followed by an iterative process of identifying and analyzing the evidence in support of each part of that model. This is quite similar to a theory-driven aggregative review (or series of reviews) that aggregatively test different parts of a causal model. The first part of the process is a form of configuration in clarifying the nature of the theory and what needs to be empirically tested; the second part is the aggregative testing of those subcomponents of the theory. The difference between this method and more ‘standard’ systematic review methods is that the search for empirical evidence is more of an iterative, investigative process of tracking down and interpreting evidence. Realist synthesis will also consider a broad range of empirical evidence and will assess its value in terms of its contribution rather than according to some preset criteria. The approach therefore differs from the predominantly a priori strategy used in either standard ‘black box’ or in theory driven aggregative reviews. There have also been attempts to combine aggregative ‘what works’ reviews with realist reviews [ 36 ]. These innovations are exploring how best to develop the breadth, generalizability and policy relevance of aggregative reviews without losing their methodological protection against bias.
There are also reviews that use other pre-existing reviews as their source of data. These reviews of reviews may draw on the data of previous reviews either by using the findings of previous reviews or by drilling down to using data from the primary studies in the reviews [ 37 ]. Information drawn from many reviews can also be mined to understand more about a research field or research methods in meta-epidemiology [ 38 ]. As reviews of reviews and meta-epidemiology both use reviews as their data, they are sometimes both described as types of ‘meta reviews’. This terminology may not be helpful as it links together two approaches to reviews which have little in common apart from the shared type of data source. A further term is ‘meta evaluation’. This can refer to the formative or summative evaluation of primary evaluation studies or can be a summative statement of the findings of evaluations which is a form of aggregative review (See Gough et al. in preparation, and [ 39 ]).
Breadth, depth, and ’work done’ by reviews
Primary research studies and reviews may be read as isolated products yet they are usually one step in larger or longer-term research enterprises. A research study usually addresses a macro research issue and a specific focused sub-issue that is addressed by its specific data and analysis [ 16 ]. This specific focus can be broad or narrow in scope and deep or not so deep in the detail in which it is examined.
Breadth of question
Many single component aggregative reviews aim for homogeneity in the focus and method of included studies. They select narrowly defined review questions to ensure a narrow methodological focus of research findings. Although well justified, these decisions may lead to each review providing a very narrow view of both research and the issue that is being addressed. A user of such reviews may need to take account of multiple narrow reviews in order to help them determine the most appropriate course of action.
The need for a broader view is raised by complex questions. One example is assessing the impact of complex interventions. There are often many variants of an intervention, but even within one particular highly specified intervention there may be variations in terms of the frequency, duration, degree, engagement, and fidelity of delivery [ 40 ]. All of this variation may result in different effects on different participants in different contexts. The variation may also impact differentially within the hypothesized program theory of how the intervention impacts on different causal pathways. Reviews therefore need a strategy for how they can engage with this complexity. One strategy is to achieve breadth through multi-component reviews; for example, a broad map which can provide the context for interpreting a narrower synthesis, a series of related reviews, or mixed methods reviews. Other strategies include ‘mega reviews’, where the results from very many primary studies or meta-analyses are aggregated statistically (for example, [ 41 , 42 ]) and multivariate analyses, where moderator variables are used to identify the ‘active ingredients’ of interventions (for example, [ 43 , 44 ]). Whether breadth is achieved within a single review, from a sequence of reviews, from reviews of reviews, or from relating to the primary and review work of others, the cycle of primary research production and synthesis is part of a wider circle of engagement and response to users of research [ 45 ].
Review resources and breadth and depth of review
The resources required for a systematic review are not fixed. With different amounts of resource one can achieve different types of review. Broad reviews such as mixed methods and other multi-component reviews are likely to require more resources, all else being constant, than narrow single method reviews. Thus, in addition to the breadth of review is the issue of its depth, or the detail with which it is undertaken. A broad review may not have greater resources than a narrow review in which case those resources are spread more thinly and each aspect of that breadth may be undertaken with less depth.
When time and other resources are very restricted then a rapid review may be undertaken where some aspect of the review will be limited; for example, breadth of review question, sources searched, data coded, quality and relevance assurance measures, and depth of analysis [ 46 , 47 ]. Many students, for example, undertake literature reviews that may be informed by systematic review principles of rigor and transparency of reporting; some of these maybe relatively modest exercises whilst others make up a substantial component of the thesis. If rigor of execution and reporting are reduced too far then it may be more appropriate to characterize the work as non systematic scoping than as a systematic review.
Reviews thus vary in the extent that they engage with a research issue. The enterprise may range in size from, for instance, a specific program theory to a whole field of research. The enterprise may be under study by one research team, by a broader group such as a review group in an international collaboration or be the focus of study by many researchers internationally. The enterprises may be led academic disciplines, applied review collaborations, by priority setting agendas, and by forums to enable different perspectives to be engaged in research agendas. Whatever the nature of the strategic content or process of these macro research issues, reviews vary in the extent that they plan to contribute to such more macro questions. Reviews thus vary in the extent that this research work is done within a review; rather than before and after a review (by primary studies or by other reviews).
Reviews can be undertaken with different levels of skill, efficiency, and automated tools [ 48 ] and so resources do not equate exactly with the ‘work done’ in progressing a research issue. In general, a broad review with relatively little depth (providing a systematic overview) may be comparable in work done to a detailed narrow review (as in many current statistical meta-analyses). A multi-component review addressing complex questions using both aggregative and configuring methods may be attempting to achieve more work, though there may be challenges in terms of maintaining consistency or transparency of detail in each component of the review. In contrast, a rapid review has few resources and so is attempting less than other reviews but there may be dangers that the limited scope (and limited contribution to the broader research agenda) is not understood by funders and users of the review. How best to use available resources is a strategic issue depending upon the nature of the review question, the state of the research available on that issue and the knowledge about that state of the research. It is an issue of being fit for purpose. A review doing comparatively little ‘work’ may be exactly what is needed in one situation but not in another.
Explicit accountable methods are required for primary research and reviews of research. This logic applies to all research questions and thus multiple methods for reviews of research are required, just as they are required for primary research. These differences in types of reviews reflect the richness of primary research not only in the range of variation but also in the philosophical and methodological challenges that they pose including the mixing of different types of methods. The dominance of one form of review question and review method and the branding of some other forms of review does not clearly describe the variation in review designs and methods and the similarities and differences between these methods. Clarity about the dimensions along which reviews vary provides a way to develop review methods further and to make critical judgments necessary for the commission, production, evaluation, and use of reviews. This paper has argued for the need for clarity in describing the design and methods of systematic reviews along many dimensions; and that particularly useful dimensions for planning, describing, and evaluating reviews are:
Review aims and approach: (i) approach of the review: ontological, epistemological, theoretical, and ideological assumptions of the reviewers and users of the review including any theoretical mode; (ii) review question: the type of answer that is being sought (and the type of information that would answer it); and (ii) aggregation and configuration: the relative use of these logics and strategies in the different review components (and the positioning of theory in the review process, the degree of homogeneity of data, and the iteration of review method).
Structure and components of reviews: (iv) the systematic map and synthesis components of the review; and (v) the relation between these components.
Breadth, depth, and ‘work done’ by reviews: (vi) macro research strategy: the positioning of the review (and resources and the work aimed to be done) within the state of what is already known and other research planned by the review team and others; and (vii) the resources used to achieve this.
Clarifying some of the main dimensions along which reviews vary can provide a framework within which description of more detailed aspects of methodology can occur; for example, the specific strategies used for searching, identifying, coding, and synthesizing evidence and the use of specific methods and techniques ranging from review management software to text mining to statistical and narrative methods of analysis. Such clearer descriptions may lead in time to a more overarching system of terminology for systematic reviews.
Authors’ information
DG, JT, and SO are all directors of the Evidence for Policy and Practice Information and Coordinating Centre (EPPI-Centre) [ 49 ].
Cooper H, Hedges L: The Handbook of Research Synthesis. 1994, Russell Sage Foundation, New York
Google Scholar
Gough D: Dimensions of difference in evidence reviews (Overview; I. Questions, evidence and methods; II.Breadth and depth; III. Methodological approaches; IV. Quality and relevance appraisal; V. Communication, interpretation and application. Series of six posters presented at National Centre for Research Methods meeting, Manchester. January 2007, EPPI-Centre, London, http://eppi.ioe.ac.uk/cms/Default.aspx?tabid=1919 ,
Gough D, Thomas J: Commonality and diversity in reviews. Introduction to Systematic Reviews. Edited by: Gough D, Oliver S, Thomas J. 2012, Sage, London, 35-65.
Chalmers I, Hedges L, Cooper H: A brief history of research synthesis. Eval Health Professions. 2002, 25: 12-37. 10.1177/0163278702025001003.
Article Google Scholar
Bohlin I: Formalising syntheses of medical knowledge: the rise of meta-analysis and systematic reviews. Perspect Sci. in press, in press
Noblit G: Hare RD: Meta-ethnography: synthesizing qualitative studies. 1988, Sage Publications, Newbury Park NY
Noyes J, Popay J, Pearson A, Hannes K, Booth A: Qualitative research and Cochrane reviews. Cochrane Handbook for Systematic Reviews of Interventions. Edited by: Higgins JPT, Green S. Version 5.1.0 (updated March 2011). The Cochrane Collaboration. www.cochrane-handbook.org
Dixon-Woods M, Cavers D, Agarwal S, Annandale E, Arthur A, Harvey J, Hsu R, Katbamna S, Olsen R, Smith L, Riley R, Sutton AJ: Conducting a critical interpretive synthesis of the literature on access to healthcare by vulnerable groups. BMC Med Res Methodol. 2006, 6: 35-10.1186/1471-2288-6-35.
Article PubMed PubMed Central Google Scholar
Pawson R: Evidenced-based policy: a realist perspective. 2006, Sage, London
Book Google Scholar
Shepperd S, Lewin S, Struas S, Clarke M, Eccles M, Fitzpatrick R, Wong G, Sheikh A: Can we systematically review studies that evaluate complex interventions?. PLoS Med. 2009, 6: 8-10.1371/journal.pmed.1000008.
Greenhalgh T, Robert G, Macfarlane F, Bate P, Kyriakidou O, Peacock R: Storylines of research in diffusion of innovation: a meta-narrative approach to systematic review. Soc Sci Med. 2005, 61: 417-430. 10.1016/j.socscimed.2004.12.001.
Article PubMed Google Scholar
Barnett-Page E, Thomas J: Methods for the synthesis of qualitative research: a critical review. BMC Med Res Methodol. 2009, 9: 59-10.1186/1471-2288-9-59.
Moher D, Liberati A, Tetzlaff J, Altman DG, The PRISMA Group: Preferred reporting items for systematic reviews and meta-analyses: the PRISMA Statement. PLoS Med. 2009, 6: 6-10.1371/journal.pmed.1000006.
PLoS Medicine Editors: Best practice in systematic reviews: The importance of protocols and registration. PLoS Med. 2011, 8: 2-
Thomas G: Introduction: evidence and practice. Evidence-based Practice in Education. Edited by: Pring R, Thomas G. 2004, Open University Press, Buckingham, 44-62.
Gough D, Oliver S, Newman M, Bird K: Transparency in planning, warranting and interpreting research. Teaching and Learning Research Briefing 78. 2009, Teaching and Learning Research Programme, London
Strauss A, Corbin J: Basics of qualitative research, grounded theory procedures and techniques. 1990, Sage, London
Miles M, Huberman A: Qualitative Data Analysis. 1994, Sage, London
Voils CI, Sandelowski M, Barroso J, Hasselblad V: Making sense of qualitative and quantitative findings in mixed research synthesis studies. Field Methods. 2008, 20: 3-25. 10.1177/1525822X07307463.
Sandelowski M, Voils CJ, Leeman J, Crandlee JL: Mapping the Mixed Methods-Mixed Research Synthesis Terrain. Journal of Mixed Methods Research. 2011, 10.1177/1558689811427913.
Pawson R, Boaz A, Grayson L, Long A, Barnes C: Types and Quality of Knowledge in Social Care. 2003, Social Care Institute for Excellence, London
Oancea A, Furlong J: Expressions of excellence and the assessment of applied and practice-based research. Res Pap Educ. 2007, 22: 119-137. 10.1080/02671520701296056.
Harden A, Gough D: Quality and relevance appraisal. Introduction to Systematic Reviews. Edited by: Gough D, Oliver S, Thomas J. 2012, Sage, London, 153-178.
Thomas J, Harden A: Methods for the thematic synthesis of qualitative research in systematic reviews. BMC Med Res Methodol. 2008, 8: 45-10.1186/1471-2288-8-45.
Oliver S, Rees RW, Clarke-Jones L, Milne R, Oakley AR, Gabbay J, Stein K, Buchanan P, Gyte G: A multidimensional conceptual framework for analyzing public involvement in health services research. Heal Expect. 2008, 11: 72-84. 10.1111/j.1369-7625.2007.00476.x.
Carroll C, Booth A, Cooper K: A worked example of “best fit” framework synthesis: a systematic review of views concerning the taking of some potential chemopreventive agents. BMC Med Res Methodol. 2011, 11: 29-10.1186/1471-2288-11-29.
Rees R, Oliver S: Stakeholder perspectives and participation in reviews. Introduction to Systematic Reviews. Edited by: Gough D, Oliver S, Thomas J. 2012, Sage, London, 17-34.
Oliver S, Dickson K, Newman M: Getting started with a review. Introduction to Systematic Reviews. Edited by: Gough D, Oliver S, Thomas J. 2012, Sage, London, 66-82.
Spencer L, Ritchie J, Lewis J, Dillon L: Quality in Qualitative Evaluation: a Framework for Assessing Research Evidence. 2003, Government Chief Social Researcher’s Office, London
Weiss C: The many meanings of research utilisation. Public Adm Rev. 1979, 29: 426-431.
Peersman G: A Descriptive Mapping of Health Promotion Studies in Young People EPPI Research Report. 1996, EPI-Centre, London
Arksey H, O’Malley L: Scoping Studies: towards a methodological framework. Int J Soc Res Methodol. 2005, 8: 19-32. 10.1080/1364557032000119616.
Levac D, Colquhoun H, O’Brien KK: Scoping studies: advancing the methodology. Implement Sci. 2010, 5: 69-10.1186/1748-5908-5-69.
Thomas J, Harden A, Oakley A, Oliver S, Sutcliffe K, Rees R, Brunton G, Kavanagh J: Integrating qualitative research with trials in systematic reviews: an example from public health. Brit Med J. 2004, 328: 1010-1012. 10.1136/bmj.328.7446.1010.
Harden A, Thomas J: Mixed methods and systematic reviews: examples and emerging issues. Handbook of Mixed Methods in the Social and Behavioral Sciences. Edited by: Tashakkori A, Teddlie C. 2010, Sage, London, 749-774. 2
Chapter Google Scholar
Leontien M, van der Knaap , Leeuw FL, Bogaerts S, Laura TJ: Nijssen Combining campbell standards and the realist evaluation approach: the best of two worlds?. J Eval. 2008, 29: 48-57. 10.1177/1098214007313024.
Smith V, Devane D, Begley CM, Clarke M: Methodology in conducting a systematic review of systematic reviews of healthcare interventions. BMC Med Res Methodol. 2011, 11: 15-10.1186/1471-2288-11-15.
Oliver S, Bagnall AM, Thomas J, Shepherd J, Sowden A, White I, Dinnes J, Rees R, Colquitt J, Oliver K, Garrett Z: RCTs for policy interventions: a review of reviews and meta-regression. Health Technol Assess. 2010, 14: 16-
Scriven M: An introduction to meta-evaluation. Educational Products Report. 1969, 2: 36-38.
Carroll C, Patterson M, Wood S, Booth A, Rick J, Balain S: A conceptual framework for implementation fidelity. Implement Sci. 2007, 2: 40-10.1186/1748-5908-2-40.
Smith ML, Glass GV: Meta-analysis of psychotherapy outcome studies. Am Psychol. 1977, 32: 752-760.
Article CAS PubMed Google Scholar
Hattie J: Visible Learning: A Synthesis of Over 800 Meta-Analyses Relating to Achievement. 2008, Routledge, London
Cook TD, Cooper H, Cordray DS, Hartmann H, Hedges LV, Light RJ, Louis TA, Mosteller F: Meta-analysis for Explanation: A Casebook. 1992, Russell Sage Foundation, New York
Thompson SG, Sharp SJ: Explaining heterogeneity in meta-analysis: a comparison of methods. Stat Med. 1999, 18: 2693-2708. 10.1002/(SICI)1097-0258(19991030)18:20<2693::AID-SIM235>3.0.CO;2-V.
Stewart R, Oliver S: Making a difference with systematic reviews. Introduction to Systematic Reviews. Edited by: Gough D, Oliver S, Thomas J. 2012, Sage, London, 227-244.
Government Social Research Unit: Rapid Evidence Assessment Toolkit. 2008, http://www.civilservice.gov.uk/networks/gsr/resources-and-guidance/rapid-evidence-assessment ,
Abrami PC, Borokhovski E, Bernard RM, Wade CA, Tamim R, Persson T, Surkes MA: Issues in conducting and disseminating brief reviews of evidence. Evidence & Policy: A Journal of Research, Debate and Practice. 2010, 6: 371-389. 10.1332/174426410X524866.
Brunton J, Thomas J: Information management in reviews. Introduction to Systematic Reviews. Edited by: Gough D, Oliver S, Thomas J. 2012, Sage, London, 83-106.
Evidence for Policy and Practice Information and Coordinating Centre (EPPI-Centre): http://eppi.ioe.ac.uk ,
Download references
Acknowledgements
The authors wish to acknowledge the support and intellectual contribution of their previous and current colleagues at the EPPI-Centre. They also wish to acknowledge the support of their major funders as many of the ideas in this paper were developed whilst working on research supported by their grants; this includes the Economic and Social Research Council, the Department of Health, and the Department for Education. The views expressed here are those of the authors and are not necessarily those of our funders.
Author information
Authors and affiliations.
EPPI-Centre, Social Science Research Unit, Institute of Education, University of London, 20 Bedford Way, London, WC1H 0AL, UK
David Gough, James Thomas & Sandy Oliver
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to David Gough .
Additional information
Competing interests.
The authors declare that they have no competing interests.
Authors’ contributions
All three authors have made substantial contributions to the conception of the ideas in this paper, have been involved in drafting or revising it critically for important intellectual content, and have given final approval of the version to be published.
Authors’ original submitted files for images
Below are the links to the authors’ original submitted files for images.
Authors’ original file for figure 1
Authors’ original file for figure 2, authors’ original file for figure 3, authors’ original file for figure 4, rights and permissions.
This article is published under license to BioMed Central Ltd. This is an Open Access article distributed under the terms of the Creative Commons Attribution License ( http://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Reprints and permissions
About this article
Cite this article.
Gough, D., Thomas, J. & Oliver, S. Clarifying differences between review designs and methods. Syst Rev 1 , 28 (2012). https://doi.org/10.1186/2046-4053-1-28
Download citation
Received : 04 January 2012
Accepted : 19 March 2012
Published : 09 June 2012
DOI : https://doi.org/10.1186/2046-4053-1-28
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Aggregation configuration
- Complex reviews
- Methodology
- Research methods
- Scoping reviews
- Systematic reviews
- Taxonomy of reviews
Systematic Reviews
ISSN: 2046-4053
- Submission enquiries: Access here and click Contact Us
- General enquiries: [email protected]
Research Methodologies
- Quantitative Research Methodologies
- Qualitative Research Methodologies
- Systematic Reviews
- Finding Articles by Methodology
- Design Your Research Project
Library Help
What is a systematic review.
Systematic reviews encompass a variety of methods that involve gathering existing studies and research, then collectively analyzing them. This group of methodologies helps to identify larger conclusions about a body of knowledge, as well as identify gaps in that knowledge. These methods can also help answer research questions that are difficult to answer in a smaller, limited study.
Systematic reviews can be used to answer questions such as:
- If a variety of treatments is available for a medical condition, which of them is most effective, and under what circumstances?
- What have been the long-term effects of policy or regulatory changes?
- What factors influence complex behavior such as decision-making?
The Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) was created by researchers around the world to standardize and improve the validity of systematic reviews and meta-analyses. These standards and recommendations are regularly updated. The latest version of the PRISMA Statement asks researchers to, among other things:
- Clearly state their research objectives
- Discuss what will be included in the review, what will be excluded, and the rationale behind these choices
- Describe how data was collected, what tools were used, and any biases that data collection may have introduced
- Address any limitations and gaps in the current state of knowledge
...and much more. The full PRISMA checklist is extensive, and can be viewed at the link below.
- PRISMA Statement The PRISMA statement was developed to facilitate transparent and complete reporting of systematic reviews and has been updated to reflect recent advances in systematic review methodology and terminology.
Types of Systematic Reviews
Meta-analysis.
For this type of study, researchers will locate and use datasets from similar, smaller studies that match a pre-determined set of criteria. Criteria can include factors such as sample selection criteria, how recently the studies were conducted, the language of publication, and so on. The authors then use statistical methods to analyze the data from these studies to draw larger conclusions and commonalities.
- De Souza Tavares, V., César Stringheta, P., Perez, R., Bastos Braga, G., Corrêa Mendonça, A., & Gomes de Souza, E. C. (2022). Composition differences between organic and conventional processed foods: A meta-analytical study. Ciência Rural, 52(5), 1–12.
- Ladeira, W. J., Nardi, V. A. M., Santini, F. de O., & Jardim, W. C. (2019). Factors influencing visual attention: a meta-analysis. Journal of Marketing Management, 35(17/18), 1710–1740.
Mixed Methods Study
This methodology generally includes a significant literature review, but also some direct data collection by the authors. The authors will then use both qualitative and quantitative methodologies to analyze their data.
- Kucharczuk, A. J., Oliver, T. L., & Dowdell, E. B. (2022). Social media’s influence on adolescents′ food choices: A mixed studies systematic literature review. Appetite, 168(105765), 1-12.
Scoping Review
This type of systematic review is the result of researcher efforts to determine how much (if any) information is available on a specific topic or research question, sometimes created as preparation for a larger systematic review.
- Mares, S. (2021). Mental health consequences of detaining children and families who seek asylum: a scoping review. European Child & Adolescent Psychiatry, 30(10), 1615–1639.
- Sepulveda, T. (2021). Barriers to hiring and accommodating people with disabilities in small and medium sized businesses: A scoping review. Journal of Applied Rehabilitation Counseling, 52(2), 104–114.
- Call : 801.863.8840
- Text : 801.290.8123
- In-Person Help
- Email a Librarian
- Make an Appointment
- << Previous: Qualitative Research Methodologies
- Next: Finding Articles by Methodology >>
- Last Updated: Jun 20, 2024 3:16 PM
- URL: https://uvu.libguides.com/methods
Log in using your username and password
- Search More Search for this keyword Advanced search
- Latest content
- Current issue
- Write for Us
- BMJ Journals
You are here
- Volume 21, Issue 2
- Reviewing the literature: choosing a review design
- Article Text
- Article info
- Citation Tools
- Rapid Responses
- Article metrics
- Helen Noble 1 ,
- Joanna Smith 2
- 1 School of Nursing and Midwifery , Queen’s University Belfast , Belfast , UK
- 2 School of Healthcare , University of Leeds , Leeds , UK
- Correspondence to Dr Helen Noble, School of Nursing and Midwifery, Queen’s University Belfast, Belfast BT9 7BL, UK; helen.noble{at}qub.ac.uk
https://doi.org/10.1136/eb-2018-102895
Statistics from Altmetric.com
Request permissions.
If you wish to reuse any or all of this article please use the link below which will take you to the Copyright Clearance Center’s RightsLink service. You will be able to get a quick price and instant permission to reuse the content in many different ways.
Many health professionals, students and academics including health researchers will have grappled with the challenges of undertaking a review of the literature and choosing a suitable design or framework to structure the review. For many undergraduate and master’s healthcare students their final year dissertation involves undertaking a review of the literature as a way of assessing their understanding and ability to critique and apply research findings to practice. For PhD and Master’s by Research students, a rigorous summary of research is usually expected to identify the state of knowledge and gaps in the evidence related to their topic focus and to provide justification for the empirical work they subsequently undertake. From discussions with students and colleagues, there appears to be much confusion about review designs and in particular the use and perhaps misuse of the term ‘systematic review’. For example, some quantitatively focused researchers subscribe to a ‘Cochrane’ approach as the only method to undertake a ‘systematic review’, with other researchers having a more pragmatic view, recognising the different purposes of a review and ways of applying systematic methods to undertake a review of the literature. Traditionally, systematic reviews have included only quantitative, experimental studies, usually randomised controlled trials. 1 More recently, systematic reviews of qualitative studies have emerged, 2 and integrative reviews which include both quantitative and qualitative studies. 3
In this article, we will build on a previous Research Made Simple article that outlined the key principles of undertaking a review of the literature in a structured and systemic way 4 by further exploring review designs and their key features to assist you in choosing an appropriate design. A reference to an example of each review outlined will be provided.
What is the purpose of undertaking a review of the evidence?
The purpose of a review of healthcare literature is primarily to summarise the knowledge around a specific question or topic, or to make recommendations that can support health professionals and organisations make decisions about a specific intervention or care issue. 5 In addition, reviews can highlight gaps in knowledge to guide future research. The most common approach to summarising, interpreting and making recommendations from synthesising the evidence in healthcare is a traditional systematic review of the literature to answer a specific clinical question. These reviews follow explicit, prespecified and reproducible methods in order to identify, evaluate and summarise the findings of all relevant individual studies. 6 Systematic reviews are typically associated with evaluating interventions, and therefore where appropriate, combine the results of several empirical studies to give a more reliable estimate of an intervention’s effectiveness than a single study. 6 However, over the past decade the range of approaches to reviewing the literature has expanded to reflect broader types of evidence/research designs and questions reflecting the increased complexity of healthcare. While this should be welcomed, this adds to the challenges in choosing the best review approach/design that meets the purpose of the review.
What approaches can be adopted to review the evidence?
- View inline
Key features of the common types of healthcare review
In summary, we have identified and described a variety of review designs and offered reasons for choosing a specific approach. Reviews are vital research methodology and help make sense of a body of research. They offer a succinct analysis which avoids the need for accessing individual research reports included in the review, increasingly vital for health professionals in light of the increasing vast amount of literature available. The field of reviews of the literature continues to change and while new approaches are emerging, ensuring methods are robust and remain paramount. This paper offers guidance to help direct choices when deciding on a review and provides an example of each approach.
- 5. ↵ Canadian Institutes of Health Research . Knowledge translation. Canadian Institutes of Health Research . 2008 . http://www.cihr.ca/e/29418.html ( accessed Jan 2018 ).
- 6. ↵ Centre for Reviews and Dissemination . Guidance for undertaking reviews in heathcare . 3rd ed . York University, York : CRD , 2009 .
- Buchwald H ,
- Braunwald E , et al
- Horvath M ,
- Massey K , et al
- Sheehan KJ ,
- Sobolev B ,
- Villán Villán YF , et al
- Christmals CD ,
- Whittemore R ,
- McInnes S ,
- Bonney A , et al
- Greenhalgh T ,
- Harvey G , et al
- Rycroft-Malone J ,
- McCormack B ,
- DeCorby K , et al
- Mitchison D ,
- 19. Joanna Briggs Institute Umbrella reviews . 2014 . http://joannabriggs.org/assets/docs/sumari/ReviewersManual-Methodology-JBI_Umbrella_Reviews-2014.pdf ( accessed Jan 2018 )
- van der Linde R , et al
Competing interests None declared.
Provenance and peer review Commissioned; internally peer reviewed.
Read the full text or download the PDF:
Systematic Reviews: Levels of evidence and study design
Levels of evidence.
"Levels of Evidence" tables have been developed which outline and grade the best evidence. However, the review question will determine the choice of study design.
Secondary sources provide analysis, synthesis, interpretation and evaluation of primary works. Secondary sources are not evidence, but rather provide a commentary on and discussion of evidence. e.g. systematic review
Primary sources contain the original data and analysis from research studies. No outside evaluation or interpretation is provided. An example of a primary literature source is a peer-reviewed research article. Other primary sources include preprints, theses, reports and conference proceedings.
Levels of evidence for primary sources fall into the following broad categories of study designs (listed from highest to lowest):
- Experimental : RTC's (Randomised Control Trials)
- Quasi-experimental studies (Non-randomised control studies, Before-and-after study, Interrupted time series)
- Observational studies (Cohort study, Case-control study, Case series)
Based on information from Centre for Reviews and Dissemination. (2009). Systematic reviews: CRD's guidance for undertaking reviews in health care. Retrieved from http://www.york.ac.uk/inst/crd/index_guidance.htm
Hierarchy of Evidence Pyramid
"Levels of Evidence" are often represented in as a pyramid, with the highest level of evidence at the top:

