
Security Company Business Plan Template
Written by Dave Lavinsky
Security Company Business Plan
You’ve come to the right place to create your Security Company business plan.
We have helped over 5,000 entrepreneurs and business owners create business plans and many have used them to start or grow their Security Companies.
Below is a template to help you create each section of your Security Company business plan.
Executive Summary
Business overview.
KB Security is a new security company located in San Antonio, Texas. KB Security provides security professionals to local establishments that need protection for their business or assets. We train our professionals for numerous situations so they are prepared for any security job. This includes anything from theft prevention to handling crisis situations. Whatever our clients’ concerns are, they can rest assured that they have hired the best security professionals in the San Antonio area.
KB Security is founded by Keith Baldwin, who has been a security professional for ten years. He has worked both as a professional security guard and as a certified trainer. In addition to his experience, he also holds an MBA. Keith’s combination of experience and education have given him the knowledge and skills to run a successful security company.
Product Offering
KB Security provides security professionals that can help businesses with all their security and surveillance needs. These can include but are not limited to:
- Protecting individuals
- Guarding property
- Preventing theft
- Helping with crisis situations
Businesses can sign up with one of our flexible contract programs when hiring our security services. We also offer a discounted trial period for those who are considering a long-term contract and want to test out our services before signing.
Customer Focus
KB Security will target local businesses, government organizations, and individuals located in San Antonio who need to hire security professionals. We expect most of our clients to be retail establishments who need help with theft prevention and guarding property and assets.
Management Team
KB Security is founded by Keith Baldwin, who has been a security professional for ten years. He has worked both as a professional security guard and as a certified trainer and received an MBA from the University of Texas. Keith’s education and experience has given him all the essential skills to run his dream security company. However, he will also hire other administrative staff to help him with the essential day-to-day functions.
Success Factors
KB Security will be able to achieve success by offering the following competitive advantages:
- Expert Security Professionals: KB Security only hires the best security professionals that have extensive training in security protocols.
- Location: KB Security is in a prime location, giving us quick and easy access to prime commercial districts. This is ideal especially when hired to handle crisis situations or alarm response.
- Affordable Pricing: The services offered by KB Security are similar in quality to its most premium-positioned competitors but are offered at a more affordable price.
- Management: Our management team has years of security and business experience that allows us to market to and serve customers in a much more sophisticated manner than our competitors.
Financial Highlights
KB Security is seeking a total funding of $300,000 of debt capital to open its office. The funding will be dedicated towards securing the office space and the office build-out. Funding will also be dedicated towards three months of overhead costs to include payroll of the staff, rent, and working capital. The breakout of the funding is below:
- Office design/build: $100,000
- Three months of overhead expenses (payroll, rent, utilities): $100,000
- Marketing & advertising: $50,000
- Working capital: $50,000
The following graph below outlines the pro forma financial projections for KB Security.
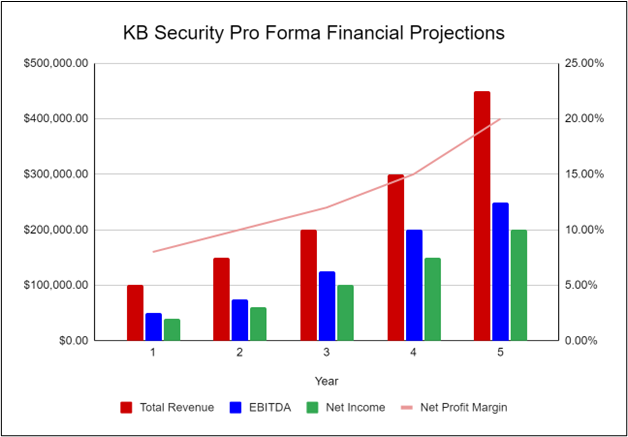
Company Overview
Who is kb security.
KB Security is founded by Keith Baldwin, who has been a security professional for ten years. He has worked both as a professional security guard and as a certified trainer. In addition to his experience, he also holds an MBA. Keith’s combination of experience and education have given him the knowledge and skills to run a successful security company.
KB Security’s History
After surveying the local customer base, and finding a potential office location, Keith Baldwin incorporated KB Security as an S-Corporation on May 1st, 2023.
Currently, the business is being run out of Keith’s home office, but once the lease on KB Security’s location is finalized, all operations will be run from there.
Since incorporation, KB Security has achieved the following milestones:
- Found a commercial space and signed a Letter of Intent to lease it
- Developed the company’s name, logo, social media accounts, and website
- Began networking with some of the area’s largest companies to understand their security needs
- Began recruiting key employees
KB Security’s Services
Businesses can sign up with one of our flexible contract programs when hiring our security services. We also offer a discounted trial period for those who are considering a long-term contract and want to test out our services before signing.
Industry Analysis
With increasing illegal events, terrorism, and fraudulent activities happening all around the world, the demand for professional security is greater than ever. Every establishment needs some form of security, whether it be in the form of security professionals or in the form of cybersecurity. As the world continues to navigate its violent challenges, security professionals will be needed to protect important assets and respond to crisis situations.
The security industry has transformed substantially to meet this demand. In addition to hiring security professionals, many businesses also invest in security tech such as cameras, motion sensors, and software. Security companies that offer a mix of security personnel and technology can provide their clients extensive and tight-knit security options that puts their clients’ minds at ease.
According to research, the security industry is expected to grow at a compound annual growth rate of 8% over the next 10 years. This is substantial growth, which shows just how essential the industry will be in the coming decade. Businesses like KB Security will continue to be in high demand and very profitable.
Customer Analysis
Demographic profile of target market.
The demographics for San Antonio, Texas are as follows:
Customer Segmentation
We will primarily target the following customer segments:
- Individuals
- Local businesses
- Government organizations
Competitive Analysis
Direct and indirect competitors.
KB Security will face competition from other companies with similar business profiles. A description of each competitor company is below.
Sky High Security
Sky High Security is a security company that was established in 2002. It provides a large team of security professionals specifically trained to protect high-value assets, such as museum collections and expensive jewelry. Their services include providing in-person officers as well as high-tech surveillance equipment.
Prime Security
Founded in 2003, Prime Security is the best security company in town for those looking for guard and patrol services. Prime Security aims to protect establishments and offer patrols to deter any unwanted visitors. The company has been highly successful and is the largest security company in the region.
First Responders Security
First Responders Security is the most popular security company for those who have more complex security concerns. They offer a wide range of services, including alarm response, theft prevention, and patrolling. Instead of hiring several companies to do several jobs, companies can depend on First Responders Security to manage all of their security concerns.
Competitive Advantage
KB Security will be able to offer the following advantages over their competition:
Marketing Plan
Brand & value proposition.
KB Security will offer the unique value proposition to its clientele:
- Professional security services
- Flexible contracts and a trial period
- Great security services at moderate rates
- Excellent customer service
Promotions Strategy
The promotions strategy for KB Security is as follows:
KB Security understands that the best promotion comes from satisfied customers. The company will encourage its clients to refer other businesses by providing economic or financial incentives for every new client produced. This strategy will increase in effectiveness after the business has already been established.
Social Media
KB Security will invest heavily in a social media advertising campaign. The brand manager will create the company’s social media accounts and invest in ads on all social media platforms. It will use targeted marketing to appeal to the target demographics.
Website/SEO
KB Security will invest heavily in developing a professional website that displays all of the features and benefits of KB Security. It will also invest heavily in SEO so that the brand’s website will appear at the top of search engine results.
Direct Mail
KB Security will blanket businesses with direct mail pieces. These pieces will provide general information on KB Security, offer discounts, and/or provide other incentives for companies to use our services.
KB Security’s pricing will be on par with competitors so clients feel they receive great value when hiring our security services.
Operations Plan
The following will be the operations plan for KB Security.
Operation Functions:
- KB Security will be owned and operated by Keith Baldwin. Keith will oversee the general operations of the company.
- Keith is joined by Jeffrey Liebowitz, who will oversee all financial and accounting aspects of the business, such as accounts payable and receivable, payroll, budgeting, forecasting, and cash flow analysis. Jeffrey will also manage all tax obligations and licensing for KB Security.
- Keith is also joined by Felicia Monroe, who will oversee all marketing and communications for the business. She will handle all in-client calls, appointments, networking, and follow-up. She will manage all advertising aspects with flyers, emails, social media, and the SEO process.
- Keith will hire an Administrative Assistant to help him with general administrative and operations tasks.
- Keith will also hire an extensive staff of security professionals that will help his clients with their security needs. He will also provide these professionals with training as necessary.
Milestones:
KB Security will have the following milestones completed in the next six months.
- 8/1/202X – Finalize contract to lease office space.
- 9/1/202X – Begin build-out and design of staffing agency office.
- 10/1/202X – Begin social media and website advertising campaign.
- 11/1/202X – Attend large industry networking events.
- 12/1/202X – Hire key employees.
- 1/1/202X – Grand opening of KB Security.
Financial Plan
Key revenue & costs.
KB Security’s revenues will come primarily from charging clients for its security services. Depending on the contract in place, KB Security may charge an hourly fee per professional working for the client or a flat fee per month.
The office lease, equipment, supplies, and labor expenses will be the key cost drivers of KB Security. Ongoing marketing expenditures are also notable cost drivers for KB Security, especially in the first few years as the company establishes itself in the market.
Funding Requirements and Use of Funds
Key assumptions.
The following outlines the key assumptions required in order to achieve the revenue and cost numbers in the financials and pay off the startup business loan.
- Year 5: 110
- Office Lease per Year: $100,000
Financial Projections
Income statement, balance sheet, cash flow statement, security company business plan faqs, what is a security company business plan.
A security company business plan is a plan to start and/or grow your security company business. Among other things, it outlines your business concept, identifies your target customers, presents your marketing plan and details your financial projections.
You can easily complete your Security Company business plan using our Security Company Business Plan Template here .
What are the Main Types of Security Company Businesses?
There are a number of different kinds of security company businesses , some examples include: Crisis management, Security guards, Surveillance company, and Security patrol.
How Do You Get Funding for Your Security Company Business Plan?
Security Companies are often funded through small business loans. Personal savings, credit card financing and angel investors are also popular forms of funding.
What are the Steps To Start a Security Company Business?
Starting a security company business can be an exciting endeavor. Having a clear roadmap of the steps to start a business will help you stay focused on your goals and get started faster.
1. Develop A Security Company Business Plan - The first step in starting a business is to create a detailed security company business plan that outlines all aspects of the venture. This should include potential market size and target customers, the services or products you will offer, pricing strategies and a detailed financial forecast.
2. Choose Your Legal Structure - It's important to select an appropriate legal entity for your security company business. This could be a limited liability company (LLC), corporation, partnership, or sole proprietorship. Each type has its own benefits and drawbacks so it’s important to do research and choose wisely so that your security company business is in compliance with local laws.
3. Register Your Security Company Business - Once you have chosen a legal structure, the next step is to register your security company business with the government or state where you’re operating from. This includes obtaining licenses and permits as required by federal, state, and local laws.
4. Identify Financing Options - It’s likely that you’ll need some capital to start your security company business, so take some time to identify what financing options are available such as bank loans, investor funding, grants, or crowdfunding platforms.
5. Choose a Location - Whether you plan on operating out of a physical location or not, you should always have an idea of where you’ll be based should it become necessary in the future as well as what kind of space would be suitable for your operations.
6. Hire Employees - There are several ways to find qualified employees including job boards like LinkedIn or Indeed as well as hiring agencies if needed – depending on what type of employees you need it might also be more effective to reach out directly through networking events.
7. Acquire Necessary Security Company Equipment & Supplies - In order to start your security company business, you'll need to purchase all of the necessary equipment and supplies to run a successful operation.
8. Market & Promote Your Business - Once you have all the necessary pieces in place, it’s time to start promoting and marketing your security company business. This includes creating a website, utilizing social media platforms like Facebook or Twitter, and having an effective Search Engine Optimization (SEO) strategy. You should also consider traditional marketing techniques such as radio or print advertising.
Learn more about how to start a successful security company :
- How to Start a Security Company