Types of Study Design
The following definitions are adapted from the Glossary in " Systematic reviews: CRD's Guidance for Undertaking Reviews in Health Care " , Centre for Reviews and Dissemination, University of York :
- Systematic Review The application of strategies that limit bias in the assembly, critical appraisal, and synthesis of all relevant studies on a specific topic and research question.
- Meta-analysis A systematic review which uses quantitative methods to summarise the results
- Randomized control clinical trial (RCT) A group of patients is randomised into an experimental group and a control group. These groups are followed up for the variables/outcomes of interest.
- Cohort study Involves the identification of two groups (cohorts) of patients, one which did receive the exposure of interest, and one which did not, and following these cohorts forward for the outcome of interest.
- Case-control study Involves identifying patients who have the outcome of interest (cases) and control patients without the same outcome, and looking to see if they had the exposure of interest.
- Critically appraised topic A short summary of an article from the literature, created to answer a specific clinical question.
EBM and Study Design
- << Previous: SR protocol
- Next: Searching for systematic reviews >>
- Getting started
- Types of reviews
- Formulate the question
- SR protocol
- Levels of evidence and study design
- Searching for systematic reviews
- Search strategies
- Subject databases
- Keeping up to date/Alerts
- Trial registers
- Conference proceedings
- Critical appraisal
- Documenting and reporting
- Managing search results
- Statistical methods
- Journal information/publishing
- Contact a librarian
- Last Updated: May 15, 2024 11:15 AM
- URL: https://ecu.au.libguides.com/systematic-reviews
Edith Cowan University acknowledges and respects the Noongar people, who are the traditional custodians of the land upon which its campuses stand and its programs operate. In particular ECU pays its respects to the Elders, past and present, of the Noongar people, and embrace their culture, wisdom and knowledge.

Library Services
UCL LIBRARY SERVICES
- Guides and databases
- Library skills
- Systematic reviews
What are systematic reviews?
- Types of systematic reviews
- Formulating a research question
- Identifying studies
- Searching databases
- Describing and appraising studies
- Synthesis and systematic maps
- Software for systematic reviews
- Online training and support
- Live and face to face training
- Individual support
- Further help

Systematic reviews are a type of literature review of research which require equivalent standards of rigour as primary research. They have a clear, logical rationale that is reported to the reader of the review. They are used in research and policymaking to inform evidence-based decisions and practice. They differ from traditional literature reviews particularly in the following elements of conduct and reporting.
Systematic reviews:
- use explicit and transparent methods
- are a piece of research following a standard set of stages
- are accountable, replicable and updateable
- involve users to ensure a review is relevant and useful.
For example, systematic reviews (like all research) should have a clear research question, and the perspective of the authors in their approach to addressing the question is described. There are clearly described methods on how each study in a review was identified, how that study was appraised for quality and relevance and how it is combined with other studies in order to address the review question. A systematic review usually involves more than one person in order to increase the objectivity and trustworthiness of the reviews methods and findings.
Research protocols for systematic reviews may be peer-reviewed and published or registered in a suitable repository to help avoid duplication of reviews and for comparisons to be made with the final review and the planned review.
- History of systematic reviews to inform policy (EPPI-Centre)
- Six reasons why it is important to be systematic (EPPI-Centre)
- Evidence Synthesis International (ESI): Position Statement Describes the issues, principles and goals in synthesising research evidence to inform policy, practice and decisions
On this page
Should all literature reviews be 'systematic reviews', different methods for systematic reviews, reporting standards for systematic reviews.
Literature reviews provide a more complete picture of research knowledge than is possible from individual pieces of research. This can be used to: clarify what is known from research, provide new perspectives, build theory, test theory, identify research gaps or inform research agendas.
A systematic review requires a considerable amount of time and resources, and is one type of literature review.
If the purpose of a review is to make justifiable evidence claims, then it should be systematic, as a systematic review uses rigorous explicit methods. The methods used can depend on the purpose of the review, and the time and resources available.
A 'non-systematic review' might use some of the same methods as systematic reviews, such as systematic approaches to identify studies or quality appraise the literature. There may be times when this approach can be useful. In a student dissertation, for example, there may not be the time to be fully systematic in a review of the literature if this is only one small part of the thesis. In other types of research, there may also be a need to obtain a quick and not necessarily thorough overview of a literature to inform some other work (including a systematic review). Another example, is where policymakers, or other people using research findings, want to make quick decisions and there is no systematic review available to help them. They have a choice of gaining a rapid overview of the research literature or not having any research evidence to help their decision-making.
Just like any other piece of research, the methods used to undertake any literature review should be carefully planned to justify the conclusions made.
Finding out about different types of systematic reviews and the methods used for systematic reviews, and reading both systematic and other types of review will help to understand some of the differences.
Typically, a systematic review addresses a focussed, structured research question in order to inform understanding and decisions on an area. (see the Formulating a research question section for examples).
Sometimes systematic reviews ask a broad research question, and one strategy to achieve this is the use of several focussed sub-questions each addressed by sub-components of the review.
Another strategy is to develop a map to describe the type of research that has been undertaken in relation to a research question. Some maps even describe over 2,000 papers, while others are much smaller. One purpose of a map is to help choose a sub-set of studies to explore more fully in a synthesis. There are also other purposes of maps: see the box on systematic evidence maps for further information.
Reporting standards specify minimum elements that need to go into the reporting of a review. The reporting standards refer mainly to methodological issues but they are not as detailed or specific as critical appraisal for the methodological standards of conduct of a review.
A number of organisations have developed specific guidelines and standards for both the conducting and reporting on systematic reviews in different topic areas.
- PRISMA PRISMA is a reporting standard and is an acronym for Preferred Reporting Items for Systematic Reviews and Meta-Analyses. The Key Documents section of the PRISMA website links to a checklist, flow diagram and explanatory notes. PRISMA is less useful for certain types of reviews, including those that are iterative.
- eMERGe eMERGe is a reporting standard that has been developed for meta-ethnographies, a qualitative synthesis method.
- ROSES: RepOrting standards for Systematic Evidence Syntheses Reporting standards, including forms and flow diagram, designed specifically for systematic reviews and maps in the field of conservation and environmental management.
Useful books about systematic reviews
Systematic approaches to a successful literature review
An introduction to systematic reviews
Cochrane handbook for systematic reviews of interventions
Systematic reviews: crd's guidance for undertaking reviews in health care.
Finding what works in health care: Standards for systematic reviews
Systematic Reviews in the Social Sciences
Meta-analysis and research synthesis.
Research Synthesis and Meta-Analysis
Doing a Systematic Review
Literature reviews.
- What is a literature review?
- Why are literature reviews important?
- << Previous: Systematic reviews
- Next: Types of systematic reviews >>
- Last Updated: May 30, 2024 4:38 PM
- URL: https://library-guides.ucl.ac.uk/systematic-reviews

Evidence Synthesis and Systematic Reviews
- Question Formulation
Systematic Reviews
Rapid reviews, scoping reviews.
- Other Review Types
- Resources for Reviews by Discipline and Type
- Tools for Evidence Synthesis
- Grey Literature
Definition : A systematic review is a summary of research results (evidence) that uses explicit and reproducible methods to systematically search, critically appraise, and synthesize on a specific issue. It synthesizes the results of multiple primary studies related to each other by using strategies that reduce biases and errors.
When to use : If you want to identify, appraise, and synthesize all available research that is relevant to a particular question with reproduceable search methods.
Limitations : It requires extensive time and a team
Resources :
- Systematic Reviews and Meta-analysis: Understanding the Best Evidence in Primary Healthcare
- The 8 stages of a systematic review
- Determining the scope of the review and the questions it will address
- Reporting the review
Definition : Rapid reviews are a form of evidence synthesis that may provide more timely information for decision making compared with standard systematic reviews
When to use : When you want to evaluate new or emerging research topics using some systematic review methods at a faster pace
Limitations : It is not as rigorous or as thorough as a systematic review and therefore may be more likely to be biased
- Cochrane guidance for rapid reviews
- Steps for conducting a rapid review
- Expediting systematic reviews: methods and implications of rapid reviews
Definition : Scoping reviews are often used to categorize or group existing literature in a given field in terms of its nature, features, and volume.
When to use : Label body of literature with relevance to time, location (e.g. country or context), source (e.g. peer-reviewed or grey literature), and origin (e.g. healthcare discipline or academic field) It also is used to clarify working definitions and conceptual boundaries of a topic or field or to identify gaps in existing literature/research
Limitations : More citations to screen and takes as long or longer than a systematic review. Larger teams may be required because of the larger volumes of literature. Different screening criteria and process than a systematic review
- PRISMA-ScR for scoping reviews
- JBI Updated methodological guidance for the conduct of scoping reviews
- JBI Manual: Scoping Reviews (2020)
- Equator Network-Current Best Practices for the Conduct of Scoping Reviews
- << Previous: Question Formulation
- Next: Other Review Types >>
- Last Updated: Jun 11, 2024 10:02 AM
- URL: https://guides.temple.edu/systematicreviews
Temple University
University libraries.
See all library locations
- Library Directory
- Locations and Directions
- Frequently Called Numbers

Need help? Email us at [email protected]
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- J Family Med Prim Care
- v.2(1); Jan-Mar 2013
Systematic Reviews and Meta-analysis: Understanding the Best Evidence in Primary Healthcare
S. gopalakrishnan.
Department of Community Medicine, SRM Medical College, Hospital and Research Centre, Kattankulathur, Tamil Nadu, India
P. Ganeshkumar
Healthcare decisions for individual patients and for public health policies should be informed by the best available research evidence. The practice of evidence-based medicine is the integration of individual clinical expertise with the best available external clinical evidence from systematic research and patient's values and expectations. Primary care physicians need evidence for both clinical practice and for public health decision making. The evidence comes from good reviews which is a state-of-the-art synthesis of current evidence on a given research question. Given the explosion of medical literature, and the fact that time is always scarce, review articles play a vital role in decision making in evidence-based medical practice. Given that most clinicians and public health professionals do not have the time to track down all the original articles, critically read them, and obtain the evidence they need for their questions, systematic reviews and clinical practice guidelines may be their best source of evidence. Systematic reviews aim to identify, evaluate, and summarize the findings of all relevant individual studies over a health-related issue, thereby making the available evidence more accessible to decision makers. The objective of this article is to introduce the primary care physicians about the concept of systematic reviews and meta-analysis, outlining why they are important, describing their methods and terminologies used, and thereby helping them with the skills to recognize and understand a reliable review which will be helpful for their day-to-day clinical practice and research activities.
Introduction
Evidence-based healthcare is the integration of best research evidence with clinical expertise and patient values. Green denotes, “Using evidence from reliable research, to inform healthcare decisions, has the potential to ensure best practice and reduce variations in healthcare delivery.” However, incorporating research into practice is time consuming, and so we need methods of facilitating easy access to evidence for busy clinicians.[ 1 ] Ganeshkumar et al . mentioned that nearly half of the private practitioners in India were consulting more than 4 h per day in a locality,[ 2 ] which explains the difficulty of them in spending time in searching evidence during consultation. Ideally, clinical decision making ought to be based on the latest evidence available. However, to keep abreast with the continuously increasing number of publications in health research, a primary healthcare professional would need to read an insurmountable number of articles every day, covered in more than 13 million references and over 4800 biomedical and health journals in Medline alone. With the view to address this challenge, the systematic review method was developed. Systematic reviews aim to inform and facilitate this process through research synthesis of multiple studies, enabling increased and efficient access to evidence.[ 1 , 3 , 4 ]
Systematic reviews and meta-analyses have become increasingly important in healthcare settings. Clinicians read them to keep up-to-date with their field and they are often used as a starting point for developing clinical practice guidelines. Granting agencies may require a systematic review to ensure there is justification for further research and some healthcare journals are moving in this direction.[ 5 ]
This article is intended to provide an easy guide to understand the concept of systematic reviews and meta-analysis, which has been prepared with the aim of capacity building for general practitioners and other primary healthcare professionals in research methodology and day-to-day clinical practice.
The purpose of this article is to introduce readers to:
- The two approaches of evaluating all the available evidence on an issue i.e., systematic reviews and meta-analysis,
- Discuss the steps in doing a systematic review,
- Introduce the terms used in systematic reviews and meta-analysis,
- Interpret results of a meta-analysis, and
- The advantages and disadvantages of systematic review and meta-analysis.
Application
What is the effect of antiviral treatment in dengue fever? Most often a primary care physician needs to know convincing answers to questions like this in a primary care setting.
To find out the solutions or answers to a clinical question like this, one has to refer textbooks, ask a colleague, or search electronic database for reports of clinical trials. Doctors need reliable information on such problems and on the effectiveness of large number of therapeutic interventions, but the information sources are too many, i.e., nearly 20,000 journals publishing 2 million articles per year with unclear or confusing results. Because no study, regardless of its type, should be interpreted in isolation, a systematic review is generally the best form of evidence.[ 6 ] So, the preferred method is a good summary of research reports, i.e., systematic reviews and meta-analysis, which will give evidence-based answers to clinical situations.
There are two fundamental categories of research: Primary research and secondary research. Primary research is collecting data directly from patients or population, while secondary research is the analysis of data already collected through primary research. A review is an article that summarizes a number of primary studies and may draw conclusions on the topic of interest which can be traditional (unsystematic) or systematic.
Terminologies
Systematic review.
A systematic review is a summary of the medical literature that uses explicit and reproducible methods to systematically search, critically appraise, and synthesize on a specific issue. It synthesizes the results of multiple primary studies related to each other by using strategies that reduce biases and random errors.[ 7 ] To this end, systematic reviews may or may not include a statistical synthesis called meta-analysis, depending on whether the studies are similar enough so that combining their results is meaningful.[ 8 ] Systematic reviews are often called overviews.
The evidence-based practitioner, David Sackett, defines the following terminologies.[ 3 ]
- Review: The general term for all attempts to synthesize the results and conclusions of two or more publications on a given topic.
- Overview: When a review strives to comprehensively identify and track down all the literature on a given topic (also called “systematic literature review”).
- Meta-analysis: A specific statistical strategy for assembling the results of several studies into a single estimate.
Systematic reviews adhere to a strict scientific design based on explicit, pre-specified, and reproducible methods. Because of this, when carried out well, they provide reliable estimates about the effects of interventions so that conclusions are defensible. Systematic reviews can also demonstrate where knowledge is lacking. This can then be used to guide future research. Systematic reviews are usually carried out in the areas of clinical tests (diagnostic, screening, and prognostic), public health interventions, adverse (harm) effects, economic (cost) evaluations, and how and why interventions work.[ 9 ]
Cochrane reviews
Cochrane reviews are systematic reviews undertaken by members of the Cochrane Collaboration which is an international not-for-profit organization that aims to help people to make well-informed decisions about healthcare by preparing, maintaining, and promoting the accessibility of systematic reviews of the effects of healthcare interventions.
Cochrane Primary Health Care Field is a systematic review of primary healthcare research on prevention, treatment, rehabilitation, and diagnostic test accuracy. The overall aim and mission of the Primary Health Care Field is to promote the quality, quantity, dissemination, accessibility, applicability, and impact of Cochrane systematic reviews relevant to people who work in primary care and to ensure proper representation in the interests of primary care clinicians and consumers in Cochrane reviews and review groups, and in other entities. This field would serve to coordinate and promote the mission of the Cochrane Collaboration within the primary healthcare disciplines, as well as ensuring that primary care perspectives are adequately represented within the Collaboration.[ 10 ]
Meta-analysis
A meta-analysis is the combination of data from several independent primary studies that address the same question to produce a single estimate like the effect of treatment or risk factor. It is the statistical analysis of a large collection of analysis and results from individual studies for the purpose of integrating the findings.[ 11 ] The term meta-analysis has been used to denote the full range of quantitative methods for research reviews.[ 12 ] Meta-analyses are studies of studies.[ 13 ] Meta-analysis provides a logical framework to a research review where similar measures from comparable studies are listed systematically and the available effect measures are combined wherever possible.[ 14 ]
The fundamental rationale of meta-analysis is that it reduces the quantity of data by summarizing data from multiple resources and helps to plan research as well as to frame guidelines. It also helps to make efficient use of existing data, ensuring generalizability, helping to check consistency of relationships, explaining data inconsistency, and quantifies the data. It helps to improve the precision in estimating the risk by using explicit methods.
Therefore, “systematic review” will refer to the entire process of collecting, reviewing, and presenting all available evidence, while the term “meta-analysis” will refer to the statistical technique involved in extracting and combining data to produce a summary result.[ 15 ]

Steps in doing systematic reviews/meta-analysis
Following are the six fundamental essential steps while doing systematic review and meta-analysis.[ 16 ]
Define the question
This is the most important part of systematic reviews/meta-analysis. The research question for the systematic reviews may be related to a major public health problem or a controversial clinical situation which requires acceptable intervention as a possible solution to the present healthcare need of the community. This step is most important since the remaining steps will be based on this.
Reviewing the literature
This can be done by going through scientific resources such as electronic database, controlled clinical trials registers, other biomedical databases, non-English literatures, “gray literatures” (thesis, internal reports, non–peer-reviewed journals, pharmaceutical industry files), references listed in primary sources, raw data from published trials and other unpublished sources known to experts in the field. Among the available electronic scientific database, the popular ones are PUBMED, MEDLINE, and EMBASE.
Sift the studies to select relevant ones
To select the relevant studies from the searches, we need to sift through the studies thus identified. The first sift is pre-screening, i.e., to decide which studies to retrieve in full, and the second sift is selection which is to look again at these studies and decide which are to be included in the review. The next step is selecting the eligible studies based on similar study designs, year of publication, language, choice among multiple articles, sample size or follow-up issues, similarity of exposure, and or treatment and completeness of information.
It is necessary to ensure that the sifting includes all relevant studies like the unpublished studies (desk drawer problem), studies which came with negative conclusions or were published in non-English journals, and studies with small sample size.
Assess the quality of studies
The steps undertaken in evaluating the study quality are early definition of study quality and criteria, setting up a good scoring system, developing a standard form for assessment, calculating quality for each study, and finally using this for sensitivity analysis.
For example, the quality of a randomized controlled trial can be assessed by finding out the answers to the following questions:
- Was the assignment to the treatment groups really random?
- Was the treatment allocation concealed?
- Were the groups similar at baseline in terms of prognostic factors?
- Were the eligibility criteria specified?
- Were the assessors, the care provider, and the patient blinded?
- Were the point estimates and measure of variability presented for the primary outcome measure?
- Did the analyses include intention-to-treat analysis?
Calculate the outcome measures of each study and combine them
We need a standard measure of outcome which can be applied to each study on the basis of its effect size. Based on their type of outcome, following are the measures of outcome: Studies with binary outcomes (cured/not cured) have odds ratio, risk ratio; studies with continuous outcomes (blood pressure) have means, difference in means, standardized difference in means (effect sizes); and survival or time-to-event data have hazard ratios.
Combining studies
Homogeneity of different studies can be estimated at a glance from a forest plot (explained below). For example, if the lower confidence interval of every trial is below the upper of all the others, i.e., the lines all overlap to some extent, then the trials are homogeneous. If some lines do not overlap at all, these trials may be said to be heterogeneous.
The definitive test for assessing the heterogeneity of studies is a variant of Chi-square test (Mantel–Haenszel test). The final step is calculating the common estimate and its confidence interval with the original data or with the summary statistics from all the studies. The best estimate of treatment effect can be derived from the weighted summary statistics of all studies which will be based on weighting to sample size, standard errors, and other summary statistics. Log scale is used to combine the data to estimate the weighting.
Interpret results: Graph
The results of a meta-analysis are usually presented as a graph called forest plot because the typical forest plots appear as forest of lines. It provides a simple visual presentation of individual studies that went into the meta-analysis at a glance. It shows the variation between the studies and an estimate of the overall result of all the studies together.
Forest plot
Meta-analysis graphs can principally be divided into six columns [ Figure 1 ]. Individual study results are displayed in rows. The first column (“study”) lists the individual study IDs included in the meta-analysis; usually the first author and year are displayed. The second column relates to the intervention groups and the third column to the control groups. The fourth column visually displays the study results. The line in the middle is called “the line of no effect.” The weight (in %) in the fifth column indicates the weighting or influence of the study on the overall results of the meta-analysis of all included studies. The higher the percentage weight, the bigger the box, the more influence the study has on the overall results. The sixth column gives the numerical results for each study (e.g., odds ratio or relative risk and 95% confidence interval), which are identical to the graphical display in the fourth column. The diamond in the last row of the graph illustrates the overall result of the meta-analysis.[ 4 ]