Start a Security Training Business
- 180 comments
- 44,689 views
Though there are countless business opportunities, the one that remains unique is the security training business. Your business will have increased attention due to the demand for security personnel everywhere. Have the right approach and the perfect time to begin earning good profits.
- Google Share
How do you train security guards or law enforcement individuals? It is an important aspect that seeks the attention of every individual when being prepared by your center.
The business meant for training security staff remains a knowledge pool for them. It works like a platform for high-performing security professionals to get them trained and keep involved in various areas they serve, including healthcare, technology, transportation, business, and locations for entertainment, as they need well-trained security professionals. Chalk out a plan before starting this business and think of managing them. Training schedule needs to be prepared effectively besides introducing newer training aspects to the best level.
Realistic Approach
The level of satisfaction every individual feels after getting trained by your security training center plays a crucial role in turning such a business successful. Keep current government regulations in mind and complete legal formalities. People getting trained from you must become eligible for security guard card licensing. They have to face challenging phases in the practicality involved in their roles as security professionals. You will get success in this fast-growing industry only if your approach is focused and the training given is worthy of making one suitable for playing an influential role in security .
Similar Articles
- Getting Contracts for Security Business
- Business Security Tips
Expand Your Business
Individuals would approach you for training. As an entrepreneur, you can focus on various security firms for corporate training assignments. It will be beneficial for the uninterrupted growth of the business. Have a team of experts who trains people satisfactorily. At the same juncture, apply various mechanisms to get clients regularly to keep your trainers engaged. Utilize the resources without any halt. The next noticeable factor is managing security effectively.
Your company will work as a consulting firm to train a security team who will get them involved in various places later on. Some minor aspects, like providing complete information about security contracts and guiding clients to learn about security proposal templates in detail, are critical related services. Best networking through franchises keeps your presence everywhere.
Good Governance
Governance and zeal to train people at the best level are vital aspects that must be focused on managing a security training business. Apply unique but workable methods and available sources to advertise your business. Always have a keen eye on the costing structure. The charges you quote for this service should be well planned. Keep your rates reasonable so that nobody feels financially burdened while joining your security training center. Other essential factors are insurance-related matters, security guard service contract rules, and a better understanding of the field reports and job applications for future role-playing.
Recommended Articles
- How to Start a Security Agency Do you have experience in providing security services? How about starting your own business guarding homes, offices, malls, and schools? Learn how from our basic guide to opening this business.
- Starting Your Own Private Security Firm In opening your own private security firm it is essential to have a good background with regards to either business management or more importantly, security.
180 Comments
- Carly said on January 8, 2011 Thank you, for that post I enjoyed it and it helped me a lot. I want to know what certification or license do I need to start a 8/16 hours security training course business. Please help. Thank you. Carly
- HARISH.Y.R said on April 21, 2011 Hi, thank you for the post its very much true b'coz i am already running a security business by name BLACKCAT DETECTIVE SERVICES my business is located in bangalore, karnataka, india. now i own a 2 acre 30guntas land in outskirts of bangalore so please tell me what all registration to be followed to start up a security training centre please respond me i really require this please keep informed. thanking you, regards, harish.y.r. cell:+919880433233
- Tyler Aydelotte said on May 4, 2012 Bellingham, Washington 98225. What are the requirements, such as Certification, Licensing, and Washington regulations, etc.
- Lwanda bikitsha said on July 15, 2012 I would like to start a security training bussines at lusikisiki the small town in eastern cape
- santosh pandey said on August 4, 2012 Dear sir, i want to start Security Training institute and placement agency business in Lucknow,UP,in India. I want to know that what are the legal documents are required to start the same. Please reply ASAP. Thanks ! Santosh Kumar Pandey, 88967400479, 08948261965
- Terri Lane said on September 17, 2012 I want to start a security training facility in Orlando, Florida. Can you give me any advice that I can use to get me started?
- masonwabe said on October 17, 2012 i want to start security training business at kraaifontein(capetown). can you give me advice.
- masonwabe said on October 23, 2012 i want to start security training in kraaifontein. what do i need to do and where can i register?
- MARSHALL said on October 31, 2012 BUSINESS LOCATION: HYDERABAD, Andhra Pradesh, India phone no: +91 98661 34695 We are planning to setup a training institute in hyderabad for security personnel across various levels. Please let me know the documentation /legalities /licenses that we need to setup the same. Are there state specific rules and regulations to setup a training institute? Please give advice... thank you in advance.
- Best Sithole said on November 17, 2012 I want to start a security training at TZANEEN in Limpopo province and NKOWANKOWA
- Ricardo Sherwin said on November 23, 2012 hi, I am looking for serious investor to start a "SECURITY Agency" in Hyderabad. i am an Ex defense person with Experience in running this business in India and many years of service in Dubai. I am in Dubai at the present and willing to discuss. Please contact me on + 971527183017 Cheers
- eliya said on December 7, 2012 hi, i would like to know what should i do to start my own security training center. between East London and mthatha, Eastern Cape
- cphiwe said on January 17, 2013 I want to start a security training at durban. so what document must be needed?
- Thelma said on January 20, 2013 i want to start my security training center around nebo. what qualification needed
- Buffy said on January 20, 2013 I want to start a Security training school in Los Angeles, Ca or San Bernardino, Ca in the United States. thank you
- VILAS P RAUT said on January 21, 2013 In Mumbai Andheri East, Maharashtra India. How to start Security Training Agency
- joseph motha said on February 6, 2013 hi i want to start a security training, what are the formalities.
- Joseph thobegane said on March 29, 2013 Hi i want to open security training in rustenburg(ledig) what qualification do i need
- Donald said on April 10, 2013 Please send info on the requirements to start a security training business. Thank you Heritage Connection
- khura said on April 29, 2013 what documentation needed to start security training business ,how long it will take & how much is it?
- onuorah Nwogalanya said on May 3, 2013 I live in the states but I am anticipating building a training outlet for security guards in nigeria. How do I go about it. ( training school)
- Mathiase said on May 7, 2013 Hi, i am a psira grade c registered so i want to start my own security training Gauteng carletonville khutsong location. what do i need to start? my cell no 078 649 4474: Thank you
- s. Mbawu said on May 15, 2013 Hi there, i have an idea of starting a Security Training Center. How possible can this be, because I'm a public servant? If i can, what, where and how can I get started? I am in blue Downs, Western Cape. My cell no. is 0837184842, please help me out, thank you.
- Lontay said on May 16, 2013 California United states - what do I need to start my own security training business
- Mathew P. George said on May 18, 2013 I would like to start a Security Guard Training Institute and a placement centre in Kerala. Kindly information me what is the preliminary steps I have to take & what certification I should get from the Govt. Thanks.
- kotstuff M. Mothobeki said on May 18, 2013 Hi, I want to start a security training institution, so what the document needed and which kind of material. Limpopo, Tzaneen
- Lonwabo said on May 23, 2013 my business is located in Century City, Cape Town. I am currently running a construction company, with a view of doing security training. what would be the best way(s) of doing this?
- Tintswalo Mathe said on June 4, 2013 Hi! I would like to open a security training in tzaneen in limpopo' so i would like to know which qualifications must i provide to open this institute? ur reply would be much appreciated.
- Maureen Reu said on June 23, 2013 I want to start a Security training center for small security firms. I have started a proposal but still need to complete a training package and budget format
- lutendo given said on July 18, 2013 hi the long time i need to open a security training school so i dnt know even where can i get the all certificate to start this business please help me for information and a number where can i call i need it very fast
- nickey van zyl said on July 29, 2013 Walvis bay namibia, where do i register such company and will such training be recognizable
- Patricia Jacobs said on August 14, 2013 Hi, thx for the above explanation. Oil would like to start a security training business, please advice what are the requirements. Thx & Regards, Miss P.M Jacobs
- kenneth makhokha mathabi said on August 16, 2013 what are the qualifications needed to open your own security training centre
- ashok dubey said on August 18, 2013 hi, i have 5 acres land and i want to open training centre business in this land can you please help me out to give the full information and requirement about training centre. Thanks and regards, MR.ASHOK DUBEY from jabalpur madhya pradesh
- Thapelo Petrus Moalusi said on August 29, 2013 Thapelo Moalusi, I live in Orange Farm extension, I'm currently working as a security guard and I have four(4)years experience, I want to start my own security training academy so I want to know which qualifications needed and were can I get them. tnx very much your help will be highly appreciated.
- siphiwe sefatela said on October 11, 2013 hi .i will like to start my own security training company, what are there procedures there of. what qualification do i need, where do i register, etc.
- Godwin Egbekun said on November 9, 2013 I WANT TO KNOW WHAT I NEED TO KNOW AND DO TO START 8HRS & 16HRS SECURITY GUARD TRAINING CENTER. THANK YOU
- Karabo said on December 15, 2013 Hi I need a informetion how to start a security training business.
- James Harris said on February 16, 2014 I wish to open a security training center in Orlando, Florida.
- Bulelani Dale said on February 26, 2014 Hi i'm Dale Nkonyeni from PE and would like to know what steps do I need to follow starting a security training academy.thanks.
- Bulelani Dale said on February 26, 2014 Hi dale from Pe Eastern Cape want to start a security training academy what steps do I take have a security background was once in the industry.
- Bulelani Dale said on March 9, 2014 Hi i'm from PE eastern cape and would like to start my own training academy and replacement centre what to do help my email add:[email protected].
- david guerrero said on March 31, 2014 Hi, I wanted to know how to start a security school for people who want to get into security.
- MLUNGISI said on April 7, 2014 i want to start my security training centre, plz sen me info. i dont know where to start
- KITARA JUSTE said on April 7, 2014 Hi... Thanks so much for your post. I would like to start a security training class in Orlando, Fl. Would you be able to send me a list of state requirements and things that I need to do in order to get started? Or even just the information on how to go about finding this out myself. Thank you...
- Mhlonishwa said on April 17, 2014 Hi, I want to establish a security training school in Vereeniging. I want to know what qualifications and requirements are needed to start this types of business. You can tell me more things which are important I need to know. Thank you
- Isaac Makhura said on May 1, 2014 I am grade B psira registered and have compitancy but would like to start my security training school and i have almost 100 people waiting for me to start training. which certificate or license is required. here is my email address: [email protected] can someone help about where to register.
- selwane makgajane sipho said on June 5, 2014 Hi, i have grade B psira reg i want to start my security training school, i don't know where to start. Plz send me info
- Sam Hanekom said on June 21, 2014 Good day. I live in Cape town South Africa. I already register the name of my company but need help to drawup a business plan.
- mandla said on July 6, 2014 hi i want to know how to start a security training center.
- siyabonga nkonyeni said on July 9, 2014 hi i'm siyabonga nkonyeni i want 2 open a security training center i have 10yrs of exp in sec industry and hv grade a, reaction/armed response, firearm certificate, basic ambulance attendant, n4&n5 in human resource management, grade 12 tx.
- Christian Tlhakudi said on July 10, 2014 Mornings Sir/Madam. I would like to start training academy, but clueless on how to get started with the registrations etc...I would kindly appreciate your assistance in providing me with tips or maybe steps on how to get started. Kind regards C.Tlhakudi
- benedict magalw said on July 26, 2014 i need an advices to start a security training school. i am a registered facilitator so i want to open the academy around Burgersfort please help me.
- Felix akpona said on August 14, 2014 What are the requirements to set up a security training school in new york
- Lebogang Molapo said on August 27, 2014 i want to start a security training, my biggest problem is where to start, what are the requirement to cn start. please give me info about d afore mentioned
- sabelo zikhali said on November 20, 2014 hi i would like to know what is needed if i want my security training academy ?
- Latonya Green said on January 12, 2015 Hello how do I start a security training business in the United States in Newark, NJ what would I need to get started
- nonzwakazi said on January 14, 2015 hi i am currently working as an aviation security, can you please help me on which step must i follow i wan to open a security training centre in Eastern cape
- elvis phoseka said on January 15, 2015 I'm residing in Witbank, MP and would like to start a security training academy. What are the procedures?
- Justice Mkhonza said on January 25, 2015 I want to start my own security academy or training centre, so i hv no idea where, how to start business i need to know if the is any legal documents or licensed needed and where to find them thnx
- Peter Ilau said on January 26, 2015 Hi, I want some guidance in developing a Security Training Academy Business Plan, and appreciate if you have some templates that could help to start and progress the Business Plan quicker. I will adjust it to allow for our National laws and regulation in line with the Security Industry Act in my country. Thank you!
- Kgabo said on February 16, 2015 Hi, may you please advise me on how to start a security training college in jhb Gauteng South Africa.
- OARABILE said on February 20, 2015 Hi i would like to know what are the requirement to open up a security training institute, and where can i obtain the required particulars. please help!
- Clifton Wheeler said on February 21, 2015 Hello, I have a location and the material to start training security guards here in NW Fl. This would be the only training site in 3 counties. The problem I am having is finding money to help get it off the ground.. could you help point us in the Right direction..
- samuel said on February 23, 2015 I want to start a security training institution around bochum, what steps do I have to take?
- Phineas Moorosi said on March 8, 2015 Can you help about information about how to open security training security
- Abegail Olayi said on April 9, 2015 I want to open a Security Training Academy ,I want to know which steps must I take ? and the requirements I need to have
- sydwell mabuza said on April 20, 2015 Hi I want to start a business of a security academy in mpumalanga. my region is nkomazi so I would like to know what should I do to open it.
- lerato said on April 28, 2015 Yebo I want to open a security training academy, i want to know which steps must I take and the requirements I must have
- Edmund said on May 8, 2015 Good evening. please help me with information regarding the starting and registration of a security training centre in gauteng, South Africa. Thank you!
- Lezothi La Lekoko said on May 8, 2015 Hi, I want to run a security training center. I want to know what requirements to have, certification for forth. My address: Galeshewe, Kimberley, South Africa, ZA
- Nkosana Tukana said on May 12, 2015 Hi, I really need to start a security training centre as I'm a security my self. and just think is time to start something of my own as felt in love with the idea more and more. please help.
- winile siphethukana said on May 16, 2015 I have started my all purpose co but I would love to stick on training the security officers and please tell me where to go and what do I need to have.
- winile siphethukana said on May 16, 2015 Hi I am living in Capetown tokai area and I would love to start my security academy in the area as it is in demand due to crime rate.
- EMELIA ASSETS(PTY)LTD said on May 18, 2015 Hi, I AM THE YOUNG AMBITIOUS VISIONAL ENTREPRENEUR, REGISTERED PRIVATE COMPANY, NOW WE WISH TO EXPAND BY OWNING THE HIGHLY DEMANDED SECURITY TRAINING COLLEGE, KINDLY HELP US TO ACHIEVE OUR GOAL. CONTACT NO: 0797129551 /KZN/SOUTH AFRICA, 0R 0748122779
- MARK said on May 31, 2015 hi, YOU NEED SOMEONE TO HELP YOU TO OPEN A SECURITY TRAINING CENTRE OR NEED THE MATERIAL CALL ME MARK 0799261073. I STAY IN KUILS RIVER (CAPE -TOWN)
- MASIWAKHE BANGILIZWE said on June 4, 2015 masiwakhe has grade B security i want to make my company for security training. but i need some money and equipment my no is 0783811332
- veinent said on June 8, 2015 Hi I need to open a security training institution, so i like to know the required documents and bills to be paid. My no is 0783105881. Positive feedback will be highly appreciated
- Godfrey mkhatshwa said on June 11, 2015 Hi at daveyton i want to start my own business security training i want information to start
- Lucky mkhatshwa said on June 11, 2015 Hi i want to start my own business security training center at daveyton benoni i need information how to start my business my cell number is 0740941377 or 0793177744
- Mpho said on June 11, 2015 Hi i want to start security training center i want to know about requirement please
- Lucky mkhatshwa said on June 11, 2015 Hi i'm godfrey i want info about security training center and requirement of the business
- ike said on June 23, 2015 I am operating a private security firm for some yrs now, am about to start security training center here in Ghana, I want a partner, interested person can contact me +233 270059400 or [email protected]
- Dale Smith said on June 26, 2015 I would like information on how to start a security training academy in California
- BONGA LESO aka KHOZA said on July 2, 2015 I WANT TO START SECURITY TRAINING IN HAMMANSKRAAL AND MOKOPANE, WHAT MUST I HAVE TO QUALIFY?
- Sudershan kumar said on July 29, 2015 Want to start Training academy for Security guards in India. Pl let me know how to go about it. Thank you
- vutomi said on August 10, 2015 I want to start a security training college in Giyani, what must I have to qualify.
- Zandile Ncube said on August 22, 2015 I'm at KZN Eshowe; I want to start security academy; pls help what document is needed to qualify
- St Felix. Albert said on August 25, 2015 100 n w 189, terr miami Florida 33269
- Calvin Dlamini said on August 28, 2015 Hi! My name is Calvin from Port Shepstone (kzn). I would like to know as to what is the procedure to starting a security guard training school and where can I get the necessary certificate. Thank you
- Jerome c Baadjies said on August 29, 2015 Hi, I want to start my own security training facility in knysna, western cape, south Africa. I dont have a business plan in place but know exactly what I want to do. my goal is to help put the security industry back on the peoples lips for it has lost positive attributes. If you could help in this regards and be in contact. My cell number 061 018 9041 and can be reached at any time.
- Reese Powell said on September 12, 2015 I just recently retired from the DOJ and I am a certified pistol instructor, chief range safety officer, active tactical shooter and a commando Kraft maga expert. I own 5 acres of land in Augusta WV. How can I obtain licensing for a security training school.? Please send me any information that could possibly get me started.
- seema said on September 30, 2015 sir,i want to start a security training center.which documents is being required.i want to know,please give me whole information. my mobile number is 7737083726
- IM Majola said on September 30, 2015 I would like to know the legal,standard and general requirements for starting a security training school.I work as an A grade security officer at present.I stay in Durban South Africa.
- Ratau Clement said on October 2, 2015 I have security company located in Groblersdal,limpopo province in south africa And I am providing security services to various market and I want to start security training center and would like to know how and where to start step by step.Can you provide me with requirements in order to qualify.
- Marvin Basson said on October 12, 2015 I would like to start a K9 tracker security services company as well as a training college for tracker security officers and K9 tracker dogs.I am also looking for managing partners for the business.I have more than 20 years experience as a tracker, K9 tracker dog handler,tracker instructor, armed response security officer,security operations and special security unit experience.I am from Namibia.
- mothusi diteko said on December 15, 2015 I want to start a security college in Botswana.I am currently in the uk.I would to south Africans as they vast experience.Also i have to look at law governing setting up colleges.Thanks for the eye opening.
- martin kekana said on January 6, 2016 Good day Please let me know what are formalities to setup security training.martin from tembisa.
- Mxolise Dastile said on February 4, 2016 I will like to register and operate a security training academy around my area Hartswater in Northern Cape province. Please assist with advice and ideas
- Minentle said on February 15, 2016 Hi I'm Minentle and I'm staying In Grasmere, I would like to open a training centre, what do I need to qualify for that because at the moment the only thing that I have is grade "A" and Psira registered. please help
- Franchise Opportunities
- Wholesale Business Opportunities
- Small Manufacturing Business
- Farming Business Ideas
- Unique Business Opportunities
- Shop Business Ideas
- Small Business Opportunities
- Startup Company Ideas
- Home Based Business Opportunity
- Rural Business Opportunities
- Tips for Buying and Selling
- Starting Rental Business
- Ideas for Small Business
- Free Business Ideas
- Internet Business Ideas
- Store Business Opportunities
- Entrepreneur Business Idea
- Retail Store Ideas
- Service Business Ideas
- Service Businesses to Start
- Top 100 Consulting Business Ideas
- Advice for Small Business
- Financing a Small Business
- Restaurant Business Opportunities
- Small Business Articles
- Business Marketing and Advertising
- Repair Business Opportunity
- Professional Career Opportunities
- Business Insurance Information
- Instructor Guides
Popular Articles
- Starting a Motorcycle Courier Business
- What Is Internal Customer Service
- Starting a Water Heater Installation Service Business
- Starting a Bill Payer Service Business
- Startup Auditing Business
- Starting a Car Service Business
- How to Start a Motorcycle Detailing Business
- Starting a Security Guard Patrol Service Business
- Starting an Early Intervention Agency
- How to Start a Rice Dealership
Business Plan for Investors
- Bank/SBA Business Plan
- Operational/Strategic Planning Services
- L1 Visa Business Plan
- E1 Treaty Trader Visa Business Plan
- E2 Treaty Investor Visa Business Plan
- EB-1 Business Plan
- EB-2 NIW Business Plan
- EB-5 Business Plan
- Innovator Founder Visa Business Plan
- Start-Up Visa Business Plan
- Expansion Worker Visa Business Plan
- Manitoba MPNP Visa Business Plan
- Nova Scotia NSNP Visa Business Plan
- British Columbia BC PNP Visa Business Plan
- Self-Employed Visa Business Plan
- OINP Entrepreneur Stream Business Plan
- LMIA Owner Operator Business Plan
- ICT Work Permit Business Plan
- LMIA Mobility Program – C11 Entrepreneur Business Plan
- USMCA (ex-NAFTA) Business Plan
- Franchise Business Plan
- Landlord business plan
- Nonprofit Start-Up Business Plan
- USDA Business Plan
- Cannabis business plan
- Ecommerce business plan
- Online boutique business plan
- Mobile application business plan
- Daycare business plan
- Restaurant business plan
- Food delivery business plan
- Real estate business plan
- Business Continuity Plan
- Pitch Deck Consulting Services
- Financial Due Diligence Services
- ICO whitepaper
- ICO consulting services
- Confidential Information Memorandum
- Private Placement Memorandum
- Feasibility study
- Fractional CFO
- How it works
- Business Plan Examples
Private Security Company Business Plan Template
MAR.20, 2017

Do you want to start a Private Security business plan?
Security is one of the biggest concerns in the world right now. It has always been important to keep not only valuable items but also information secure and out of the wrong hands. Therefore, there is a significant need for investment in the business plan related to private security firms.
Developing a business plan for a security company involves much more than coming up with a cool slogan. Much like a window cleaning business plan , you will need to learn how to write a business plan for a security company.
Here, we are presenting the business plan for Diamond Phase, a private security firm. You can use this business plan to develop a plan for your own business. So, whatever the scale of your business, this template can act as a great help to design a successful business model.
Executive Summary
2.1 about the business .
Diamond Phase will be a security firm started by Jacque Hail. The firm will provide help with business planning process for security systems in different residential and commercial sectors. The company will offer a wide range of services, from securing full-fledged security systems for whole buildings to offering small-scale security services for a particular office or space.
2.2 Management of Private Security Firm
Business plans for security companies need to be very thorough as they provide a very important service. The business needs to be well-managed to ensure proper functioning after the launch. This can be achieved through a security company business plan template like the one given here.
You can also refer to professional business plan services to get an operational plan developed. If you possess some experience and you want to develop your plan on your own, you may take guidance from this security guard company business plan.
2.3 Customers of Private Security Firm
The customers of Diamond Phase will belong to different scales of operations. As such, our customers for a basic business plan security are as follows:
- Residential Community
- Small/ Large Businesses
- Jewelry Stores
- Highly Sensitive Areas
2.4 Business Target
The target of Diamond Phase is to establish itself as a major player in the private security business in Portland. We want to be known as the most efficient security solution in Portland within two years of the launch.
Furthermore, the financial targets we want to achieve within five years of operation are as follows:
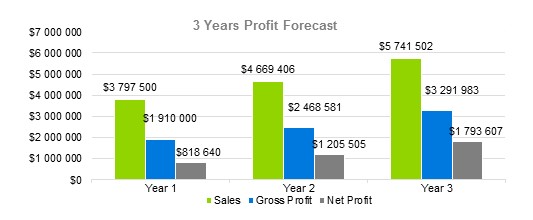
Company Summary
3.1 company owner.
The owner of the company will be Jacque Hail. Jacque worked as a security manager in a top security firm for two years. Before this, he attained his education in computer forensics and networks. He realized that he could utilize his experience and education to start a new security firm of its kind. And thus, Diamond Phase was ideated.
3.2 History of Diamond Phase
While working as a security manager, Jacque saw that a lot of his clients required not only physical security measures but also computer network safety. Considering the rapid increase in the penetration of technology in every sector of the market, Jacque decided to present a business model that improved upon existing physical and computer security businesses.
3.3 How the Private Security company will be started
Step1: Ideate the Business
The first part of any security business plan sample is the description of the company that you are trying to start. Nothing happens without an idea. Therefore, Jacques decided to build on his dream and create a concrete idea for his business plan of a security company.
Step2: Research and Analysis
The next step to starting a business is to look into your market. This will help you filter out your major competitors and entry points in the market which can help you get ahead in the competition. As part of this security company business plan pdf, Jacque did comprehensive research about the security industry to identify his competitors.
Step3: Register the Business
Once Jacque knew that his business idea was viable, he looked into as many security company business plan examples as he could to learn the process of registration. He not only registered the company name to the state but also registered the space for a main office in the Portland commercial center.
Step4: Go Online
One of the best ways to advertise a business is through online ads and social media. Therefore, Jacque decided to hire a sales team with a social media sub-team to help with advertisement and the online existence of the company.
Step5: Know Your Finances
Another important part of any business plan, even a plumbing company business plan, is the financial planning of its operations. To manage this, Diamond Phase will have a financial plan developed by a business consultancy firm.
The services of a business are its basis and the reason it exists. Before you start writing business plan for a security service company, you need to be very clear about the types of services you will be offering. This will not only help you to properly write a business plan for a private security company but also guide you throughout the operational years of your business.
To write a private security business plan for his company, Jacques decided to lean back on his market research. It is because he knew that each sample business plan for security services decides its services according to market needs. From this research, he decided upon a list of services to include in this template to learn how to start a security company pdf.
The general services for a private security firm are listed below. Some of these are identical to those mentioned in the locksmith business plan .
- Security Guards
The biggest service offered by Diamond Phase will be to provide teams of security guards for the maintenance of a manual security system in a commercial or residential area. The number and requirements of these guards will be agreed upon by the company and its clients. The guards will be hired and trained by the company and will work on a contract basis for our customers.
- Automated Setups
Many places don’t require huge teams dedicated to security. For instance, security concerns in residential areas and homes can be handled by automated systems with just one physical team on site. To promote the efficient use of resources, Diamond Phase will provide state-of-the-art automated security systems to its customers.
Not only will the company provide trained security personnel, but it will also provide training for the guards hired by our customers. The customers can hire us to provide regular sessions for proper training of their staff in electronic as well as manual security niche.
- Network Security
As part of its hybrid business model, Diamond Phase will offer not only physical and automated security but also network security and maintenance personnel if needed by its data-sensitive clients.
Marketing Analysis of Private Security Company
Excellent work.
excellent work, competent advice. Alex is very friendly, great communication. 100% I recommend CGS capital. Thank you so much for your hard work!
A security guard business proposal needs to contain everything from the preliminary idea of the business to the basic viability guarantees of the business. To establish a security business star up , you will need a comprehensive security systems business plan that contains all the details to make the business viable for existence.
For his business plan for a security company , Jacque used his market research to build a strong case for starting Diamond Phase. If you want to learn how to start a private security company from scratch, you can follow this business plan for a security company pdf. You can also learn the basic idea from other plans, such as a dog training business plan .
Here, we will present the marketing analysis and details for Diamond Phase, through which you can learn how to open up a security company that can succeed.
5.1 Market Trends
According to Statista, the private security industry in the US already has a market share of $32 billion, which is a $1 billion increase from 2019. The market is consistently growing with an increase in valuable projects, businesses, and residential areas. Therefore, this is the prime time to learn how to start a security agency as it will help the new business become a part of the growth spurt.
5.2 Marketing Segmentation
The customers targeted by Diamond Phase are as follows:
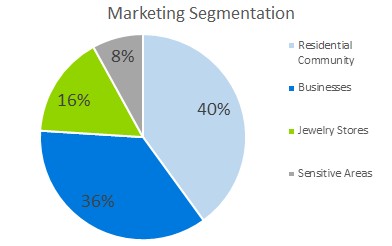
5.2.1 Residential Community
The main customers of our company will be residential areas that require not only an automated security system in each home but also centralized security teams in place to deal with a breach. We expect to gain about 60% of our customer base from this domain.
5.2.2 Small/ Large Businesses
We will also provide automated systems, network security services, and small batches of guards to small and large businesses. Mostly, these businesses will require a few guards and a basic automatic security system linked to the police.
5.2.3 Jewelry Stores
Our company will also serve Jewelry stores that require a state-of-the-art automatic security system as well as an equipped security team that can respond in a short time.
5.2.4 Highly Sensitive Areas
Lastly, Diamond Phase is aware that there are warehouses and hidden locations that often need security. We expect to come into business contracts with large companies.
5.3 Business Target
- Establish ourselves as an efficient and versatile one-stop solution in the market.
- To attain a customer satisfaction score of 98% within the first 6 months.
- To slowly expand our client base to include multinational corporations.
5.4 Product Pricing
The prices of our products will be competitive with the market baselines. We will offer a wide range of services to choose from so that our clients don’t have to look towards any other firm for full-coverage security solutions.
Setting up a security firm can be tough from a market standpoint. Most places already have trusted firms that they use for security systems. So, it can be hard starting a private security company in such an environment. To deal with these hardships, Jacque decided to come up with competitive advantages from the very beginning. His compelling sales strategy and competitive advantages are given in this business plan of a security company.
So, just as a dog daycare business plan can help a dog daycare business prosper, a business plan targeted at a security firm can help it succeed as well. Therefore, if you want to learn how to start a private security firm, you can go through the plan developed by Jacque for Diamond Phase.
6.1 Competitive Analysis
- We have a versatile business that offers security in 3 dimensions: manual, automatic, and communication network.
- Our customers can get one-stop solutions at our company, eliminating the need for multiple security systems.
- We have systems in place for training clients’ own employees and guards.
6.2 Sales Strategy
- We will offer comprehensive security packages based on a client’s needs.
- The services of our security analyst to design the security system will be free for clients.
- We will offer a money-back guarantee in case of any issues within the first year.
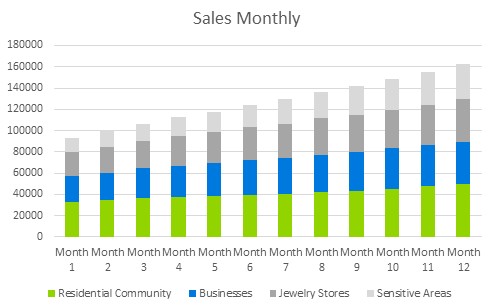
6.3 Sales Monthly
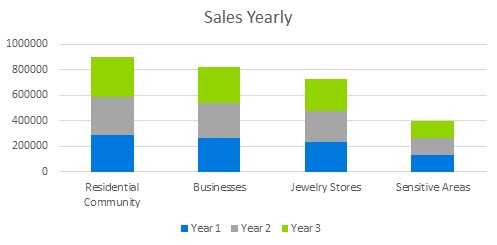
6.4 Sales Yearly
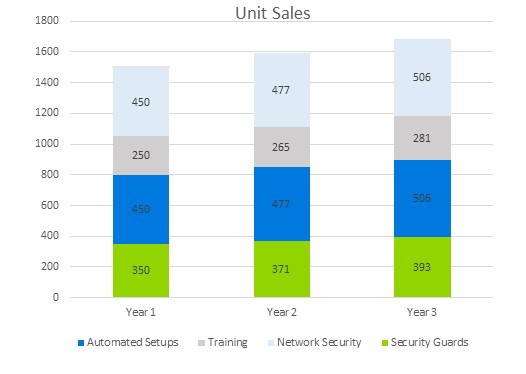
6.5 Sales Forecast
Personnel plan
When learning how to open up a security company, you need to go into details such as which type of workforce can help you maintain and run the business. Every private security company business plan contains these details.
The employees Jacque decided to hire for Diamond Phase are listed below in this business plan for a security company pdf.
7.1 Company Staff
- 1 Co-Manager to help in overall operations
- 20 Trained Guards
- 2 Sales Executives to promote sales
- 1 Accountant
- 1 Receptionist
7.2 Average Salary of Employees
Financial plan.
If you are new to the security domain, you may be wondering what you need to start a security company. The truth is, there are a lot of components that make a business plan security company successful. One of the essential components is the financial planning of the business.
Financial planning can include details ranging from how much it costs to start a security company to the rates for your services. For the financial planning of the Diamond Phase, Jacque dived deep into the profit vs. cost analysis of services to ensure the sustainable working of the business.
The financial plan for the Diamond Phase with all its details is demonstrated below for a better understanding.
8.1 Important Assumptions
8.2 break-even analysis.
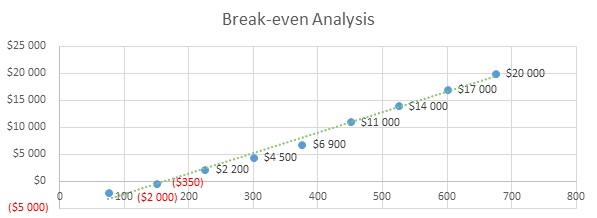
8.3 Projected Profit and Loss
8.3.1 profit monthly.
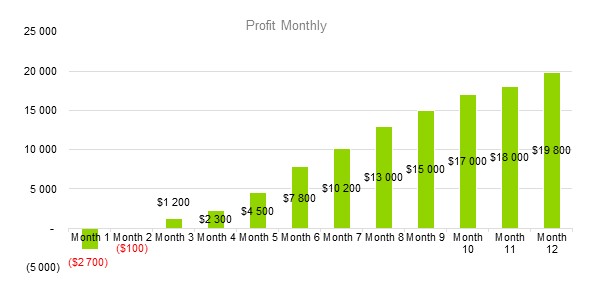
8.3.2 Profit Yearly
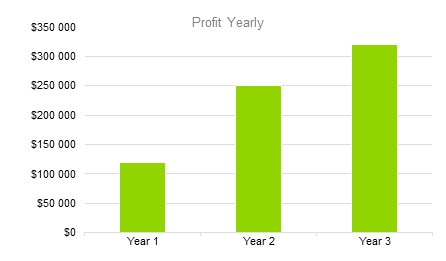
8.3.3 Gross Margin Monthly
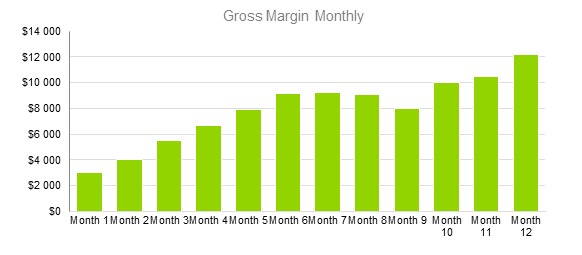
8.3.4 Gross Margin Yearly
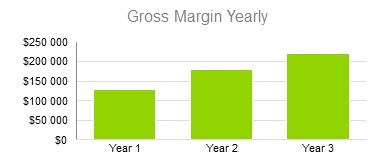
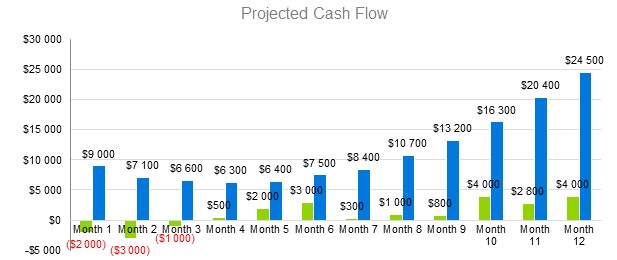
8.4 Projected Cash Flow
8.5 Projected Balance Sheet
8.6 business ratios.
- How do I write a business proposal for a security company?
You can learn how to write a business proposal for a security company through the example of a business plan for a security company given above.
- How do you write an executive summary for a security company?
An executive summary is an important part of all security company business plans. To write one, you can look into the security company business plan template given above.
- What are the goals of a security company?
The goals of a security company are dependent on many factors such as location, owner’s expectation, target market, investment, etc., all of which are demonstrated in the business plan for a security company.
Download sample a business plan for a security company pdf
OGSCapital’s team has assisted thousands of entrepreneurs with top-rate business plan development, consultancy and analysis. They’ve helped thousands of SME owners secure more than $1.5 billion in funding, and they can do the same for you.

Add comment
E-mail is already registered on the site. Please use the Login form or enter another .
You entered an incorrect username or password
Comments (0)
mentioned in the press:
Search the site:
OGScapital website is not supported for your current browser. Please use:

How to Start a Security Guard Company
This is a needed business because companies and individuals often don’t have the resources to perform their own security detail. Security guard services usually charge hourly fees for the services being provided. The prices charged will increase based on the number of security guards provided for the clients.
Learn how to start your own Security Guard Company and whether it is the right fit for you.
Ready to form your LLC? Check out the Top LLC Formation Services .

Start a security guard company by following these 10 steps:
- Plan your Security Guard Company
- Form your Security Guard Company into a Legal Entity
- Register your Security Guard Company for Taxes
- Open a Business Bank Account & Credit Card
- Set up Accounting for your Security Guard Company
- Get the Necessary Permits & Licenses for your Security Guard Company
- Get Security Guard Company Insurance
- Define your Security Guard Company Brand
- Create your Security Guard Company Website
- Set up your Business Phone System
We have put together this simple guide to starting your security guard company. These steps will ensure that your new business is well planned out, registered properly and legally compliant.
Exploring your options? Check out other small business ideas .
STEP 1: Plan your business
A clear plan is essential for success as an entrepreneur. It will help you map out the specifics of your business and discover some unknowns. A few important topics to consider are:
What will you name your business?
- What are the startup and ongoing costs?
- Who is your target market?
How much can you charge customers?
Luckily we have done a lot of this research for you.
Choosing the right name is important and challenging. If you don’t already have a name in mind, visit our How to Name a Business guide or get help brainstorming a name with our Security Guard Company Name Generator
If you operate a sole proprietorship , you might want to operate under a business name other than your own name. Visit our DBA guide to learn more.
When registering a business name , we recommend researching your business name by checking:
- Your state's business records
- Federal and state trademark records
- Social media platforms
- Web domain availability .
It's very important to secure your domain name before someone else does.
Want some help naming your security guard company?
Business name generator, what are the costs involved in opening a security guard company.
Costs for starting a security guard business are minimal. The largest cost is insurance, which can be up to $3,000 for a 6-month term. Legal and regulatory costs will run about $500. The cost for basic equipment and uniforms varies. If guards have their own firearms or force equipment, then the cost will be minimal. If not, they can range from just a couple hundred dollars for a used handgun to several thousand dollars.
Uniforms will run about $100 per guard or officer.
Some local and state laws require security companies to maintain an office. Minimize these costs by using shared-space small offices. A shared office will cost several hundred dollars per month, depending on where you live. Dedicated offices can run several thousand per month.
This is a business where having a large office isn’t important. Only get as much office space as you absolutely need.
Marketing materials for the new business will likely run $1,000 to $2,000.
Websites are another cost you should consider. They will run you between $300 and $500 for a basic website. Hosting should cost no more than $100 per year. In many cases, you can find hosting for much less.
What are the ongoing expenses for a security guard company?
Normal ongoing expenses for this business are minimal. Mostly, you’re paying for insurance, an office, a security team’s salary (and related expenses).
Who is the target market?
Security companies typically work with wealthier clients who have valuable property to protect. These clients are usually businesses that guard valuable information, tangible items, or individuals within their premises.
On rare occasions, a company might be hired to protect an individual, like a local or national celebrity, a political figure, or CEO of a large company.
How does a security guard company make money?
Most security companies charge clients an hourly rate or flat fee for services. Larger security guard companies have corporate or commercial clients. The ideal client is one who signs a multi-year service contract. However, when you’re just starting out, these types of clients are hard to get.
Security guard companies tend to have a range of prices, depending on the services they’re offering. For unarmed security, you can charge between $10 and $25 per hour. For armed security, you can charge from $35, up to even $100, if it’s a special or high-risk event.
However, this is not the only way to charge clients. Security contracts, including both short and long-term contracts, can fetch a much higher total fee for services. Some companies will charge “by the job,” in which case the company is charging a contract fee. These fees can amount to several thousand dollars per contract.
In some cases, a client pays monthly, semi-annually, or annually for services and renews the contract for many years. This is an ideal scenario, and produces stable long-term income for the business.
Per-contract fees are usually reserved for established clients, however.
Another factor affecting what you can charge clients is the number of security personnel on-site for a job. Most companies charge more if there are more guards on-site.
How much profit can a security guard company make?
Security companies can generate approximately $40,000-$60,000 per security guard, per year. If you hire a team of 5 security guards at startup, then you may be able to clear $300,000 in revenue. Net profits vary based on your insurance costs, labor costs, and regulatory costs in your state.
How can you make your business more profitable?
Most security businesses could benefit from specialization and charging higher prices. Closing higher-paying clients will also bring in more money.
For example, instead of offering generic security services to a local business, try specializing in bodyguard services, mall services, or catered event services for politicians. If your company becomes known for providing security for high-profile clients, you’ll have very little competition.
Also, a security guard typically has all the skills necessary to provide bodyguard services as well. However, the term “bodyguard” typically connotes a larger, muscular person who is capable of intimidating potential threats to the client’s person. If you feel as though you can provide these services--which typically involve protection of individual people--this is an effective way to increase clientele.
Want a more guided approach? Access TRUiC's free Small Business Startup Guide - a step-by-step course for turning your business idea into reality. Get started today!
STEP 2: Form a legal entity
The most common business structure types are the sole proprietorship , partnership , limited liability company (LLC) , and corporation .
Establishing a legal business entity such as an LLC or corporation protects you from being held personally liable if your security guard company is sued.
Form Your LLC
Read our Guide to Form Your Own LLC
Have a Professional Service Form your LLC for You
Two such reliable services:
You can form an LLC yourself and pay only the minimal state LLC costs or hire one of the Best LLC Services for a small, additional fee.
Recommended: You will need to elect a registered agent for your LLC. LLC formation packages usually include a free year of registered agent services . You can choose to hire a registered agent or act as your own.
STEP 3: Register for taxes
You will need to register for a variety of state and federal taxes before you can open for business.
In order to register for taxes you will need to apply for an EIN. It's really easy and free!
You can acquire your EIN through the IRS website . If you would like to learn more about EINs, read our article, What is an EIN?
There are specific state taxes that might apply to your business. Learn more about state sales tax and franchise taxes in our state sales tax guides.
STEP 4: Open a business bank account & credit card
Using dedicated business banking and credit accounts is essential for personal asset protection.
When your personal and business accounts are mixed, your personal assets (your home, car, and other valuables) are at risk in the event your business is sued. In business law, this is referred to as piercing your corporate veil .
Open a business bank account
Besides being a requirement when applying for business loans, opening a business bank account:
- Separates your personal assets from your company's assets, which is necessary for personal asset protection.
- Makes accounting and tax filing easier.
Recommended: Read our Best Banks for Small Business review to find the best national bank or credit union.
Get a business credit card
Getting a business credit card helps you:
- Separate personal and business expenses by putting your business' expenses all in one place.
- Build your company's credit history , which can be useful to raise money later on.
Recommended: Apply for an easy approval business credit card from BILL and build your business credit quickly.
STEP 5: Set up business accounting
Recording your various expenses and sources of income is critical to understanding the financial performance of your business. Keeping accurate and detailed accounts also greatly simplifies your annual tax filing.
Make LLC accounting easy with our LLC Expenses Cheat Sheet.
STEP 6: Obtain necessary permits and licenses
Failure to acquire necessary permits and licenses can result in hefty fines, or even cause your business to be shut down.
State & Local Business Licensing Requirements
In most states, it is necessary to obtain a license to work as a security guard. Certain other state permits and licenses may be needed to operate a security guard business. Learn more about licensing requirements in your state by visiting SBA’s reference to state licenses and permits.
Most businesses are required to collect sales tax on the goods or services they provide. To learn more about how sales tax will affect your business, read our article, Sales Tax for Small Businesses .
Service Contract
Security guard businesses should require clients to sign a service agreement before starting a new project. This agreement should clarify client expectations and minimize risk of legal disputes by setting out payment terms and conditions, and service level expectations.
Recommended: Rocket Lawyer makes it easy to create a professional service agreement for your security guard business when you sign up for their premium membership. For $39.95 per month, members receive access to hundreds of legal agreements and on call attorneys to get complimentary legal advice.
Certificate of Occupancy
A security guard business typically features an office from which clerical operations are carried out. Businesses operating out of a physical location typically require a Certificate of Occupancy (CO). A CO confirms that all building codes, zoning laws and government regulations have been met.
- If you plan to lease a location:
- It is generally the landlord’s responsibility to obtain a CO.
- Before leasing, confirm that your landlord has or can obtain a valid CO that is applicable to a security guard business.
- After a major renovation, a new CO often needs to be issued. If your place of business will be renovated before opening, it is recommended to include language in your lease agreement stating that lease payments will not commence until a valid CO is issued.
- If you plan to purchase or build a location:
- You will be responsible for obtaining a valid CO from a local government authority.
- Review all building codes and zoning requirements for your business’ location to ensure your security guard business will be in compliance and able to obtain a CO.
Miscellaneous Considerations
Here is a list of relevant considerations when starting a security guard service from Cornell University Law School’s website.
STEP 7: Get business insurance
Just as with licenses and permits, your business needs insurance in order to operate safely and lawfully. Business Insurance protects your company’s financial wellbeing in the event of a covered loss.
There are several types of insurance policies created for different types of businesses with different risks. If you’re unsure of the types of risks that your business may face, begin with General Liability Insurance . This is the most common coverage that small businesses need, so it’s a great place to start for your business.
Another notable insurance policy that many businesses need is Workers’ Compensation Insurance . If your business will have employees, it’s a good chance that your state will require you to carry Workers' Compensation Coverage.
FInd out what types of insurance your Security Guard Company needs and how much it will cost you by reading our guide Business Insurance for Security Guard Company.
STEP 8: Define your brand
Your brand is what your company stands for, as well as how your business is perceived by the public. A strong brand will help your business stand out from competitors.
If you aren't feeling confident about designing your small business logo, then check out our Design Guides for Beginners , we'll give you helpful tips and advice for creating the best unique logo for your business.
Recommended : Get a logo using Truic's free logo Generator no email or sign up required, or use a Premium Logo Maker .
If you already have a logo, you can also add it to a QR code with our Free QR Code Generator . Choose from 13 QR code types to create a code for your business cards and publications, or to help spread awareness for your new website.
How to promote & market a security guard company
Many security companies rely on direct mail, social media, and referrals for business. Contact your local mailing list broker and ask about lists of businesses that have hired security companies in the past. Mail these companies with your offer. You can also try sending out fliers and handing out business cards to local companies.
How to keep customers coming back
Specialization is a great way to stand out from the crowd. How many companies do special events in your area? If you’re the only one, then you’ll get all the business in that niche.
STEP 9: Create your business website
After defining your brand and creating your logo the next step is to create a website for your business .
While creating a website is an essential step, some may fear that it’s out of their reach because they don’t have any website-building experience. While this may have been a reasonable fear back in 2015, web technology has seen huge advancements in the past few years that makes the lives of small business owners much simpler.
Here are the main reasons why you shouldn’t delay building your website:
- All legitimate businesses have websites - full stop. The size or industry of your business does not matter when it comes to getting your business online.
- Social media accounts like Facebook pages or LinkedIn business profiles are not a replacement for a business website that you own.
- Website builder tools like the GoDaddy Website Builder have made creating a basic website extremely simple. You don’t need to hire a web developer or designer to create a website that you can be proud of.
Recommended : Get started today using our recommended website builder or check out our review of the Best Website Builders .
Other popular website builders are: WordPress , WIX , Weebly , Squarespace , and Shopify .
STEP 10: Set up your business phone system
Getting a phone set up for your business is one of the best ways to help keep your personal life and business life separate and private. That’s not the only benefit; it also helps you make your business more automated, gives your business legitimacy, and makes it easier for potential customers to find and contact you.
There are many services available to entrepreneurs who want to set up a business phone system. We’ve reviewed the top companies and rated them based on price, features, and ease of use. Check out our review of the Best Business Phone Systems 2023 to find the best phone service for your small business.
Recommended Business Phone Service: Phone.com
Phone.com is our top choice for small business phone numbers because of all the features it offers for small businesses and it's fair pricing.
Is this Business Right For You?
This business is suitable for individuals who are passionate about personal security and want to help others feel more secure in their homes and businesses. It may require working long hours or unusual schedules, like nights and weekends. Because of this, the business may not be suitable for individuals with family commitments or other obligations that fall outside of traditional 9-5 work days.
Want to know if you are cut out to be an entrepreneur?
Take our Entrepreneurship Quiz to find out!
Entrepreneurship Quiz
What happens during a typical day at a security guard company?
Day-to-day activities of a security company include preparing security-related documents like incident reports and proposals, strategic or tactical initiatives and reviewing these documents. Management also needs to provide ongoing training and education for subordinates, plan security detail for special and high-risk events, and review financial reports to make sure security operations are never in jeopardy.
A security company’s management also needs to maintain its budget for security operations, order security-related supplies and equipment, coordinate operations and activities with law enforcement (and other agencies), and attend meetings and professional seminars. In rare circumstances, you may also have to coordinate and provide support during emergencies.
What are some skills and experiences that will help you build a successful security guard company?
Security guards typically have some form of formal training from combat fields such as policing, military service, etc. In addition to this, security professionals should a have a private patrol operator’s license and extensive knowledge of law enforcement techniques.
What is the growth potential for a security guard company?
These businesses can be run at a small or large scale. A small security business can be run by just a handful of individuals. When operating a small company, the biggest concern is usually cost control and recouping the startup costs, like insurance, office space, and equipment.
All other things being equal, it’s easier to recoup these costs with a minimum staff of 5 people than with 3. The more guards you can hire, the better.
Large operations are more expensive to run, but also tend to have more stable income and more lucrative service contracts because they are more likely to land large multi-year corporate contracts.
TRUiC's YouTube Channel
For fun informative videos about starting a business visit the TRUiC YouTube Channel or subscribe to view later.
Take the Next Step
Find a business mentor.
One of the greatest resources an entrepreneur can have is quality mentorship. As you start planning your business, connect with a free business resource near you to get the help you need.
Having a support network in place to turn to during tough times is a major factor of success for new business owners.
Learn from other business owners
Want to learn more about starting a business from entrepreneurs themselves? Visit Startup Savant’s startup founder series to gain entrepreneurial insights, lessons, and advice from founders themselves.
Resources to Help Women in Business
There are many resources out there specifically for women entrepreneurs. We’ve gathered necessary and useful information to help you succeed both professionally and personally:
If you’re a woman looking for some guidance in entrepreneurship, check out this great new series Women in Business created by the women of our partner Startup Savant.
What are some insider tips for jump starting a security guard company?
Partnering with local HOAs, landlords, and local businesses could help you secure your initial security contracts. Try to keep costs associated with office space to a minimum. In most cases, you won’t need a large office when you’re just starting out.
How and when to build a team
In most cases, it makes sense to take on a team of 3 to 5 security professionals when you’re first starting out. Not only does this help you recover the initial startup costs, it helps build your revenue stream faster, since you can take on more work. As your company grows and becomes more well-known, you can hire additional security guards as finances allow.
Useful Links
Industry opportunities.
- National Association of Security Companies
- National Council of Investigation and Security Services
Real World Examples
- American Guard Services
Further Reading
- PoliceOne Services
Have a Question? Leave a Comment!