Interpretation of meta-analysis[ 4 ]
Thus, the horizontal lines represent individual studies. Length of line is the confidence interval (usually 95%), squares on the line represent effect size (risk ratio) for the study, with area of the square being the study size (proportional to weight given) and position as point estimate (relative risk) of the study.[ 7 ]
For example, the forest plot of the effectiveness of dexamethasone compared with placebo in preventing the recurrence of acute severe migraine headache in adults is shown in Figure 2 .[ 17 ]

Forest plot of the effectiveness of dexamethasone compared with placebo in preventing the recurrence of acute severe migraine headache in adults[ 17 ]
The overall effect is shown as diamond where the position toward the center represents pooled point estimate, the width represents estimated 95% confidence interval for all studies, and the black plain line vertically in the middle of plot is the “line of no effect” (e.g., relative risk = 1).
Therefore, when examining the results of a systematic reviews/meta-analysis, the following questions should be kept in mind:
- Heterogeneity among studies may make any pooled estimate meaningless.
- The quality of a meta-analysis cannot be any better than the quality of the studies it is summarizing.
- An incomplete search of the literature can bias the findings of a meta-analysis.
- Make sure that the meta-analysis quantifies the size of the effect in units that you can understand.
Subgroup analysis and sensitivity analysis
Subgroup analysis looks at the results of different subgroups of trials, e.g., by considering trials on adults and children separately. This should be planned at the protocol stage itself which is based on good scientific reasoning and is to be kept to a minimum.
Sensitivity analysis is used to determine how results of a systematic review/meta-analysis change by fiddling with data, for example, what is the implication if the exclusion criteria or excluded unpublished studies or weightings are assigned differently. Thus, after the analysis, if changing makes little or no difference to the overall results, the reviewer's conclusions are robust. If the key findings disappear, then the conclusions need to be expressed more cautiously.
Advantages of Systematic Reviews
Systematic reviews have specific advantages because of using explicit methods which limit bias, draw reliable and accurate conclusions, easily deliver required information to healthcare providers, researchers, and policymakers, help to reduce the time delay in the research discoveries to implementation, improve the generalizability and consistency of results, generation of new hypotheses about subgroups of the study population, and overall they increase precision of the results.[ 18 ]
Limitations in Systematic Reviews/Meta-analysis
As with all research, the value of a systematic review depends on what was done, what was found, and the clarity of reporting. As with other publications, the reporting quality of systematic reviews varies, limiting readers’ ability to assess the strengths and weaknesses of those reviews.[ 5 ]
Even though systematic review and meta-analysis are considered the best evidence for getting a definitive answer to a research question, there are certain inherent flaws associated with it, such as the location and selection of studies, heterogeneity, loss of information on important outcomes, inappropriate subgroup analyses, conflict with new experimental data, and duplication of publication.
Publication Bias
Publication bias results in it being easier to find studies with a “positive” result.[ 19 ] This occurs particularly due to inappropriate sifting of the studies where there is always a tendency towards the studies with positive (significant) outcomes. This effect occurs more commonly in systematic reviews/meta-analysis which need to be eliminated.
The quality of reporting of systematic reviews is still not optimal. In a recent review of 300 systematic reviews, few authors reported assessing possible publication bias even though there is overwhelming evidence both for its existence and its impact on the results of systematic reviews. Even when the possibility of publication bias is assessed, there is no guarantee that systematic reviewers have assessed or interpreted it appropriately.[ 20 ]
To overcome certain limitations mentioned above, the Cochrane reviews are currently reported in a format where at the end of every review, findings are summarized in the author's point of view and also give an overall picture of the outcome by means of plain language summary. This is found to be much helpful to understand the existing evidence about the topic more easily by the reader.
A systematic review is an overview of primary studies which contains an explicit statement of objectives, materials, and methods, and has been conducted according to explicit and reproducible methodology. A meta-analysis is a mathematical synthesis of the results of two or more primary studies that addressed the same hypothesis in the same way. Although meta-analysis can increase the precision of a result, it is important to ensure that the methods used for the reviews were valid and reliable.
High-quality systematic reviews and meta-analyses take great care to find all relevant studies, critically assess each study, synthesize the findings from individual studies in an unbiased manner, and present balanced important summary of findings with due consideration of any flaws in the evidence. Systematic review and meta-analysis is a way of summarizing research evidence, which is generally the best form of evidence, and hence positioned at the top of the hierarchy of evidence.
Systematic reviews can be very useful decision-making tools for primary care/family physicians. They objectively summarize large amounts of information, identifying gaps in medical research, and identifying beneficial or harmful interventions which will be useful for clinicians, researchers, and even for public and policymakers.
Source of Support: Nil
Conflict of Interest: None declared.

Literature Reviews: Types of Clinical Study Designs
- Library Basics
- 1. Choose Your Topic
- How to Find Books
- Types of Clinical Study Designs
- Types of Literature
- 3. Search the Literature
- 4. Read & Analyze the Literature
- 5. Write the Review
- Keeping Track of Information
- Style Guides
- Books, Tutorials & Examples
Types of Study Designs
Meta-Analysis A way of combining data from many different research studies. A meta-analysis is a statistical process that combines the findings from individual studies. Example : Anxiety outcomes after physical activity interventions: meta-analysis findings . Conn V. Nurs Res . 2010 May-Jun;59(3):224-31.
Systematic Review A summary of the clinical literature. A systematic review is a critical assessment and evaluation of all research studies that address a particular clinical issue. The researchers use an organized method of locating, assembling, and evaluating a body of literature on a particular topic using a set of specific criteria. A systematic review typically includes a description of the findings of the collection of research studies. The systematic review may also include a quantitative pooling of data, called a meta-analysis. Example : Complementary and alternative medicine use among women with breast cancer: a systematic review. Wanchai A, Armer JM, Stewart BR. Clin J Oncol Nurs . 2010 Aug;14(4):E45-55.
Randomized Controlled Trial A controlled clinical trial that randomly (by chance) assigns participants to two or more groups. There are various methods to randomize study participants to their groups. Example : Meditation or exercise for preventing acute respiratory infection: a randomized controlled trial . Barrett B, et al. Ann Fam Med . 2012 Jul-Aug;10(4):337-46.
Cohort Study (Prospective Observational Study) A clinical research study in which people who presently have a certain condition or receive a particular treatment are followed over time and compared with another group of people who are not affected by the condition. Example : Smokeless tobacco cessation in South Asian communities: a multi-centre prospective cohort study . Croucher R, et al. Addiction. 2012 Dec;107 Suppl 2:45-52.
Case-control Study Case-control studies begin with the outcomes and do not follow people over time. Researchers choose people with a particular result (the cases) and interview the groups or check their records to ascertain what different experiences they had. They compare the odds of having an experience with the outcome to the odds of having an experience without the outcome. Example : Non-use of bicycle helmets and risk of fatal head injury: a proportional mortality, case-control study . Persaud N, et al. CMAJ . 2012 Nov 20;184(17):E921-3.
Cross-sectional study The observation of a defined population at a single point in time or time interval. Exposure and outcome are determined simultaneously. Example : Fasting might not be necessary before lipid screening: a nationally representative cross-sectional study . Steiner MJ, et al. Pediatrics . 2011 Sep;128(3):463-70.
Case Reports and Series A report on a series of patients with an outcome of interest. No control group is involved. Example : Students mentoring students in a service-learning clinical supervision experience: an educational case report . Lattanzi JB, et al. Phys Ther . 2011 Oct;91(10):1513-24.
Ideas, Editorials, Opinions Put forth by experts in the field. Example : Health and health care for the 21st century: for all the people . Koop CE. Am J Public Health . 2006 Dec;96(12):2090-2.
Animal Research Studies Studies conducted using animal subjects. Example : Intranasal leptin reduces appetite and induces weight loss in rats with diet-induced obesity (DIO) . Schulz C, Paulus K, Jöhren O, Lehnert H. Endocrinology . 2012 Jan;153(1):143-53.
Test-tube Lab Research "Test tube" experiments conducted in a controlled laboratory setting.
Adapted from Study Designs. In NICHSR Introduction to Health Services Research: a Self-Study Course. http://www.nlm.nih.gov/nichsr/ihcm/06studies/studies03.html and Glossary of EBM Terms. http://www.cebm.utoronto.ca/glossary/index.htm#top
Study Design Terminology
Bias - Any deviation of results or inferences from the truth, or processes leading to such deviation. Bias can result from several sources: one-sided or systematic variations in measurement from the true value (systematic error); flaws in study design; deviation of inferences, interpretations, or analyses based on flawed data or data collection; etc. There is no sense of prejudice or subjectivity implied in the assessment of bias under these conditions.
Case Control Studies - Studies which start with the identification of persons with a disease of interest and a control (comparison, referent) group without the disease. The relationship of an attribute to the disease is examined by comparing diseased and non-diseased persons with regard to the frequency or levels of the attribute in each group.
Causality - The relating of causes to the effects they produce. Causes are termed necessary when they must always precede an effect and sufficient when they initiate or produce an effect. Any of several factors may be associated with the potential disease causation or outcome, including predisposing factors, enabling factors, precipitating factors, reinforcing factors, and risk factors.
Control Groups - Groups that serve as a standard for comparison in experimental studies. They are similar in relevant characteristics to the experimental group but do not receive the experimental intervention.
Controlled Clinical Trials - Clinical trials involving one or more test treatments, at least one control treatment, specified outcome measures for evaluating the studied intervention, and a bias-free method for assigning patients to the test treatment. The treatment may be drugs, devices, or procedures studied for diagnostic, therapeutic, or prophylactic effectiveness. Control measures include placebos, active medicines, no-treatment, dosage forms and regimens, historical comparisons, etc. When randomization using mathematical techniques, such as the use of a random numbers table, is employed to assign patients to test or control treatments, the trials are characterized as Randomized Controlled Trials.
Cost-Benefit Analysis - A method of comparing the cost of a program with its expected benefits in dollars (or other currency). The benefit-to-cost ratio is a measure of total return expected per unit of money spent. This analysis generally excludes consideration of factors that are not measured ultimately in economic terms. Cost effectiveness compares alternative ways to achieve a specific set of results.
Cross-Over Studies - Studies comparing two or more treatments or interventions in which the subjects or patients, upon completion of the course of one treatment, are switched to another. In the case of two treatments, A and B, half the subjects are randomly allocated to receive these in the order A, B and half to receive them in the order B, A. A criticism of this design is that effects of the first treatment may carry over into the period when the second is given.
Cross-Sectional Studies - Studies in which the presence or absence of disease or other health-related variables are determined in each member of the study population or in a representative sample at one particular time. This contrasts with LONGITUDINAL STUDIES which are followed over a period of time.
Double-Blind Method - A method of studying a drug or procedure in which both the subjects and investigators are kept unaware of who is actually getting which specific treatment.
Empirical Research - The study, based on direct observation, use of statistical records, interviews, or experimental methods, of actual practices or the actual impact of practices or policies.
Evaluation Studies - Works consisting of studies determining the effectiveness or utility of processes, personnel, and equipment.
Genome-Wide Association Study - An analysis comparing the allele frequencies of all available (or a whole genome representative set of) polymorphic markers in unrelated patients with a specific symptom or disease condition, and those of healthy controls to identify markers associated with a specific disease or condition.
Intention to Treat Analysis - Strategy for the analysis of Randomized Controlled Trial that compares patients in the groups to which they were originally randomly assigned.
Logistic Models - Statistical models which describe the relationship between a qualitative dependent variable (that is, one which can take only certain discrete values, such as the presence or absence of a disease) and an independent variable. A common application is in epidemiology for estimating an individual's risk (probability of a disease) as a function of a given risk factor.
Longitudinal Studies - Studies in which variables relating to an individual or group of individuals are assessed over a period of time.
Lost to Follow-Up - Study subjects in cohort studies whose outcomes are unknown e.g., because they could not or did not wish to attend follow-up visits.
Matched-Pair Analysis - A type of analysis in which subjects in a study group and a comparison group are made comparable with respect to extraneous factors by individually pairing study subjects with the comparison group subjects (e.g., age-matched controls).
Meta-Analysis - Works consisting of studies using a quantitative method of combining the results of independent studies (usually drawn from the published literature) and synthesizing summaries and conclusions which may be used to evaluate therapeutic effectiveness, plan new studies, etc. It is often an overview of clinical trials. It is usually called a meta-analysis by the author or sponsoring body and should be differentiated from reviews of literature.
Numbers Needed To Treat - Number of patients who need to be treated in order to prevent one additional bad outcome. It is the inverse of Absolute Risk Reduction.
Odds Ratio - The ratio of two odds. The exposure-odds ratio for case control data is the ratio of the odds in favor of exposure among cases to the odds in favor of exposure among noncases. The disease-odds ratio for a cohort or cross section is the ratio of the odds in favor of disease among the exposed to the odds in favor of disease among the unexposed. The prevalence-odds ratio refers to an odds ratio derived cross-sectionally from studies of prevalent cases.
Patient Selection - Criteria and standards used for the determination of the appropriateness of the inclusion of patients with specific conditions in proposed treatment plans and the criteria used for the inclusion of subjects in various clinical trials and other research protocols.
Predictive Value of Tests - In screening and diagnostic tests, the probability that a person with a positive test is a true positive (i.e., has the disease), is referred to as the predictive value of a positive test; whereas, the predictive value of a negative test is the probability that the person with a negative test does not have the disease. Predictive value is related to the sensitivity and specificity of the test.
Prospective Studies - Observation of a population for a sufficient number of persons over a sufficient number of years to generate incidence or mortality rates subsequent to the selection of the study group.
Qualitative Studies - Research that derives data from observation, interviews, or verbal interactions and focuses on the meanings and interpretations of the participants.
Quantitative Studies - Quantitative research is research that uses numerical analysis.
Random Allocation - A process involving chance used in therapeutic trials or other research endeavor for allocating experimental subjects, human or animal, between treatment and control groups, or among treatment groups. It may also apply to experiments on inanimate objects.
Randomized Controlled Trial - Clinical trials that involve at least one test treatment and one control treatment, concurrent enrollment and follow-up of the test- and control-treated groups, and in which the treatments to be administered are selected by a random process, such as the use of a random-numbers table.
Reproducibility of Results - The statistical reproducibility of measurements (often in a clinical context), including the testing of instrumentation or techniques to obtain reproducible results. The concept includes reproducibility of physiological measurements, which may be used to develop rules to assess probability or prognosis, or response to a stimulus; reproducibility of occurrence of a condition; and reproducibility of experimental results.
Retrospective Studies - Studies used to test etiologic hypotheses in which inferences about an exposure to putative causal factors are derived from data relating to characteristics of persons under study or to events or experiences in their past. The essential feature is that some of the persons under study have the disease or outcome of interest and their characteristics are compared with those of unaffected persons.
Sample Size - The number of units (persons, animals, patients, specified circumstances, etc.) in a population to be studied. The sample size should be big enough to have a high likelihood of detecting a true difference between two groups.
Sensitivity and Specificity - Binary classification measures to assess test results. Sensitivity or recall rate is the proportion of true positives. Specificity is the probability of correctly determining the absence of a condition.
Single-Blind Method - A method in which either the observer(s) or the subject(s) is kept ignorant of the group to which the subjects are assigned.
Time Factors - Elements of limited time intervals, contributing to particular results or situations.
Source: NLM MeSH Database
- << Previous: How to Find Books
- Next: Types of Literature >>
- Last Updated: Dec 29, 2023 11:41 AM
- URL: https://research.library.gsu.edu/litrev

Higher Education News , Tips for Online Students , Tips for Students
A Comprehensive Guide to Different Types of Research
Updated: June 19, 2024
Published: June 15, 2024

When embarking on a research project, selecting the right methodology can be the difference between success and failure. With various methods available, each suited to different types of research, it’s essential you make an informed choice. This blog post will provide tips on how to choose a research methodology that best fits your research goals .
We’ll start with definitions: Research is the systematic process of exploring, investigating, and discovering new information or validating existing knowledge. It involves defining questions, collecting data, analyzing results, and drawing conclusions.
Meanwhile, a research methodology is a structured plan that outlines how your research is to be conducted. A complete methodology should detail the strategies, processes, and techniques you plan to use for your data collection and analysis.

Research Methods
The first step of a research methodology is to identify a focused research topic, which is the question you seek to answer. By setting clear boundaries on the scope of your research, you can concentrate on specific aspects of a problem without being overwhelmed by information. This will produce more accurate findings.
Along with clarifying your research topic, your methodology should also address your research methods. Let’s look at the four main types of research: descriptive, correlational, experimental, and diagnostic.
Descriptive Research
Descriptive research is an approach designed to describe the characteristics of a population systematically and accurately. This method focuses on answering “what” questions by providing detailed observations about the subject. Descriptive research employs surveys, observational studies , and case studies to gather qualitative or quantitative data.
A real-world example of descriptive research is a survey investigating consumer behavior toward a competitor’s product. By analyzing the survey results, the company can gather detailed insights into how consumers perceive a competitor’s product, which can inform their marketing strategies and product development.
Correlational Research
Correlational research examines the statistical relationship between two or more variables to determine whether a relationship exists. Correlational research is particularly useful when ethical or practical constraints prevent experimental manipulation. It is often employed in fields such as psychology, education, and health sciences to provide insights into complex real-world interactions, helping to develop theories and inform further experimental research.
An example of correlational research is the study of the relationship between smoking and lung cancer. Researchers observe and collect data on individuals’ smoking habits and the incidence of lung cancer to determine if there is a correlation between the two variables. This type of research helps identify patterns and relationships, indicating whether increased smoking is associated with higher rates of lung cancer.
Experimental Research
Experimental research is a scientific approach where researchers manipulate one or more independent variables to observe their effect on a dependent variable. This method is designed to establish cause-and-effect relationships. Fields like psychology , medicine, and social sciences frequently employ experimental research to test hypotheses and theories under controlled conditions.
A real-world example of experimental research is Pavlov’s Dog experiment. In this experiment, Ivan Pavlov demonstrated classical conditioning by ringing a bell each time he fed his dogs. After repeating this process multiple times, the dogs began to salivate just by hearing the bell, even when no food was presented. This experiment helped to illustrate how certain stimuli can elicit specific responses through associative learning.
Diagnostic Research
Diagnostic research tries to accurately diagnose a problem by identifying its underlying causes. This type of research is crucial for understanding complex situations where a precise diagnosis is necessary for formulating effective solutions. It involves methods such as case studies and data analysis and often integrates both qualitative and quantitative data to provide a comprehensive view of the issue at hand.
An example of diagnostic research is studying the causes of a specific illness outbreak. During an outbreak of a respiratory virus, researchers might conduct diagnostic research to determine the factors contributing to the spread of the virus. This could involve analyzing patient data, testing environmental samples, and evaluating potential sources of infection. The goal is to identify the root causes and contributing factors to develop effective containment and prevention strategies.
Using an established research method is imperative, no matter if you are researching for marketing , technology , healthcare , engineering, or social science. A methodology lends legitimacy to your research by ensuring your data is both consistent and credible. A well-defined methodology also enhances the reliability and validity of the research findings, which is crucial for drawing accurate and meaningful conclusions.
Additionally, methodologies help researchers stay focused and on track, limiting the scope of the study to relevant questions and objectives. This not only improves the quality of the research but also ensures that the study can be replicated and verified by other researchers, further solidifying its scientific value.

How to Choose a Research Methodology
Choosing the best research methodology for your project involves several key steps to ensure that your approach aligns with your research goals and questions. Here’s a simplified guide to help you make the best choice.
Understand Your Goals
Clearly define the objectives of your research. What do you aim to discover, prove, or understand? Understanding your goals helps in selecting a methodology that aligns with your research purpose.
Consider the Nature of Your Data
Determine whether your research will involve numerical data, textual data, or both. Quantitative methods are best for numerical data, while qualitative methods are suitable for textual or thematic data.
Understand the Purpose of Each Methodology
Becoming familiar with the four types of research – descriptive, correlational, experimental, and diagnostic – will enable you to select the most appropriate method for your research. Many times, you will want to use a combination of methods to gather meaningful data.
Evaluate Resources and Constraints
Consider the resources available to you, including time, budget, and access to data. Some methodologies may require more resources or longer timeframes to implement effectively.
Review Similar Studies
Look at previous research in your field to see which methodologies were successful. This can provide insights and help you choose a proven approach.
By following these steps, you can select a research methodology that best fits your project’s requirements and ensures robust, credible results.
Completing Your Research Project
Upon completing your research, the next critical step is to analyze and interpret the data you’ve collected. This involves summarizing the key findings, identifying patterns, and determining how these results address your initial research questions. By thoroughly examining the data, you can draw meaningful conclusions that contribute to the body of knowledge in your field.
It’s essential that you present these findings clearly and concisely, using charts, graphs, and tables to enhance comprehension. Furthermore, discuss the implications of your results, any limitations encountered during the study, and how your findings align with or challenge existing theories.
Your research project should conclude with a strong statement that encapsulates the essence of your research and its broader impact. This final section should leave readers with a clear understanding of the value of your work and inspire continued exploration and discussion in the field.
Now that you know how to perform quality research , it’s time to get started! Applying the right research methodologies can make a significant difference in the accuracy and reliability of your findings. Remember, the key to successful research is not just in collecting data, but in analyzing it thoughtfully and systematically to draw meaningful conclusions. So, dive in, explore, and contribute to the ever-growing body of knowledge with confidence. Happy researching!
At UoPeople, our blog writers are thinkers, researchers, and experts dedicated to curating articles relevant to our mission: making higher education accessible to everyone.
Related Articles
Click through the PLOS taxonomy to find articles in your field.
For more information about PLOS Subject Areas, click here .
Loading metrics
Open Access
Peer-reviewed
Research Article
Influencing factors of stroke in patients with type 2 diabetes: A systematic review and meta-analysis
Roles Conceptualization, Methodology, Software, Visualization, Writing – original draft, Writing – review & editing
Affiliation School of Nursing, Zhejiang Chinese Medical University, Hangzhou, 310053, China
Roles Funding acquisition, Methodology, Supervision, Writing – review & editing
Affiliation Department of Nursing, Zhejiang Provincial People’s Hospital (Affiliated People’s Hospital), Hangzhou Medical College, Hangzhou, 310014, China
Roles Methodology, Software, Visualization
Roles Funding acquisition, Methodology, Project administration, Supervision, Writing – review & editing
* E-mail: [email protected] (SHJ)
- Mengjiao Zhao,
- Yongze Dong,
- Luchen Chen,
- Huajuan Shen