How to Start a Security Company: 8 Simple Steps

Starting your own security company can be a bit confusing. Did you know the security services industry is expected to grow steadily over the next few years? This article lays out clear steps to get your business off the ground, from legal requirements to hiring staff.
Key Takeaways
- Choose a specific niche within the security industry to define your brand and target market effectively.
- Develop a comprehensive business plan outlining your mission, target market, financial projections, and pricing strategies for services.
- Ensure legal compliance by obtaining necessary licenses, insurance, and understanding state - specific requirements when establishing your security company.
Steps to Starting a Security Company
Choose a specialty within the security industry that interests you and aligns with your skills and experience. Develop a business plan to outline your company's mission, target market, and financial projections.
Take into consideration legal and financial considerations such as obtaining necessary licenses, insurance, and establishing a solid brand identity for marketing purposes. Lastly, when hiring employees, ensure that they meet all qualifications and training requirements for security services.
Choose a specialty
Selecting a specific area of security to focus on can greatly impact your success. Whether you decide to offer armed guards, event security, residential patrols or cybersecurity services, honing in on a niche will help define your brand identity and target market.
A specialized approach allows you to tailor your training programs and marketing efforts more effectively, attracting clients who need exactly what you have to excel in.
Building expertise within a chosen specialty also strengthens your company's reputation. Invest time in understanding the unique risks and challenges of that sector which, in turn, enables you to provide unparalleled service quality.
This dedication showcases not just proficiency but commitment — two qualities highly valued within the security industry regulations and by potential clients seeking top-tier protection for their assets or events.
Develop a business plan
Creating a strong business plan is your roadmap to success in the world of security services. Outline your vision, mission, and the specific security services you'll offer. Pin down your target market, whether it's retail businesses, corporate clients, or residential neighborhoods.
Calculate start-up costs including licensing fees, insurance premiums for security guards, equipment expenses, and marketing budgets.
Dive into the nitty-gritty details with clear financial projections for at least three years ahead. Establish pricing strategies for your services to ensure profitability while remaining competitive.
Identify milestones like business registration completion and qualified manager hiring that will mark your progress as you establish your new venture in the security industry. Set practical goals linked to timelines; this level of detail will make implementing and following through on each aspect of starting up less overwhelming and more structured.
Legal and financial considerations
Understanding legal and financial aspects is crucial when you're setting up a security company. You need to register your business with the appropriate authorities, which might involve state and federal levels depending on where you operate.
This process includes selecting a proper business structure like an LLC or corporation, which impacts your liability and taxes. Also, acquiring the right licenses is mandatory for operating legally; this could encompass both security business licensing and qualified manager requirements specific to your region.
Regarding finances, creating a solid plan that outlines startup costs, operational expenses, and projected revenues is key to securing funding if you need it. It's also essential to get insurance for your security guards — they are the frontline of your services and must be adequately covered against potential risks or mishaps on duty.
Having all legal documents in order alongside strong financial planning establishes a robust foundation for your security services establishment.
Marketing your business
Develop a strong brand identity to set your security company apart. Create a professional website and utilize social media platforms to reach potential clients. Implement targeted marketing strategies to highlight the unique value your business provides, such as tailored security solutions or specialized expertise in certain industries.
Engage with local businesses and community events to build relationships and establish credibility within your target market.
Utilize online advertising, search engine optimization, and email campaigns to increase visibility. Offer informative content that showcases your knowledge of security best practices and industry trends.
Hiring employees
Seek out individuals with a background in law enforcement or military experience. Look for candidates who possess strong communication skills and have the ability to remain calm under pressure.
Ensure that potential employees pass thorough background checks and drug screenings before bringing them onto your team.
Craft detailed job descriptions that outline the specific qualifications, duties, and expectations for each role within your security company. Be prepared to offer competitive salaries and benefits packages to attract and retain top talent.
Necessary Licenses and Requirements
Different states have varying requirements for security company licenses, so it's important to research and understand the specific regulations in your state. In California, for example, you'll need to obtain a Private Patrol Operator (PPO) license and provide documentation of liability insurance.
It's also crucial to familiarize yourself with other important laws and regulations that may apply to your security business.
Different state requirements
Each state has its own specific requirements for starting a security company. It's important to research and understand the regulations in your particular state to ensure compliance and success. Here are some of the different state requirements you may need to consider:
- Business entity formation: Registering your security company as a legal business entity with the appropriate state authorities, such as filing articles of organization for an LLC or incorporating your business.
- Licensing and permits: Obtaining the necessary licenses, permits, and certifications required by the state for operating a security company, which may include security guard licensing and firearm permits.
- Insurance requirements: Meeting the state's insurance requirements for your security business, including general liability insurance, workers' compensation coverage, and professional liability insurance.
- Background checks and training: Complying with state-mandated background check procedures for employees and ensuring that all security personnel meet the training and certification standards set by the state regulatory agencies.
- Compliance with labor laws: Adhering to state labor laws regarding wages, hours of work, overtime pay, and other employment regulations applicable to security industry workers.
- Contractual agreements: Understanding any specific contractual or legal requirements imposed by the state when engaging clients or contracts within the security services sector.
- Tax obligations: Fulfilling tax obligations at both the state and local levels, which may involve registering for state tax identification numbers or obtaining relevant sales tax permits.
- Ongoing regulatory changes: Staying informed about any new or evolving regulations impacting security companies within your respective state to remain compliant with current laws.
California specific requirements
To start a security company in California, you need to be aware of the specific regulations and requirements that apply to the state. The following are the key California-specific requirements essential for starting a security business:
- Obtain a Private Patrol Operator (PPO) License from the Bureau of Security and Investigative Services (BSIS).
- Comply with training and certification requirements for security guards as outlined by BSIS.
- Adhere to background check regulations for all employees working in the security sector.
- Secure insurance coverage specifically tailored for the security industry, including general liability and workers' compensation.
- Ensure strict compliance with California labor laws and regulations pertaining to employee rights, wages, and working conditions.
- Familiarize yourself with local ordinances and municipal codes that may impact the operation of your security business in different cities within California.
Other important laws and regulations
It's important to be aware of the various laws and regulations that govern the security industry. Here are some key considerations:
- Licensing requirements: Different states have different licensing requirements for security companies, so it's crucial to familiarize yourself with the specific regulations in your state.
- Insurance regulations: As a security company, you will need to have the appropriate insurance coverage for your business and employees. This may include liability insurance, workers' compensation, and more.
- Compliance with industry standards: Security companies must adhere to industry standards for training, equipment, and operational procedures to ensure they are compliant with relevant laws and regulations.
- Background checks and screening: Security personnel must undergo thorough background checks and screening processes in accordance with state and federal laws.
- Compliance with privacy laws: Security companies must also be mindful of privacy laws when gathering and handling personal information as part of their services.
- Adherence to labor laws: It is essential to comply with labor laws regarding employee wages, working hours, and other related regulations.
- Data protection regulations: If your security company deals with any form of electronic data, it's necessary to ensure compliance with data protection regulations such as GDPR or HIPAA.
- Use of force regulations: Depending on the nature of your security services, there may be specific rules governing the use of force by security personnel that you must adhere to.
Tools for Success as a Security Business Owner
As an owner of a security guard company, it's crucial to utilize the latest technology to enhance security operations, implement effective marketing strategies to reach potential clients, and take advantage of networking opportunities within the private security industry.
Utilizing Technology
Security companies, especially those offering private security services, can benefit greatly from utilizing technology to improve operations and provide better services to clients. Implementing digital surveillance systems, GPS tracking for security personnel, and electronic reporting tools can enhance the efficiency and effectiveness of security measures.
Additionally, leveraging mobile applications for scheduling, communication, and incident reporting can streamline processes and ensure real-time updates for both clients and staff members. Embracing automation in administrative tasks such as invoicing, payroll management, and client data organization through specialized software solutions not only saves time but also reduces the risk of errors, a key aspect when managing a private patrol operator's license.
Marketing Strategies
When marketing your security guard company, focus on creating a strong brand identity to stand out. Utilize online platforms and social media to showcase your services and engage with potential clients. Implement targeted advertising campaigns to reach your ideal customer base and highlight what sets your business apart from competitors. Networking within the industry is also crucial for building partnerships and getting referrals. Utilize technology such as video marketing, virtual tours of facilities, or live streaming to demonstrate your expertise in security services. Consider offering free resources like informative blog posts or e-books on security best practices to attract potential clients and position yourself as an authority in the field.

Networking Opportunities
Connect with other security professionals and potential clients by attending industry conferences, trade shows, and local business events. Joining professional associations and online forums can also provide valuable networking opportunities. Engaging in these activities can help you stay updated on the latest trends, gain insights from experienced professionals, and build relationships that could lead to new business opportunities or partnerships within the private security business. Leverage social media platforms to connect with fellow security entrepreneurs as well as potential clients. Share your expertise through insightful posts, participate in relevant discussions, and interact with others in the field.
Develop a strong business plan to guide your security company's growth. Obtain the necessary security guard license and meet state-specific requirements for legal compliance. Utilize technology, implement effective marketing strategies, and network with industry professionals to ensure success. If you are considering starting your own security guard company, don't forget to open a dedicated business bank account for smoother financial management.
For guidance on acquiring a private patrol operator license and insights into running a successful private security business, feel free to contact us . We're here to help you embark on your journey in the security industry.
1. What are the first steps to start a security company?
To start a security business, you'll need to register your company, develop a detailed business plan, and create a strong brand identity for your startup.
2. Do I need insurance for my security guards?
Yes, securing insurance for your security guards is critical when setting up your security business model; it protects both your staff and your company.
3. How do I get my security company officially registered?
The application process for registering a security company includes filling out necessary paperwork with local authorities and getting the right licenses to operate legally.
4. Can anyone start a security business or do you need special qualifications?
Starting this type of business typically requires some background in law enforcement or private safety along with understanding how to manage all aspects of running an effective security operation.
Security Business Plans
Security guard business plan.
Batten-Hatchez Security will remove worries for clients who require security guards for their buildings, facilities, and events by providing excellent customer service for clients and in-depth training for their employees.
Video Documentation Service Business Plan
Safe Keeping is a start-up business offering video documentation of home or business belongings for customer's insurance purposes.
Online and physical security is a necessary measure for businesses to keep their employees, clients, and data secure. Whether you’re providing trained security staffing or the technology to upgrade security measures, you’ll need a business plan to do it. Check out our library of security-based sample plans to ensure your business plan is as well established as the security measures you provide.
Tax Season Savings
Get 40% off LivePlan
The #1 rated business plan software
Discover the world’s #1 plan building software

Cyber Security Business Plan Template
Written by Dave Lavinsky

Over the past 20+ years, we have helped over 500 entrepreneurs and business owners create business plans to start and grow their cyber security companies.
If you’re unfamiliar with creating a cyber security business plan, you may think creating one will be a time-consuming and frustrating process. For most entrepreneurs it is, but for you, it won’t be since we’re here to help. We have the experience, resources, and knowledge to help you create a great business plan.
In this article, you will learn some background information on why business planning is important. Then, you will learn how to write a cyber security business plan step-by-step so you can create your plan today.
Download our Ultimate Business Plan Template here >
What Is a Business Plan?
A business plan provides a snapshot of your cyber security business as it stands today, and lays out your growth plan for the next five years. It explains your business goals and your strategies for reaching them. It also includes market research to support your plans.
Why You Need a Business Plan
If you’re looking to start a cyber security business or grow your existing cyber security company, you need a business plan. A business plan will help you raise funding, if needed, and plan out the growth of your cyber security business to improve your chances of success. Your cyber security business plan is a living document that should be updated annually as your company grows and changes.
Sources of Funding for cyber security Businesses
With regard to funding, the main sources of funding for a cyber security business are personal savings, credit cards, bank loans, and angel investors. When it comes to bank loans, banks will want to review your business plan and gain confidence that you will be able to repay your loan and interest. To acquire this confidence, the loan officer will not only want to ensure that your financials are reasonable, but they will also want to see a professional plan. Such a plan will give them the confidence that you can successfully and professionally operate a business. Personal savings and bank loans are the most common funding paths for cyber security companies.
Finish Your Business Plan Today!
How to write a business plan for a cyber security business.
If you want to start a cyber security business or expand your current one, you need a business plan. The guide below details the necessary information for how to write each essential component of your cyber security business plan.
Executive Summary
Your executive summary provides an introduction to your business plan, but it is normally the last section you write because it provides a summary of each key section of your plan.
The goal of your executive summary is to quickly engage the reader. Explain to them the kind of cyber security business you are running and the status. For example, are you a startup, do you have a cyber security business that you would like to grow, or are you operating a chain of cyber security businesses?
Next, provide an overview of each of the subsequent sections of your plan.
- Give a brief overview of the cyber security industry.
- Discuss the type of cyber security business you are operating.
- Detail your direct competitors. Give an overview of your target customers.
- Provide a snapshot of your marketing strategy. Identify the key members of your team.
- Offer an overview of your financial plan.
Company Overview
In your company overview, you will detail the type of cyber security business you are operating.
For example, you might specialize in one of the following types of cyber security businesses:
- Remote security center services : This type of cyber security is focused on providing comprehensive security for networks and devices remotely from a main control center.
- Cloud security services . As more businesses turn to storage in cloud platforms, this type of service protects the data of clients from being utilized by others in that platform.
- Vulnerability scan & management: This service screens client devices and network systems remotely on a monthly maintenance basis.
- Endpoint security services: This service is dedicated to the mobile and end user devices in corporate offices; protection for computers is not included.
In addition to explaining the type of cyber security business you will operate, the company overview needs to provide background on the business.
Include answers to questions such as:
- When and why did you start the business?
- What milestones have you achieved to date? Milestones could include the number of security breaches determined, the amount of revenue earned, or reaching X number of clients served, etc.
- Your legal business Are you incorporated as an S-Corp? An LLC? A sole proprietorship? Explain your legal structure here.
Industry Analysis
In your industry or market analysis, you need to provide an overview of the cyber security industry.
While this may seem unnecessary, it serves multiple purposes.
First, researching the cyber security industry educates you. It helps you understand the market in which you are operating.
Secondly, market research can improve your marketing strategy, particularly if your analysis identifies market trends.
The third reason is to prove to readers that you are an expert in your industry. By conducting the research and presenting it in your plan, you achieve just that.
The following questions should be answered in the industry analysis section of your cyber security business plan:
- How big is the cyber security industry (in dollars)?
- Is the market declining or increasing?
- Who are the key competitors in the market?
- Who are the key suppliers in the market?
- What trends are affecting the industry?
- What is the industry’s growth forecast over the next 5 – 10 years?
- What is the relevant market size? That is, how big is the potential target market for your cyber security business? You can extrapolate such a figure by assessing the size of the market in the entire country and then applying that figure to your local population.
Customer Analysis
The customer analysis section of your cyber security business plan must detail the customers you serve and/or expect to serve.
The following are examples of customer segments: government contractors, for-profit corporations, securities businesses, private security services, and individuals.
As you can imagine, the customer segment(s) you choose will have a great impact on the type of cyber security business you operate. Clearly, government contractors would respond to different marketing promotions than individuals, for example.
Try to break out your target customers in terms of their demographic and psychographic profiles. With regards to demographics, including a discussion of the ages, genders, locations, and income levels of the potential customers you seek to serve.
Psychographic profiles explain the wants and needs of your target customers. The more you can recognize and define these needs, the better you will do in attracting and retaining your customers.
Finish Your Cyber Security Business Plan in 1 Day!
Don’t you wish there was a faster, easier way to finish your business plan?
With Growthink’s Ultimate Business Plan Template you can finish your plan in just 8 hours or less!
Competitive Analysis
Your competitive analysis should identify the indirect and direct competitors your business faces and then focus on the latter.
Direct competitors are other cyber security businesses.
Indirect competitors are other options that customers have to purchase from that aren’t directly competing with your product or service. Software companies, home or office hardware, and remote alarm services may be examples of indirect competitors. You will want to mention any direct competition, as well.
For each direct competitor, provide an overview of their business and document their strengths and weaknesses. Unless you once worked at your competitors’ businesses, it will be impossible to know everything about them. But you should be able to find out key things about them such as
- What types of customers do they serve?
- What type of cyber security business are they?
- What is their pricing (premium, low, etc.)?
- What are they good at?
- What are their weaknesses?
With regard to the last two questions, think about your answers from the customers’ perspective. And, don’t be afraid to ask your competitors’ customers what they like most and least about them.
The final part of your competitive analysis section is to document your areas of competitive advantage. For example:
- Will you provide discounts for major government contractors?
- Will you offer scan protection and management that your competition doesn’t?
- Will you provide better customer service?
- Will you offer better pricing?
Think about ways you will outperform your competition and document them in this section of your plan.
Finish Your Business Plan Today!
Marketing plan.
Traditionally, a marketing plan includes the four P’s: Product, Price, Place, and Promotion. For a cyber security business plan, your marketing strategy should include the following:
Product : In the product section, you should reiterate the type of cyber security company that you documented in your company overview. Then, detail the specific products or services you will be offering. For example, will you provide in-person and remote cyber security services for major corporations or will you offer compliance solutions for select clients?
Price : Document the prices you will offer and how they compare to your competitors. Essentially in the product and price sub-sections of your plan, you are presenting the products and/or services you offer and their prices.
Place : Place refers to the site of your cyber security company. Document where your company is situated and mention how the site will impact your success. For example, is your cyber security business located in a professional business district, a quiet corporate area, a standalone building or a remote, unnamed location? Discuss how your site might be the ideal location for your customers.
Promotions : The final part of your cyber security marketing plan is where you will document how you will drive potential customers to your location(s). The following are some promotional methods you might consider:
- Advertise in trade magazines
- Reach out to websites
- Engage in email marketing
- Advertise on social media platforms
- Improve the SEO (search engine optimization) on your website for targeted keywords
Operations Plan
While the earlier sections of your business plan explained your goals, your operations plan describes how you will meet them. Your operations plan should have two distinct sections as follows.
Everyday short-term processes include all of the tasks involved in running your cyber security business, including answering calls, planning and providing scan management, responding to emergency situations, billing clients and assisting with computer equipment, etc.
Long-term goals are the milestones you hope to achieve. These could include the dates when you expect to book your Xth client, or when you hope to reach $X in revenue. It could also be when you expect to expand your cyber security business to a new city.
Management Team
To demonstrate your cyber security business’ potential to succeed, a strong management team is essential. Highlight your key players’ backgrounds, emphasizing those skills and experiences that prove their ability to grow a company.
Ideally, you and/or your team members have direct experience in managing cyber security businesses. If so, highlight this experience and expertise. But also highlight any experience that you think will help your business succeed.
If your team is lacking, consider assembling an advisory board. An advisory board would include 2 to 8 individuals who would act as mentors to your business. They would help answer questions and provide strategic guidance. If needed, look for advisory board members with experience in managing a cyber security business or successfully running a data management business.
Financial Plan
Your financial plan should include your 5-year financial statement broken out both monthly or quarterly for the first year and then annually. Your financial statements include your income statement, balance sheet, and cash flow statements.
Income Statement
An income statement is more commonly called a Profit and Loss statement or P&L. It shows your revenue and then subtracts your costs to show whether you turned a profit or not.
In developing your income statement, you need to devise assumptions. For example, will you increase customer retention by 20% quarterly, offer reduced pricing for hardware maintenance contracts, or offer discounted packaged pricing for multiple services? And will sales grow by 2% or 10% per year? As you can imagine, your choice of assumptions will greatly impact the financial forecasts for your business. As much as possible, conduct research to try to root your assumptions in reality.
Balance Sheets
Balance sheets show your assets and liabilities. While balance sheets can include much information, try to simplify them to the key items you need to know about. For instance, if you spend $50,000 on building out your cyber security business, this will not give you immediate profits. Rather it is an asset that will hopefully help you generate profits for years to come. Likewise, if a lender writes you a check for $50,000, you don’t need to pay it back immediately. Rather, that is a liability you will pay back over time.
Cash Flow Statement
Your cash flow statement will help determine how much money you need to start or grow your business, and ensure you never run out of money. What most entrepreneurs and business owners don’t realize is that you can turn a profit but run out of money and go bankrupt.
When creating your Income Statement and Balance Sheets be sure to include several of the key costs needed in starting or growing a cyber security business:
- Cost of computer and software equipment
- Payroll or salaries paid to staff
- Business insurance
- Other start-up expenses (if you’re a new business) like legal expenses, permits, furnishings and travel expenses
Attach your full financial projections in the appendix of your plan along with any supporting documents that make your plan more compelling. For example, you might include the cyber security credentials of the CEO and COO or a list of client contracts.
Writing a business plan for your cyber security business is a worthwhile endeavor. If you follow the template above, by the time you are done, you will truly be an expert. You will understand the cyber security industry, your competition, and your customers. You will develop a marketing strategy and will understand what it takes to launch and grow a successful cyber security business.
Cyber Security Business Plan FAQs
What is the easiest way to complete my cyber security business plan.
Growthink's Ultimate Business Plan Template allows you to quickly and easily write your cyber security company business plan.
How Do You Start a Cyber Security Business?
Starting a Cyber Security business is easy with these 14 steps:
- Choose the Name for Your Cyber Security Business
- Create Your Cyber Security Business Plan
- Choose the Legal Structure for Your Cyber Security Business
- Secure Startup Funding for Your Cyber Security Business (If Needed)
- Secure a Location for Your Business
- Register Your Cyber Security Business with the IRS
- Open a Business Bank Account
- Get a Business Credit Card
- Get the Required Business Licenses and Permits
- Get Business Insurance for Your Cyber Security Business
- Buy or Lease the Right Cyber Security Business Equipment
- Develop Your Cyber Security Business Marketing Materials
- Purchase and Setup the Software Needed to Run Your Cyber Security Business
- Open for Business
Where Can I Download a Free Business Plan Template PDF?
Click here to download the pdf version of our basic business plan template.
Our free business plan template pdf allows you to see the key sections to complete in your plan and the key questions that each must answer. The business plan pdf will definitely get you started in the right direction.
We do offer a premium version of our business plan template. Click here to learn more about it. The premium version includes numerous features allowing you to quickly and easily create a professional business plan. Its most touted feature is its financial projections template which allows you to simply enter your estimated sales and growth rates, and it automatically calculates your complete five-year financial projections including income statements, balance sheets, and cash flow statements. Here’s the link to our Ultimate Business Plan Template.
Don’t you wish there was a faster, easier way to finish your Cyber Security business plan?
OR, Let Us Develop Your Plan For You
Since 1999, Growthink has developed business plans for thousands of companies who have gone on to achieve tremendous success.
Click here to see how a Growthink business planning consultant can create your business plan for you.
Other Helpful Business Plan Articles & Templates


Developing A Comprehensive Corporate Security Plan: Tips And Best Practices
Posted by CorpSecurity | Jul 20, 2023 | Informative | 0

Published by: Navya Sri
Establishing a robust corporate security plan is essential for protecting an organization’s assets, reputation, and people. In an increasingly complex and interconnected world, businesses face a wide range of security threats that require a comprehensive approach. This Blog provides valuable insights, tips, and best practices for developing a comprehensive corporate security plan.
The Importance Of A Comprehensive Corporate Security Plan
- Protects assets: Safeguards physical assets and intellectual property from theft or unauthorized access.
- Mitigates risks : Identifies and addresses potential threats and vulnerabilities to minimize their impact on the organization.
- Ensures data and information security: Protects sensitive data from unauthorized access or loss, building trust with customers and partners.
- Ensures regulatory compliance: Meets industry-specific security requirements, avoiding penalties and legal issues.
- Enables business continuity: Prepares for and responds to security incidents, minimizing disruptions and restoring operations efficiently.
- Enhances employee safety: Creates a secure work environment, ensuring the well-being and productivity of employees.
- Builds stakeholder confidence: Demonstrates the organization’s commitment to protecting assets, data, and people, establishing trust with stakeholders.
Assessing Security Risks And Threats
- Identifying Risks: Recognizing potential risks and threats that could harm the organization’s assets, operations, or personnel. This includes physical risks (e.g., theft, vandalism, natural disasters) and cybersecurity risks (e.g., data breaches, hacking, malware).
- Analyzing Impact: Evaluating the potential consequences and impact of identified risks on the organization. This helps prioritize risks based on their severity and potential harm to critical assets, operations, or reputation.
- Vulnerability Assessment: Examining vulnerabilities in existing security measures, processes, and systems that could be exploited by threats. This includes assessing physical vulnerabilities (e.g., weak access controls, inadequate surveillance) and cybersecurity vulnerabilities (e.g., outdated software, lack of employee training).
- Probability Assessment: Assessing the likelihood of each identified risk occurring. This helps in understanding the level of risk exposure and informs the allocation of resources and mitigation strategies.
- Risk Ranking and Prioritization: Ranking risks based on their impact and probability to determine the order in which they should be addressed. This ensures that the most critical and likely risks receive appropriate attention and mitigation efforts.
- Gathering Information: Collecting data and information from various sources, such as incident reports, security audits, threat intelligence, and employee feedback. This helps in gaining a comprehensive understanding of the organization’s risk landscape.
- Continuous Monitoring: Recognizing that security risks evolve over time, regular monitoring is necessary to identify new risks and changes in existing ones. This enables proactive mitigation and adjustments to the security strategy as needed.
Implementing Access Controls And Physical Security Measures
- Access Control Systems: Use systems like key cards, biometrics, or PIN codes to regulate and monitor entry to facilities based on roles and permissions.
- Surveillance Cameras: Install cameras for monitoring and recording activities, acting as a deterrent and providing evidence in case of incidents.
- Intrusion Detection Systems: Employ sensors, alarms, and security personnel response mechanisms to identify unauthorized entry or movement within restricted areas.
- Perimeter Security: Establish physical barriers, gates, and controls to secure the organization’s boundaries and implement visitor management procedures.
- Security Personnel: Assign trained personnel to patrol and respond to security incidents, ensuring a visible security presence.
- Locking Mechanisms: Use strong locks on doors, windows, and storage areas to prevent unauthorized access.
- Lighting: Maintain proper lighting indoors and outdoors to deter criminal activities and improve safety.
- Security Policies and Training: Develop clear policies and conduct training to educate employees on security measures, reporting procedures, and emergency responses.
- Incident Response Planning: Establish a plan outlining steps to be taken during security breaches or incidents, with assigned roles and responsibilities.
- Regular Assessments and Updates: Continuously evaluate and update physical security measures through audits, risk assessments, and system testing to address vulnerabilities and adapt to changing threats.
Employee Security Awareness And Training Programs
- Security Policies and Best Practices: Train employees on organizational security policies and guidelines for protecting data and maintaining a secure work environment.
- Phishing and Social Engineering Awareness: Educate employees to recognize and respond to phishing attacks and social engineering scams.
- Password Management: Instruct employees on creating strong passwords, using password managers, and enabling multi-factor authentication.
- Data Handling and Protection: Teach employees how to securely handle and protect sensitive data, both in digital and physical formats.
- Mobile and Remote Security: Provide guidance on securing mobile devices and remote work setups, including secure network usage and device encryption.
- Physical Security Awareness: Promote awareness of physical security measures, such as ID badges, workstations, and office security, and report suspicious activities.
- Incident Reporting and Response: Encourage employees to report security incidents promptly and train them on their roles in the incident response process.
- Regular Security Updates and Refreshers: Conduct periodic training sessions to keep employees informed about emerging threats and policy updates.
- Simulated Security Exercises: Perform simulated phishing campaigns and security exercises to test employees’ responses and enhance security awareness.
- Ongoing Reinforcement: Continuously reinforce security awareness through reminders, communication, and employee engagement.
Continual Improvement And Adaptation Of The Security Plan
- Regular Assessments: Conduct periodic assessments of security measures, processes, and vulnerabilities to identify areas for improvement and address emerging threats.
- Risk Monitoring: Continuously monitor and evaluate the evolving risk landscape to stay informed about new threats, industry trends, and regulatory changes.
- Incident Analysis: Analyze security incidents and near-misses to identify underlying causes, patterns, and areas where the security plan can be strengthened.
- Employee Feedback: Seek feedback from employees regarding their experiences, observations, and suggestions for enhancing security measures and procedures.
- Security Metrics and Key Performance Indicators (KPIs): Establish measurable security metrics and KPIs to track the effectiveness of security initiatives and identify areas that require attention.
- Collaboration and Information Sharing: Engage in industry forums, share best practices, and collaborate with peers and security experts to gain insights into emerging threats and effective security strategies.
- Training and Awareness: Provide ongoing security training and awareness programs to ensure employees stay informed about new risks and preventive measures.
- Technology Upgrades: Regularly assess and upgrade security technologies to leverage advancements and address evolving threats. This includes software updates, patches, and implementing emerging security tools and solutions.
- Incident Response Plan Updates: Review and update the incident response plan based on lessons learned from security incidents, changes in the organization’s environment, and new regulatory requirements.
- Testing and Drills: Conduct regular testing, simulations, and drills to validate the effectiveness of security measures, identify gaps, and enhance response capabilities.
Conclusion:
In conclusion, Developing a comprehensive corporate security plan is vital for safeguarding assets, mitigating risks, and ensuring employee safety. By conducting thorough assessments, implementing appropriate measures, and staying proactive, organizations can establish a strong security framework to protect against threats and maintain business continuity. Prioritizing security is essential in today’s dynamic security landscape.
MUST READ: The Role of Technology in Corporate Security: Advancements and Trends to Watch Out In 2023
Share this:
Related posts.