- Published: June 24, 2024
- https://doi.org/10.1371/journal.pone.0305954
- Reader Comments
Stroke stands as a significant macrovascular complication among individuals with Type 2 diabetes mellitus (T2DM), often resulting in the primary cause of mortality and disability within this patient demographic. Presently, numerous studies have been conducted to investigate the underlying causes of stroke in individuals with T2DM, yet the findings exhibit inconsistencies.
This paper aims to consolidate and summarize the available evidence concerning the influential factors contributing to stroke among patients diagnosed with T2DM.
We conducted a comprehensive search across multiple databases, including Cochrane Library, PubMed, Web Of Science, Embase, China Biology Medicine (CBM), China National Knowledge Infrastructure (CNKI), Wanfang and Weipu up to August 2023. Google Scholar was also searched to retrieve gray literature. We calculated odds ratios (OR) and 95% confidence intervals (CI) using Stata software.
Our analysis encompassed 43 observational studies, exploring factors across sociodemographic, biochemical, complications, and hypoglycemic agent categories. The findings identified several risk factors for stroke in patients with T2DM: age, gender, T2DM duration, hypertension, body-mass index (BMI), smoking, Glycated hemoglobin (HbA1c), estimated Glomerular Filtration Rate (eGFR), albuminuria, Triglycerides (TG), Low density lipoprotein cholesterol (LDL-C), Coronary heart disease (CHD), Atrial fibrillation (AF), diabetic retinopathy (DR), Peripheral vascular disease (PVD), and carotid plaque. Conversely, exercise, High density lipoprotein cholesterol (HDL-C), metformin (MET), pioglitazone, and metformin combination therapy emerged as protective factors.
This study underscores the multitude of influencing factors contributing to stroke in people with T2DM patients, among which the microvascular complications of T2DM play an most important role. Therefore, we emphasize the importance of screening for microvascular complications in patients with T2DM. However, due to limitations arising from the number of articles reviewed, there remain areas where clarity is lacking. Further research efforts are warranted to expand upon and reinforce our current findings.
Citation: Zhao M, Dong Y, Chen L, Shen H (2024) Influencing factors of stroke in patients with type 2 diabetes: A systematic review and meta-analysis. PLoS ONE 19(6): e0305954. https://doi.org/10.1371/journal.pone.0305954
Editor: Jacopo Sabbatinelli, Universita Politecnica delle Marche, ITALY
Received: February 8, 2024; Accepted: June 9, 2024; Published: June 24, 2024
Copyright: © 2024 Zhao et al. This is an open access article distributed under the terms of the Creative Commons Attribution License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Data Availability: All relevant data are within the manuscript and its Supporting Information files.
Funding: This work was supported by the General Project of Zhejiang Medical and Health Science and Technology Plan (Grant No.2021KY468 and Grant No.2021KY066). The funders had no role in study design, data collection and analysis, decision to publish, or preparation of the manuscript.
Competing interests: The authors have declared that no competing interests exist.
1. Introduction
T2DM currently affects an estimated 10.5% (536.6 million) of the global population, a figure expected to escalate to 12.2% (783.2 million) by 2045, as projected by the International Diabetes Federation [ 1 ]. This chronic condition predisposes individuals to various macrovascular and microvascular complications, significantly contributing to mortality rates worldwide [ 2 – 3 ]. Stroke, among the prevalent macrovascular complications associated with T2DM, accounted for 6.55 million fatalities in 2019, securing its place as the second leading cause of death globally [ 4 ]. Notably, individuals with diabetes face a two to four fold increased risk of stroke compared to their nondiabetic counterparts. Moreover, diabetic patients tend to experience exacerbated post-stroke outcomes and possess a heightened susceptibility to stroke recurrence [ 5 – 6 ].
The occurrence of stroke in T2DM patients results from a convergence of factors including age, gender, hypertension, smoking, dyslipidemia, and more [ 7 – 9 ]. Recent studies indicate a predictive relationship between T2DM microvascular complications such as diabetic nephropathy (DN), DR, diabetic neuropathy, and the likelihood of stroke [ 10 ]. Furthermore, emerging evidence recognizes the cardiovascular protective properties of novel hypoglycemic drugs like sodium-glucose cotransporter-2 inhibitors (SGLT-2is) and glucagon-like peptide-1 receptor agonists (GLP-1 RAs) [ 11 ]. However, the existing body of research on stroke causation in T2DM patients exhibits variations in focus, population demographics, sample sizes, and consequent disparate findings.
Therefore, we conducted the current systematic review and meta-analysis to review the influencing factors of stroke in patients with T2DM worldwide and explore the strengths of such associations for early identification and prevention of stroke.
This review was conducted in accordance with the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) [ 12 ]. The study was registered in the "International Prospective Register of Systematic Reviews" (PROSPERO) on November 20, 2023 (CRD42023480426).
2.1 Search strategy
Articles were searched on eight electronic databases, including PubMed, Web Of Science, Embasse, Cochrane Library, CBM, CNKI, Weipu and Wanfang database. Gray literature was researched in Google Scholar. We performed the search strategy until August 2023. A combination of MeSH terms and free terms related to “Diabetes Mellitus, Type 2 OR Diabetes Mellitus, Type II OR Type 2 Diabetes Mellitus OR Type 2 Diabetes OR Diabetes, Type 2 OR Diabetes Mellitus, Noninsulin-Dependent OR Diabetes Mellitus, Non Insulin Dependent OR Diabetes Mellitus, Non-Insulin-Dependent OR Non-Insulin-Dependent Diabetes Mellitus”, “Strokes OR Stroke OR Cerebrovascular Accident* OR Cerebrovascular Apoplexy OR Apoplexy, Cerebrovascular OR Vascular Accident, Brain OR Brain Vascular Accident* OR Cerebral Stroke* OR Apoplexy OR Stroke, Acute OR Acute Cerebrovascular Accident OR Hemorrhagic Stroke* OR Ischemic Stroke* OR Acute Ischemic Stroke* OR Thrombotic Stroke* OR Embolic Stroke* OR Cerebral Infarction*”, “risk factors OR risk factor OR influence factor* OR relevant factor*” were used to search. (S1 Table in S1 Appendix )
2.2 Inclusion and exclusion criteria
Studies that reported possible influencing factors of stroke in patients with T2DM were selected based on these inclusion criteria: (1) Patient age ≥ 18 years; (2) observational study (case control, cohort and cross-sectional study); (3) studies that provide the OR with 95% CI, or can be calculated with sufficient information. (4) English or Chinese article. Studies were excluded if they were: (1) duplicate literature; (2) case reports, reviews, conference abstracts, systematic reviews; (3) incomplete or unavailable literature.
2.3 Quality assessment
Two researchers, Mengjiao Zhao and Luchen Chen, independently evaluated article quality using the Newcastle-Ottawa Scale (NOS) for cohort and case-control studies (score ≥ 7 considered high quality) [ 13 ], and the criteria of America Agency for Healthcare Research and Quality (AHRQ) for cross-sectional studies (score ≥ 8 considered high quality) [ 14 ]. In the case of uncertainty or disagreement about quality, the article was reviewed by a third researcher, Yongze Dong.
2.4 Data extraction
Data extraction was performed by Mengjiao Zhao and Luchen Chen using a standardized form, encompassing details like author, publication year, country, study type, sample size, influencing factors, and adjusted OR with 95% CI for potential confounding variables. Consensus was reached in cases of disagreement through group discussion.
2.5 Data synthesis and statistical analysis
Stata 15.1 software facilitated data analysis, computing pooled OR with 95% CI. A significance level of P < 0.05 was applied. Heterogeneity was assessed using Cochran Q and I 2 statistics, adopting a fixed-effects model in the absence of significant heterogeneity (P > 0.10 and I 2 ≤ 50%). Otherwise, a random-effects model was employed. Subgroup and sensitivity analyses were performed to explore heterogeneity causes. We analysed subgroups by study area, sample size, type of study design and different classes of influencing factors. Additionally, sensitivity analyses by iteratively removing one study at a time. Egger’s linear regression test gauged publication bias (P > 0.05 indicates no significant publication bias; P < 0.05 suggests publication bias).
3.1 Search results
As shown in Fig 1 . In total, 13,827 articles were initially identified, with 2,887 duplicates removed. After screening titles and abstracts, 10,771 papers were excluded. A full-text assessment of 169 studies followed, resulting in the exclusion of 126 ineligible studies. Ultimately, 43 studies met the eligibility criteria for inclusion [ 15 – 57 ].
- PPT PowerPoint slide
- PNG larger image
- TIFF original image
https://doi.org/10.1371/journal.pone.0305954.g001
3.2. Characteristics of the included studies
Table 1 showcases the essential features of the 43 incorporated articles, spanning publication years from 2001 to 2023. The studies comprised 28 cohort studies, 8 case-control studies, and 7 cross-sectional studies. Among these, 22 were conducted in developed nations (USA, UK, Australia, Denmark, New Zealand, Spain, Korea, Japan) and 21 in developing countries (China, Saudi Arabia). The sample sizes varied from 96 [ 30 ] to 1,297,131 [ 29 ], totaling 2,730,010 participants. The quality assessment showed a literature quality assessment score of 7–9 for cohort and case-control studies and 8–10 for cross-sectional studies. (S2-S4 Table in S1 Appendix )
https://doi.org/10.1371/journal.pone.0305954.t001
3.3. Meta-analysis for influencing factors
The meta-analysis encompassed 22 influencing factors categorized into sociodemographic factors, biochemical factors, complications, and hypoglycemic agents. Among the sociodemographic factors are age [ 15 – 26 ], gender [ 15 , 17 , 20 , 27 – 28 ], course of T2DM [ 15 , 20 , 23 , 29 , 31 ], hypertension [ 15 , 20 – 22 , 28 , 30 , 32 – 35 ], BMI [ 15 , 19 – 20 , 33 ], smoking [ 15 , 17 , 24 , 29 , 33 , 36 ] and exercise [ 29 , 33 , 36 ]; Biochemical indexes are HbA1c [ 15 , 17 , 22 , 30 , 37 ], eGFR [ 16 , 19 , 22 , 38 – 39 ], TC [ 16 , 25 , 30 – 31 ], TG [ 16 , 19 , 24 ], Albuminuria [ 16 , 31 , 40 – 41 ], HDL-C [ 19 , 42 ] and LDL-C [ 19 , 42 ]; Complications are CHD [ 27 , 29 , 35 ], AF [ 16 , 29 , 31 , 35 , 41 , 43 ], DR [ 16 , 41 , 44 ], PVD [ 21 , 24 , 45 ] and carotid plaque [ 23 , 32 ], as well as hypoglycemic agents are MET [ 46 – 47 ], pioglitazone [ 48 – 49 ] and MET combination therapy [ 50 – 53 ]. Among the four categories, the pooled OR of complications was the highest (2.09, 95% CI: 1.44–3.05), followed by sociodemographic factors (1.37, 95% CI: 1.14–1.65) and biochemical factors (1.28, 95% CI: 1.05–1.57), while the hypoglycemic agents was the lowest (0.63, 95% CI: 0.46–0.85), which was a protective factor. The details are shown in Table 2 . In addition, the forest plot containing all the influencing factors is shown in Fig 2 .
https://doi.org/10.1371/journal.pone.0305954.t002
https://doi.org/10.1371/journal.pone.0305954.g002
3.3.1 Sociodemographic factors.
A study of 22 articles exploring the correlation between sociodemographic factors and stroke in T2DM patients highlighted age, hypertension, and duration of T2DM as frequently studied factors. Notably, hypertension demonstrated the highest pooled OR (2.71, 95% CI: 2.41–3.04), followed by smoking (1.65, 95% CI: 1.60–2.97). Additionally, factors such as longer T2DM duration (1.46, 95% CI: 1.28–1.67), male gender (1.40, 95% CI: 1.34–1.46), BMI (1.18, 95% CI: 1.14–1.23), and age (1.10, 95% CI: 1.06–1.13) were associated with higher stroke risk. Conversely, exercise exhibited a protective effect (0.77, 95% CI: 0.69–0.86).
3.3.2 Biochemical factors.
Among 17 articles investigating biochemical factors, LDL-C exhibited the highest pooled OR (3.41, 95% CI: 1.81–6.41), followed by eGFR (2.15, 95% CI: 1.81–2.55) and albuminuria (1.32, 95% CI: 1.17–1.49). Other factors, including TG (1.16, 95% CI: 1.06–1.26) and HbA1c (1.09, 95% CI: 1.07–1.11), were identified as risk factors for stroke, whereas HDL-C (0.14, 95% CI: 0.05–0.39) appeared protective. However, TC (0.90, 95% CI: 0.59–1.37) was not significantly associated with stroke in T2DM patients.
3.3.3 Complications.
The analysis of 13 studies exploring complications and stroke revealed CHD (2.92, 95% CI: 1.35–6.30), PVD (2.84, 95% CI: 1.86–4.34), and AF (2.76, 95% CI: 2.56–2.97) as factors with the highest pooled OR. DR(1.59, 95% CI: 1.35–1.88) and carotid plaque (1.36, 95% CI: 1.14–1.62) were also linked to increased stroke risk.
3.3.4 Hypoglycemic agents.
Exploring hypoglycemic agents across 8 articles, MET combination therapy (0.74, 95% CI: 0.66–0.83) and pioglitazone (0.72, 95% CI: 0.64–0.81) showed similar pooled OR, indicating a protective effect. In contrast, MET alone exhibited the lowest pooled OR (0.47, 95% CI: 0.43–0.52).
3.3.5 Other factors.
In addition to the factors noted above, several variables have shown significant associations with stroke occurrences in patients with T2DM. These factors include central obesity [ 25 ] (2.07, 95% CI: 1.39–3.09), inadequate sleep duration [ 33 ] (< 6h/ day: 1.44, 95% CI: 1.20–1.73; > 8h/ day: 1.22, 95% CI: 1.05–1.42), obstructive sleep apnea [ 54 ] (1.57, 95% CI: 1.27–1.94), lower educational attainment [ 28 ] (2.60, 95% CI: 1.20–5.80), alcohol misuse [ 24 ] (2.60, 95% CI: 1.20–5.80), degree of cerebral artery stenosis [ 32 ] (4.77, 95% CI: 2.60–9.81), diabetic neuropathy [ 16 ] (1.73, 95% CI: 1.14–2.64), congestive heart failure [ 18 ] (2.08, 95% CI: 1.26–3.42), and SU [ 55 ] (as compared to MET: 3.23, 95% CI: 3.01–3.45). Furthermore, Free triiodothyronine [ 32 ] (0.36, 95% CI: 0.20–0.64), SGLT2-i [ 56 ] (0.85, 95% CI: 0.82–0.88), and GLP-1RA [ 57 ] (0.82, 95% CI: 0.74–0.91) have demonstrated negative correlations.
3.3.6 Subgroup analysis.
Subgroup analysis was performed on five factors exhibiting high heterogeneity, excluding HDL-C and LDL-C due to the limited number of included articles. These factors comprised age, HbA1c, duration of T2DM, exercise, TC, and CHD. Age was categorized into three subgroups: >75 years old, 65–75 years old, and <65 years old ( Fig 3 ). The duration of T2DM was divided into two subgroups, with exclusion of “Ye 2016” [ 23 ] due to unclear reporting: >5 years and >10 years ( Fig 4 ). HbA1c was stratified into two subgroups: 7%-9% and >9% ( Fig 5 ). Sensitivity analyses were employed for subgroups exhibiting persistent high heterogeneity, and specifics are outlined in Table 3 .
https://doi.org/10.1371/journal.pone.0305954.g003
https://doi.org/10.1371/journal.pone.0305954.g004
https://doi.org/10.1371/journal.pone.0305954.g005
https://doi.org/10.1371/journal.pone.0305954.t003
3.3.7 Sensitivity analysis.
To evaluate the robustness of the association results, we performed a sensitivity analysis by iteratively removing one study at a time and recalculating the summary OR.(S1 Fig in S1 Appendix )
Among the influencing factors, the study by “Xu 2022” [ 15 ] exhibited notable impacts on hypertension-related heterogeneity. Upon its exclusion, the pooled OR was found to be 2.71 (2.41, 3.04), with a substantial reduction in heterogeneity (I 2 = 0%, p = 0.45). Similarly, concerning smoking, exclusion of the same study (“Xu 2022” [ 15 ]) resulted in a pooled OR of 1.65 (1.60, 1.69), accompanied by a significant decrease in heterogeneity (I 2 = 0%, p = 0.82). Furthermore, when considering eGFR, exclusion of the study by “Shi 2020” [ 19 ] led to a pooled OR of 2.15 (1.81, 2.55), along with a marked reduction in heterogeneity (I 2 = 0%, p = 0.55). Additionally, the study by “Chan(1) 2018” [ 51 ] affected heterogeneity in MET combination therapy; its exclusion notably decreased heterogeneity (I 2 = 0%, p = 0.48), yielding a pooled OR of 0.74 (0.66, 0.83).
In the sensitivity analysis, the study conducted by “Niwa 2019” [ 21 ] significantly impacted the heterogeneity related to Age 65–75 years. Upon its exclusion, the pooled OR was 1.74 (1.46, 2.08), accompanied by a substantial reduction in heterogeneity (I 2 = 0%, p = 0.54). Apart from these instances, no significant changes in pooled OR were observed for the other influencing factors, indicating the stability and reliability of our results.
3.3.8 Publication bias.
Egger’s test was utilized to assess publication bias within the study. Notably, the P-values obtained from Egger’s test were greater than 0.05 for all exposure variables, except for age (P = 0.000), albuminuria (P = 0.016), and age < 65 years (P = 0.020). These outcomes suggest the presence of publication bias specifically in relation to age, albuminuria, and age < 65 years. Further details regarding these findings are available in Table 2 and Table 3 .
4. Disscussion
4.1 discussion of the main results.
This study delved into a comprehensive exploration of stroke risk factors in patients with T2DM across sociodemographic factors, biochemical factors, complications, and hypoglycemic agent categories. Within these categories, 16 (76%) factors were identified as risk indicators, while 5 (24%) were identified as protective factors through meta-analyses.
Our investigation revealed that sociodemographic and biochemical factors have been extensively studied, among these factors, age emerged as a crucial factor influencing stroke risk in T2DM patients. Subgroup analysis revealed an increasing stroke risk with advancing age, consistent with prior research [ 58 ] indicating a higher stroke risk among elderly T2DM patients due to declining bodily functions and the prevalence of cardiovascular risk factors like hypertension and microvascular complications. The timing of T2DM diagnosis was inversely linked to cardiovascular risk [ 59 – 60 ], suggesting the need for heightened vigilance among patients diagnosed at younger ages. Gender-based differences in stroke risk presented conflicting findings. While certain studies [ 61 ] suggested a higher risk in women, others [ 62 ] indicated the opposite. These disparities might relate to cultural and racial variations among study populations. Additionally, hypertension was strongly associated with an increased risk of stroke in T2DM patients, aligning with previous research [ 60 ] attributing this to metabolic syndrome, insulin resistance, and related cardiovascular damage [ 63 ]. The duration of T2DM proved to be an independent risk factor for stroke [ 64 ]. Studies [ 5 ] highlighted a consistent increase in stroke risk with prolonged T2DM duration, the risk of stroke increased by 3% per year in patients with T2DM duration ≥10 years, potentially linked to exacerbated atherosclerosis and endothelial dysfunction. Smoking was identified as another contributor to heightened stroke risk in T2DM patients [ 65 ], with evidence supporting smoking cessation as a means of reducing this risk, and smoking cessation in patients with T2DM reduces the risk of ischemic stroke by 20% [ 66 ]. Moreover, BMI exhibited a linear relationship with cardiovascular disease risk, with every 5-unit BMI increase correlating with a 9% rise in cardiovascular risk [ 67 ]. This association was attributed to obesity-related dyslipidemia, promoting insulin resistance and fostering atherosclerosis [ 68 ]. However, other studies have pointed out that insulin resistance reduces the incidence and mortality of cardiovascular disease in obese patients. This self-contradictory conclusion suggests that the induction of insulin resistance may be a physiological adaptation process. Therefore, it is suggested that health care providers should pay more attention to daily nutrition management and physical exercise to reduce the risk of stroke in obese and dyslipidemia patients with T2DM, instead of relying on high doses of insulin and sulfonylurea medications [ 69 ]. In addition, higher levels of HbA1c correlated positively with increased stroke risk, especially among patients with HbA1c levels above 9% [ 70 – 71 ]. This underlines the importance of glycemic control in preventing stroke. Although the effect of intensive glycemic control on cardiovascular disease is still controversial, studies have shown that the reduction of HbA1c and the prolongation of intensive glycemic control may have a positive effect on cardiovascular disease [ 72 ].
An important finding of this study was that complications arising from T2DM were identified as the most robust indicators of stroke risk. Atherosclerosis, aggravated by T2DM, notably increased the risk of stroke, especially in patients with large artery atherosclerosis [ 5 ]. Microvascular complications such as DR, DN, and diabetic neuropathy emerged as significant predictors of future macrovascular diseases. And after adjusting for traditional risk factors, DR and DN are still independent predictors of stroke in patients with T2DM [ 73 – 74 ]. Additionally, AF was identified as a substantial risk factor for stroke in T2DM patients [ 75 ]. Macrovascular and microvascular complications of T2DM are the main causes of disability and death in patients. However, Due to the long duration of pre-diabetes in most patients, many patients have macrovascular and microvascular damage before the onset of overt diabetes occurs [ 61 , 76 ]. Therefore, for people with diabetes risk factors and genetic susceptibility, health care personnel should carefully assess their macrovascular and microvascular changes and guide them to follow a healthy lifestyle to prevent or timely detect macrovascular and microvascular complications. In addition, it is deemed essential for future articles to find new predictors such as biomarkers and related gene induction studies [ 77 ].
Another finding of this study was MET, Pioglitazone, and MET combination therapy were protective factors against stroke in T2DM patients. The cardiovascular protective effects of MET and pioglitazone have been confirmed in previous studies, but for patients with existing cardiovascular diseases, there is insufficient evidence to rely on monotherapy [ 76 ]. One research [ 78 ] have shown that MET combination therapy can better control blood glucose, while reducing the risk of late glycemic control failure, and did not increase hypoglycemic events. It appears that our findings differ because the included article in our study compared MET combination therapy with MET + SU, rather than directly contrasting it with MET monotherapy. Otherwise, the American Diabetes Association and the European Association for the Study of Diabetes [ 79 ] recommend SGLT2-i or GLP-1RA as hypoglycemic agents for patients at high risk of cardiovascular disease, and studies [ 11 ] have shown that SGLT2-i or GLP-1RA may reduce the risk of stroke in patients with T2DM. Nonetheless, given the limited number of articles included, there is not adequate evidence to conclusively support these findings. Consequently, there is a clear indication for additional large-scale prospective studies to validate and further substantiate these conclusions in the future.
In summary, stroke occurrence in T2DM patients is multifactorial, influenced by a spectrum of variables. Beyond conventional pharmacological approaches, the cultivation of enduring healthy habits, including adherence to a well-rounded nutritional regimen, cessation of smoking, and consistent engagement in physical exercise, stands as imperative in averting stroke incidents [ 79 ]. As personalized medicine advances, preventing strokes in T2DM necessitates a holistic approach, leveraging accurate personalized risk prediction models powered by algorithms. We anticipate this study to serve as a reference point for enhancing related risk prediction models. Significantly, our analysis solely scrutinized hypoglycemic agents. Hence, to devise a more comprehensive strategy for managing T2DM, there exists an urgent imperative to delve deeper into the interrelationships among diverse medications, including antihypertensive agents, lipid-lowering medications, antiplatelet therapies, and multifaceted drug regimens concerning stroke occurrences in individuals with T2DM. This holistic exploration would markedly enhance our comprehension and fortify therapeutic approaches aimed at addressing the complexities of managing T2DM complications, specifically in the context of reducing the peril associated with strokes.
4.2 Strengths and weaknesses
The strengths of our systematic review consist of the included articles are high-quality. Moreover, we specifically analyzed the complications and hypoglycemic medications of T2DM patients. This can offer a more comprehensive reference for the holistic management of stroke risk in T2DM patients. In addition, some potentially modifiable risk factors offers actionable insights into preventive strategies.
However, several limitations in this review merit acknowledgment. Firstly, observational studies inherently carry confounding factors. While we extracted multivariate adjusted OR, the likelihood of other unmeasured factors influencing the actual relationships cannot be dismissed. Secondly, although numerous factors were explored, the limited number of individual studies impedes a comprehensive elucidation of crucial factors contributing to the heterogeneity in research outcomes, such as regional disparities, racial influences, and sample sizes. Furthermore, the predominance of studies from Asian regions raises concerns about the generalizability and representativeness of the results. Moreover, not all articles included were prospective studies, which curtails establishing a definitive causal relationship between outcomes and variables. Hence, the results should be interpreted cautiously, considering these limitations.
5. Conclusion
This comprehensive review and meta-analysis identified several prominent risk factors associated with stroke in patients diagnosed with T2DM. Age, gender, T2DM duration, hypertension, dyslipidemia, smoking habits, elevated HbA1c levels, and various T2DM-related complications such as CHD, DR, AF, DN, PVD, and carotid plaque were all identified as significant risk factors. Conversely, exercise, HDL-C, and certain hypoglycemic agents demonstrated a protective effect against stroke in these patients. Healthcare practitioners can leverage these findings to develop targeted prevention strategies for individuals with T2DM. Beyond advocating for lifestyle improvements, proactive screening for both macrovascular and microvascular complications is crucial. Additionally, the judicious adjustment of hypoglycemic medications holds promise in mitigating stroke risk in this patient population.
Supporting information
S1 checklist. prisma checklist..
https://doi.org/10.1371/journal.pone.0305954.s001
S1 Appendix.
https://doi.org/10.1371/journal.pone.0305954.s002
Acknowledgments
We really appreciate the efforts of all the researchers whose articles were included in this study.
- View Article
- PubMed/NCBI
- Google Scholar
- 32. WU H M. Establishment and validation of a predictive model for acute ischemic stroke in elderly patients with type 2 diabetes mellitus [D]. GanSu: LanZhou University, 2022. https://doi.org/10.27204/d.cnki.glzhu.2022.000261 .
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
- My Bibliography
- Collections
- Citation manager
Save citation to file
Email citation, add to collections.
- Create a new collection
- Add to an existing collection
Add to My Bibliography
Your saved search, create a file for external citation management software, your rss feed.
- Search in PubMed
- Search in NLM Catalog
- Add to Search
Study designs: Part 7 - Systematic reviews
Affiliations.
- 1 Department of Anaesthesiology, Tata Memorial Centre, Homi Bhabha National Institute, Mumbai, Maharashtra, India.
- 2 Director, Jawaharlal Institute of Postgraduate Medical Education and Research, Puducherry, India.
- PMID: 32670836
- PMCID: PMC7342340
- DOI: 10.4103/picr.PICR_84_20
In this series on research study designs, we have so far looked at different types of primary research designs which attempt to answer a specific question. In this segment, we discuss systematic review, which is a study design used to summarize the results of several primary research studies. Systematic reviews often also use meta-analysis, which is a statistical tool to mathematically collate the results of various research studies to obtain a pooled estimate of treatment effect; this will be discussed in the next article.
Keywords: Research design; review [publication type]; systematic review [publication type].
Copyright: © 2020 Perspectives in Clinical Research.
PubMed Disclaimer
Conflict of interest statement
There are no conflicts of interest.
Similar articles
- Study designs: Part 8 - Meta-analysis (I). Ranganathan P, Aggarwal R. Ranganathan P, et al. Perspect Clin Res. 2020 Oct-Dec;11(4):178-181. doi: 10.4103/picr.PICR_283_20. Epub 2020 Oct 6. Perspect Clin Res. 2020. PMID: 33489837 Free PMC article.
- Systematic review finds that study data not published in full text articles have unclear impact on meta-analyses results in medical research. Schmucker CM, Blümle A, Schell LK, Schwarzer G, Oeller P, Cabrera L, von Elm E, Briel M, Meerpohl JJ; OPEN consortium. Schmucker CM, et al. PLoS One. 2017 Apr 25;12(4):e0176210. doi: 10.1371/journal.pone.0176210. eCollection 2017. PLoS One. 2017. PMID: 28441452 Free PMC article. Review.
- Conducting systematic reviews of intervention questions III: Synthesizing data from intervention studies using meta-analysis. O'Connor AM, Sargeant JM, Wang C. O'Connor AM, et al. Zoonoses Public Health. 2014 Jun;61 Suppl 1:52-63. doi: 10.1111/zph.12123. Zoonoses Public Health. 2014. PMID: 24905996
- Systematic reviews and their application to research in speech and language therapy: a response to T. R. Pring's 'Ask a silly question: two decades of troublesome trials' (2004). Garrett Z, Thomas J. Garrett Z, et al. Int J Lang Commun Disord. 2006 Jan-Feb;41(1):95-105. doi: 10.1080/13682820500071542. Int J Lang Commun Disord. 2006. PMID: 16272005 Review.
- The use of systematic reviews and meta-analyses in infection control and hospital epidemiology. Bent S, Shojania KG, Saint S. Bent S, et al. Am J Infect Control. 2004 Jun;32(4):246-54. doi: 10.1016/j.ajic.2003.10.004. Am J Infect Control. 2004. PMID: 15175624 Review.
- Study designs: Part 9 - Meta-analysis (II). Ranganathan P, Aggarwal R. Ranganathan P, et al. Perspect Clin Res. 2021 Jan-Mar;12(1):53-57. doi: 10.4103/picr.PICR_369_20. Epub 2021 Jan 19. Perspect Clin Res. 2021. PMID: 33816210 Free PMC article.
- Centre for Evidence Based Medicine. [Last accessed on 2020 Apr 01]. Available from: http://wwwcebmnet .
- Chandler J, Cumpston M, Thomas J, Higgins JP, Deeks JJ, Clarke MJ. Higgins JP, Thomas J, Chandler J, Cumpston M, Li T, Page MJ, et al., editors. Introduction. Cochrane Handbook for Systematic Reviews of Interventions Version 60 (updated August 2019) Ch 1 Cochrane. 2019. Available from: http://wwwtrainingcochraneorg/handbook .
- Impellizzeri FM, Bizzini M. Systematic review and meta-analysis: A primer. Int J Sports Phys Ther. 2012;7:493–503. - PMC - PubMed
- Akobeng AK. Understanding systematic reviews and meta-analysis. Arch Dis Child. 2005;90:845–8. - PMC - PubMed
- Safi S, Sethi NJ, Nielsen EE, Feinberg J, Jakobsen JC, Gluud C. Beta-blockers for suspected or diagnosed acute myocardial infarction. Cochrane Database Syst Rev. 2019;12:CD012484. - PMC - PubMed
LinkOut - more resources
Full text sources.
- Europe PubMed Central
- Ovid Technologies, Inc.
- PubMed Central
- Citation Manager
NCBI Literature Resources
MeSH PMC Bookshelf Disclaimer
The PubMed wordmark and PubMed logo are registered trademarks of the U.S. Department of Health and Human Services (HHS). Unauthorized use of these marks is strictly prohibited.
A Systematic Review of Personal Information Sharing in Smart Cities: Risks, Impacts, and Controls
- Open access
- Published: 24 June 2024
Cite this article
You have full access to this open access article