Best Risk Assessment Steps For Businesses 2023
March 30, 2023

From Aspiring To Accomplishment: The Inspiring Journey Of Meymuna M Adan- CorpSecurity Certified Security Manager
August 24, 2023

Supply Chain Risks Management For Corporates 2023
April 6, 2023
Dual Auhtentication – simple and effective way to keep your stuff secure
March 31, 2023
Leave a Reply Cancel reply
Creating a comprehensive cyber security plan template for small businesses: A step-by-step guide for protecting your business from cyber attacks

A cyber attack is disastrous for businesses. This is even more true for small businesses without the proper security strategies in place.
Luckily, you can protect your business from unwanted threats with a cyber security plan template for small business success.
Keep reading to learn about the importance of strong cyber security practices and find out how you can create your own plan.
What is a cyber security plan template for small business?
A cyber security plan template for small business outlines everything you need to protect your business from cyber security threats.
Our research indicates that any effective cyber security plan includes both preventative and reactionary measures for cyber-attacks and breaches.
What is the purpose of the cyber security plan template for small business?
There are many reasons behind a cyber security plan template for small businesses. As per our expertise, preparing against security threats is crucial to reduce risk as your company grows.
In general, a cyber security plan takes three factors into account.
- Technologies: Downloading protection software for your devices.
- Processes: Educating your team and enforcing security policies.
- Access controls: Segmenting your business information, and giving access to only those who need it.
Focusing on these three factors, a cyber security template clarifies the different kinds of security risks you need in order to protect your company.
Why you need a cyber security plan
Every day, your team relies on business data to keep operations moving. This includes:
- Customer information.
- Financial data.
- Sales history.
If you lose this data to a cyber security breach, you risk losing your business.
Unfortunately, no business is immune to cyber security threats! Our findings show that even organizations at the forefront of their industry have fallen victim to this.
But it’s a lesser known fact that small and medium businesses are the prime targets for cyber attacks.
“43% of cyber attacks target small businesses.” – Cybint , 2022.
A cyber security strategy is your first line of defense against these attacks. A complete security plan prevents cyber attacks, and provides quick solutions when required.
Based on our firsthand experience, the more secure your organization, the more trust customers have in your product or service. And more trust leads to more sales .
For example, companies with log-in websites often implement two-factor authentication for their users. This adds an additional level of security, as it requires more than just a password for access to your system.
Without proper security procedures, both your physical computers and online accounts are at risk of security breaches. And through our practical knowledge, if you don’t take advantage of antivirus resources, for example, entire operating systems can crash on you.
Usually, companies that thrive in cybersecurity have systems in place that prevent and solve security issues. And drawing from our experience, you can achieve both with an incident response plan.
Planning for the worst saves you time and stress. More importantly, it clarifies exactly what actions you need to take in the event of an emergency.
The more concise your plan, the better your business will be at handling cybersecurity responsibilities.
Local network security devices like firewalls are key in filtering the connection between your private network and the public Internet.
Encryption of sensitive files on your computer, or within applications, is another key factor to consider. Any file or program that contains customer data is important to protect.
Let’s take a look at the cyber threats that can affect your business below.
Common cyber threats for small businesses
Of course, one of the requirements for creating a cyber security plan template for small business protection is to understand your business’ risk.
To identify your possible vulnerabilities, you need to know what threats are out there. Our research indicates that these are the most common cyber security threats for small businesses.
Malware attacks
Malware is the biggest cyber threat for small businesses today.
The term itself is broad and refers to all categories of malicious software meant to harm devices or networks.
Three common types of malware attacks include:
- Ransomware.
Let’s dive deeper into each one.
In short, a virus is a piece of computer code meant to harm your technological equipment. Computer viruses affect your devices in many ways, including:
- Corrupting or deleting files.
- Damaging computer programs.
- Slowing down device performance.
- Causing excessive pop-up windows.
In your cyber security plan template for small business, there are several benefits to highlighting the signs when a device has become infected with a virus.
What’s more is that there are several ways that your devices can catch a virus, such as:
- File sharing.
- Downloading harmful software.
- Infected emails.
Viruses used to be the only cyber threat that businesses worried about, but cyber security has evolved and now includes other attack strategies.
Ransomware attacks
Ransomware is malware where hackers access your data and hold it for ransom by encrypting it. You then pay them to decrypt your data and regain access.
So, if your business experiences a ransomware attack, your products or services provided will likely come to a screeching halt.
A surprising statistic:
“Ransomware is the third most popular type of malware used in data breaches.” – Verizon , 2020.
Our findings show that this will do more than just affect your numbers. Depending on the information that the hacker gathers, a ransomware attack can be tragic for your small business. It could cost you everything to pay off the hacker.
Unfortunately, even if you comply with the hacker, there’s a chance that they won’t keep up their end of the deal. They may ask for additional payments, or cut communications once they have what they want.
Spyware is a type of malware that collects information from your device without your knowledge. Based on our observations, it’s difficult to detect, and many people never know that they’ve been subject to a spyware attack!
With spyware, cyber criminals can not only oversee your business operations. Data privacy and data security become a pipe dream as well.
Since it’s invisible, once spyware has been downloaded to a device, there is little you can do to restore your network security.
One of the most common ways spyware hackers install spyware is through phishing emails.
Phishing scams
Unlike the other attacks on this list, phishing isn’t software. Phishing is a technique used to gather sensitive information through deception.
The act of convincing someone to disclose information to a hacker is called social engineering.
The most common case of phishing involves sending emails with links that lead to a website infected with malware. These scams can affect consumers and businesses alike.
A common social engineering strategy is to trick recipients to reply to emails with personal information by pretending to be a credible source, such as a colleague.
Our findings show that cyber criminals often claim to have management roles in the businesses they target. A similar strategy involves impersonating a company that has a strong reputation.
As per our expertise, it’s important to include strategies to prevent phishing attacks in your cyber security plan template, most of which surrounds employee education (more on this later).
The state of your cybersecurity hinges on making a plan. Let’s jump into how to create a cyber security plan for small business.
How to create your business cyber security plan
Creating a security plan requires you to look at your current business processes to figure out your vulnerabilities.
From there, you can put together a plan to eliminate those vulnerabilities and reduce your risk.
You might think as a relatively unknown “small biz” that you’re safe against cyberattacks. In reality, it’s small business cybersecurity that cybercriminals target most. This is because a small organization tends to have much weaker cyber security than a larger enterprise.
It’s a good idea to use a cyber security plan template for small business through this process. Through our practical knowledge, templates for your business’ cybersecurity plan are useful tools as they eliminate internal confusion over protocols and best practices.
To guide you, here are 5 key steps to creating your plan.
1. Identify your biggest threats
Of course, drawing from our experience, protecting your company from cyber threats requires more than just filling out a planner.
Creating a cyber security plan is similar to setting your sales goals . For example, both involve taking every aspect of your business into account.
You can’t create a line of defense if you don’t know what you need defending from.
This is why the first step in creating a cyber security plan for small business is to understand your business risk.
The most common threats for small businesses include:
- Ransomware.
- Weak passwords.
Our research indicates that identifying your risks helps you find ways to prevent these risks from happening. This includes solutions, such as:
- Antivirus software.
- Newer devices with updated security features (i.e., fingerprint scanning).
- Password parameters.
If you have an IT team, this is a job for them. If not, consult an IT professional to identify your exposure and create a plan.
2. Prioritize your assets
Cyber security asset assessment involves identifying your IT assets and potential security risks. Your assets include traditional devices as well as digital assets.
Here are some examples of common business assets to consider:
- PCs and mobile devices.
- Networks and servers.
- Cloud-based data.
In reality, any part of your IT infrastructure is at risk of cyber security threats, so be sure to create a comprehensive list.
From there, decide which assets are the most important. That way you can determine the most vulnerable ones to begin creating your security plan.
3. Set your goals
The goal of your security plan is to protect your small business. However, several smaller goals play into this larger objective.
In a perfect world, creating a plan to prevent cyber attacks, and including a network security device like a firewall, would be enough. However, solely relying on prevention is unrealistic.
As much as you try to prevent cyber security attacks, there’s always a risk of cyber attackers getting through your defense. So, as per our expertise, your goals should also include optimal readiness to respond to threats.
If you’ve already made the plans to handle unauthorized users in your system, then you’ll greatly reduce the amount of damage they can do.
Of course, malware detection is the first step once your cybersecurity is breached. So planning the ways to detect threats is as important as planning how to deal with them.
Better yet, our research indicates that you should have a goal for your recovery time to minimize your exposure and damage to your assets.
4. Document your plan
Once you’ve determined your current cyber security risks and created a business plan to improve your response readiness, it’s time to document your plan.
Based on our firsthand experience, documenting is easy if you use a cyber security plan template for small business, as you just have to fill in the sections in the template.
There are several reasons why documenting cybersecurity plans is important.
For starters, you don’t want anything to slip through cracks when it comes to a cyber security plan for small business. It only takes one small slip-up for a hacker to access your information.
Thoroughly documenting your plan minimizes the risk of overlooking an aspect of your business, and removes the possibility for any intrusion into it.
Sometimes, you’ll have conversations with your customers that are difficult . But nothing’s harder than explaining that your cyber security has been compromised. A well-documented plan softens the blow and reduces a breach’s impact.
What’s more, employee training plays a huge part in your cyber security strategy. So, document your plan in a way that’s easy to understand.
5. Do a test run
Once you have the proper cyber security infrastructure in place that your employees are trained on, test your plan.
Don’t forget to test your employees’ ability to recognize threats by sending test phishing emails. You can also simulate a ransomware attack through encryption of your own files.
It’s important to note that cyber security is always evolving. Once you confirm that your new plan works, set up a schedule to conduct regular tests to ensure up to date strategies.
Now that you know how to create your plan, let’s explore what to include in your template.
What to include in your cyber security plan template for small business
Making a cyber security strategy is no small task. There are two points to remember about your plan:
- It’s a document your team regularly references.
- The security of your business depends on it.
Organizations that acknowledge these points always have the most robust security strategy, making them the most cyber secure. To address these two factors, you want to ensure that you include as much detail in your plan as possible.
Using a cyber security plan template for small business simplifies the process and ensures that your plan captures every aspect of your business.
Since this plan will be included in the core employee resources of your organization, a template ensures that you’ve covered all your bases in a way that’s still easy to follow.
Here’s what to include in your template.
Your objectives
To kick things off, your cyber security plan for small business protection should open with your goals.
Your goals guide your plan, so clearly stating them at the start gives context to your proposed strategies.
As a result, the reader sees the bigger picture and better understands the importance of cyber security strategies.
Common threats
To fully understand your cyber security strategies, you need to outline your business’ security threats.
Make sure that your plan describes each threat to your business. This means associating each common threat with an asset.
For example, one common threat to small business security is password hacking, and one of the assets at risk is your company’s data. Knowing this, you can strengthen your employee passwords to prevent data breach.
Identifying threats specific to your business is a crucial step in protecting your staff and your customers from cyber attacks.
Security policies
Cyber security policies serve as the framework of your plan.
Policies outline how you expect your team to protect your business assets. Some basic security practices include:
- Limiting who accesses information.
- Restricting internet browsing on your network.
- Implementing a plan of action for suspicious emails.
There are also companies that offer products or services, like antivirus software to ward off security threats.
Your security policies are mainly preventative, so you should consider how to react to security breaches.
Breach response plan
Prevention is the best tool to protect your business, but it shouldn’t be your only tool. If your business does become the victim of a cyber attack, you should have a plan of how you’ll react.
When unauthorized users infiltrate your business systems, panic sets in. It becomes difficult to think clearly and act accordingly.
Without an established breach response plan, you’ll lack the tools to quickly restore your business.
A breach response process allows you to identify an attack and shut it down as soon as possible. This reduces damage to your business data and ensures that you’re back up and running in no time.
Your breach response plan should include clear steps and a timeline of how long you have to shut down an attack before your business is at risk.
Employee education plan
You can have the tightest cyber security policies in place, but if your employees don’t know them, your business is still exposed.
So, it’s important to implement a system that educates your employees. A cyber security plan for small business isn’t complete without employee training.
To be successful, your employees need to be up to speed on your business’ cyber risks and security policies. Design a cyber security training program to walk your employees through these.
A complete employee education plan results in your employees:
- Creating strong passwords.
- Recognizing phishing emails.
- Resisting other social engineering techniques.
- Knowing what to do if they accidentally disclose information.
Highlight your training plan in your cyber security plan template for small business.
For best results, conduct a cyber security training at least once a year and test employees’ knowledge monthly.
Wrap up: Cyber security plan template for small business success
The truth is that if you don’t have a solid cyber security plan for small business, you risk losing your business completely.
With this in mind, it’s important to prioritize cyber security policies and implement them into your business process. The applications of this plan will guarantee longevity for your business.
The key content of a complete plan includes:
- Clear goals.
- Potential threats.
- Security policies.
- A breach response plan.
- Employee training.
The health of your cyber security depends on these five factors for a number of reasons. Establishing each of these now means that you can quickly shut down unauthorized user or activities within your business down the road.
The quality of your product or service means nothing if your cyber system is unsecure.
With the support of a template, your cybersecurity plan is clear, concise, and comprehensive. It allows you to draft and organize all the content that your plan requires.
Free cyber security plan template for small businesses
Protect your business from cyber attacks by drafting a robust cyber security plan.
If you don’t see the download form, download template here .
Brush up on other technology trends for your small business in this blog !
Cyber security plan template for small business FAQs
How do i implement a cyber security plan for small business.
To implement a cyber security plan for your small business, the most important step is educating your employees. Once your plan has been created, the hard part is done.
Make your cyber security plan customary and accessible so that your employees know about your business’ strategies in the event of a cyber threat.
If you’re unfortunate enough to experience a cyber threat, remind your staff of your plan– then follow each step closely.
How do I choose the right cyber security products for my small business?
To choose the right cyber security products for your small business, first identify all your company’s potential cyber threats. Once those are established, there are many security products to choose from.
There is not a one-size-fits all solution to cyber security. You can choose which products suit your needs, but it’s important to note that you can never be too secure.
Many cyber security companies offer free trials, so consider experimenting with different products to find the perfect fit for your business.
Where can I find a cyber security plan template for small business?
For a comprehensive cyber security plan template for small businesses plus more, simply:
- Follow this link .
- Fill out your business’ basic information.
- Click download.
Keep your data more secure with a free trial of Method:CRM.
Image credit: cottonbro via Pexels .
About The Author
Shana Cesaire
Related posts.

3 ways you win with QuickBooks mobile access

Conference Travel Tips to Get You There Energized
Streamline your business with method.
Start your free trial — no credit card, no contract.

- Case Studies
- Koorsen Companies
- Koorsen Training Center
- Kasey Program
- Fire Protection
- Communications
- Mobile Equipment Solutions
- Additional Products + Services
- Restaurants
- Property Management
- Hospitality
- Construction
- Koorsen Blog
- Koorsen In The News
- Kasey the Dog Blog
How to Create a Security Plan for Your Business

Businesses in the United States, particularly the small and medium scale, are vital to the economy's growth. As of today, over 56 million jobs in the United States come from these businesses.
Unfortunately, the scale of these businesses makes them a target for theft, vandalism, and other related criminal activities. When these crimes occur, they result in grave losses that could be worth millions of dollars.
To avoid these losses, business owners must develop their security plans to identify their vulnerabilities and make out strategies to keep their companies safe and secure.
This article discusses how you can create a security protection plan to secure all assets in your business.

The Process of Creating a Master Security Plan
A master security plan is a detailed, long-term strategy that entails all the aspects of security operations in an organization. For such programs to be successful, they must be based on two core principles.
First, it must be in line with your business's strategic plans while combining the best principles for protection and support.
For example, if one of your critical business goals is to value customer relationships, your security plan should include customer safety. As such, you would be looking to protect customer records and information both online and offline.
Second, your business security plan will only work well when it inputs all your business's critical stakeholders. All these people will come together to evaluate security risks and develop a documented plan that they would test, implement and maintain over time.
How Do You Evaluate Existing Security Risks?
To evaluate existing security risks, the management has to go through a series of information gathering. Risk evaluation allows you to plan for any risks using the already existing business security layout.
You will need to work with different leaders in your firm, starting with those at the C-suite and then with the HR manager and other key leaders in your organization. You might also have to do an on-site assessment to see the issues on the ground correctly.
You will be looking for records of theft, corruption, hazards, extortions, and any other security challenges. As you explore these challenges, you should also consider their impacts financially and the impacts on people's safety in your environment. You should also consider how much these risks affect your production schedules, delivery, and your company's overall reputation.
To get the most out of the evaluation exercise, you must ask as many questions as possible to get all the needed information.
Addressing the Risks with Security System Tools and Equipment
Understanding the risks alone would not do you any good. Your master security plan must also address the needed tools to combat the security risks you evaluated. The following are some helpful tools.
Video Surveillance
Video surveillance cameras are security tools that allow you to record and collect video footage of activities on your business's premises. In many cases, the police would require the footage from these devices as evidence for prosecution. The footage can also help expedite your claims from insurance companies.
Alarm Systems
Monitored alarm systems are essential tools for the safety of your business. They can be security alarm systems and fire alarm systems , and their job is to notify you and the authorities in cases of emergencies and crimes.
Access Control
Access control refers to pass cards, keys, pin codes, or other security technologies that you can use to secure sensitive areas of your business. Using access control tools, you can limit the number of people who have access to certain areas on your premises.
Staff Training / Monitoring
Training your staff can help reduce the occurrences of crime. The training will cover how they can recognize security threats and deal with them without causing issues for your customers.
Training alone is not enough. You also need to monitor your staff after you have trained them. Aside from the fact that monitoring boosts productivity, it will also reduce the risk of your employees committing crimes.
Contact Koorsen for Your Security Needs!
To learn more about Business Security Plans and how Koorsen Fire & Security can help address security risks, contact your local branch today. At Koorsen Fire & Security, our security experts can help evaluate your business's potential security risks and provide a customized solution to reduce security and safety issues.

Topics: Monitoring , Commercial Security , Small Business Security , Video Surveillance
Contact Us Now!
Disclaimer: The information in this article is for informational purposes only. It is believed to be reliable, but Koorsen Fire & Security assumes no responsibility or liability for any errors or omissions in the content of this article. It does not constitute professional advice. The user of this article or the product(s) is responsible for verifying the information's accuracy from all available sources, including the product manufacturer. The authority having jurisdiction should be contacted for code interpretations.
Related posts