- Maha Ibrahim Alabsi ORCID: orcid.org/0000-0003-1791-6907 1 , 2 &
- Asif Qumar Gill ORCID: orcid.org/0000-0001-6239-6280 1
Smart cities aim to deliver smart services that rely on emerging technologies to their users. In order for users to get the provided services, they need to share their personal information with different parties. However, sharing personal information in smart cities may impact the privacy of that information. Thus, there is a need to address privacy risks relevant to sharing personal information in smart cities. This study aims to address this issue by conducting a systematic literature review (SLR) to identify and extract privacy risks, impacts, and existing controls associated with sharing personal information, considering elements involved and interacting during the sharing activity in smart cities. A set of 83 selected studies in both academic and industry fields were reviewed, and the results were categorised into three main groups: privacy risks, impacts, and controls. Moreover, the implications and future research directions were also reported. The proposed privacy risk taxonomy will provide a much-needed foundation for the industry and research community, intending to research and evaluate privacy risk frameworks and design solutions for sharing personal information in smart cities.
Avoid common mistakes on your manuscript.
Introduction
More recently, the concept of smart cities has been getting significant attention from research and practice perspectives (Ahmad Mohamad et al., 2019 ). Several countries across the globe (e.g. Asia, Africa, America, and Europe) aim to consider their cities “smart” by developing and delivering smart services to their citizens and residents by using emerging ICT (information and communication technologies) (Ahmad Mohamad et al., 2019 ; Albino et al., 2015 ; Hsiao et al., 2021 ). The definitions of smart cities focus on the quality of citizens’ performance and activities, along with enhancing economic competitiveness by managing city resources and improving information and communications technology (ICT) infrastructure (Giffinger et al., 2007 , Caragliu et al. 2009 , Vu & Hartley, 2018 ). Also, smart city is defined as a 4th industrial model where emerging technologies, such as the Internet of Things, cloud computing, and big data, are used to optimise the cities (Safiullin et al., 2019 ). Accordingly, smart cities are proposed in particular areas or sectors such as governments, health, energy, buildings, airports, and businesses/organisations (Khatoun & Zeadally, 2017 ).
Due to the strong relationship between ICT and smart services within the overarching concept of smart cities, a vast amount of personal information is collected from users, devices, and applications (Martinez-Balleste et al., 2013 ). Furthermore, sharing and exchanging information among parties, including individuals and organisations, is possible using different sharing platforms that play a vital role in smart cities (Kong et al., 2018 , Kusumastuti et al., 2022 ). Internet of Things (IoT), Cloud, fog computing, and blockchain technology are examples of such platforms (Qian et al., 2018 , Imine et al., 2020 ; Gill, 2021 ). However, the flow of personal information in smart cities may result in individuals suffering from serious privacy risks that may impact their information (Martinez-Balleste et al., 2013 , Sharma et al., 2020 ).
According to NIST (Stoneburner et al., 2002 ), the risk is the possibility of a threat source exploiting a specific information system vulnerability and the resultant consequence. Assessing information privacy risks in smart cities is challenging due to information complexity and uncertain impact levels (Bogoda et al., 2019 ). In addition, privacy risks need to be assessed to minimise the risk impact by using appropriate controls (Hong et al., 2004 ). Thus, there is a need to assess privacy risks when sharing personal information in smart cities. This includes identifying and addressing privacy threats and vulnerabilities, their impacts, and appropriate privacy risk mitigation controls.
To the best of our knowledge, there is a lack of consolidated literature on this important topic of privacy assessments that cover privacy risks, impacts, and current controls for sharing personal information, considering the interaction among elements involved in sharing activity in smart cities. A consolidated view of the current work is needed to provide a foundation for further development in this important area of research.
Thus, this paper addresses this need by conducting a SLR and synthesising published research with a view to identify and extract privacy risks, impacts, existing controls, and elements involved and interacting to share personal information in smart cities, along with relevant regulation, to influence this activity. Thus, this paper focuses on the following key research questions:
RQ1: What are the privacy risks associated with sharing personal information in the context of smart cities considering the elements involved and interacting while sharing personal information?
RQ2: What are the impacts of those personal information privacy risks?
RQ3: What current privacy controls are in place to mitigate the identified risks?
This work builds on the earlier research on identifying privacy risks in smart airports (Alabsi & Gill, 2021 ). This paper extended this work to provide broader coverage of smart cities. This will help extract and define more comprehensive views of privacy risks, which will be used to design a holistic solution for assessing the privacy risks that may impact passengers’ personal information in their interaction journey in smart airports within the border context of smart cities. This will ensure that important privacy concerns are not overlooked when dealing with information privacy in smart airports. The main motivation behind this paper is the future development of the privacy framework in a smart airport context. The development of the proposed framework is beyond this paper’s scope and is subject to further research.
Contribution
The key contributions of this research are outlined below:
This paper provides an updated knowledge base covering various articles published in academic and industrial databases between 2017 and 2021, including smart cities, sharing information, privacy risk, impact, and existing control.
This paper provides both a theoretical and practical view of the review results by using the Adaptive EA and Concerns for Information Privacy framework (CFIP) as a theoretical lens and the NIST 800–30 framework as a practical lens. These lenses help identify the risk assessment components: privacy risk, the resulting impact, and current privacy control.
This paper contributes to enhancing the understanding of the review results by proposing a privacy risk taxonomy using the Concerns for Information Privacy framework (CFIP) as a theoretical lens. Based on CFIP, the proposed taxonomy categorises threats and vulnerabilities into the following: collection, error, unauthorised use, and improper access types.
This paper provides novel knowledge by mapping the privacy risks associated with sharing personal information with elements involved and interacting during the sharing activity by adopting the Adaptive EA framework as a theoretical lens. The mapping links the privacy risks dimensions under CFIP with the layers of Adaptive EA, including human, technology, facility, and environmental.
This paper provides a set of actionable knowledge by providing a clear understanding and mapping of the identified privacy threats to the requirements and available existing controls.
This paper provides future research directions regarding the privacy risks of sharing personal information in smart cities.
In a nutshell, this research provides a knowledge foundation, which can be casted into developing theoretical and practical frameworks and solutions for studying and enhancing personal information privacy in the contemporary context of smart cities.
This paper is organised as follows: the “Background and Related Work” section provides the research background and related works. The “Research Method” section explains the research method. Then, data extraction and synthesis are discussed in the “Data Extraction and Synthesis” section, followed by the SLR results in the “ Results ” section. The discussion of implications, study validity and limitations, and work directions is elaborated in the "Discussion" section. The last section encompasses the conclusion.
Background and Related Work
The meaning of privacy varies from one researcher to another. However, core components are common to most definitions of privacy. The most historical definition of privacy was “the right to be let alone” (Warren & Brandeis, 1890 ). Information privacy is defined as the relationship between an individual’s right to privacy and the ability to access and control the information held by organisations (Cranor, 2012 ; Hoffman, 1977 ; Hough, 2009 ; Martinez-Balleste et al., 2013 ). At present, many definitions of privacy have been proposed, and through the years, these definitions have evolved based on societal changes and technological development (Hiller & Russell, 2017 ; Li & Palanisamy, 2018 ; Peppet, 2014 ).
The smart city context has recently risen, and technology has gradually developed. A smart city is identified as an urban area that uses information and communication technology (ICT) to improve its services and enhance its residents’ quality of life (Giffinger et al., 2007 ; Kusumastuti et al., 2022 ). As a result, the individual shares their personal information with service providers, who share it with other organisations either explicitly—implying that the user is involved—or implicitly without the user’s knowledge (Spiekermann & Cranor, 2008 ). Personal information can be used to identify an individual, either directly or indirectly, such as name, email, or biometric information email (Wolford, 2020 ).
Accordingly, information privacy and security concerns have been significantly increased because cities are digitally connected, and individuals’ personal information has become more accessible and available (Hiller & Russell, 2017 ; Solove, 2011 ). This sometimes obstructs society’s adoption of smart cities (Pal et al., 2021 ). For that, personal information privacy risks that arise when sharing personal information in smart cities should be considered carefully to seize new threats and find reasonable solutions. This section briefs privacy risks, regulations, and privacy-enhancing technologies.
Privacy Risks
Privacy risk is defined as the expected losses related to personal information disclosure (Xu et al., 2011 ). Pervasive literature attempts to identify the privacy risks of personal information. For example, Nissenbaum ( 2004 ) proposed a privacy taxonomy based on the contextual integrity (CI) theory, which considers human factors, including their norms and attitudes, as part of privacy risk arising in public surveillance. Henriksen-Bulmer et al. ( 2019 )proposed a taxonomy using the same theoretical lens, IC, to address privacy risks in open data publishing. The privacy taxonomy developed by Solove ( 2006 ) aimed to improve the understanding of information privacy in the legal system. This taxonomy classified privacy risk into four elements: collection, processing, dissemination, and invasion (Solove, 2006 ). Avancha et al. ( 2012 ) developed a privacy taxonomy that classified privacy threats into identity threats, access threats, and disclosure threats in the health system. The framework designed by Deng et al. ( 2011 ) provides a comprehensive analysis of privacy threats to help analysts cover key issues in designing software. In the smart airport, unauthorised access, information leakage, and second use were discussed as privacy threats that affect passenger information (Choudhury & Rabbani, 2019 ; Khi, 2020 ; Tedeschi & Sciancalepore, 2019 ; Zhang, 2019 ). The review conducted by Ismagilova et al. ( 2020 ) focused on security, privacy, and risk in smart cities and how they impact the operational process of smart cities. In addition, a systematic literature review is conducted to identify privacy risks and current solutions relevant to passengers’ information (Alabsi & Gill, 2021 ). In this work, the privacy risks were classified based on the CFIP theory into four types: collection, error, unauthorised use, and improper access.
This review of the literature shows that despite attempts to analyse privacy risks, they only focused on addressing threats without considering vulnerabilities as an essential factor in privacy risk analysis. Furthermore, there is a lack of addressing privacy risks relevant to personal information in other smart city themes, such as smart airport.
Privacy Regulations
The General Data Protection Regulation (GDPR) is a significant regulation that regulates information privacy. The EU adopted the GDPR in 2018 and incorporated principles for personal information processing (Wolford, 2020 ). The GDPR explains principles that help in protecting individual privacy (EUGDPR, 2018 ). Consent, breach announcement, and privacy by design are examples of GDPR principles (EUGDPR, 2018 ).
In the USA, the Fair Information Practices (FIPs) regulation was developed in 1973 to discuss the importance of protecting individual privacy, and it was adopted by the U.S. Privacy Act (Gellman, 2017 ; Li & Palanisamy, 2018 ). Following that time, different sectors in the USA, such as the health and business sectors, developed their privacy regulations called the Health Insurance Portability and Accountability Act (HIPAA) (Silva et al., 2021 ).
In Australia, the Privacy Act 1988 (Act) developed the Australian Privacy Principles (APPs) to protect and guide the use of personal information (Office of the Australian Information Commissioner n.d. ). The APPs consist of principles governing the collection, handling, accessing of personal information, and ensuring the accuracy and integrity of personal information (Office of the Australian Information Commissioner n.d. ).
Based on the above review, it is clear that countries share a common objective in protecting the privacy of personal information and governing how to use it despite their differing regulations.
Privacy-Enhancing Technologies
The interest in privacy protection has been increasing since the 1990s. Thus, there has been a continuous flux of efforts to develop and use Privacy-Enhancing Technologies (PETs) (Hiller & Blanke, 2016 ). PETs are well-designed (ICT) systems for securing and protecting the privacy of information through the reduction, deletion, or avoidance of improper and unnecessary processing of personal data without decreasing the value of the individual information (Chun, 2015 ). The goal of using PET in smart cities is to enable the personal and sensitive information embedded in the collected data to be hidden and not be discovered by any third party or service provider (Curzon et al., 2019 ). Recently, many PETs have been proposed to protect the privacy of information. For example, Van Blarkom et al. ( 2003 ) described PETs techniques such as encryption, anonymisation, pseud-identity, biometric, identification, authorisation, and authentication. Heurix et al. ( 2015 ) provided PETs taxonomy that covered privacy aspects such as user privacy and data privacy across domains not covered in security classifications. Curzon et al. ( 2019 ) provided a detailed review of privacy-enhancing technologies, commonly classified as anonymisation (such as masking and disruption of sensitive data) and security techniques (such as hashing and cryptographic techniques), as the broad types of techniques used mostly for personal information privacy protection. The PETs classification proposed by Kang et al. ( 2007 ) includes three types based on the privacy information life-cycle, including operation technology, common-based technology, and administrative technologies.
It is clear from previous and related research that the study of privacy-enhancing technology has been actively addressed, reflecting its importance in protecting the privacy of personal information.
In summary, protecting the privacy of personal information in smart cities is critical for its effective adoption by citizens or users. Studies have attempted to cover this topic by investigating many solutions and approaches. However, lack of systematic reviews effectively address and assess privacy risks, including threats, vulnerabilities, impacts, and exciting controls relevant to sharing personal information in smart cities, considering who and what is involved and interacted during the sharing activity. This study aims to address this critical need by employing the well-known SLR approach detailed in the following section.
Research Method
This section presents the SLR method applied to conduct this systematic literature review (Kitchenham & Charters, 2007 ). This section includes the following SLR stages: (A) study inclusion and exclusion criteria, (B) data sources and search strategies, (C) study selection process, and (D) quality assessment.
Study Inclusion and Exclusion Criteria
In this study, a set of inclusion and exclusion criteria based on the research questions was used to select the relevant studies from well-known academic and industrial sources. It is important to note here that industry sources have been used to complement the academic sources. Academic studies must be peer-reviewed, including journal articles, conference papers, and book chapters. The studies must satisfy the following criteria: written in the English language, published between 2017 and 2021, include the specified search terms (see Table 1 ), and provide information to address the research questions listed in “ Introduction ” section. Studies that did not meet the inclusion criteria were excluded. This ensures that recent literature relevant to the scope of this study has been adequately covered.
Data Source and Search Strategy
The following well-known electronic databases were used to answer the identified research questions: IEEE Xplore ( www.ieexplore.ieee.org/Xplore/ ), ScienceDirect ( www.sciencedirect.com ), ProQuest( www.proquest.com ), Willy (onlinelibrary.wiley.com/), Gartner ( www.gartner.com/ ).
The selected databases collectively cover a wide range of disciplines relevant to the topic at hand. Furthermore, this SLR includes academic and industrial studies, which distinguishes it from traditional SLR. However, the industrial sources were analysed separately to avoid mixing the non-peer-reviewed studies with academic sources. In the initial research stage, we used the selected search categories and terms presented in Table 1 to find the relevant studies that address the identified research questions. Each search term in the “privacy-preserving” category was combined with each term under the “information sharing” and “smart cities” categories with the operator “AND”. Furthermore, the operator “OR” is used to combine similar terms in each category to ensure maximum coverage.
Study Selection Process
The study selection process assesses the inclusion and exclusion criteria through the following stages. In stage 1, all identified search terms and keywords (see Table 1 ) were searched in the selected databases (as explained earlier), and studies not relevant to inclusion and exclusion criteria were excluded. This stage resulted in 1089 industrial and academic studies. In stage 2, a set of 372 industrial and academic studies were selected after the titles and keywords assessment. In stage 3, further assessments were conducted for the abstract and conclusion, and 127 from both academic and industrial sources were included. A full-text assessment was applied in the final stage to obtain the final set of 83 studies. Further, the quality assessment has been performed on the final selected studies based on pre-identified assessment criteria (Table 3 ) (Kitchenham & Charters, 2007 ). The relevant studies from each stage were stored and managed using EndNote and then exported to Excel sheets to recode inclusion/exclusion decisions. A flowchart of the study selection process, including stages and the number of included studies in each stage, is shown in Fig. 1 . Table 2 also presents the number of selected studies from each selected database in each stage.

Selection process stages and number of included studies
Quality Assessment
The quality assessment was performed based on the checklist made by Kitchenham and Charters ( 2007 ) to ensure the quality of this SLR. The quality assessment criteria items are presented in Table 3 .
The questions of quality criteria were applied to identify the study’s context, aim, and credibility. The selected studies were scored between 1 and 5 based on criteria items. The total score of the study reflects its quality. Each criterion got a score of “1” or “0”. The selected studies from academic sources scored 1 in the research column. Four selected studies scored “0” in the aim column due to a lack of clarity about the study’s aim, while a set of 3 selected studies scored “0” in the column of context because they did not include clear research context details. The majority of studies scored “1” in the finding column. A set of 12 selected studies scored “0” in the future column because of the lack of clarity about the future research directions. To sum up, as indicated in the last column of Table 4 , the quality of selected studies is considered acceptable if the score is 3 or more out of 5 (60% or above).
Data Extraction and Synthesis
We systematically analysed and synthesised the selected studies using the Adaptive Enterprise Architecture (AEA) and Concerns for Information Privacy framework (CFIP) as a theoretical lens, besides the NIST 800–30 framework as a practical lens. We used the CFIP because it helps extract the privacy risk elements (threats and vulnerability) of sharing personal information, which was configured into a proposed privacy risk taxonomy (Fig. 2 ). Our proposed taxonomy consists of four categories based on CFIP: collection, error, unauthorised use, and improper access. CFIP seems to be an appropriate lens (Smith et al., 1996 ) to assess and analyse individual concerns regarding the privacy of organisational information practices. It is a multidimensional framework used as one of the most reliable tools for addressing individual information privacy concerns in many areas, such as e-commerce (Van Slyke et al., 2006 ). The extracted privacy risks under CFIP dimensions are mapped with the AEA framework’s human, technology, facility, and environmental layers (Fig. 3 ). We also used Adaptive EA because it provides systematic layers to extract and map elements involved and interact while sharing personal information, besides relevant regulation as a governmental element that influences this activity. It is important to note here that sharing activity is considered the main element under the interaction layer. Adaptive EA (Gill, 2015 ) is a framework that guides the interaction in the digital ecosystems among five main layers: human, technology, facility, environment, and security. Further, we used NIST SP 800–30, the well-known standard, as a practical lens to identify and extract essential elements to assess privacy risks (Stoneburner et al. 2002 ). NIST was used to complement the theoretical lenses used in this study.

Proposed privacy risk taxonomy based on CFIP framework

Mapping CFIP with Adaptive EA
This was done to ensure that important points from practice were not overlooked. Thus, this study provides rich information incorporating both theoretical and practical perspectives. These elements include privacy threats, vulnerabilities, requirements, and privacy controls (see Fig. 4 ). The identified privacy controls include technical and non-technical controls (Fig. 4 ). The NIST 800–30 is used to carry out risk assessments according to the NIST guidelines (Peacock, 2021 ). The dimensions of CIFP cover different types of privacy risk components (threats and vulnerabilities) related to sharing personal information. Further, NIST 800–30 also offers a structured process that is used to assess privacy risks. Thus, we use CFIP and NIST 800–30 to report the results of this study, which are presented in the following section.

Assessing information privacy risk based on NIST 800–30
To answer the indicated research questions, we analysed the final selected papers in Table 14 in the Appendix. We reviewed and analysed the selected studies using CFIP and NIST 800–30 frameworks to address the research questions to identify privacy risks (privacy threats, vulnerability), privacy risk impacts, and existing privacy controls. It is worth mentioning that the majority of the papers (86%) were taken from academic sources, whereas only 14% of selected studies were found relevant from the well-known industry Gartner data.
It is widely accepted that information risk is composed of threats and relevant vulnerabilities that may impact information assets (Norta et al., 2019 ). In this context, privacy controls are placed to mitigate the risk.
To answer RQ1, we use the CFIP and Adaptive EA as theoretical lenses. Firstly, we identify and categorise the privacy risk components, including privacy threats and vulnerabilities, related to the privacy risk of sharing personal information in smart cities by adopting the CFIP framework dimensions: collection, error, unauthorised use, and improper access (Smith et al., 1996 ). Then, we mapped the identified risks with the layers of Adaptive EA to present the elements involved and interacted in sharing personal information associated with the identified risks and relevant regulation as a governmental element that influences this sharing activity. Adaptive EA consists of the following layers: human, technology, facility, and environmental (Gill, 2015 ).
Privacy Threats
NIST defines threats as undesired and potential harm to the organisational assets such as information, operation and service, or individuals (National Institute of Standards and Technology 2013 ). We reviewed the selected studies to identify privacy threats that affect the sharing of personal information in smart cities in general and several smart city sectors such as smart healthcare, smart grid, smart governments, smart business/organisation, and smart transportation. Based on the CFIP framework, we identified seven types of privacy threats: collection, unauthorised use, improper access, and error from 41% of selected studies. Table 5 presents the identified threats, categories, and selected studies.
As shown in Table 5 , the majority of selected studies (31%) discussed privacy threats under the unauthorised use category. This category includes the following threats: secondary use (T2), information modification (T3), information leakage (T4), and identity theft (T5). Seventeen percent of the reviewed studies highlighted unauthorised access (T1) as a privacy threat under the improper access category. The remaining studies discussed policy and regulation non-compliance privacy threat (T7) under the collection category (6%), with a few studies (2%) focused on information misuse (T6) privacy threats under the error category (3).
As shown in Table 5 , the privacy threats related to patient information sharing in smart health have been widely discussed in the reviewed studies (N3, S4, S5, S6, S7, S8, S12, S17, S3, S27). For example, unauthorised access (T1), information misuse (T6), and modification (T3) threats have been identified as the most common threats that affect the privacy of patient information (Iwaya et al., 2019 ). Patient biometric data are collected and shared with many parties in the smart health sector, which leads to secondary use (T2) and ID theft (T5) threats (Romanou, 2018 ). Regulators and ethics committees are relevant to the health sector classified information leakage (T4) as a privacy threat that affects the collection, use, and sharing of personal information in smart health (Thapa & Camtepe, 2020 ).
As for smart grid, reviewed studies (S9, S16, S18, S19) highlighted that threats included information modification (T3), information leaking (T4), and unauthorised access (T1) are the most common threats that impact consumers’ privacy information shared with different parties. On the other hand, unauthorised access (T1), secondary use (T2), and information leakage (T4) are discussed in the reviewed studies (S11, S20, S21, S13, S10, S22, N2, N5) as privacy threats that affect personal information sharing in smart cities.
As shown in Table 5 , 6 % of reviewed studies identified non-compliance with privacy policies and regulations (T7) as a privacy threat. Several countries and organisations have taken considerable steps toward data privacy policies and regulations in order to protect personal information. According to Wall et al. ( 2015 ), privacy compliance refers to an organisation’s adherence to regulatory privacy requirements to protect personal information. Studies have discussed the increasing information privacy issues in organisations due to non-compliance with privacy policies and regulations in different sectors, including smart cities. For example, healthcare industries handle patients’ information in the USA without explicit patient consent, which is at odds with granular consent under the Health Insurance Portability and Accountability Act (HIPAA) (Runyon, 2020 ).
Vulnerability
According to NIST (National Institute of Standards and Technology 2013 ), vulnerability is the weakness of an asset (e.g. information and system) plausibly exploited by threats. This section reviewed the selected studies based on this definition to extract the perceived vulnerabilities that identified threats might exploit.
As shown in Table 6 , we identified three types of vulnerabilities relevant to the identified threats. Based on our review, 5% of selected studies mentioned that lack and un-transparent policies lead to several privacy threats (Chua et al., 2017 ; Hou et al., 2018 ; Taplin, 2021 ). Examples of these policies include consent, ethics, and privacy policies. Furthermore, the lack of privacy regulation related to handling and sharing personal information, including biometric data, could make this information vulnerable to several privacy threats (S30) (Khi, 2020 ). Insecure/unprotected storage systems and insecure/unprotected sharing mechanisms were identified as vulnerabilities in 3% of selected studies. Insecure storage refers to storing sensitive data without appropriately controlling access. Sharing information in unsecured or unprotected environments leads to privacy risks in smart cities (Agrawal et al., 2021 ; Romanou, 2018 ).
Mapping CFIP Dimensions with Adaptive EA Layers
Our review focused on the threats that affect personal information shared in smart cities in general and different smart city sectors such as smart health, smart grid, smart government, and smart business/organisation. Furthermore, we considered who and what are involved and interacted in the sharing activity, besides relevant regulation as a governmental element that influences this activity (based on Adaptive EA). Tables 7 , 8 , 9 , 10 , and 11 present the elements relevant to Adaptive EA layers: human, technology, facility, and environment, in smart cities. Figures 5 , 6 , 7 , and 8 represent the map of CFIP dimensions with Adaptive EA layers.
As illustrated in Fig. 5 , in the smart health context, elements under human layers are identified from 11% of selected studies that discussed the unauthorised use privacy risk associated with sharing patients’ information in smart health. In contrast, with improper access and error risks, the studies’ percentages dropped to 7% and 1%. On the other hand, elements under technology layers are discussed in 6% of selected studies that investigated improper access and unauthorised use privacy risks, with 0% of studies in error and collection risks. However, the environmental layer is considered in selected studies (4%) when addressing privacy risks categorised under unauthorised use more than in improper access (1%) and collection dimensions (2%). We identified patients, service providers, and doctors as the main actors under human layers from 13% of selected studies. At the same time, infrastructure such as IoT and data storage, such as centralised databases, are identified under technology layers in 11% of selected studies. Facility layers are discussed in 6% of selected studies. The facility layer presents different smart health buildings, such as hospitals, medical centres, laboratories, and clinics. Privacy regulations are mainly discussed under the environmental layer in 6% of selected studies, which can be used to define or inform a separate layer of privacy. This seems to suggest the extension of the Adaptive EA framework through the introduction of the privacy layer. Table 7 presents elements under each layer of Adaptive AE in smart health context.

Mapping CFIP dimensions with AEA layers in smart health
In the smart grid, Fig. 6 shows that more selected studies mentioned human, technology, and facility layers when addressing improper access and unauthorised use privacy risks associated with sharing users’ information, while no studies discussed theses layers with error and collection privacy risks.

Mapping CFIP dimensions with AEA layers in the smart grid
In Table 8 , 4% of selected studies identified different actors under the human layer in the smart grid context, including users and customer service providers. Based on our review, 6% of selected studies discuss the usage of the cloud as the main data storage in the smart grid, while IoT applications and smart metres are the main infrastructures discussed in the smart grid system. Elements under facilities layers are found in 6% of selected studies that discuss privacy risks associated with sharing personal information in the smart grid. Examples of facility layer elements are control centres, power sources, and home gateways.
As presented in Fig. 7 , almost a few percent of studies only mentioned human and technology layers with improper access risk compared with studies that addressed unauthorised use privacy risks associated with sharing users’ information in the smart city context.

Mapping CFIP dimensions with AEA layers in smart city
Based on Table 9 , from 5% of selected studies, we identified two main actors under human layers who are involved in sharing personal information in smart cities. The main actors include individuals, such as citizens and users, and organisations, including service providers and data holders. Moreover, IoT devices, Cloud systems, and smart city applications are identified in 6% of selected studies as elements under technology layers used in sharing personal information in smart cities.
As illustrated in Fig. 8 , most selected studies in the smart business/organisation context explain elements in human, technology, and facilities layers when addressing unauthorised privacy risks associated with sharing personal information, whereas this percentage decreased with improper access privacy risk. On the other hand, the environmental layer is mentioned in 2% of studies that addressed privacy risks under improper access and unauthorised risks, with 1% with collection privacy risks.

Mapping CFIP dimensions with AEA layers in smart business/organisation
Based on Table 10 , we identified several actors, such as employees, customers, and experts, under the human layer from 4% of selected studies. The facility layer includes buildings, such as organisations, public workplaces, and industry, discussed in 7%. On the other hand, technical layer elements, such as infrastructure and data storage, and environmental elements, such as privacy regulation, are discussed in 5% of selected studies.
As shown in Table 11 , human, technology, and facility layers have been mentioned in 2% of selected studies that discussed improper access and unauthorised use privacy risks in smart government, with 1% of studies addressing unauthorised use in the smart transportation context.
Privacy Risks Impacts
To answer RQ2, we reviewed the selected studies to identify and extract privacy requirements impacted by the identified privacy risks. The proper privacy requirements should be considered when personal information is shared in smart cities. Thus, we reviewed the selected studies to extract the privacy requirements that the identified threats might impact (Table 12 maps the requirements with relevant threats). As shown in Table 12 , we identified eight classified requirements. The classifications include the CIA triad (confidentiality, integrity, availability) and IAAA (identification, authentication, authorization, accounting). In addition, we extracted the privacy requirements based on the classification proposed by Pfitzmann and Hansen ( 2010 ), which is very common in the privacy domain. The classification consists of anonymity and pseudonymity, unlinkability, undetectability, and unobservability. Table 12 includes a list of privacy requirements that need to be satisfied when sharing personal information in smart cities.
Concerning the CIA classification, 20% of selected studies discussed confidentiality and integrity as essential requirements to achieve privacy (Table 12 ). In contrast, availability is discussed in 10% of selected studies to achieve security besides privacy. In smart health, Health Information Exchange (HIE) has been adopted to enable the electronic sharing of patient information between several parties (Mutanu et al., 2022 ). Thus, confidentiality, integrity, and availability are essential to preserve patient information privacy and security (Yi et al., 2013 ). In addition, the CIA triad should be satisfied with a smart grid and smart transportation to protect privacy as the information is shared between relevant parties to provide various services to the users (Yang et al. 2014 ).
As for the IAAA classification, 13% of selected studies discussed authentication as a requirement for privacy (Table 12 ). However, authorization was discussed in 5% of selected studies, whereas identification was discussed in 2% of selected studies. In the smart grid, identification and authentication requirements need to be satisfied to secure access to the information or system component (Ferrag et al., 2018 ; Sadhukhan et al., 2021 ). In smart health, authentication, authorization, and identification requirements should be satisfied when sharing patient information to ensure that privacy is not compromised (Shamshad et al., 2020 ; Wang et al., 2019 ).
We reviewed the selected studies to extract the requirements classified based on the terminology proposed by Pfitzmann and Hansen ( 2010 ). As shown in Table 12 , 12% of selected studies discussed anonymity as an essential requirement to ensure the privacy of information, whereas only 1% mentioned unlinkability requirements. These requirements are addressed in both smart health and smart transportation to achieve the privacy of personal information (Yang et al., 2018 , Chenthara et al., 2019 ).
Existing Privacy Control
To answer the RQ3, we reviewed the privacy-preserving schemes for sharing personal information in smart cities. We also extracted the existing privacy controls proposed to mitigate the identified risks from the selected studies (Table 13 maps the privacy controls with identified threats). Further, we classified the identified control under technical and non-technical, as shown in Table 13 . Figure 9 represents the percentage of the identified privacy controls from the selected studies. Technical control methods include security-based solutions, such as encryption, access control, etc., whereas non-technical methods refer to policies, procedures and standards (National Institute of Standards and Technology, 2013 ).