SEARCH OUR BLOG
- There are no suggestions because the search field is empty.
Subscribe to Our Blog
Recent posts.
- Fire Protection (110)
- Commercial Security (101)
- Fire Safety & Security (72)
- Koorsen News (72)
- Fire Safety (59)
- Fire Sprinkler Systems (59)
- Fire Extinguisher (58)
- Fire Alarm Systems (56)
- Inspection/Testing (43)
- Access Control Systems (39)
- Small Business Security (39)
- Fire Suppression (37)
- Kitchen Fire Suppression (35)
- Restaurant Industry (25)
- Fire Training (24)
- Video Surveillance (24)
- Emergency/Exit Lighting (20)
- Education Industry (18)
- Commercial Kitchen (17)
- Monitoring (15)
- Training & Education (15)
- Healthcare Industry (12)
- Property Management Industry (10)
- General (9)
- Nurse Call System (9)
- Kasey Program (8)
- Restaurant (8)
- Education (7)
- Property Management (7)
- Construction Industry (6)
- Fire Pumps (6)
- Koorsen Family Foundation (6)
- Retail Industry (6)
- Emergency Notification (5)
- Mobile Equipment (4)
- Vehicle Fire Suppression (4)
- Engineering (3)
- Hospitality Industry (3)
- Long Term Care (3)
- Podcast (3)
- Bi-Directional Amplifier (2)
- Dry Chem Suppression (2)
- Industrial (2)
- Infographics (2)
- KnoxBox (2)
- Backflow Preventer (1)
- Construction (1)
- Distributed Antenna Systems (1)
- Flame Detection (1)
- Government (1)
- Home Security (1)
- The Joint Commission (1)
- Underground Services (1)
ALL PRODUCTS AND SERVICES
- Fire Extinguishers
- General Fire Products
- Emergency/Exit Lighting
- Fire Alarm Systems
- Fire Sprinkler Systems
- Kitchen Fire Suppression
- Fire Suppression Systems
- Commercial Security
- Emergency Notification
- Home Security
- Nurse Call Systems
OTHER COMPANIES
- KOORSEN ENVIRONMENTAL
- KOORSEN FACILITIES MANAGEMENT
CONTACT KOORSEN
866-311-7753
- KOORSEN CAREERS
- MEDIA RELATIONS
- TRANSPARENCY IN COVERAGE
© 2024 Koorsen Fire & Security | PRIVACY POLICY
More From Forbes
7 steps to elevate your organization's security culture.
- Share to Facebook
- Share to Twitter
- Share to Linkedin
Perry Carpenter is Chief Evangelist for KnowBe4 Inc. , provider of the popular Security Awareness Training & Simulated Phishing platform.
News reports appear almost daily highlighting new security attacks that put employee and customer data at risk. It’s an ongoing fight that companies can’t afford to quit. Although 39% of IT professionals admit that phishing is their biggest fear, the number should be much higher, considering that the FBI reported that online scammers had snatched $10.3 billion from Americans in 2022 alone. The good news is that a well-established security culture—reflected in the ability to effectively respond to security threats—can increase resilience by 46% .
The savviest companies understand that improving security isn’t a one-and-done event. It’s an ongoing process that is built, foundationally, on a strong positive security culture. But knowing that, and doing that, are two different things. Changing the culture within your organization to lean into cybersecurity best practices (or safe end-user habits) can seem arduous but it’s worth the effort. Employees have a genuine desire to safeguard company data and security because it could be their own credentials and identity at risk. With a supportive culture, users can become more proficient at recognizing and thwarting cyberattacks and social engineering threats, mitigating potential harm to your network.
Here are some best practices for elevating your organization’s security culture:
1. Choose one or two behaviors you would like to change.
You can’t change or improve everything at once. Yet that’s what many organizations attempt to do when it comes to their security efforts. That’s also why many organizations fail in their attempts.
Best High-Yield Savings Accounts Of 2024
Best 5% interest savings accounts of 2024.
Instead, focus on a few things that are most likely to have the greatest impact. The formula Risk = Likelihood x Impact can help you identify where you should apply your initial efforts. Focus on those things that may span a few different dimensions of risk and give yourself three to six months to impact changes. Then, move down your list of priorities.
2. Design a plan to influence behaviors on an organizational scale.
Behaviors drive actions, so if we can change behaviors, we can achieve the changes we need to impact security culture. Applying project management principles can help here, something that those in technical roles may find practical and familiar.
Identify people who can help influence the desired changes and who can be advocates for your efforts. People are social beings, and their actions tend to align with others. The right champions can be instrumental in achieving the changes you want to achieve.
3. Get leadership buy-in.
Champions are important and they can have a significant impact in driving change and reinforcing your security culture. But they can’t do it alone. Leadership buy-in sends a strong message throughout the organization, not just in terms of what they say but in terms of what they do to support your efforts.
But leaders are busy and they may balk if you ask too much of them. To minimize the impact of your “ask,” consider:
• Providing an executive summary that spells out the “why” of your collective efforts rather than listing the minute details.
• Encouraging leaders to visibly demonstrate their own behavior changes to prompt changes in others.
• Using examples that are relatable and real. For instance, illustrate how the reporting of phishing emails can measurably reduce the risk of ransomware and minimize financial risk.
Executives will give you their buy-in. But if you can make it as easy as possible for them to do so, you’ll see greater commitment and more concerted action.
4. Communicate often and clearly.
Ongoing, easy to understand, relevant and relatable communication is critical to any change management effort. That’s certainly true when attempting to develop a sustainable security culture. Be concrete in your communications, use clear and realistic examples and share your messages multiple times in varying ways. Partner with colleagues in marketing to help ensure your messaging is as impactful and engaging as it can be.
5. Execute the plan.
Executing your plan to improve your organization’s security culture requires a clear goal or outcome in terms of what success will look like and a solid understanding of where you’re starting from. Conducting a security culture survey can help establish that baseline.
Involve your advocates or champions in the execution of your plan. But don’t expect clear sailing. Be prepared to respond to push-back and challenges along the way.
6. Measure results.
When you have a clear and measurable idea of where you’re starting from, you’re able to measure the results you’re making. Document these results in a report that can be shared not only with leadership, but with everyone in the organization. Find a good balance between what’s working well and the successes you’ve seen, as well as areas where there is room for continued focus and improvement.
7. Determine your move-forward strategy.
Culture change is a work in progress and an ongoing endeavor. As you evaluate progress, adjust your goals to improve the odds of success as well as the strategies and tactics you’ll use to achieve those goals. Seek out best practices and celebrate results. Ask advocates for feedback and ideas that can be used moving forward. Finally, continue to communicate progress, shifts and successes.
Yes, improving security culture can be an uphill battle, especially at first. It can also be highly rewarding. Commit to following the steps provided here to start your organization along the path to a resilient security culture.
Forbes Business Council is the foremost growth and networking organization for business owners and leaders. Do I qualify?

- Editorial Standards
- Reprints & Permissions

Hello. It looks like you’re using an ad blocker that may prevent our website from working properly. To receive the best experience possible, please make sure any blockers are switched off and refresh the page.
If you have any questions or need help you can email us
Elevating Your Business Through Security Training
Through proper training, your firm and ultimately your clients can significantly reduce the risk of a data breach. Here's how.
Apr. 01, 2024

By Dr. Sangeeta Chhabra
Here’s a sobering stat for accountants and business owners alike: 74% of data breaches occur due to human errors, encompassing mistakes, privilege misuse, stolen credentials, or social engineering.
But there is hope—through proper training, your firm and ultimately your clients can significantly reduce the risk of a breach.
Do staff follow data security policies?
Outstanding data security stands as a fundamental pillar of any successful business—undoubtedly so, your firm included. Yet, amidst discussions of firewalls and encryption, the pivotal role of training within this security framework often goes unnoticed.
Remember, your team constitutes the frontline defense of your enterprise, and their proficiency in handling sensitive data is paramount. Well-trained employees not only act as a shield against potential breaches but also serve as torchbearers in fostering a culture of data security awareness throughout the organization.
As mentioned above, human error remains the largest cause of data breaches—whether it’s unwittingly clicking on malicious links, succumbing to phishing scams (which are getting more advanced by the day), or mishandling sensitive information. While technological safeguards undoubtedly play a critical role, they alone cannot entirely mitigate these risks. This is precisely where comprehensive employee training assumes its pivotal role.
Benefits of employee training
1. minimized exposure to data breaches.
When employees are well-trained, they’re less likely to be targets of cyberattacks, lowering the risk of data breaches and the costs involved. Additionally, simulating mock data breaches helps prepare staff for such situations, enabling quicker responses and reducing containment time.
2. Financial
Although training necessitates an initial investment, its expense pales in comparison to the aftermath of a data breach, which encompasses legal expenses, regulatory penalties, and damage to reputation.
In cases where personal data is compromised and staff lacks training in managing such incidents, the information regulator can levy huge fines, along with potential imprisonment, depending on the gravity of the violation.
3. Enhanced compliance
Many regulations mandate that organizations offer cybersecurity training to their employees, a crucial step in ensuring legal adherence. Meeting these mandates guarantees compliance with regulations like GDPR (General Data Protection Regulator) or POPIA (Protection of Personal Information Act), which must be considered when designing training programs.
Fostering a culture of compliance: Employees play a pivotal role in cultivating a culture of compliance within the organization. This involves raising awareness about data protection, privacy, and the significance of adhering to regulations.
4. Enhanced staff engagement
When employees feel empowered to safeguard the company’s data, they exhibit greater confidence and job satisfaction.
Foster a culture of communication: Encourage employees to discuss data security among themselves, fostering an open dialogue in the workplace. This enables them to ask any questions they may have, as I often say, “No question is a silly question unless it goes unasked, leaving you feeling uncertain.” The more at ease your employees are with communicating and voicing even minor concerns, the better prepared your company will be to address data security challenges.
What does successful training look like?
Cybersecurity awareness.
It’s crucial for employees to understand various cyber threats they might encounter. It includes recognizing phishing emails, understanding social engineering tactics, identifying malware, and being aware of other common attack methods. Additionally, they should comprehend the significance of data security to your organization.
Data protocols
Clear guidelines on how to handle sensitive data, whether in digital or physical form, are essential. Employees must learn the secure storage, transmission, and disposal of data. Familiarity with audit trails, authentication procedures, and session management contributes to overall data safety.
Password and access management best practices
Training should encompass best practices for creating strong passwords and enforcing access control policies. It’s vital to emphasize the importance of restricting access to sensitive information.
An incident response plan
Employees need to be educated on proper procedures to follow in the event of a security incident or breach. A well-prepared response can help minimize potential damage.
Processes for handling client data or payments
Instructing staff to adhere to specific steps, such as verifying the credentials of individuals requesting data access, confirming their affiliation with the stated company and department, and requesting documentation like bank verification letters or company registration documents to validate company bank details, is crucial. Providing a checklist for reference can significantly mitigate risk levels.
Actionable insights for implementation
Putting effective employee methods into practice can be simplified by adhering to these practical guidelines:
Personalize training programs
- Craft training sessions that cater to your organization’s unique requirements, considering the data you manage and the regulatory standards of your industry. You may incorporate additional governmental regulations such as GDPR or POPIA to underscore the significance of data protection from external regulatory perspectives.
- Moreover, customize training modules to align with specific departments such as administration, accounting, human resources, and development. By doing so, you can effectively address the distinct data handling practices and emphasize the importance of data security relevant to each group.
- When considering delivery methods, weigh the benefits of online employee training against in-person programs to determine the most suitable approach for your organization’s needs.
Stay current with regular updates
- As cyber threats continue to evolve, it’s imperative that your training program evolves alongside them. Keep your curriculum current to effectively tackle emerging risks.
- Subscribe to websites that provide regular updates on threat management to ensure your staff remains well-informed about potential dangers.
- Maintain an active group chat to promptly disseminate information regarding any potential threats employees should be vigilant about.
- Additionally, consider implementing a revamped training process for new employees to ensure they’re equipped to navigate the evolving landscape of cybersecurity threats.
Fostering engagement
- Enhance training sessions by making them interactive and engaging. Incorporate real-world examples and scenarios to make the content more relatable to employees’ everyday experiences.
- Encourage active participation from staff members to ensure their engagement throughout the training.
- Facilitate a Q&A session afterward to encourage discussion and dialogue. Employees may share experiences or insights they’ve encountered, offering valuable perspectives and potential solutions that could benefit the company.
Monitoring and assessment
- Consistently track the performance of your training program and solicit feedback from employees to enhance its effectiveness.
Establish safe reporting channels
- At some point, an employee may misplace their phone or inadvertently click on something that triggers issues. A swift response can significantly mitigate risks, but it depends on employees feeling secure in reporting problems without facing repercussions.
- We all make mistakes. Swiftly securing data following an error is crucial to minimize the potential loss of customer, employee, or company information.
- Ensure employees understand that reporting problems promptly is preferable, as it may prevent a breach if addressed in time and assure them that it’s safe to do so.
The bottom line: A culture of data security
Data security is a collective responsibility. The company must diligently safeguard its physical, cloud, and in-house equipment and data from breaches. Employees play a pivotal role in upholding this safety. It’s essential to educate them on how to maintain equipment and data security to safeguard everyone’s interests.
Training is crucial for equipping your staff with the knowledge of potential threats lurking to breach your systems. By implementing a handful of straightforward checklists or action items, you can significantly mitigate risks, saving valuable time and financial resources—and preserving the trust of your clients.
ABOUT THE AUTHOR:
Dr. Sangeeta Chhabra, co-founder and director of Ace Cloud Hosting, is a leader and innovative entrepreneur with more than 20 years of experience in the IT sector. She has positioned the company as a leading global provider of IT and managed cloud services, celebrated for its QuickBooks hosting tailored for the accounting sector, as well as its Managed Security Services and Public Cloud offerings for SMBs and enterprises. Under her leadership, Ace Cloud was honored as the Best Outsourced Technology Provider at the CPA Practice Advisor Readers’ Choice Awards 2023, among other accolades. Beyond her professional successes, Dr. Chhabra is a passionate advocate for women’s empowerment and is committed to fostering an inclusive environment at Ace Cloud.
- Small Business

ABOUT CPA PRACTICE ADVISOR
- Cookie Policy
- Terms & Conditions
Magazines & Newsletters
- Magazine Archive
- Newsletters
Join for free!
CPA Practice Advisor is your technology and practice management resource for the accounting profession, giving you personalized access to the latest news, accounting-related events, and expert commentary across all of our channels, including website, whitepapers, newsletters, podcasts, social media, and our annual conference – Ensuring Success.
Join for free
CPA Practice Advisor is registered with the National Association of State Boards of Accountancy (NASBA) as a sponsor of continuing professional education on the National Registry of CPE Sponsors.
© 2024 Firmworks, LLC. All rights reserved
Business Plan Writer Moscow
A well written business plan is an essential component for any company seeking to raise capital. Our team at Prospectus.com has over 20 years of experience writing business plans and structuring business models for start-ups, later stage and expansion companies, those seeking venture or angel financing all the way to mezzanine and 144A funding, spanning a wide range of industries across the globe. We have been involved in thousands business projects and assisted with business planning, offering and private placement setup, feasibility studies, drafting financial projections, both for private companies and those seeking initial public offerings or listings on a stock exchange. Our team is a recognized leader in business plan development. In fact, our CEO is the Chairman and Founder of Borders.org ( Business Plans Without Borders ), a not-for-profit 501c3 organization which assist low income families as well as refugees and immigrants with business plan writing services and grants.
Our Team’s Business Plan Advisory Services Value-Proposition:
- Our staff are known as one of the most reliable and affordable Business Plan developers in the U.S. and worldwide. Our straight forward and honest assessment of one’s business is one of our strongest characteristics
- Offices and associates in numerous countries, including New York, London, Hong Kong Beijing, Singapore and Seattle
- 1 to 2 weeks’ average time for completing business plans
- Proven track record of saving entrepreneurs thousands of dollars in needless spending while developing the business plan
- Ability to draft your business plan and prospectus or private placement memorandum or offering memorandum for debt or equity offerings or any other service and package everything as one price
- We are somewhat of a one stop business for most of the startup and later stage company needs.
Moscow Business Plan Options
There are mainly two types of business plans that are written in Moscow: capital raising business plans and management or managerial business plans.
Raise Capital with a Business Plan
Most business plans are written with eye towards raising money for their venture. In a business plan that is written for investment capital, the structure of the business plans and therefore the most important point of the document will be the value-added benefit. Information on the products, services and the market will play central roles in the development of the plan, as well as various payout or exit strategies for the investors. Most business plans will focus on either selling equity or debt to investors.
- Equity : In an equity business plan the company seeking funding will sell an ownership stake. If the company is a corporation, they will sell shares or common stock or a variation of them. If the company is a LLC or a Limited Company (which is popular worldwide) interest or units in the company would be offered. Both a form of ownership, just with a different name for each entity. In additional, there are other sweeteners one can add into any business plan offering, including warrants or preferred shares or preferred units or convertible debt.
- Debt : in a debt offering business plan the company will be issuing some type of bond or a note to investors. A bond or note differ only in terms of the length of each security, which bonds being considered a longer maturity date than a note. There are also convertible debt securities that would convert the notes/bonds to equity at a certain fixed point in time. The business plan for bonds would detail the terms, such as the maturity date, interest rate and other vital information.
Managerial Guidance Business Plan
- No Capital Raising : In a managerial or a management business plan, the focus is not on raising money but what strategy a company should employ. While most companies that write business plans do so to raise capital, there are some that simply want to get a second opinion or an outside view of their business. They ask us to write them a business plan for growth opportunities, not to raise money. Said another way, the management of the company wants to see our view and take on their business and what we would do to expand their company.
- Recommendations : A business plan used to simply strategically plan one’s next move is referred to as managerial guidance business plan document. No capital is being raised initially, although sometimes we may conclude that capital should be raised for the company to penetrate or open new markets or opportunities. In the course of research, we may conclude that, in fact, the company should conduct an offering and raise money. We will recommend the amount to raise based on the company’s expansion needs and the company valuation.
3 Levels of Business Plans
Our firm offers various levels of business plan writing service and consulting, including: Level I Start-up Business Plan »
- Prospectus.com’s team consists of industry expert business plan writers. Our Level I Start-up Business Plan can be used for companies raising initial seed funding and getting off the ground. The dollar amount being raised is not of paramount importance.
- The Start-up Plan includes complete financials, potential cash-flow, market analysis and marketing strategies as well as a break-even analysis, and a separate executive summary and much more.
Level II Expansion or Series B Business Plan »
- Prospectus’ Level II Expansion or Series B Business Plan assists companies and entrepreneurs that are seeking to expand or scale their business, including by increasing market share.
- The Level II Start-up Plan helps to define concepts, target markets and market potential, as well as financial clarity necessary to define your concept, identify your market potential, and identify capital requirements. Executive summary included.
Level III Enterprise Business Plan »
- Prospectus’ Level III Enterprise Business Plan serves the need of those later stage and established companies seeking to raise additional capital to expand their businesses, often in the form of issuing debt securities such as bonds or convertible notes.
- The Level III Enterprise Business Plan is our most comprehensive business plan and often our clients will need a prospectus or a private placement memorandum (offering memorandum) written as well.
Our firm has years of experience drafting securities documents and is confident we can assist with your Moscow Business Plan Writer. Feel free to contact us anytime, or call us to setup an appointment at any one of our global offices.
Contact Us Today To Schedule Your Free Consultation
- Prospectus Writing
- IPO Stock Exchange Listing
- Bonds Offerings
- 144A Reg S Offerings
- Hedge Funds and Mutual Funds
- Offering Memorandum
- Private Placement Memorandum
- Offering Circular
- Explanatory Memorandum
- Information Memorandum
- Fund Setup Formation
- Securities Identifiers
- Registration and Filing
- Business Plans
Newsletter Sign Up
Get the latest updates sent to your email
For Unique Capital Growth Strategies
Questions? Fill out the Contact form , or get in touch:
- (212 ) 812-2127
- [email protected]

City Politics | Chesapeake’s proposed budget includes money for…
Share this:.
- Click to share on Facebook (Opens in new window)
- Click to share on X (Opens in new window)
e-Pilot Evening Edition
- Latest Headlines
- Environment
City Politics
City politics | chesapeake’s proposed budget includes money for public safety training academy, pay increases.