Existing privacy control
Considering the technical solution, we identified ten technical controls categorised into four groups: anonymisation, cryptographic techniques, access control techniques, blockchain, and machine learning (Table 13 ). In this study, the classification of technical solutions is based on the classification of PETs proposed by Van Blarkom et al. ( 2003 ) and Curzon et al. ( 2019 ). In addition, we reviewed technical controls developed on blockchain and machine learning.
Data Anonymization
As sown in Table 13 , 7% of reviewed studies discussed anonymization techniques as technical privacy controls. This includes K-anonymity, differential privacy, and pseudonym. Data anonymization is the method used to protect personal information by preventing linking their identities (Curzon et al., 2019 ; Iyengar, 2002 ; Silva et al., 2021 ). K-anonymity and differential privacy are the most common methods of anonymization technique (Iyengar, 2002 ). As for smart health, the reviewed study (S12) discussed the popularity of using anonymity to preserve the privacy of transmitted personal information between parties. On the other hand, the pseudonym is discussed in (S49) as an anonymous technique that is proposed to preserve the privacy of sharing information in smart transportation.
Cryptographic Technique
Table 13 includes cryptographic techniques used in privacy-preserving schemes for sharing personal information in smart cities. The techniques were extracted from 8% of selected studies. Cryptographic technology entails ways of totally hiding data equivalent to the intensity of the cryptographic key and algorithm employed. Encrypting transmitted or stored personal information in smart cities is a broadly used technology that protects from leakage and achieves privacy requirements (Curzon et al., 2019 ; Gaire et al., 2019 ). For example, attribute-based encryption (ABE) is proposed to preserve patient information sharing in smart health (S7, S57). Cryptographic technique for processing biometric data is presented in (S12); in this method, the digital key is securely linked by a biometric sample that is used to encrypt and decrypt the key. Elliptic curve cryptography to secure and authenticate the communication between the consumer and the service provider in the smart grid is discussed in (S36, S28).
Access Control Mechanism
Access control is defined as security methods to control the access and use of information by applying access policies (Sandhu & Samarati, 1994 ). In Table 13 , 6% of reviewed studies discussed privacy-preserving schemes developed based on the access control mechanism. For example, schemes presented in selected studies proposed several access control mechanisms, such as fine-grained access control and multi-layer access control (MLAC), to preserve the privacy of patient information shared between different parties in a cloud-based environment.
Machine Learning
Table 13 shows that privacy-preserving schemes for sharing information in smart cities using machine learning techniques are discussed in 2% of selected studies. A self-organising map (SOM) is a machine learning technique used to share information about electricity usage between parties in the smart grid (S65). The machine learning technique, federated learning, is used to share and analyse medical cases in smart health without compromising patient privacy (S58).
As shown in Table 13 , 42% of selected studies proposed privacy-preserving schemes for sharing information using Blockchain technology. Blockchain is a decentralized cryptographic scheme employed to privatise and safeguard transactions in the confines of a network (Curzon et al., 2019 ). It has been noticed that the privacy-preserving schemes in selected studies integrated blockchain with other PETs to share personal information without compromising their privacy. For example, access control mechanisms and blockchain are proposed in studies (S4, S6, S20, S41, S48, S50, S6, S8, S26, S27, S33, S34) mainly for two purposes. The first one is to allow individuals to monitor and regulate their information sharing between parties in smart cities. The second purpose is to authenticate the identity while sharing and accessing the information in smart cities. The selected studies (S9, S39, S14, S63, S21, S45, S31) proposed privacy-preserving schemes that use several cryptographic techniques, including signature, identity-based proxy, proxy re-encryption, zero-knowledge, and attribute-based encryption, with blockchain to protect the privacy of individual information in smart grid and smart health.
Non-technical Control
Among the selected studies, a total of 35% discussed non-technical privacy control to mitigate the identified threats (Table 13 ). For example, the importance of privacy by design (PbD) as a principle of GDPR is discussed in an attempt to protect the privacy of personal information in smart health and biometric applications (S12). Several policy-based schemes are discussed to capture the imposed requirements and restrictions that enhance the privacy of shared information in smart cities (S5, S66). On the other hand, privacy management is discussed in the selected studies as a type of non-technical privacy controls (S42, S13, S68, S67). As shown in Table 13 , the non-technical privacy controls are discussed widely in the industrial reports (N1, N6, N7, N8, N9, N10, N11, N12, N4). Organisations need to reduce information disclosure as it leads to privacy and financial risks (Brian Lowans & Meunier, 2019 ). Effective privacy management programs should address privacy risk prevention and incorporate privacy-by-design principles into all business activities (Bart Willemsen, 2017 ). In this context, many risk management approaches, such as integrated risk management (IRM), data security governance (DSG) framework, privacy impact assessment(PIA), and continuous adaptive risk and trust assessment (CARTA), are discussed to help businesses dealing with risks and their consequences and also to ensure the sustainability of the protection of any project (N6, N7, N1, N11). Furthermore, the importance of designing a privacy-aware risk programme to define and assess the risk of using blockchain technology for sharing personal information is discussed in industry publications (N8, N9).
This research provided a consolidated view of the selected studies from academic and industrial sources and reported on the privacy risks, impacts, and controls related to personal information sharing in smart cities. This was done to thoroughly identify the privacy risks that affect the sharing of personal information in smart cities. Since sharing personal information in smart cities results from the interaction among different elements, this study also aims to identify these elements, including actors, technologies, facilities, and privacy laws, that are involved in sharing activity. Identifying privacy risks, including threats and vulnerabilities, the risk impacts, and existing controls, taking into account the elements involved in sharing activity, will assist organisations in determining the appropriate controls to mitigate the risks when sharing personal information in smart cities. This section describes the implications based on our review and analysis of selected studies. It also includes the limitations of this work.
Implications
Privacy risk.
Many studies have proposed threat taxonomies that organise threats into different categories (Deng et al., 2011 ; Xiong & Lagerström, 2019 ). However, to the best of our knowledge, there is a lack of systematic and theoretical understanding, which is filled by this study using the CFIP as a theoretical lens. This study proposed a taxonomy of privacy risks of sharing personal information in smart cities, including threats and vulnerabilities, based on the CFIP theoretical lens. Based on Table 5 , our findings show that the selected studies do not properly investigate policies and consent non-compliance, misuse, and ID theft as serious threats that widely affect the privacy of sharing personal information in smart cities. Furthermore, we found that selected studies did not clearly distinguish between threats’ events and their sources, making it hard to identify the relevant privacy threats to the scope of this study. Thus, there is still a great deal of work to be done in this area in both academic and industrial research.
On the other hand, based on Table 5 , we found that most selected studies discussed privacy threats associated with sharing personal information in smart cities in general and in the smart health system. In contrast, studies that discussed the same topic under the smart grid, smart government, smart business, and smart transportation systems were limited. One immediate impact of this finding on the digital economy is the reinforcement of the importance of investing in robust technological solutions and infrastructures, as well as developing risk management frameworks to mitigate the privacy and security risks associated with personal information in smart cities (Ahmed, 2021 , Jnr et al., 2023 , Jin, 2024 ).
The digital economy is the deep integration of digital technology and production factors in smart cities to manage the transformation cost, improve cities’ capabilities and implement innovative solutions (Sotirelis et al., 2022 ; Vinod Kumar & Dahiya, 2017 ; Wang et al., 2021 ; Zhiyong et al., 2024 ).
The emphasis on privacy risks of sharing personal information in smart cities highlights the need for innovative solutions that simultaneously advance their capabilities while rigorously safeguarding individual privacy. This could increase investment in implementing privacy controls to protect individual information handled within smart city sectors (Jin, 2024 ).
As smart city sectors heavily rely on sharing individual information by integrating smart technologies, there is a pressing need to address privacy risks associated with personnel. This could spur investment in privacy-enhancing technologies, regulatory frameworks, and public awareness campaigns tailored to these specific domains. This draws our attention to the need for more studies in order to cover this gap.
On the other hand, selected studies from industry sources discussed the identified privacy threats relevant to personal information without mentioning their relationship with smart cities or any other smart system.
On the other hand, it is well-accepted that any risk analysis should be done based on identified threats and relevant vulnerabilities (Stoneburner et al. 2002 , Norta et al., 2019 ). The identification of vulnerabilities is an essential factor that plays a role in identifying privacy risks. Based on Table 6 , we found that selected studies do not investigate vulnerabilities as a significant factor in addressing privacy risks relevant to sharing personal information in smart cities. As a result, the knowledge about the identified privacy risks was limited. Thus, there is a need to understand the threats and vulnerabilities to identify and mitigate privacy risks.
Based on our review, very limited studies currently explain who and what elements are involved when addressing privacy risks associated with sharing personal information in smart cities. Furthermore, to the best of our knowledge, no previous studies have demonstrated the interaction among the elements involved when addressing the topic mentioned above. To overcome the shortcomings of previous studies outlined above, we adopted Adaptive EA as a theoretical lens to map the identified privacy risks relevant to sharing personal information in smart cities, with elements involved and interacting in sharing activity. This study mapped the identified privacy risks based on CFIP dimensions, including improper access, unauthorised use, error, and collection, with Adaptive EA layers that include human, technology, facility, and environmental. Based on Figs. 5 , 6 , 7 , and 8 , we found that out of all the studies that addressed privacy risks associated with sharing personal information, most studies discussed human and technical layers, followed by the facility layer in all smart city sectors. However, few studies discussed the environmental layer, including privacy regulation and policies, only when addressing improper access and unauthorised use of privacy risks relevant to sharing personal information in smart health and smart business/organisation contexts.
Furthermore, according to Tables 7 , 8 , 9 , 10 , and 11 , we found that most studies that defined elements under human and technology layers are relevant to smart health, with few studies in other smart city sectors. Additionally, although applying policies and regulations is vital to mitigate privacy risks associated with personal information in any smart city, we noticed that these elements, mainly categorised under the environmental layer, have not been investigated enough in the selected studies. Based on the above, there is a need to cover these gaps in future work.
Undoubtedly, defining privacy requirements helps to study the consequences of privacy risks relevant to personal information. Moreover, it helps to choose the proper treatment for the identified risks. In this regard, we reviewed the selected studies to identify the privacy requirements based on well-known classifications such as CIA, IAAA, and the privacy requirement terminology (Pfitzmann & Hansen, 2010 ). Based on Table 12 , our findings reveal that current studies investigate CIA triad and identification, authorization, authentication, and anonymity requirements for privacy risk in smart cities. However, addressing the impact of privacy risk on accounting, undetectability, unobservability, and pseudonymity is still largely unclear. This draws our attention to the need for more studies defining those requirements when discussing the privacy risks of sharing personal information in smart cities. Another finding shows that most selected studies link the requirements with the proposed technical controls. They test proposed solutions against those requirements to explain how they should satisfy them. However, there is a lack of studies that discuss the link between these requirements and privacy risks. For example, to the best of our knowledge, secondary use, ID theft, and policy and consent non-compliance threats are not linked with any one of the identified requirements; thus, more studies need to cover this gap to address the consequences and impacts of these risks.
Existing Control
We reviewed the selected studies to extract the existing privacy controls to preserve the privacy of sharing personal information in smart cities. We categorised privacy controls based on the well-known practical framework NIST 800–30 into technical and non-technical controls. Based on Table 13 , our findings show that technical privacy controls, such as cryptography, anonymity, access control, blockchain, and machine learning, are frequently discussed in the selected studies. However, those controls are insufficient to preserve personal information privacy in smart cities because they are poorly developed due to technical and cost restrictions. Another finding shows that a set of 23 selected studies proposed technical solutions without implicitly explaining what kind of privacy threats could be mitigated by the proposed solution. This means they proposed the solution to preserve privacy issues in smart cities. Thus, linking the technical solution with specific privacy threats needs more investigation in the literature. Table 13 also finds that blockchain is widely used in privacy-preserving schemes proposed in academic literature. This indicates the importance and effectiveness of using it to share personal information in smart cities without compromising privacy when integrating it with different PETs. On the other hand, our findings show that risk management has fewer research activities in academic fields; thus, this area requires further investigation.
Finally, the current research investigates risks, impact, and existing controls in different areas of focus (e.g. information security/privacy), and across various domains (e.g. smart health, smart grid, smart airport, and smart organisations). However, based on the analysis results, these studies seem to lack a systematic and common understanding of information privacy risks in smart cities. To address this challenge, there is a need to develop an ontology-based privacy risk assessment framework for a systematic and common understanding of privacy risks associated with sharing personal information in smart cities. Thus, this study is the first step to systematically synthesis and conceptualise the knowledge dispersed across different papers. It will provide a knowledge base and foundation for developing the personal information privacy risk ontology. The ontology will help enhance understanding the complex concepts and their relationships. Furthermore, it will help establish a common understanding for assessing and mitigating privacy risks in an informed manner. The development and evaluation of such ontology are beyond this paper’s scope and subject to further research. However, this paper provided a strong foundation for this much-needed ontology work.
Validity and Limitations
This work has some limitations like any other SLR. Given this study’s scope, we used well-known academic and industry databases to ensure sufficient coverage of the research topic. This provided a combination of academic and industrial studies explicitly emphasised in the analysis.
Given our emphasis on rigorously identifying and selecting relevant publications through systematic search strategies, the research methodology used in this study was suitable because it provided a multistage process. The process includes applying predefined inclusion and exclusion criteria and synthesising findings to derive meaningful insights to ensure that the process is unbiased.
One potential methodological limitation of the employed methodology in this study is the reliance on predefined databases, which may limit the comprehensiveness of the literature search. However, the identified databases encompass academic and industry sources, totalling six. This ensures that the selected databases cover a wide range of studies relevant to the topic at hand.
To ensure the validity and rigour of the adopted research methodology, we tested the search terms and keywords based on the identified research questions across the pre-selected databases. Furthermore, the process was reviewed to confirm the research’s quality and coverage prior to the documentation stage. In addition, the quality assessment criteria were used to avoid researcher bias and ensure the selected studies’ relevance and quality. Human error might lead to inconsistencies when conducting such research. Thus, regular meetings between the senior researcher and this study’s author were held to minimise the possibility of human error and ensure the quality of the research process and results. This also includes reviewing and learning from the SLRs published in different domains in quality academic outlets. Integrating the employed approach with an additional one to enhance the rigour and comprehensiveness of reviews is suggested as a future research direction.
The term “smart city” has become the focus of several countries striving to improve their population quality, enhance their economies, and ensure sustainability. To achieve their objectives, cities have adopted innovative technologies and applications and developed their ICT infrastructure to support smart city initiatives in many sectors. These sectors include health, government, transportation, business, and organisation. However, due to the strong relationship between ICT and smart cities, personal information is easily shared among relevant parties, leading to serious privacy risks that may affect individuals and organisations. These risks need to be addressed, as highlighted in this SLR. This study analysed and synthesised published research to identify and extract privacy risks, impacts, and existing controls related to sharing personal information in different sectors in smart cities. It also considers elements involved and interacting in the sharing activity based on the well-known CFIP framework and Adaptive EA as theoretical lenses and NIST 800–30 as a practical lens. Based on NIST 800–30, we identified seven privacy threats, three vulnerabilities, and eight requirements that might be impacted by the identified threats, along with seven privacy controls classified into technical and non-technical types. Furthermore, we used CFIP as a theoretical lens to identify and categorise privacy threats and vulnerabilities relevant to the scope of this study. Based on CFIP, we categorised the identified privacy risks (threats and vulnerabilities) into four main groups: collection, unauthorised access, improper use, and errors.
Furthermore, we mapped the identified risks to identified requirements and current controls. The Adaptive EA is used to map the identified risks under CFIP dimensions with layers that interact while sharing personal information in smart cities. Our findings show the need for contemporary solutions to improve the privacy level of sharing personal information in smart cities. Furthermore, there is a need to represent privacy risk assessment components and their relationship and the relation among elements involved in sharing personal information using ontology to facilitate common understanding and sharing of the relevant concepts between different parties involved in connected smart cities. This SLR can benefit both academia and industry by helping them better understand the privacy of sharing personal information in smart cities and providing a synthesised foundation for further work in this important area of research.
Data Availability
Not applicable.
Agrawal, T. K., Kumar, V., Pal, R., Wang, L., & Chen, Y. (2021). Blockchain-based framework for supply chain traceability: A case example of textile and clothing industry. Computers & Industrial Engineering, 154 , 107130.
Article Google Scholar
Ahmad Mohamad, A.-S., Alsmadi, M. K., Abdel Karim, B., Ibrahim, A., Abouelmagd, H., & Osman SaadShidwan, A. (2019). Emergent situations for smart cities: A survey. International Journal of Electrical and Computer Engineering, 9 (6), 4777–4787.
Google Scholar
Ahmed, E. M. (2021). Modelling Information and communications technology cyber security externalities spillover effects on sustainable economic growth. Journal of the Knowledge Economy, 12 (1), 412–430.
Alabsi, M. I., & Gill, A. Q. (2021). A review of passenger digital information privacy concerns in smart airports. IEEE Access, 9 , 33769-33781.
Albino, V., Berardi, U., & Dangelico, R. M. (2015). Smart cities: Definitions, dimensions, performance, and initiatives. Journal of Urban Technology, 22 (1), 3–21.
Avancha, S., Baxi, A., & Kotz, D. (2012). Privacy in mobile technology for personal healthcare. ACM Computing Surveys (CSUR), 45 (1), 1–54.
Bart Willemsen, P. B. (2017). The four do’s and don’ts of implementing your privacy program . Gartner.
Bogoda, L., Mo, J., Bil, C., & Ieee, (2019). A systems engineering approach to appraise cybersecurity risks of cns/atm and avionics systems. In 2019 Integrated Communications, Navigation and Surveillance Conference .
BrianLowans, B. W., & Meunier, M.-A. (2019). Use the data security governance framework to balance business needs and risks . Gartner.
Caragliu, A., Del Bo, C., & Nijkamp, P. (2009). Smart cities in Europe. Journal of Urban Technology, 18 , 65–82.
Chenthara, S., Khandakar, A., & Whittaker, F. (2019). Privacy-preserving data sharing using multi-layer access control model in electronic health environment. EAI Endorsed Transactions on Scalable Information Systems , 6, 22. https://doi.org/10.4108/eai.13-7-2018.159356
Choudhury, Z. H., & Rabbani, M. M. A. (2019). Biometric passport for national security using multibiometrics and encrypted biometric data encoded in the QR code. Journal of Applied Security Research, 15 , 1–31.
Chua, H. N., Herbland, A., Wong, S. F., & Chang, Y. (2017). Compliance to personal data protection principles: A study of how organisations frame privacy policy notices. Telematics and Informatics, 34 (4), 157–170.
Chun, S.-H. (2015). Privacy enhancing technologies (PETs) and investment strategies for a data market. Procedia-Social and Behavioral Sciences, 185 , 271–275.
Cranor, L. F. (2012). Necessary but not sufficient: Standardized mechanisms for privacy notice and choice. J on Telecomm & High Tech L, 10 , 273.
Curzon, J., Almehmadi, A., & El-Khatib, K. (2019). A survey of privacy enhancing technologies for smart cities. Pervasive and Mobile Computing, 55 , 76–95.
Deng, M., Wuyts, K., Scandariato, R., Preneel, B., & Joosen, W. (2011). A privacy threat analysis framework: Supporting the elicitation and fulfillment of privacy requirements. Requirements Engineering, 16 (1), 3–32.
EUGDPR. (2018). “GDPR key changes.” Retrieved 20 Sep, 2019, from http://www.eugdpr.org/key-changes.html .
Ferrag, M. A., Maglaras, L. A., Janicke, H., Jiang, J., & Shu, L. (2018). A systematic review of data protection and privacy preservation schemes for smart grid communications. Sustainable Cities and Society, 38 , 806–835.
Gaire, R., Ghosh, R. K., Kim, J., Krumpholz, A., Ranjan, R., Shyamasundar, R., & Nepal, S. (2019). Crowdsensing and privacy in smart city applications (pp. 57–73). Elsevier.
Gellman, R. (2017). Fair information practices: A basic history. Available at SSRN 2415020.
Giffinger, R., Fertner, C., Kramar, H., Kalasek, R., Milanović, N., & Meijers, E. (2007). Smart cities - Ranking of European medium-sized cities . Centre of Regional Science, Vienna University of Technology.
Gill, A. Q. (2015). Adaptive cloud enterprise architecture . World Scientific.
Book Google Scholar
Gill, A. Q. (2021). A theory of information trilogy: Digital ecosystem information exchange architecture. Information, 12 (7), 283.
Henriksen-Bulmer, J., Faily, S., & Jeary, S. (2019). Privacy risk assessment in context: A meta-model based on contextual integrity. Computers & Security, 82 , 270–283.
Heurix, J., Zimmermann, P., Neubauer, T., & Fenz, S. (2015). A taxonomy for privacy enhancing technologies. Computers & Security, 53 , 1–17.
Hiller, J. S., & Blanke, J. M. (2016). Smart cities, big data, and the resilience of privacy. Hastings LJ, 68 , 309.
Hiller, J. S., & Russell, R. S. (2017). Privacy in crises: The NIST privacy framework. Journal of Contingencies and Crisis Management, 25 (1), 31–38.
Hoffman, L. (1977). Modern methods for computer security and privacy . Englewood Cliffs: Prentice-Hall.
Hong, J. I., Ng, J. D., Lederer, S., & Landay, J. A. (2004). Privacy risk models for designing privacy-sensitive ubiquitous computing systems. In Proceedings of the 5th conference on Designing interactive systems: processes, practices, methods, and techniques .
Hou, Y., Gao, P., & Nicholson, B. (2018). Understanding organisational responses to regulative pressures in information security management: The case of a Chinese hospital. Technological Forecasting and Social Change, 126 , 64–75.
Hough, M. G. (2009). Keeping it to ourselves: Technology, privacy, and the loss of reserve. Technology in Society, 31 (4), 406–413.
Hsiao, Y.-C., Wu, M.-H., & Li, S. C. (2021). Elevated performance of the smart city-A case study of the IoT by innovation mode. IEEE Transactions on Engineering Management, 68 (5), 1461–1475.
Imine, Y., Lounis, A., & Bouabdallah, A. (2020). An accountable privacy-preserving scheme for public information sharing systems. Computers & Security, 93 , 101786.
Ismagilova, E., Hughes, L., Rana, N. P., & Dwivedi, Y. K. (2020). Security, privacy and risks within smart cities: Literature review and development of a smart city interaction framework. Information Systems Frontiers.
Iwaya, L. H., Fischer-Hübner, S., Åhlfeldt, R.-M., & Martucci, L. A. (2019). Mobile health systems for community-based primary care: Identifying controls and mitigating privacy threats. JMIR mHealth and uHealth, 7 (3), e11642.
Iyengar, V. S. (2002). Transforming data to satisfy privacy constraints. In Proceedings of the eighth ACM SIGKDD international conference on Knowledge discovery and data mining .
Jin, W. (2024). Security and privacy of digital economic risk assessment system based on cloud computing and blockchain. Soft Computing, 28 (3), 2753–2768.
Jnr, B. A., Sylva, W., Watat, J. K., & Misra, S. (2023). A framework for standardization of distributed ledger technologies for interoperable data integration and alignment in sustainable smart cities. Journal of the Knowledge Economy .
Kalloniatis, C., Kavakli, E., & Gritzalis, S. (2008). Addressing privacy requirements in system design: The PriS method. Requirements Engineering, 13 (3), 241–255.
Kang, Y., Lee, H., Chun, K., & Song, J. (2007). Classification of privacy enhancing technologies on life-cycle of information. The International Conference on Emerging Security Information, Systems, and Technologies (SECUREWARE 2007), IEEE.
Khatoun, R., & Zeadally, S. (2017). Cybersecurity and privacy solutions in smart cities. IEEE Communications Magazine, 55 (3), 51–59.
Khi, I. A. (2020). Ready for take-off: How biometrics and blockchain can beat aviation’s quality issues. Biometric Technology Today, 2020 (1), 8–10.
Kitchenham, B., & Charters, S. (2007). Guidelines for performing systematic literature reviews in software engineering, 2 (3).
Kong, Y., Zhao, J., Yuan,, L., Dong, N., Lin, Y. & Yang, B. (2018). Research on data sharing analysis and key technology of smart city. In 2018 26th International Conference on Geoinformatics .
Kusumastuti, R. D., Nurmala, N., Rouli, J., & Herdiansyah, H. (2022). Analyzing the factors that influence the seeking and sharing of information on the smart city digital platform: Empirical evidence from Indonesia. Technology in Society, 68 , 101876.
Li, C., & Palanisamy, B. (2018). Privacy in Internet of Things: From principles to technologies. IEEE Internet of Things Journal, 6 (1), 488–505.
Martinez-Balleste, A., Perez-Martinez, P. A., & Solanas, A. (2013). The pursuit of citizens’ privacy: A privacy-aware smart city is possible. IEEE Communications Magazine, 6 , 136.
Mutanu, L., Gupta, K., & Gohil, J. (2022). Leveraging IoT solutions for enhanced health information exchange. Technology in Society, 68 , 101882. https://doi.org/10.1016/j.techsoc.2022.101882
National Institute of Standards and Technology, (2013). Guide for conducting risk assessments. https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
Nissenbaum, H. (2004). Privacy as contextual integrity. Wash. l. Rev., 79 , 119.
Norta, A., Matulevičius, R., & Leiding, B. (2019). Safeguarding a formalized Blockchain-enabled identity-authentication protocol by applying security risk-oriented patterns. Computers & Security, 86 , 253–269.
Office of the Australian Information Commissioner (n.d.). “Australian privacy principles.” Retrieved 2 Jun, 2020, from https://www.oaic.gov.au/privacy/australian-privacy-principles
Pal, D., Zhang, X., & Siyal, S. (2021). Prohibitive factors to the acceptance of Internet of Things (IoT) technology in society: A smart-home context using a resistive modelling approach. Technology in Society, 66 , 101683.
Peacock, J. (2021). What is NIST SP 800 30. Retrieved 9 September 2021, from https://www.cybersaint.io/blog/what-is-nist-sp-800-30
Peppet, S. R. (2014). Regulating the internet of things: First steps toward managing discrimination, privacy, security and consent. Tex. l. Rev., 93 , 85.
Pfitzmann, A., & Hansen, M. (2010). A terminology for talking about privacy by data minimization: Anonymity, unlinkability, undetectability, unobservability, pseudonymity, and identity management . Dresden.
Qian, Y., Liu, Z., Yang, J. & Wang, Q. (2018). A method of exchanging data in smart city by blockchain. In 2018 IEEE 20th International Conference on High Performance Computing and Communications; IEEE 16th International Conference on Smart City; IEEE 4th International Conference on Data Science and Systems (HPCC/SmartCity/DSS) .
Romanou, A. (2018). The necessity of the implementation of Privacy by Design in sectors where data protection concerns arise. Computer Law & Security Review, 34 (1), 99–110.
Runyon, B. (2020). Healthcare CIOs: Prepare for granular patient consent . Gartner.
Sadhukhan, D., Ray, S., Obaidat, M. S., & Dasgupta, M. (2021). A secure and privacy preserving lightweight authentication scheme for smart-grid communication using elliptic curve cryptography. Journal of Systems Architecture, 114 , 101938.
Safiullin, A., Krasnyuk, L., & Kapelyuk, Z. (2019). Integration of Industry 4.0 technologies for “smart cities” development. IOP conference series: materials science and engineering, IOP Publishing.
Sandhu, R. S., & Samarati, P. (1994). Access control: Principle and practice. IEEE Communications Magazine, 32 (9), 40–48.
Shamshad, S., Mahmood, K., Kumari, S., & Chen, C.-M. (2020). A secure blockchain-based e-health records storage and sharing scheme. Journal of Information Security and Applications, 55 , 102590.
Sharma, S., Singh, G., Sharma, R., Jones, P., Kraus, S., & Dwivedi, Y. K. (2020). Digital health innovation: exploring adoption of COVID-19 digital contact tracing apps. In IEEE transactions on engineering management , 1–17.
Silva, P., Monteiro, E., & Simões, P. (2021). Privacy in the Cloud: A survey of existing solutions and research challenges. IEEE Access, 9 , 10473–10497.
Smith, H., Milberg, S., & Burke, S. J. (1996). Information privacy: Measuring individuals’ concerns about organisational practices. MIS Quarterly, 20 , 167–196.
Solove, D. J. (2006). A taxonomy of privacy. University of Pennsylvania Law Review, 154 (3), 477–564.
Solove, D. J. (2011). “Nothing to hide: The false tradeoff between privacy and security (Introduction).”
Sotirelis, P., Nakopoulos, P., Valvi, T., Grigoroudis, E., & Carayannis, E. (2022). Measuring smart city performance: A multiple criteria decision analysis approach. Journal of the Knowledge Economy, 13 (4), 2957–2985.
Spiekermann, S., & Cranor, L. F. (2008). Engineering privacy. IEEE Transactions on Software Engineering, 35 (1), 67–82.
Stoneburner, G., Goguen, A., & Feringa, A. (2002). Risk management guide for information technology systems, special publication (NIST SP), National Institude of Standard and Technology.
Taplin, K. (2021). South Africa’s PNR regime: Privacy and data protection. Computer Law & Security Review, 40 , 105524.
Tedeschi, P., & Sciancalepore, S. (2019). Edge and fog computing in critical infrastructures: Analysis, security threats, and research challenges. In 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW) .
Thapa, C., & Camtepe, S. (2020). Precision health data: Requirements, challenges and existing techniques for data security and privacy. Computers in Biology and Medicine , 104130.
Van Blarkom, G., Borking, J. J., & Olk, J. E. (2003). Handbook of privacy and privacy-enhancing technologies. Privacy Incorporated Software Agent (PISA) Consortium, The Hague 198.
Van Slyke, C., Shim, J., Johnson, R., & Jiang, J. (2006). Concern for information privacy and online consumer purchasing. Journal of the Association for Information Systems , 7 (6). https://doi.org/10.17705/1jais.00092
Vinod Kumar, T., & Dahiya, B. (2017). “Smart economy in smart cities. In Smart economy in smart cities: International collaborative research: Ottawa, St. Louis, Stuttgart, Bologna, Cape Town, Nairobi, Dakar, Lagos, New Delhi, Varanasi, Vijayawada, Kozhikode, Hong Kong, 3–76.
Vu, K., & Hartley, K. (2018). Promoting smart cities in developing countries: Policy insights from Vietnam. Telecommunications Policy, 42 (10), 845–859.
Wall, J., Lowry, P. B., & Barlow, J. B. (2015). Organisational violations of externally governed privacy and security rules: Explaining and predicting selective violations under conditions of strain and excess. Journal of the Association for Information Systems, 17 (1), 39–76.
Wang, Y., Zhang, A., Zhang, P., & Wang, H. (2019). Cloud-assisted EHR sharing with security and privacy preservation via consortium blockchain. IEEE Access, 7 , 136704–136719.
Wang, C., Zhang, N., & Wang, C. (2021). Managing privacy in the digital economy. Fundamental Research, 1 (5), 543–551.
Warren, S. D., & Brandeis, L. D. (1890). Right to privacy. Harvard Law Review, 4 , 193.
Wolford, B. (2020). “What is GDPR, the EU’s new data protection law?” Retrieved 2 Feb, 2020, from https://gdpr.eu/what-is-gdpr/ .
Xiong, W., & Lagerström, R. (2019). Threat modeling – A systematic literature review. Computers & Security, 84 , 53–69.
Xu, H., Dinev, T., Smith, J., & Hart, P. (2011). Information privacy concerns: Linking individual perceptions with institutional privacy assurances. Journal of the Association for Information Systems, 12 (12), 1.
Yang, Y., Zheng, X., Guo, W., Liu, X., & Chang, V. (2018). Privacy-preserving fusion of IoT and big data for e-health. Future Generation Computer Systems, 86 , 1437–1455.
Yang, L., Xue, H., & Li, F. (2014). Privacy-preserving data sharing in smart grid systems. In 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm) , IEEE.
Yi, X., Miao, Y., Bertino, E. & Willemson, J. (2013). Multiparty privacy protection for electronic health records. In 2013 IEEE Global Communications Conference (GLOBECOM) , IEEE.
Zhang, Z. (2019). Technologies raise the effectiveness of airport security control. In 2019 IEEE 1st International Conference on Civil Aviation Safety and Information Technology (ICCASIT) .
Zhiyong, Z., Yongbin, X., & Jiaying, C. (2024). Digital economy, industrial structure upgrading and green innovation efficiency of family enterprises. International Entrepreneurship and Management Journal, 20 (1), 479–503.
Download references
Open Access funding enabled and organized by CAUL and its Member Institutions. This work was supported by Taibah University, Saudi Arabia, which provided a Ph.D. scholarship that covered funding for this work. This work was done at the University of Technology Sydney, Australia.
Author information
Authors and affiliations.
Faculty of Engineering and Information Technology, School of Computer Science, University of Technology Sydney, Ultimo, Sydney, NSW, 2007, Australia
Maha Ibrahim Alabsi & Asif Qumar Gill
Applied College, Taibah University, Al-Madinah Al-Munawarrah, Madina, Saudi Arabia
Maha Ibrahim Alabsi
You can also search for this author in PubMed Google Scholar
Contributions
All authors have contributed to this manuscript and approved the published version. The first author participated in all the work, including drafting, reviewing, and updating the article. The second author contributed to the research approach, review, and revisions of the article.
Corresponding author
Correspondence to Maha Ibrahim Alabsi .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Alabsi, M.I., Gill, A.Q. A Systematic Review of Personal Information Sharing in Smart Cities: Risks, Impacts, and Controls. J Knowl Econ (2024). https://doi.org/10.1007/s13132-024-02126-1
Download citation
Received : 19 October 2023
Accepted : 02 June 2024
Published : 24 June 2024
DOI : https://doi.org/10.1007/s13132-024-02126-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Information privacy
- Privacy risk
- Privacy requirements
- Privacy control
- Privacy risk assessment
- Find a journal
- Publish with us
- Track your research
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Published: 12 June 2024
Microsurgery in periodontics and oral implantology: a systematic review of current clinical applications and outcomes
- Hamoun Sabri ORCID: orcid.org/0000-0001-6581-2104 1 ,
- Sara Alhachache 2 ,
- Pramiti Saxena 1 ,
- Prerana Dubey 1 ,
- Paolo Nava ORCID: orcid.org/0009-0009-6177-3000 1 ,
- Syed Hanan Rufai 1 &
- Farzin Sarkarat 3
Evidence-Based Dentistry ( 2024 ) Cite this article
60 Accesses
Metrics details
- Dental implants
- Dentoalveolar surgery
The aim of this systematic review was to comprehensively explore the current trends and therapeutic approaches in which an operating microscope (OM) is used in periodontics and dental implant surgeries.
Materials and methods
A systematic search strategy was built to detect studies including various surgical techniques performed under an OM. PubMed, EMBASE, and SCOPUS databases were searched. No limitations in terms of time and language were applied. The data regarding the study design, type of procedure, treatment groups, and surgical outcomes were collected and analyzed descriptively. In addition, a bibliometric analysis was performed concerning the co-authorship and keyword co-occurrence network.
Out of 1985 articles, finally, 55 met the inclusion criteria. Current periodontal and implant microsurgery trends consist of: periodontal therapy, dental implant microsurgery, soft tissue grafting and periodontal plastic surgery, bone augmentation, ridge preservation, and ortho-perio microsurgery. The bibliometric analysis revealed “guided tissue regeneration”, “periodontal regeneration” and “root coverage” being the most repeated keywords (landmark nodes). 132 authors within 29 clusters were identified, publishing within the frameworks of “periodontal and implant microsurgery”.
Within its limitations, this systematic review provides an overview of the latest trends in periodontal and implant microsurgery when considering the use of an OM as the magnification tool. Also, it discusses the reported success and outcomes of the mentioned procedures.
This is a preview of subscription content, access via your institution
Access options
Subscribe to this journal
Receive 4 print issues and online access
251,40 € per year
only 62,85 € per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout

Similar content being viewed by others
Minimally invasive periodontal regeneration with the buccal approach: a systematic review and meta-analysis of clinical studies
A comparison of techniques for the explantation of osseointegrated dental implants
Does a history of periodontal disease affect implant survival?
Data availability.
The data is available upon request from the authors.
Cortellini P, Tonetti MS. Microsurgical approach to periodontal regeneration. Initial evaluation in a case cohort. J Periodontol. 2001;72:559–69.
Article CAS PubMed Google Scholar
Yu SH, Oh TJ, Wang HL, Chan HL. Amnion-Chorion Membrane in Open-Wound Approach for Localized Horizontal Ridge Augmentation: A Case Series Report. Clin Adv Periodontics. 2022;12:101–5.
Article PubMed Google Scholar
Srivastava R, Mohan R, Saravana Balaji MD, Vijay VK, Srinivasan S, Navarasu M. A Randomized Controlled Trial on a Minimally Invasive Microsurgical Versus Conventional Procedure for the Management of Localized Gingival Recession in Esthetic Zone using Alloderm. J Pharm Bioallied Sci. 2021;13:S476–83.
Article PubMed PubMed Central Google Scholar
Di Gianfilippo R, Wang I, Steigmann L, Velasquez D, Wang H-L, Chan H-L. Efficacy of microsurgery and comparison to macrosurgery for gingival recession treatment: a systematic review with meta-analysis. Clin Oral Investig. 2021;25:4269–80.
Sultan N, Jafri Z, Sawai M, Bhardwaj A. Minimally invasive periodontal therapy. J Oral Biol Craniofacial Res. 2020;10:161–5.
Article Google Scholar
Sabri H, SamavatiJame F, Sarkarat F, Wang HL, Zadeh HH. Clinical efficacy of Vestibular Incision Subperiosteal Tunnel Access (VISTA) for treatment of multiple gingival recession defects: a systematic review, meta-analysis and meta-regression. Clin Oral Investig. 2023;27:7171–87.
Tamai S. History of microsurgery. Plast Reconstructive Surg. 2009;124:e282–94.
Article CAS Google Scholar
Shanelec DA. Periodontal microsurgery. J Esthet Restor Dent. 2003;15:402–7. discussion 408.
Tibbetts LS, Shanelec D. Periodontal microsurgery. Dent Clin North Am. 1998;42:339–59.
Daniel RK. Microsurgery: through the looking glass. N. Engl J Med. 1979;300:1251–7.
Carr GB, Murgel CA. The use of the operating microscope in endodontics. Dent Clin. 2010;54:191–214.
Google Scholar
Sitbon Y, Attathom T, St-Georges A. Minimal intervention dentistry II: part 1. Contribution of the operating microscope to dentistry. Br Dent J. 2014;216:125–30.
Shanelec DA, Tibbetts LS. A perspective on the future of periodontal microsurgery. Periodontology. 1996;11:58–64.
Chambrone L, Pini Prato GP. Clinical insights about the evolution of root coverage procedures: The flap, the graft, and the surgery. J Periodontol. 2019;90:9–15.
Azaripour A, Kissinger M, Farina VSL, Van Noorden CJ, Gerhold‐Ay A, Willershausen B, et al. Root coverage with connective tissue graft associated with coronally advanced flap or tunnel technique: a randomized, double‐blind, mono‐centre clinical trial. J Clin Periodontol. 2016;43:1142–50.
Burkhardt R, Lang NP. Coverage of localized gingival recessions: comparison of micro‐and macrosurgical techniques. J Clin Periodontol. 2005;32:287–93.
Gargallo-Albiol J, Sinjab KH, Barootchi S, Chan H-L, Wang H-L. Microscope and micro-camera assessment of Schneiderian membrane perforation via transcrestal sinus floor elevation: A randomized ex vivo study. Clin Oral Implants Res. 2019;30:682–90.
Jiao Y, Hasegawa M, Inohara N. The role of oral pathobionts in dysbiosis during periodontitis development. J Dent Res. 2014;93:539–46.
Article CAS PubMed PubMed Central Google Scholar
Hajishengallis G. Periodontitis: from microbial immune subversion to systemic inflammation. Nat Rev Immunol. 2015;15:30–44.
Cortellini P, Nieri M, Pini Prato G, Tonetti MS. Single minimally invasive surgical technique with an enamel matrix derivative to treat multiple adjacent intra‐bony defects: Clinical outcomes and patient morbidity. J Clin Periodontol. 2008;35:605–13.
Cortellini P, Tonetti MS. Improved wound stability with a modified minimally invasive surgical technique in the regenerative treatment of isolated interdental intrabony defects. J Clin Periodontol. 2009;36:157–63.
Cortellini P, Pini-Prato G, Nieri M, Tonetti MS. Minimally invasive surgical technique and enamel matrix derivative in intrabony defects: 2. Factors associated with healing outcomes. Int J Periodontics Restor Dent. 2009;29:257–65.
Bertossi D, Vercellotti T, Podesta A, Nocini PF. Orthodontic Microsurgery for Rapid Dental Repositioning in Dental Malpositions. J Oral Maxillofac Surg. 2011;69:747–53.
Cortellini P, Tonetti M, Prato GP. The partly epithelialized free gingival graft (pe-fgg) at lower incisors. A pilot study with implications for alignment of the mucogingival junction. J Clin Periodontol. 2012;39:674–80.
Penmetsa GS, Panda KD, Manthena AKR, Korukonda RR, Gadde P. Evaluating the efficacy of different magnification variables during root planing procedure under a surgical operating microscope in chronic periodontitis: A randomized clinical trial. J Indian Soc Periodontol. 2020;24:32–36.
Rodriguez JAM, Ruiz AJO. Apical approach in periodontal reconstructive surgery with enamel matrix derivate and enamel matrix derivate plus bone substitutes: a randomized, controlled clinical trial. Clin Oral Investig. 2022;26:2793–805.
Shanelec DA, Tibbetts LS. Implant Microsurgery: Immediate Implant Placement With Implant‐Supported Provisional. Clin Adv Periodontics. 2011;1:161–72.
Sabri H, Barootchi S, Heck T, Wang HL. Single‐rooted extraction socket classification: A systematic review and proposal of a new classification system based on morphologic and patient‐related factors. J Esthet Restor Dent. 2023;35:168–82.
Pandolfi A. A modified approach to horizontal augmention of soft tissue around the implant: omega roll envelope flap. Description of surgical technique. La Clin Terapeutica. 2018;169:e165–9.
CAS Google Scholar
Jain D, Mohan R, Singh VD. Comparison of microsurgical and macrosurgical technique using bioactive synthetic bone graft and collagen membrane for an implant site development: A randomized controlled clinical trial. J Indian Soc Periodontol. 2019;23:448–460.
Sirinirund B, Chan H-L, Velasquez D. Microscope-Assisted Maxillary Sinus Augmentation: A Case Series. Int J Periodontics Restor Dent. 2021;41:531–7.
Shakibaie- MB. Comparison of the effectiveness of two different bone substitute materials for socket preservation after tooth extraction: a controlled clinical study. Int J Periodontics Restor Dent. 2013;33:223–8.
Shakibaie B. Microscope-controlled internal sinus floor elevation (MCI-SFE): A new technique to evaluate the sinus membrane during transcrestal lifting. Int J Microdentistry. 2013;4:12–19.
Shakibaie B, Sabri H, Blatz MB, Barootchi S. Comparison of the minimally-invasive roll-in envelope flap technique to the holding suture technique in implant surgery: A prospective case series. J Esthet Restor Dent. 2023;35:625–31.
Chambrone L, Tatakis DN. Periodontal soft tissue root coverage procedures: a systematic review from the AAP Regeneration Workshop. J Periodontol. 2015;86:S8–51.
Richardson CR, Allen EP, Chambrone L, et al. Periodontal Soft Tissue Root Coverage Procedures: Practical Applications From the AAP Regeneration Workshop. Clin Adv Periodontics. 2015;5:2–10.
Harris RJ. A comparison of two techniques for obtaining a connective tissue graft from the palate. Int J Periodontics Restor Dent. 1997;17:260–71.
Stefanini M, Barootchi S, Tavelli L, Marzadori M, Mazzotti C, Mounssif I, et al. Difficulty score for the treatment of isolated gingival recessions with the coronally advanced flap: a preliminary reliability study. Clin Oral Investig. 2022;27:559–69.
Zuhr O, Bäumer D, Hürzeler M. The addition of soft tissue replacement grafts in plastic periodontal and implant surgery: critical elements in design and execution. J Clin Periodontol. 2014;41:S123–42.
Gil Escalante M, Tatakis DN. Gingival cyst of the adult as early sequela of connective tissue grafting. Case Rep Dent. 2015;2015:473689.
Maia VTG, Kahn S, Souza ABD, Fernandes G. De‐epithelialized connective tissue graft and the reminiscent epithelial content after harvested by the Harris’ technique: a histological and morphometrical case series. Clin Adv Periodontics. 2021;11:150–4.
Kahn S, Araújo ITE, Dias AT, Balduíno A, Chambrone L, de Oliveira Fernandes GV. Histologic and histomorphometric analysis of connective tissue grafts harvested by the parallel incision method: a pilot randomized controlled trial comparing macro-and microsurgical approaches. Quintessence Int. 2021;52:772.
PubMed Google Scholar
Patel C, Mehta R, Joshi S, Hirani T, Joshi C. Comparative evaluation of treatment of localized gingival recessions with coronally advanced flap using microsurgical and conventional techniques. Contemp Clin Dent. 2018;9:613.
Francetti L, Del Fabbro M, Calace S, Testori T, Weinstein RL. Microsurgical treatment of gingival recession: a controlled clinical study. Int J Periodontics Restor Dent. 2005;25:181–8.
Francetti L, Del Fabbro M, Testori T, Weinstein RL. Periodontal microsurgery: report of 16 cases consecutively treated by the free rotated papilla autograft technique combined with the coronally advanced flap. Int J Periodontics Restor Dent. 2004;24:272–9.
Kahn S, WJdPR Rodrigues, MdO Barceleiro. Periodontal plastic microsurgery in the treatment of deep gingival recession after orthodontic movement. Case Rep. Dent. 2013;2013:851413.
PubMed PubMed Central Google Scholar
Yadav D, Singh S, Roy S. Periodontal microsurgery for management of multiple marginal tissue recession using Zucchelli’s modification of coronally advanced flap and pericardium membrane in an esthetic zone. J Indian Soc Periodontol. 2019;23:284.
Kumar A, Bains VK, Jhingran R, Srivastava R, Madan R, Rizvi I. Patient-centered microsurgical management of gingival recession using coronally advanced flap with either platelet-rich fibrin or connective tissue graft: A comparative analysis. Contemp Clin Dent. 2017;8:293.
Thankkappan P, Roy S, Mandlik VB. Comparative evaluation of management of gingival recession using subepithelial connective tissue graft and collagen membrane by periodontal microsurgical technique: A clinical study of 40 cases. J Indian Soc Periodontol. 2016;20:189.
Agarwal SK, Jhingran R, Bains VK, Srivastava R, Madan R, Rizvi I. Patient-centered evaluation of microsurgical management of gingival recession using coronally advanced flap with platelet-rich fibrin or amnion membrane: A comparative analysis. Eur J Dent. 2016;10:121–33.
Kaval B, Renaud DE, Scott DA, Buduneli N. The role of smoking and gingival crevicular fluid markers on coronally advanced flap outcomes. J Periodontol. 2014;85:395–405.
Andrade PF, Grisi MF, Marcaccini AM, et al. Comparison between micro‐and macrosurgical techniques for the treatment of localized gingival recessions using coronally positioned flaps and enamel matrix derivative. J Periodontol. 2010;81:1572–9.
Nizam N, Bengisu O, Sönmez Ş. Micro- and Macrosurgical Techniques in the Coverage of Gingival Recession Using Connective Tissue Graft: 2 Years Follow-Up. J Esthet Restor Dent. 2015;27:71–83.
Kareem N, Mahendra J, Kumar KA. Triangular coronally advanced flap: Conventional versus Microsurgery. J Indian Soc Periodontol. 2018;22:73.
Bittencourt S, Del Peloso Ribeiro É, Sallum EA, Nociti FH Jr, Casati MZ. Surgical microscope may enhance root coverage with subepithelial connective tissue graft: A randomized‐controlled clinical trial. J Periodontol. 2012;83:721–30.
Pandey S, Mehta D. Treatment of localized gingival recession using the free rotated papilla autograft combined with coronally advanced flap by conventional (macrosurgery) and surgery under magnification (microsurgical) technique: A comparative clinical study. J Indian Soc Periodontol. 2013;17:765.
Chandra A, Gupta HL, Kumar P. Esthetic root coverage by sub epithelial connective tissue graft microsurgery: a case report.IJSS Case Reports & Reviews 2015;2:16–9.
Jaiswal PG, Puri SS, Bhongade ML. Evaluation of effectiveness of subepithelial connective tissue graft in combination with coronally positioned flap in the treatment of isolated gingival recession in esthetic areas by using surgical microscope. J Datta Meghe Inst Med Sci Univ. 2017;12:79.
Jindal U, Pandit N, Bali D, Malik R, Gugnani S. Comparative evaluation of recession coverage with sub-epithelial connective tissue graft using macrosurgical and microsurgical approaches: A randomized split mouth study. J Indian Soc Periodontol. 2015;19:203–7.
Mohan R, Jain R. Microsurgical Approach for Root Coverage of Receding Gingiva in the Esthetic Zone. Arch Reconstr Microsurg. 2013;22:69–73.
Georgieva I. Coronally advanced flap technique for root coverage in the aesthetic zone of upper jaw. J IMAB Annu Proc Sci Pap. 2020;26:3267–70.
Dhir V, Jha A. Microsurgical treatment of gingival recession by subepithelial connective tissue graft: a case report. Med J Armed Forces India. 2011;67:293.
Nivetha R. Clinical outcome of coronally advanced flap and modified coronally advanced flap using microsurgery technique in the treatment of miller’s class I and II gingival recession: A Comparative study. Madurai: Best Dental Science College; 2018.
Kahn S, de Oliveira LZ, Dias AT, Fernandes GVO. Clinical evaluation and biological understanding of the early step-by-step healing after periodontal microsurgery: A case report with PES analysis comparing initial and 31-day result. J Adv Periodontol Implant Dent. 2022;14:141–5.
Katariya C, Rajasekar A. Comparison between conventional and micro-assisted periodontal surgery: Case series. J Adv Pharm Technol Res. 2022;13:S348–52.
Karmakar S, Kamath DSG, Shetty NJ, Natarajan S. Treatment of Multiple Adjacent Class I and Class II Gingival Recessions by Modified Microsurgical Tunnel Technique and Modified Coronally Advanced Flap Using Connective Tissue Graft: A Randomized Mono-center Clinical Trial. J Int Soc Prev Community Dent. 2022;12:38–48.
Mohan R, Srivastava R, Gundappa M. Microsurgical Reconstruction of Receded Gingiva Using Alloderm In Esthetic Zone. Juniper Online J Orthopedic Orthoplastic Surg. 2017;1:30–2.
Karring T, Östergaard E, Löe H. Conservation of tissue specifically after heterotopic transplantation of gingiva and alveolar mucosa. J Periodontal Res. 1971;6:282–93.
Induchoodan A, Remya R. Interdental Papilla Reconstruction using Modified Nordland’s Microsurgical Technique: A Case Study. Int J Drug Res Dent Sci. 2021;3:97–105.
Akiyama K. Papilla reconstruction using the dental operating microscope. Int. J. Microdentistry. 2009;1:25–9.
Singh D, Jhingran R, Bains VK, Madan R, Srivastava R. Efficacy of platelet-rich fibrin in interdental papilla reconstruction as compared to connective tissue using microsurgical approach. Contemp Clin Dent. 2019;10:643.
Reddy SSP, Manohar B. Microsurgical approach for the management of gingival cleft: A case series and decision-making process. Clin Adv Periodontics. 2024. https://doi.org/10.1002/cap.10277 .
Mamoun J. Use of elevator instruments when luxating and extracting teeth in dentistry: clinical techniques. J Korean Assoc Oral Maxillofac Surg. 2017;43:204–11.
Mamoun J. Use of high-magnification loupes or surgical operating microscope when performing prophylaxes, scaling or root planing procedures. N. Y State Dent J. 2013;79:48.
Donthu N, Kumar S, Mukherjee D, Pandey N, Lim WM. How to conduct a bibliometric analysis: An overview and guidelines. J Bus Res. 2021;133:285–96.
Sabri H, Wang HL, Peri-implantitis: A. bibliometric network analysis of top 100 most-cited research articles. Clin Implant Dent Relat Res. 2023;25:284–302.
Sabri H, Manouchehri N, Tavelli L, Kan JYK, Wang HL, Barootchi S. Five decades of research on immediate implant therapy: A modern bibliometric network analysis via Altmetric and level of evidence mapping. Clin Oral Implants Res. 2024. https://doi.org/10.1111/clr.14269 .
Ribeiro FV, Casarin RCV, Junior FHN, Sallum EA, Casati MZ. The Role of Enamel Matrix Derivative Protein in Minimally Invasive Surgery in Treating Intrabony Defects in Single-Rooted Teeth: A Randomized Clinical Trial. J Periodontol. 2011;82:522–32.
Ribeiro FV, Casarin RCV, Palma MAG, Junior FHN, Sallum EA, Casati RZ. Clinical and Patient-Centered Outcomes After Minimally Invasive Non-Surgical or Surgical Approaches for the Treatment of Intrabony Defects: A Randomized Clinical Trial. J Periodontol. 2011;82:1256–66.
Aslan S, Buduneli N, Cortellini P. Clinical outcomes of the entire papilla preservation technique with and without biomaterials in the treatment of isolated intrabony defects: A randomized controlled clinical trial. J Clin Periodontol. 2020;47:470–8.
Aslan S, Buduneli N, Cortellini P. Reconstructive surgical treatment of isolated deep intrabony defects with guided tissue regeneration using entire papilla preservation technique: A prospective case series. J Periodontol. 2021;92:488–95.
Sabri H, Sarkarat F, Mortezagholi B, Aghajani D. Non‐surgical management of oro‐antral communication using platelet‐rich fibrin: A review of the literature. Oral Surg. 2022;15:455–64.
Cortellini P, Tonetti MS. Clinical and radiographic outcomes of the modified minimally invasive surgical technique with and without regenerative materials: a randomized-controlled trial in intra-bony defects. J Clin Periodontol. 2011;38:365–73.
Ahmad N, Tewari S, Narula SC, Sharma RK, Tanwar N. Platelet-rich fibrin along with a modified minimally invasive surgical technique for the treatment of intrabony defects: a randomized clinical trial. J Periodontal Implant Sci. 2019;49:355–65.
Azar EL, Rojas MA, Mandalunis P, Gualtieri A, Carranza N. Histological evaluation of subepithelial connective tissue grafts harvested by two different techniques: Preliminary study in humans. Acta Odontol Latinoam. 2019;32:10–16.
Rauten AM, Surlin P, Oprea B, Siloşi I, Moisa M, Caramizaru D, et al. Matrix metalloproteinase 9 levels in gingival crevicular fluid in patients after periodontal microsurgery for orthodontic induced gingival hypertrophy. Rom J Morphol Embryol. 2011;52:431–3.
Download references
The author(s) received no specific funding for this work.
Author information
Authors and affiliations.
Department of Periodontics and Oral Medicine, University of Michigan School of Dentistry, Ann Arbor, MI, USA
Hamoun Sabri, Pramiti Saxena, Prerana Dubey, Paolo Nava & Syed Hanan Rufai
Department of Periodontics, University of Louisville School of Dental Medicine, Louisville, KY, USA
Sara Alhachache
Department of Oral and Maxillofacial Surgery, Gulf Medical University, Ajman, United Arab Emirates
Farzin Sarkarat
You can also search for this author in PubMed Google Scholar
Contributions
HS: Conceptualization, manuscript writing, data analysis, SA: Manuscript writing, data collection, final revision, PS: Manuscript writing, data collection, final revision, PD: Manuscript writing, data collection, final revision, PN: data collection, final revision, SHR: data collection, final revision, FS: Conceptualization, manuscript writing, critical review of final version.
Corresponding author
Correspondence to Hamoun Sabri .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Supplementary information, rights and permissions.
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Cite this article.
Sabri, H., Alhachache, S., Saxena, P. et al. Microsurgery in periodontics and oral implantology: a systematic review of current clinical applications and outcomes. Evid Based Dent (2024). https://doi.org/10.1038/s41432-024-01024-4
Download citation
Received : 06 March 2024
Accepted : 03 May 2024
Published : 12 June 2024
DOI : https://doi.org/10.1038/s41432-024-01024-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies

IMAGES
VIDEO
COMMENTS
Study designs: Part 7 - Systematic reviews. In this series on research study designs, we have so far looked at different types of primary research designs which attempt to answer a specific question. In this segment, we discuss systematic review, which is a study design used to summarize the results of several primary research studies.
A systematic review is a type of review that uses repeatable methods to find, select, and synthesize all available evidence. It answers a clearly formulated research question and explicitly states the methods used to arrive at the answer. Example: Systematic review. In 2008, Dr. Robert Boyle and his colleagues published a systematic review in ...
Topic selection and planning. In recent years, there has been an explosion in the number of systematic reviews conducted and published (Chalmers & Fox 2016, Fontelo & Liu 2018, Page et al 2015) - although a systematic review may be an inappropriate or unnecessary research methodology for answering many research questions.Systematic reviews can be inadvisable for a variety of reasons.
A systematic review collects all possible studies related to a given topic and design, and reviews and analyzes their results [ 1 ]. During the systematic review process, the quality of studies is evaluated, and a statistical meta-analysis of the study results is conducted on the basis of their quality. A meta-analysis is a valid, objective ...
A systematic review is a type of review that uses repeatable methods to find, select, and synthesise all available evidence. It answers a clearly formulated research question and explicitly states the methods used to arrive at the answer. Example: Systematic review. In 2008, Dr Robert Boyle and his colleagues published a systematic review in ...
Systematic reviews are characterized by a methodical and replicable methodology and presentation. They involve a comprehensive search to locate all relevant published and unpublished work on a subject; a systematic integration of search results; and a critique of the extent, nature, and quality of evidence in relation to a particular research question.
A systematic review is a type of study that synthesises research that has been conducted on a particular topic. Systematic reviews are considered to provide the highest level of evidence on the hierarchy of evidence pyramid. Systematic reviews are conducted following rigorous research methodology. To minimise bias, systematic reviews utilise a ...
Abstract. A systematic review identifies and synthesizes all relevant studies that fit prespecified criteria to answer a research question. Systematic review methods can be used to answer many types of research questions. The type of question most relevant to trialists is the effects of treatments and is thus the focus of this chapter.
A preliminary review, which can often result in a full systematic review, to understand the available research literature, is usually time or scope limited. Complies evidence from multiple reviews and does not search for primary studies. 3. Identifying a topic and developing inclusion/exclusion criteria.
Definition. A document often written by a panel that provides a comprehensive review of all relevant studies on a particular clinical or health-related topic/question. The systematic review is created after reviewing and combining all the information from both published and unpublished studies (focusing on clinical trials of similar treatments ...
A systematic review is a scholarly synthesis of the evidence on a clearly presented topic using critical methods to identify, define and assess research on the topic. A systematic review extracts and interprets data from published studies on the topic (in the scientific literature), then analyzes, describes, critically appraises and summarizes interpretations into a refined evidence-based ...
This site explores different review methodologies such as, systematic, scoping, realist, narrative, state of the art, meta-ethnography, critical, and integrative reviews. The LITR-EX site has a health professions education focus, but the advice and information is widely applicable. Types of Reviews. Review the table to peruse review types and ...
A systematic review is a particular type of evidence synthesis whose methodology seeks to maximize objectivity and transparency while minimizing bias in the identification, evaluation and use of information used to support an answer to a research question. Here below are some ways different authors have described the systematic review approach:
This paper argues that the current proliferation of types of systematic reviews creates challenges for the terminology for describing such reviews. Terminology is necessary for planning, describing, appraising, and using reviews, building infrastructure to enable the conduct and use of reviews, and for further developing review methodology. There is insufficient consensus on terminology for a ...
What is a Systematic Review? Systematic reviews encompass a variety of methods that involve gathering existing studies and research, then collectively analyzing them. This group of methodologies helps to identify larger conclusions about a body of knowledge, as well as identify gaps in that knowledge. These methods can also help answer research ...
The purpose of a review of healthcare literature is primarily to summarise the knowledge around a specific question or topic, or to make recommendations that can support health professionals and organisations make decisions about a specific intervention or care issue. 5 In addition, reviews can highlight gaps in knowledge to guide future research.
Systematic reviews play a crucial role in evidence-based practices as they consolidate research findings to inform decision-making. However, it is essential to assess the quality of systematic reviews to prevent biased or inaccurate conclusions. This paper underscores the importance of adhering to r …
Secondary sources are not evidence, but rather provide a commentary on and discussion of evidence. e.g. systematic review. Primary sources contain the original data and analysis from research studies. No outside evaluation or interpretation is provided. An example of a primary literature source is a peer-reviewed research article.
Finding out about different types of systematic reviews and the methods used for systematic reviews, and reading both systematic and other types of review will help to understand some of the differences. Typically, a systematic review addresses a focussed, structured research question in order to inform understanding and decisions on an area.
Definition: A systematic review is a summary of research results (evidence) that uses explicit and reproducible methods to systematically search, critically appraise, and synthesize on a specific issue.It synthesizes the results of multiple primary studies related to each other by using strategies that reduce biases and errors. When to use: If you want to identify, appraise, and synthesize all ...
Because no study, regardless of its type, should be interpreted in isolation, a systematic review is generally the best form of evidence. So, the preferred method is a good summary of research reports, i.e., systematic reviews and meta-analysis, which will give evidence-based answers to clinical situations.
Systematic Review A summary of the clinical literature. A systematic review is a critical assessment and evaluation of all research studies that address a particular clinical issue. The researchers use an organized method of locating, assembling, and evaluating a body of literature on a particular topic using a set of specific criteria.
This type of research helps identify patterns and relationships, indicating whether increased smoking is associated with higher rates of lung cancer. Experimental Research. Experimental research is a scientific approach where researchers manipulate one or more independent variables to observe their effect on a dependent variable.
Background Stroke stands as a significant macrovascular complication among individuals with Type 2 diabetes mellitus (T2DM), often resulting in the primary cause of mortality and disability within this patient demographic. Presently, numerous studies have been conducted to investigate the underlying causes of stroke in individuals with T2DM, yet the findings exhibit inconsistencies. Objective ...
We undertook a systematic review (rather than a meta-analysis) for two main reasons. First, our dataset comprises quantitative as well as qualitative papers. Second, a systematic review is more appropriate for an evolving field (as in our case) looking at a broad range of outcomes and aiming to direct research avenues for future researchers ...
The purpose of this study was to systematically investigate how novice visual representation of design ideas has been operationalized, measured, or assessed in the research literature. In the different screening phases in this systematic review, inclusion, exclusion, and quality criteria were applied.
Abstract. In this series on research study designs, we have so far looked at different types of primary research designs which attempt to answer a specific question. In this segment, we discuss systematic review, which is a study design used to summarize the results of several primary research studies. Systematic reviews often also use meta ...
Moreover, the implications and future research directions were also reported. The proposed privacy risk taxonomy will provide a much-needed foundation for the industry and research community, intending to research and evaluate privacy risk frameworks and design solutions for sharing personal information in smart cities.
The aim of this systematic review was to comprehensively explore the current trends and therapeutic approaches in which an operating microscope (OM) is used in periodontics and dental implant ...
Background: Accelerated by technological advancements and the recent global pandemic, there is burgeoning interest in digital mental health literacy (DMHL) interventions that can positively affect mental health. However, existing work remains inconclusive regarding the effectiveness of DMHL interventions. Objective: This systematic review and meta-analysis investigated the components and modes ...