CHESAPEAKE — The city’s nearly $2 billion proposed budget and capital improvement plan earmarks more than $100 million to fund a new public safety training academy in southern Chesapeake, along with general wage increases and additional funding for open space preservation.
The proposed operating budget for fiscal year 2025 is $1.6 billion, which represents a nearly 4% increase from the previous adopted budget . The total proposed budget is nearly $2 billion when including the city’s capital improvement plan.
City Manager Christopher Price and Budget Director Jonathan Hobbs presented the proposed spending plan to City Council members this week during a work session. Residents have the opportunity to weigh in on the budget throughout April during upcoming work sessions ahead of the regular council meetings. Council members are expected to adopt the budget in May, and it will span from July 1 to June 30, 2025.
The proposed budget doesn’t include any new fees, but homeowners can expect to see slightly higher tax bills because of a nearly 4.5% increase in real estate assessments citywide — still a slower rate of growth than the previous two years. In the city’s past two fiscal budgets, council reduced the real estate tax rate by 4 cents, making it $1.01 per $100 of valuation, to help offset steep increases in assessments. The proposed fiscal 2025 budget keeps the rate at $1.01.
About $390.5 million in real estate tax revenue is expected for fiscal 2025, which is 4.3% more than the fiscal 2024 budget. But a change in the proposed budget is the dedication of a half-cent of real estate tax to the city’s lockbox to help fund debt service on the new public safety training academy project. The half-cent dedication is expected to generate nearly $1.8 million, with all allocations to the city lockbox totaling $29 million in fiscal 2025.
The new training facility is a top priority in the capital improvement program and is expected to cost a total of $150 million. The fiscal 2025 budget earmarks $104.5 million for the project. The academy will be located on a portion of the Heritage Park site near Fire Station 7 and Saint Brides Road and will include multiple classrooms, housing for training administration, indoor shooting ranges, burn buildings, a confined space maze, a vehicle extrication training area, canine training area and other outdoor training facilities.
The proposed budget also includes more than $9 million for a 3.5% general wage increase for employees, some of whom may receive more as a market adjustment that keeps Chesapeake workers’ pay competitive and within the top three cities in Hampton Roads.
For the 2023 fiscal budget, council increased the city’s meal tax to 6%. Over the previous two fiscal years, actual revenue from the meal tax has grown 21.1% and 19.7%, respectively, with city leaders attributing the increases to inflation in the prices of groceries and prepared meals along with wage increases that enabled persistent consumer expenditures. For the proposed fiscal budget, restaurant food tax revenue is expected to be $45 million, a 14% increase from last year’s budget.
Chesapeake School Board approves $801 million budget request that includes pay raises
About $861 million will fund the city’s capital improvement plan through 2029, with $367.5 million allocated in 2025. City leaders said the capital budget is being heavily impacted by inflation, leading to some projects no longer being fully funded and in need of additional funding down the road. Besides the new training academy, other major priorities in the plan include about $8.7 million for facility maintenance — particularly the replacement of security technology — and $3.1 million in new funding for the acquisition and preservation of open space and agricultural land.
The budget also includes the addition of 20 new deputy sheriff and deputy sergeant positions for the sheriff’s office following the closure of the Hampton Roads Regional Jail . Additional state revenue will allow for four more behavioral health case workers for the sheriff’s office as well.
Per a council request, the cost of concealed carry permit fees were also cut in half and now cost $25.
Natalie Anderson, 757-732-1133, [email protected]
More in City Politics

Transportation | Newport News plans to reconfigure a Warwick Boulevard intersection to reduce crash rate

Business | Outdoor inflatable park could pop up soon in Virginia Beach mall parking lot

Housing | Developer seeks to turn empty Norfolk church into affordable senior housing

City Politics | Owners of Dollywood, Ripley’s are interested in Virginia Aquarium, but foundation not on board
Trending nationally.

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Press Releases
Department of Homeland Security Unveils Artificial Intelligence Roadmap, Announces Pilot Projects to Maximize Benefits of Technology, Advance Homeland Security Mission
DHS Will Launch Three Pilot Projects to Test AI Technology to Enhance Immigration Officer Training, Help Communities Build Resilience and Reduce Burden for Applying for Disaster Relief Grants, and Improve Efficiency of Law Enforcement Investigations
WASHINGTON – Today, Secretary of Homeland Security Alejandro N. Mayorkas and Chief Information Officer and Chief Artificial Intelligence Officer Eric Hysen announced the Department of Homeland Security’s (DHS) first “Artificial Intelligence Roadmap.” The roadmap details DHS’s 2024 plans, including to test uses of the technologies that deliver meaningful benefits to the American public and advance homeland security, while ensuring that individuals’ privacy, civil rights, and civil liberties are protected.
As part of the roadmap, DHS announced three innovative pilot projects that will deploy AI in specific mission areas. Homeland Security Investigations (HSI) will test AI to enhance investigative processes focused on detecting fentanyl and increasing efficiency of investigations related to combatting child sexual exploitation. The Federal Emergency Management Agency (FEMA) will deploy AI to help communities plan for and develop hazard mitigation plans to build resilience and minimize risks. And, United States Citizenship and Immigration Services (USCIS) will use AI to improve immigration officer training.
“The unprecedented speed and potential of AI’s development and adoption presents both enormous opportunities to advance our mission and risks we must mitigate,” said Secretary of Homeland Security Alejandro N. Mayorkas . “The DHS AI roadmap and pilots will guide our efforts this year to strengthen our national security, improve our operations, and provide more efficient services to the American people, while upholding our commitment to protect civil rights, civil liberties, and privacy. What we learn from the pilot projects will be beneficial in shaping how the Department can effectively and responsibly use AI across the homeland security enterprise moving forward.”
The roadmap lays out DHS’s initiatives in AI, describes the potential of AI technologies across the Department, and offers clearer visibility into the Department’s approach to AI, while underscoring the Department’s commitment to responsible utilization.
The AI roadmap outlines three lines of effort DHS is using to guide its work:
- Responsibly leverage AI to advance Homeland Security missions while protecting individuals’ privacy, civil rights, and civil liberties – DHS is committed to ensuring that its use of AI fully respects privacy, civil liberties, and civil rights, is rigorously tested to avoid bias, disparate impact, privacy harms, and other risks, and that it is understandable to the people we serve.
- Promote Nationwide AI Safety and Security – Advances in AI will revolutionize the delivery of essential goods and services upon which Americans rely. AI can create tremendous efficiencies and benefits for citizens, but it can also present new and novel risks. To protect U.S. cyber networks and critical infrastructure, DHS will help govern the safe and responsible development and use of AI.
- Continue to lead in AI through strong cohesive partnerships – DHS will foster strong relationships with private sector, academia, State, Local, Territorial, and Tribal governments, international partners, non-government organizations, research institutions, and thought leaders to accelerate the development and deployment of AI solutions tailored to the unique challenges faced by the DHS. In line with the DHS’s commitment to transparency and visibility into the Department’s vision for AI and to ensuring responsible use, DHS will continue to share information and engage with communities, advocates, and partners to demonstrate responsible AI use.
DHS’s three new pilot programs will allow the Department to assess the efficacy of AI in improving its mission capabilities. Each pilot team is partnering with privacy, cybersecurity, and civil rights and civil liberties experts throughout their development and evaluation process. This work will inform Department-wide policies on AI governance. DHS offices and agencies submitted dozens of proposals for consideration to the Chief AI Officer, who selected three pilots that would best support evaluating the effectiveness of Large Language Models (LLM) and Generative AI technology at DHS.
The new pilot programs announced today will:
- Transform Security Investigative Processes, Unlock Data-Driven Insights, and Improve Mission Outcomes – HSI’s pilot project will strengthen their investigative processes by introducing a LLM-based system designed to enhance the efficiency and accuracy of summaries investigators rely upon. The LLM-based system will leverage open-source technologies to allow investigators to more quickly summarize and search for contextually relevant information within investigative reports. The pilot could lead to increases in detection of fentanyl-related networks, aid in identification of perpetrators and victims of child exploitation crimes, and surface key patterns and trends that could further HSI’s vital work.
- Bolster Planning Assistance for Resilient Communities – FEMA will launch a GenAI pilot to create efficiencies for the hazard mitigation planning process for local governments, including underserved communities. Hazard mitigation plans are not only a foundational step that communities can take to build their resilience but can be lengthy to produce and challenging for communities that lack resources to do so. The pilot will specifically support State, Local, Tribal, and Territorial governments’ understanding of how to craft a plan that identifies risks and mitigation strategies as well as generate draft plan elements—from publicly-available, well-researched sources — that governments could customize to meet their needs. This pilot could lead to more communities having the ability to submit grant applications for funding to become more resilient and reduce disaster risks.
- Enhance Immigration Officer Training through Generative AI – United States Citizenship and Immigration Services is developing an interactive application that uses GenAI to improve the way the agency trains immigration officer personnel. USCIS will generate dynamic, personalized training materials that adapt to officers’ specific needs and ensure the best possible knowledge and training on a wide range of current policies and laws relevant to their jobs. The goal is to help enhance trainees’ understanding and retention of crucial information, increase the accuracy of their decision making process, and limit the need for retraining over time.
The roadmap and announcement of pilot programs are the latest in the Department’s ongoing AI initiatives.
In February, Secretary Mayorkas and CIO Hysen announced the Department’s first-ever hiring sprint to recruit 50 AI technology experts to help build teams that will help better leverage AI responsibly across strategic areas of the homeland security enterprise. These include efforts to counter fentanyl, combat child sexual exploitation and abuse, deliver immigration services, secure travel, fortify our critical infrastructure, and enhance our cybersecurity. DHS has received a strong response to date and is in the process of reviewing. interviewing, and hiring AI technologists to support mission-enhancing initiatives. The Department continues to accept applications on dhs.gov/AI .
Last year, DHS established the Department’s first AI Task Force and named CIO Hysen its first Chief AI Officer. Informed by the Task Force’s work over the past 11 months, DHS has identified areas where AI can enhance the effectiveness of the Department’s efforts — helping pave the way for this roadmap and these new projects. The Task Force’s focus is on DHS’s entire mission space. For instance, it is working to enhance the integrity of our supply chains and the broader trade environment by helping deploy AI to improve cargo screening, the identification of imported goods produced with forced labor, and risk management. The Task Force is also charged with using AI to better detect fentanyl shipments, identify and interdict the flow of precursor chemicals around the world, and disrupt key nodes in criminal networks.
The Department’s latest efforts follow President Biden’s Executive Order (EO) “ Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence ,” signed in October2023. The EO directed DHS to promote the adoption of AI safety standards globally, protect U.S. networks and critical infrastructure, reduce the risks that AI can be used to create weapons of mass destruction, combat AI-related intellectual property theft, and help the United States attract and retain skilled talent, among other missions. The President has directed DHS to establish an AI Safety and Security Advisory Board to support the responsible development of AI. This Board will bring together preeminent industry experts from AI hardware and software companies, leading research labs, critical infrastructure entities, and the U.S. government. This Board will issue recommendations and best practices for an array of AI use cases to ensure AI deployments are secure and resilient.
To read the DHS AI Roadmap, visit the DHS Artificial Intelligence Roadmap webpage .
To learn more about how DHS uses AI technologies to protect the homeland, visit Artificial Intelligence at DHS .
- Secretary of Homeland Security
- Science and Technology
- Artificial Intelligence (AI)
- Federal Emergency Management Agency (FEMA)
- Homeland Security Investigations (HSI)
- U.S. Citizenship and Immigration Services (USCIS)
- Election 2024
- Entertainment
- Newsletters
- Photography
- Personal Finance
- AP Buyline Personal Finance
- Press Releases
- Israel-Hamas War
- Russia-Ukraine War
- Global elections
- Asia Pacific
- Latin America
- Middle East
- Election Results
- Delegate Tracker
- AP & Elections
- March Madness
- AP Top 25 Poll
- Movie reviews
- Book reviews
- Personal finance
- Financial Markets
- Business Highlights
- Financial wellness
- Artificial Intelligence
- Social Media
AT&T notifies users of data breach and resets millions of passcodes
FILE - An AT&T sign is seen at a store in Pittsburgh, Monday, Jan. 30, 2023. AT&T said, Saturday, March 30, 2024, it has begun notifying millions of customers about the theft of personal data recently discovered online. (AP Photo/Gene J. Puskar, File)
- Copy Link copied
AT&T said it has begun notifying millions of customers about the theft of personal data recently discovered online.
The telecommunications giant said Saturday that a dataset found on the “dark web” contains information such as Social Security numbers for about 7.6 million current AT&T account holders and 65.4 million former account holders.
The company said it has already reset the passcodes of current users and will be communicating with account holders whose sensitive personal information was compromised.
It is not known if the data “originated from AT&T or one of its vendors,” the company said in a statement. The compromised data is from 2019 or earlier and does not appear to include financial information or call history, it said. In addition to passcodes and Social Security numbers, it may include email and mailing addresses, phone numbers and birth dates.
While the data surfaced on a hacking forum nearly two weeks ago, it closely resembles a similar data breach that surfaced in 2021 but which AT&T never acknowledged, said cybersecurity researcher Troy Hunt .
“If they assess this and they made the wrong call on it, and we’ve had a course of years pass without them being able to notify impacted customers,” then it’s likely the company will soon face class action lawsuits, said Hunt, founder of an Australia-based website for warning people when their personal information has been exposed.
An AT&T spokesperson didn’t immediately return a request for comment Saturday.
It is not the first crisis this year for the Dallas-based company. An outage in February temporarily knocked out cellphone service for thousands of U.S. users. AT&T at the time blamed the incident on a technical coding error, not a malicious attack.

IMAGES
VIDEO
COMMENTS
The breakout of the funding is below: Office design/build: $100,000. Three months of overhead expenses (payroll, rent, utilities): $100,000. Marketing & advertising: $50,000. Working capital: $50,000. Easily complete your Security Company business plan! Download the Security Company business plan template (including a customizable financial ...
How to Create a Winning Security Guard Training Company Business Plan. If you've done your homework, you already know that writing a business plan is the most critical thing you can do for your company. Although it might seem like an unnecessary formality, your security guard training company's business plan is a document that will shape your ...
Traditionally, a marketing plan includes the four P's: Product, Price, Place, and Promotion. For a security guard business plan, your marketing strategy should include the following: Product: In the product section, you should reiterate the type of security company that you documented in your company overview.
Start a Security Training Business. 180 comments; 44,660 views; Though there are countless business opportunities, the one that remains unique is the security training business. Your business will have increased attention due to the demand for security personnel everywhere. Have the right approach and the perfect time to begin earning good ...
Step1: Ideate the Business. The first part of any security business plan sample is the description of the company that you are trying to start. Nothing happens without an idea. Therefore, Jacques decided to build on his dream and create a concrete idea for his business plan of a security company.
Start a security guard company by following these 10 steps: Plan your Security Guard Company. Form your Security Guard Company into a Legal Entity. Register your Security Guard Company for Taxes. Open a Business Bank Account & Credit Card. Set up Accounting for your Security Guard Company.
Steps to Starting a Security Company. Choose a specialty. Develop a business plan. Legal and financial considerations. Marketing your business. Hiring employees. Necessary Licenses and Requirements. Different state requirements. California specific requirements.
Get access to Upmetrics software, invite your team members and start writing your business plan. 1. Get tried and tested tips. Upmetrics business plan builder gives you everything you need to stay in sync and guides you on every step of your business plan writing. 3. Stunning business plan cover pages.
Here are some tips for choosing a name for your security company: Make sure the name is available. Check your desired name against trademark databases and your state's list of registered business names to see if it's available. Also check. to see if a suitable domain name is available. Keep it simple.
The market for security guard services includes building management companies, retail businesses, event venues, and other businesses. IBISworld.com reports that the security services industry as a whole was $29.7 billion in 20xx. While this number includes investigative services and armored car services, it is estimated that security guards ...
Knowing your market is essential to building a successful security consulting business. To develop an effective plan, you must identify the needs of your target customers and tailor your services accordingly. Whether serving small businesses, large corporations, government agencies, or individuals, each sector will require a unique approach and ...
Video Documentation Service Business Plan. Safe Keeping is a start-up business offering video documentation of home or business belongings for customer's insurance purposes. Online and physical security is a necessary measure for businesses to keep their employees, clients, and data secure. Whether you're providing trained security staffing ...
Sales estimates projects revenues of approximately $1.4 million in the first year, and $1.7 million by year 3. Our projections contained herein are authentic and will be used as the budget for business. The firm estimates profits of approximately $329,235 by year 3 with a net profit margin of 19.28%.
Traditionally, a marketing plan includes the four P's: Product, Price, Place, and Promotion. For a cyber security business plan, your marketing strategy should include the following: Product: In the product section, you should reiterate the type of cyber security company that you documented in your company overview.
Business Plan of ABC Security (Pty) Ltd. 3.3 Business Operational Strategy 3.3.1 Marketing Strategy 3.3.1.1 Viral Marketing ABC will focus on excellent service delivery standards to build a strong wave of viral marketing. This is the best and most price effective form of marketing. Word of mouth produces immediate trust and doesn't cost money.
Security Policies and Training: Develop clear policies and conduct training to educate employees on security measures, reporting procedures, and emergency responses. Incident Response Planning: Establish a plan outlining steps to be taken during security breaches or incidents, with assigned roles and responsibilities.
3. Set your goals. The goal of your security plan is to protect your small business. However, several smaller goals play into this larger objective. In a perfect world, creating a plan to prevent cyber attacks, and including a network security device like a firewall, would be enough.
A master security plan is a detailed, long-term strategy that entails all the aspects of security operations in an organization. For such programs to be successful, they must be based on two core principles. First, it must be in line with your business's strategic plans while combining the best principles for protection and support.
In order to start a security company, you will need to register with the Private Security Regulatory Authority (PSIRA). This is one of the governing bodies of private security companies in South Africa. You will have to pay a registration fee and complete an exam to determine your competence level. On completion and passing of the exam, you ...
2. Design a plan to influence behaviors on an organizational scale. Behaviors drive actions, so if we can change behaviors, we can achieve the changes we need to impact security culture.
An incident response plan Employees need to be educated on proper procedures to follow in the event of a security incident or breach. A well-prepared response can help minimize potential damage.
Business Plan Writer Moscow. A well written business plan is an essential component for any company seeking to raise capital. Our team at Prospectus.com has over 20 years of experience writing business plans and structuring business models for start-ups, later stage and expansion companies, those seeking venture or angel financing all the way to mezzanine and 144A funding, spanning a wide ...
Chesapeake's nearly $2 billion proposed operating budget and capital improvement plan earmarks more than $100 million to fund a new public safety training academy in southern Chesapeake, along ...
WASHINGTON - Today, Secretary of Homeland Security Alejandro N. Mayorkas and Chief Information Officer and Chief Artificial Intelligence Officer Eric Hysen announced the Department of Homeland Security's (DHS) first "Artificial Intelligence Roadmap." The roadmap details DHS's 2024 plans, including to test uses of the technologies that ...
dormakaba Group, a provider of access and security solutions, has committed to be a sponsor of All-over-IP 2017 in Moscow, 22-24 November. All-over-IP is a premier networking event that drives...
AT&T says it has begun notifying millions of customers about the theft of personal data recently discovered online. The telecommunications giant said Saturday that a dataset found on the "dark web" contains information such as Social Security numbers for about 7.6 million current AT&T account holders and 65.4 million former account holders.
The mission of Allied Joint Force Command Naples is to prepare for, plan and conduct military operations in order to preserve the peace, security and territorial integrity of Alliance member states and freedom of the seas and economic lifelines throughout SACEURs Area of Responsibility (AOR and beyond.
The Moscow city government plans to expand video surveillance and offer residents more services through the Internet in the next five years in a project worth 329.5 billion rubles ($11.7 billion). Video cameras will be installed in 95 percent of apartment buildings and 75 percent of infrastructure in the Russian capital by 2016, said a Bloomberg report.
House Republicans have a plan to raise the age at which Americans receive Social Security benefits — and the agency's leader isn't on board.. Earlier this week, the Republican Study Committee ...
Best Small Business Loans. Best Tax Software for Small Business. SELECT. All Taxes. Filing For Free ...